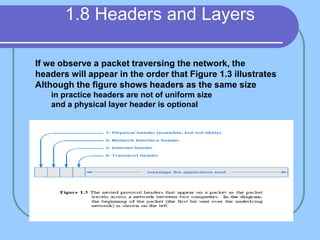
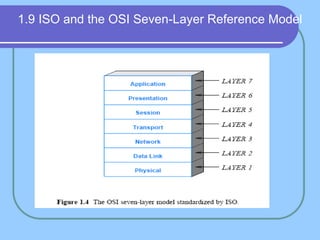
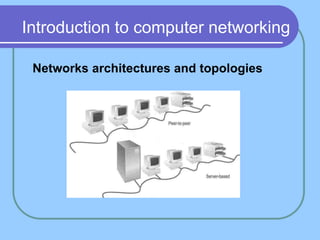
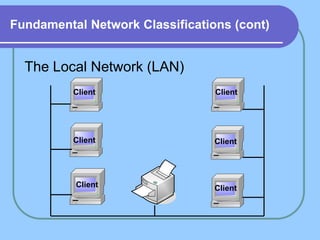
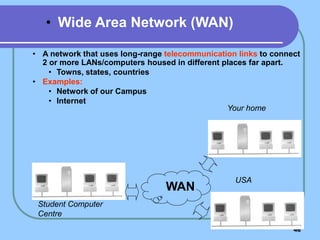
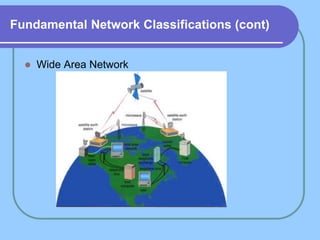
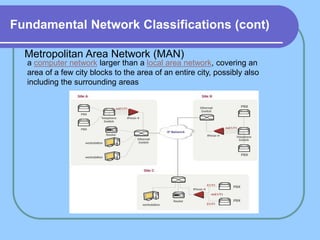
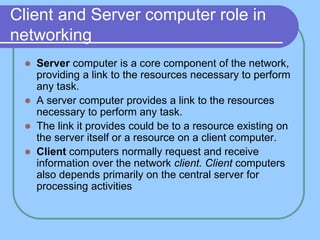
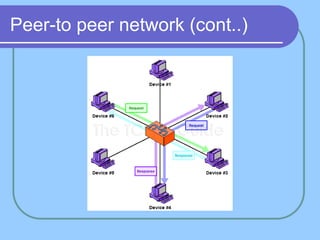
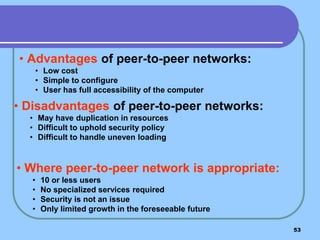
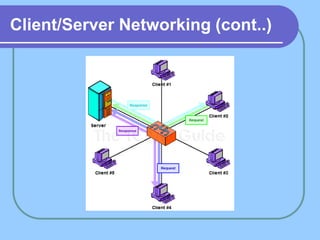
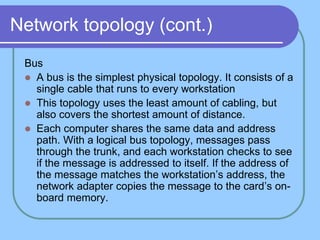
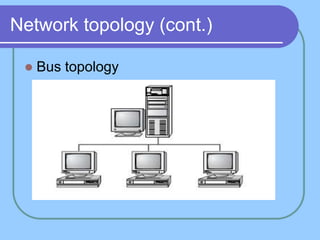
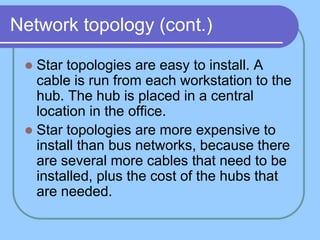
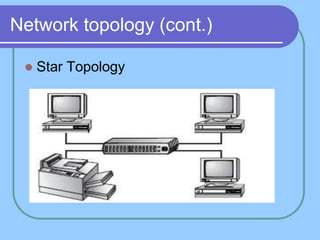
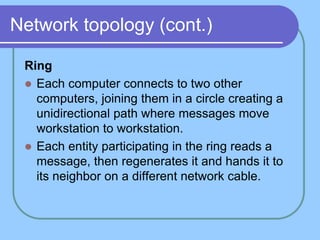
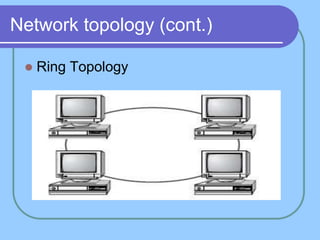
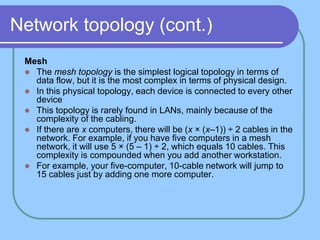
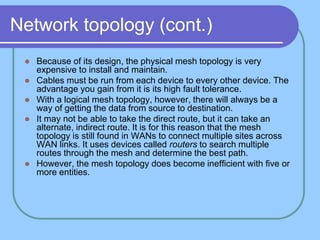
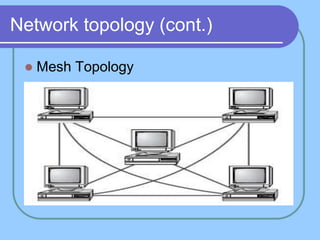
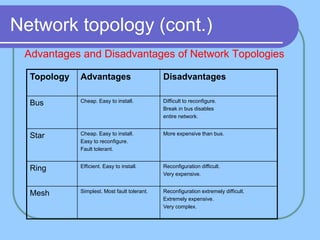
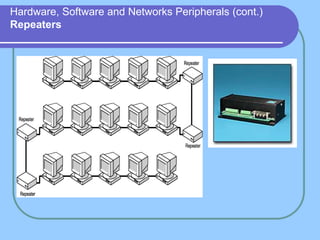
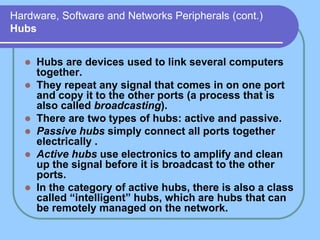
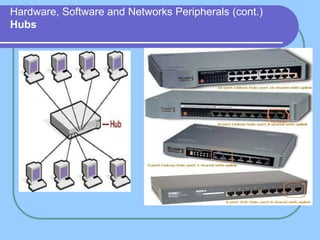
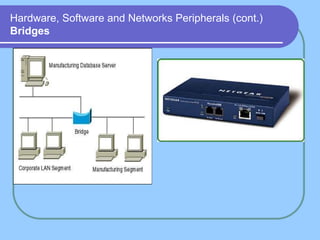
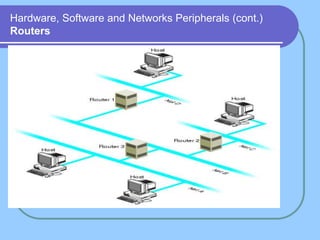
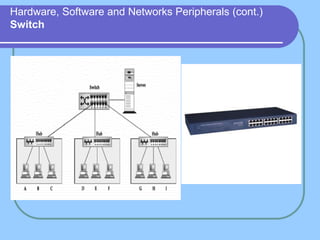
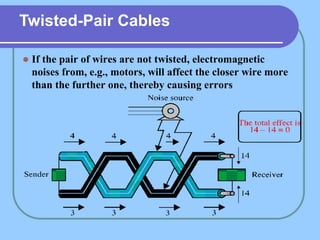
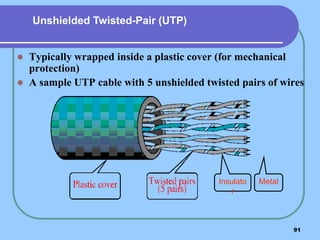
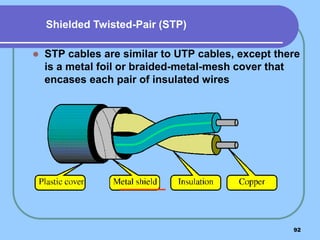
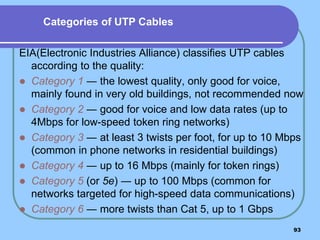
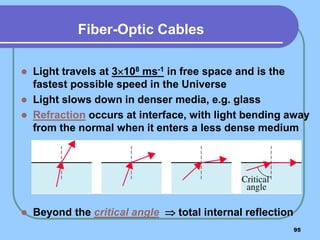
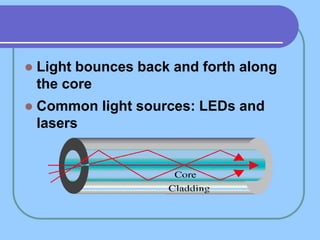
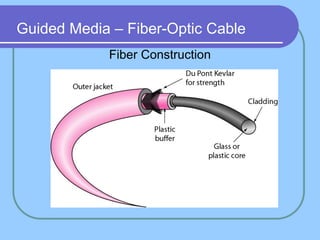
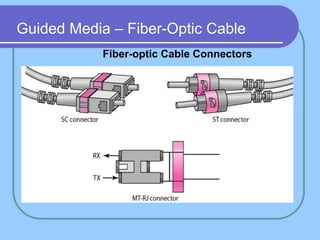
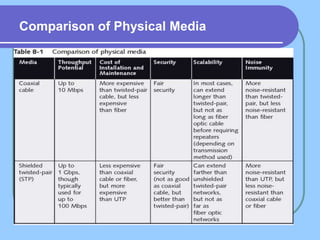
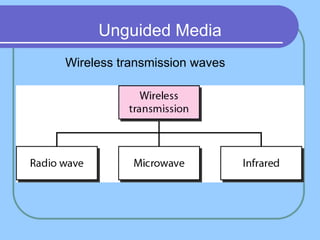
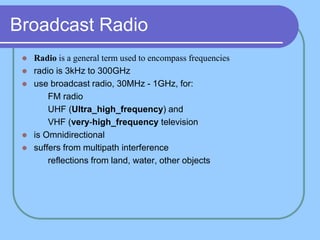
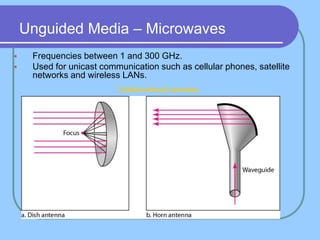
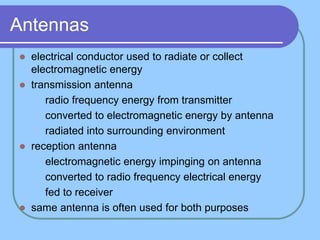
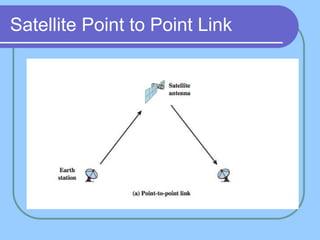
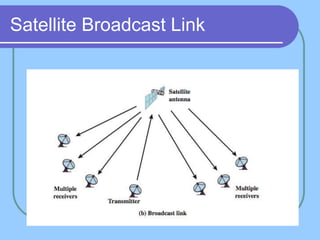
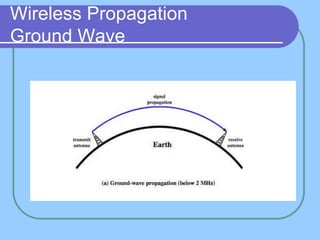
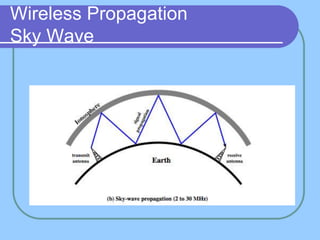
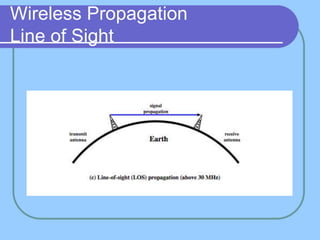
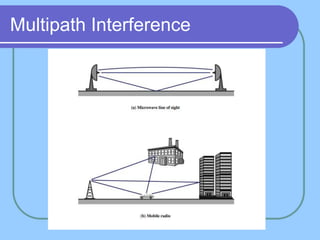
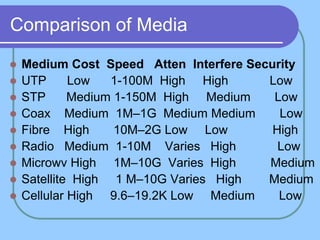
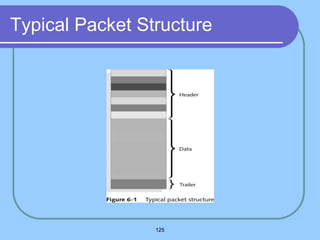
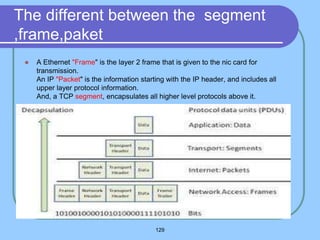
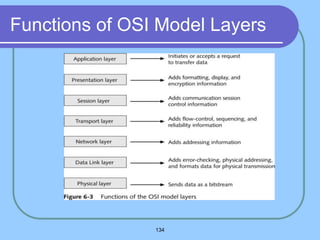
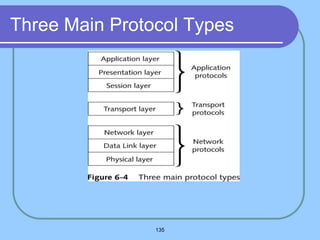
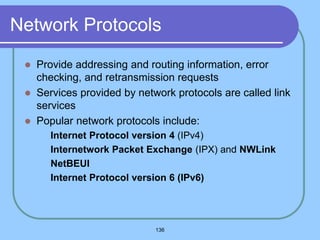
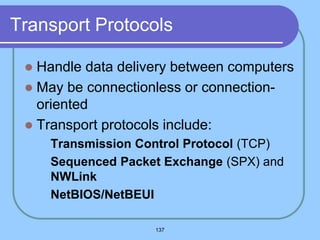
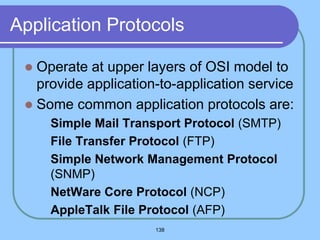
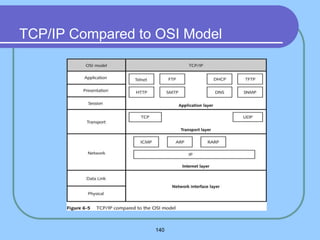
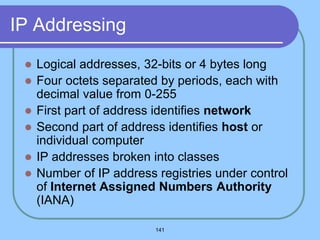
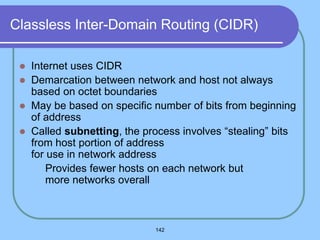
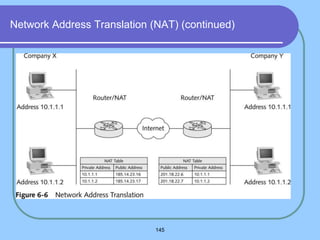
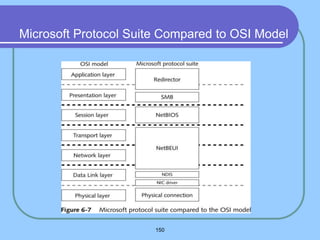
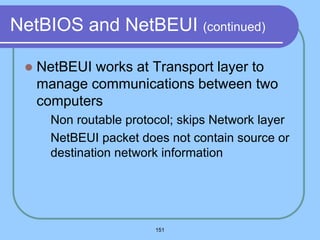
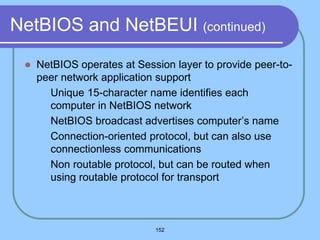
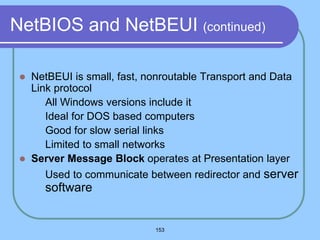
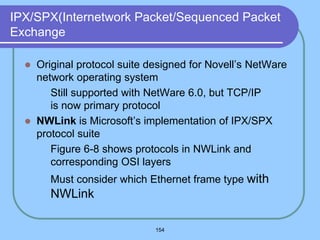
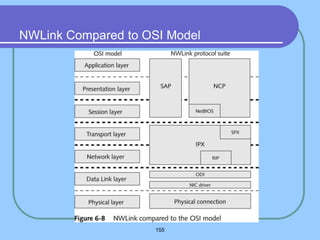
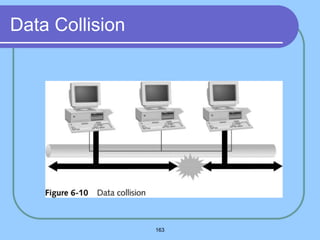
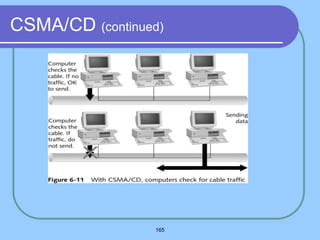
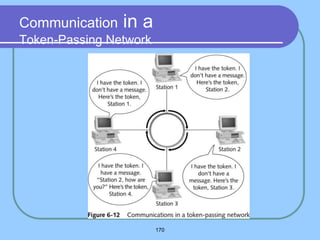
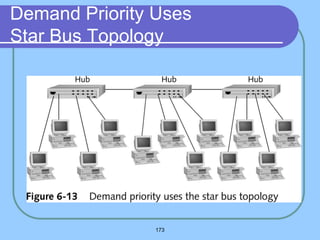
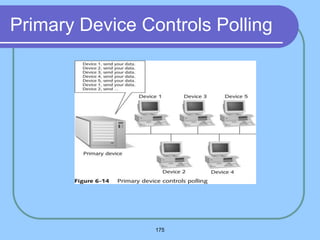
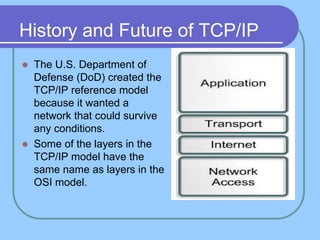
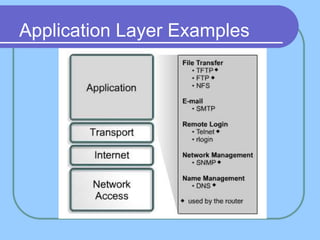
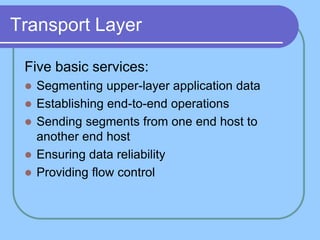
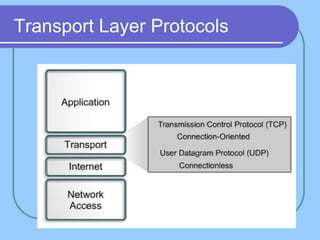
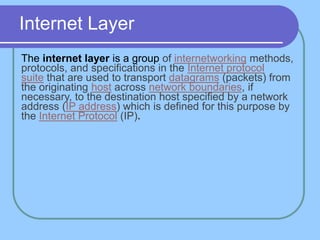
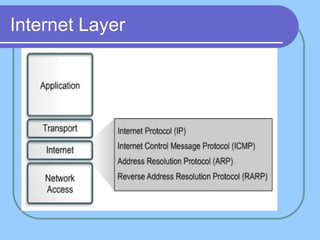
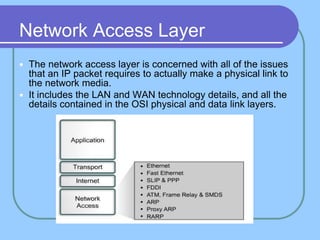
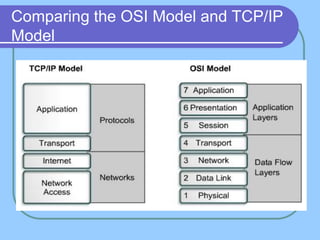
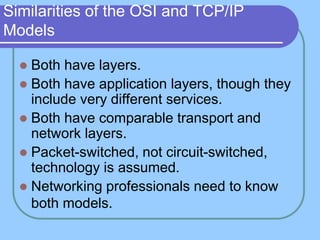
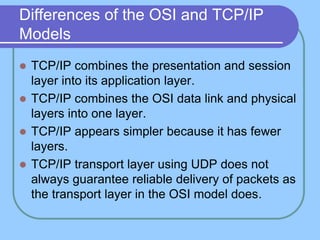
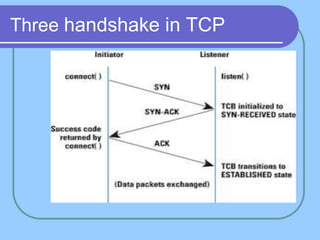
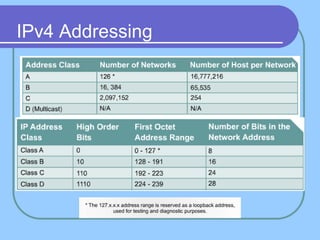
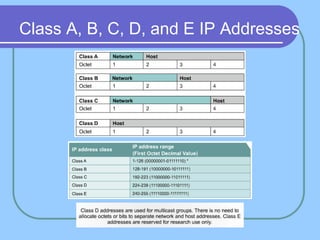
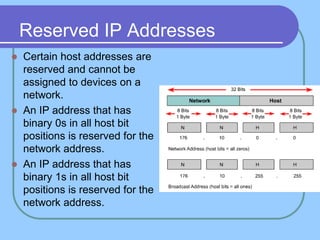
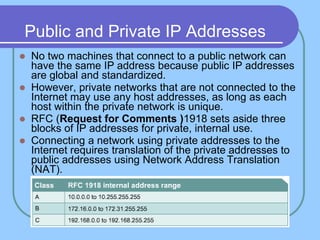
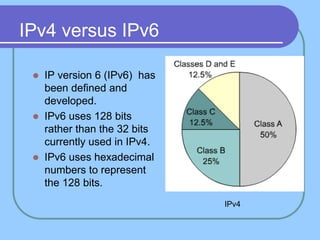
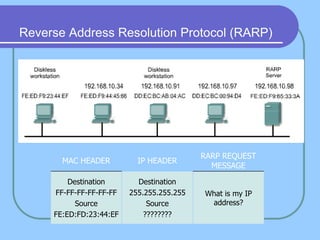
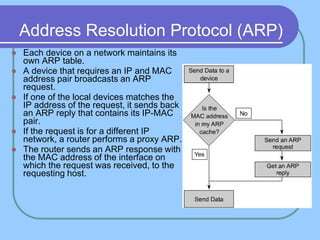
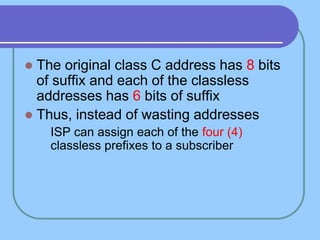
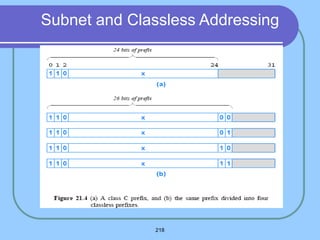
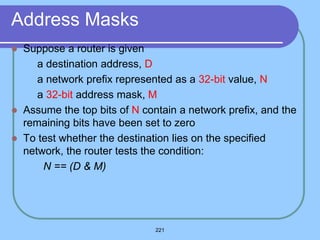
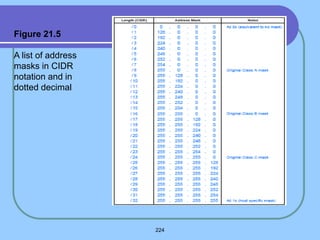
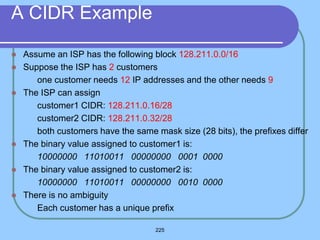
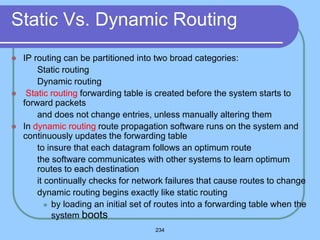
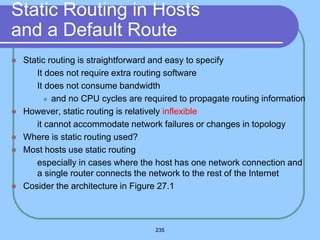
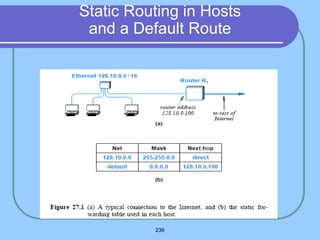
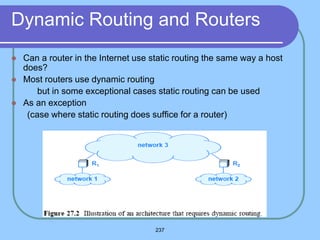
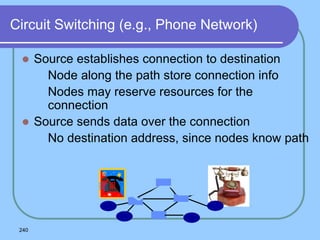
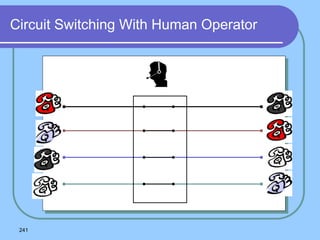
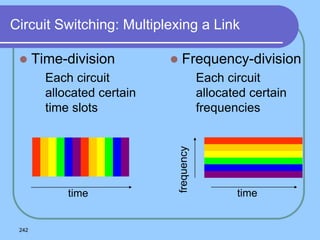
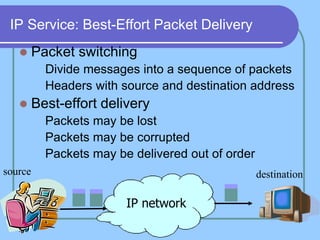
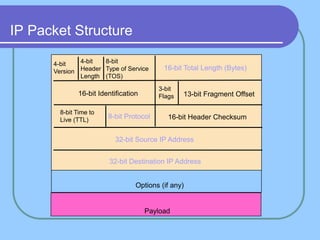
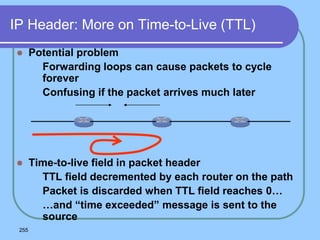
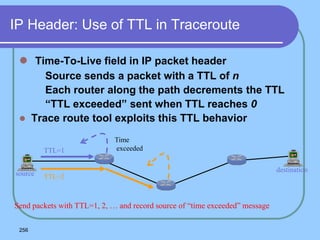
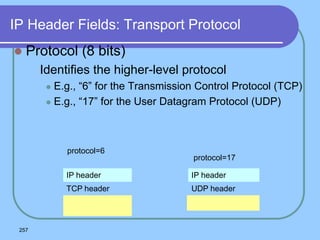
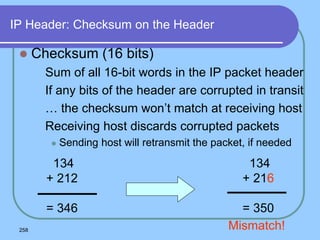
The document provides an overview of a computer networks course, including its objectives, topics, and introduction. The course aims to develop an understanding of key networking principles, models, protocols, and technologies. It will cover the history and growth of networks and the Internet, network architectures and topologies, protocols, and various applications. Lectures will explore topics like different network types, the layered OSI and TCP/IP models, switching, routing, wireless networks and more. The introduction defines what a computer network is and discusses advantages and disadvantages of networking. It also classifies networks based on transmission medium, size, management methods, and topology.