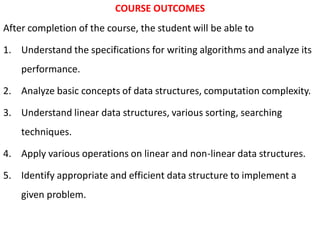
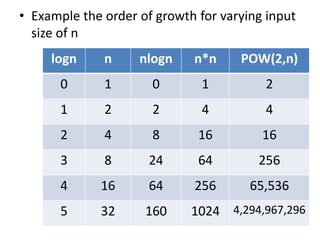
This document discusses data structures and algorithms. It provides course objectives which include imparting concepts of data structures and algorithms, introducing searching and sorting techniques, and developing applications using suitable data structures. Course outcomes include understanding algorithm performance analysis, concepts of data structures, linear data structures, and identifying efficient data structure implementations. The document also covers algorithm basics, specifications, expressions, analysis techniques and asymptotic notations for analyzing algorithms.












![• The Identifier should begin by letter and not by digit. An
identifier can be a combination of alphanumeric string.
• Assignment operator
Ex:- Variable Expression
• There are other types of operators like Boolean(true , false),
Logical(and , or , not) and Relational(<,<=,>,>=,=).
• Array indices [ , ] initial index is 0.
• Inputting and outputting can be done using read and write.
Ex:- write(“WELCOME”);
read(val);](https://image.slidesharecdn.com/dsaunit1-221114141529-4d928371/85/DSA-14-320.jpg)



















![Analysis of Algorithms
• We can have three cases to analyze an algorithm:
1) Worst Case
2) Average Case
3) Best Case
Ex:- Linear Search
int search(int arr[], int n, int x)
{
int i;
for (i=0; i<n; i++)
{
if (arr[i] == x)
return i;
}
return -1;
}](https://image.slidesharecdn.com/dsaunit1-221114141529-4d928371/85/DSA-35-320.jpg)


![int binarySearch(int arr[], int l, int r, int x)
{
if (r >= l)
{
int mid = l + (r - l)/2;
if (arr[mid] == x)
return mid;
if (arr[mid] > x)
return binarySearch(arr, l, mid-1, x);
return binarySearch(arr, mid+1, r, x);
}
return -1;
}](https://image.slidesharecdn.com/dsaunit1-221114141529-4d928371/85/DSA-38-320.jpg)













