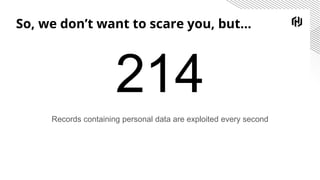
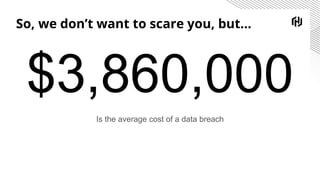
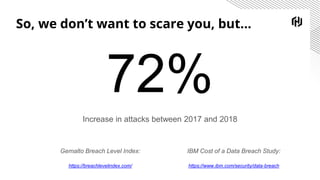
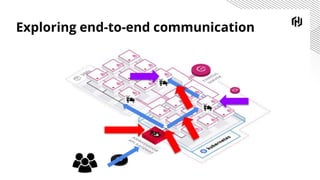
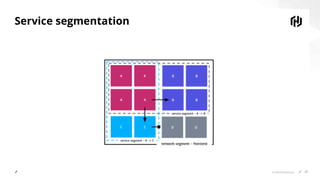
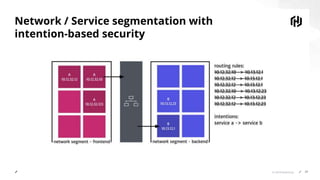
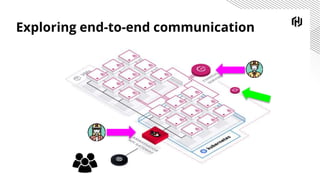
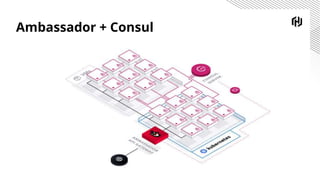
The document discusses the increasing importance of securing cloud-native communications amid application modernization and hybrid platforms, emphasizing the need for decoupling apps and infrastructure securely. It highlights critical security practices such as defense in depth, network segmentation, and service mesh usage to protect data in motion. Key statistics on data breaches underline the urgency of these security measures for organizations.