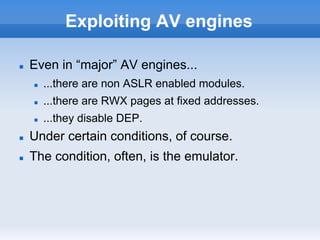
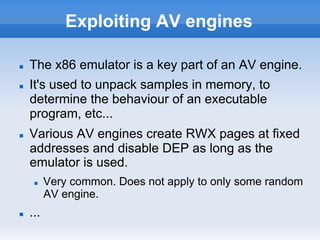
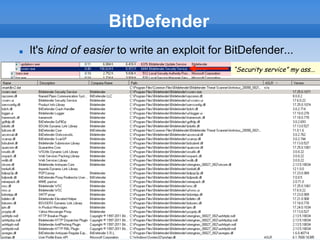
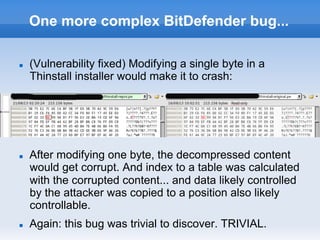
This document discusses breaking and attacking antivirus software. It begins by outlining common features of antivirus engines like being written in C/C++ and supporting various file formats. It then discusses attacking antivirus engines by exploiting vulnerabilities in how they handle different file formats and unpack files. Specific vulnerabilities found by fuzzing various antivirus engines are presented, including heap overflows and potential remote code execution issues. Methods for exploiting antivirus engines remotely are covered, noting ways the emulators used by antivirus software can be leveraged in attacks. The document concludes by providing details on local privilege escalation vulnerabilities the author found in some antivirus products.