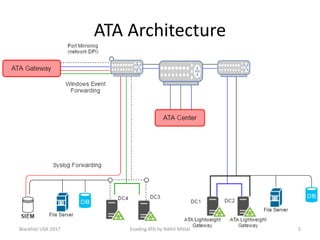
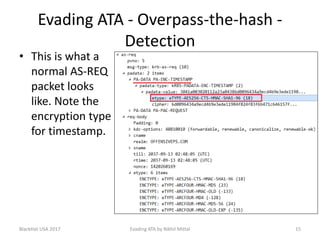
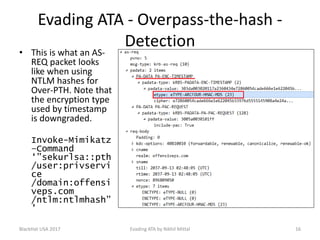
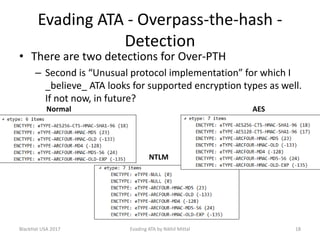
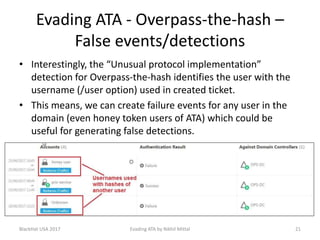
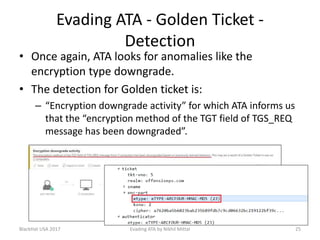
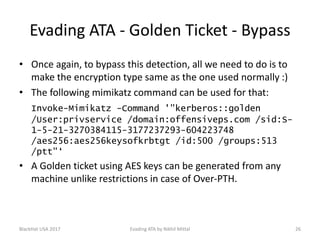
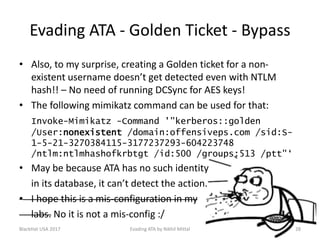
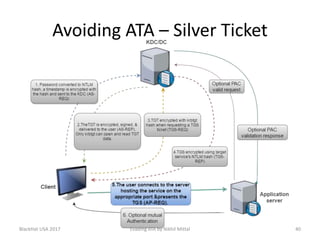
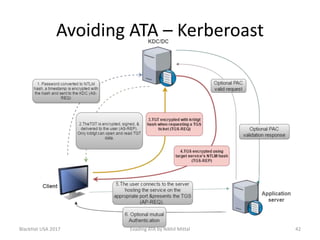
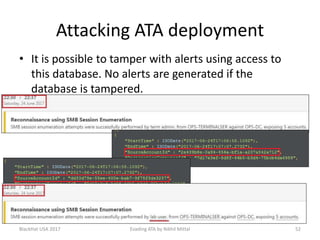
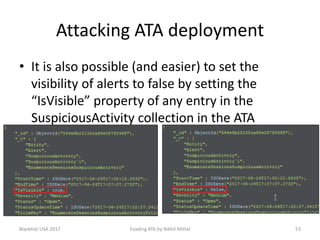
The document discusses techniques for evading Microsoft's Advanced Threat Analytics (ATA) in the context of Active Directory attacks. It details various attack methods, including reconnaissance, brute force, overpass-the-hash, and golden ticket attacks, along with their detection mechanisms and ways to bypass them. The presentation emphasizes the importance of avoiding direct interactions with the domain controller to remain undetected while executing these attacks.