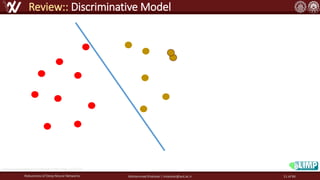
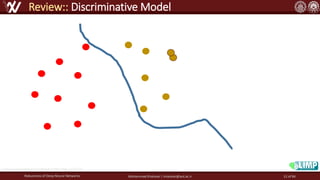
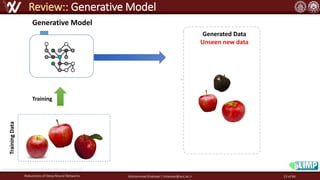
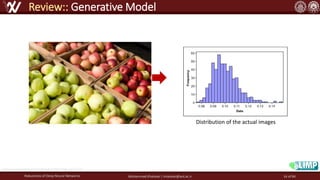
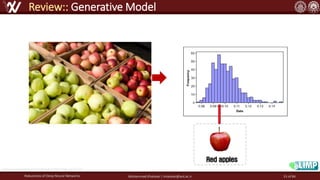
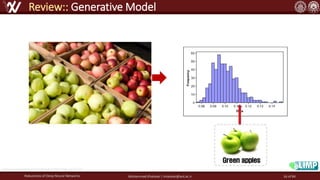
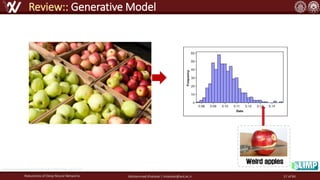
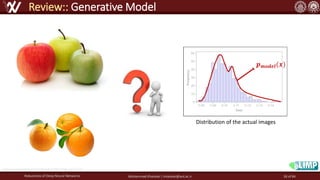
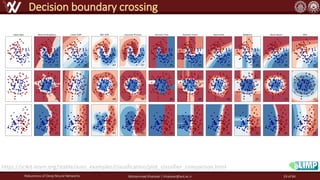
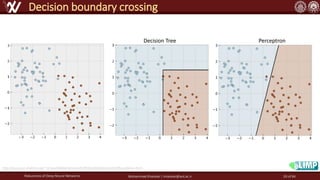
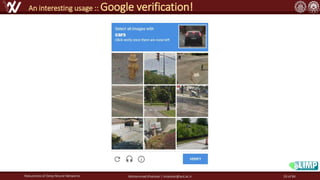
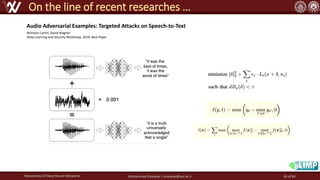
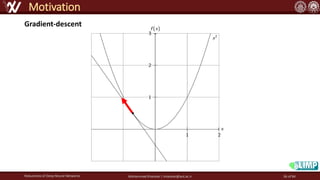
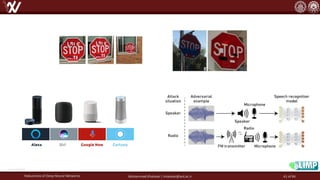
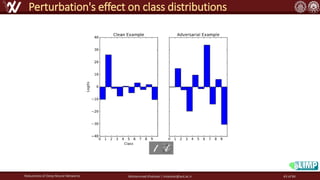
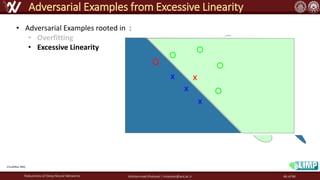
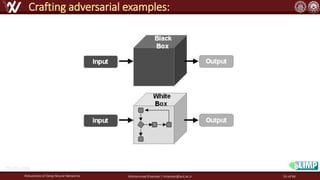
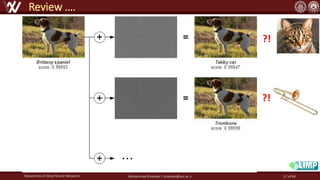
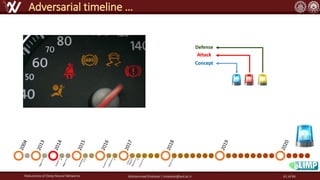
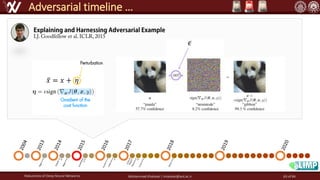
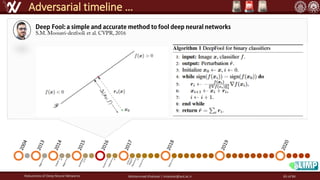
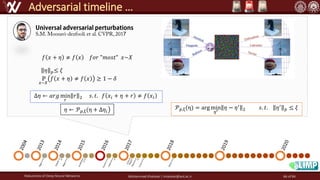
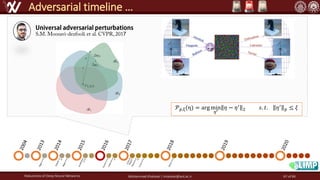
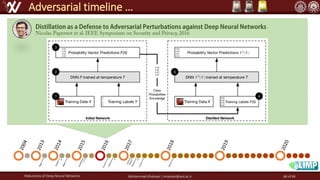
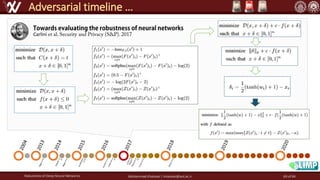
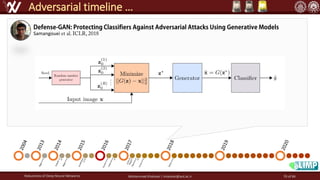
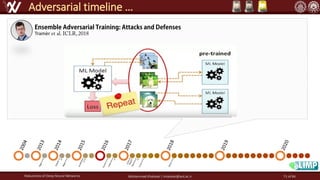
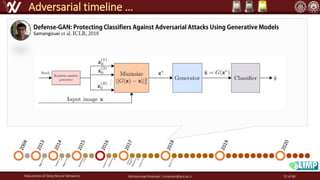
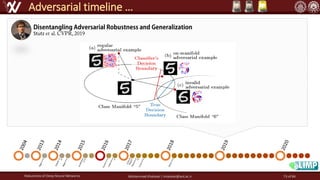
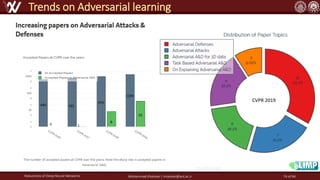
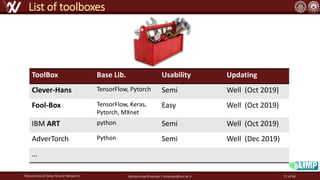
The document discusses the robustness of deep neural networks (DNN), focusing on their vulnerabilities to various types of attacks, including adversarial examples. It explores different attack models, defense strategies, and the complexities of maintaining DNN robustness amidst adversarial threats. Additionally, the document emphasizes the challenges associated with creating effective defenses against these adversarial attacks.