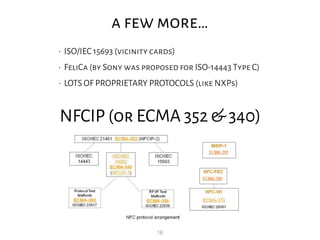
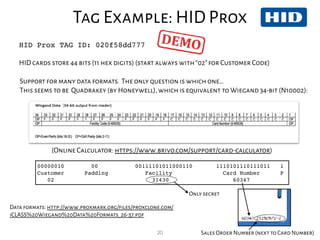
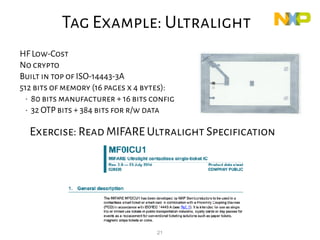
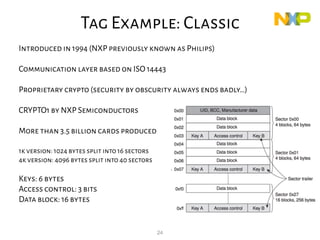
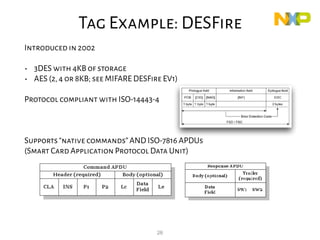
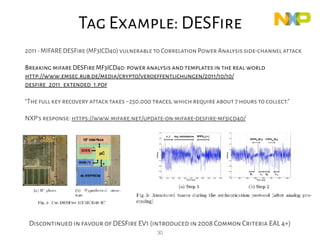
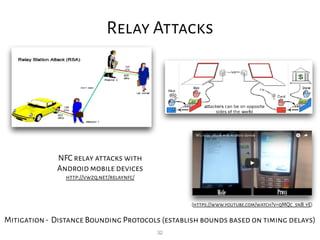
This document provides an overview of RFID security modules and discusses various RFID tag and reader technologies. It summarizes key RFID standards like ISO/IEC 14443 and describes common tag types, including HID Prox, MIFARE Ultralight, MIFARE Classic, and DESFire EV1. It also discusses relay attacks and ways they can be mitigated using distance bounding protocols.




![5
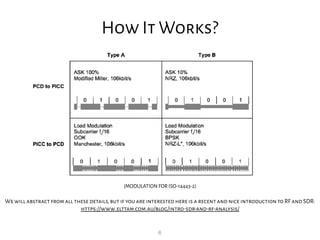
How It Works?
[Taken from 13.56 MHz RFID Proximity Antennas (http://www.nxp.com/documents/application_note/AN78010.pdf)]
Proximity
Inductive
Coupling
Card
Proximity
Coupling
Device](https://image.slidesharecdn.com/rfidsecslides-190201105209/85/RFID-Security-Module-5-320.jpg)



![10
ACR122U
NFC Tools: http://nfc-tools.org/index.php?title=ACR122
Basic NFC USB READER
Only HF (13.56mHz)
Support for a few specs (iso 14443 a/b,MIFARE,FeliCa…)
Cost ~20eur
OpenSource libraries (like LibNFC[https://github.com/nfc-tools/libnfc] )
Compatible with Android](https://image.slidesharecdn.com/rfidsecslides-190201105209/85/RFID-Security-Module-10-320.jpg)