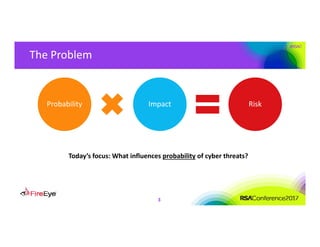
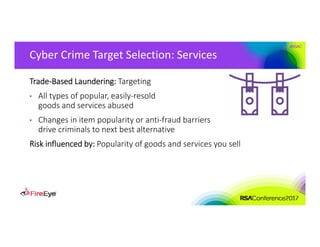
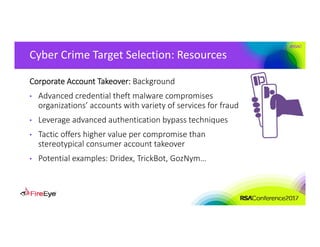
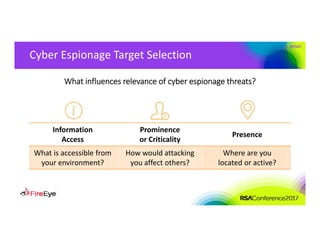
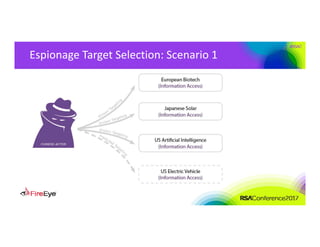
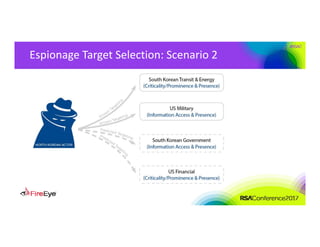
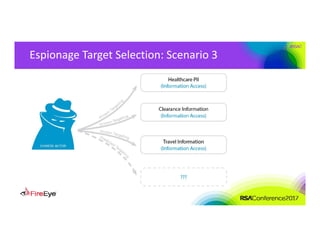
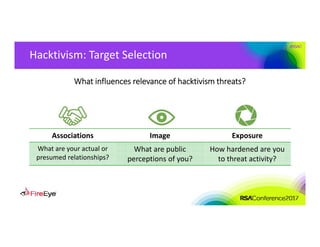
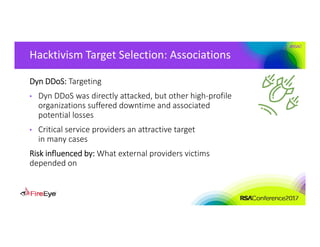
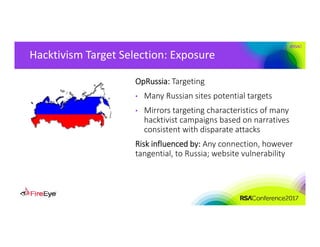
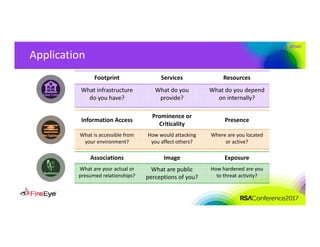
The document discusses the complexities of cyber threat prioritization, emphasizing that organizations often rely on simplistic criteria related to their sector or region, which can lead to missed opportunities for prevention. It outlines factors influencing the selection of cyber crime, cyber espionage, and hacktivism targets, including accessibility of resources, public perception, and the prominence of information. Ultimately, organizations are encouraged to assess threats based on a broader perspective, considering how various adversaries may target them beyond traditional boundaries.