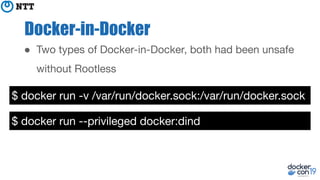
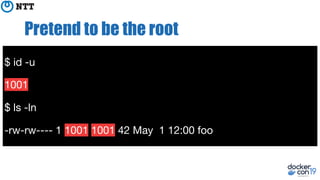
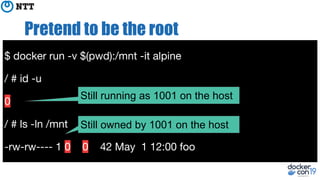
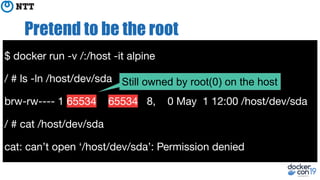
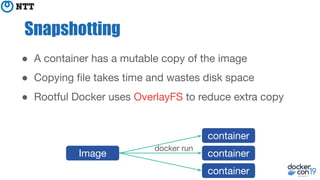
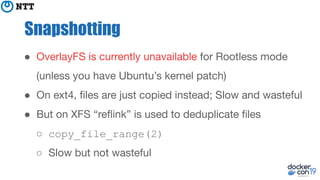
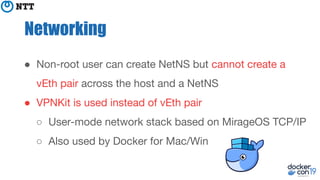
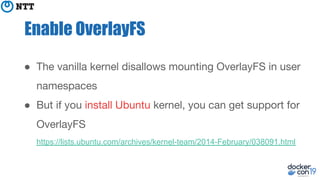
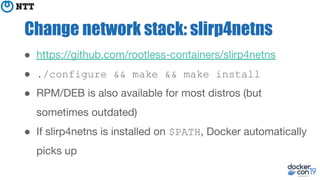
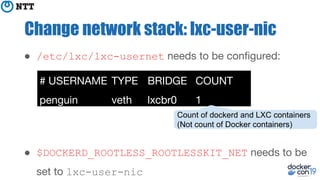
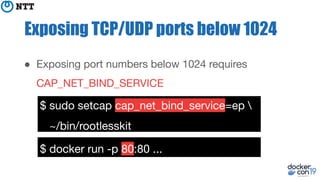
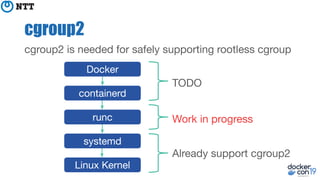
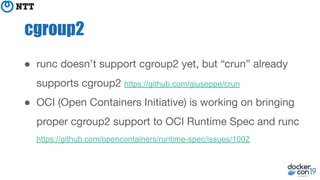
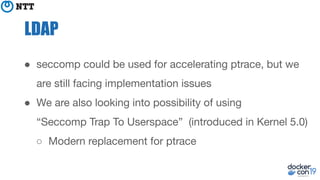
The document discusses the implementation and benefits of running Docker in rootless mode, which allows users to execute Docker as non-root, potentially mitigating security vulnerabilities and misconfigurations. It emphasizes that while rootless mode enhances security, it doesn't eliminate all risks and presents some limitations related to functionality and performance. Additionally, it provides practical tips for installation and configuration, including the use of systemd services and network stack adjustments.









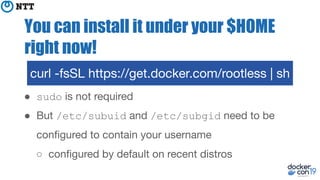
![You can install it under your $HOME
right now!
● The installer shows helpful error if /etc/sub[ug]id is
unconfigured
○ Thanks to Tõnis Tiigi and Tibor Vass!
● Feel free to ask me after this session if it doesn’t work
curl -fsSL https://get.docker.com/rootless | sh](https://image.slidesharecdn.com/hardeningdockerdaemonwithrootlessmode-190501210234/85/DockerCon-2019-Hardening-Docker-daemon-with-Rootless-mode-15-320.jpg)