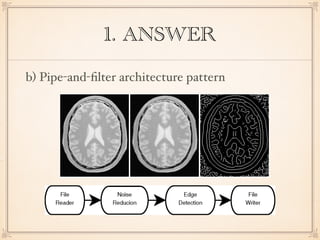
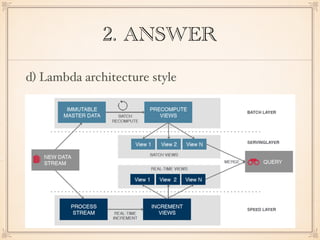
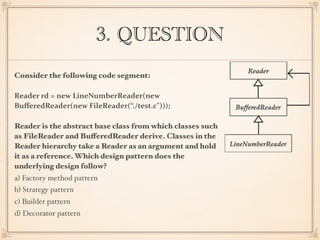
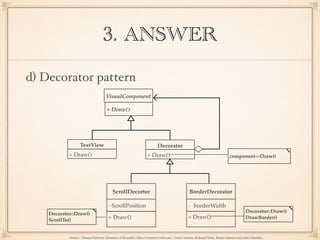
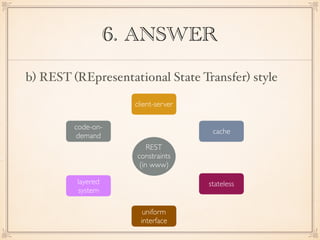
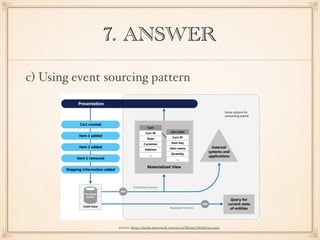
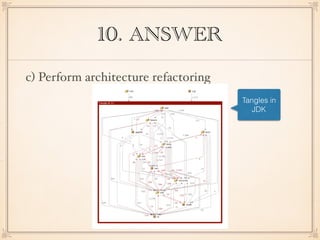
The document describes an application with a pipe-and-filter architecture pattern where sensor data flows through multiple components that each transform the data before passing it to the next component and finally to a modeling and visualization unit. It then asks questions about software architecture patterns and styles like pipe-and-filter, lambda architecture, decorator pattern, Conway's law, architecture drift, REST, event sourcing, and recommends architecture refactoring when dependency analysis finds numerous cycles and tangles.