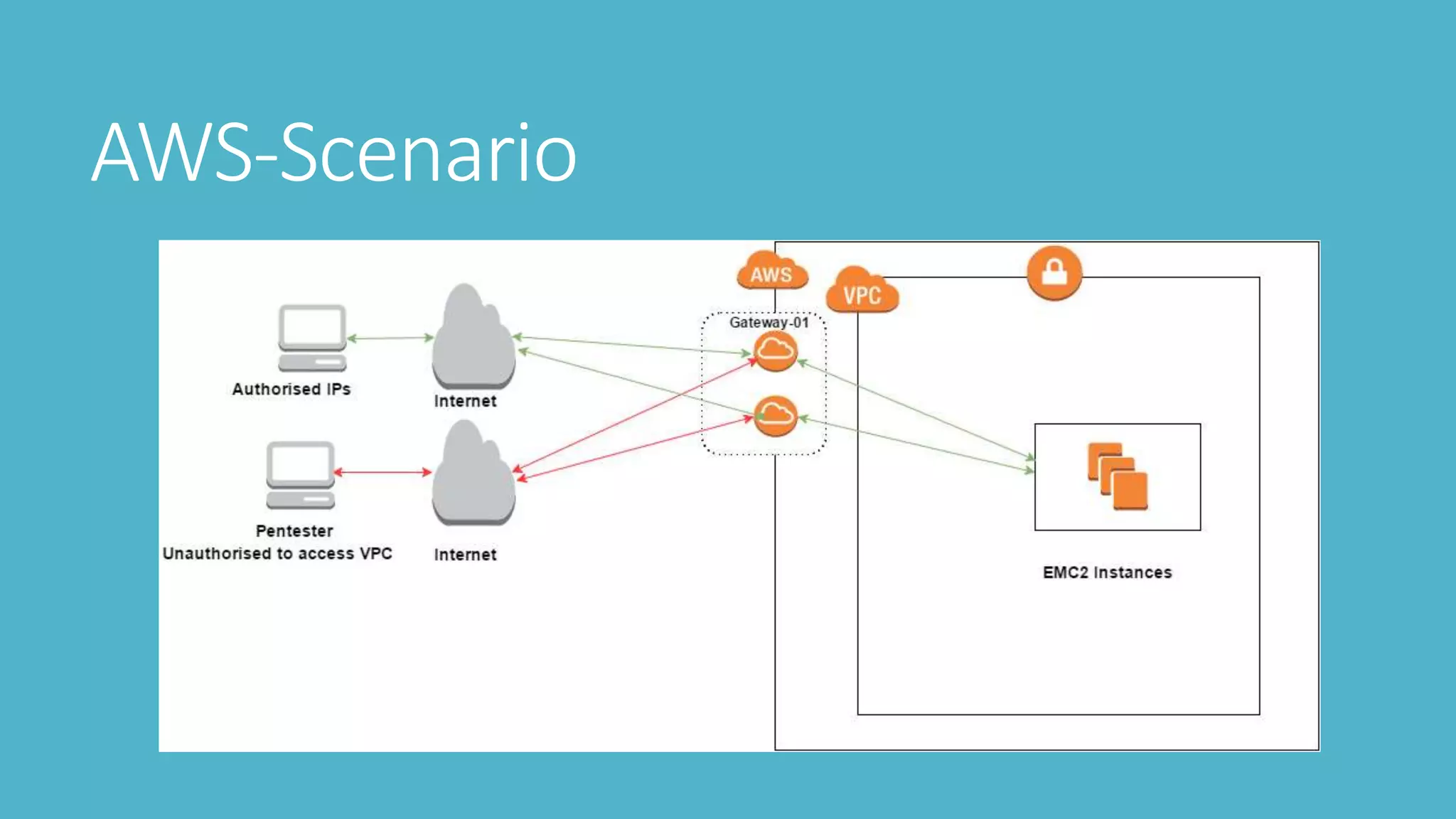
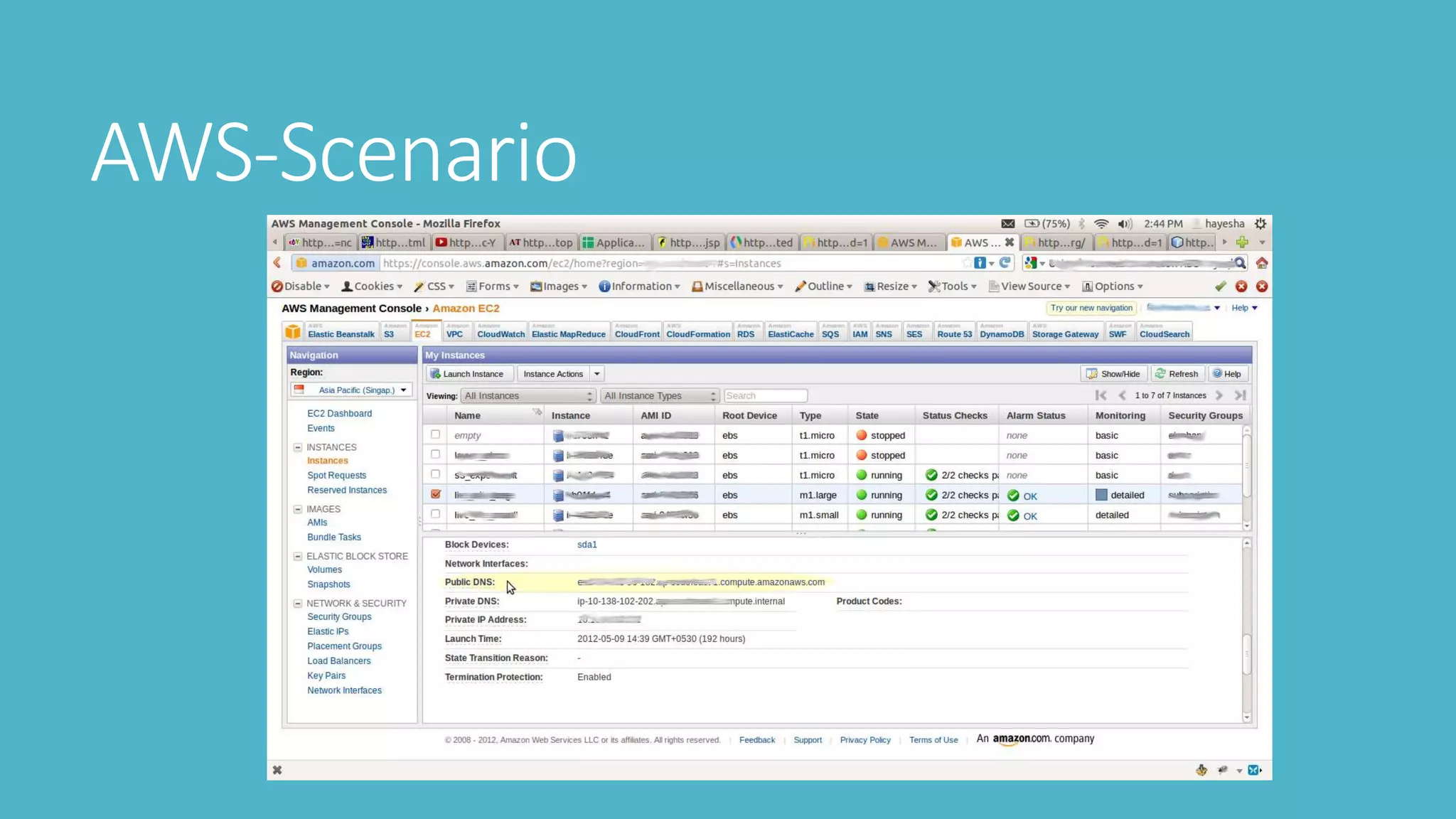
This document outlines steps for penetration testing an AWS environment, including:
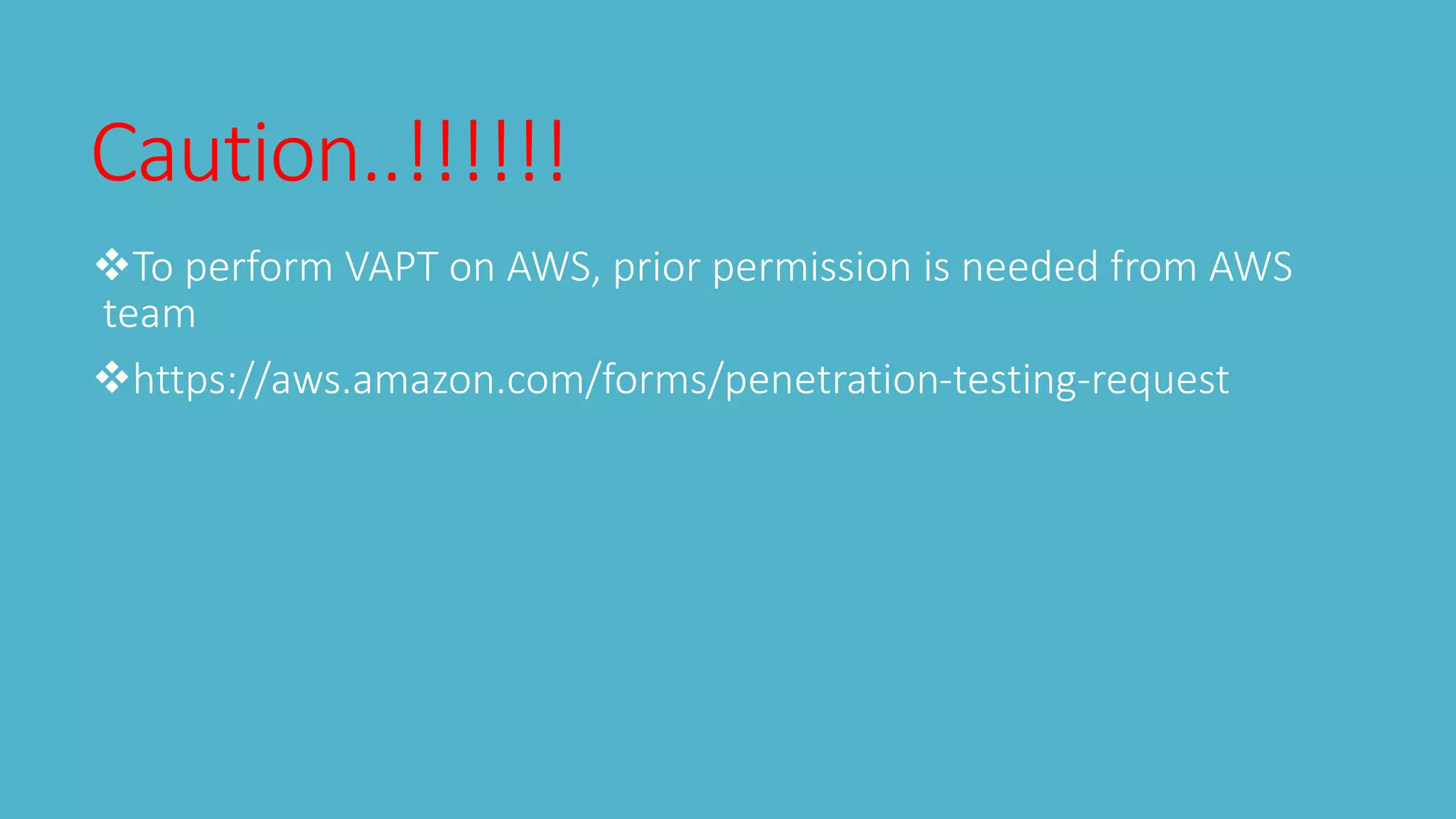
1. Requesting permission from AWS for testing
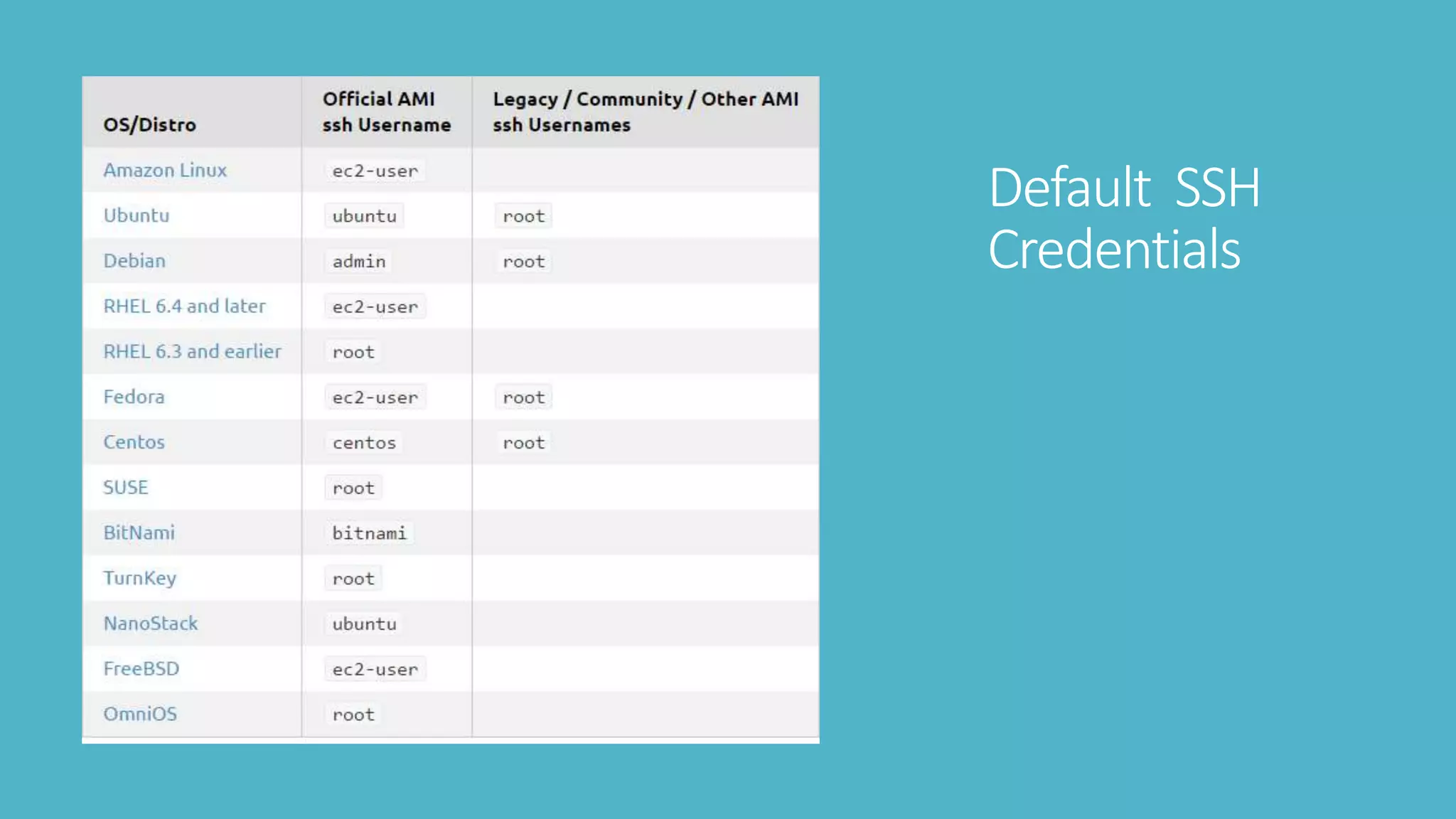
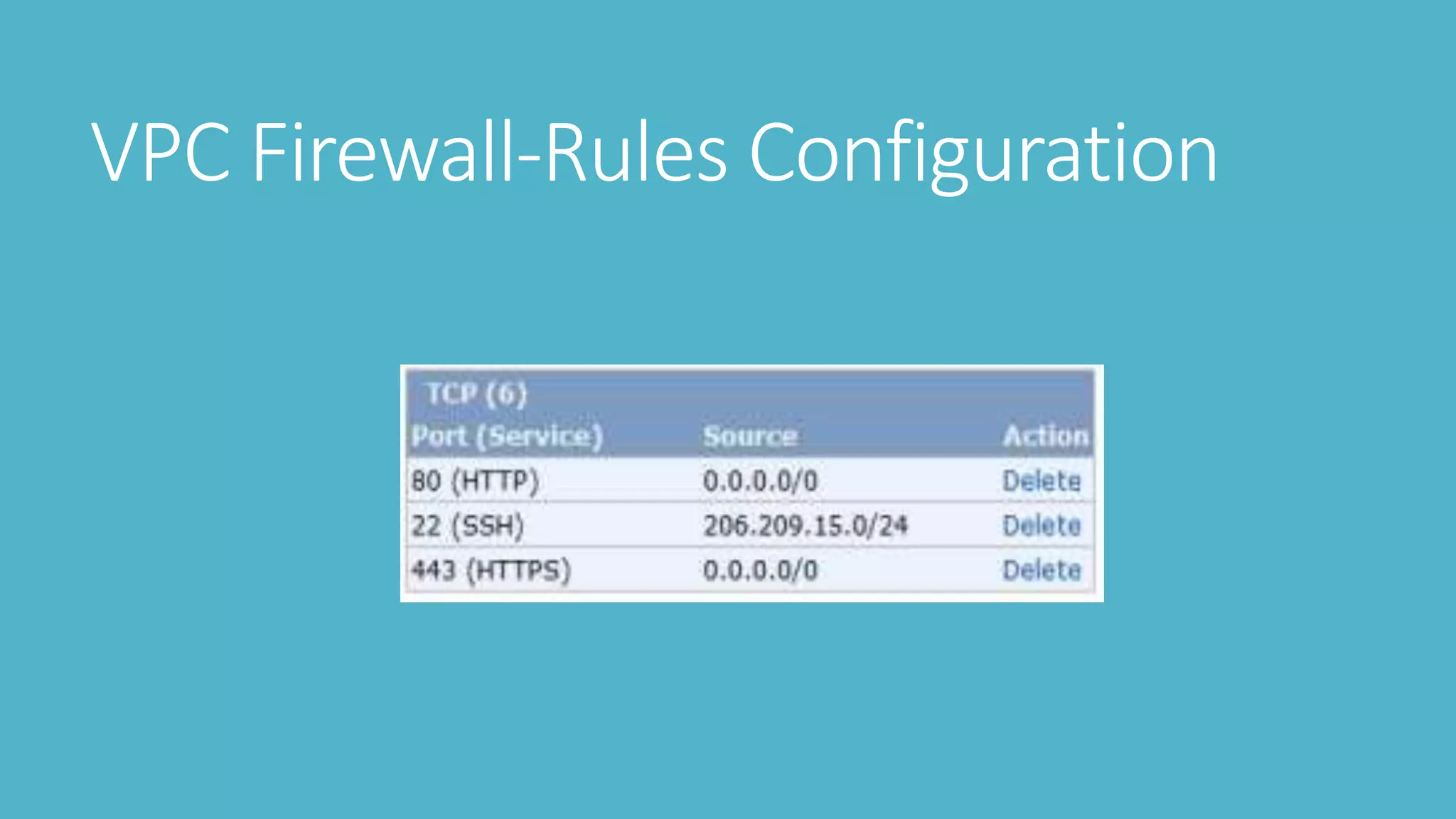
2. Testing SSH security like default credentials and open ports
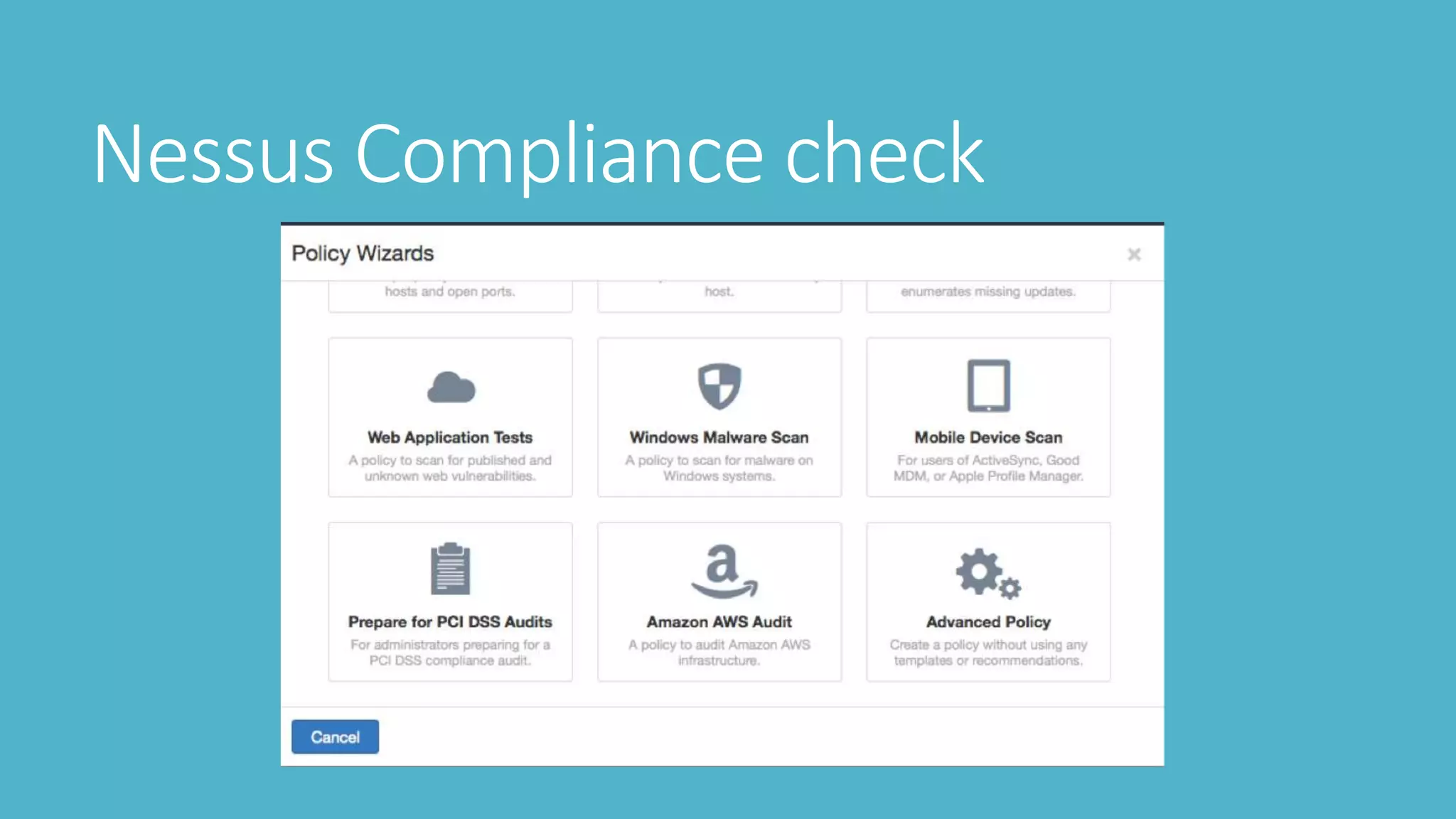
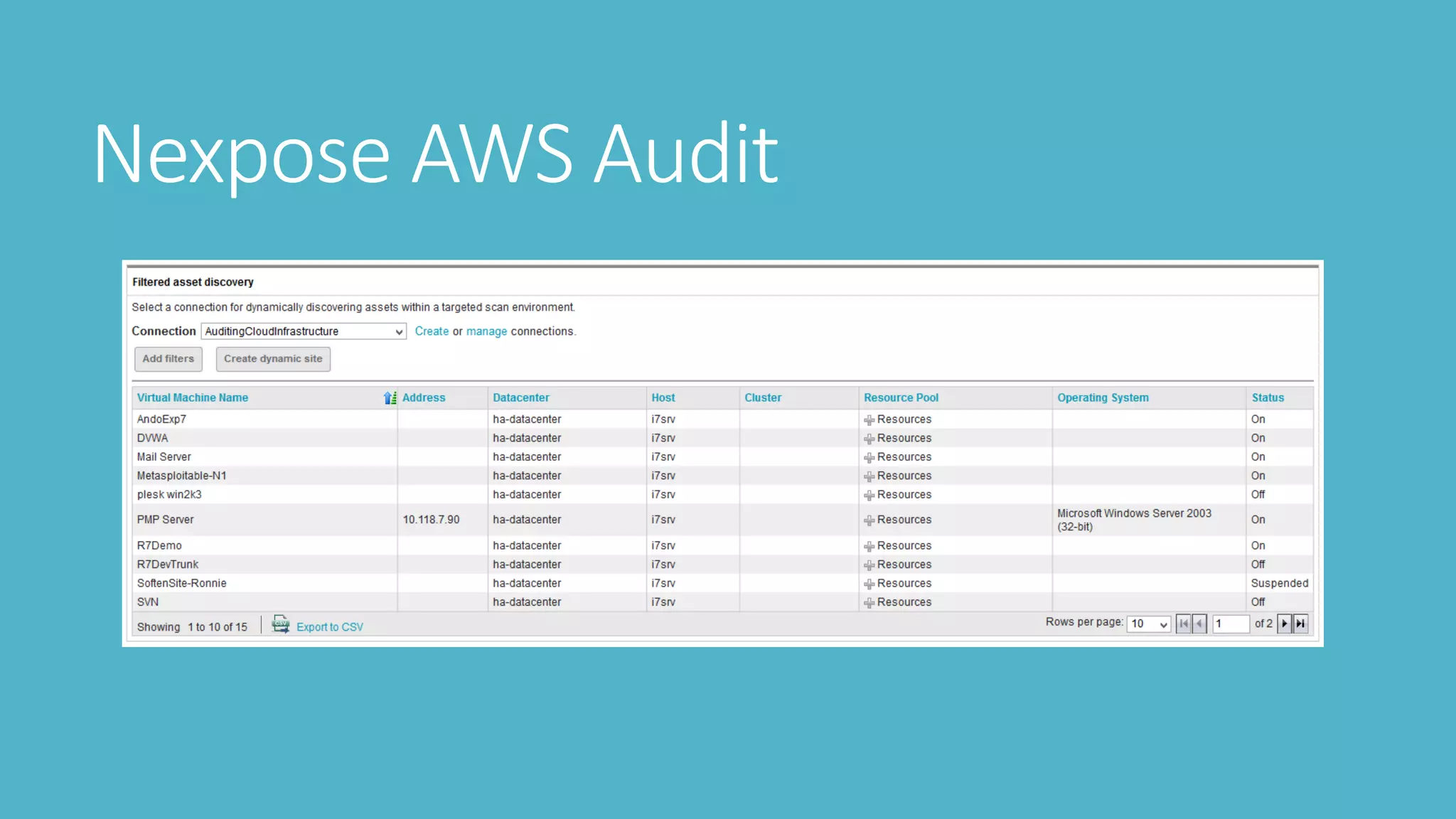
3. Scanning with tools like Nessus, Nmap, and OpenVAS to check vulnerabilities
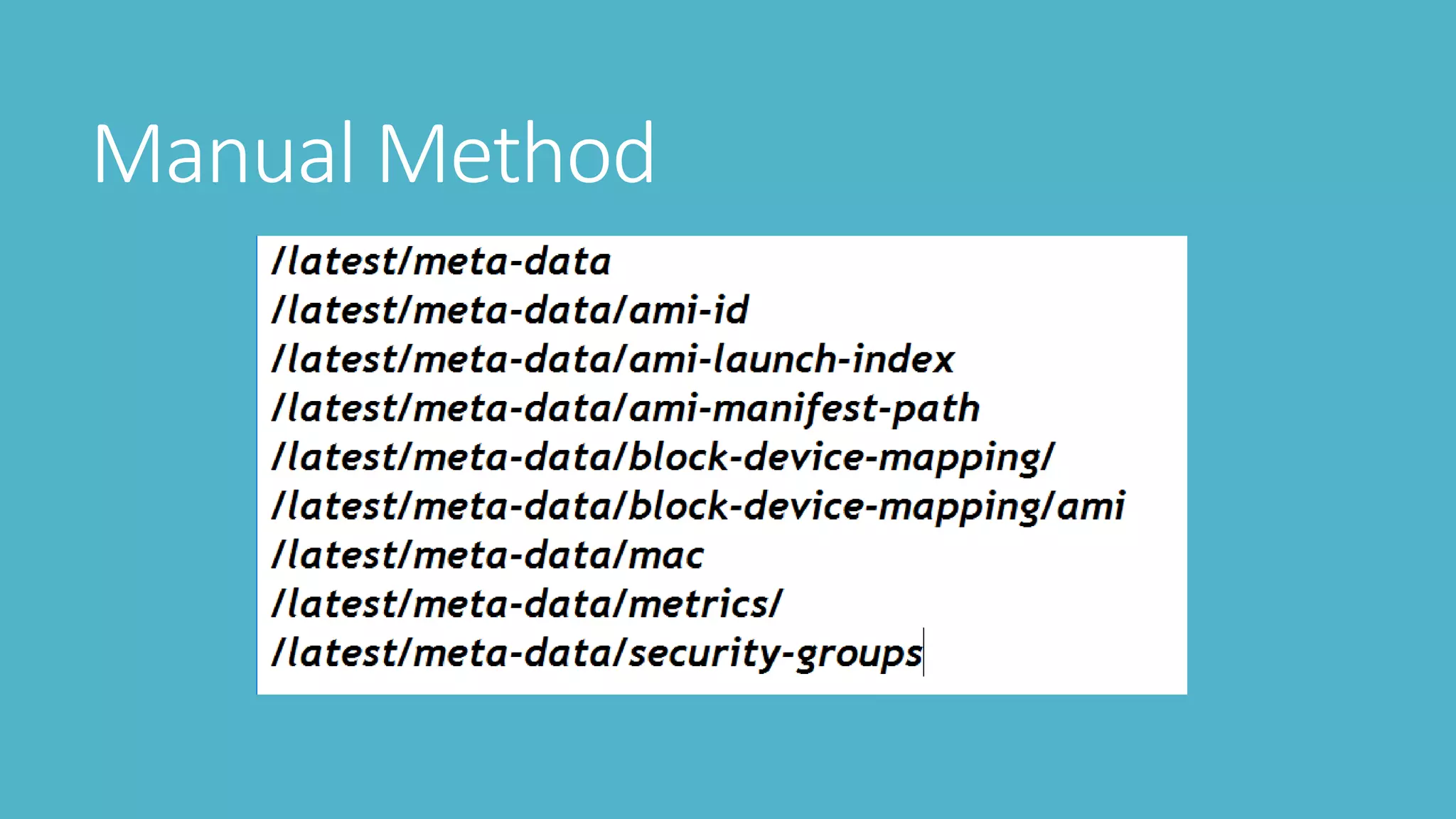
4. Using tools like Nimbostratus to extract metadata like permissions and users