Target breach deck 2014 - Delivered to the World's Largest Retailer and Fourth Largest Website
•
2 likes•579 views
Anatomy of the World's Largest Retail Breach 2013-2014
Report
Share
Report
Share
Recommended
10 Types Of Cyber Attacks And How They Can Affect You- Detox technologies.pdf

10 Types Of Cyber Attacks And How They Can Affect You- Detox technologies.pdfCyber security professional services- Detox techno
Recommended
10 Types Of Cyber Attacks And How They Can Affect You- Detox technologies.pdf

10 Types Of Cyber Attacks And How They Can Affect You- Detox technologies.pdfCyber security professional services- Detox techno
More Related Content
What's hot
What's hot (20)
CryptoLocker and the Emergence of Ransomware Attacks

CryptoLocker and the Emergence of Ransomware Attacks
Detecting phishing websites using associative classification (2)

Detecting phishing websites using associative classification (2)
Jean pier talbot - web is the battlefield - atlseccon2011

Jean pier talbot - web is the battlefield - atlseccon2011
Cyber espionage nation state-apt_attacks_on_the_rise

Cyber espionage nation state-apt_attacks_on_the_rise
Knowledge base compound approach against phishing attacks using some parsing ...

Knowledge base compound approach against phishing attacks using some parsing ...
KNOWLEDGE BASE COMPOUND APPROACH AGAINST PHISHING ATTACKS USING SOME PARSING ...

KNOWLEDGE BASE COMPOUND APPROACH AGAINST PHISHING ATTACKS USING SOME PARSING ...
Viewers also liked
Viewers also liked (15)
Challenges Faced By Youth Aging Out of Foster Care

Challenges Faced By Youth Aging Out of Foster Care
مخطط التنمية للوكالة الوطنية لانعاش التشغيل و الكفاءات في أفق 2020

مخطط التنمية للوكالة الوطنية لانعاش التشغيل و الكفاءات في أفق 2020
Similar to Target breach deck 2014 - Delivered to the World's Largest Retailer and Fourth Largest Website
Similar to Target breach deck 2014 - Delivered to the World's Largest Retailer and Fourth Largest Website (20)
Phishing, Pharming, and the latest potholes on the Information Highway

Phishing, Pharming, and the latest potholes on the Information Highway
onlinesecurityandpaymentsystem-140116021418-phpapp01.pdf

onlinesecurityandpaymentsystem-140116021418-phpapp01.pdf
Seceon’s Comprehensive Cybersecurity Platform - Seceon.pptx

Seceon’s Comprehensive Cybersecurity Platform - Seceon.pptx
SplunkLive! London - Scoping Infections and Disrupting Breaches breakout

SplunkLive! London - Scoping Infections and Disrupting Breaches breakout
Recently uploaded
Recently uploaded (20)
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Human Factors of XR: Using Human Factors to Design XR Systems

Human Factors of XR: Using Human Factors to Design XR Systems
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...

Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
Vulnerability_Management_GRC_by Sohang Sengupta.pptx

Vulnerability_Management_GRC_by Sohang Sengupta.pptx
Enhancing Worker Digital Experience: A Hands-on Workshop for Partners

Enhancing Worker Digital Experience: A Hands-on Workshop for Partners
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...

Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...
Hyderabad Call Girls Khairatabad ✨ 7001305949 ✨ Cheap Price Your Budget

Hyderabad Call Girls Khairatabad ✨ 7001305949 ✨ Cheap Price Your Budget
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
Target breach deck 2014 - Delivered to the World's Largest Retailer and Fourth Largest Website
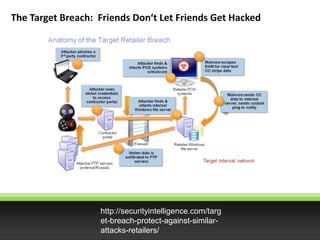
- 1. The Target Breach: Friends Don‘t Let Friends Get Hacked http://securityintelligence.com/targ et-breach-protect-against-similar- attacks-retailers/
- 2. November December Breach High-Level Access to Vendor Purchasing Portal Data Exfiltration to Remote Site Credentials Lifted Planting of POS Malware Remote Downloading HVAC Vendor Phished
- 3. One or more recipients clicks link(s) and/or downloads file Research Study social media: Facebook, LinkedIn, Instagram, Twitter Phishing Malware/Exploit Craft targeted email with malware on website link. Send to target(s). Anatomy of Phishing and Credential Theft
- 4. Compromise Network Exploit Portal Easily found Vendor Portals for National Labs VPN Network Breach Remote Access with Multi- Factor Vendor Portal Vendor Portal
- 5. Sample Memory Search Commodity Malware Malware Commonly Available on Internet Customizable Search Memory Black POS Plant Malware
- 6. Criminals Retreive from External Servers Package Data to Internal Server Copy to Internal Windows Server Drop on External Server Retreive from External Server Job Transfers Compressed Card Data on Schedule Exfiltrate Data
- 7. November HVAC Vendor Phished Access to Vendor Purchasing Portal Data Exfiltration to Remote Site Credentials Lifted Planting of POS Malware Remote Downloading December What can be done to Stop this? Block Malware Educate Vendors VPN Token Protect Systems Third Party Monitoring Block Egress
