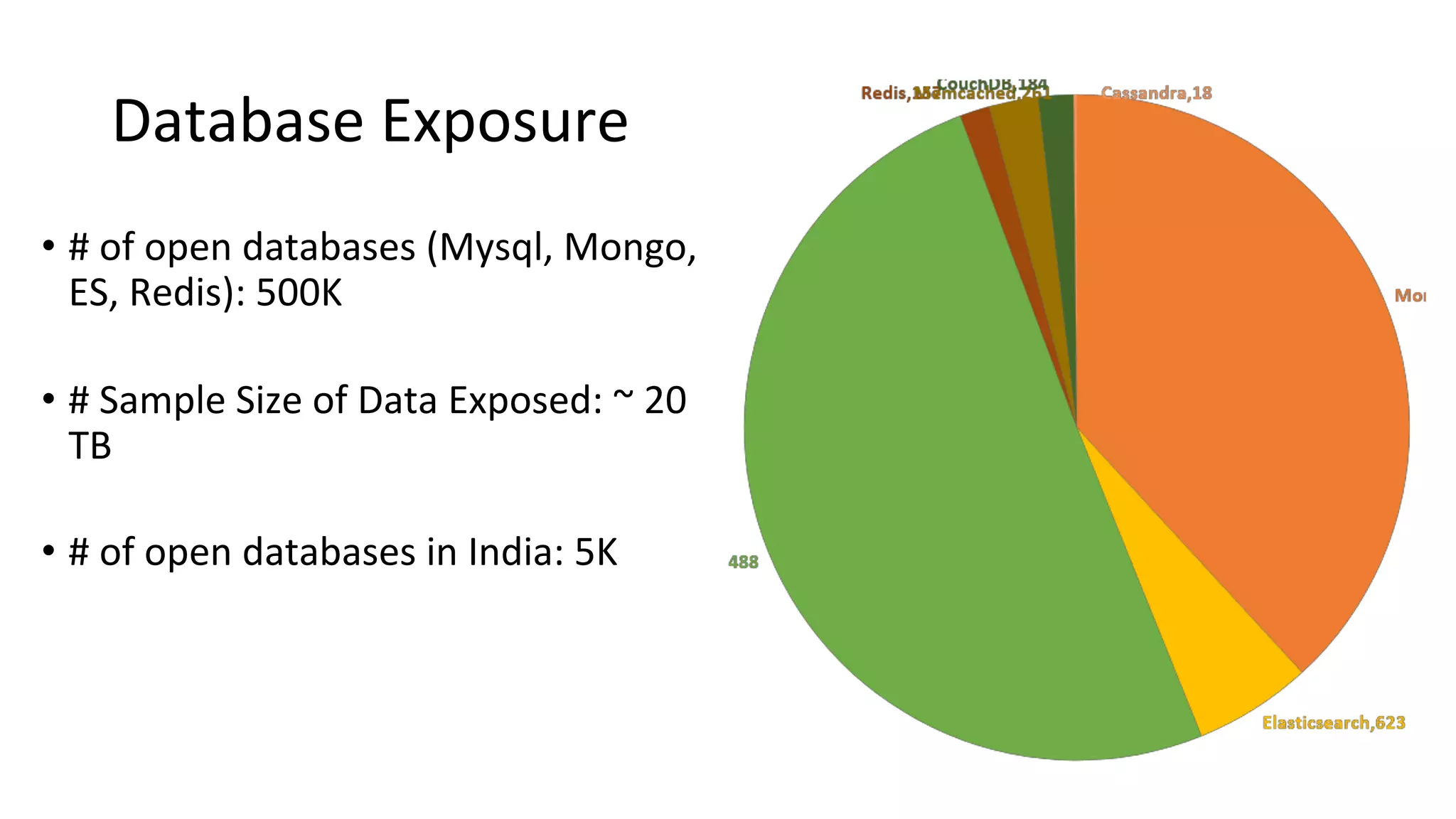
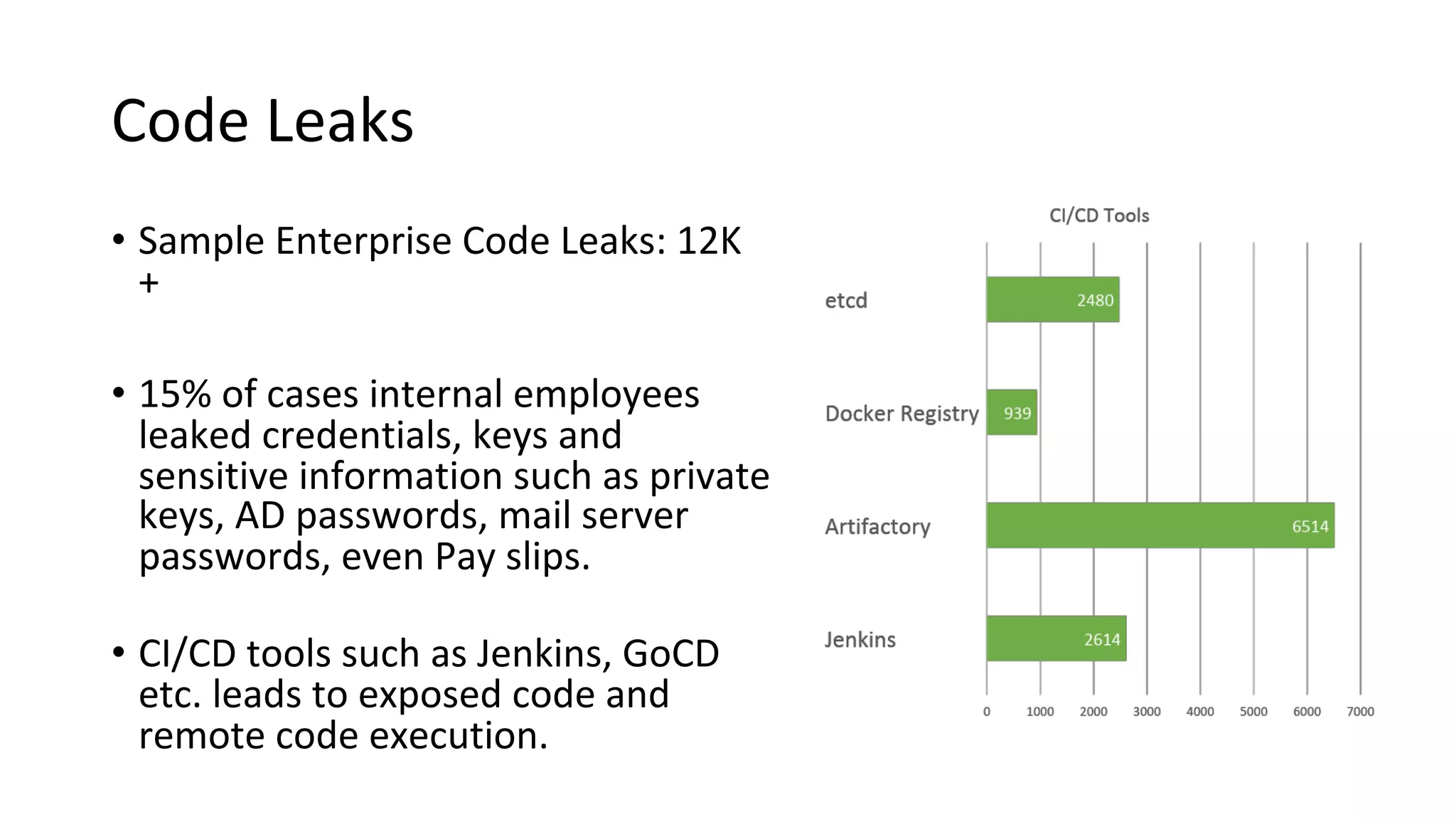
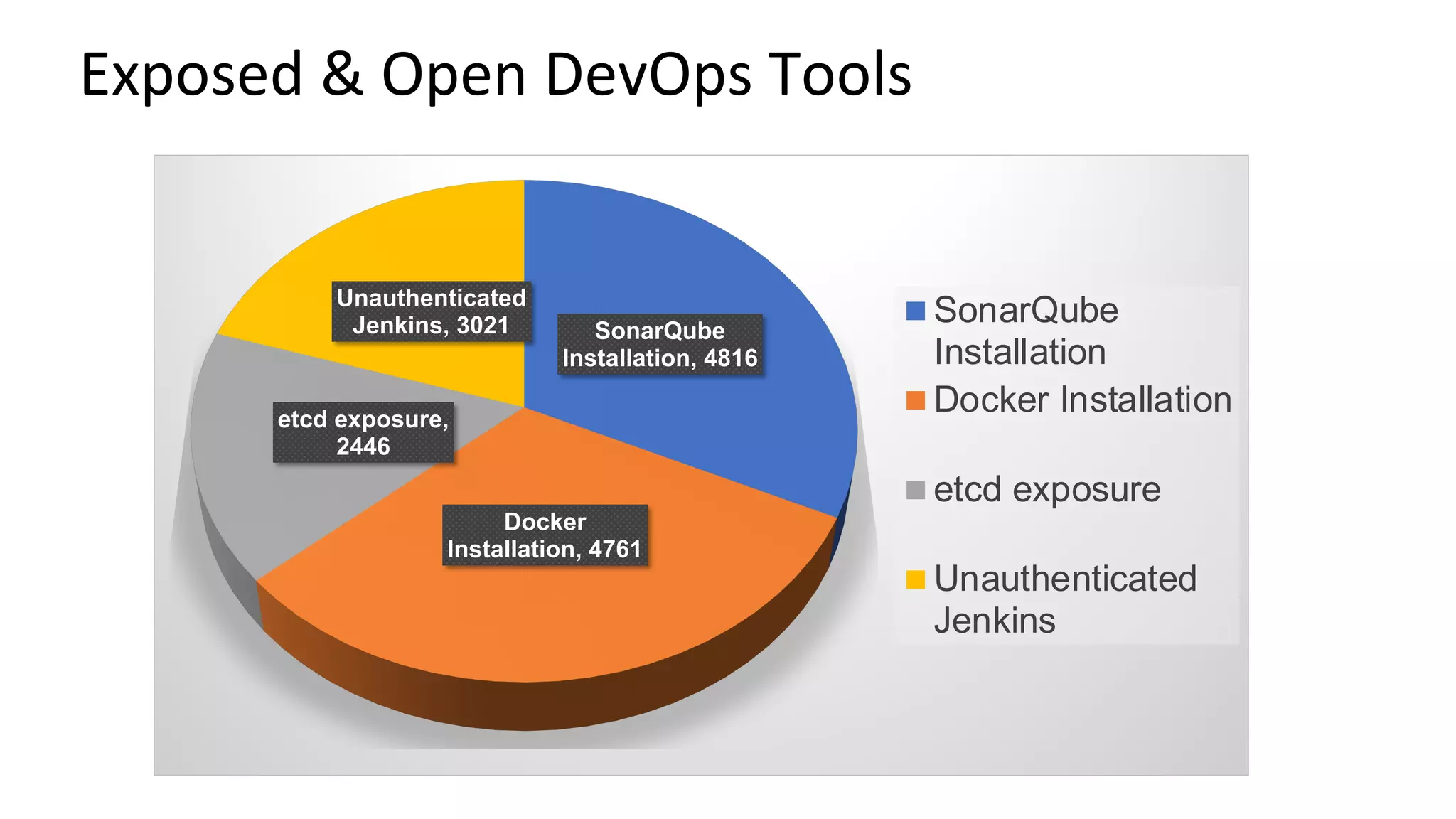
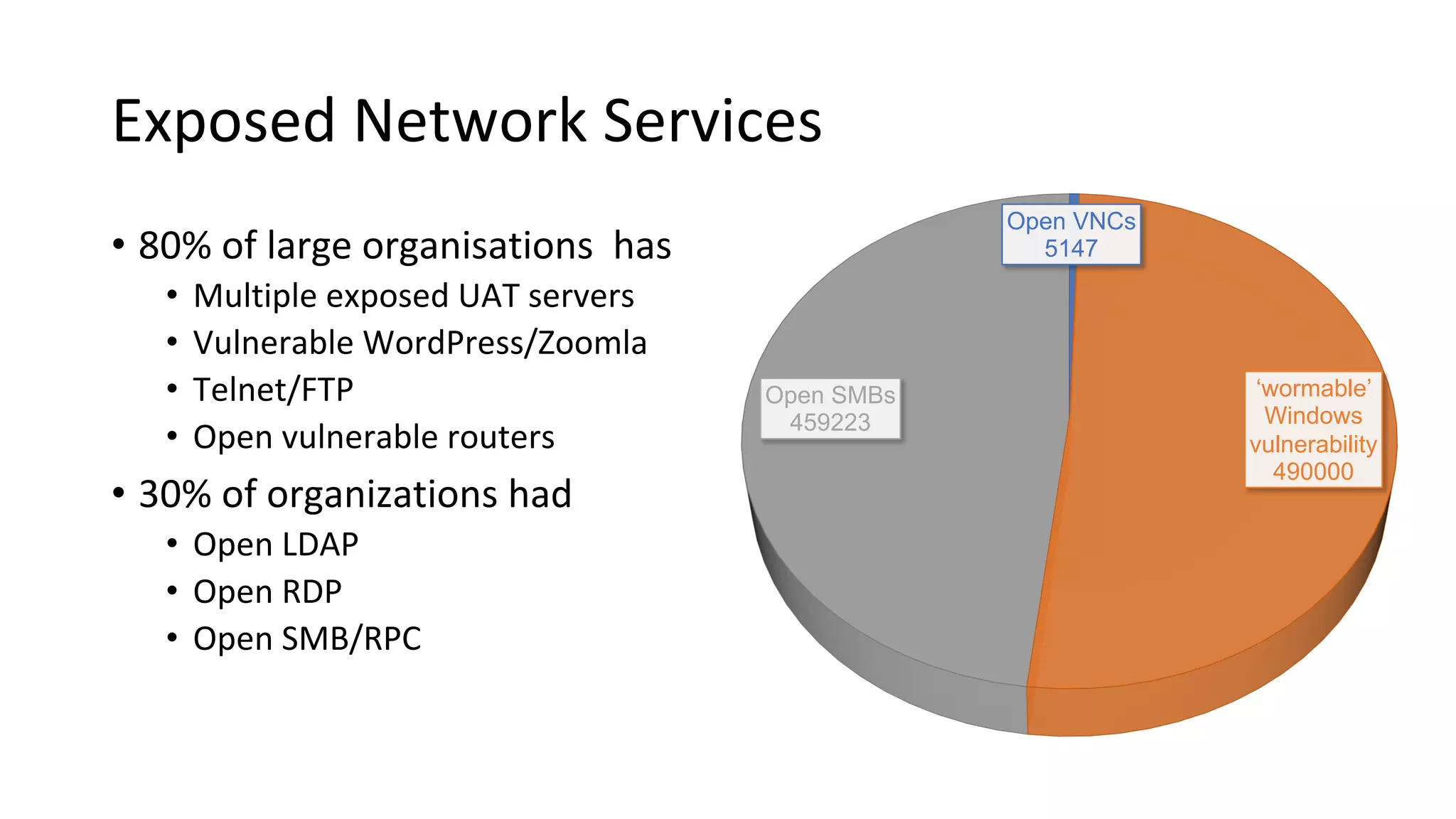
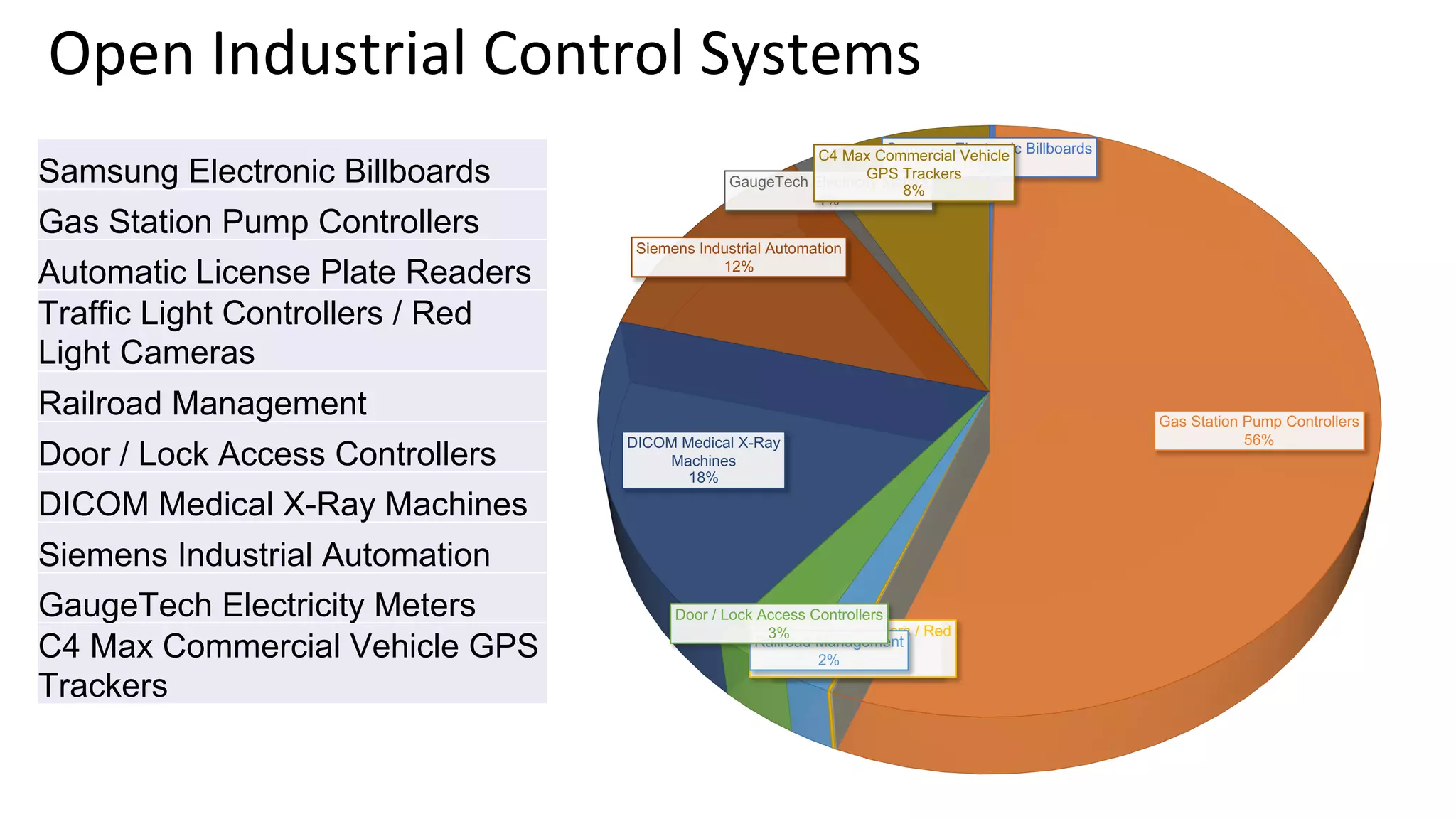
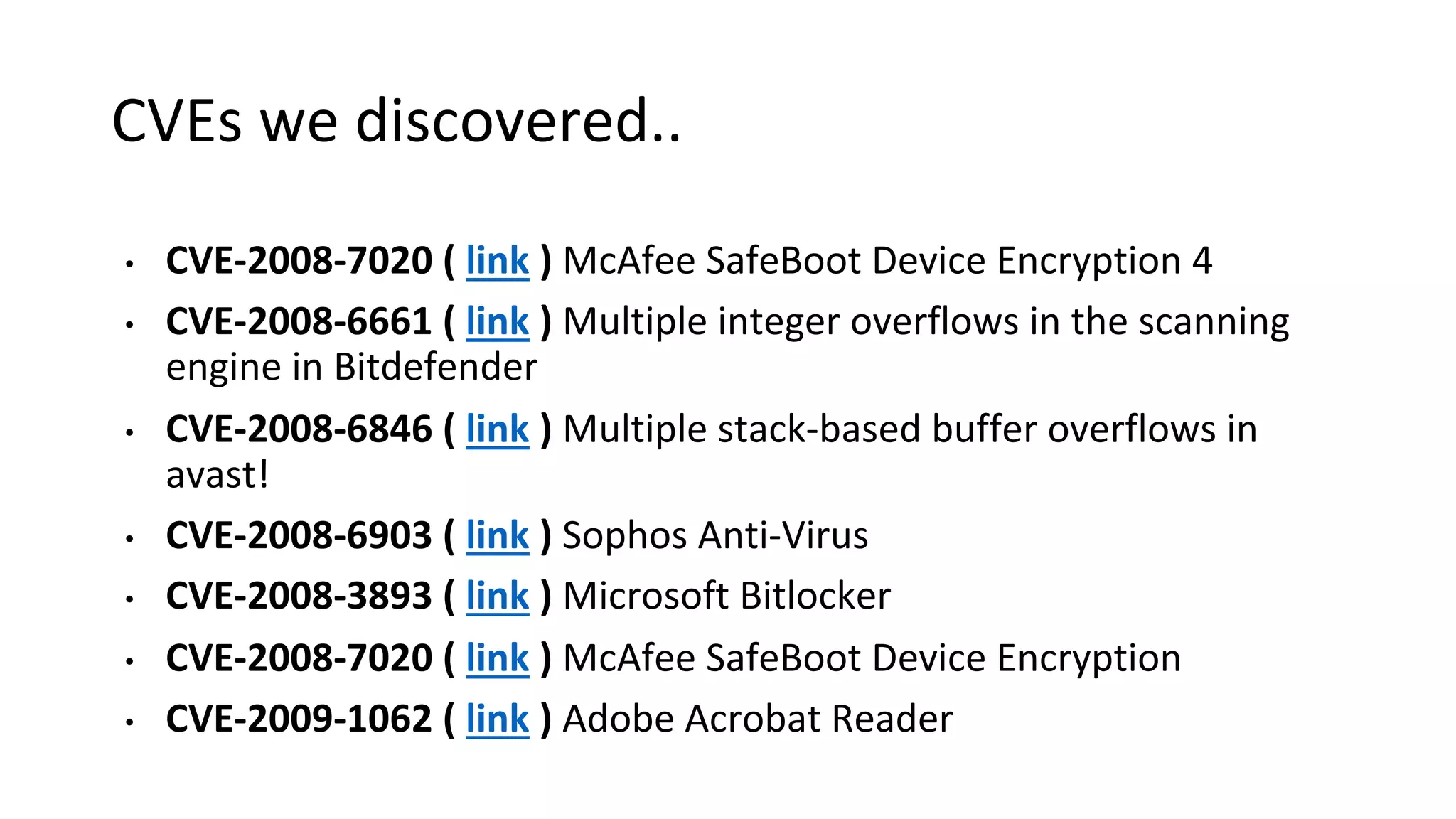
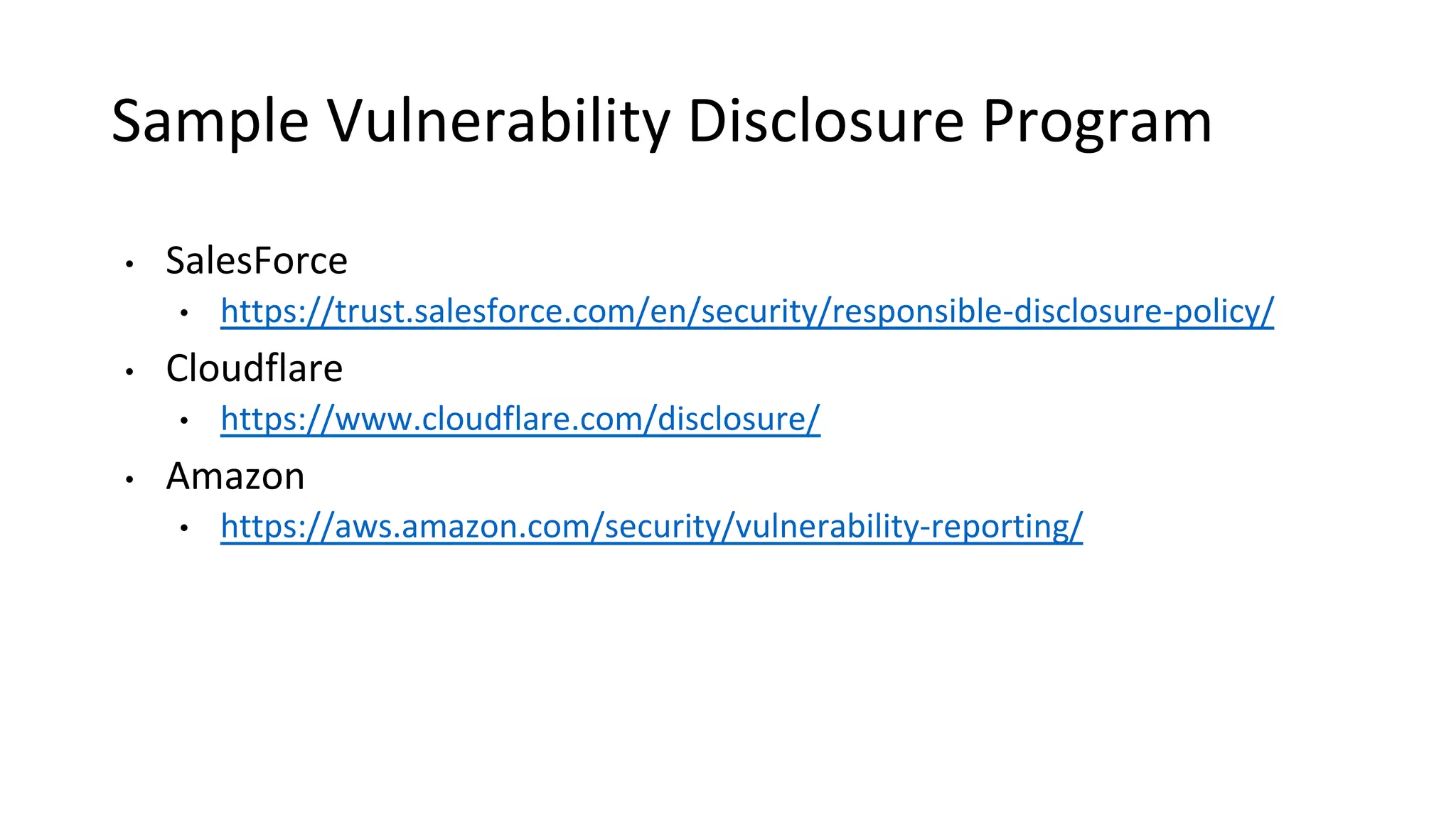
The document outlines best practices and guidelines for handling breach disclosures, emphasizing the importance of vulnerability disclosure policies (VDP) and real-time monitoring of sensitive data exposures. Key findings include significant data vulnerabilities from open databases, code leaks, and misconfigured cloud resources. It also provides resources and templates for creating effective VDPs and communication strategies in the event of a data breach.