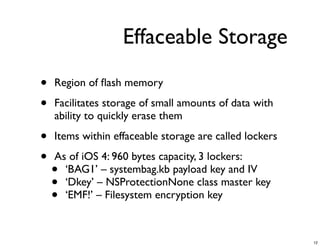
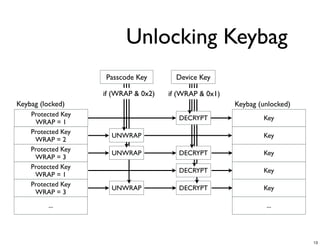
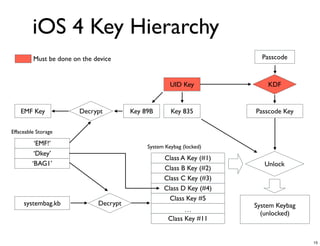
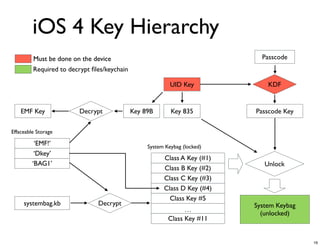
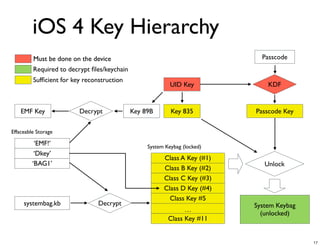
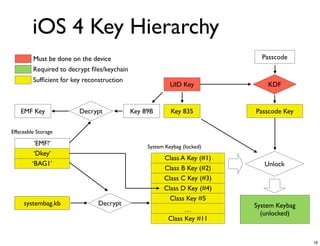
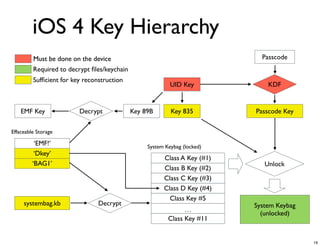
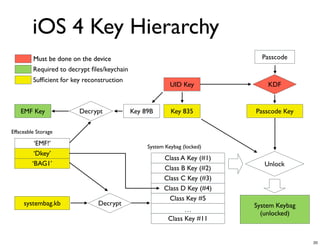
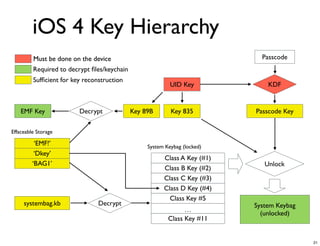
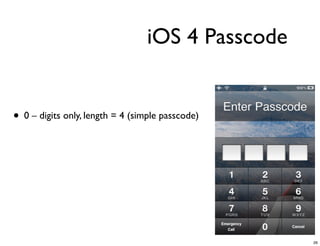
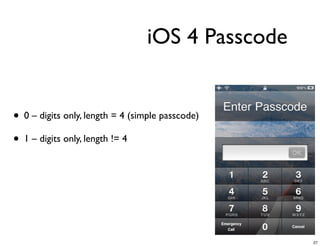
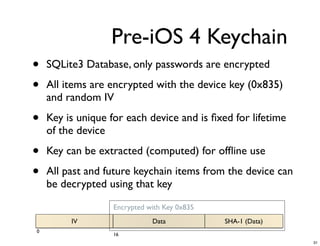
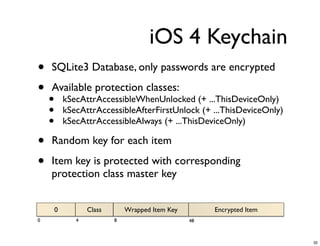
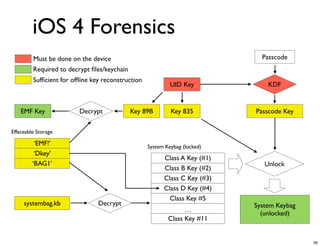
The document discusses iOS forensics and data protection in iOS 4. It covers how iOS 4 introduced stronger encryption for storage and keychain data using per-file and per-item keys protected by class keys stored in an encrypted keybag that requires the device passcode to unlock. It also describes how acquiring the device's effaceable storage contents and passcode are needed to decrypt storage images and reconstruct the encryption keys offline.