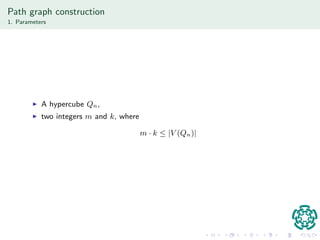
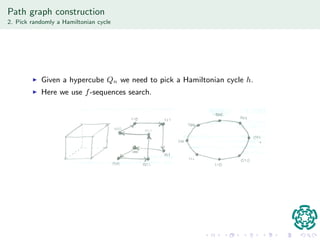
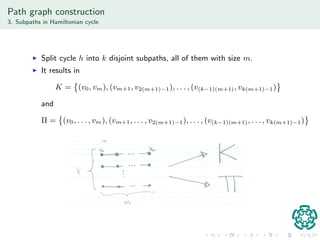
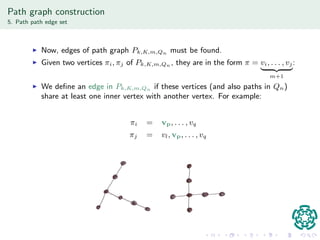
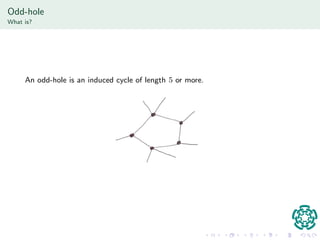
The document discusses authentication protocols based on zero-knowledge proofs, outlining the concepts of interactive proofs and their properties, including completeness and soundness. It proposes a specific authentication protocol that utilizes zero-knowledge proofs and constructs a path graph based on Hamiltonian cycles, while examining related computational challenges like the odd-hole problem. The document also details completed and current tasks in developing this proposed solution within the context of graph theory.









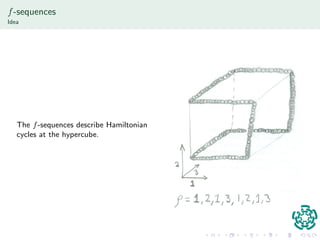






![nition
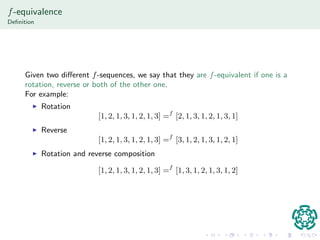
Given two dierent f-sequences, we say that they are f-equivalent if one is a
rotation, reverse or both of the other one.
For example:
I Rotation
[1; 2; 1; 3; 1; 2; 1; 3] =f [2; 1; 3; 1; 2; 1; 3; 1]
I Reverse
[1; 2; 1; 3; 1; 2; 1; 3] =f [3; 1; 2; 1; 3; 1; 2; 1]
I Rotation and reverse composition
[1; 2; 1; 3; 1; 2; 1; 3] =f [1; 3; 1; 2; 1; 3; 1; 2]](https://image.slidesharecdn.com/apbozkpbi-141112232017-conversion-gate02/85/Authentication-protocols-based-on-zero-knowledge-proof-Part-2-Brief-talk-29-320.jpg)