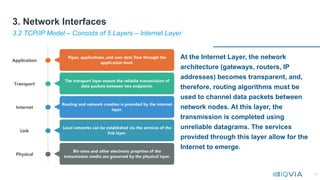
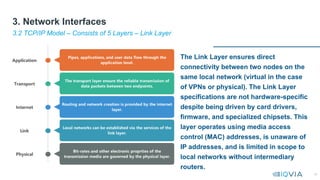
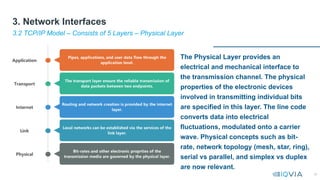
This document serves as a comprehensive guide on interface design and management for system engineers, emphasizing the crucial role interfaces play in connecting systems, applications, and components. It covers various types of interfaces, including user interfaces, file interfaces, and application programming interfaces (APIs), and discusses the importance of effective interface management in complex integration projects. Additionally, it provides insights into network interfaces, architectural principles, and usability heuristics essential for designing efficient and user-friendly interfaces.