The document discusses IMSI catchers, focusing on both conventional and WiFi-based types that exploit vulnerabilities in mobile and wireless networks. It highlights various techniques for tracking, authentication issues, and potential protections against IMSI exposure, emphasizing the need for stronger privacy measures in mobile technology. The content underscores ongoing efforts to address these security challenges by both operators and operating system developers.


![What is an IMSI?
• International Mobile Subscriber Identity
• Globally unique identifier
• 15 digit number (MCountryCode+MNetCode+MSIdNum)
• e.g. 234123456789012
• Allows for [mutual] authentication of a device to the network
• GSM/2G: Only using SIM’s secret authentication Key (Ki)
• 3/4G: Using Ki and a shared Sequence Number (SQN)
• Stored in two places:
• In the ‘SIM Card’ (UICC/USIM)
• IMSI is accessible in a read only section of the U/SIM
• Secret key (Ki) and SQN are not directly readable
• At the Operator
• IMSI indexes Ki and SQN in Operator’s Database (HSS/AuC)
• An identifier that provides for tracking of devices
• There are others like WiFi/Bluetooth/NFC Hardware address (e.g.
MAC), IMEI, MSISDN (Phone number), etc.](https://image.slidesharecdn.com/g04mrkedqzegphi8ad2d-signature-40f4714a7511dbefb3f8b81978ee26a52b8bc17a56b46da771a1d673a5b4d7df-poli-170804175449/85/WiFi-Based-IMSI-Catcher-3-320.jpg)


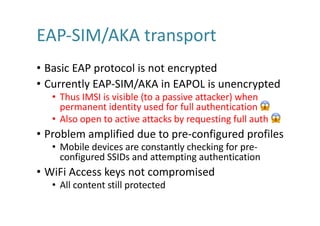
![WiFi-Based IMSI Catcher
• Features
• Tracking: IMSI, Location
• No interception (yet)
• Operates in unlicensed (ISM) Bands: WiFi
• Range - few hundred meters – can be extended…
• Fake Access Points
• Redirect/Spoofs mobile packet data gateway
• Exploits protocol & configuration weaknesses
• Based on two separate techniques [3GPP TS33.234]
• WiFi Network Authentication (‘WLAN direct IP access’)
• WiFi-Calling Authentication (‘WLAN 3GPP IP access’)
• Cost
• Low: Virtually any WiFi capable computer](https://image.slidesharecdn.com/g04mrkedqzegphi8ad2d-signature-40f4714a7511dbefb3f8b81978ee26a52b8bc17a56b46da771a1d673a5b4d7df-poli-170804175449/85/WiFi-Based-IMSI-Catcher-7-320.jpg)



![Automatic WiFi Authentication
• Port Based Network Access Control [IEEE 802.1X]
• Uses Extensible Authentication Protocol (EAP) [RFC3748]
over LAN (EAPOL) over WiFi
• Based upon two EAP Methods
• EAP-SIM [RFC 4186]
• GSM based security - Currently most widely used
• EAP-AKA [RFC 4187]
• 3G based security - Being deployed
• Support in Android, iOS, Windows Mobile, and
Blackberry devices
• We’ve reported the issue to them all and to operators &
GSMA
• No privacy bounties 😕
• Deployed in many countries – adoption growing](https://image.slidesharecdn.com/g04mrkedqzegphi8ad2d-signature-40f4714a7511dbefb3f8b81978ee26a52b8bc17a56b46da771a1d673a5b4d7df-poli-170804175449/85/WiFi-Based-IMSI-Catcher-12-320.jpg)