Infographic: Are we backing up too much?
•
0 likes•283 views
As backup is getting easier, does this mean we're backing up too much? Infographic from our recent Data Health Check 2013.
Report
Share
Report
Share
Download to read offline
Recommended
Annual environment and health conference 2018 fiona o rourke epa 2018 env&...

Annual environment and health conference 2018 fiona o rourke epa 2018 env&...Environmental Protection Agency, Ireland
Recommended
Annual environment and health conference 2018 fiona o rourke epa 2018 env&...

Annual environment and health conference 2018 fiona o rourke epa 2018 env&...Environmental Protection Agency, Ireland
More Related Content
What's hot
What's hot (20)
Allegient and IUPUI Develop Big Data Search Tool (SURAAK)

Allegient and IUPUI Develop Big Data Search Tool (SURAAK)
Software Advice IndustryView: Use of Speech Therapy Software for Home Practice

Software Advice IndustryView: Use of Speech Therapy Software for Home Practice
Personalized Mobile Applications in HealthCare by Bhargavi Upadhya

Personalized Mobile Applications in HealthCare by Bhargavi Upadhya
The 2017 Hospital Guide to Secure Mobile Messaging Success

The 2017 Hospital Guide to Secure Mobile Messaging Success
Keeping Community Hospitals Thriving and Independent

Keeping Community Hospitals Thriving and Independent
Convert with Confidence: Barriers and Benefits of the EHR Switch

Convert with Confidence: Barriers and Benefits of the EHR Switch
Sleep Tech: An Ecosystem of Electric Sleep - Daniel Ruppar, Frost & Sullivan ...

Sleep Tech: An Ecosystem of Electric Sleep - Daniel Ruppar, Frost & Sullivan ...
The State of Mobile Communications in Healthcare: Survey Results Part 2

The State of Mobile Communications in Healthcare: Survey Results Part 2
2015 Identity Summit - Philips Case Study: New Healthcare Solutions and Pati...

2015 Identity Summit - Philips Case Study: New Healthcare Solutions and Pati...
Applying the principles to community engagement projects

Applying the principles to community engagement projects
HxRefactored 2015: MediSafe "Cloud-Synced Medication Management for Patients ...

HxRefactored 2015: MediSafe "Cloud-Synced Medication Management for Patients ...
Going Mobile: Using mobile to enhance care and efficiency

Going Mobile: Using mobile to enhance care and efficiency
Digital Health & Wellness Summit @ Mobile World Congress 2016

Digital Health & Wellness Summit @ Mobile World Congress 2016
Putting the Power in the Patient's Hands: Digital Health Trends

Putting the Power in the Patient's Hands: Digital Health Trends
Top Wearables Predictions for the Year Ahead and 2018: Year in Review

Top Wearables Predictions for the Year Ahead and 2018: Year in Review
Similar to Infographic: Are we backing up too much?
Similar to Infographic: Are we backing up too much? (20)
A Guide to Thoughtful Governance - Liberty and Justice for All

A Guide to Thoughtful Governance - Liberty and Justice for All
Crossing the Threshold: Clinical Portals from a Site Perspective 

Crossing the Threshold: Clinical Portals from a Site Perspective
Responsible Data for Children Training_PublicSlides_110922.pdf

Responsible Data for Children Training_PublicSlides_110922.pdf
How Good Privacy Practices can help prepare for a Data Breach from TRUSTe 

How Good Privacy Practices can help prepare for a Data Breach from TRUSTe
Conducting High Impact Research: Building data ownership and improving data use

Conducting High Impact Research: Building data ownership and improving data use
2016 Connected Patient Report - Sponsor Content From: Salesforce 

2016 Connected Patient Report - Sponsor Content From: Salesforce
Stop, Collaborate and Listen: The Social Lives of Healthcare Professionals

Stop, Collaborate and Listen: The Social Lives of Healthcare Professionals
More from Databarracks
More from Databarracks (20)
How to write an effective Cyber Incident Response Plan

How to write an effective Cyber Incident Response Plan
How to recover from ransomware lessons from real recoveries

How to recover from ransomware lessons from real recoveries
How to know when combined backup and replication is for you

How to know when combined backup and replication is for you
How to write an effective Cyber Incident Response Plan

How to write an effective Cyber Incident Response Plan
Introducing rubrik a new approach to data protection

Introducing rubrik a new approach to data protection
The Databarracks Continuity Toolshed: Free tools for better recoveries

The Databarracks Continuity Toolshed: Free tools for better recoveries
Recently uploaded
Recently uploaded (20)
Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics

Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Human Factors of XR: Using Human Factors to Design XR Systems

Human Factors of XR: Using Human Factors to Design XR Systems
"Federated learning: out of reach no matter how close",Oleksandr Lapshyn

"Federated learning: out of reach no matter how close",Oleksandr Lapshyn
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
Unlocking the Potential of the Cloud for IBM Power Systems

Unlocking the Potential of the Cloud for IBM Power Systems
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
Scanning the Internet for External Cloud Exposures via SSL Certs

Scanning the Internet for External Cloud Exposures via SSL Certs
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Infographic: Are we backing up too much?
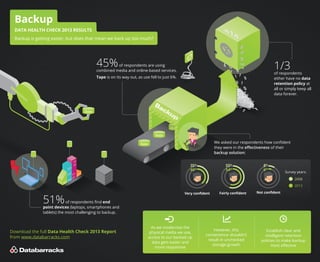
- 1. Backup DATA HEALTH CHECK 2013 RESULTS Backup is getting easier, but does that mean we back up too much? 45% 1/3 of respondents are using combined media and online-based services. of respondents either have no data retention policy at all or simply keep all data forever. Tape is on its way out, as use fell to just 6%. We asked our respondents how confident they were in the effectiveness of their backup solution: 35% 40% 55% 54% 8% 6% Survey years: 2008 2013 51% Very confident Fairly confident Not confident of respondents find end point devices (laptops, smartphones and tablets) the most challenging to backup. Download the full Data Health Check 2013 Report from www.databarracks.com As we modernise the physical media we use, access to our backed up data gets easier and more responsive However, this convenience shouldn’t result in unchecked storage growth Establish clear and intelligent retention policies to make backup most effective
