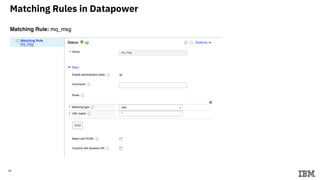
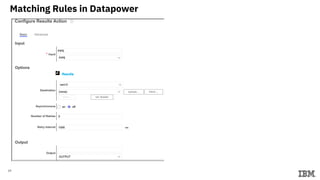
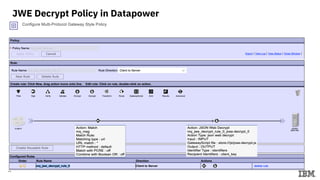
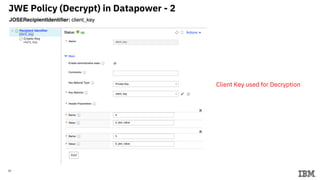
This document describes setting up a microservices architecture with IBM Datapower for securing communication between services using JSON Web Tokens (JWT). It includes details on:
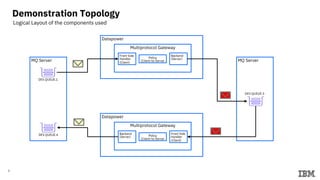
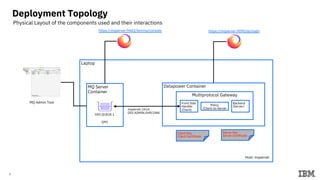
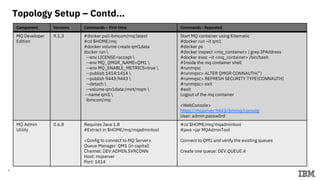
1) The topology used consisting of a Datapower gateway, MQ server, and laptop.
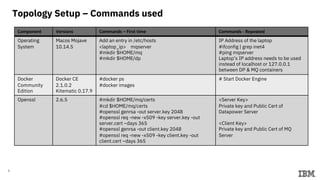
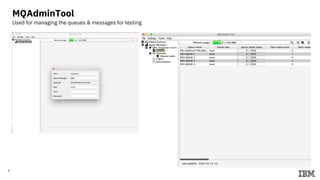
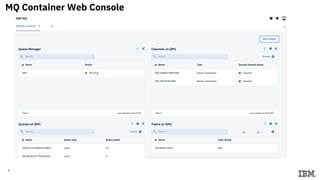
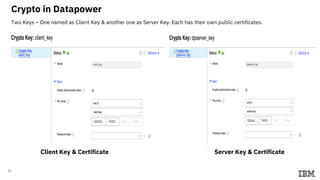
2) Commands to setup Docker containers for each component and generate keys/certificates.
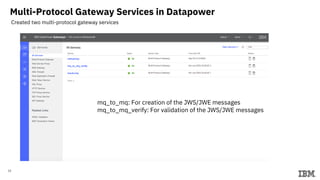
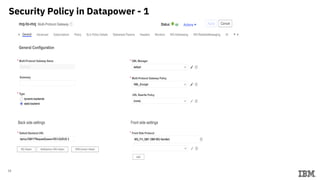
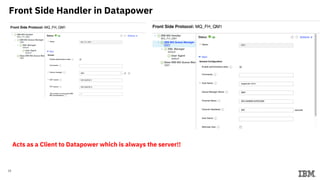
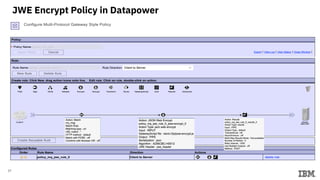
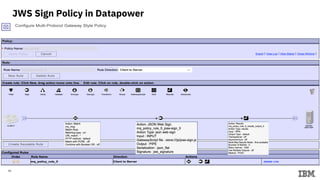
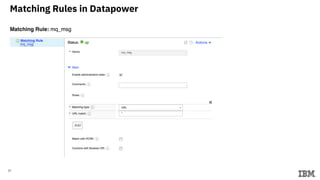
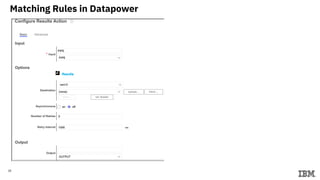
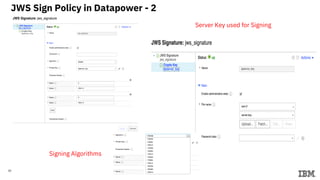
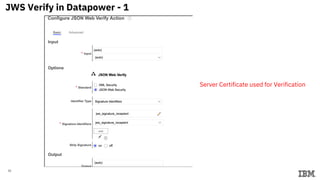
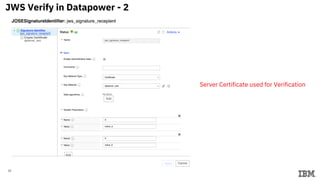
3) Configuring Datapower policies for JWT signing, verification, encryption, and decryption to secure messages between the MQ server and Datapower gateway.
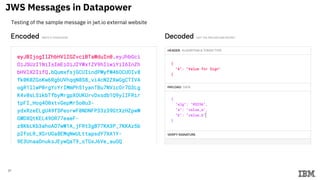
4) Testing the end-to-end flow by sending sample messages through the Datapower gateway.










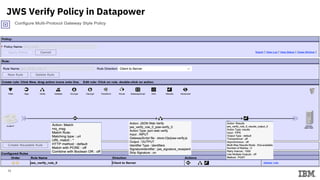



![38
JWE Messages in Datapower
Output: JWS MessageInput Plain Text
A sample message shown for reference
{"recipients":[{
"encrypted_key":"uk2TlCWTaEVsWViqV_jOp3rc5B8EaNBegM75WD
onYtnqdpmLwHdelqeqzThp1LcdJcl3h2nyx5jj222RMpuGMv9QFHcb
GzppwlDbYqETHUtoeGglHuZimni3TfIXbHybYaUEGRvAudks43KECby
WMmv84zHBdLwFRSeC9cojENzQpxTvl3_K5VT5SGi6t_0gHhSTy08U
EU7FmjmpXwe83UkirbUkPi5zhm51cqB_Yb2_00fnewyp2sOpJX3kM
V8VFelUS6po_C4ZTo7gteWu7foruxGMOxPJyIORYXiix6Ix2fliSKExcG
OEbX8iNdnqthspjR_miR_Y8GXiJGYDQw"}],
"protected":"eyJlbmMiOiJBMjU2Q0JDLUhTNTEyIiwiYSI6ImFfandlX
3ZhbHVlIiwiYiI6ImJfandlX3ZhbHVlIiwiYWxnIjoiUlNBMV81In0",
"ciphertext":"mMnBovrT5Vz6b1SS_zSoyVpZ6m9a-
TGzTdGaMzuHj9E",
"iv":"nyEFkTnDH9uAL9OkXhXAOQ",
"tag":"akoKNEY6MzL-XvwOx_0PFX5bg1hCHlJnasU5VK0KUo4"}
{”A”: “Value for Encrypt”}](https://image.slidesharecdn.com/ibmdatapowersecurityscenarioshandsonjwefinal-200331102906/85/IBM-Datapower-Security-Scenario-with-JWS-JWE-38-320.jpg)

