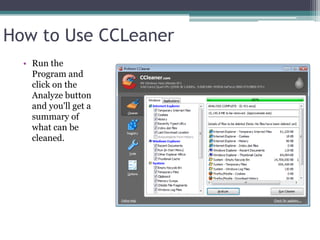
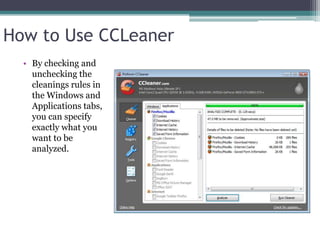
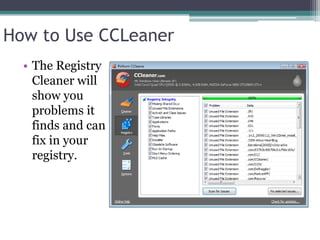
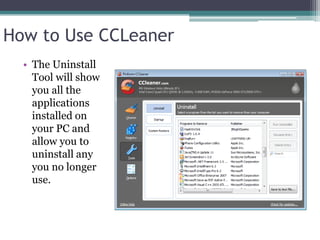
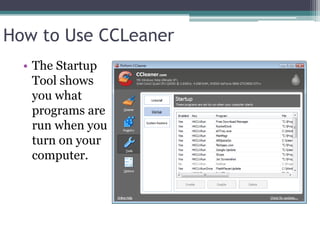
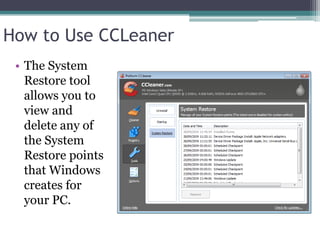
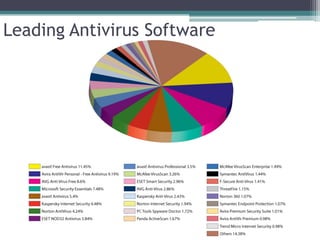
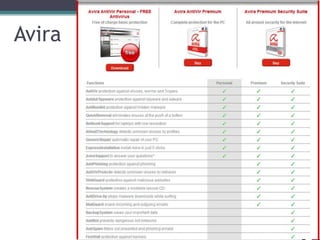
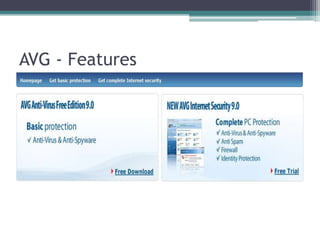
This document provides information on different types of free and open source software, including open source, shareware, and freeware. Open source software has open licensing that allows free distribution and modification of the source code. Shareware is proprietary trial software that has limited functionality and stops working after a trial period without payment. Freeware is fully functional software that can be used indefinitely without cost but may have some usage restrictions. Examples of each type are also provided.