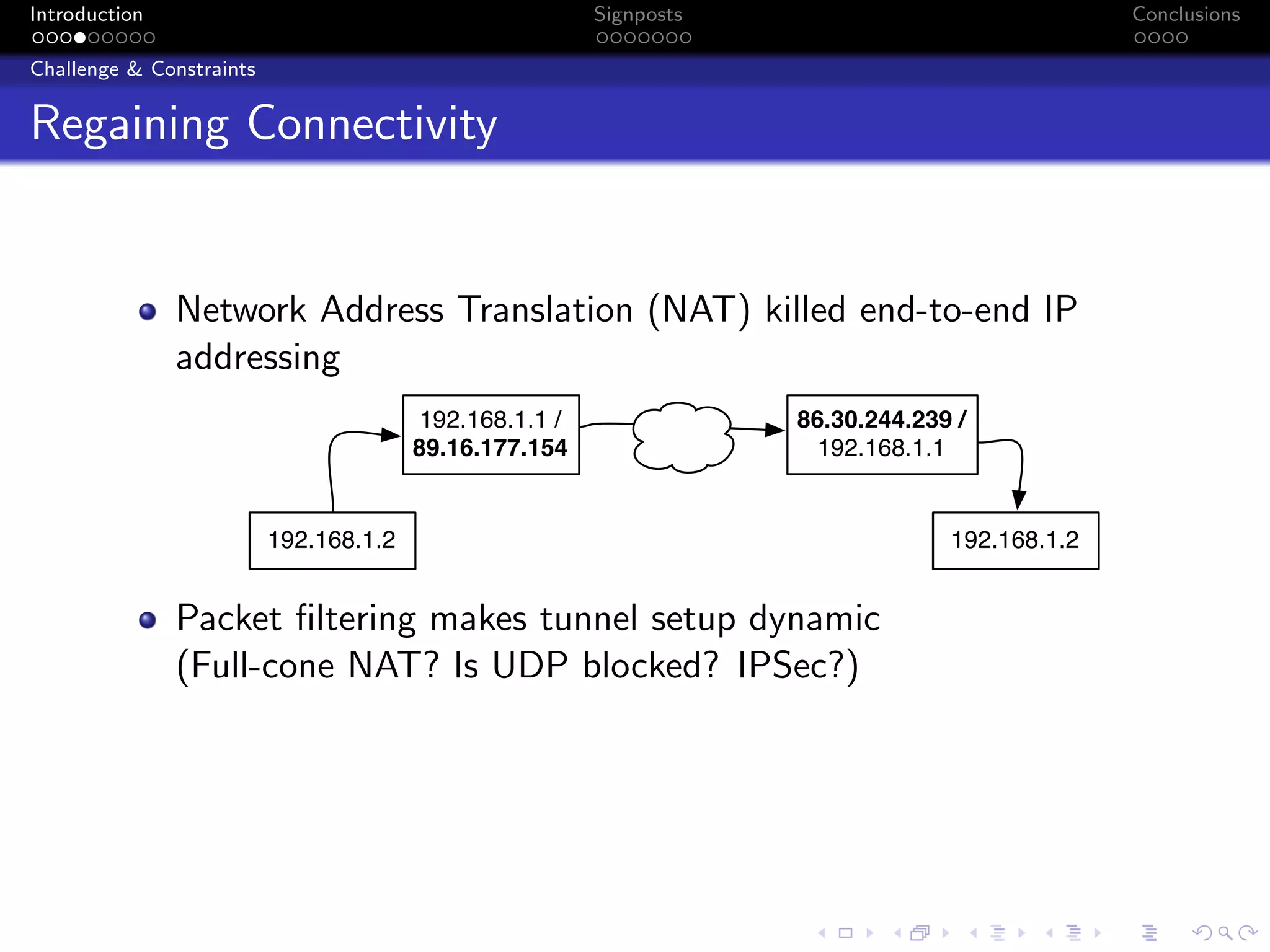
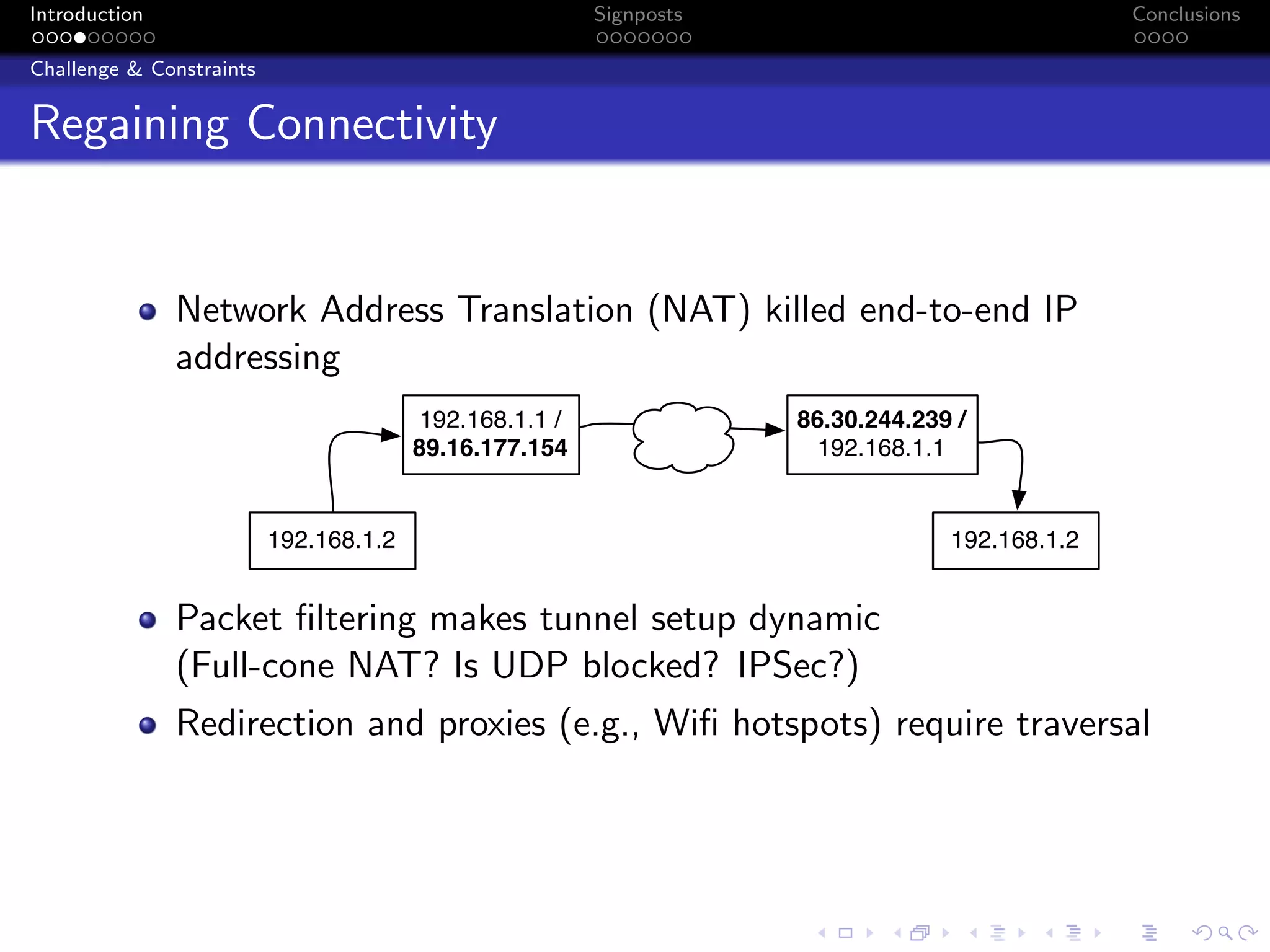
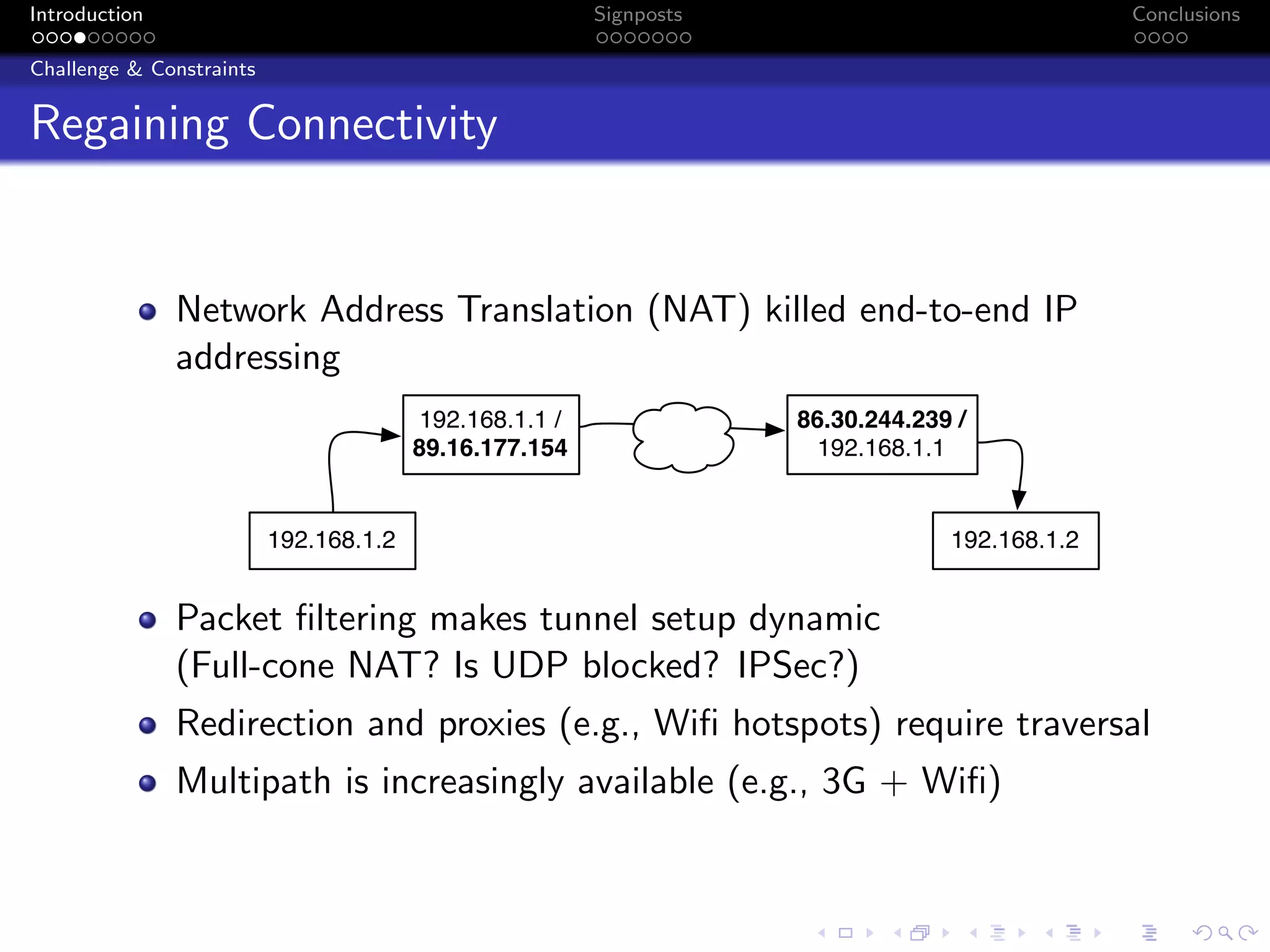
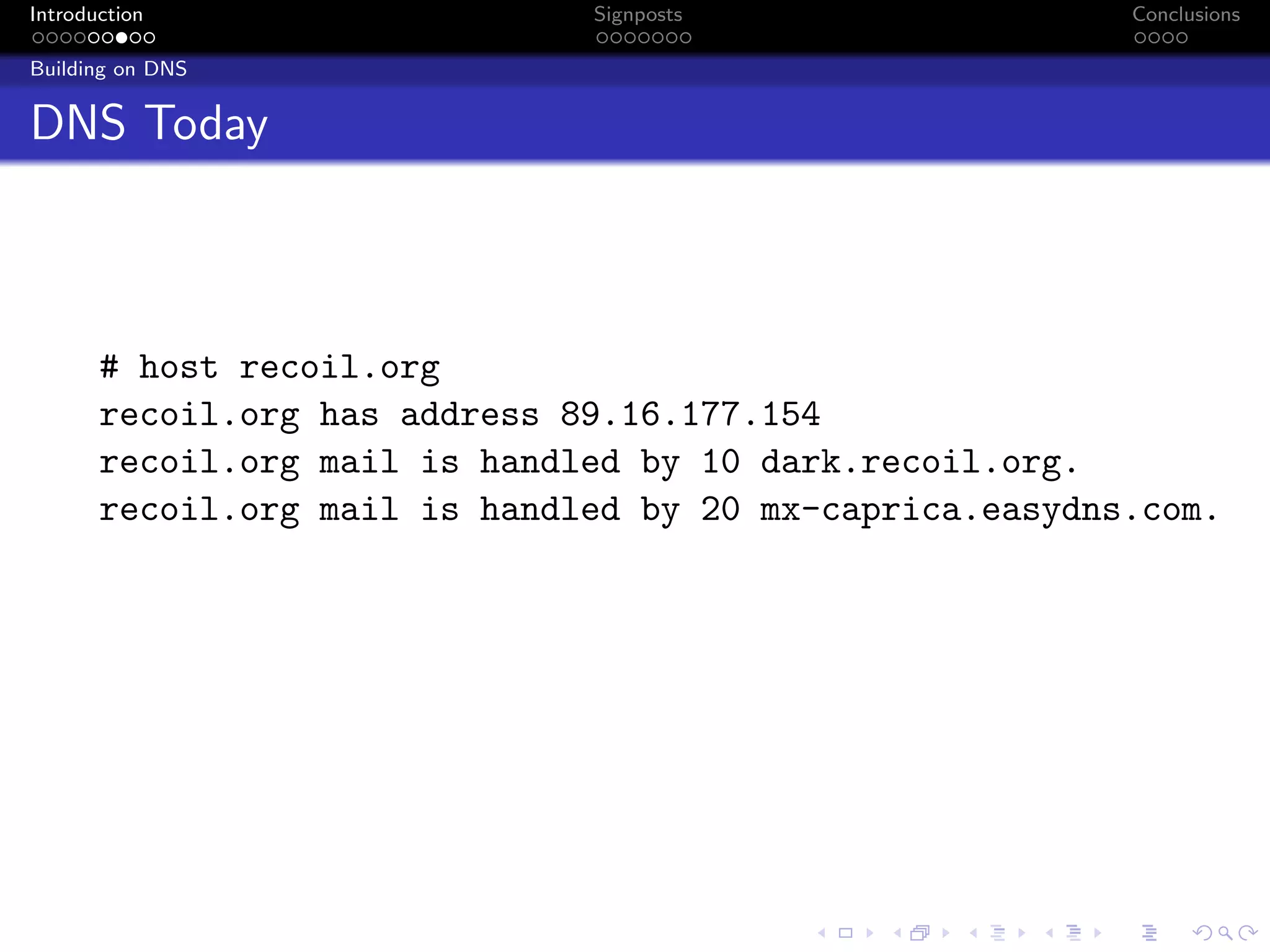
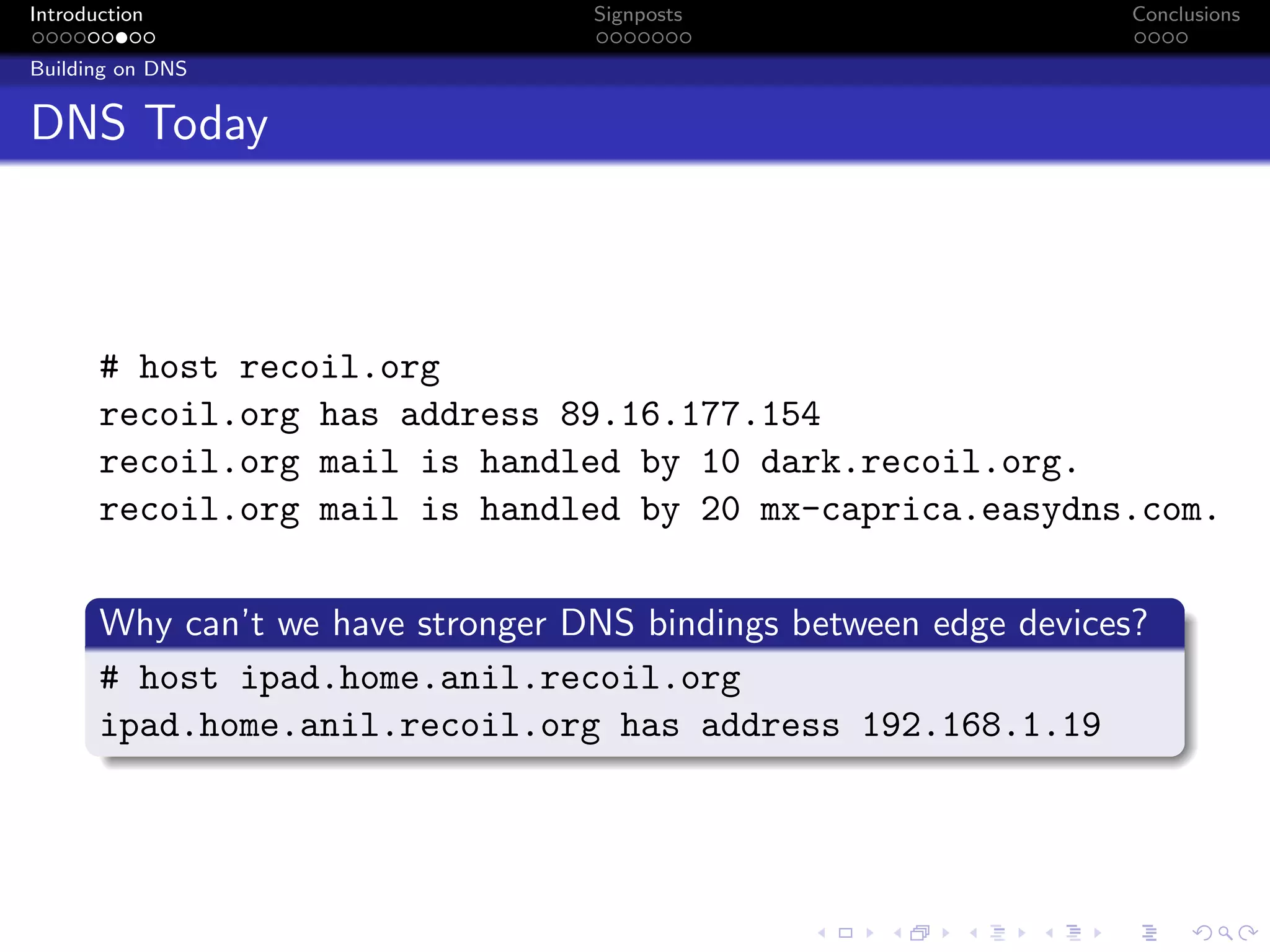
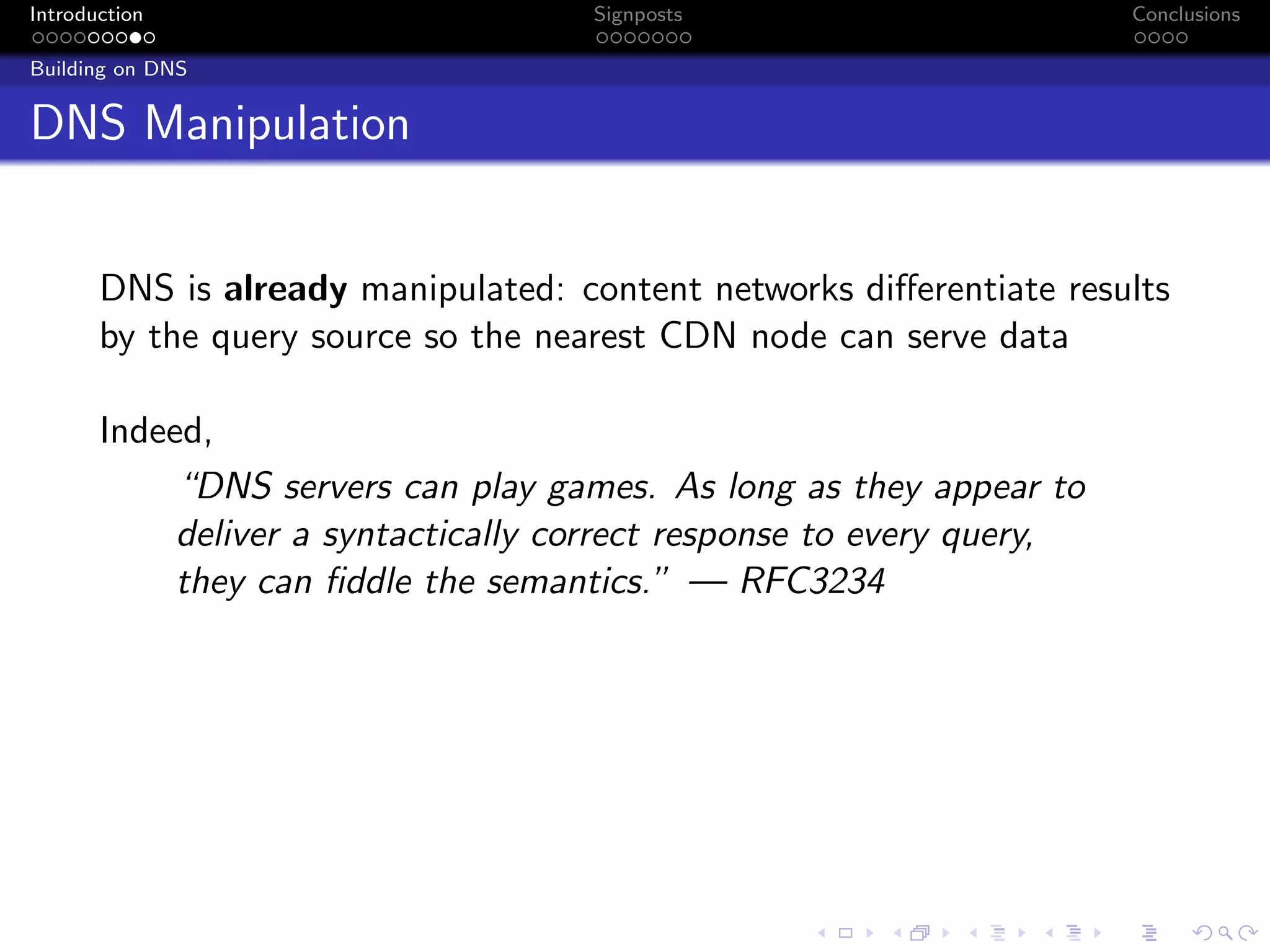
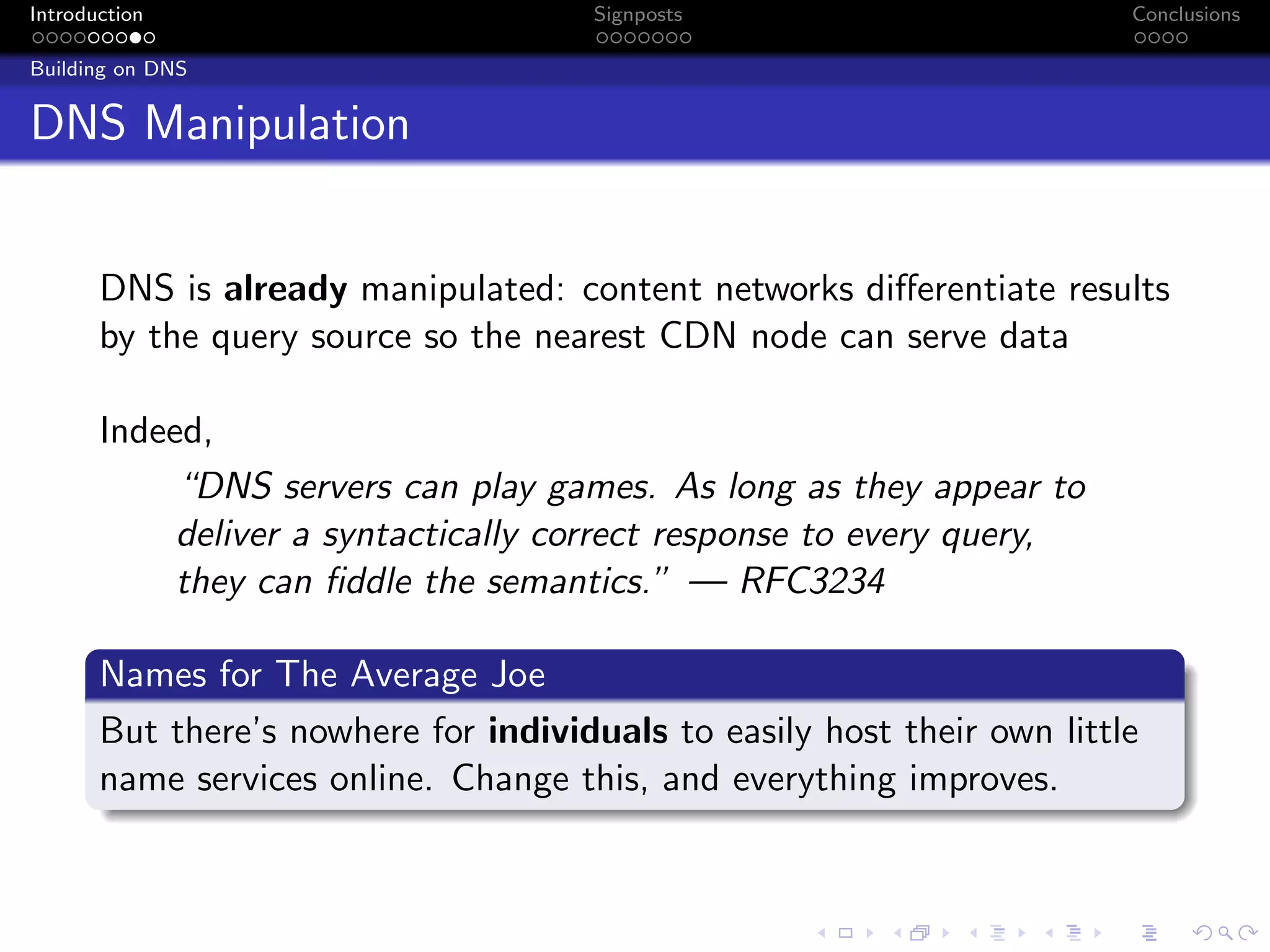
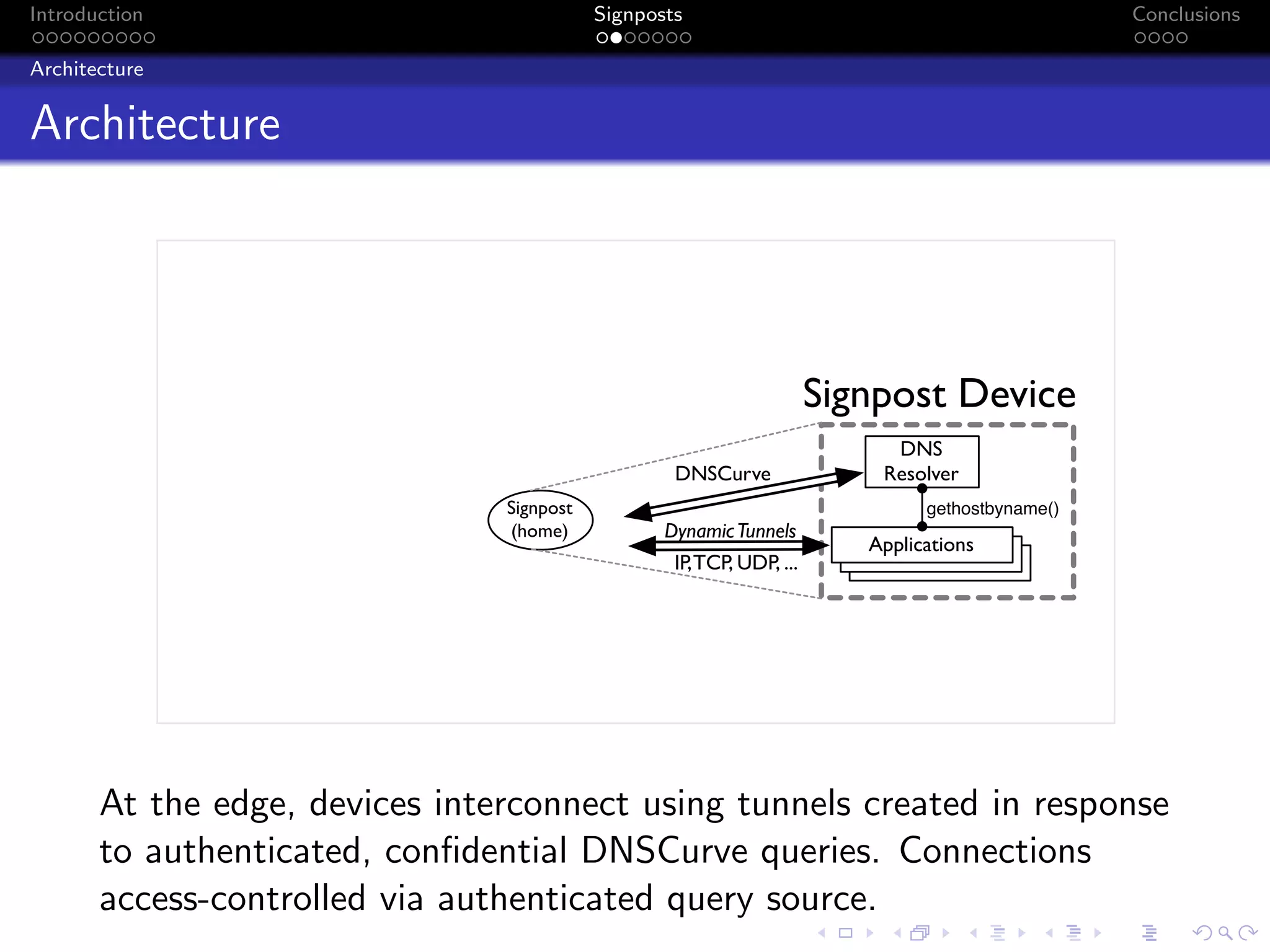
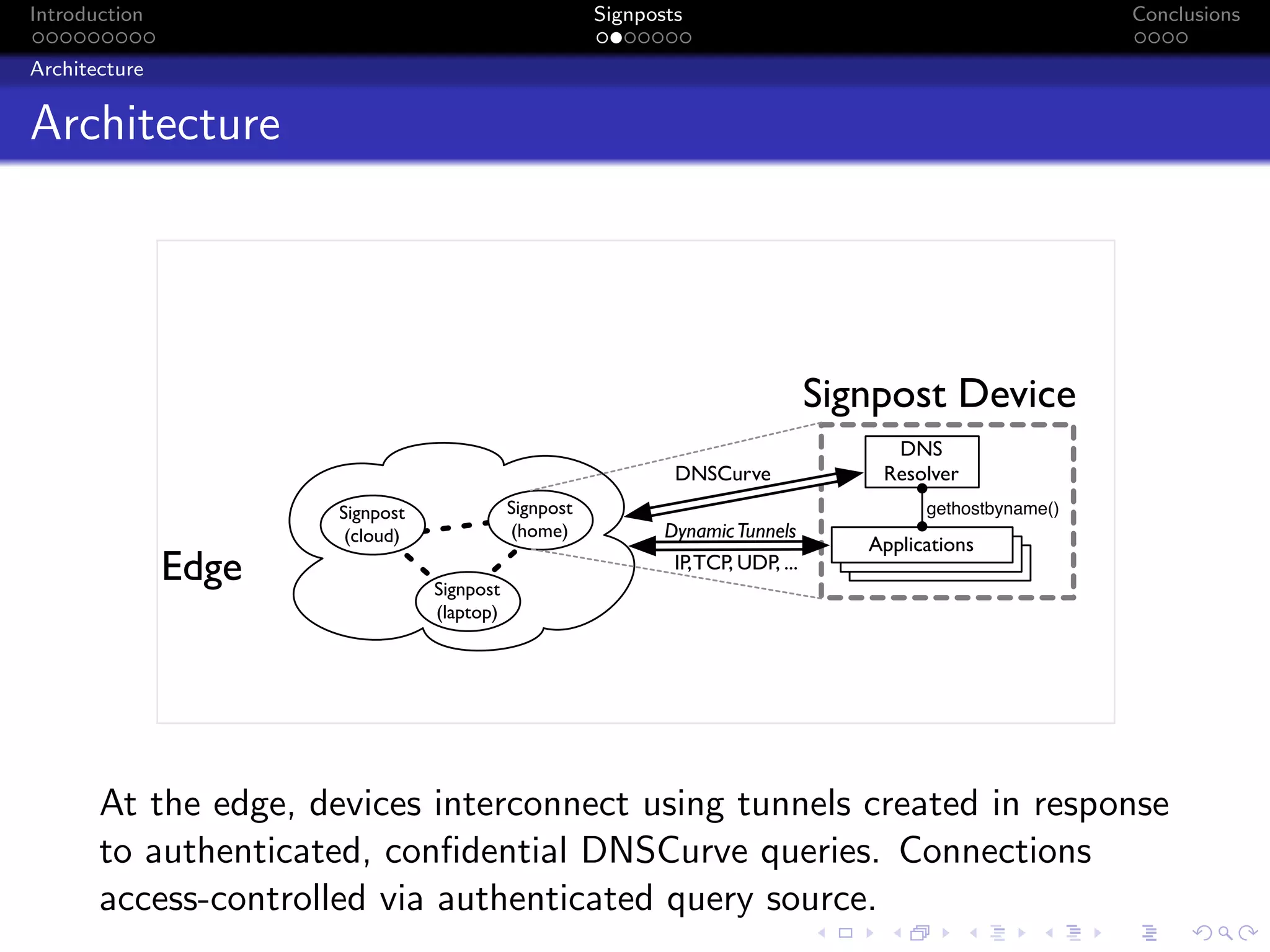
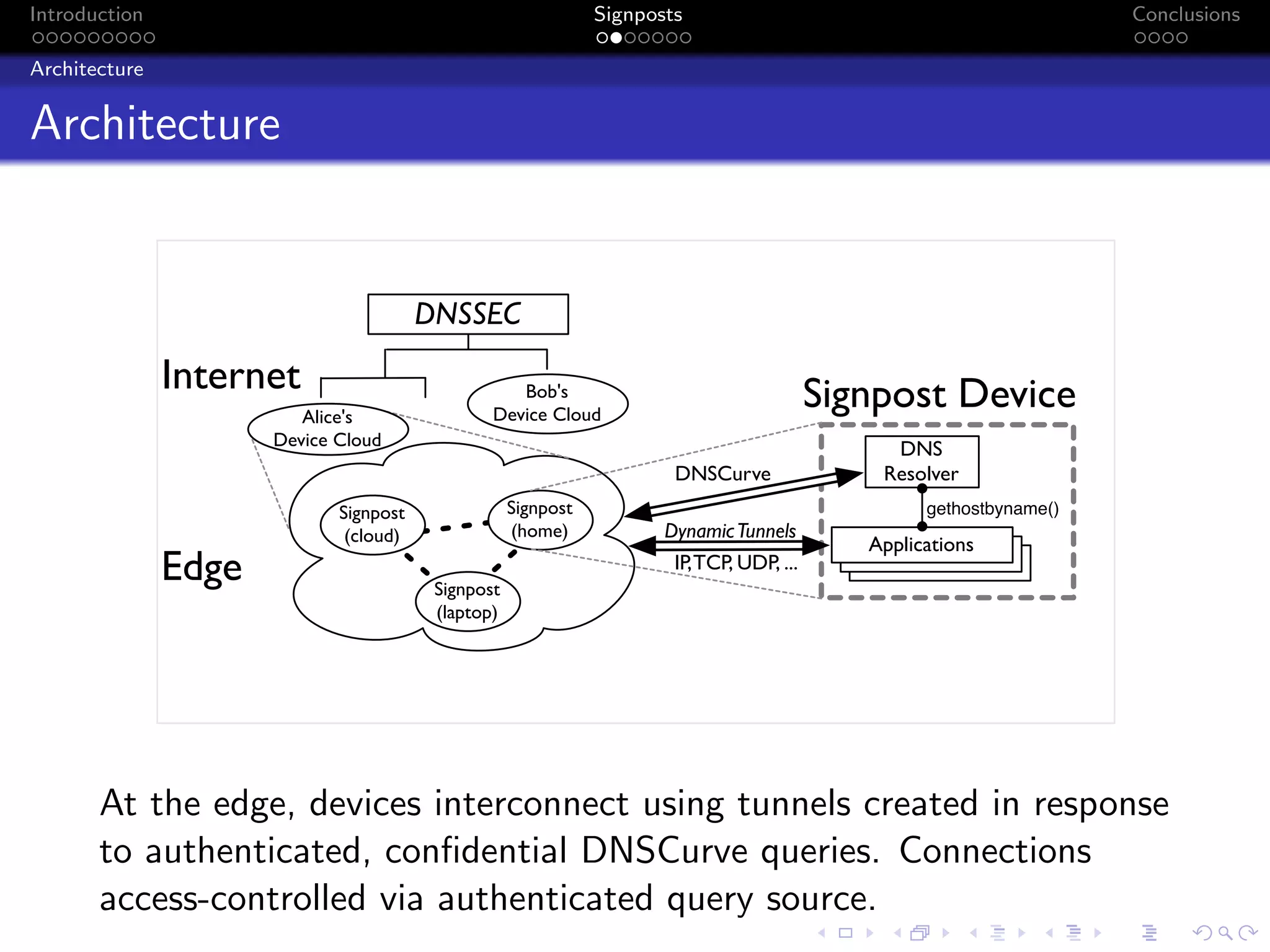
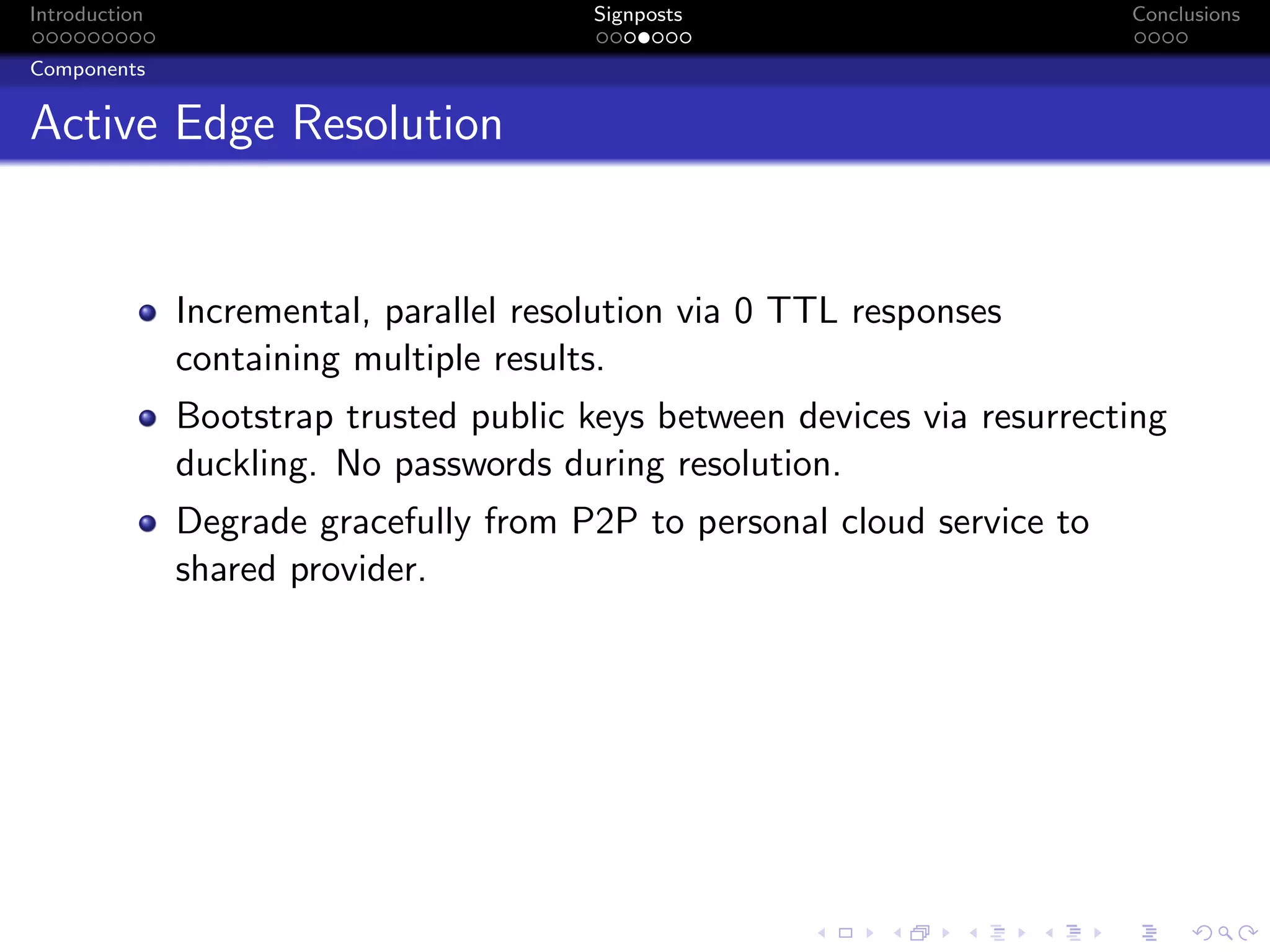
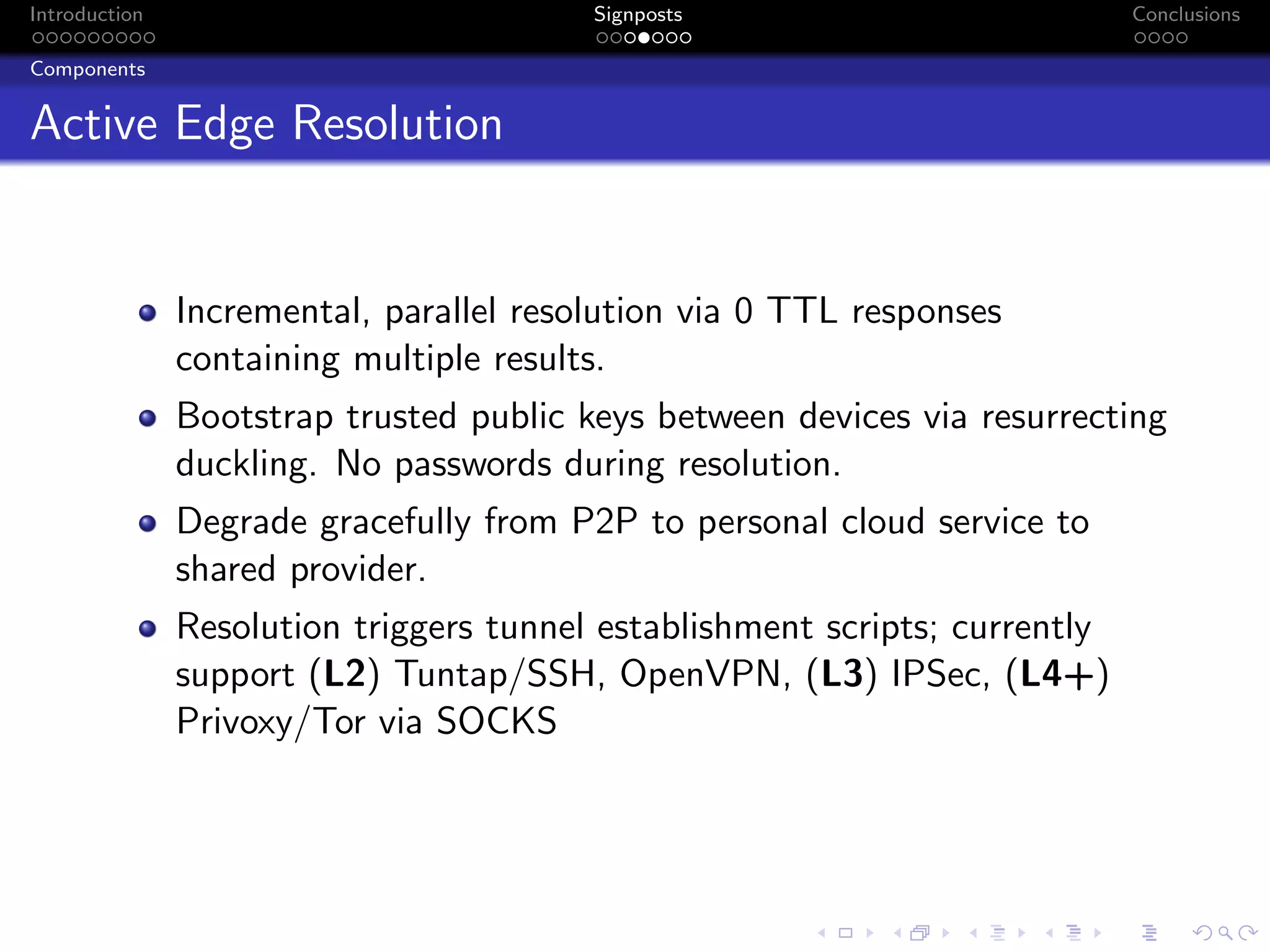
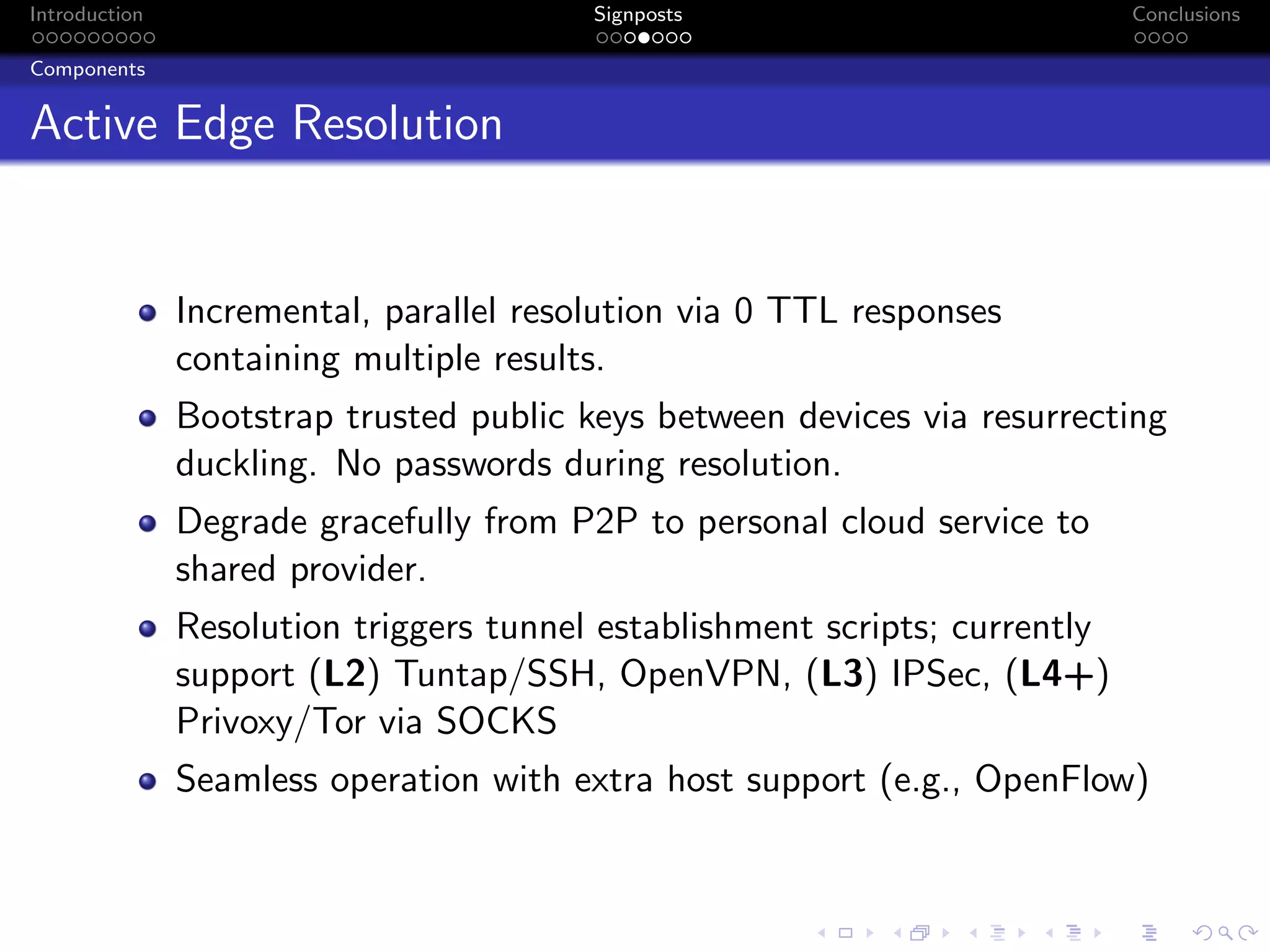
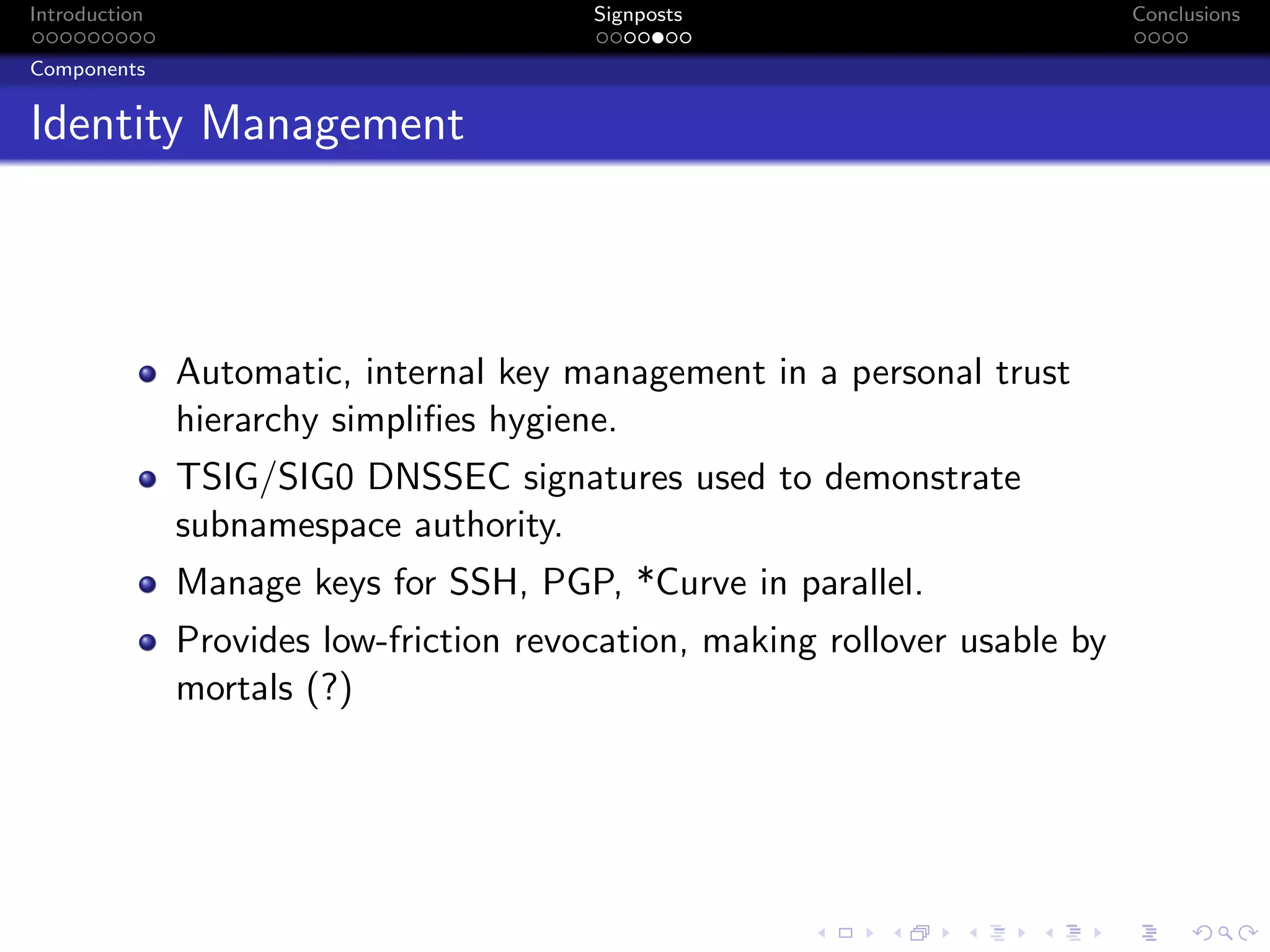
The document discusses the challenges posed by centralized cloud-hosted services, such as data loss and service shutdowns, and proposes a solution using DNS to establish personal clouds for secure and efficient app deployment. It outlines architectural components, constraints around compatibility and connectivity, and emphasizes the importance of end-to-end connectivity which has been impacted by network address translation (NAT). The proposed system aims to enhance individual user representation on the internet while ensuring robust security and efficient inter-device communication.