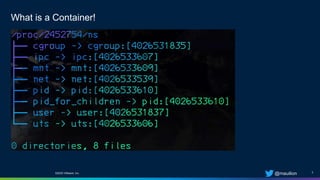
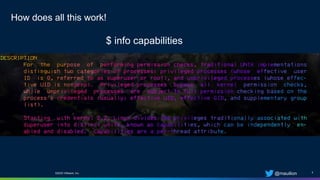
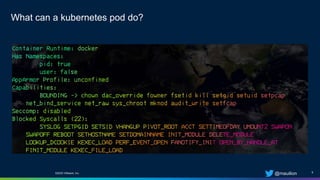
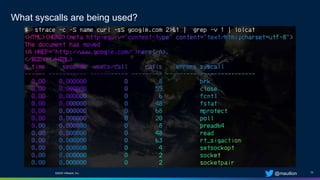
The document is a practical guide on Seccomp security profiles, focusing on their implementation in Kubernetes and Docker containers. It emphasizes the importance of using Seccomp filters to manage syscalls and enhance container security against various attacks, such as supply chain vulnerabilities and exploitable application bugs. The author also notes that Kubernetes disables default Seccomp profiles used in Docker due to the complexities introduced by multiple containers in a pod.