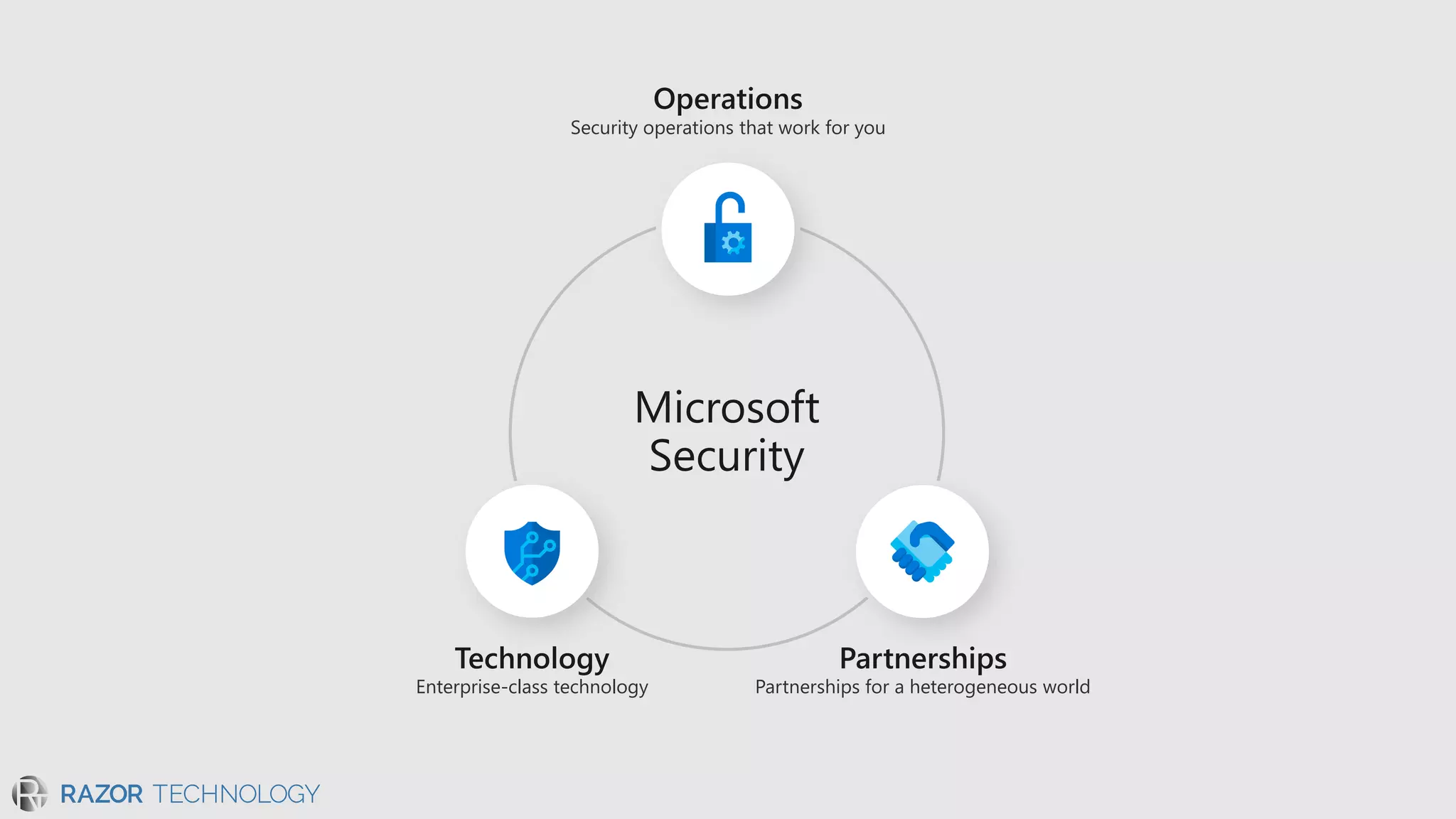
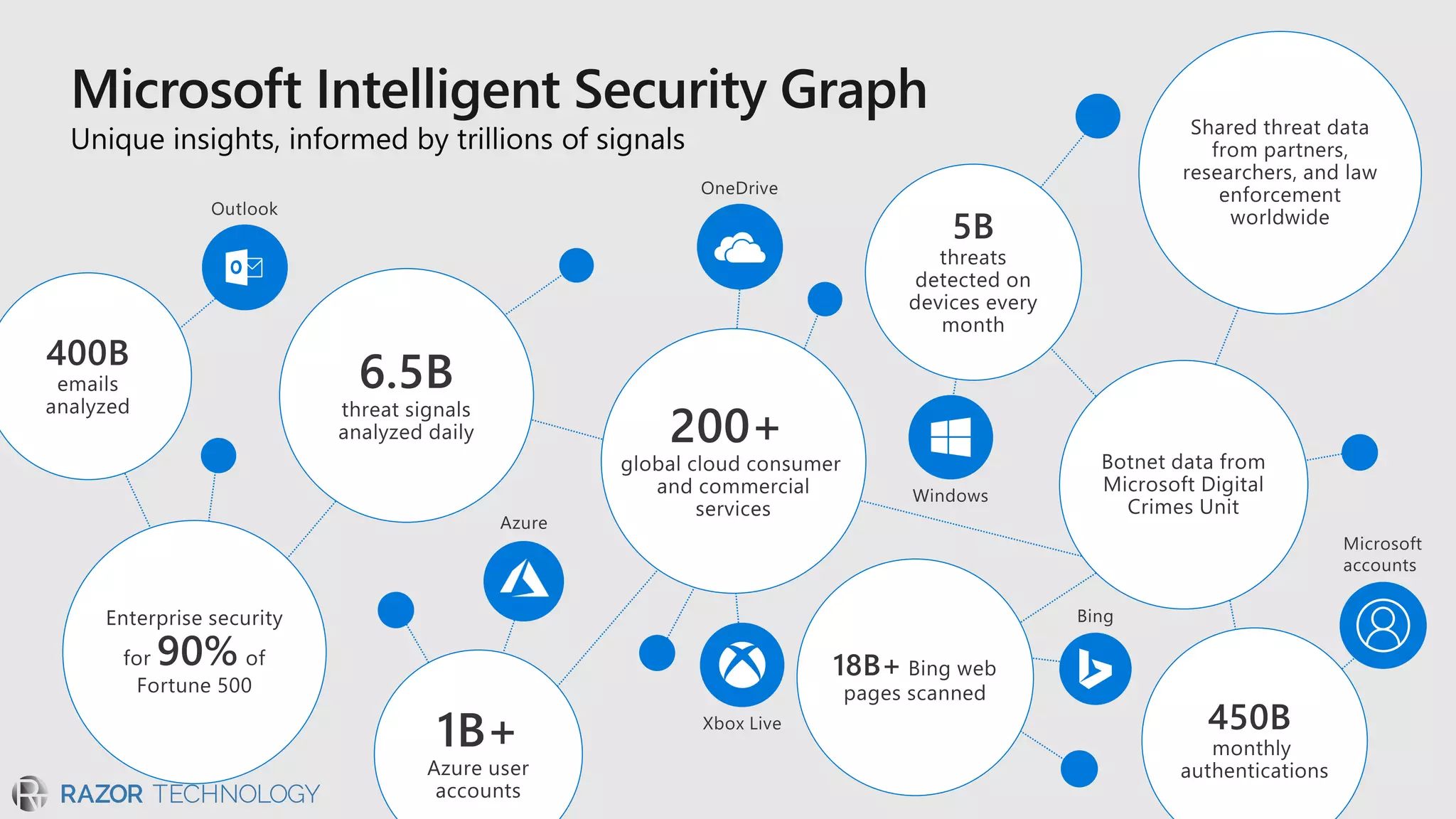
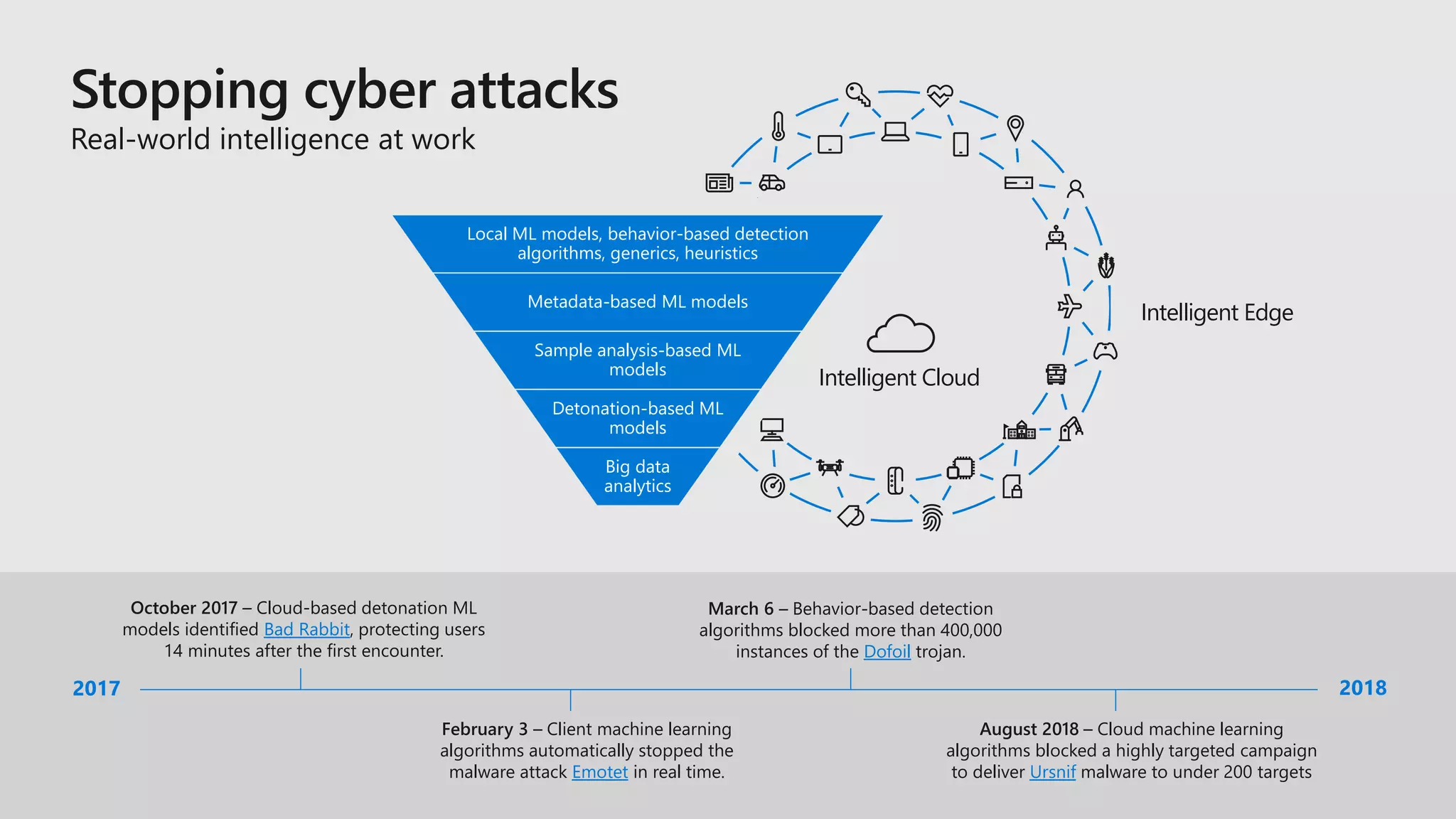
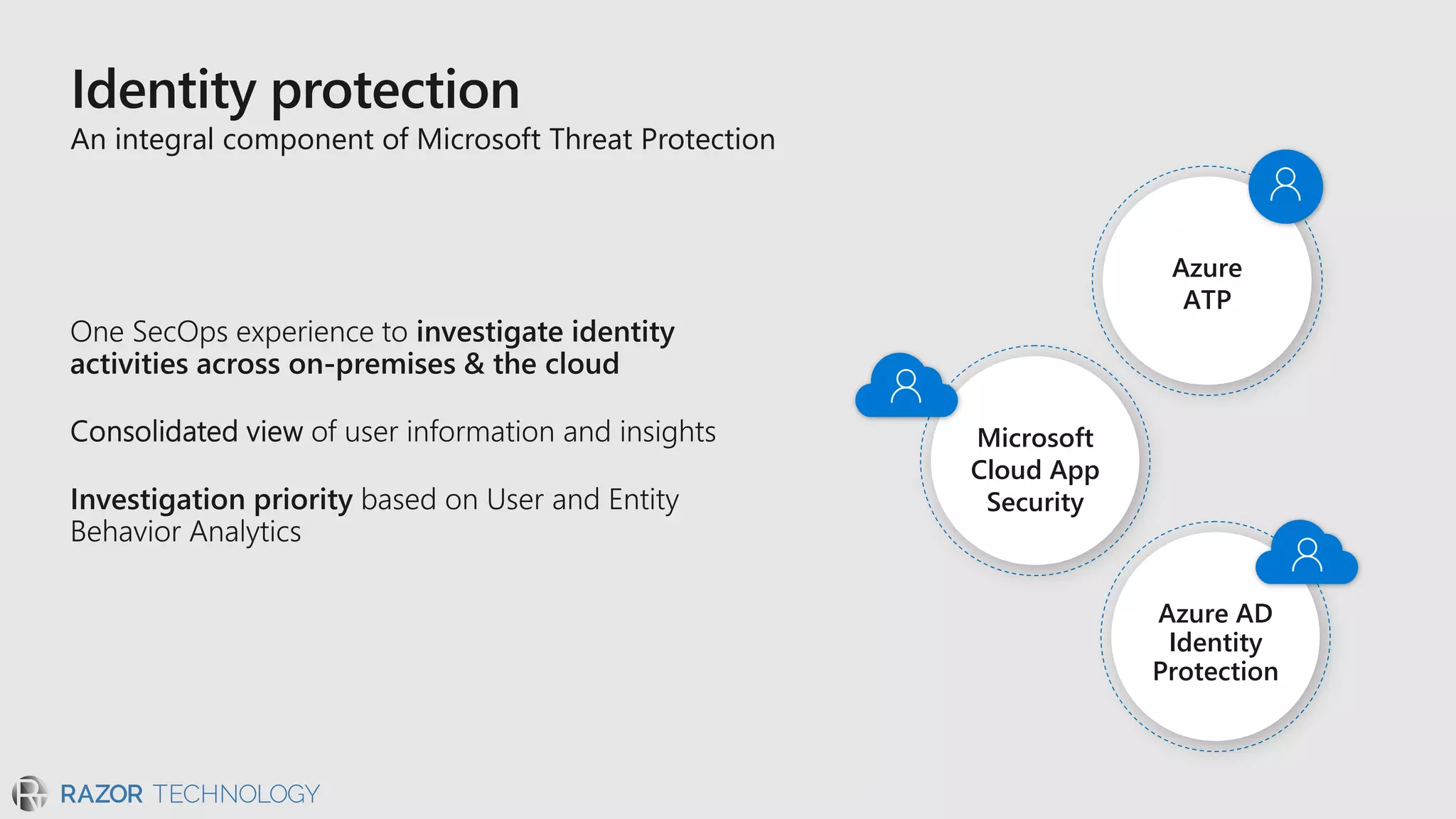
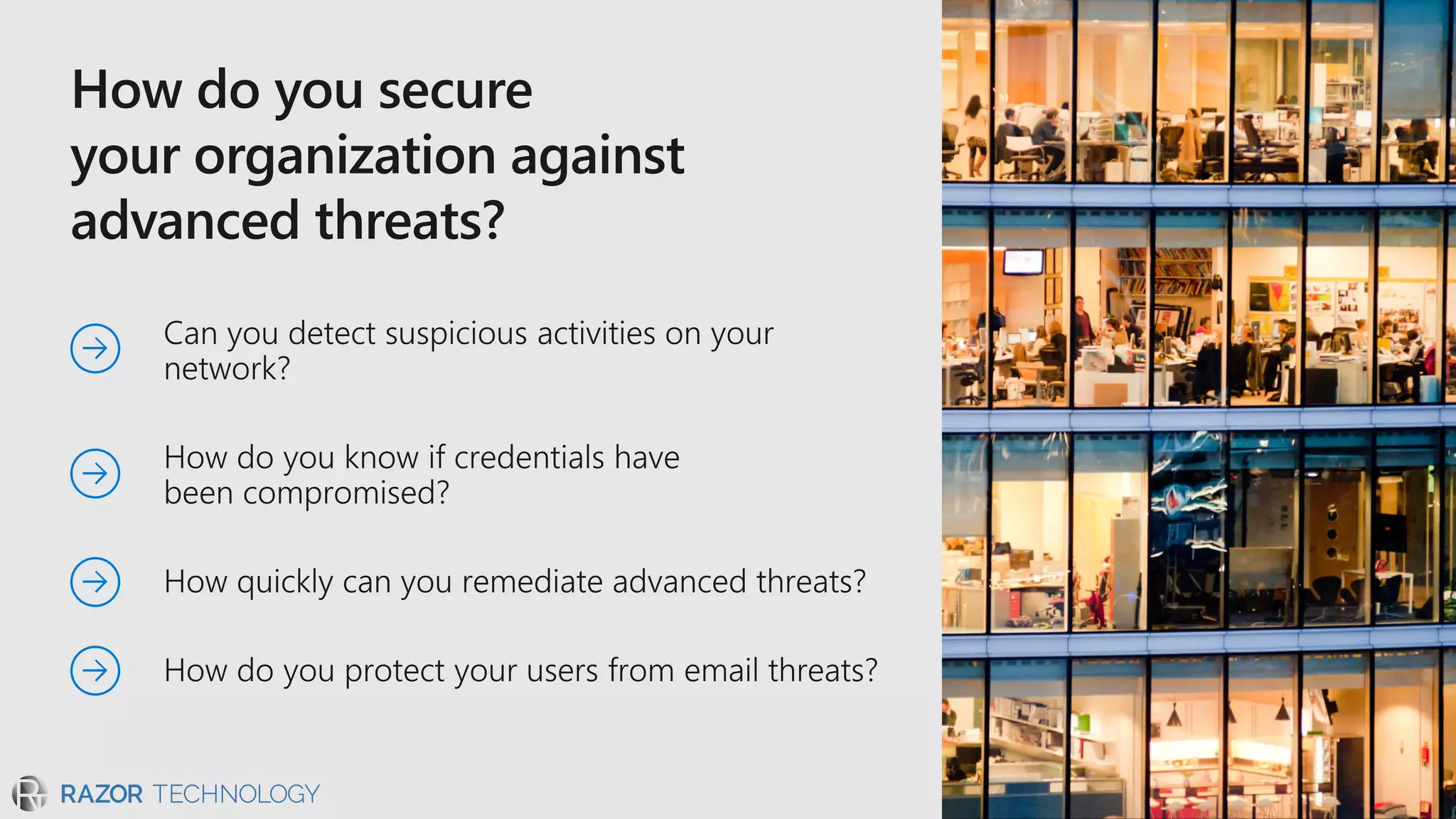
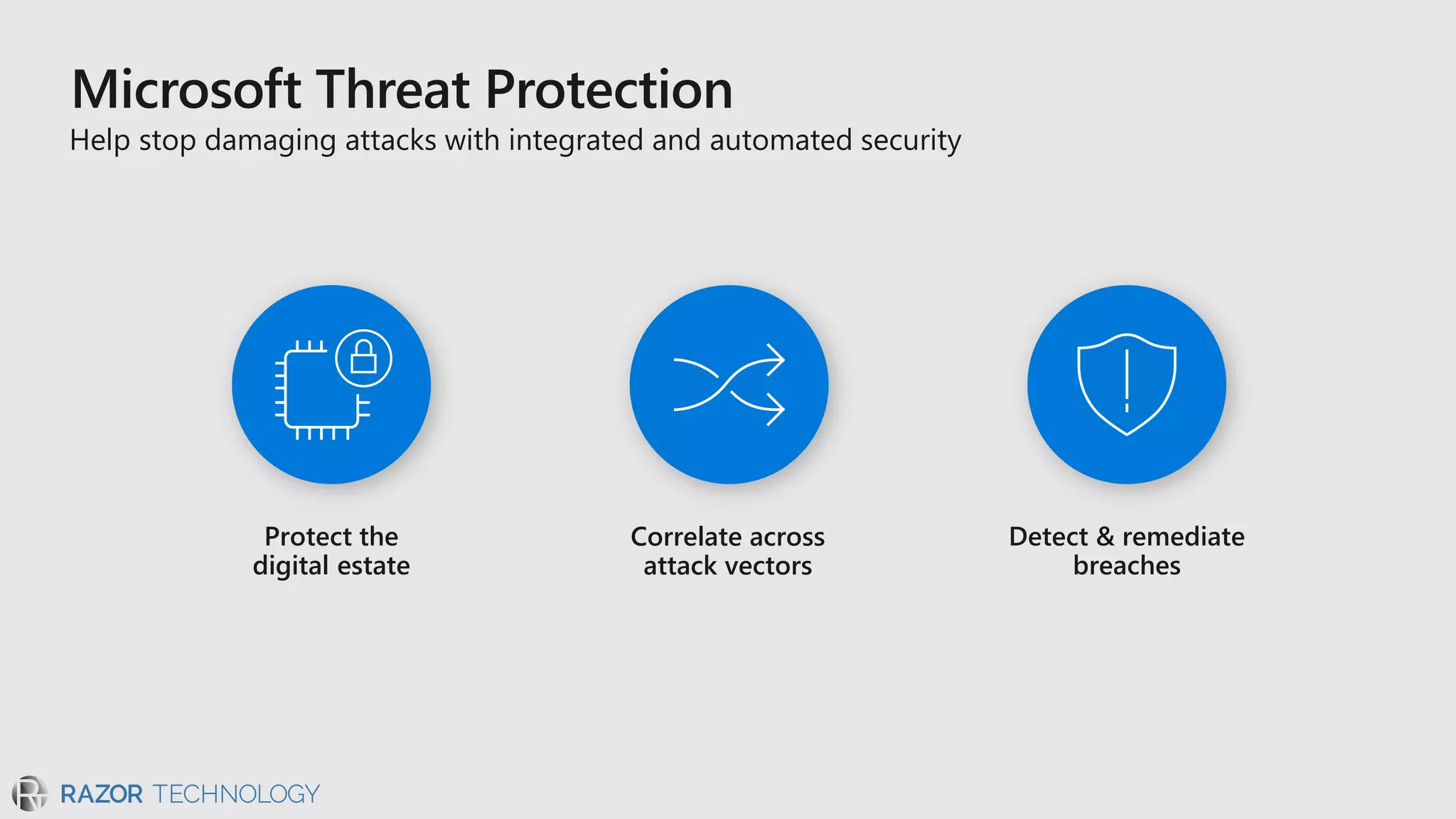
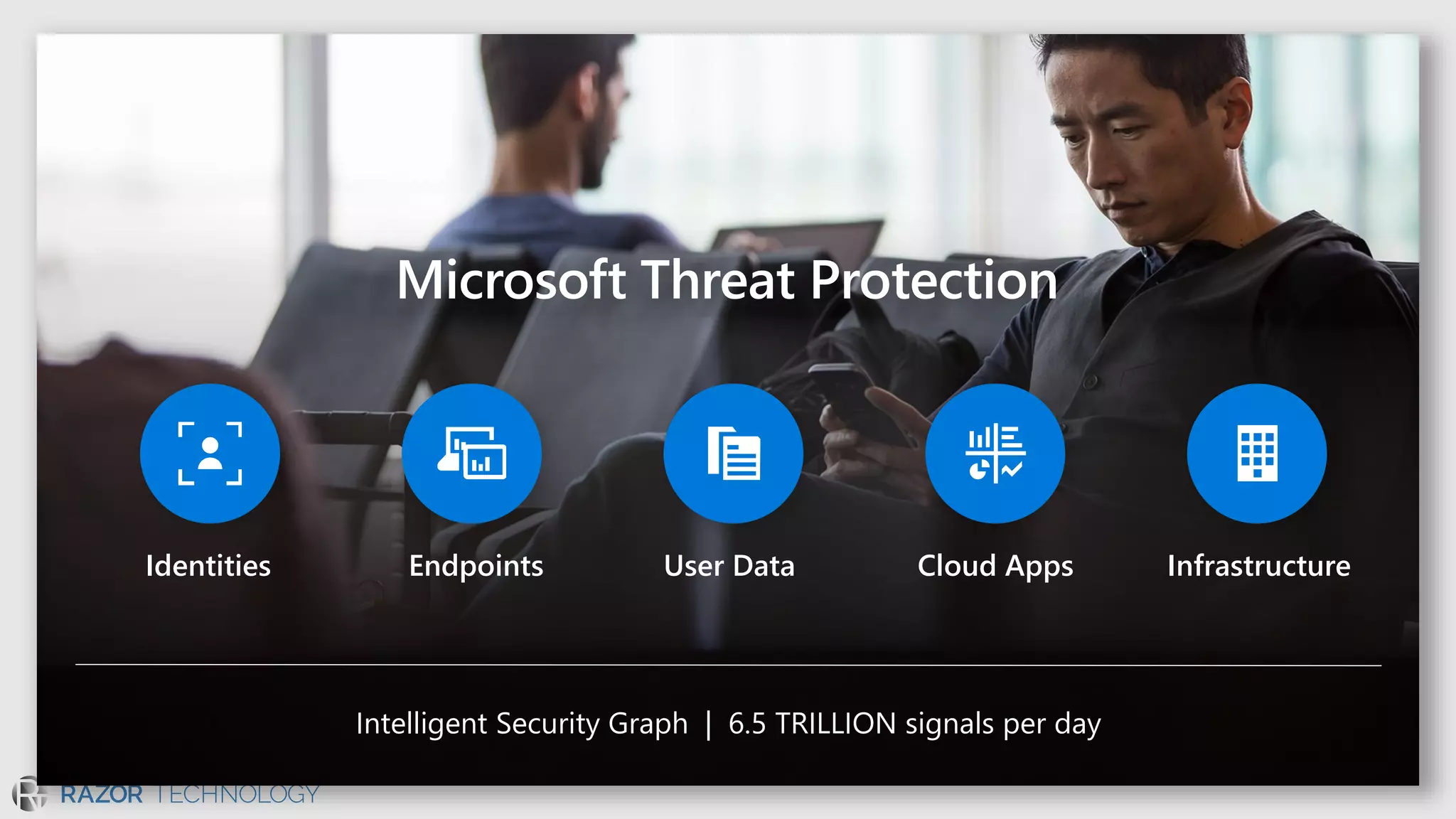
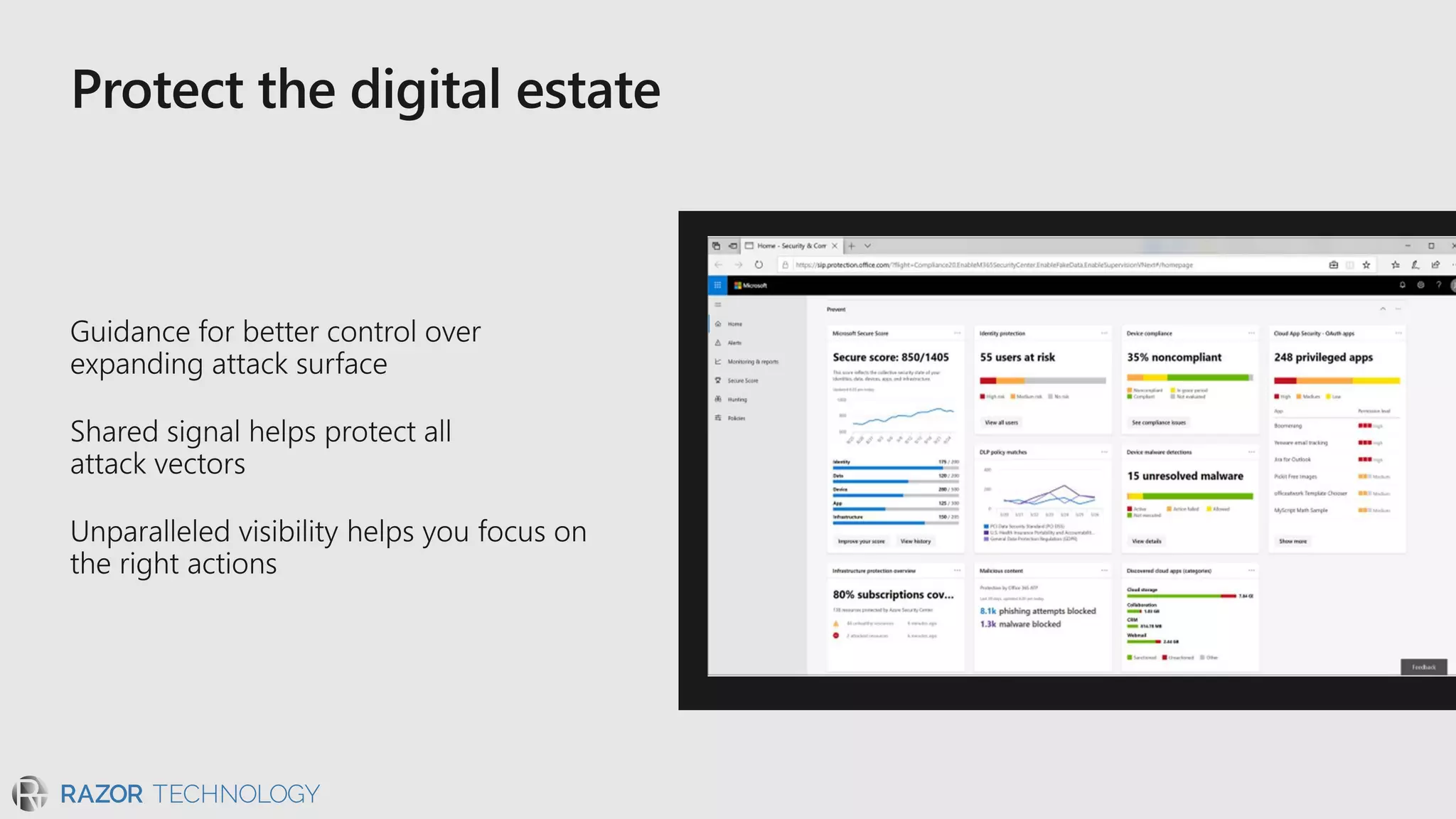
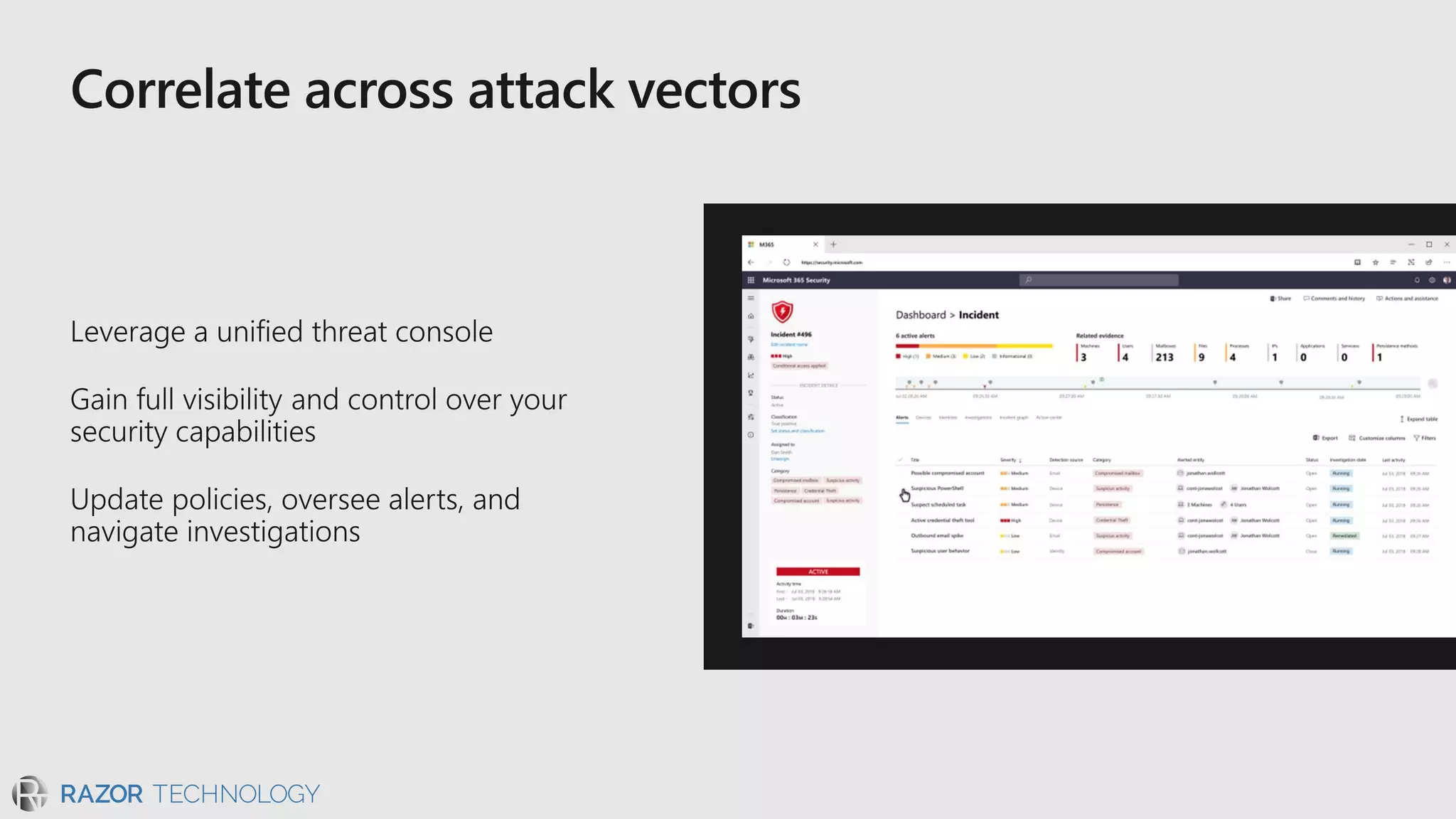
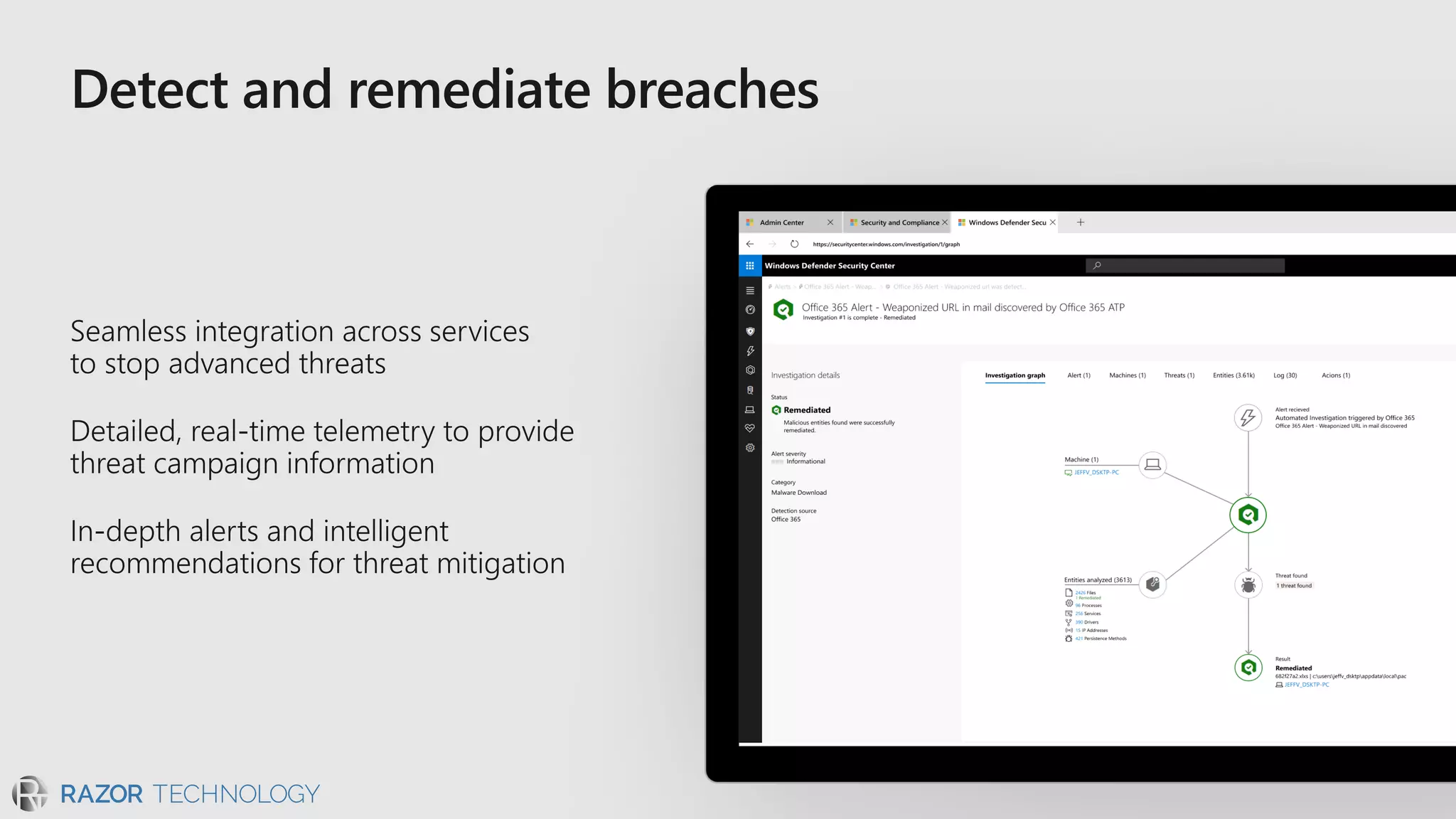
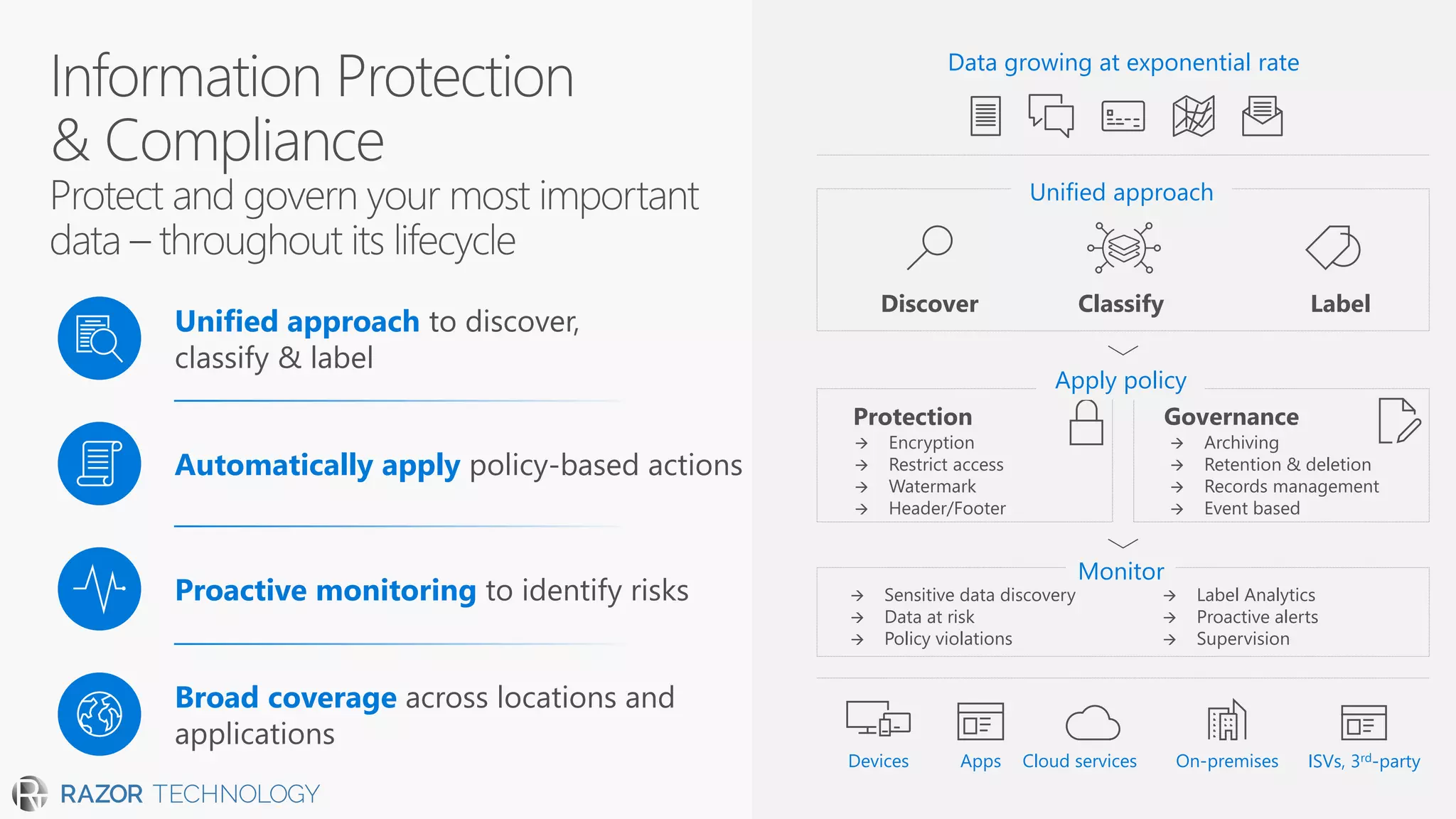
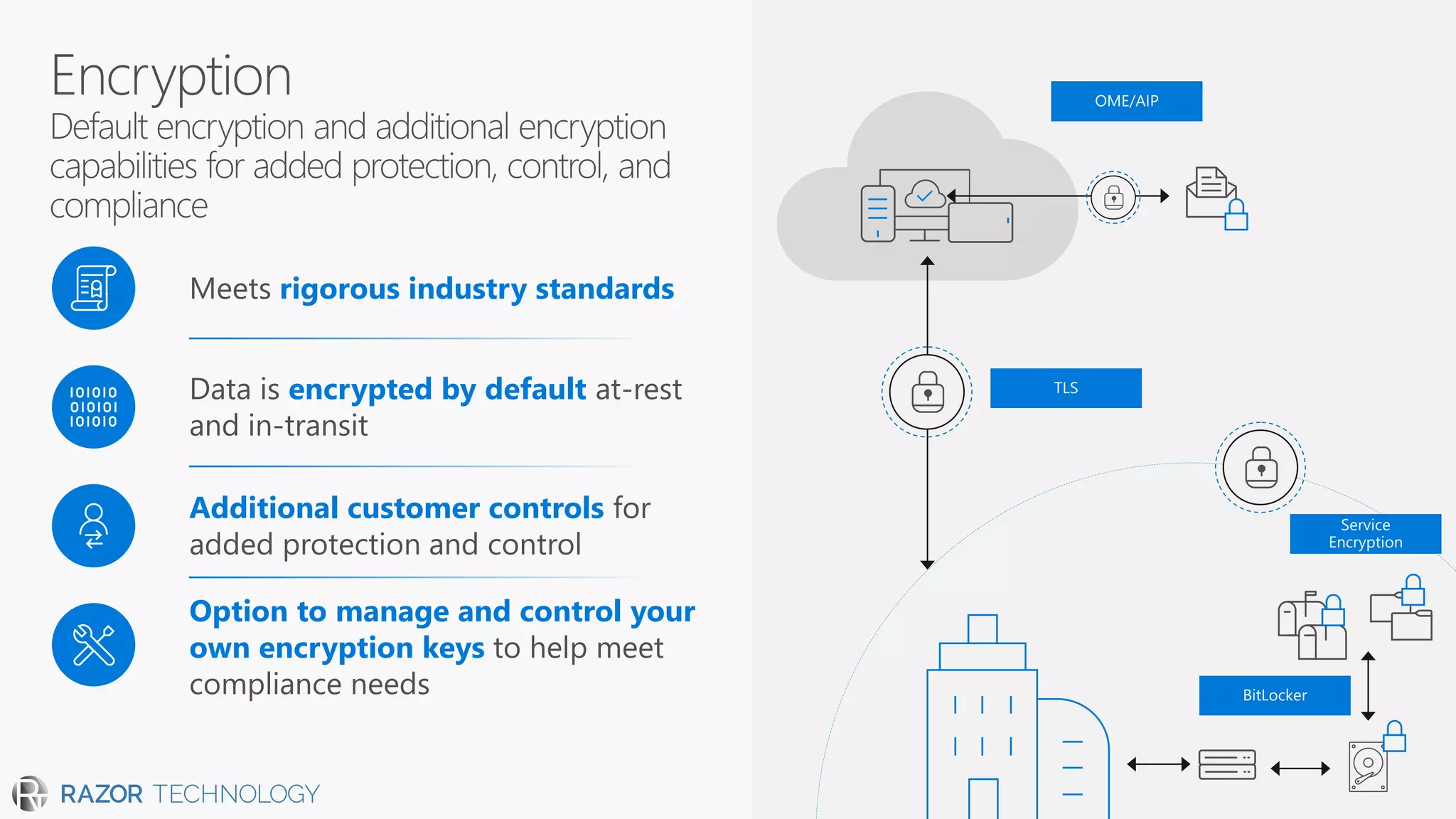
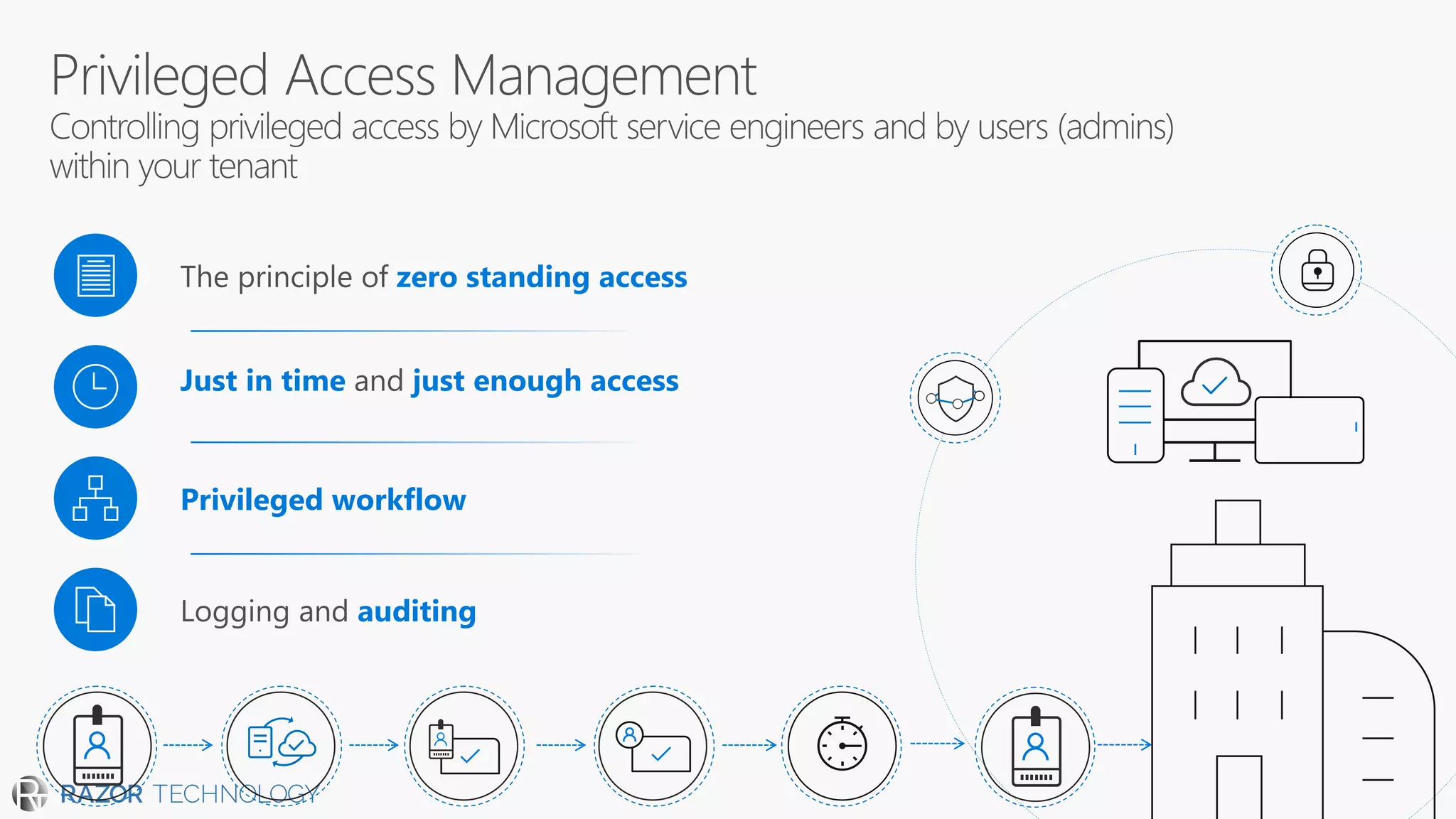
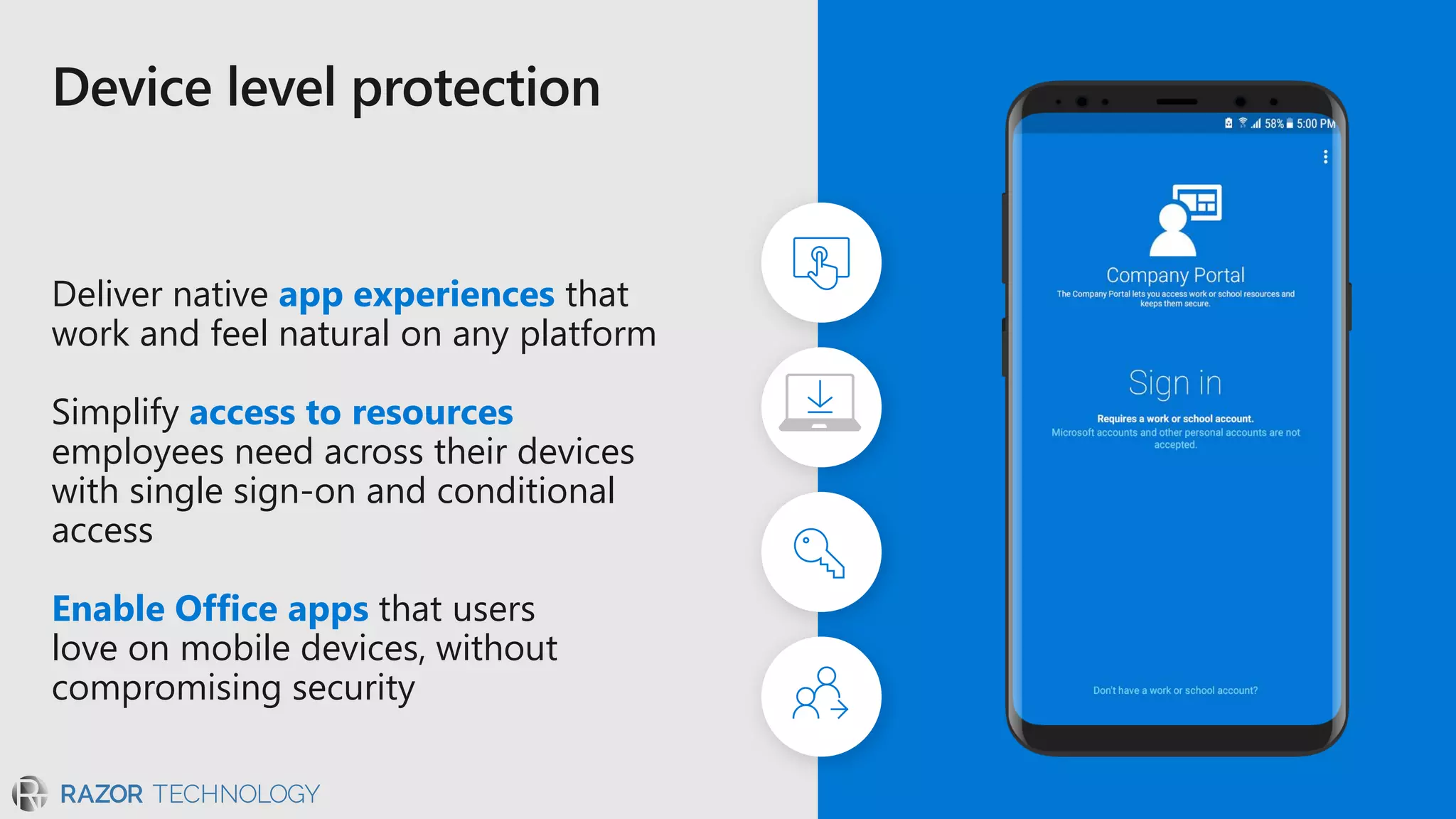
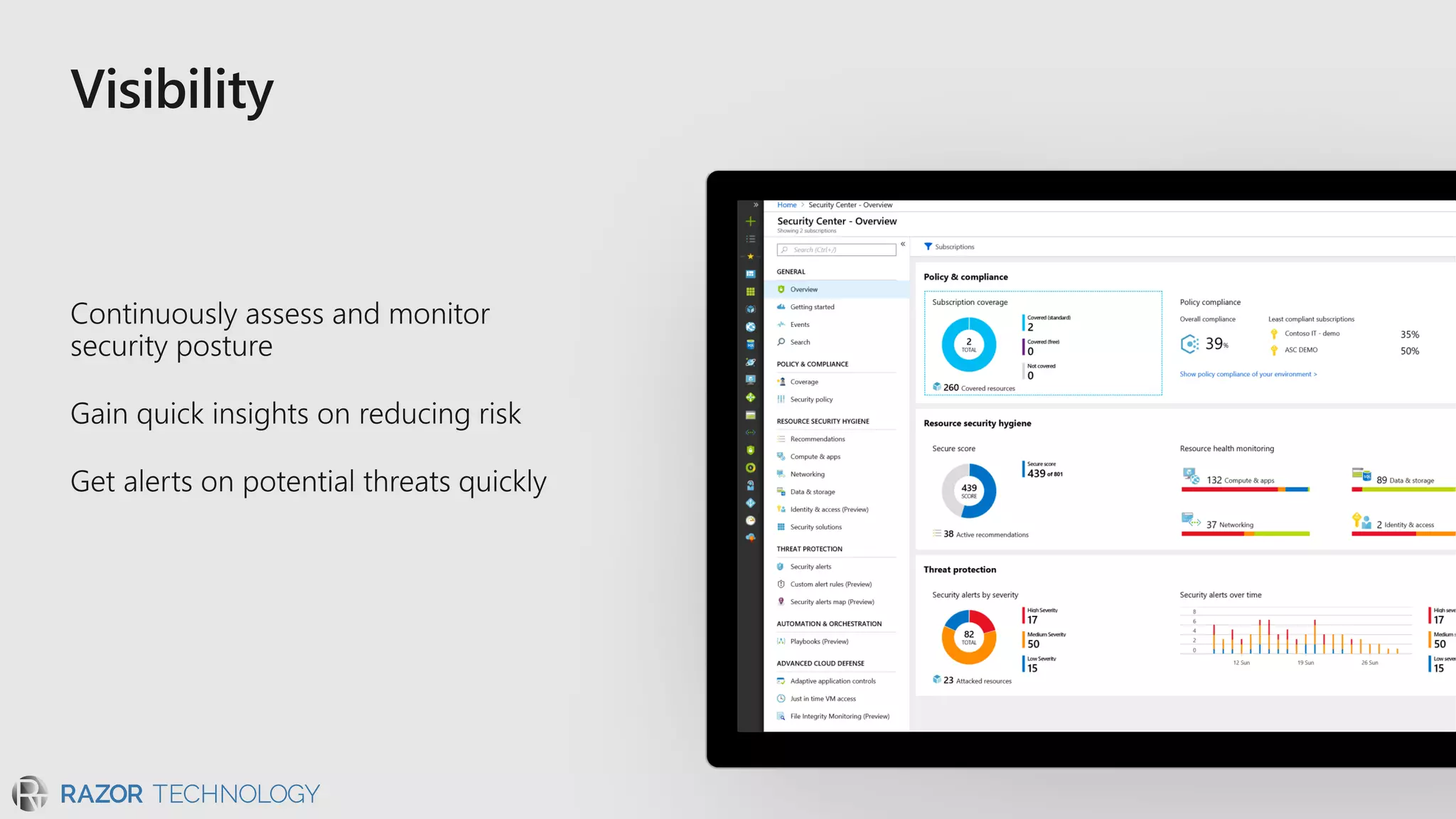
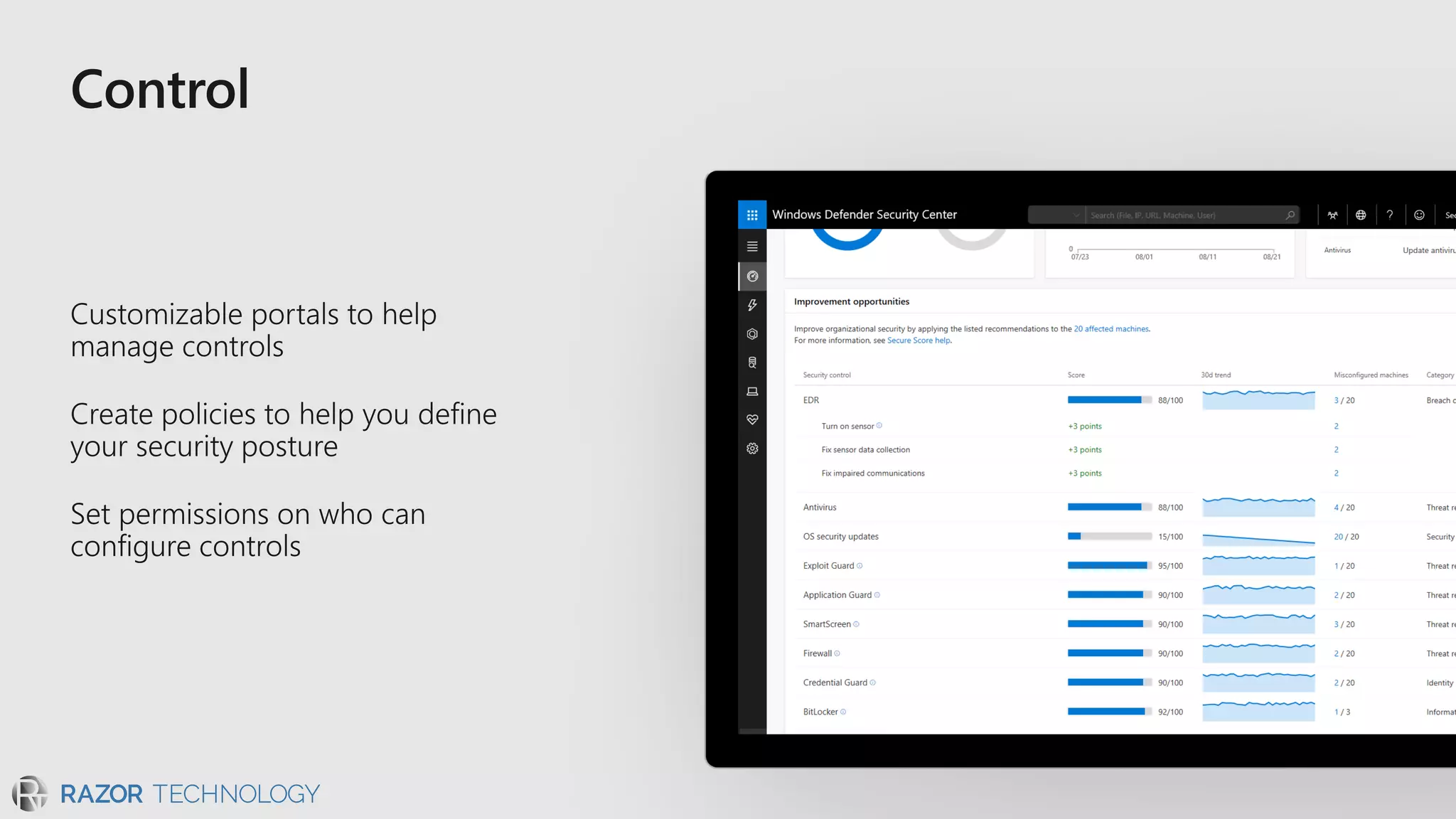
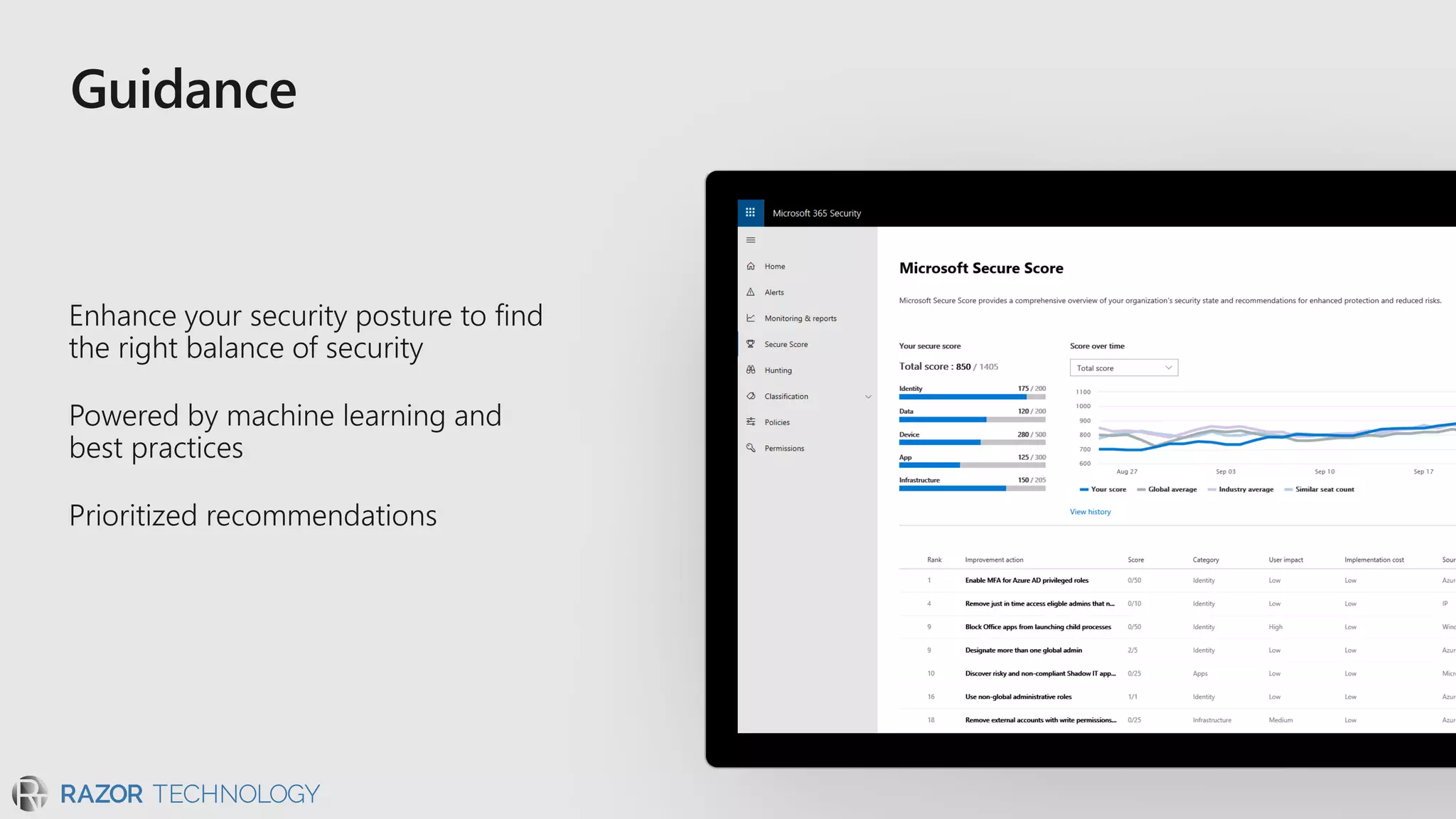
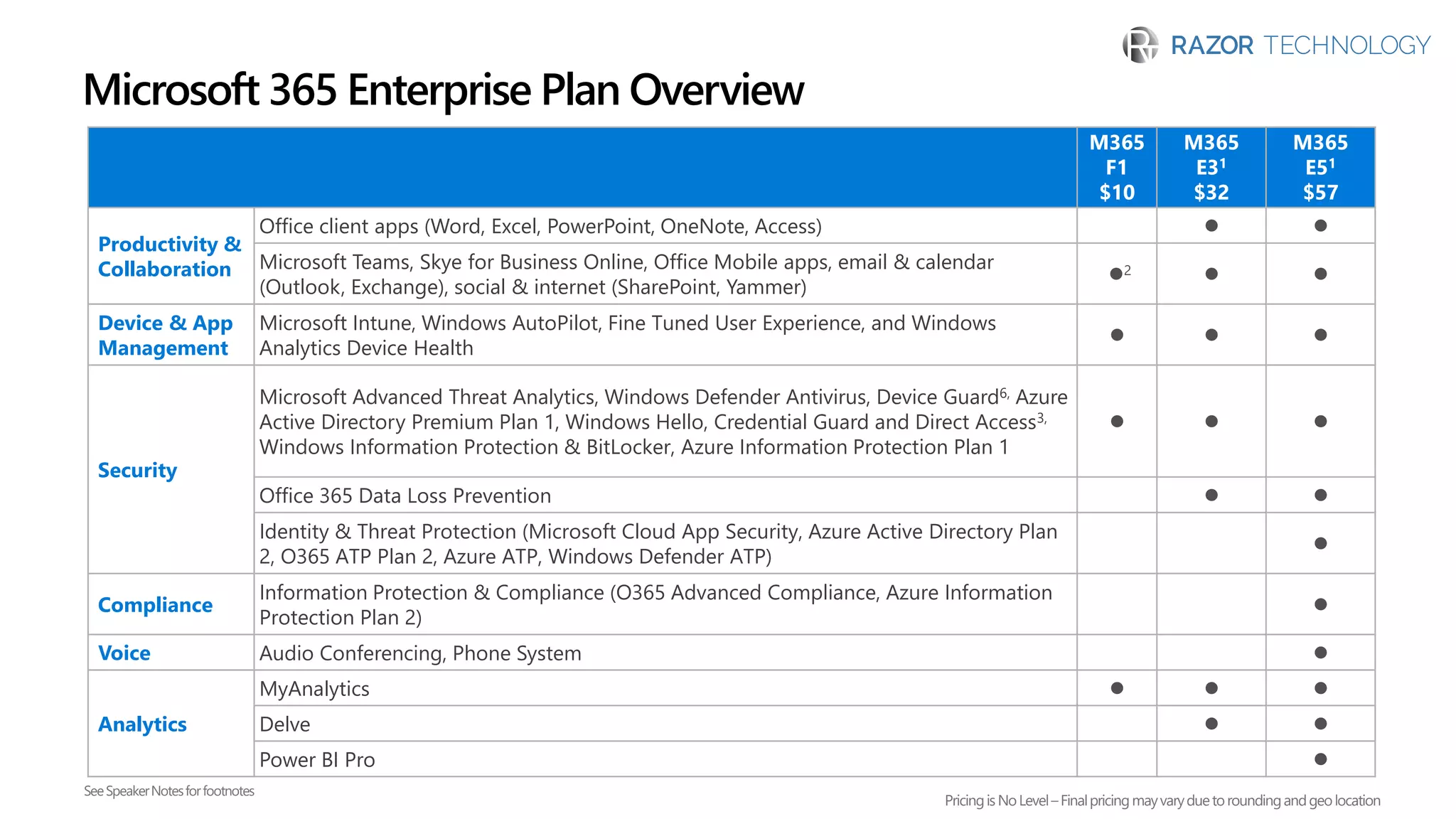
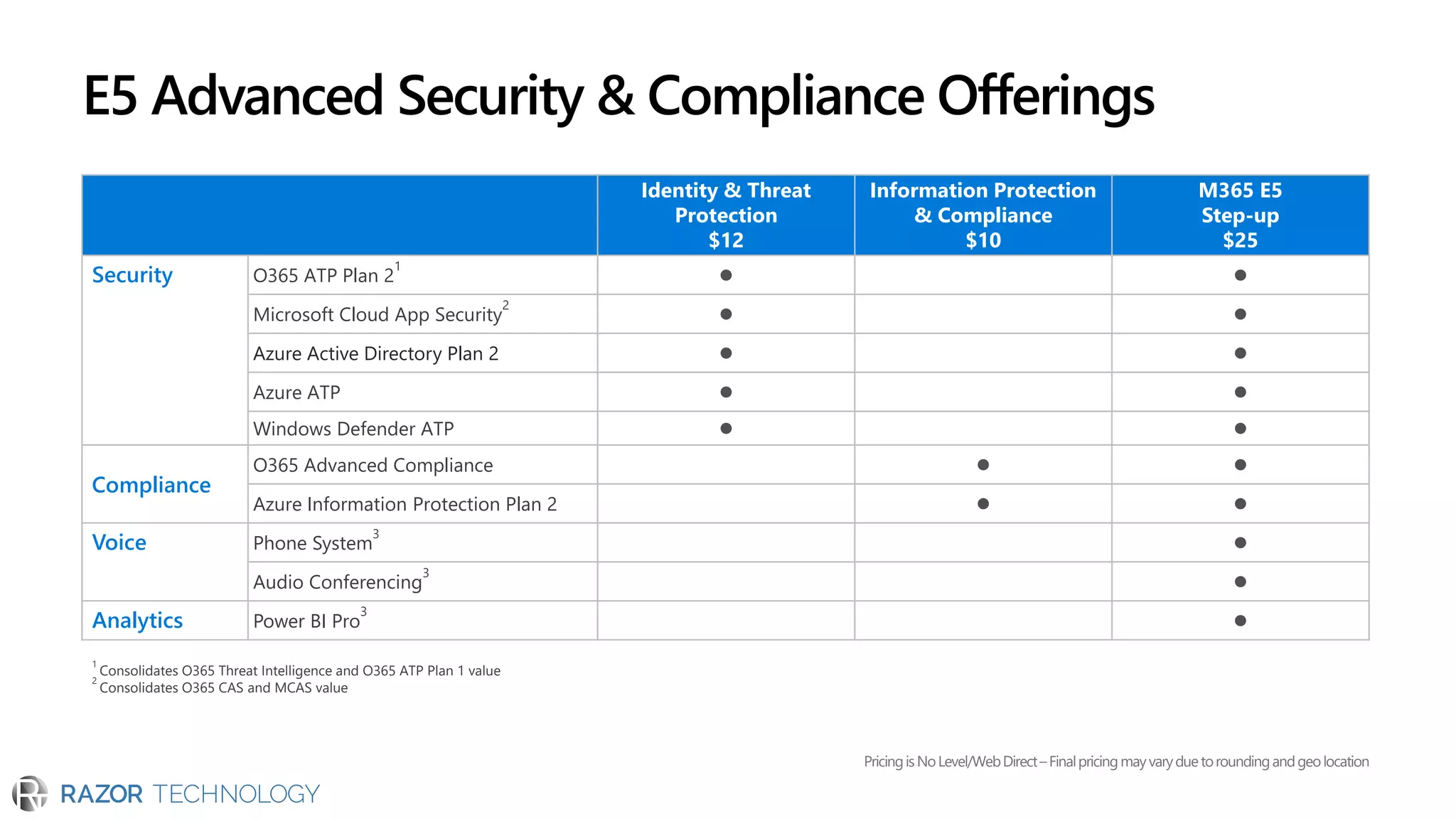
The document discusses the evolving security landscape in cyberspace, highlighting challenges such as talent shortages and the need for improved security solutions. It emphasizes Microsoft's commitment to addressing security threats through integrated technologies, artificial intelligence, and partnerships. Lastly, it outlines various security offerings aimed at enhancing organizational protection, compliance, and operational efficiency.