Memory and File Formats Explained
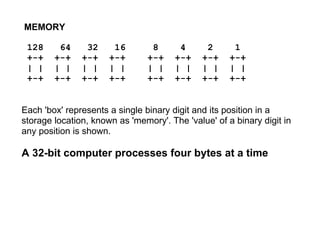
- 1. MEMORY 128 64 32 16 8 4 2 1 +-+ +-+ +-+ +-+ +-+ +-+ +-+ +-+ | | | | | | | | | | | | | | | | +-+ +-+ +-+ +-+ +-+ +-+ +-+ +-+ Each 'box' represents a single binary digit and its position in a storage location, known as 'memory'. The 'value' of a binary digit in any position is shown. A 32-bit computer processes four bytes at a time
- 2. BITS & BYTES 1 BIT - stands for Binary digIT 1 Byte = 8 bits ½ byte = 1 nibble = 4 bits 2x byte = 1 word = 16 bits 2x word = 1 long word = 32 bits 1KByte = 1,024 bytes = 210 1MByte = 1,048,576 bytes = 220 1GByte = 230 bytes 1TByte = 240 bytes
- 3. Memory Addressing The ability of a computer to access any particular area of its memory is referred to as "addressing". Addressing is a function of the number of microprocessor address lines on its "BUS", and is therefore, hardware dependant. ● 8088/86 cpu can address up to 1MB with its 20 address lines ● 80286 cpu can address up to 16MB with its 24 address lines ● 80386 cpu can address up to 4GB with its 32 address lines Intel® Desktop Processor Comparison Chart http://compare.intel.com/PCC/default.aspx?familyid=1&culture=en-US
- 4. EXTENDED MEMORY MAP 2^32 4GB +---------+ | | This shows a 'grid' of | | memory 'cells', 8-bits | | wide by 4GB long. 2^24 16MB| | | | 2^20 1MB |---------| FFFFF |---------| E0000 |---------| C0000 640KB |---------| A0000 | | | | 0KB +---------+ 00000
- 5. INTERPRETATION OF MEMORY CONTENTS Memory cells store voltages - Interpreted as 0 or 1 Combinations REPRESENT numeric data ie. Letters, numbers, punctuation marks, graphics characters Memory is not restricted to using numeric coding Bytes can represent: ● CPU Instruction codes ● alpha numeric characters (word processors) ● pure binary No's It's all down to interpretation with the software application.
- 6. ASCII AMERICAN STANDARD CODE FOR INFORMATION INTERCHANGE ASCII is a coding standard which means that data is stored according to the ascii standards rules. Original ASCII, 128 codes (0 to127) represented • English alphabet • punctuation • control codes
- 7. Now 256 codes (0---->255) = orig ASCII + 128 codes called extended character set European characters Graphic '' Scientific '‘ Each keyboard key has an ASCII code assigned eg: 128 is stored as 3 BYTES OF ASCII DATA 1-------> 49 2-------> 50 8-------> 56 whereas (pure) binary data would be stored as 1 byte
- 8. A.S.C.I.I. Coding There are 255 characters available to 8 bits. 0 isn't used. Only the numbers from 32 to 126 (20 to 7E hex) are defined as *printable* characters (the others are defined as control codes) 0 1 2 3 4 5 6 7 8 9 A B C D E F --------------------------------- 2 | ! " # $ % & ' ( ) * + , - . / 3 | 0 1 2 3 4 5 6 7 8 9 : ; < = > ? 4 | @ A B C D E F G H I J K L M N O 5 | P Q R S T U V W X Y Z [ ] ^ _ 6 | ` a b c d e f g h i j k l m n o 7 | p q r s t u v w x y z { | } ~ http://en.wikipedia.org/wiki/ASCII http://www.asciitable.com/
- 9. Microsoft file names Windows 9x onwards allows long file names and control characters to be used. When transferring files to INTERNET systems, the filenames have to be re-formatted to comply with UNIX standards. No character is allowed which the system uses for commands or other functions, such as , /, ., etc. The underscore character _ is accepted as a separator as a space cannot be used. Older MS-DOS formatted filenames can contain no more than 8 characters, and these must not contain any of the command characters.
- 10. File extensions ● The file name is followed by a dot . which separates it from its extension. ● The file extension is 3 characters long and describes the type of file. *.COM - Command file. Runs from the DOS prompt. Small file =<64 KB *.EXE - Executable file. Larger file >= 64 KB *.SYS - System file. Installed in memory using an installation program. *.BAT - Batch File. Contains series of text commands batched together. Other extensions are produced typically by application software for their data files, eg .doc, .html, etc. (The * is used here to represent any filename)
- 11. Windows drive storage The DOS system uses drive letters, such as a: and b: for floppy disk drives c: for the hard disk drive d: or e: for a CD-ROM drive f: onwards for network drives |_ a:____ |_ b: |_ subdirectories |_ c: |_ |_ d: |_ |_ e: |_ f:____ |_ |_ subdirectories
- 12. UNIX drive storage ● There are no drive letters. ● The directory structure starts from the 'root' where everything is seen as a file. ● Directories are simply 'mounted' into another directory. ● Internet URLs follow Unix filename conventions Windows: k:drivespace Unix: /home/user/webspace/images Internet: http://news.bbc.co.uk/1/hi/sci/tech/default.stm
- 13. +-----+ | / | +--+--+ | +--------+---+-----+--------+ | | | | +--+--+ +--+--+ +---+--+ +--+--+ | bin | | usr | | home | | etc | +-----+ +-----+ +--+---+ +-----+ | +-------------+-----+ | | +---+--+ +---+--+ | FRED | | DAVE | +---+--+ +---+--+ | | +-----+---+ +----+-----+ | | | | +---+--+ +---+--+ +--+---+ +---+--+ | work | | web | | work | | web | +------+ +------+ +------+ +------+
- 14. Commercial Web filespace • ISP webspace hosting your own web domain, the industry standard access tool is FTP • The web root, eg http://www.somenet.com will be kept in a subdirectory • Every ISP puts this subdirectory in different places, eg. http://splicehost.com/faq.html PROGRAMS' LOCATION - What is the path to PERL? /usr/bin/perl - What is the path to SENDMAIL? /usr/sbin/sendmail - What is the path to DATE? /bin/date - What is the path of my files? /home/yourusername - Web read-able files are in /home/username/public_html However, you are only allowed to work from /public_html, and /home/username is kept invisible to you. NOTE: DRIVE LETTERS NEVER APPEAR - ONLY UNIX DIRECTORIES
- 15. Internet file naming rules are UNIX
