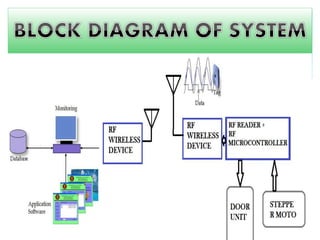
The document discusses radio-frequency identification (RFID) technology. It describes how RFID uses radio waves to transfer data between a reader and a tag to identify items. An RFID system consists of an antenna, transceiver, and RF tag. The document provides examples of how RFID can be used for personal identification, attendance tracking, access control, and vehicle identification by reading tags affixed to items or people. Benefits mentioned include automated data collection, security, scalability, and ability to function without line of sight. Potential applications discussed are inventory management, attendance management, and more.