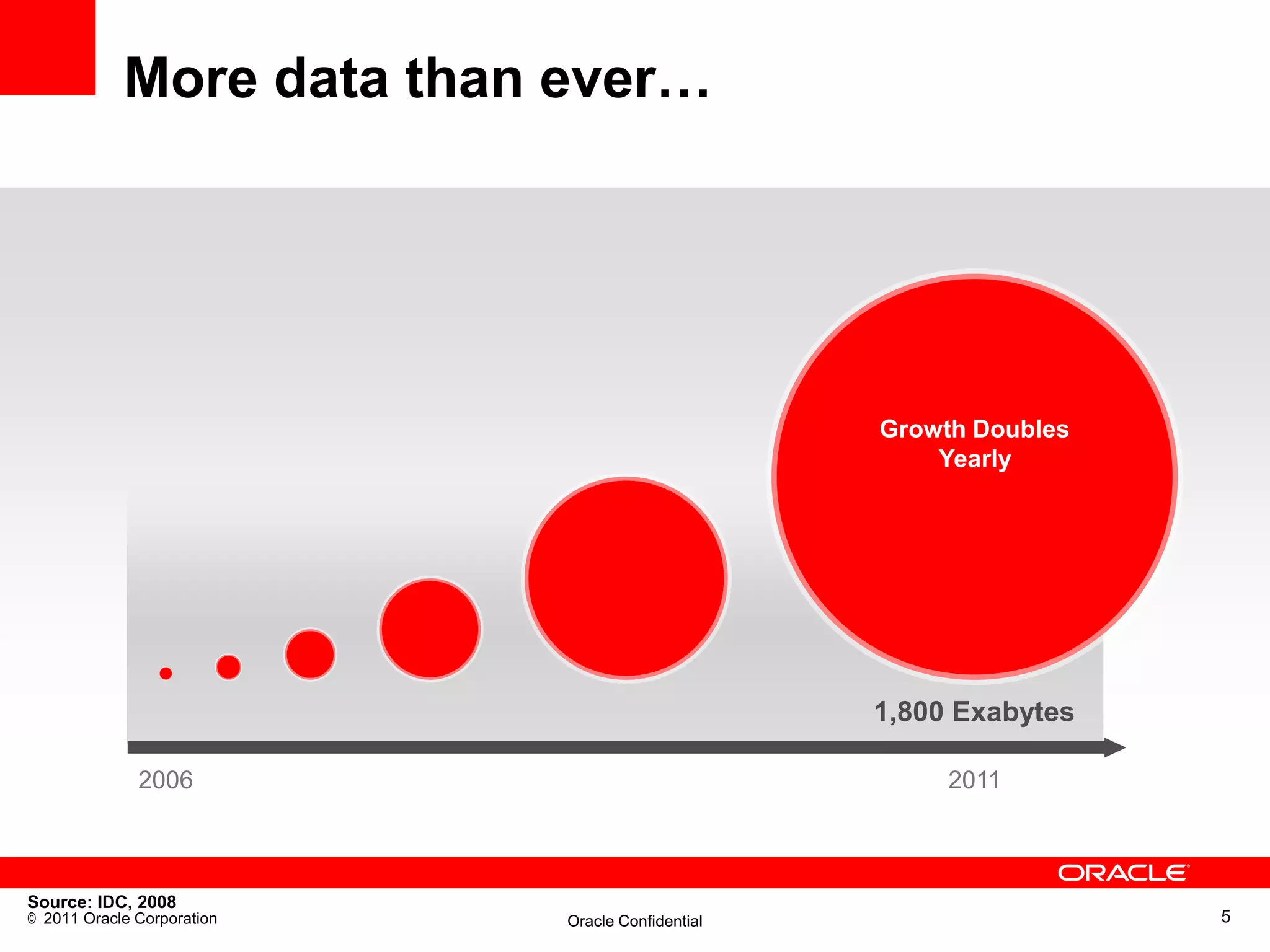
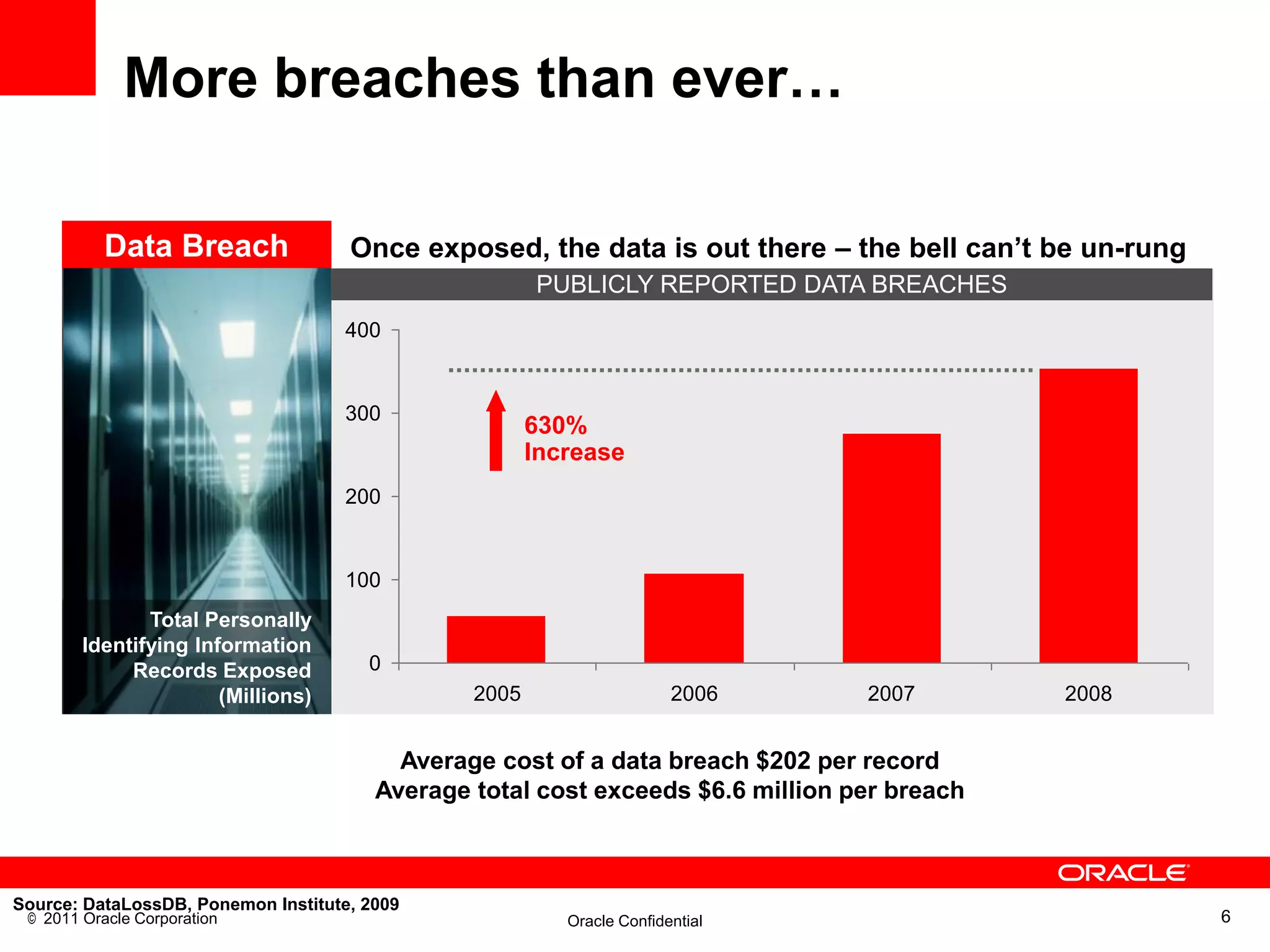
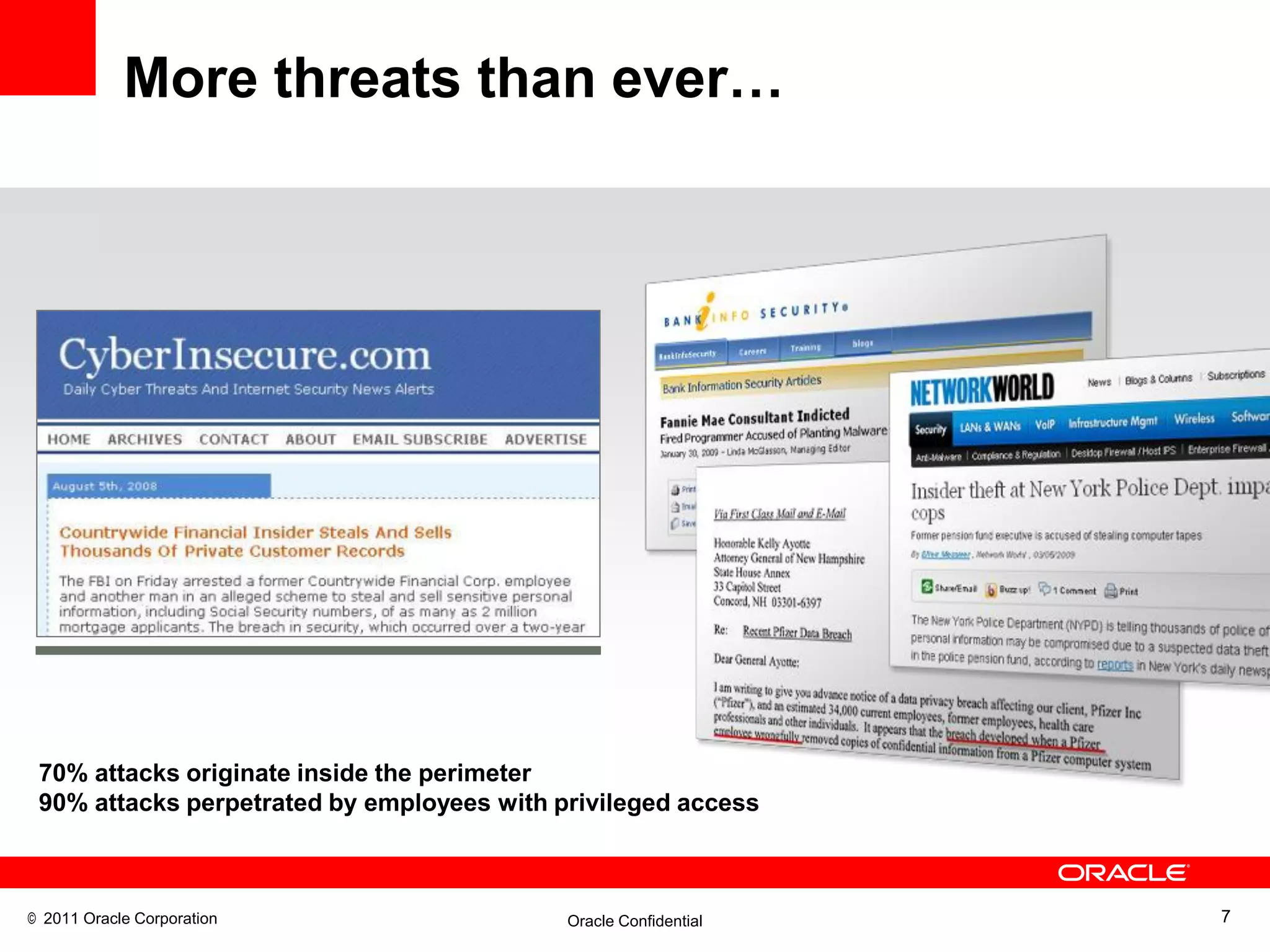
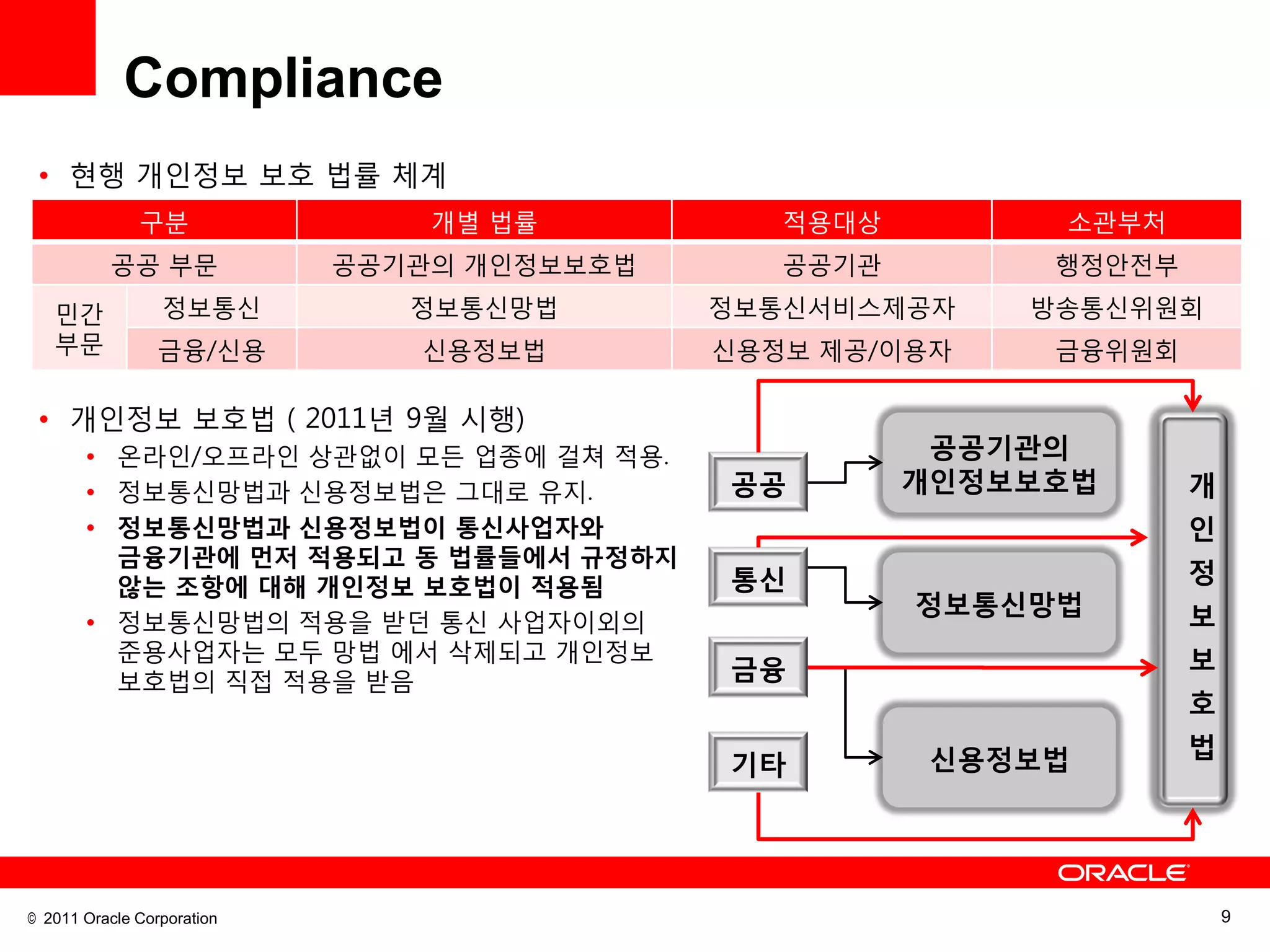
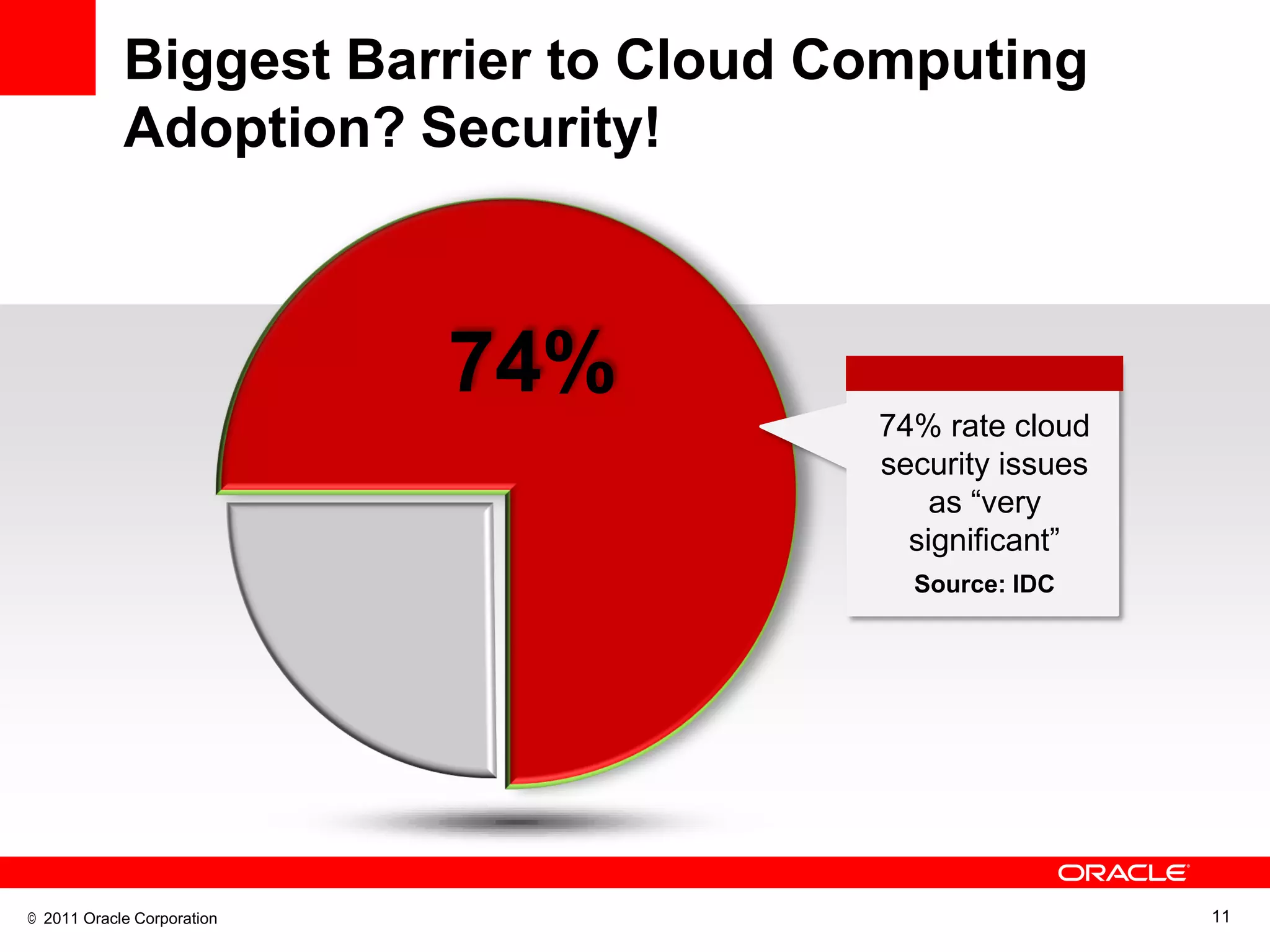
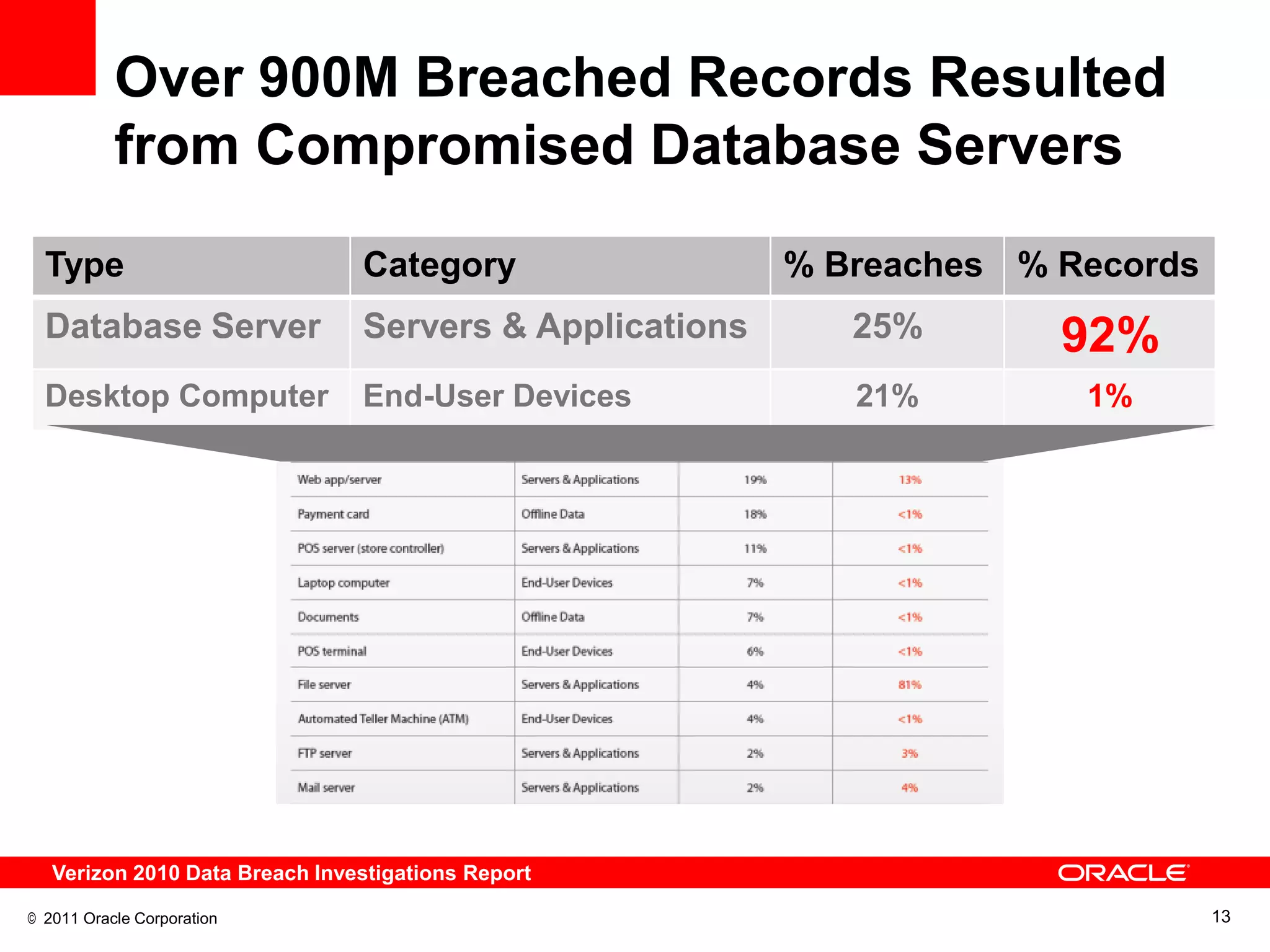
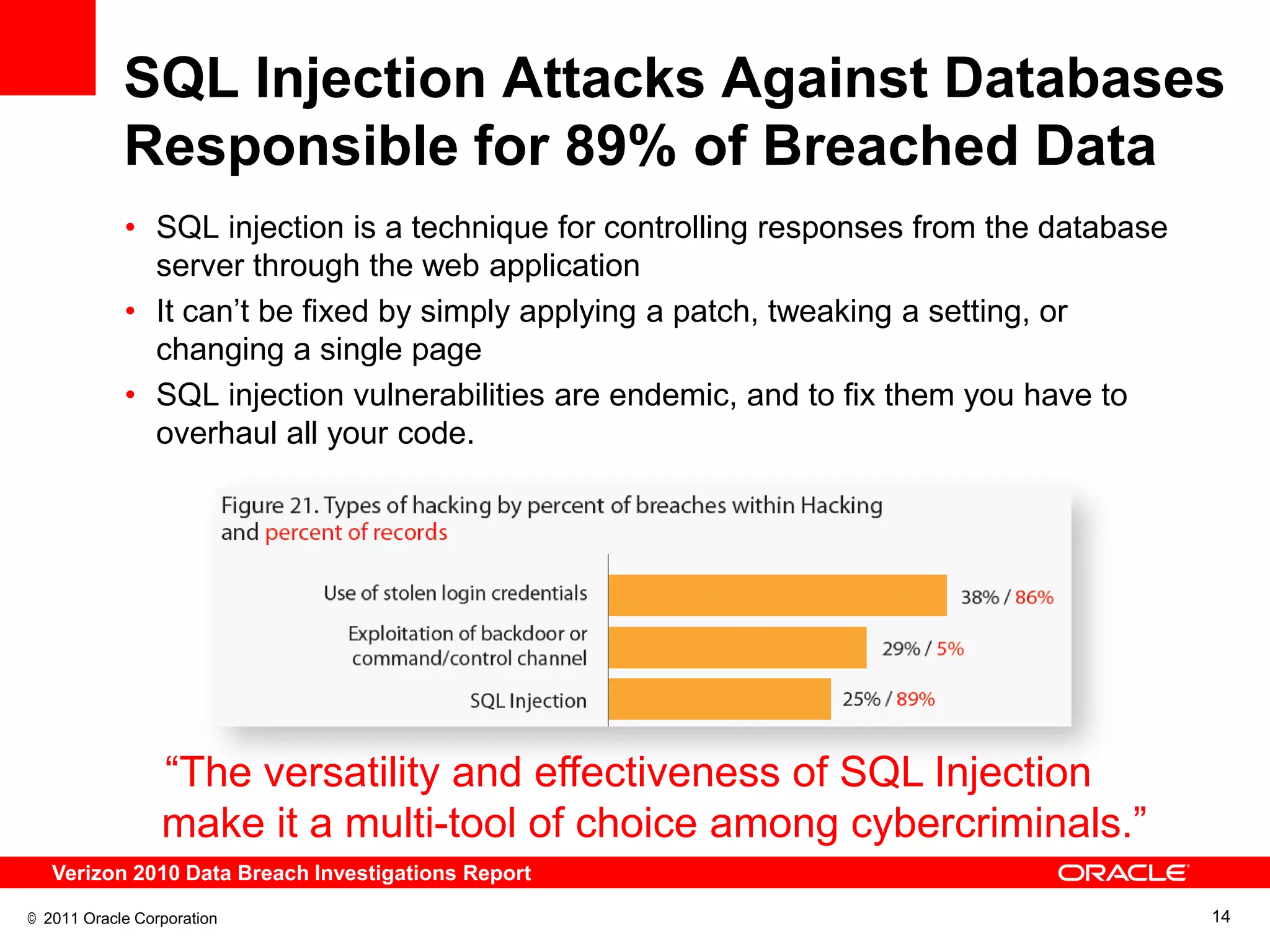
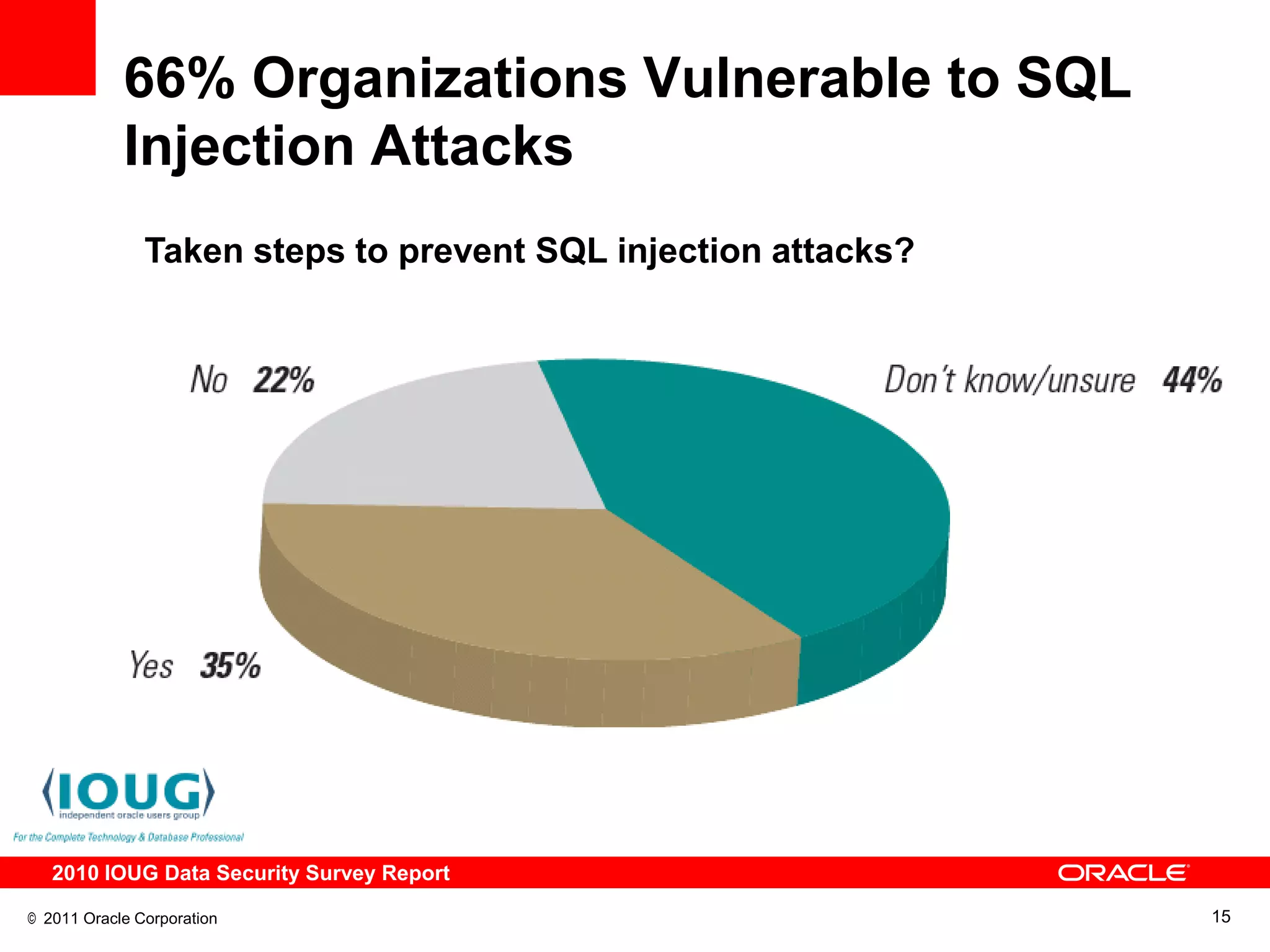
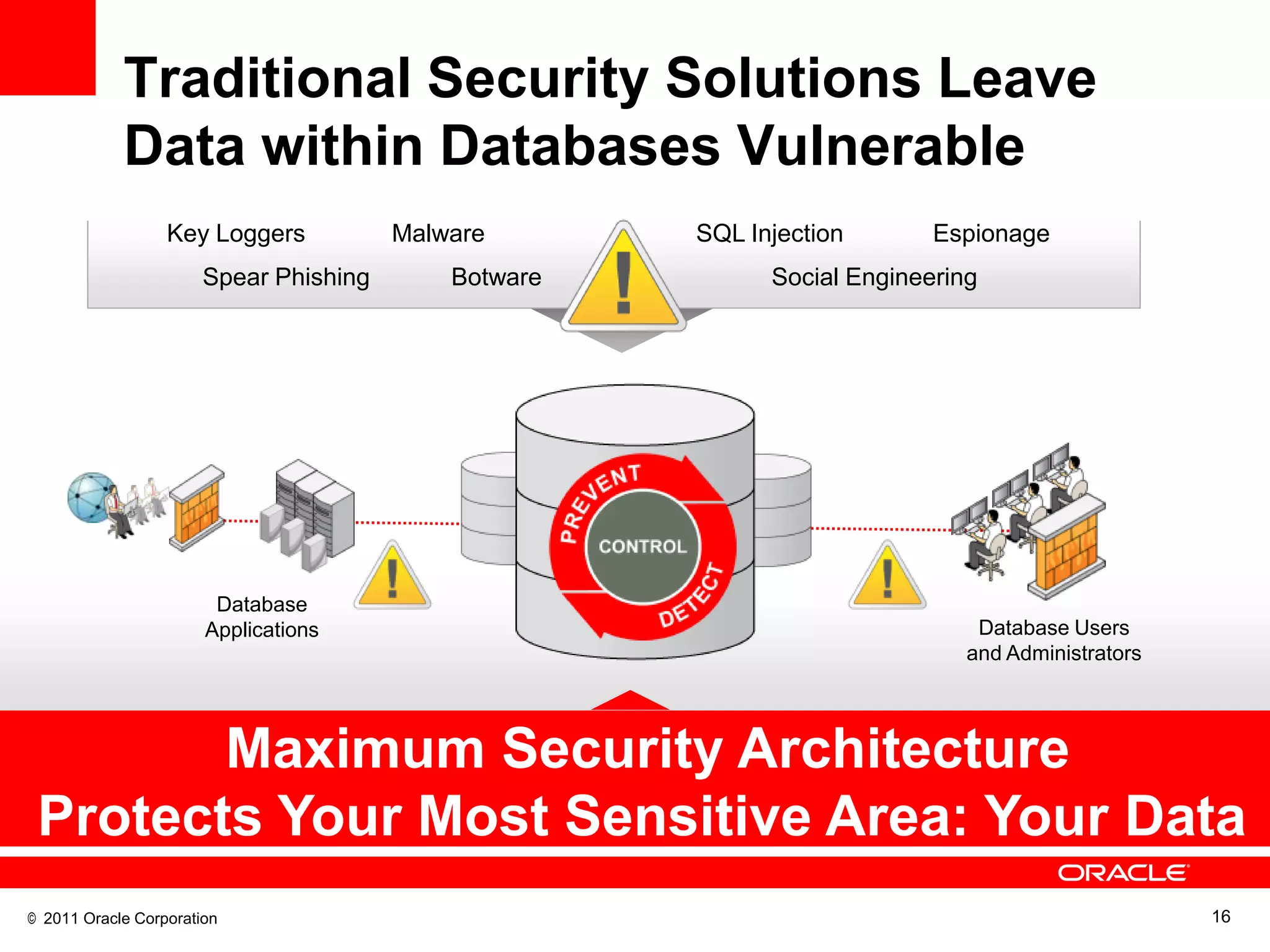
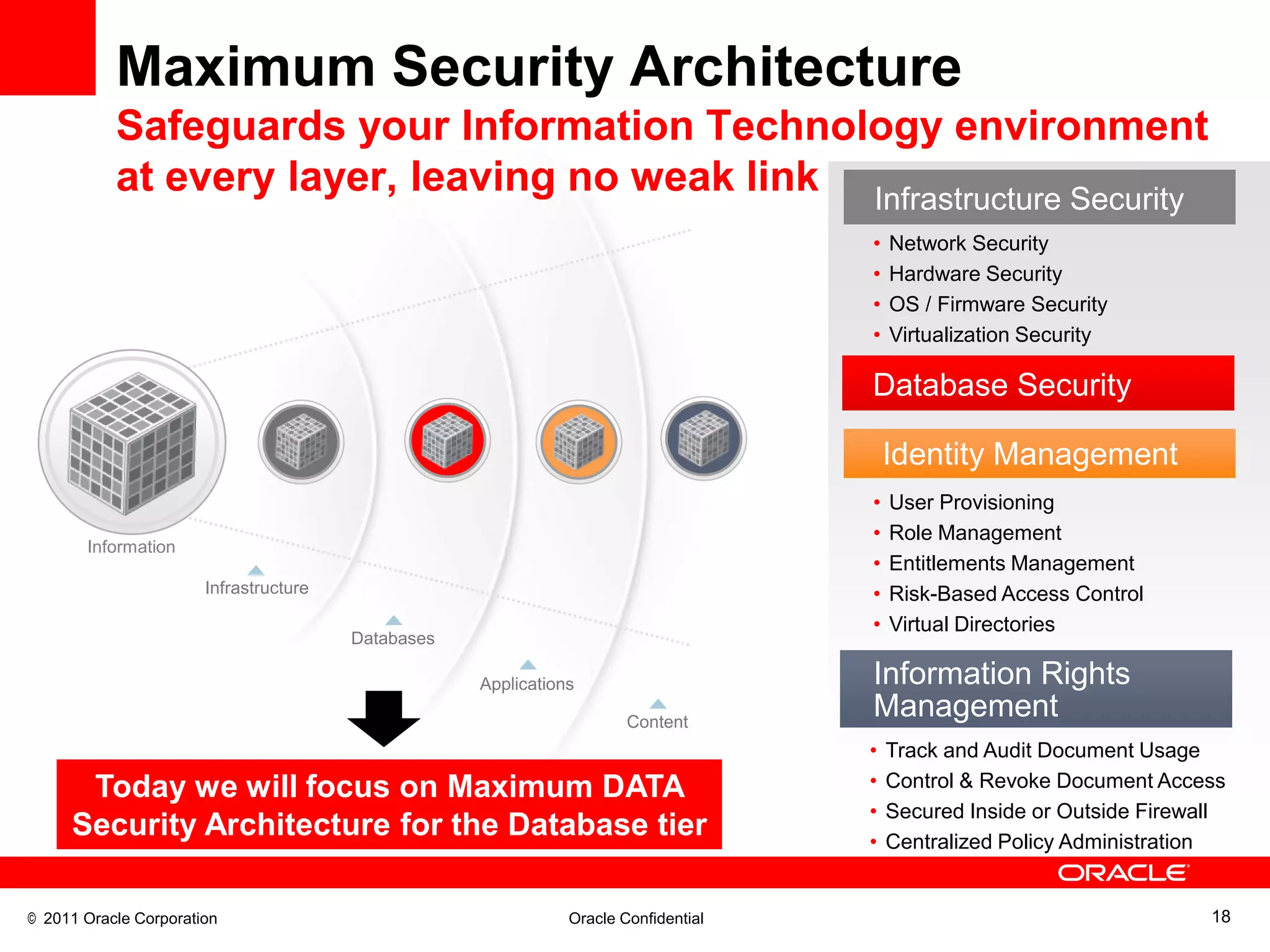
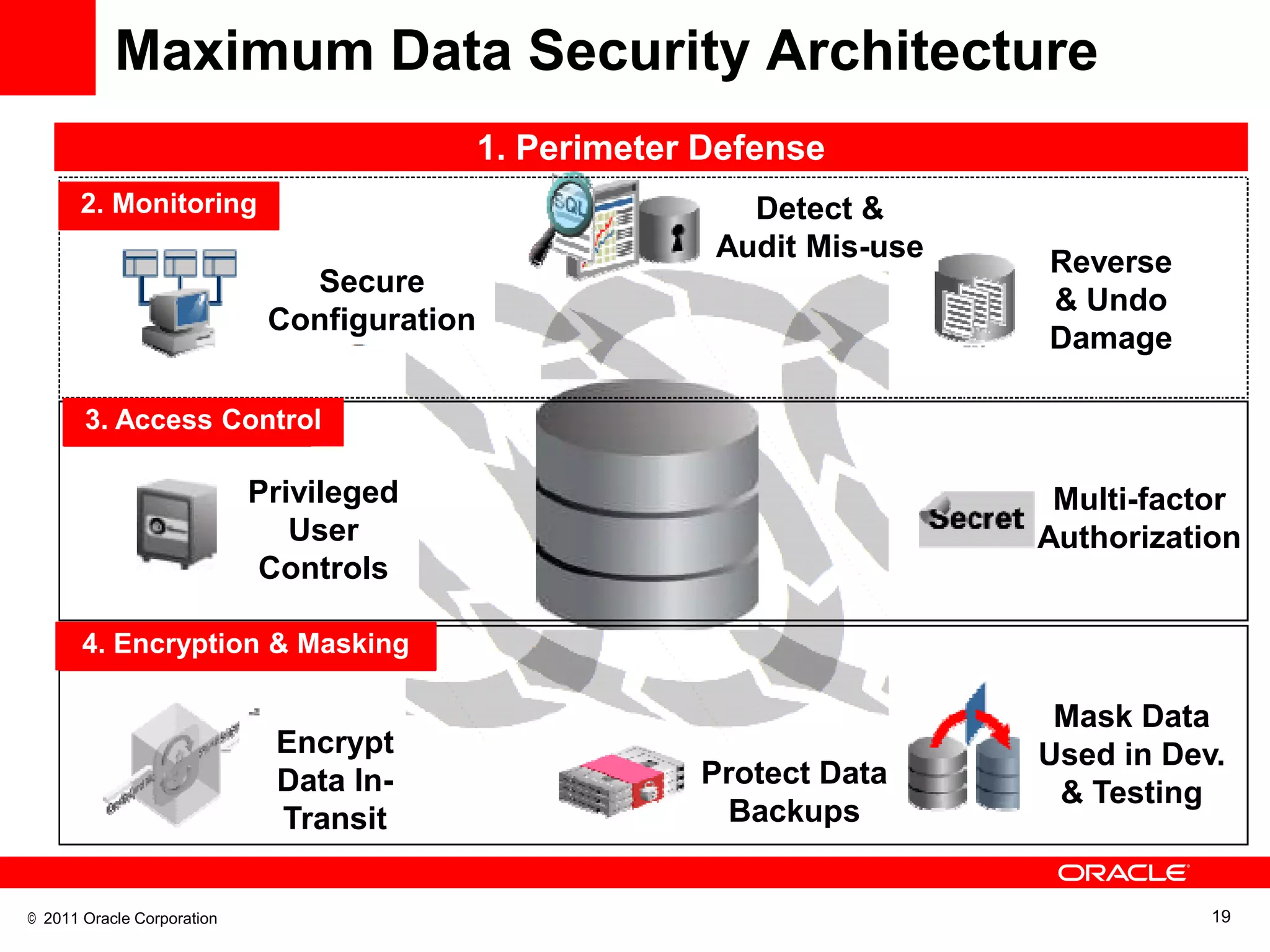
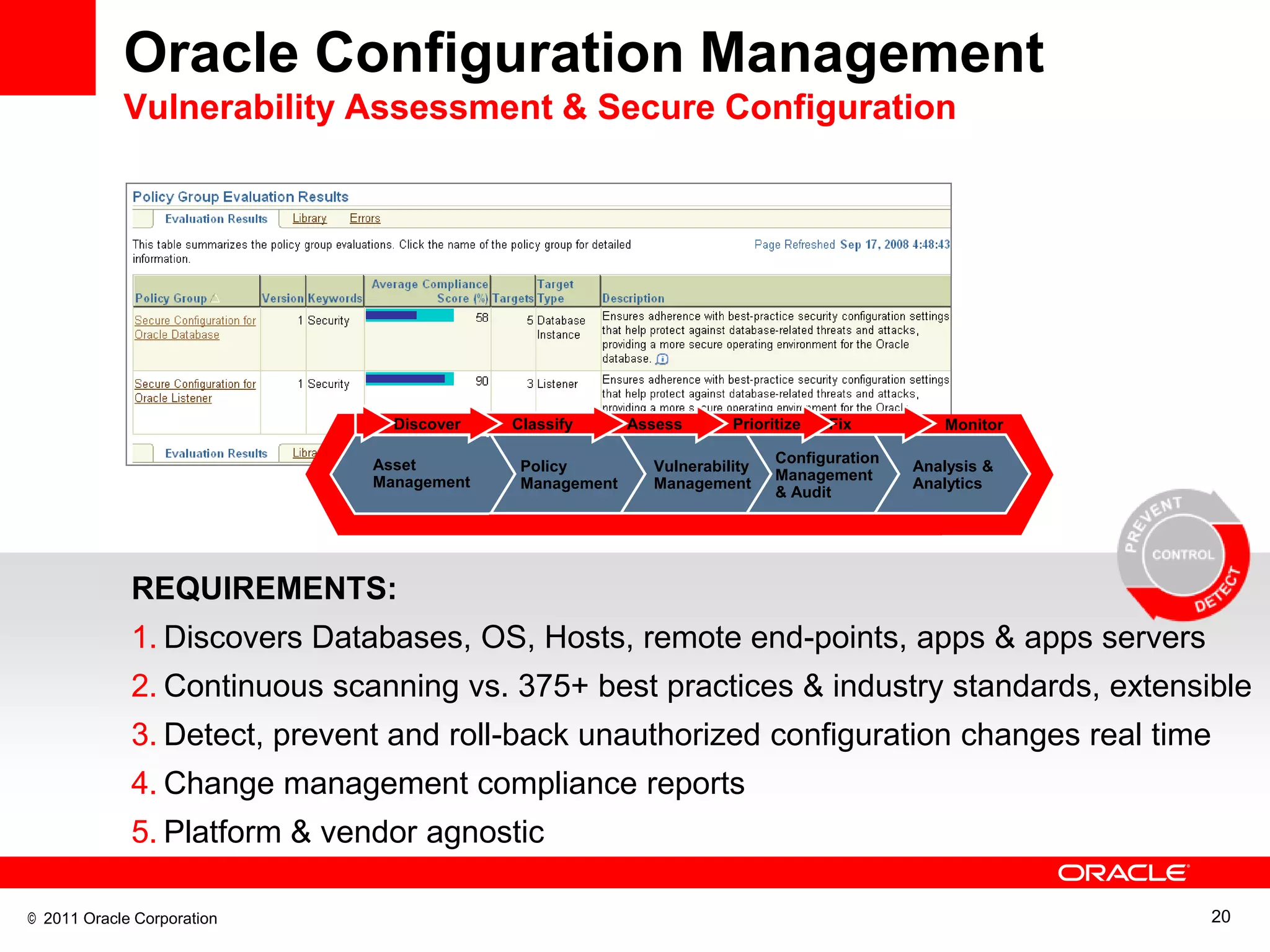
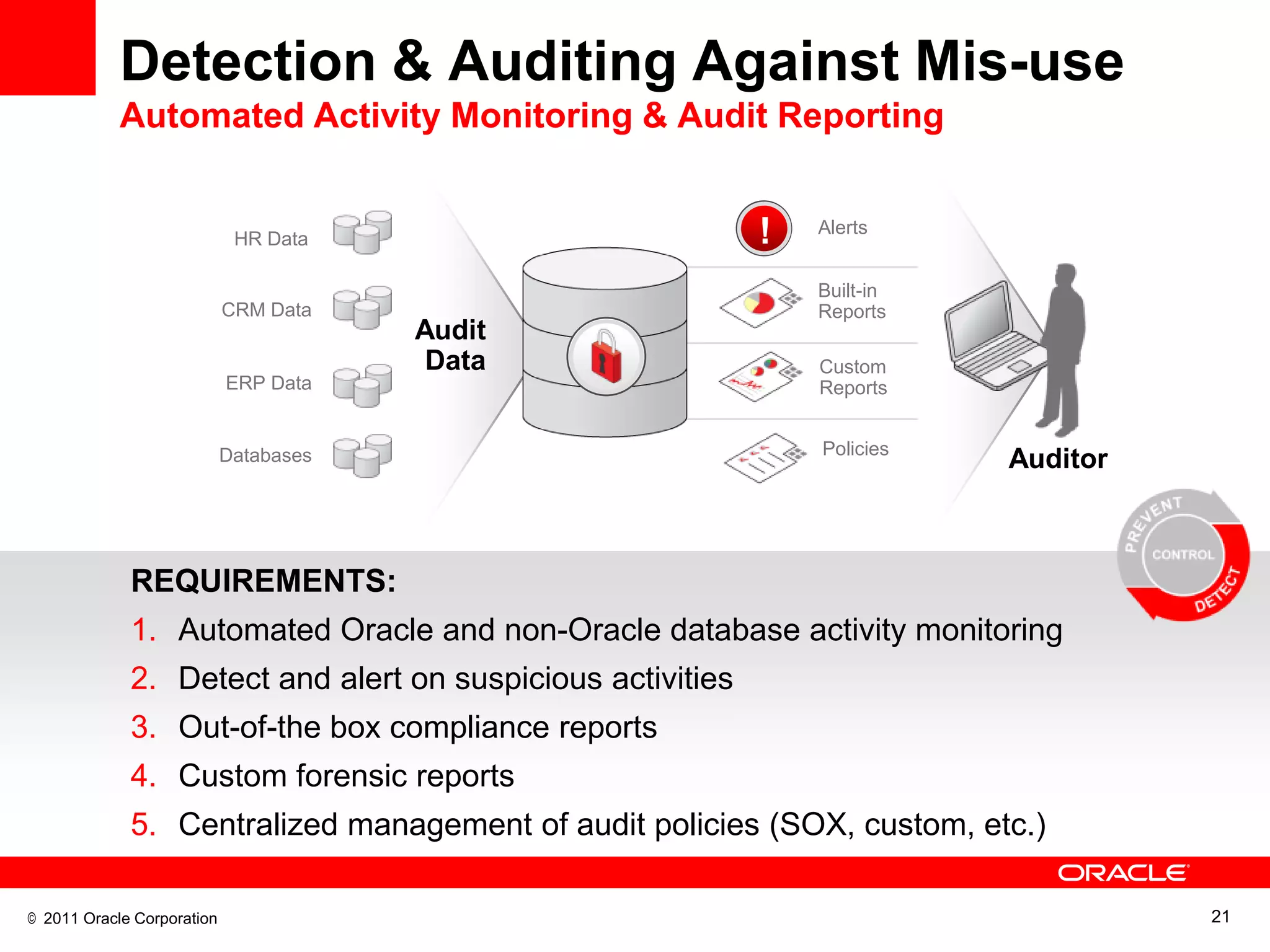
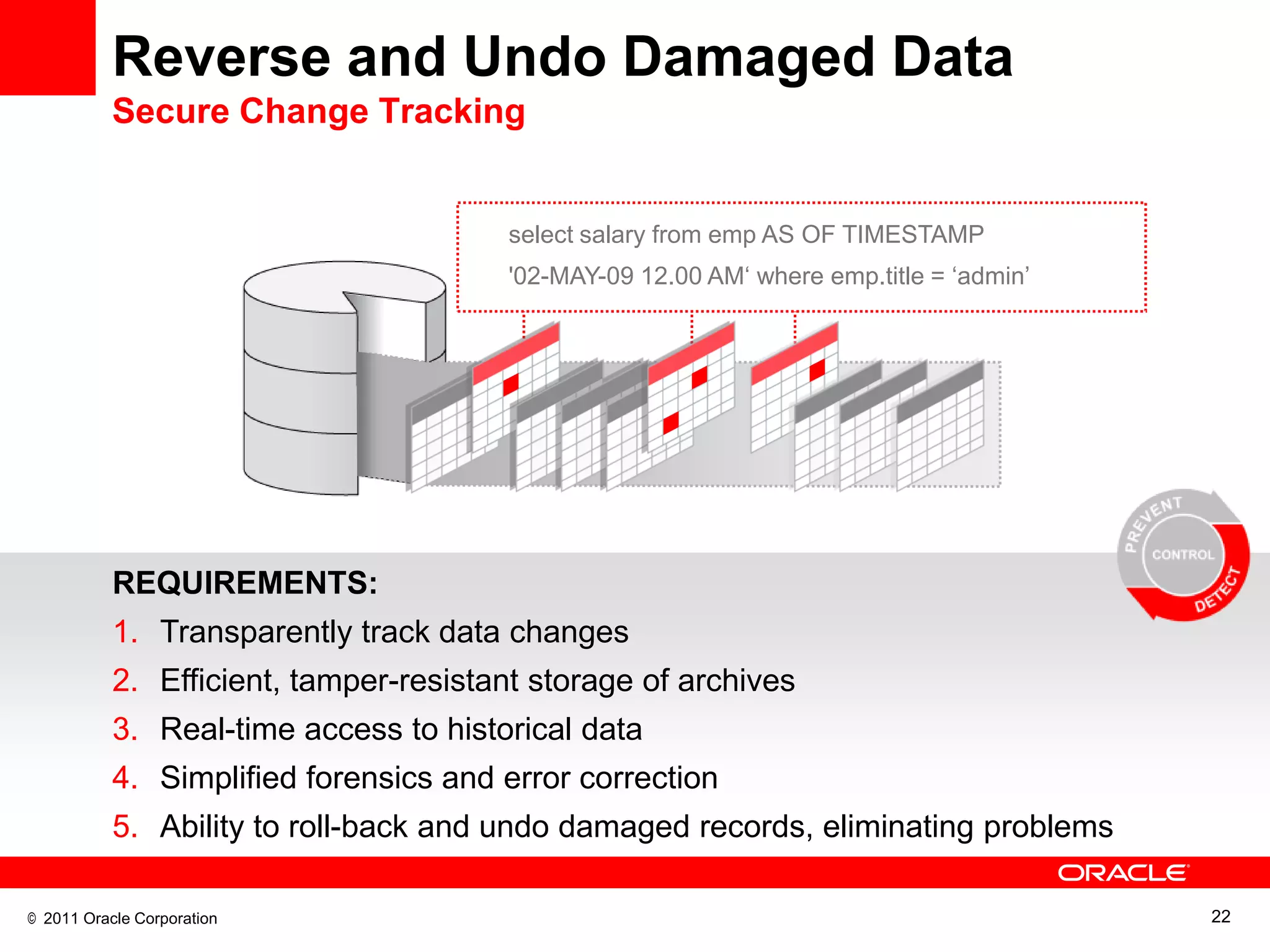
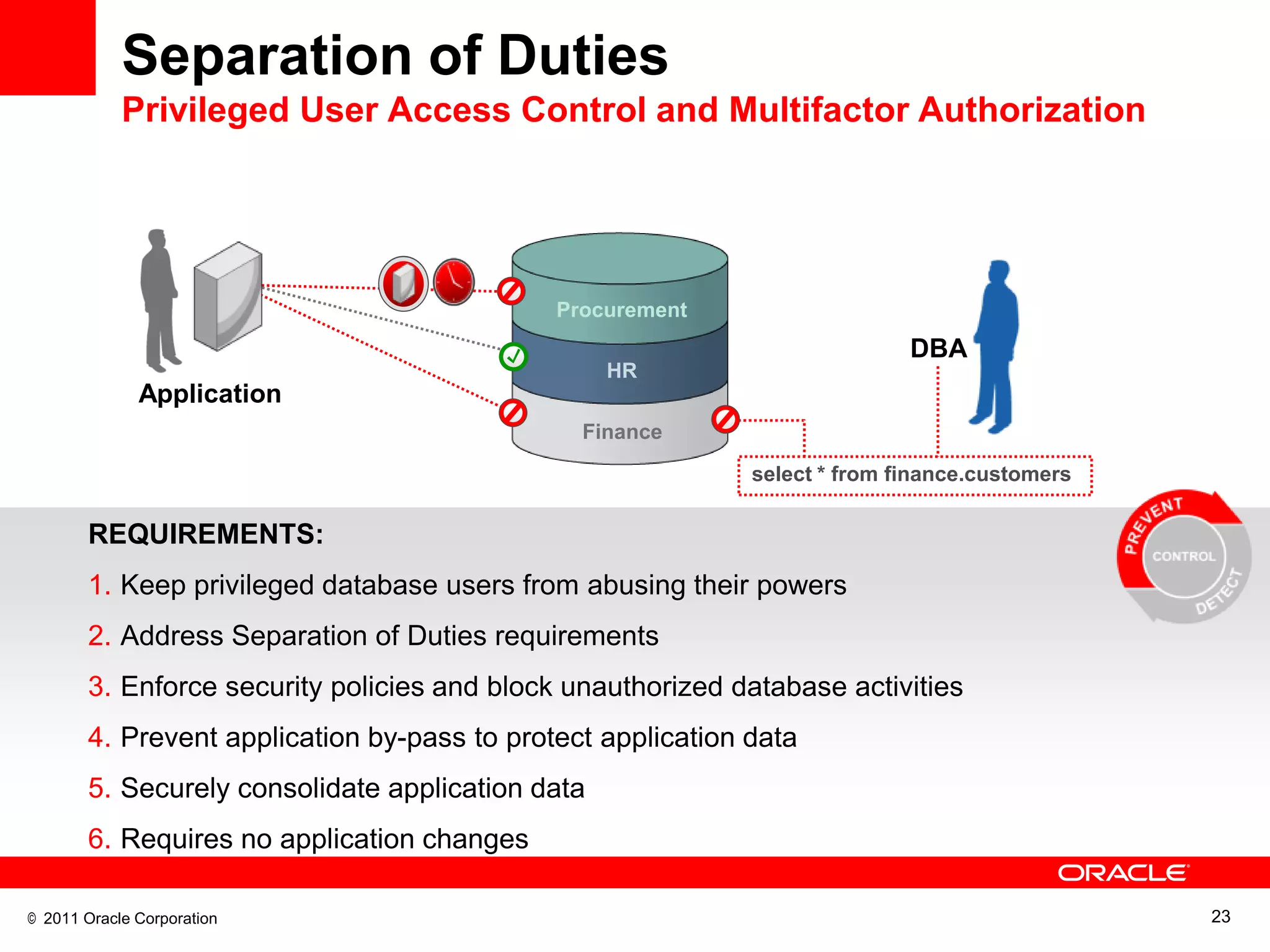
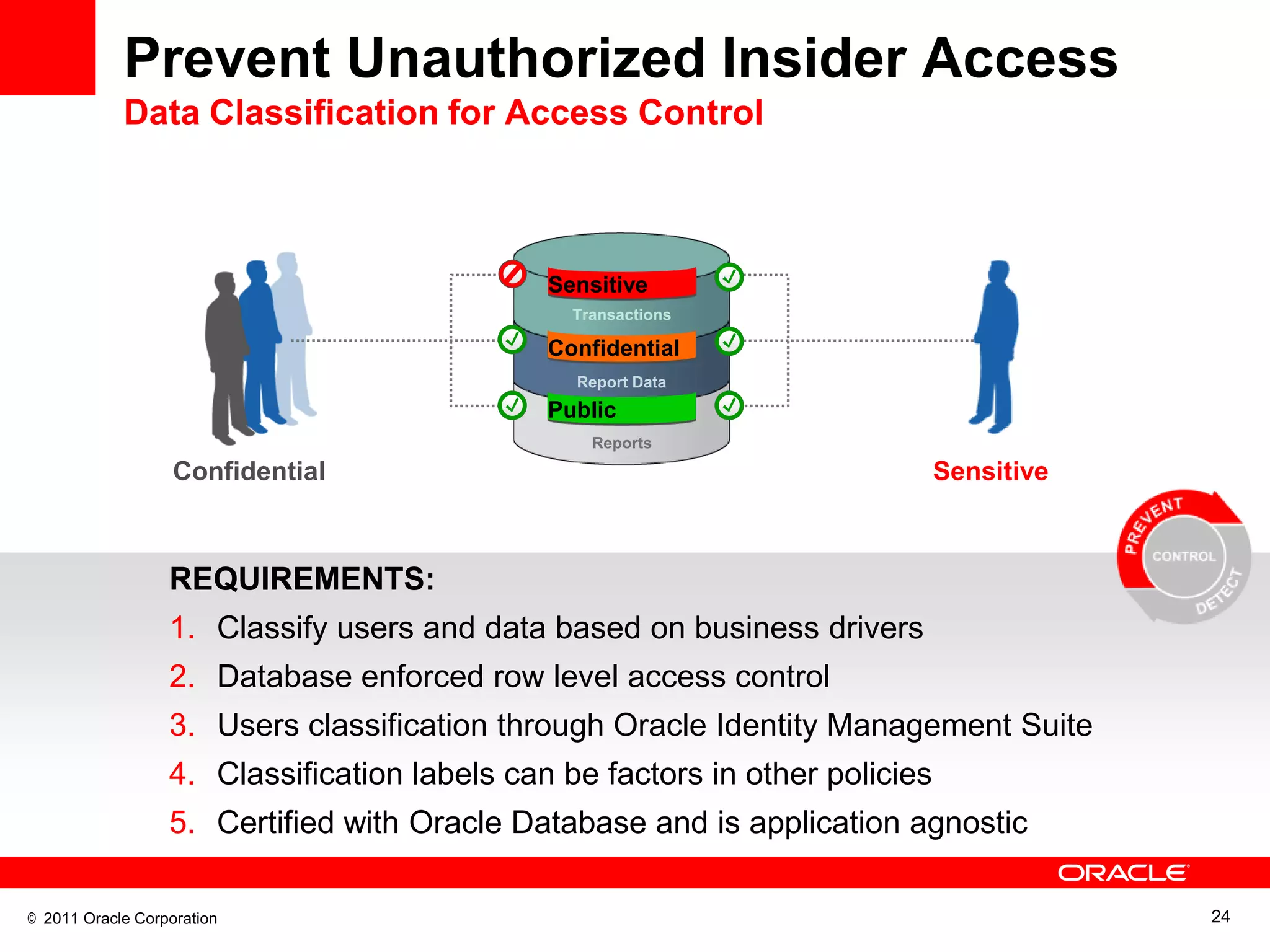
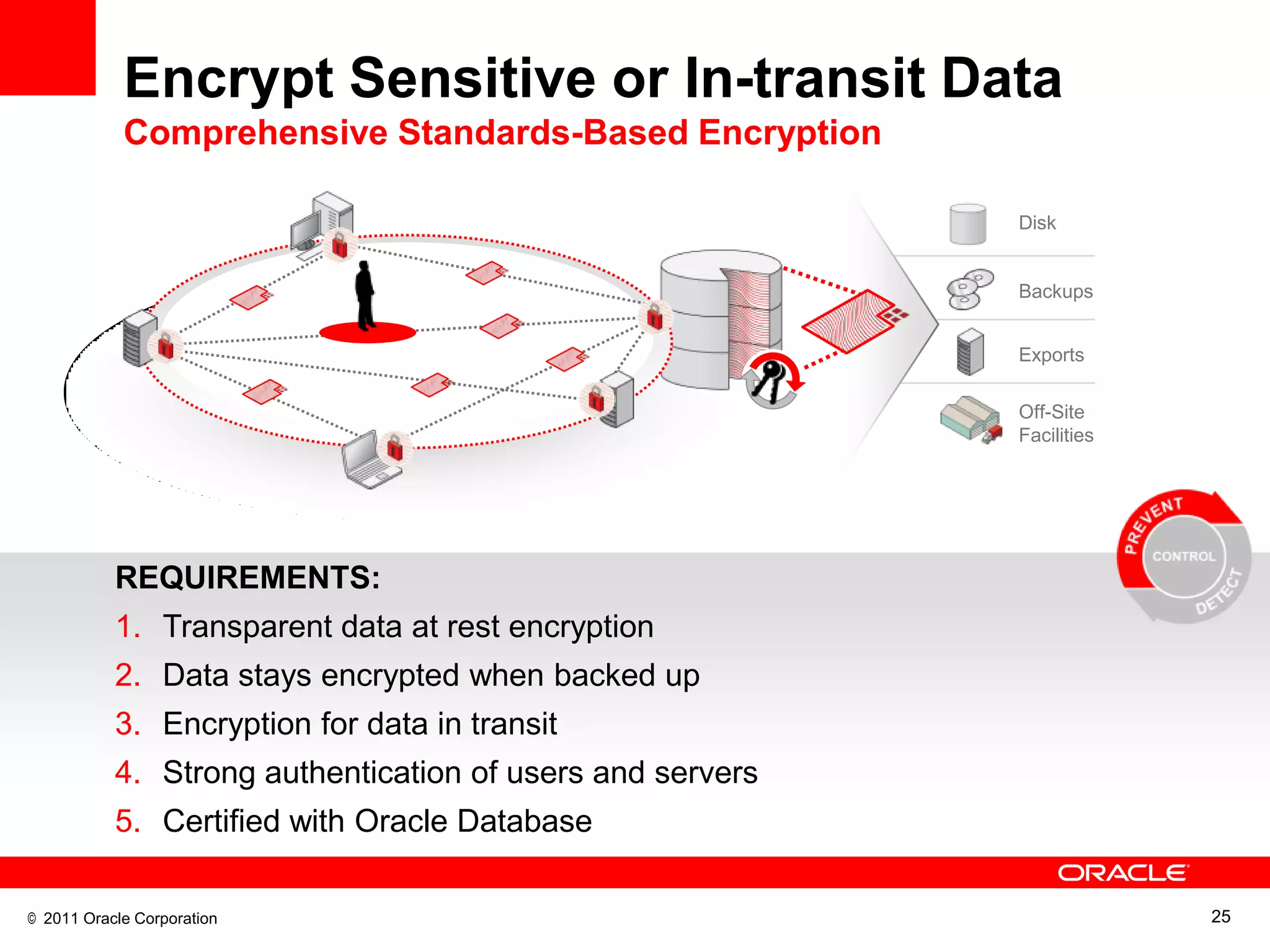
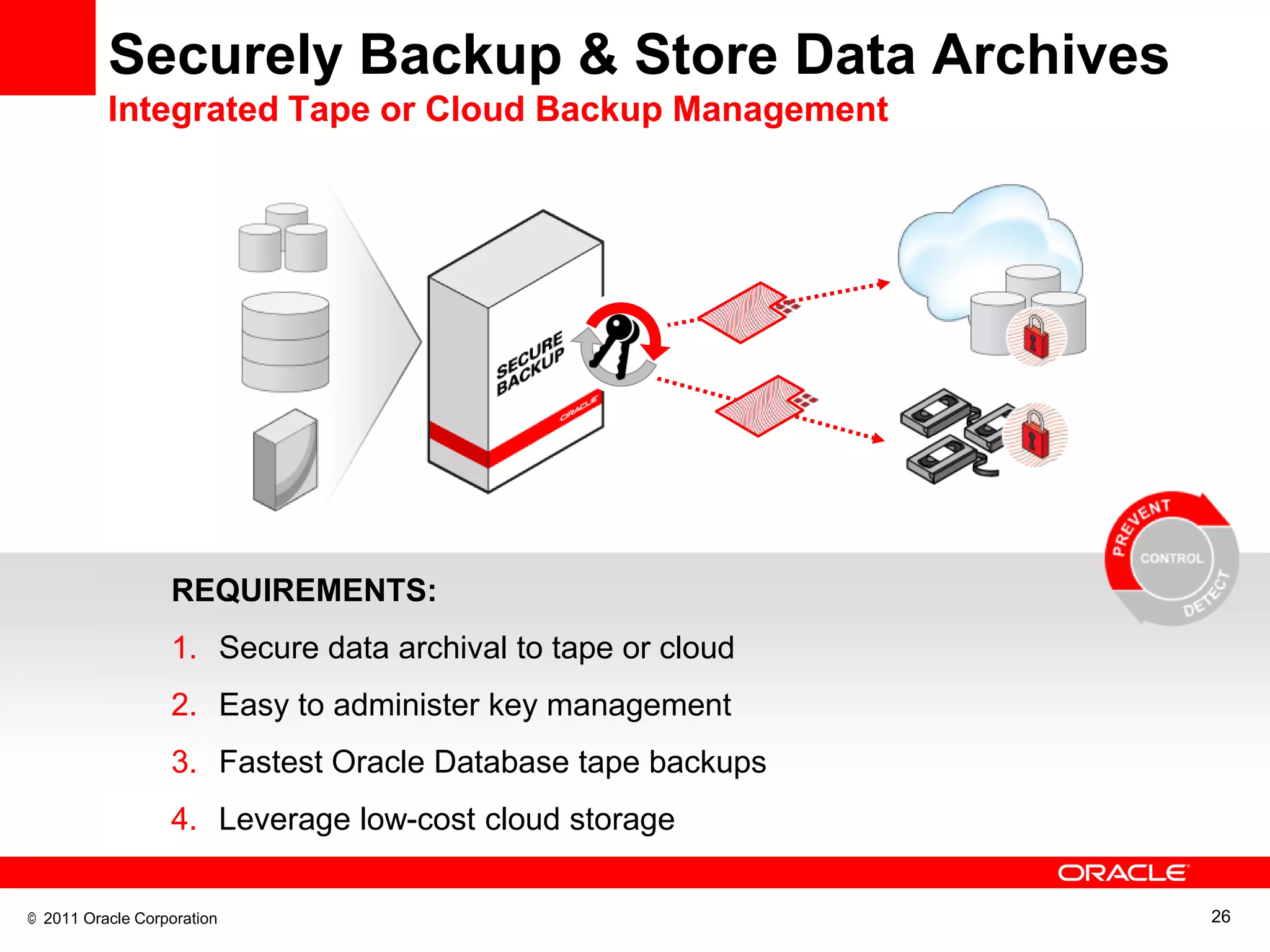
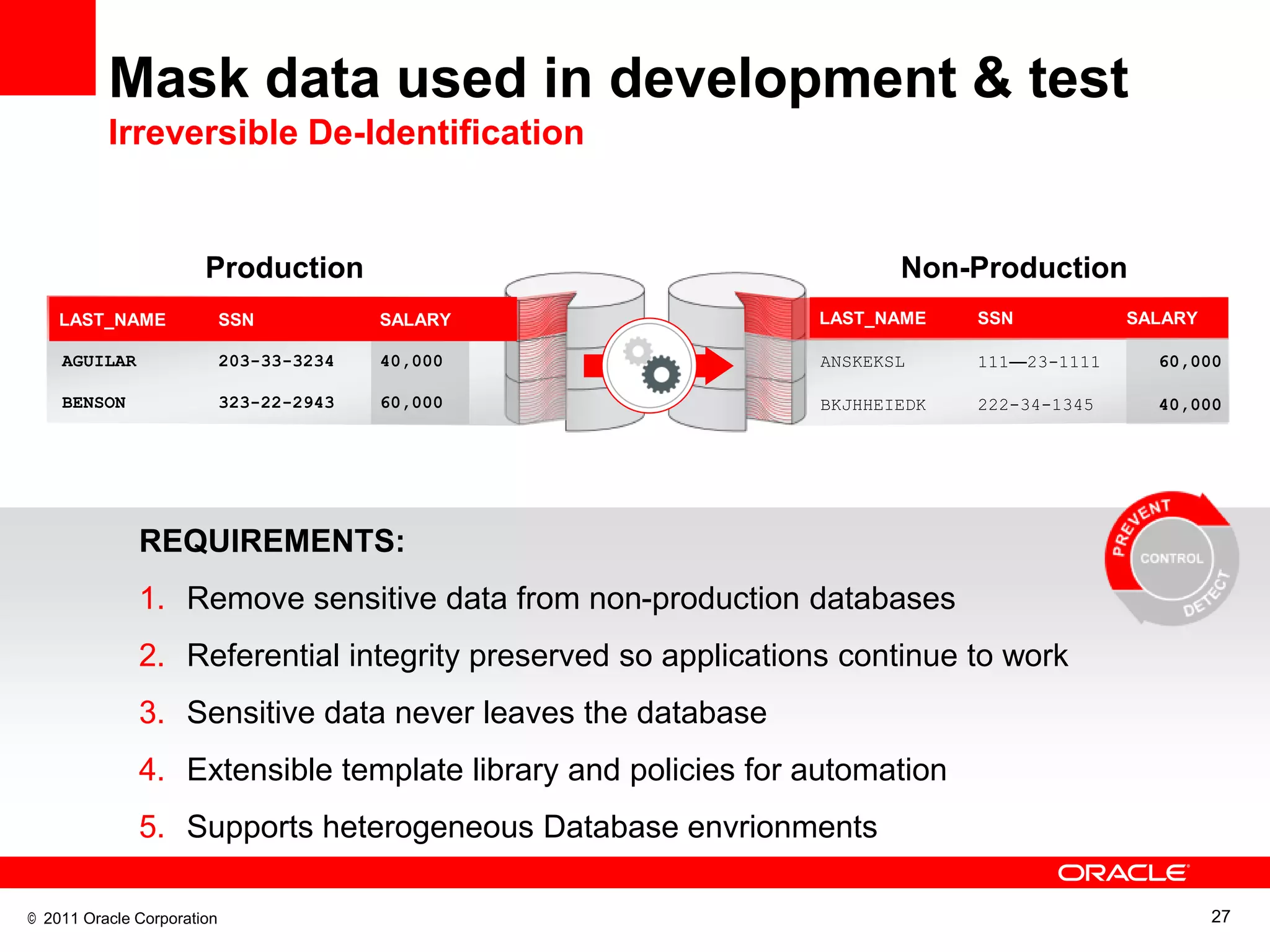
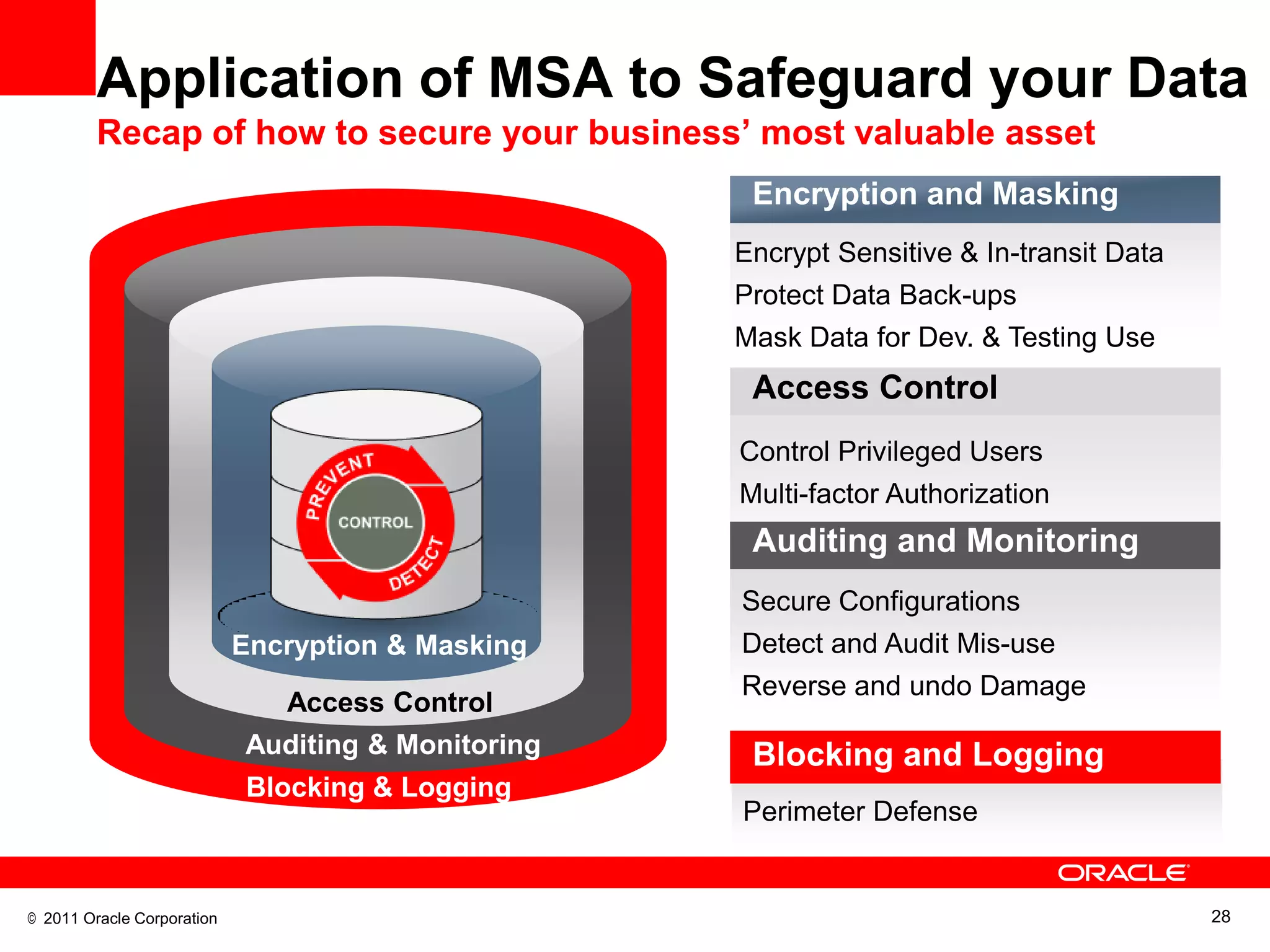
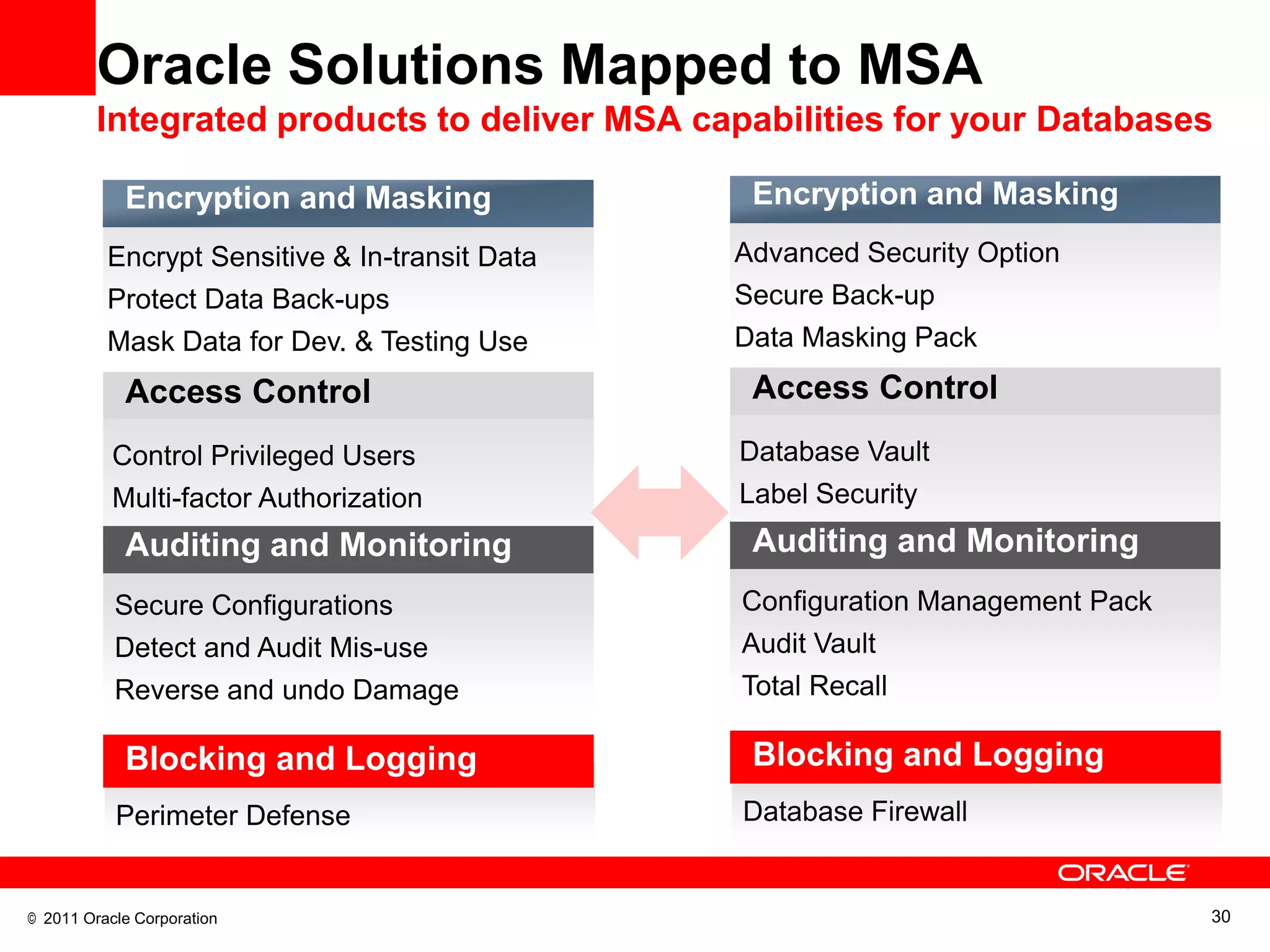
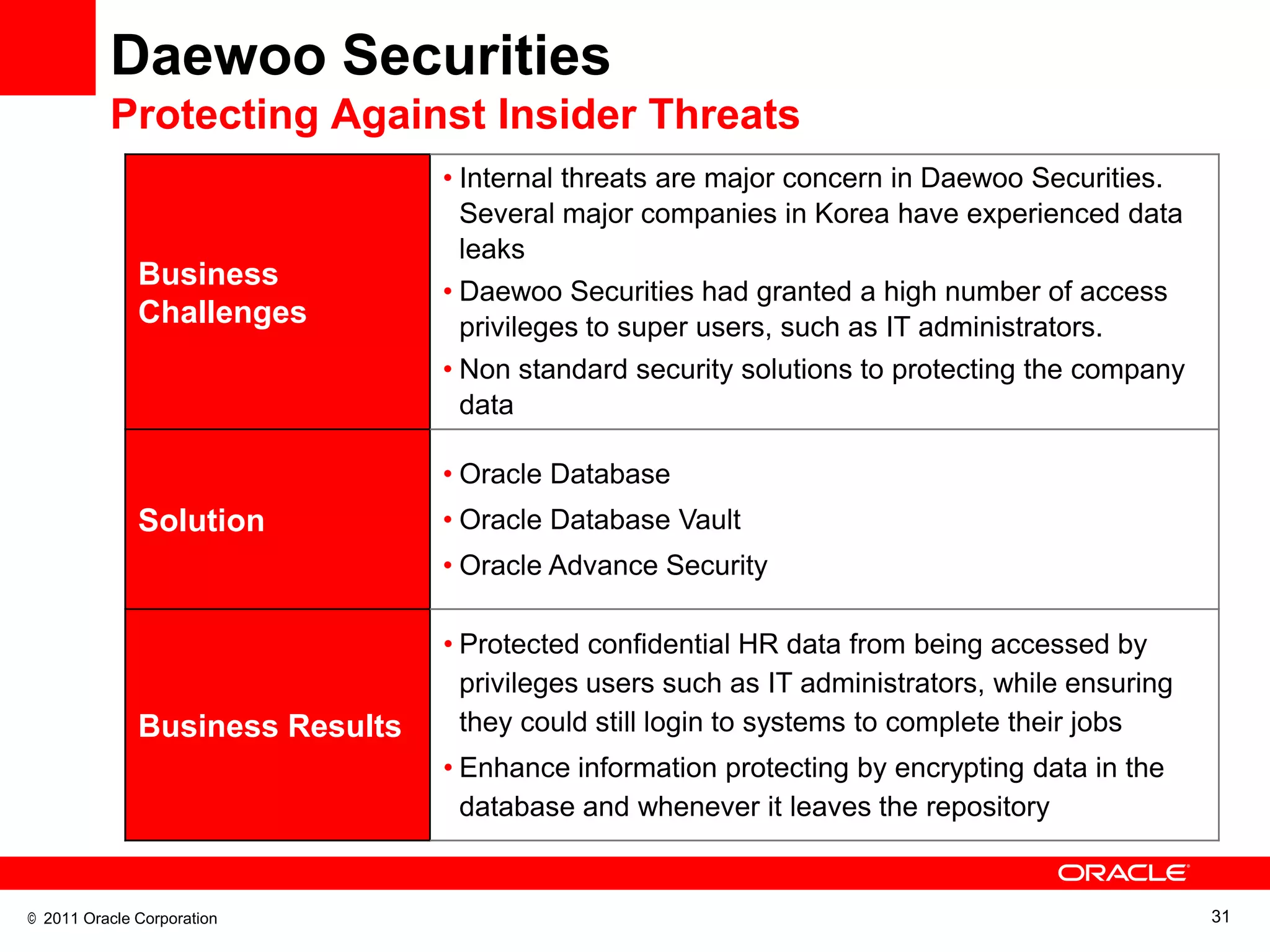
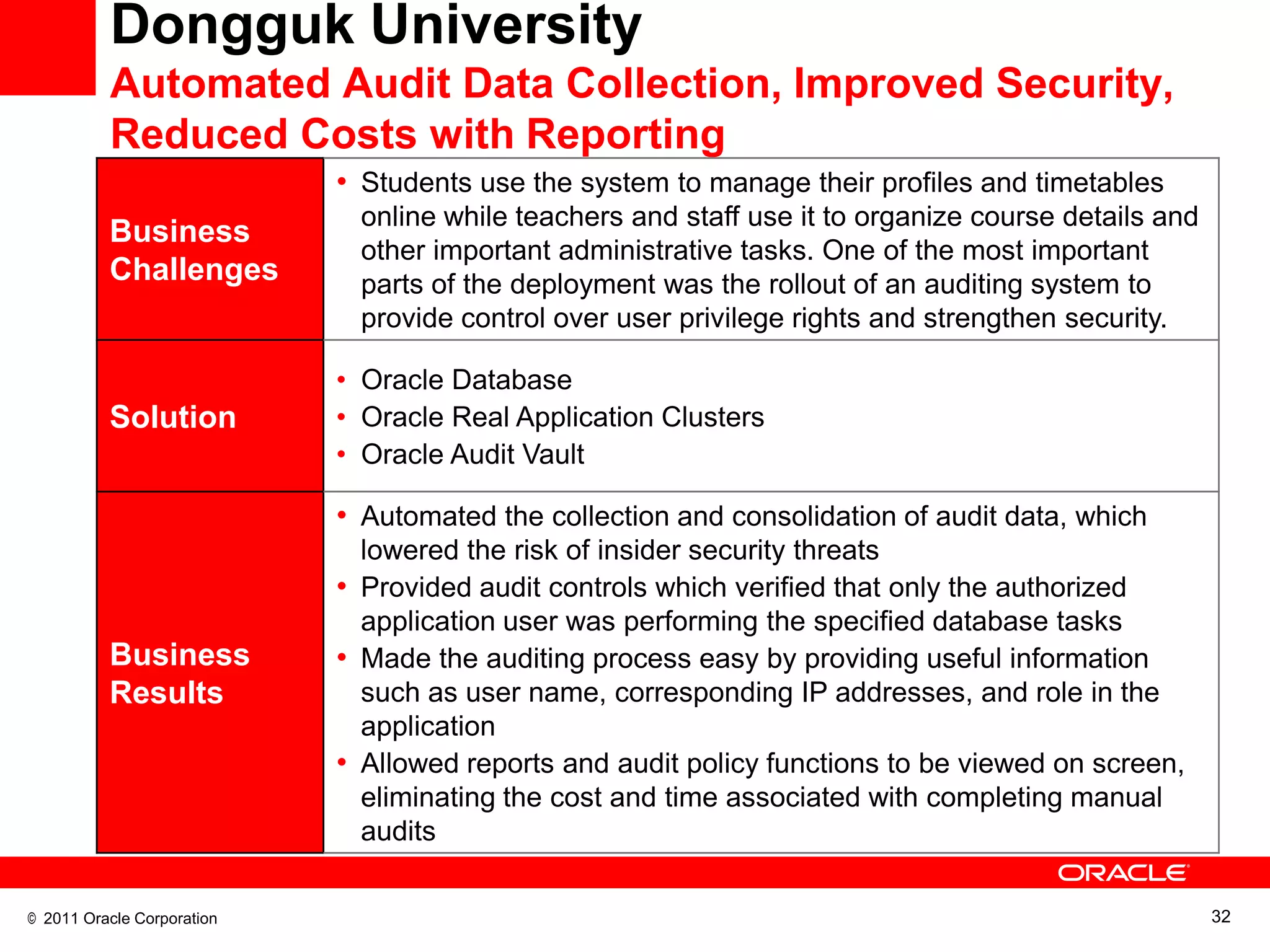
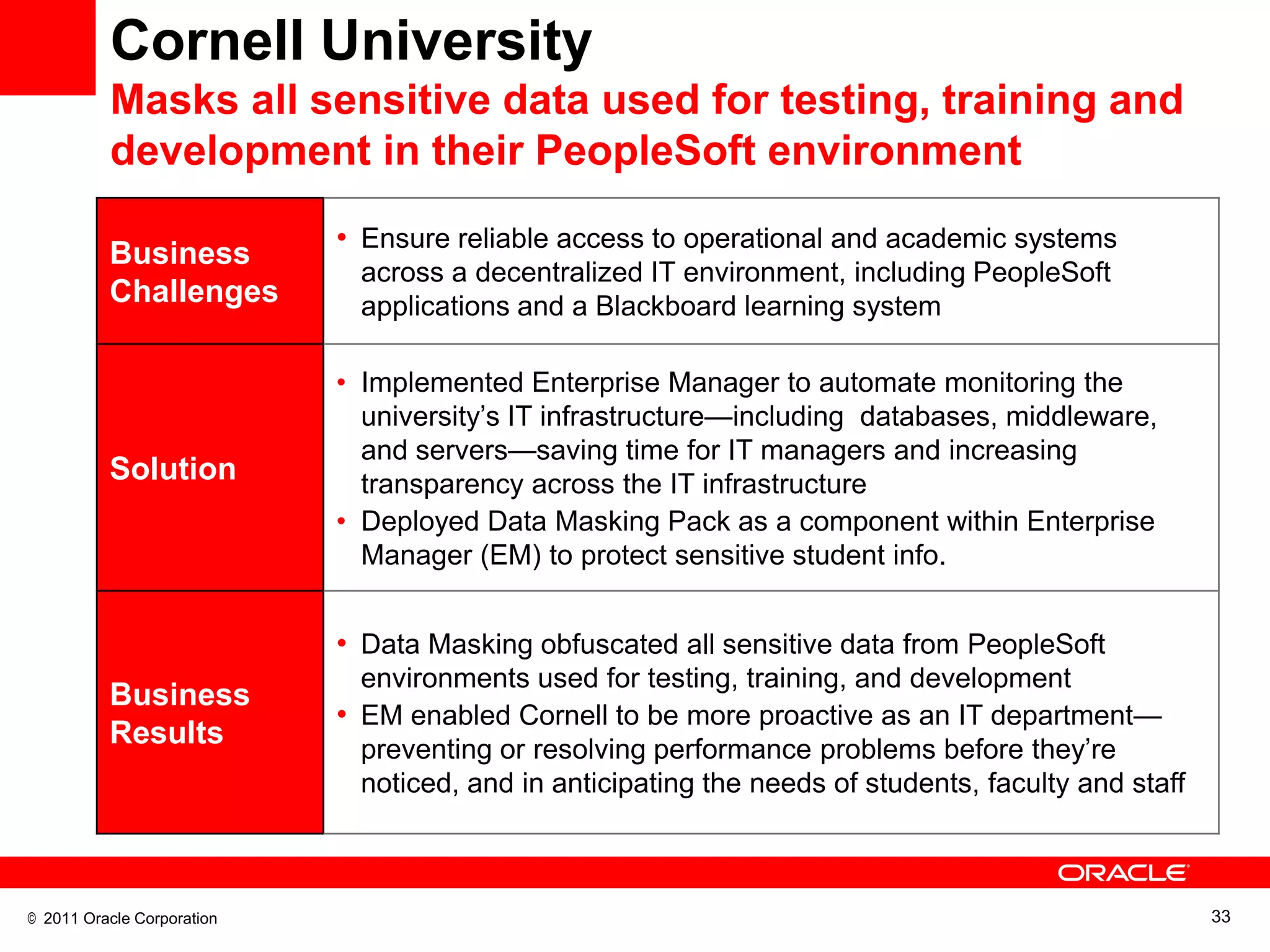
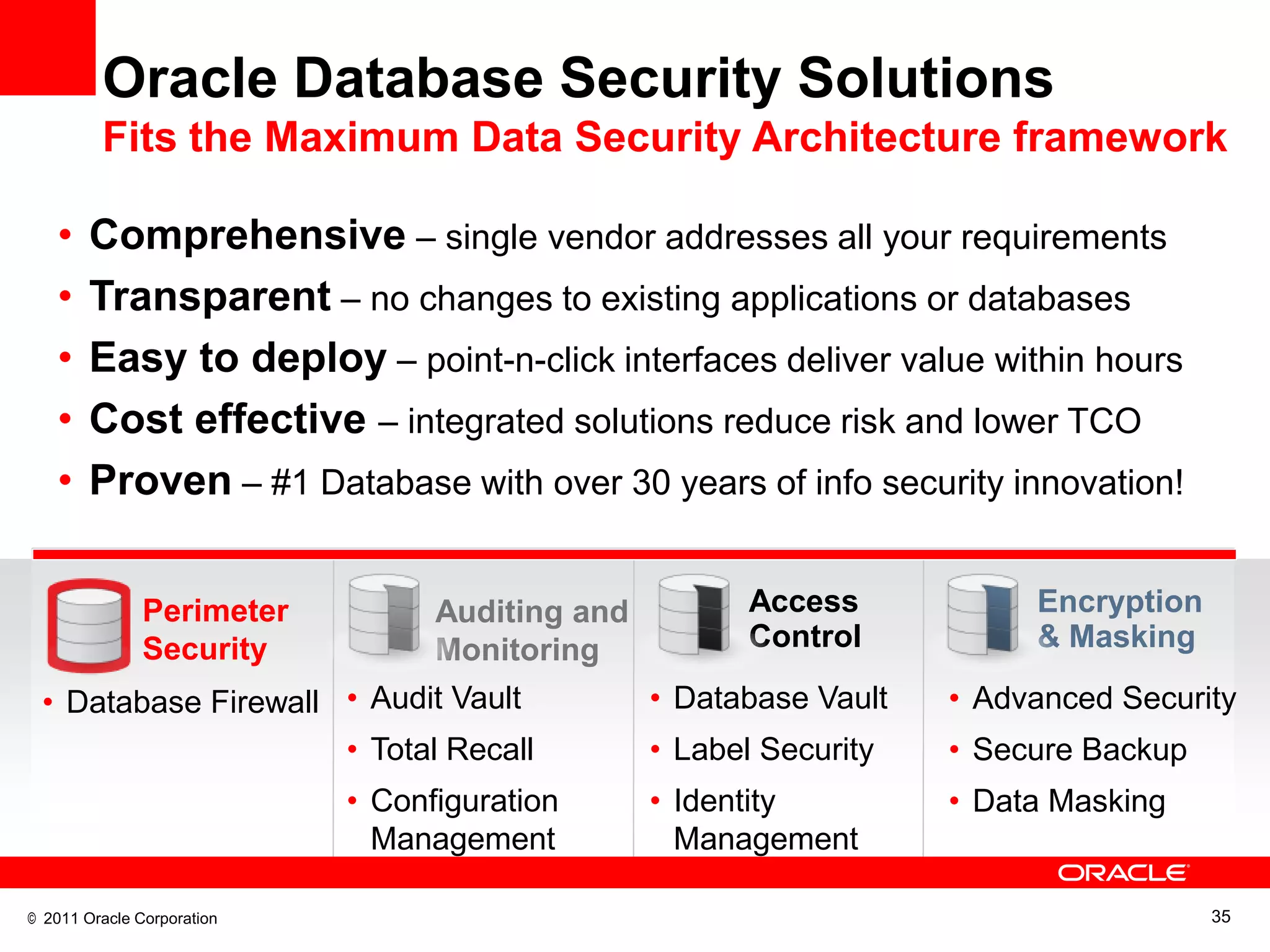
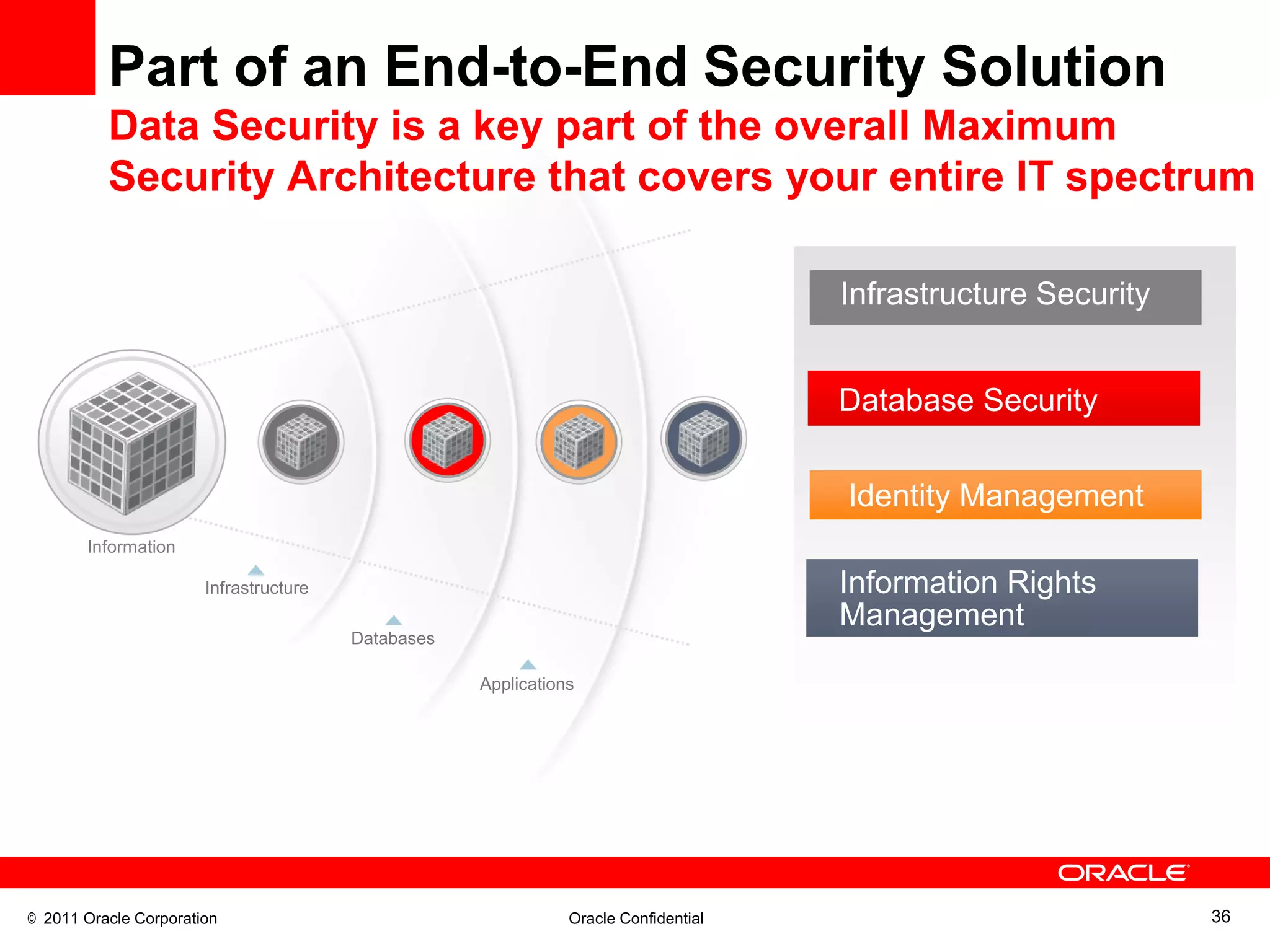
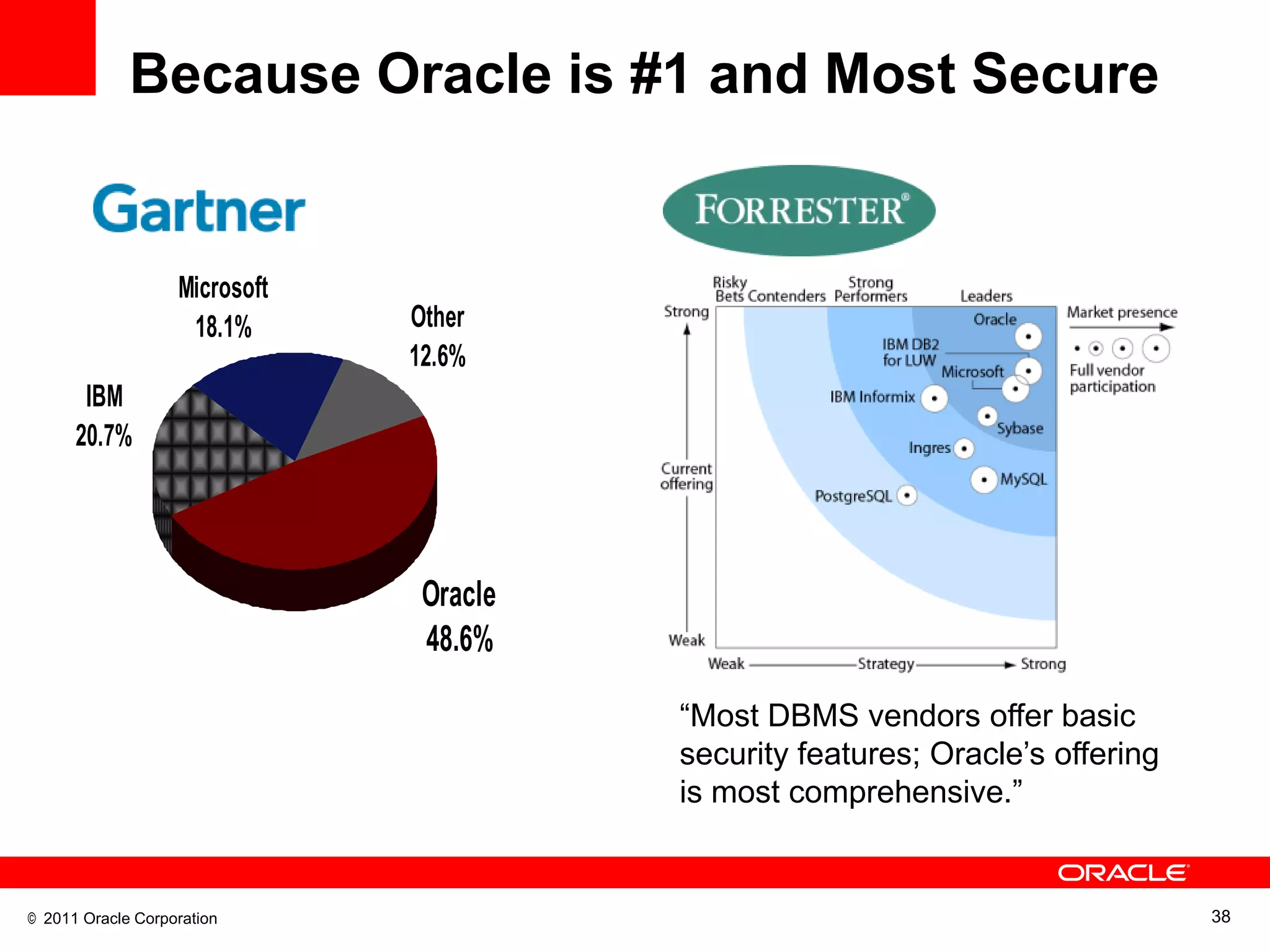
This document discusses building a maximum security architecture to protect sensitive data. It begins by outlining data security trends like more data and breaches than ever before. It then introduces the concept of a maximum security architecture that safeguards data at every layer, with a focus on database security. The architecture includes perimeter defense, monitoring, access control, encryption and masking, and blocking and logging. The document provides examples of how Oracle solutions map to this architecture to deliver capabilities like encryption, access control, auditing and more. It concludes by summarizing how applying a maximum security architecture can help secure an organization's most valuable asset, its data.