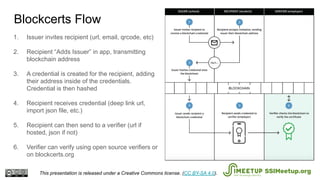
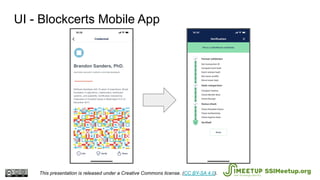
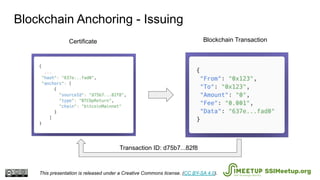
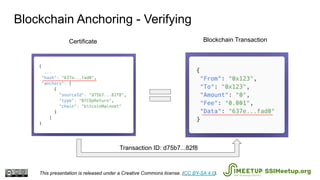
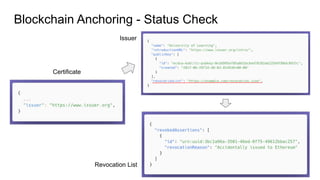
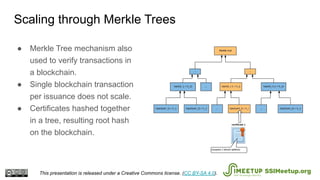
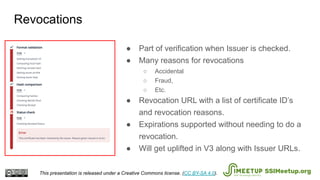
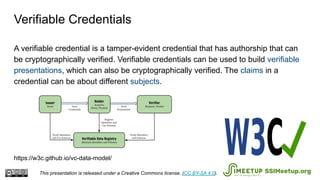
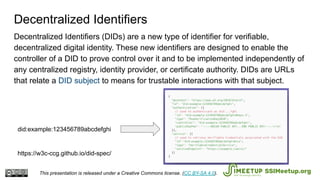
The document presents Blockcerts, an open standard for issuing and verifying blockchain-based credentials such as certificates and licenses. It outlines the technical processes involved in creating, verifying, and managing these credentials, including mechanisms for revocation and privacy. The document emphasizes the importance of decentralization and interoperability, highlighting upcoming enhancements in future versions.