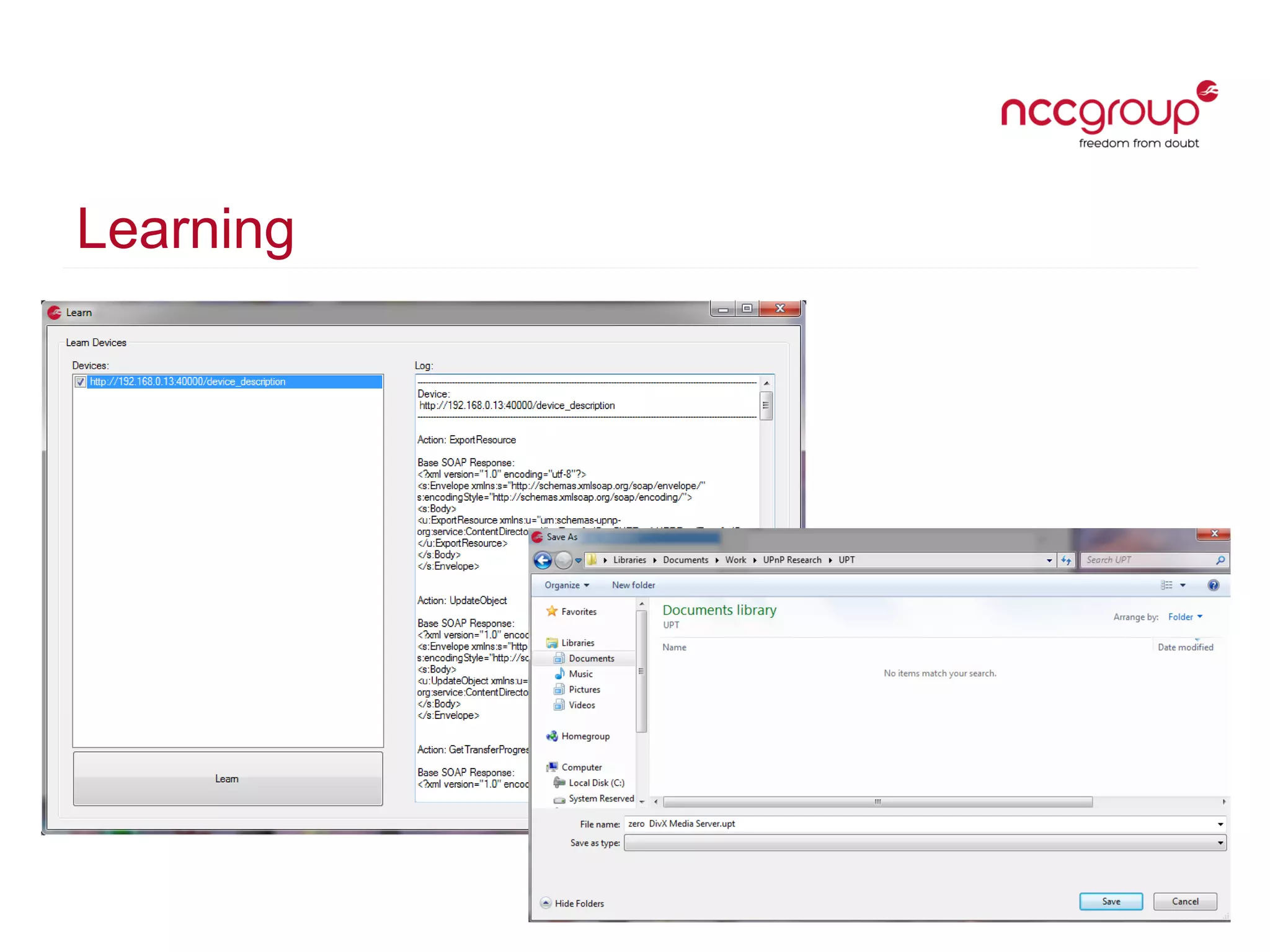
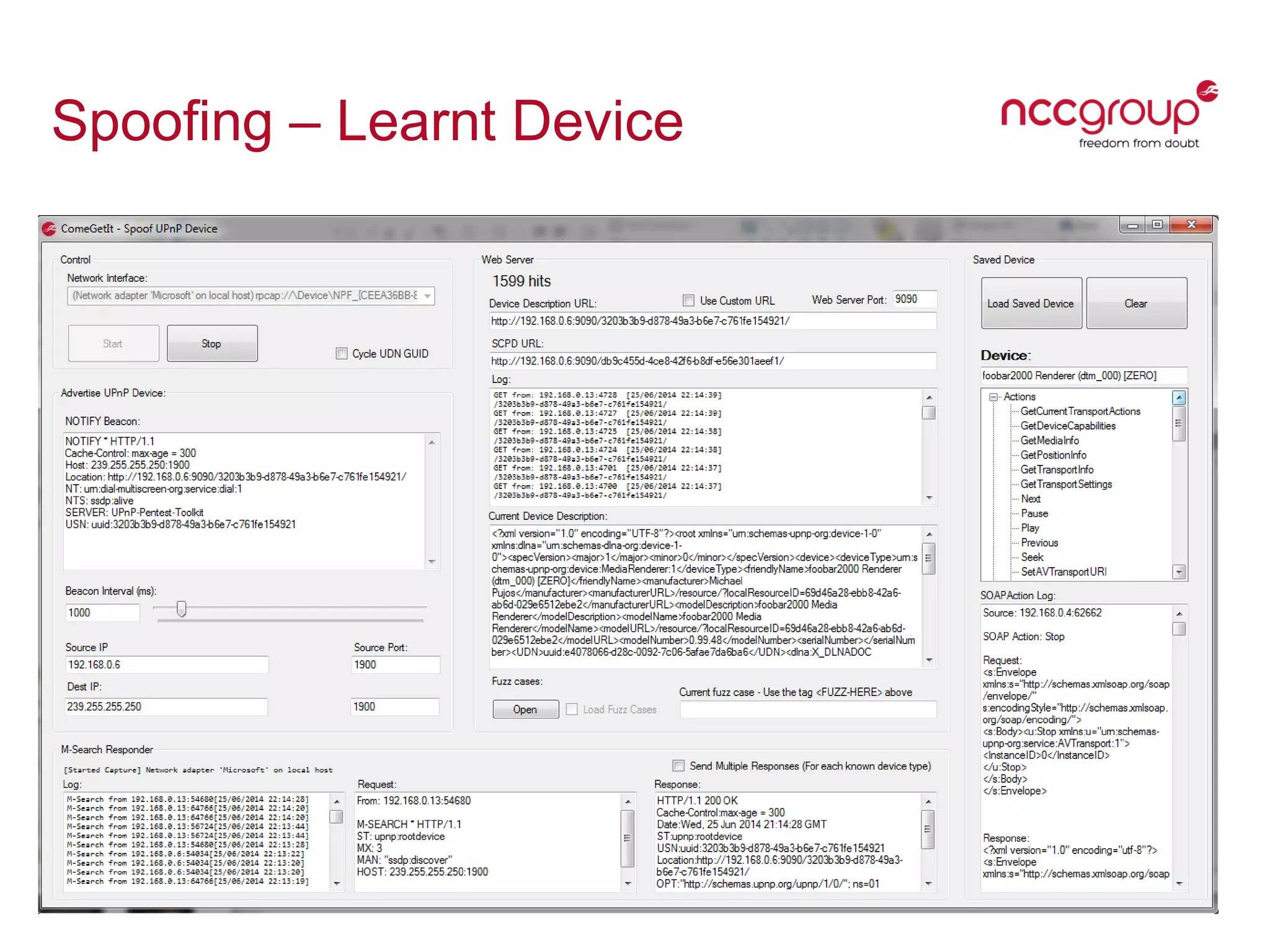
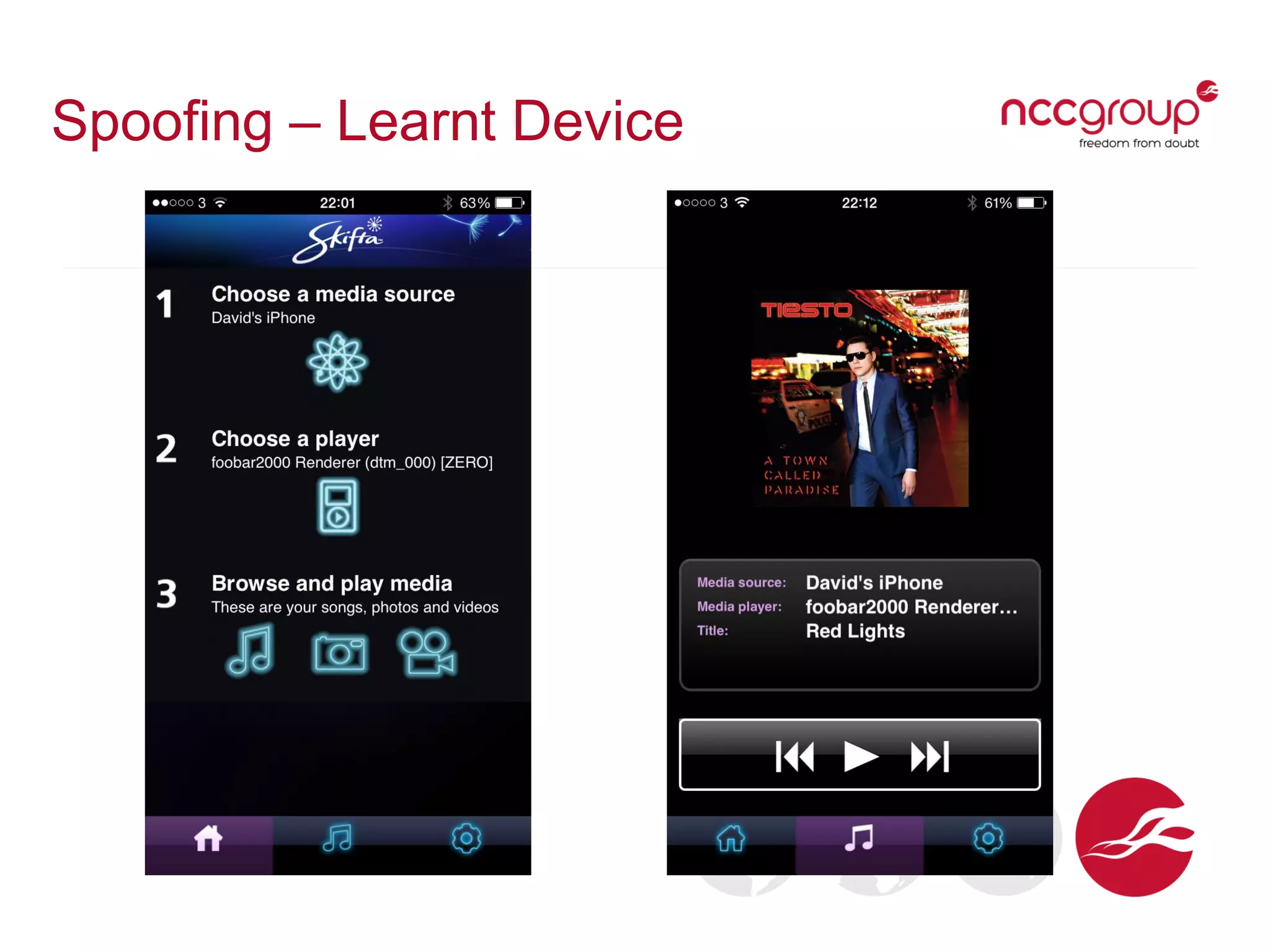
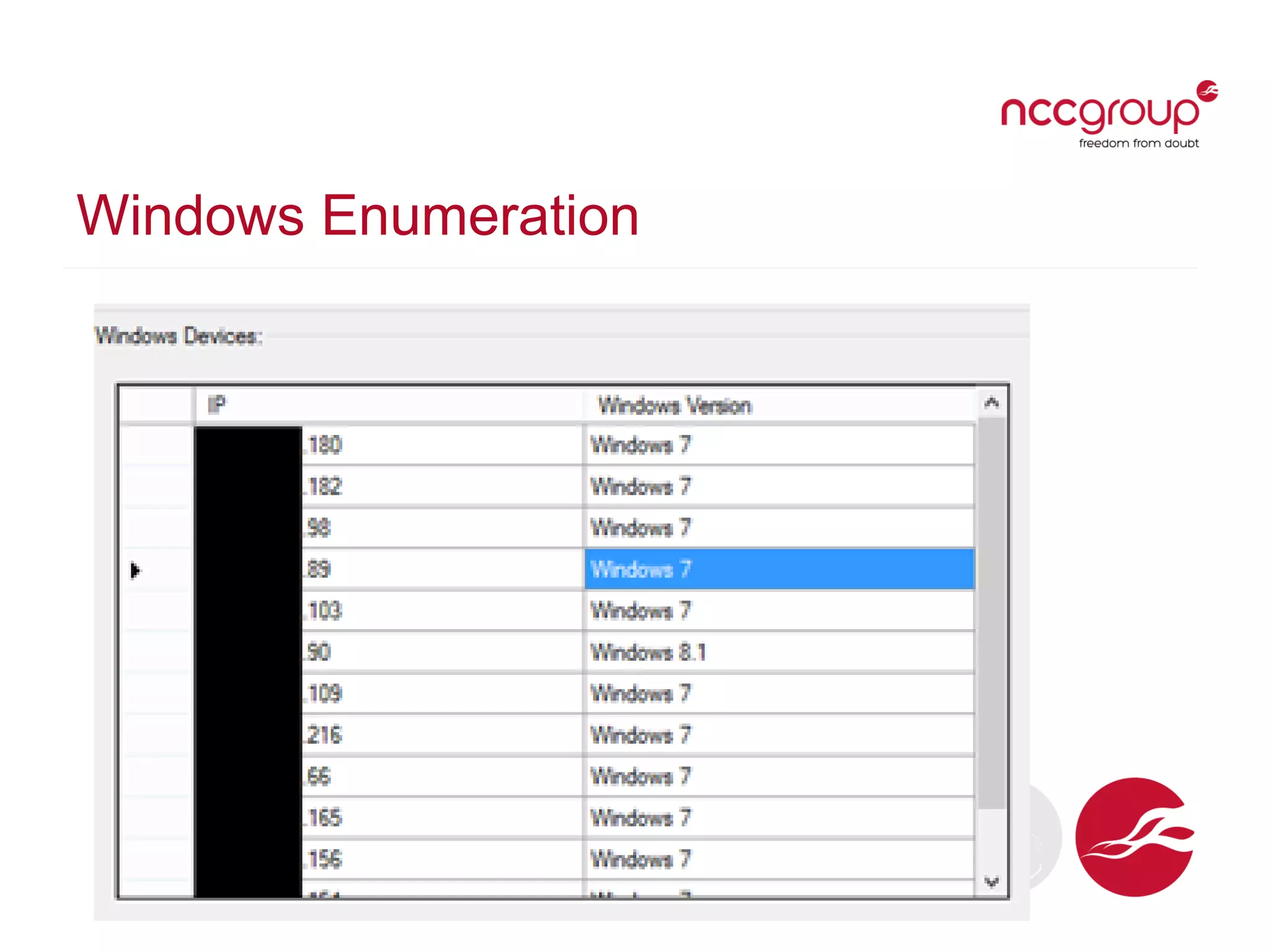
The document presents a talk by David Middlehurst on the security implications of Universal Plug and Play (UPnP) technologies, highlighting common vulnerabilities and the introduction of a new UPnP Pentest Toolkit. It outlines the mechanisms of UPnP device discovery and discusses flaws related to authorization and external traffic that can lead to security risks such as Denial of Service (DoS). The conclusion emphasizes the need for security assessments of UPnP implementations and the toolkit's potential in facilitating such evaluations.




















![Where are we heading?
“UPnP+ will expand beyond the group's
traditional work on devices using Internet
Protocol on WiFi LANs to create bridges to
wide-area networks and non-IP devices.”
"Today there's not a good standard for
accessing devices across any network, but
UPnP [Forum] is working on it," said Alan
Messer, a Samsung researcher in San Jose
who is vice president of UPnP [Forum].
From: http://www.eetindia.co.in/ART_8800698124_1800001_NT_8dd16112.HTM](https://image.slidesharecdn.com/uplugweplay-nedsummitcork13-11-14public-141116121600-conversion-gate01/75/U-Plug-We-Play-NED-Summit-Cork-Ireland-31-2048.jpg)