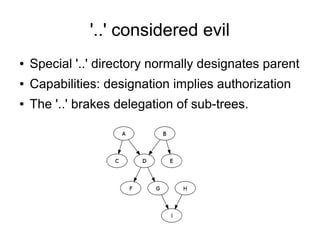
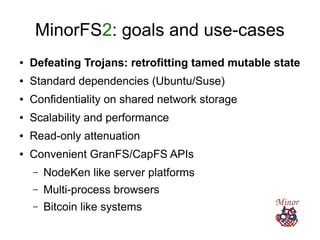
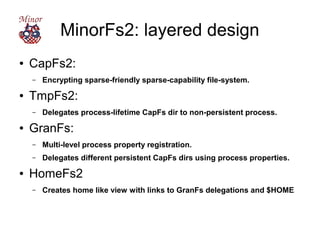
The document discusses improving security in software systems by emphasizing user delegation of authority and the need for better user authentication and authorization mechanisms. It critiques traditional identity-centric models and promotes using capabilities and minimizing global mutable state to reduce vulnerabilities. Suggestions include implementing processes that support privacy and delegation while also introducing a framework called minorfs2 for enhanced security and scalability in file systems.