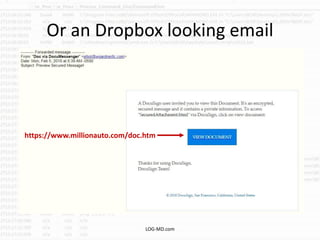
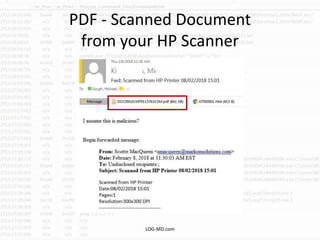
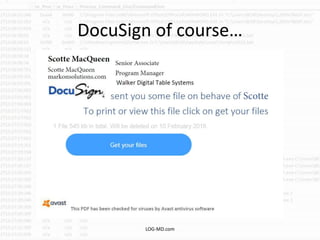
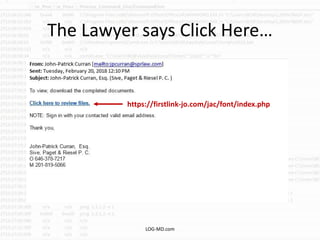
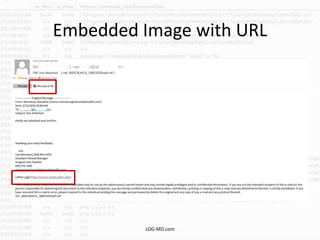
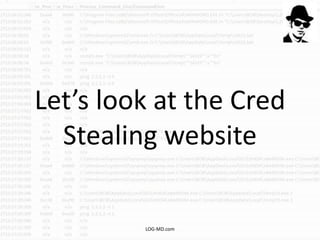
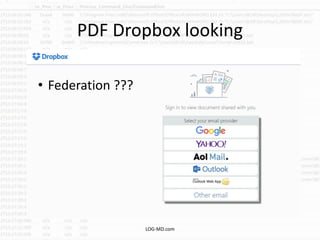
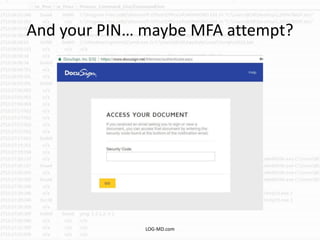
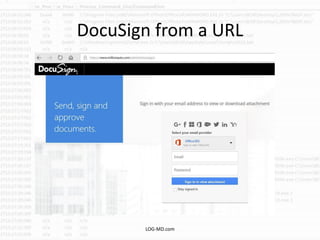
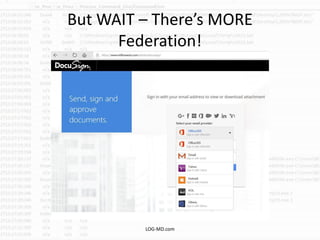
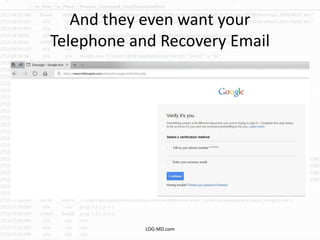
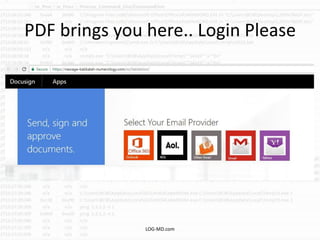
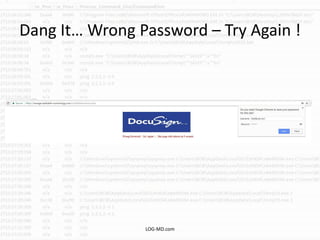
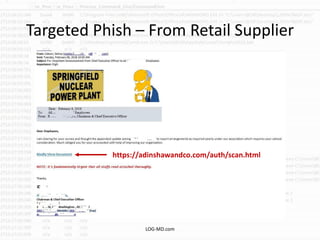
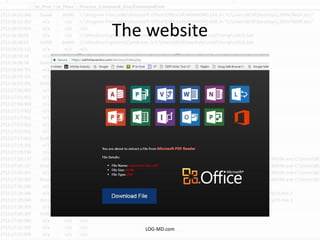
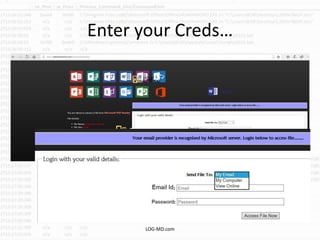
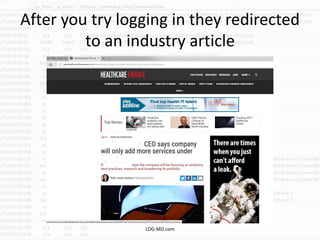
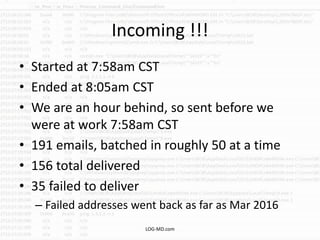
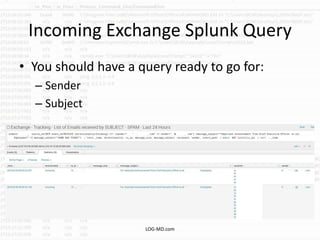
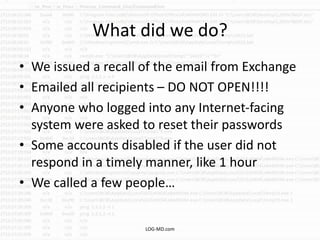
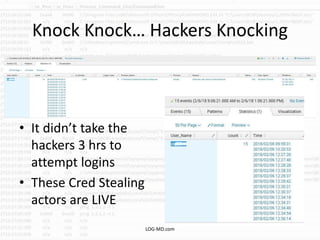
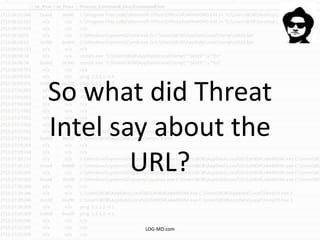
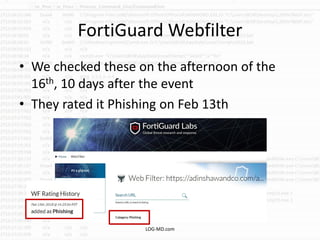
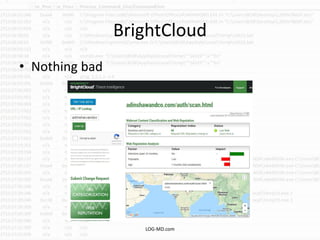
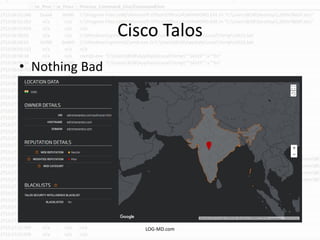
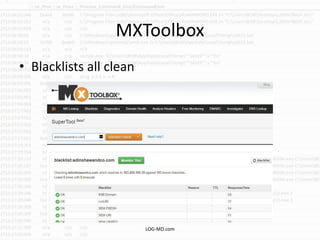
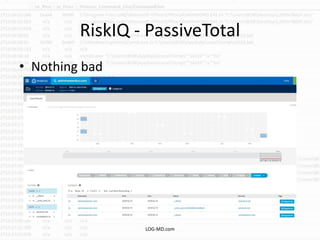
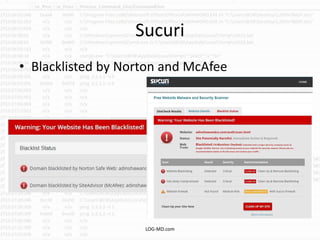
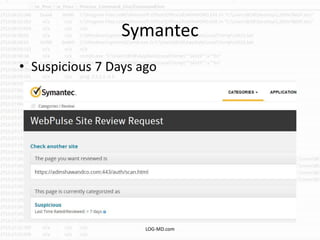
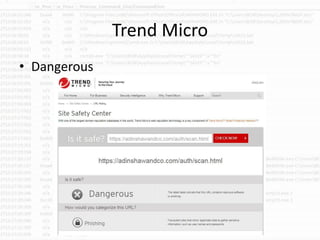
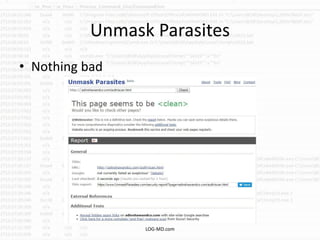
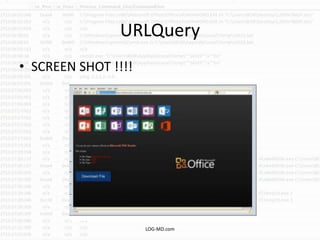
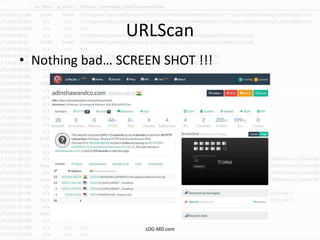
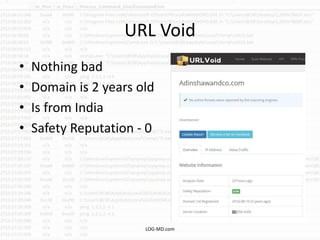
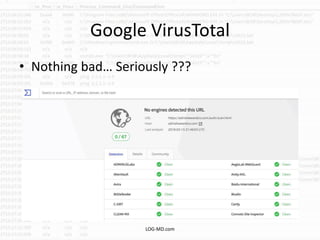
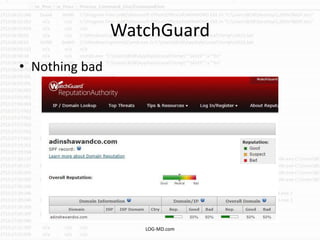
The document discusses the rising challenge of credential stealing emails, detailing the tactics used by hackers to bypass security measures. It outlines the response strategies implemented by a security team during a phishing incident, emphasizing the importance of multi-factor authentication and rapid detection. Recommendations for evaluating threats and securing accounts are provided, alongside resources for further information and monitoring.