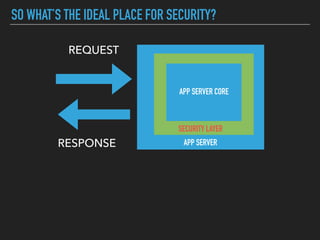
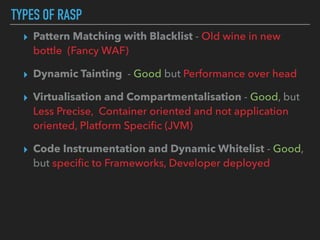
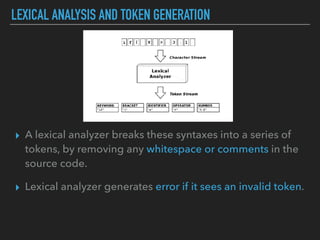
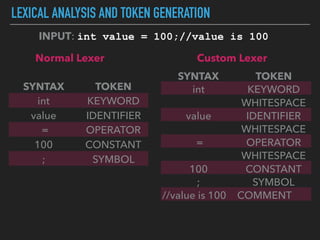
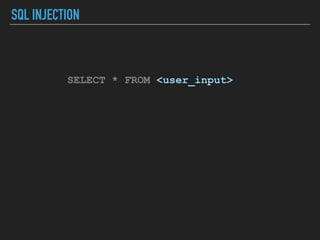
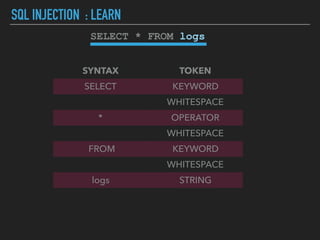
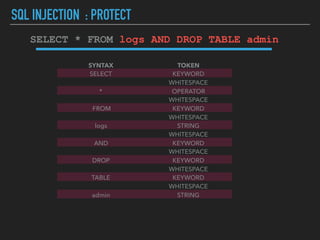
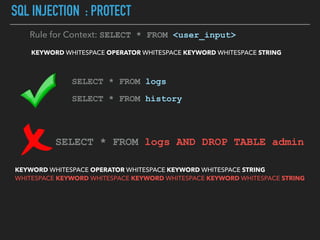
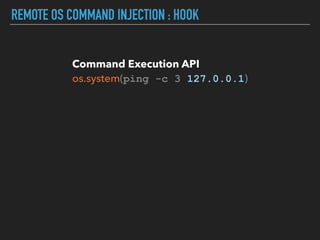
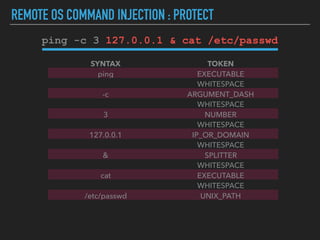
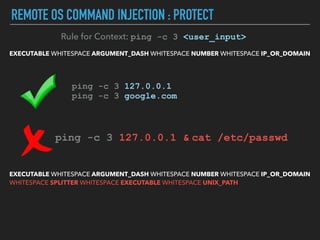
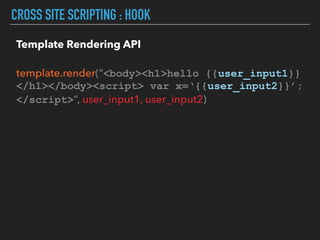
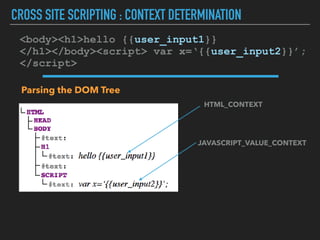
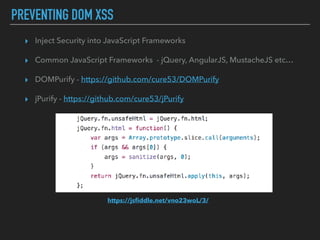
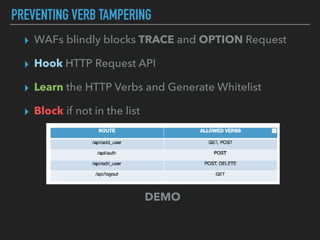
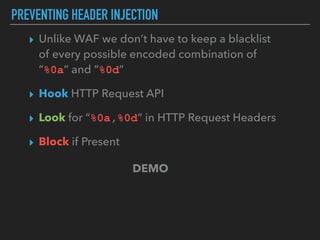
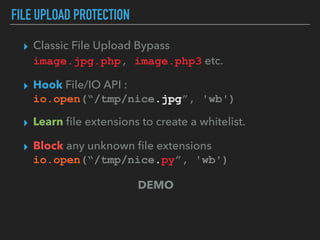
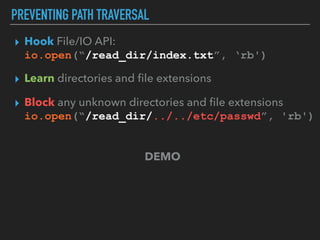
Ajin Abraham discusses the importance of integrating security into web applications at runtime, highlighting the limitations of traditional Web Application Firewalls (WAFs) and urging the adoption of Runtime Application Self-Defense (RASP) techniques. He outlines various web security challenges, including session hijacking and SQL injection, and emphasizes the need for precise vulnerability detection and prevention without heavy reliance on blacklists. The talk advocates for minimal performance impact and easy deployment of security solutions, ensuring robust protection against zero-day vulnerabilities.