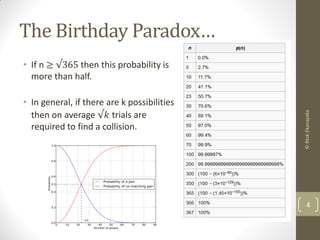
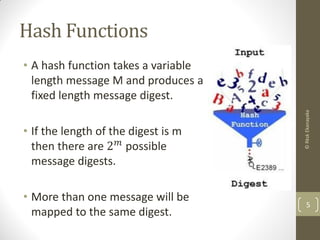
The document explains the birthday paradox, illustrating the counterintuitive probability of shared birthdays among a group, and notes that with 22 people, the chance exceeds 50%. It discusses how hash functions can lead to collisions, enabling a 'birthday attack' where attackers can exploit this probability to forge signatures. To mitigate this risk, it suggests using hash functions with a longer output length to make such attacks computationally infeasible.