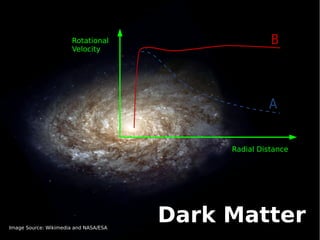
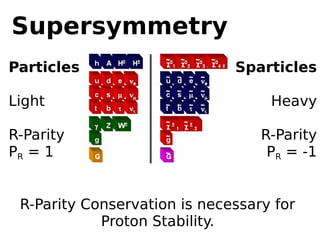
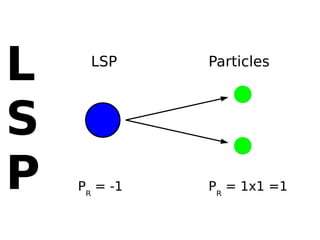
This document discusses supersymmetric dark matter and its potential detection by the IceCube neutrino observatory. It introduces the neutralino as a dark matter candidate particle arising from supersymmetry. Neutralinos could accumulate in celestial bodies like the Sun due to gravitational interactions and weak/gravitational forces. Their annihilation could produce neutrino signals detectable by IceCube. The document outlines scans of the parameter space of the MSSM-25 supersymmetric model to identify regions favored by dark matter relic density and predict event rates and likelihoods for IceCube. The goal is to interpret any neutrino signals IceCube detects in terms of supersymmetric dark matter models.