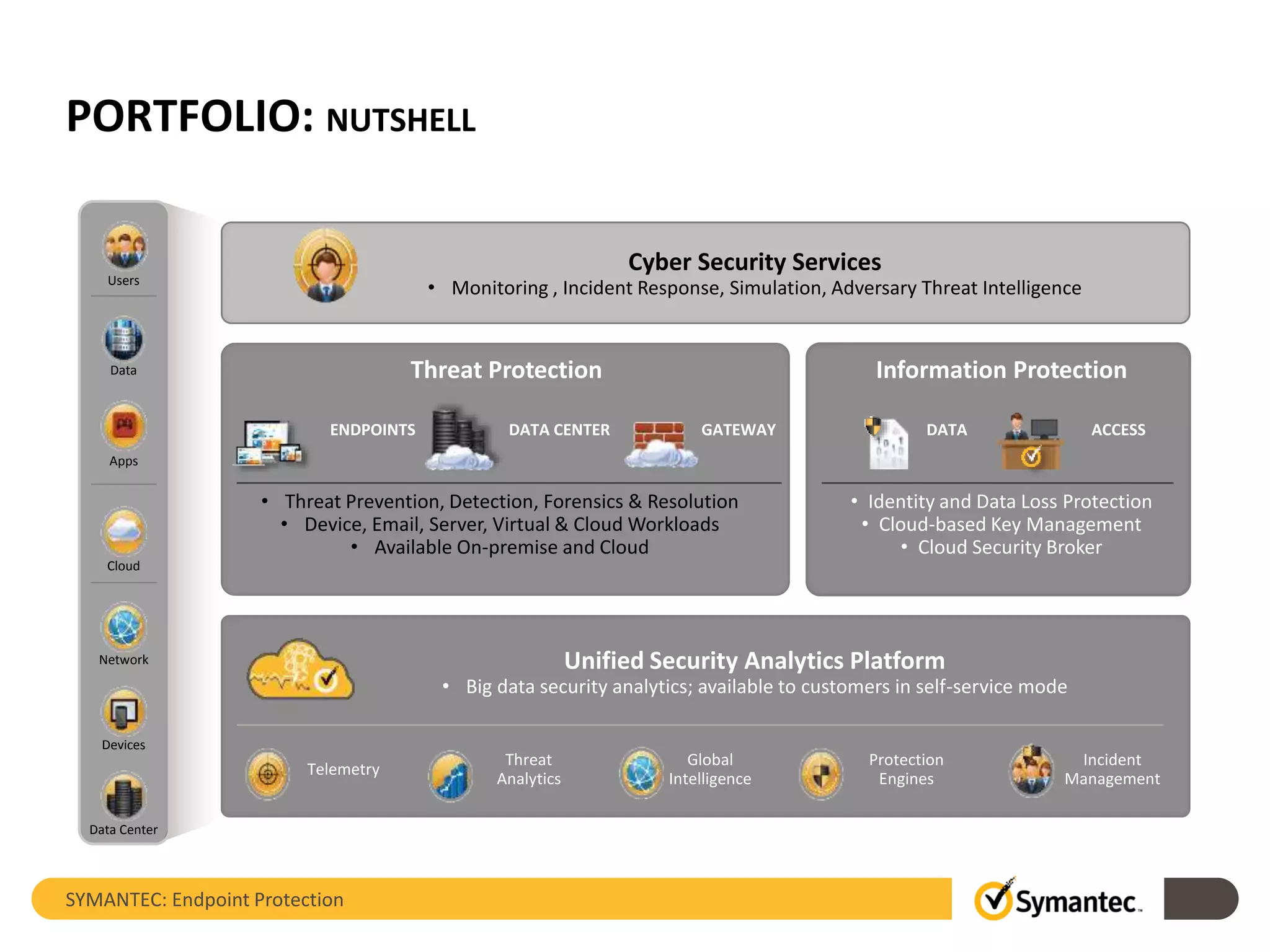
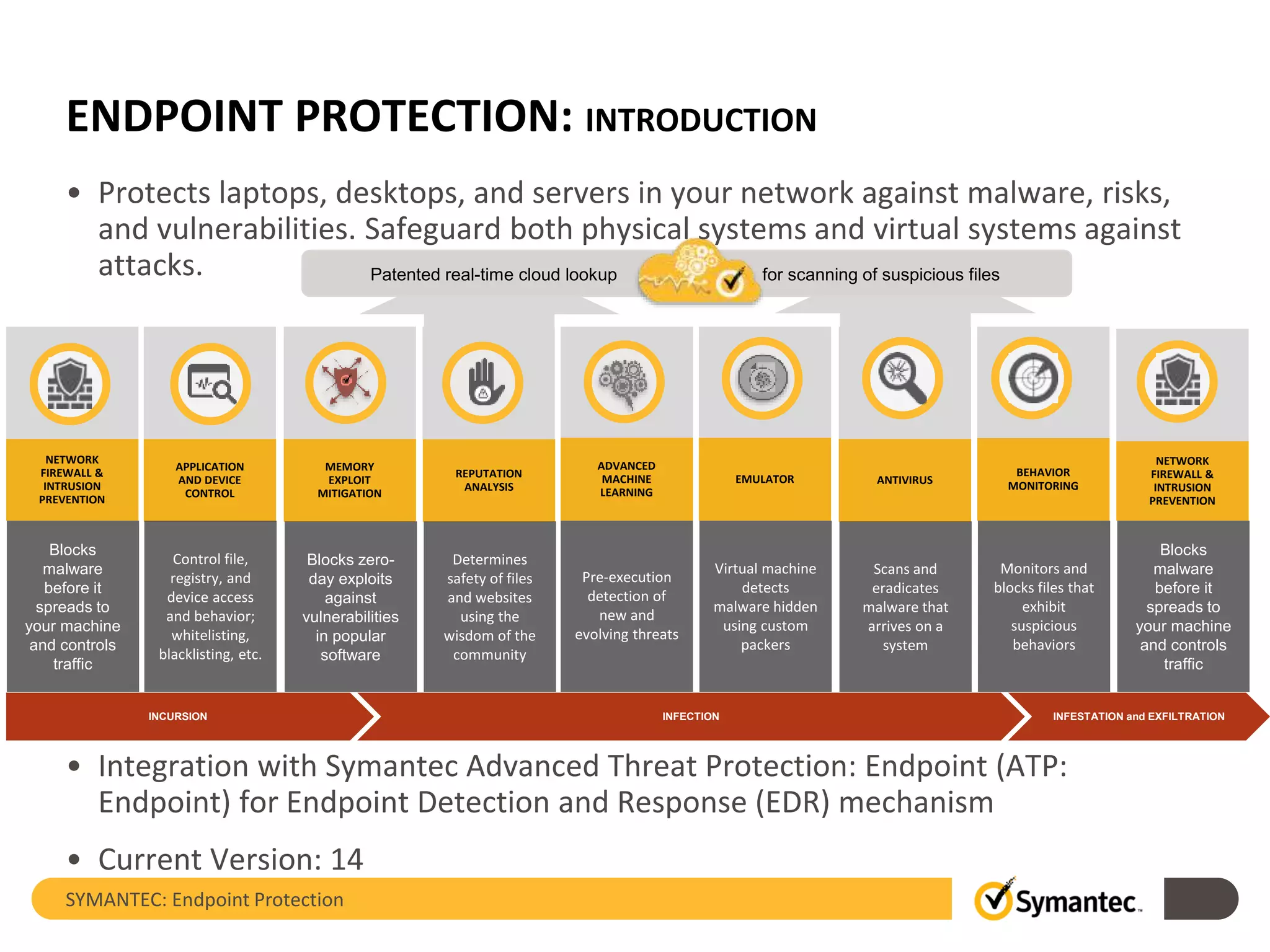
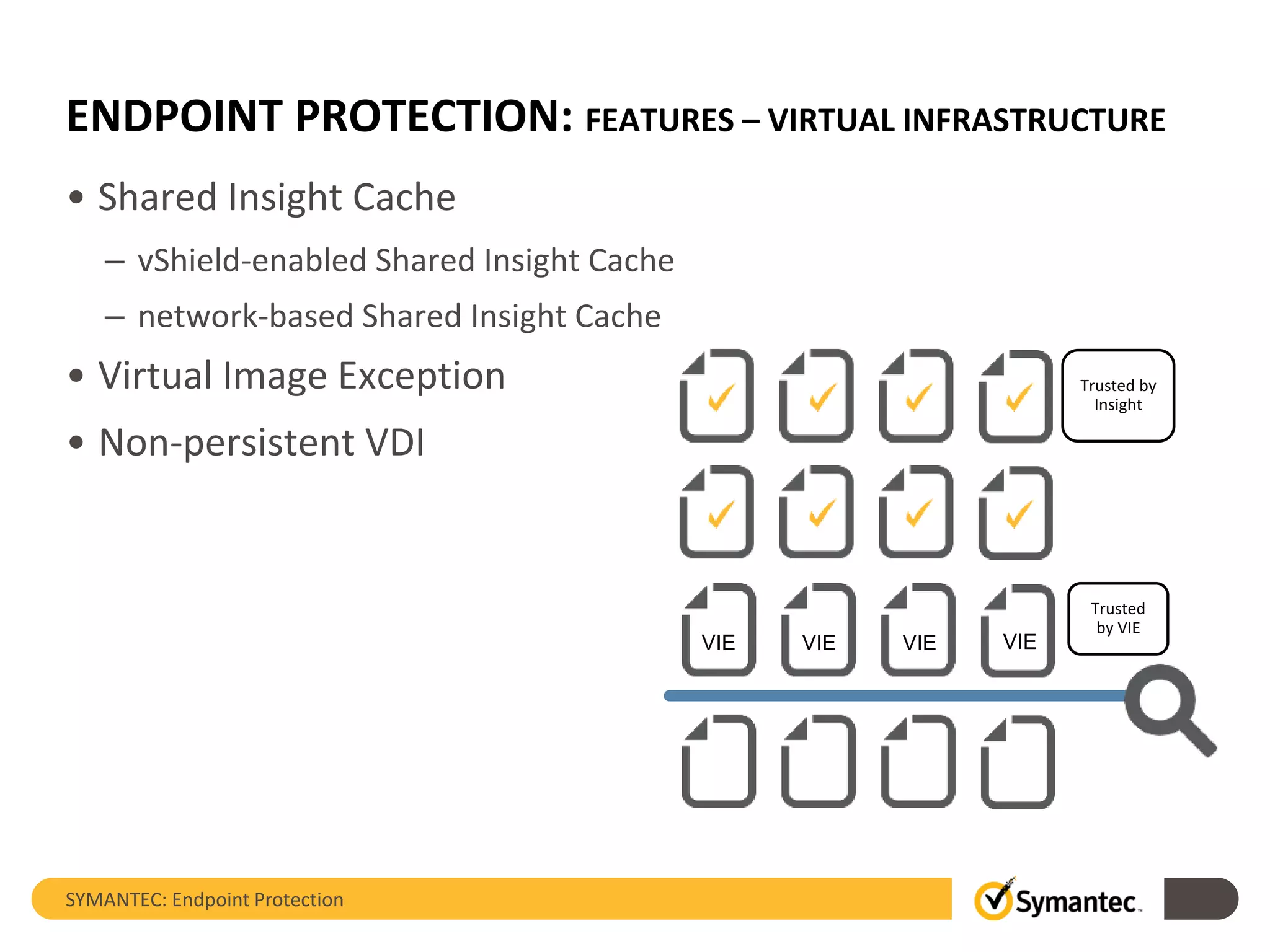
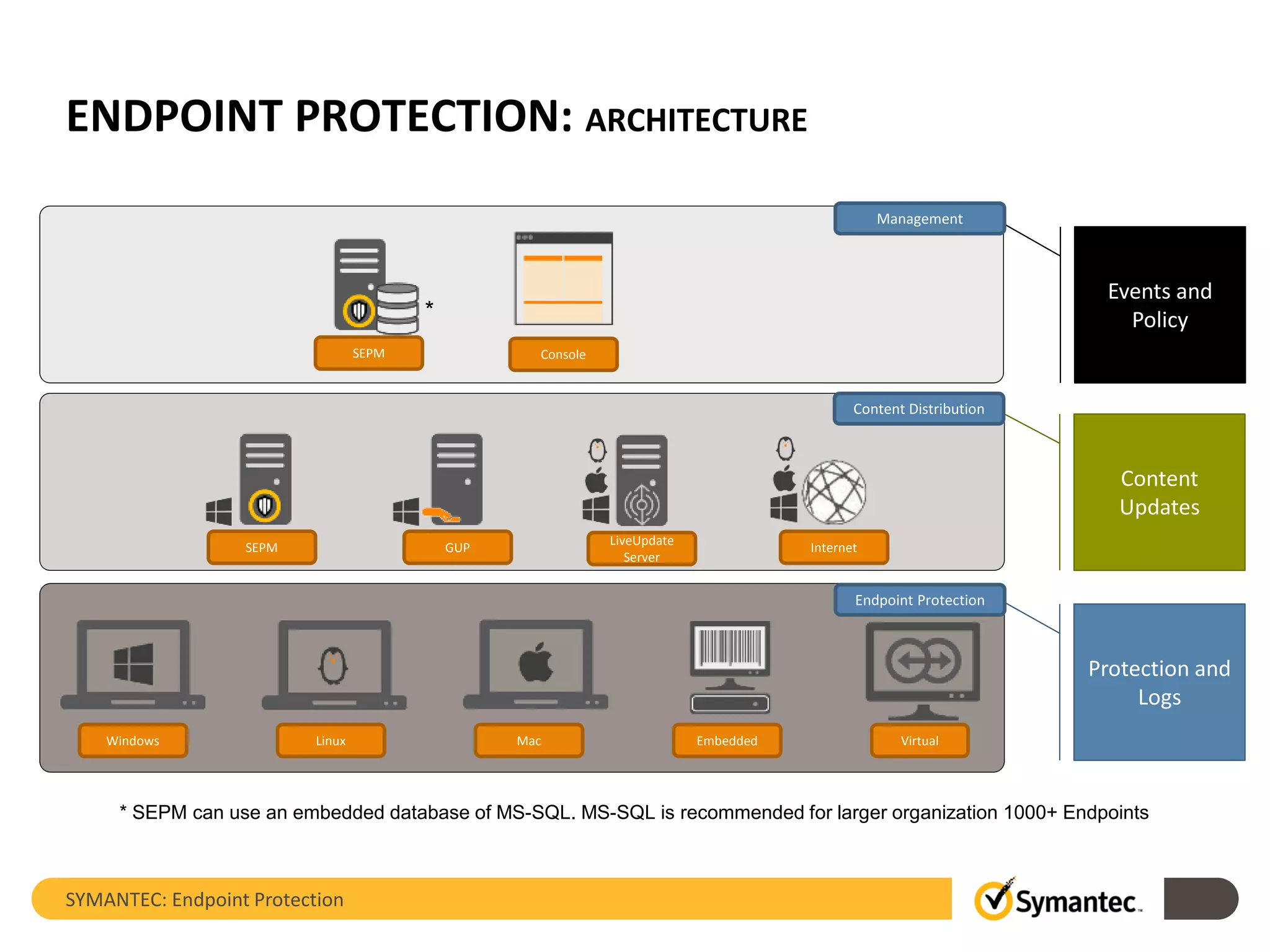
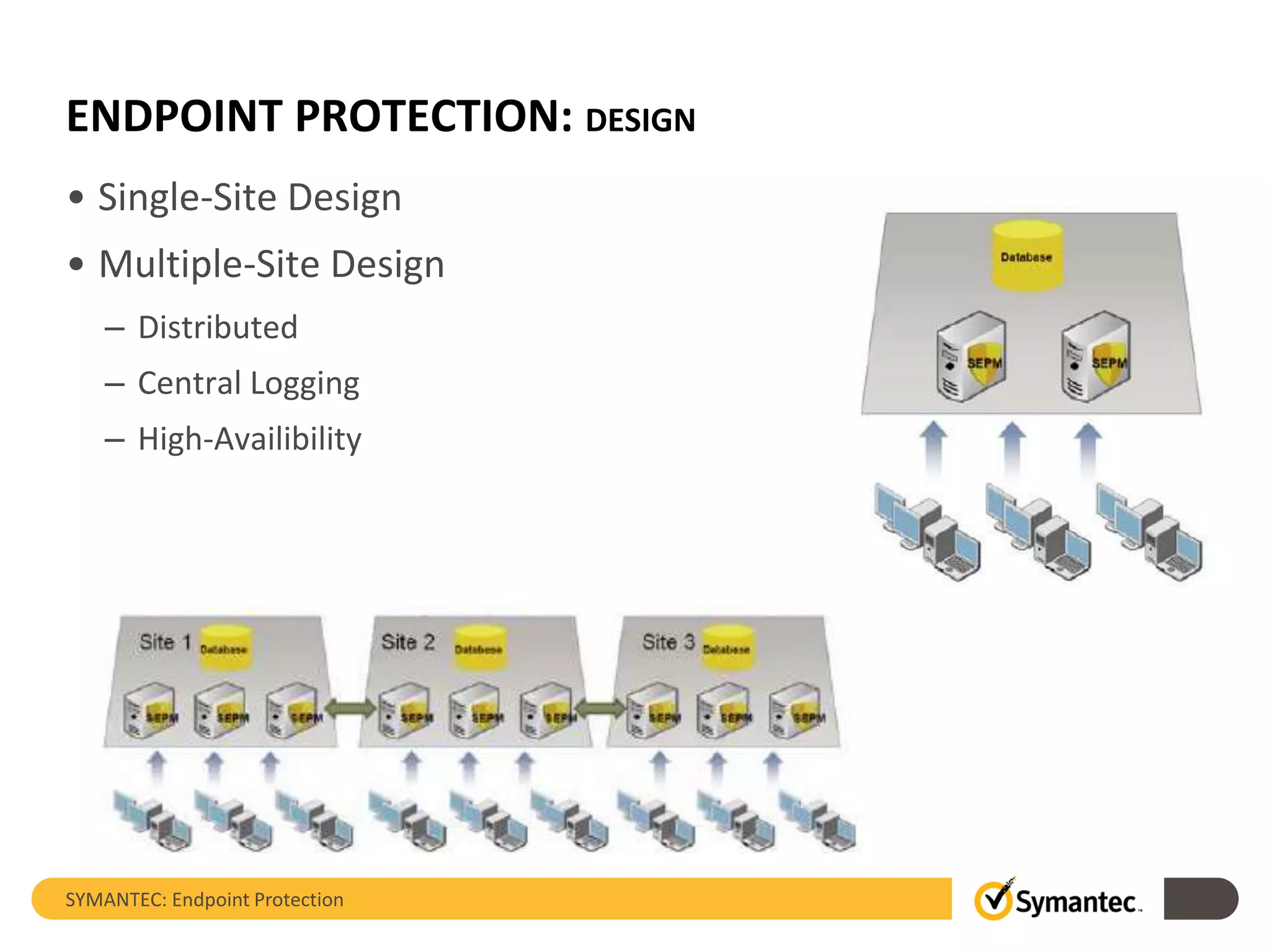
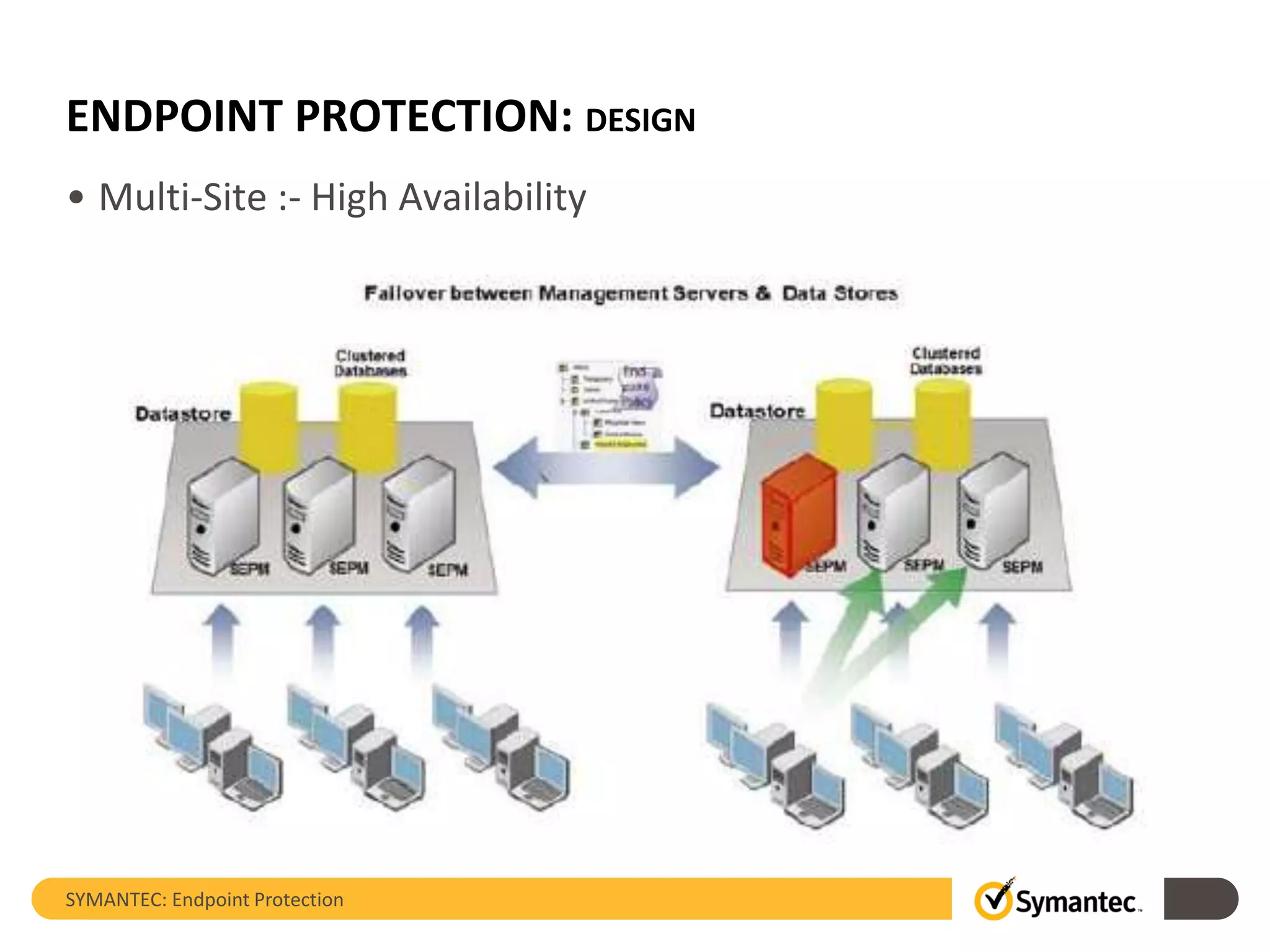
The document provides an overview of Symantec Endpoint Protection, detailing the company's history, solutions, and focus areas, including cybersecurity services against malware, cyber attacks, and identity theft. It outlines the product's features such as pre-execution threat detection, client management, and virtual infrastructure support, along with system requirements and licensing information. Symantec Endpoint Protection aims to safeguard physical and virtual systems, offering comprehensive solutions for enterprise security.