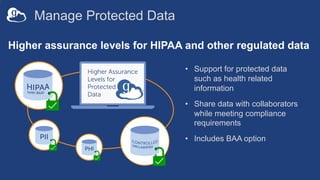
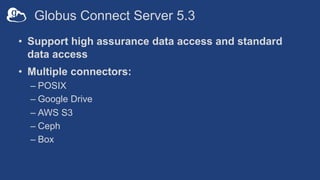
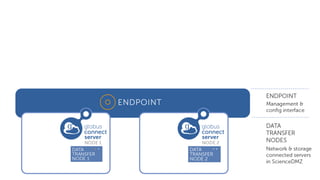
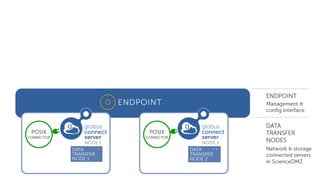
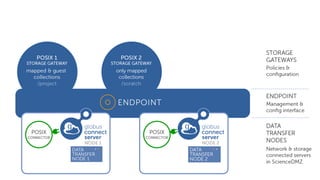
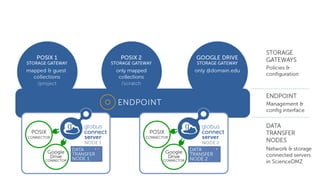
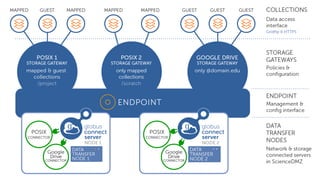
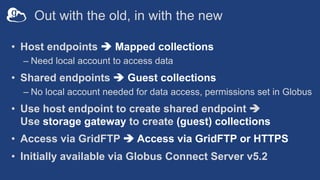
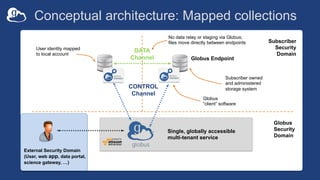
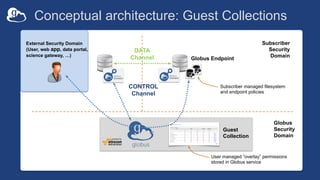
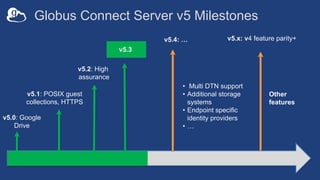
The document outlines the management of protected data using Globus Connect Server v5, emphasizing compliance with regulations such as HIPAA for health-related information. It discusses features like Business Associate Agreements, high assurance data access, and security protocols for data handling, while detailing the integration of various storage connectors. The document also describes user authentication flows, permission management, and highlights future advancements in data security and service functionalities.





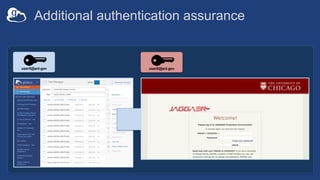



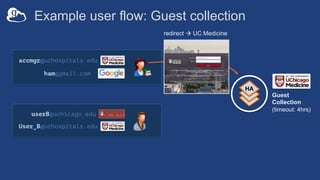
![Example user flow: Guest collection
HA
userA@uchicago.edu
User_A@uchospitals.edu
g.user@gmail.com
accmgr@uchospitals.edu
ham@gmail.com
Guest
Collection
(timeout: 4hrs)
[Role:Access Manager]
grants:Read](https://image.slidesharecdn.com/tut03gw19globushighassurance-190516135252/85/Tutorial-Managing-Protected-Data-with-Globus-Connect-Server-v5-26-320.jpg)
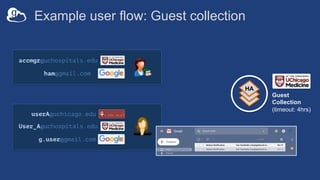


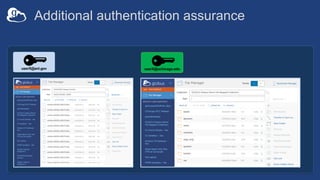
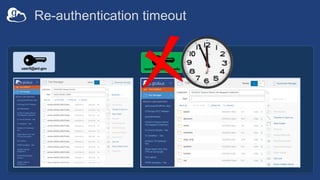
![Example user flow: Guest collection
HA
userA@uchicago.edu
User_A@uchospitals.edu
g.user@gmail.com
accmgr@uchospitals.edu
ham@gmail.com
[Permission:Read]
Guest
Collection
(timeout: 4hrs)](https://image.slidesharecdn.com/tut03gw19globushighassurance-190516135252/85/Tutorial-Managing-Protected-Data-with-Globus-Connect-Server-v5-30-320.jpg)









