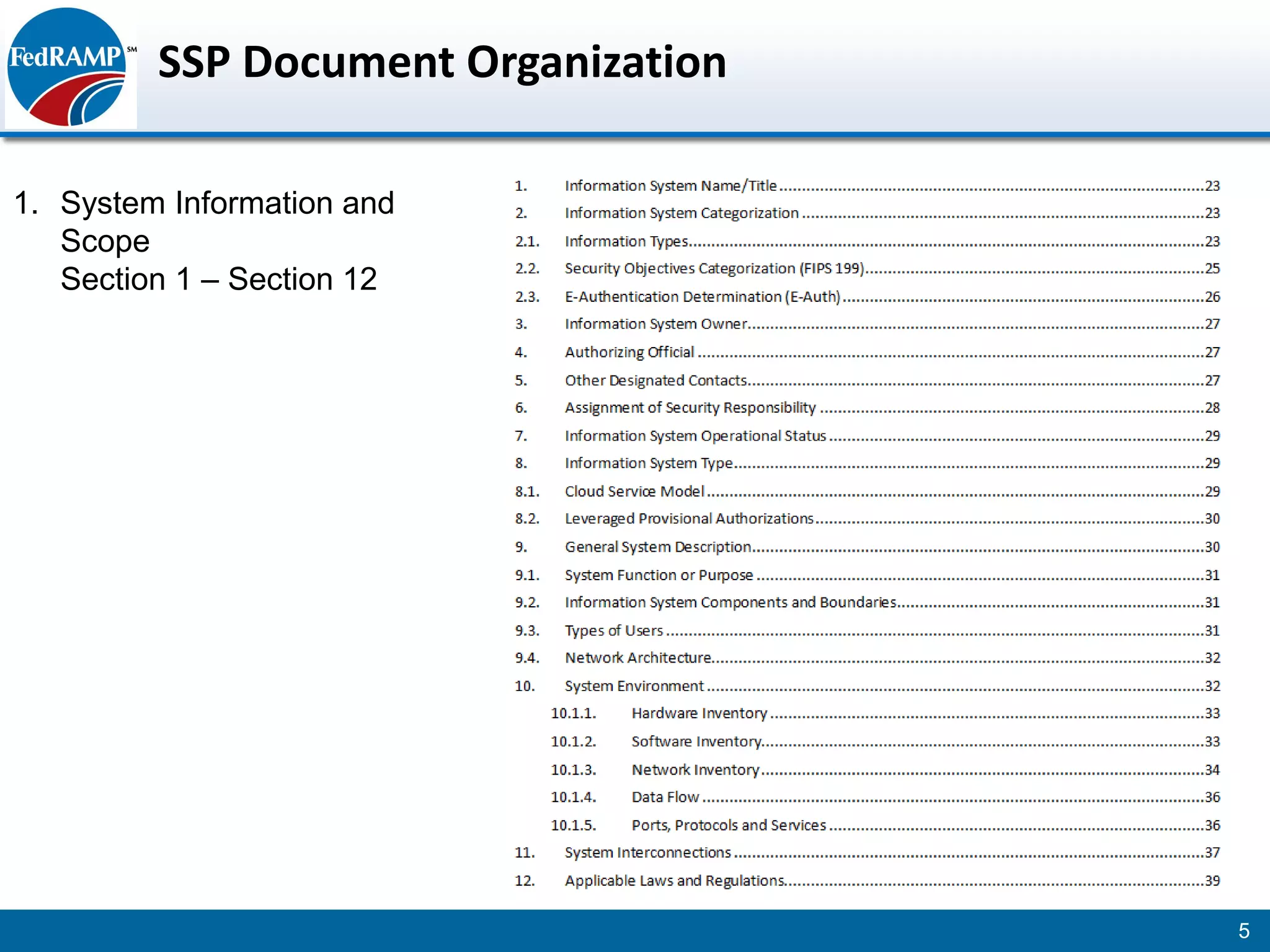
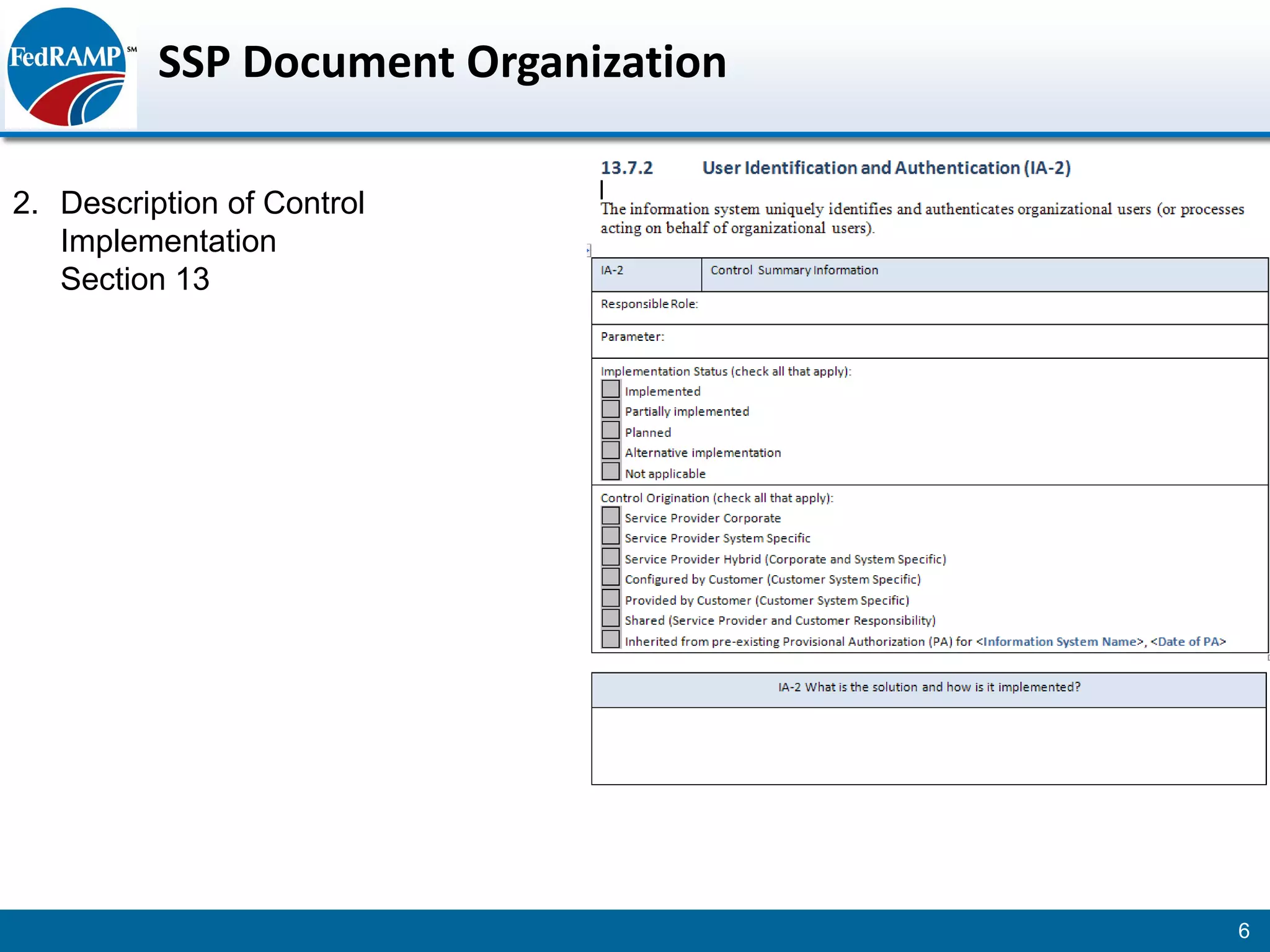
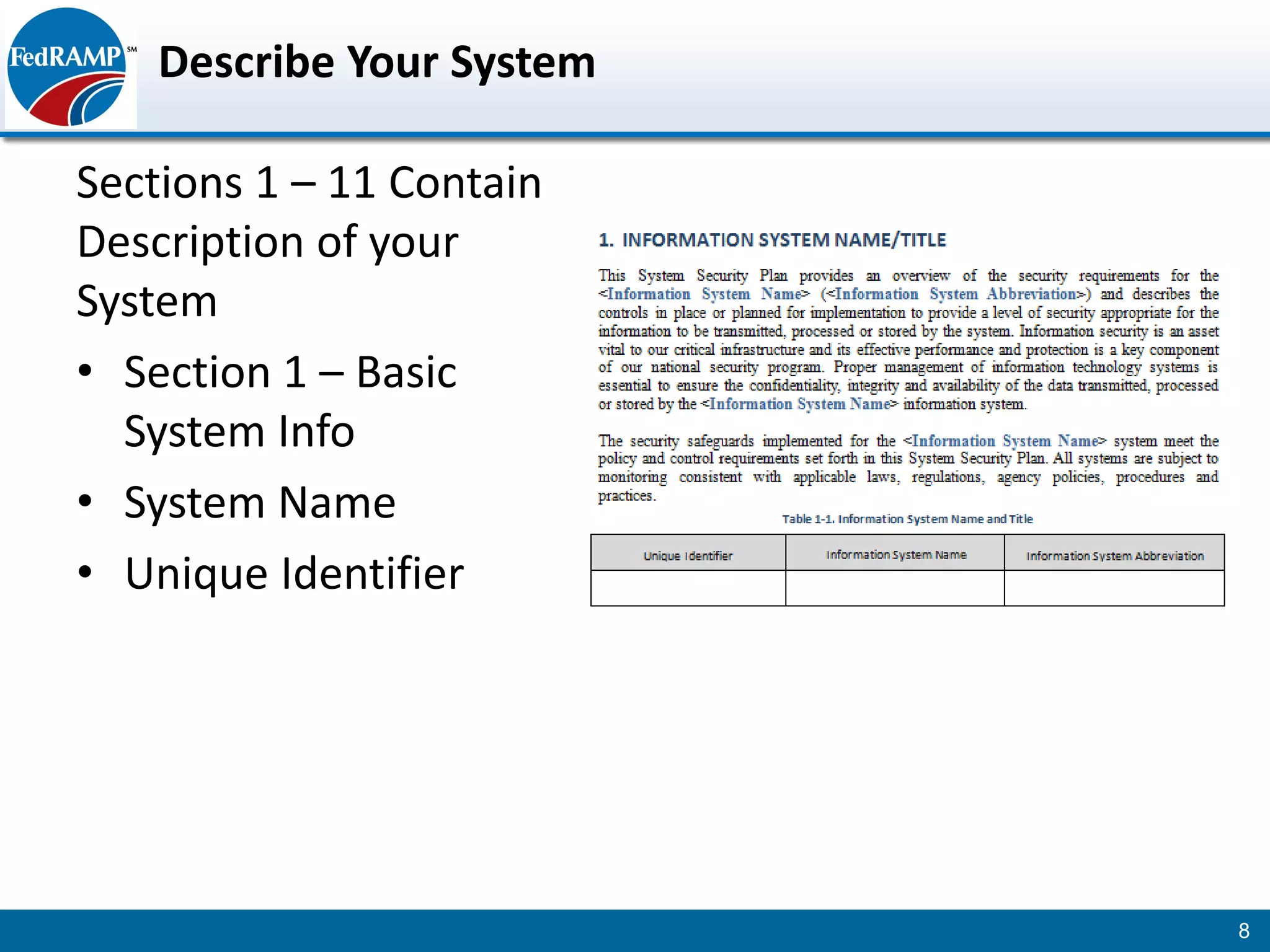
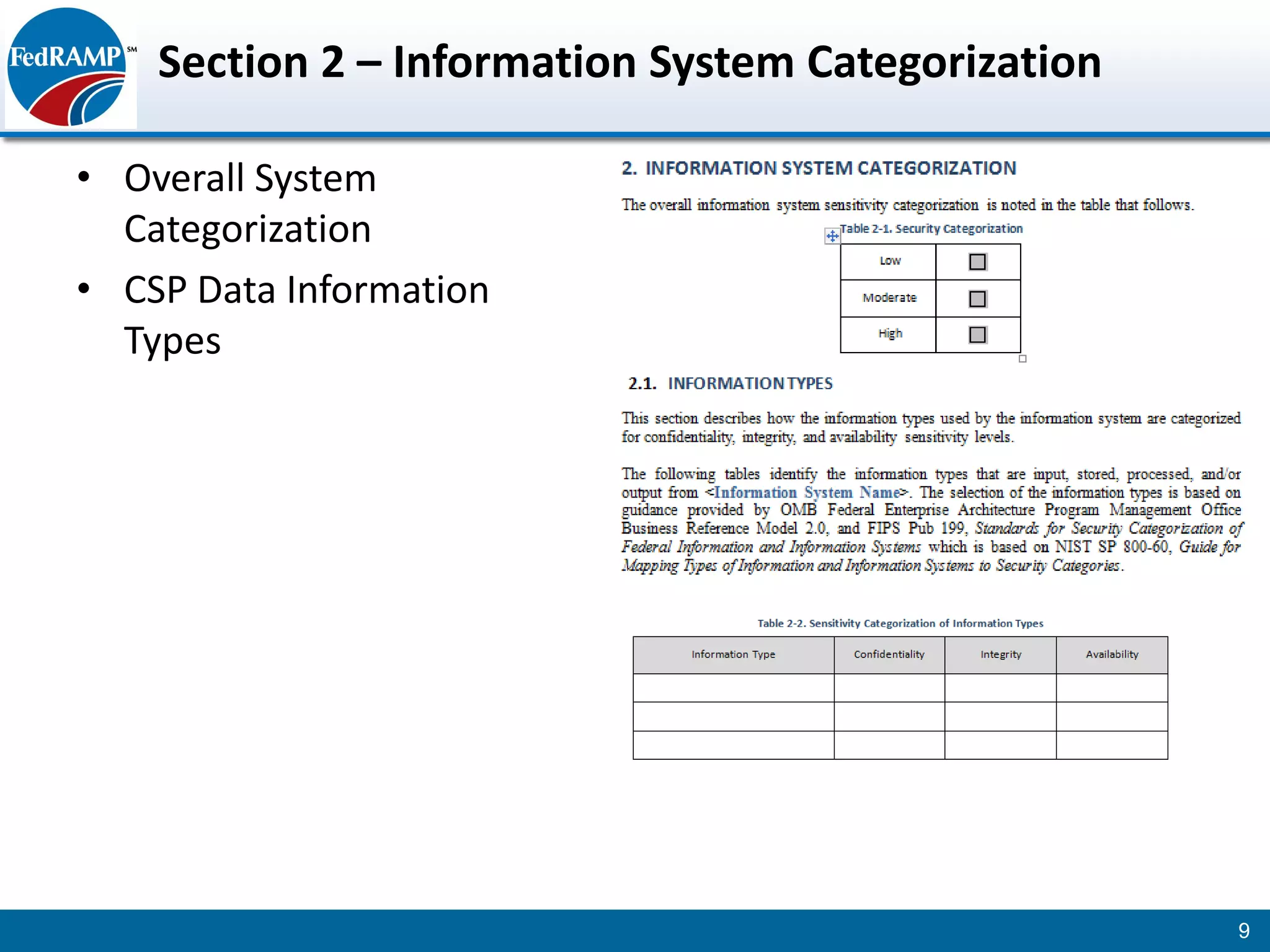
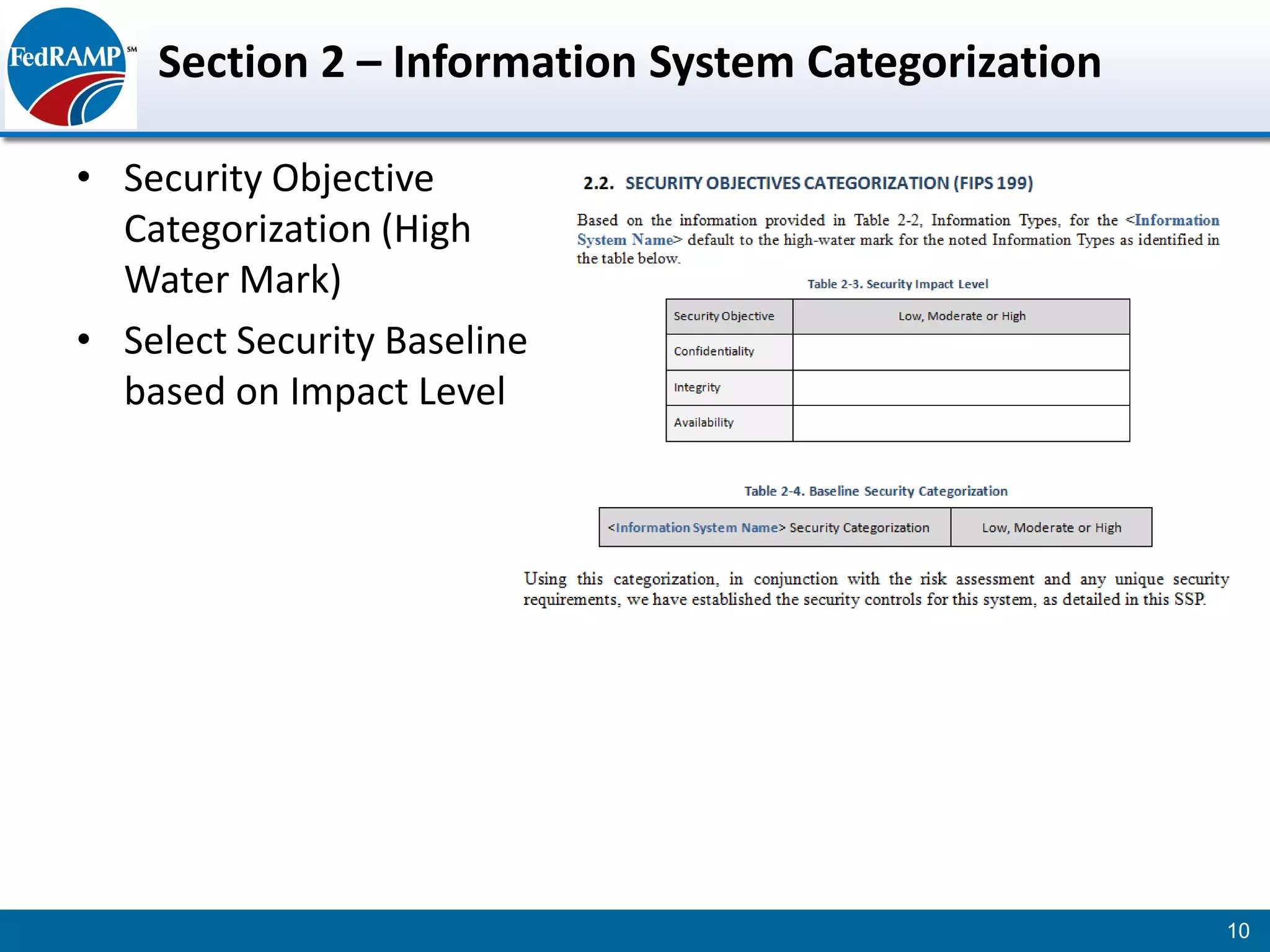
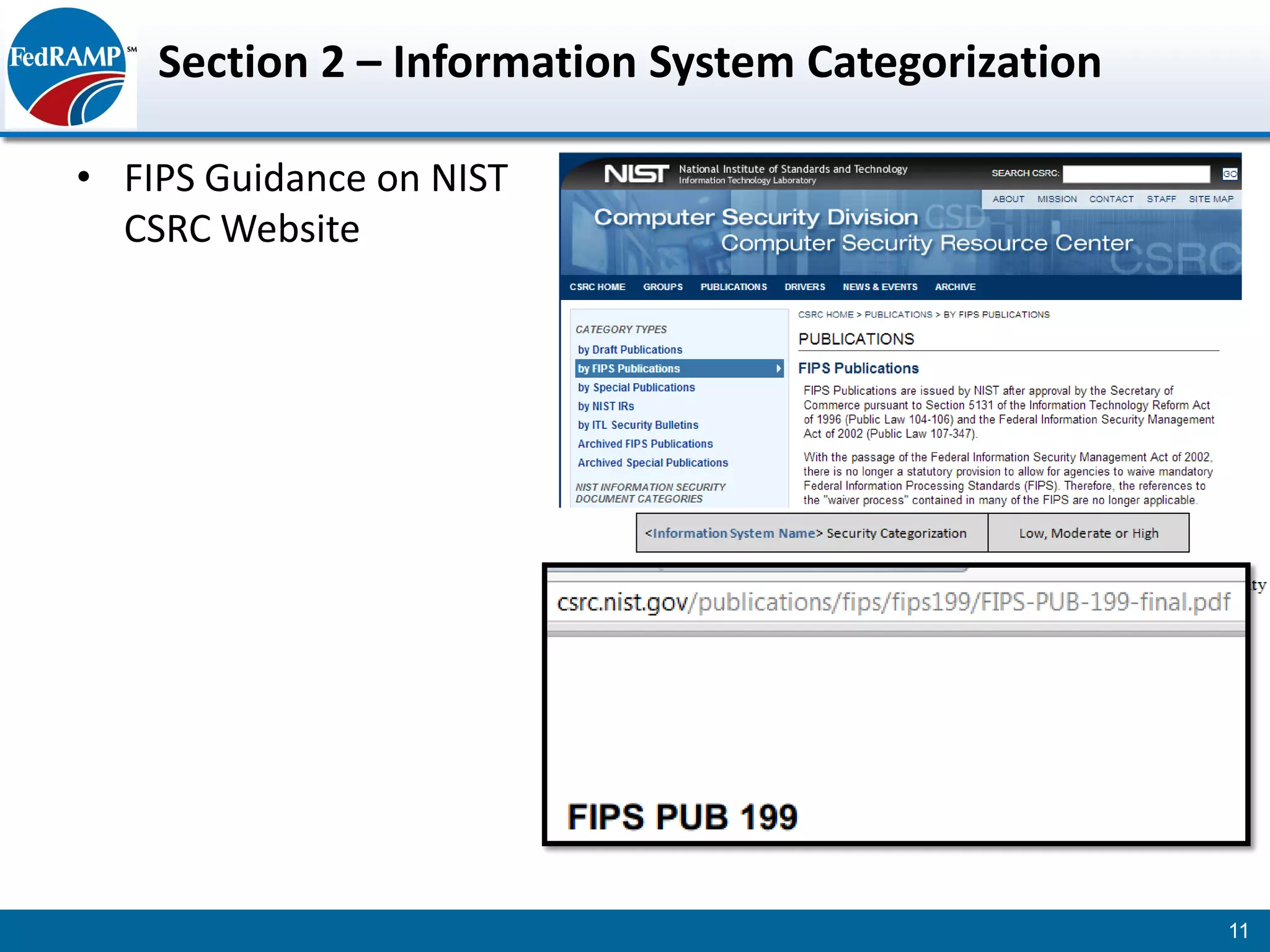
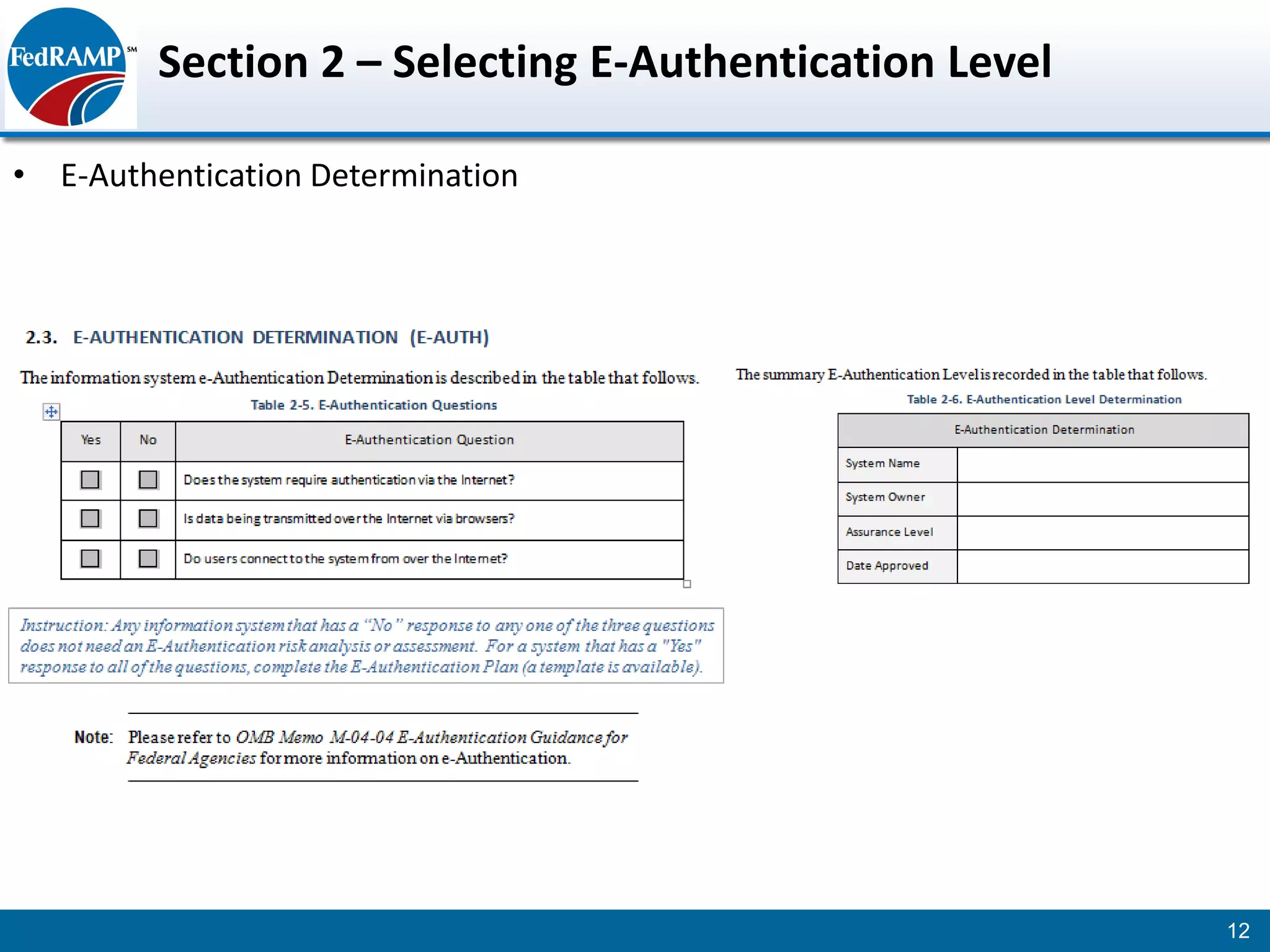
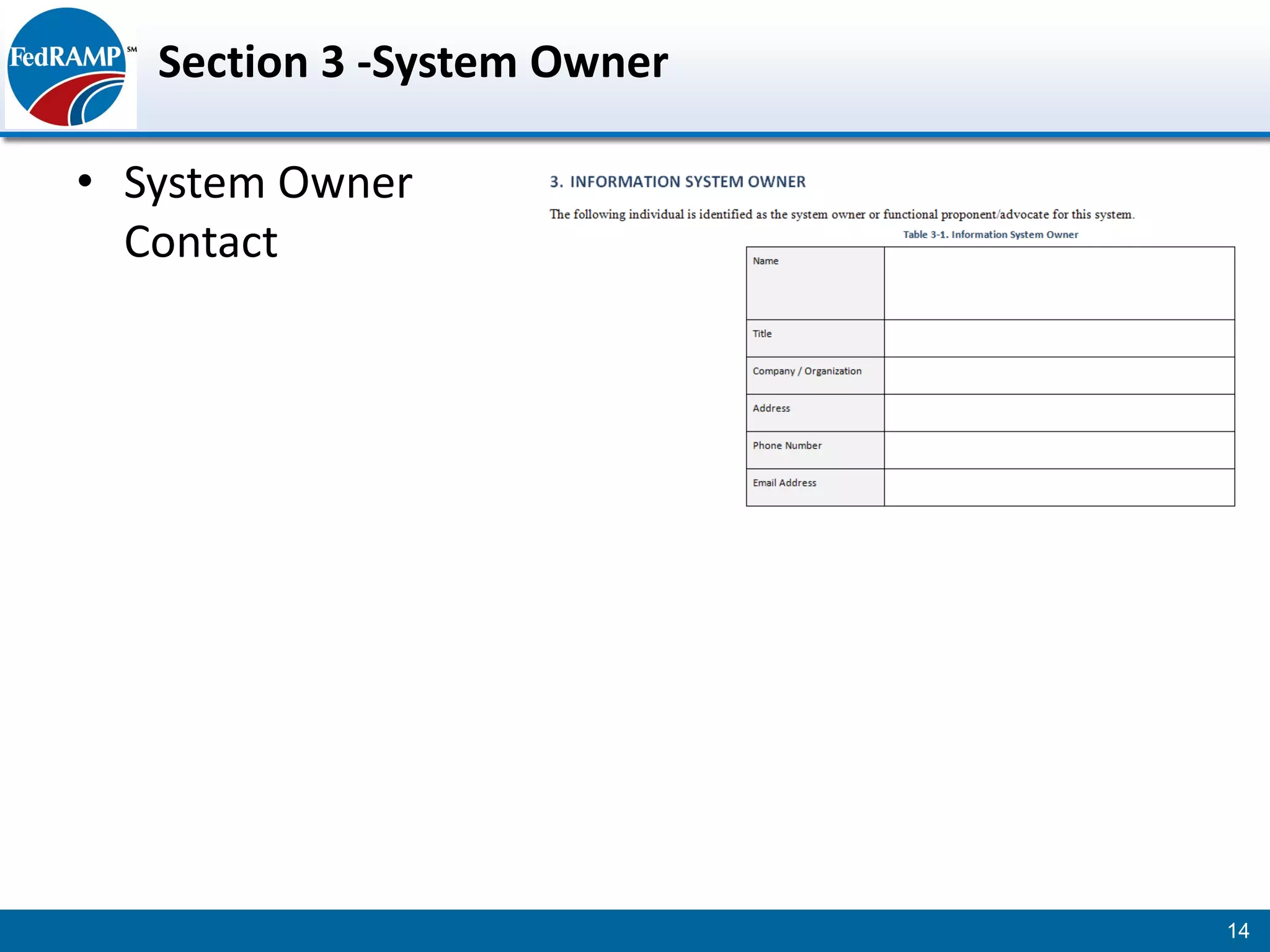
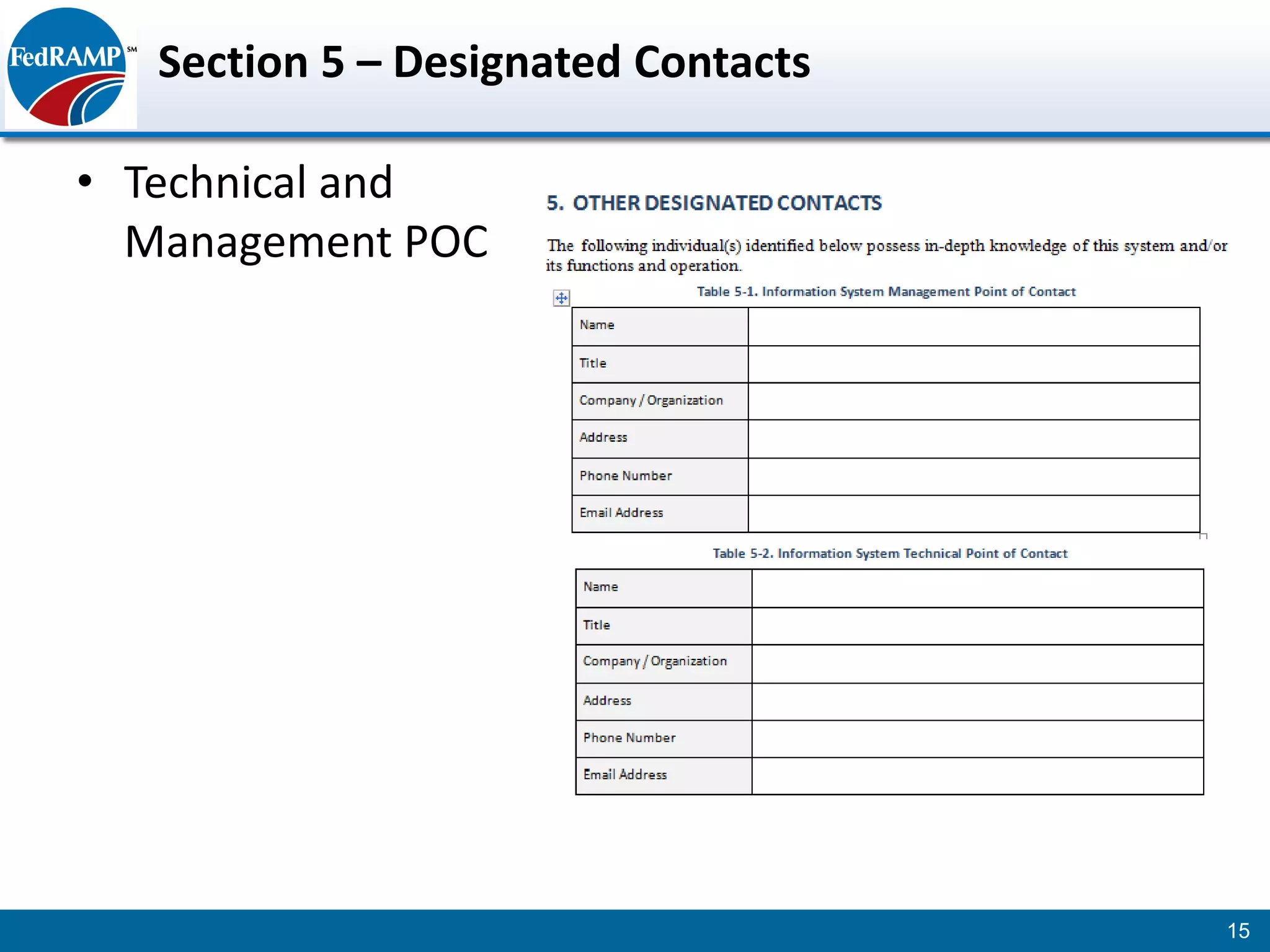
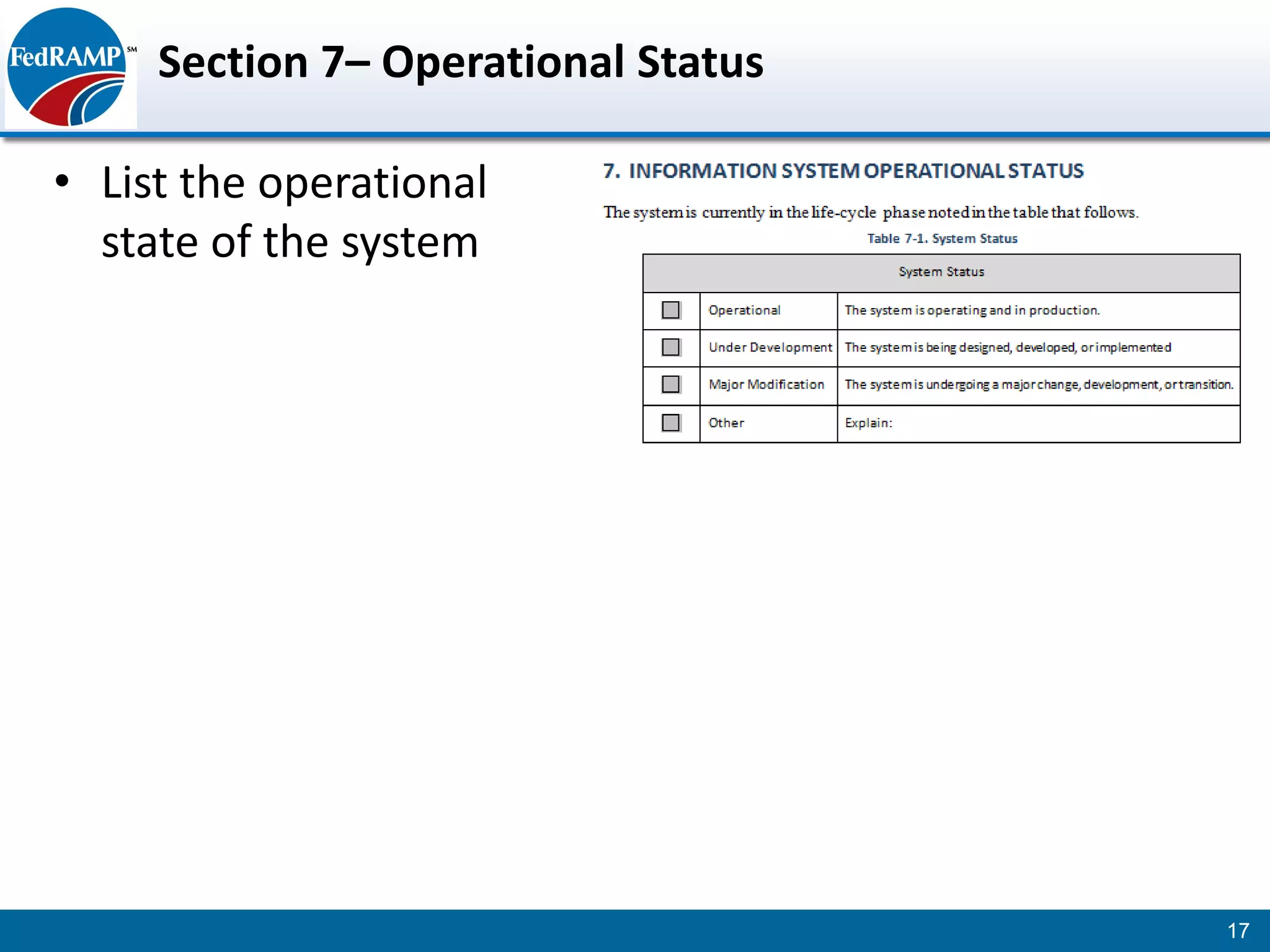
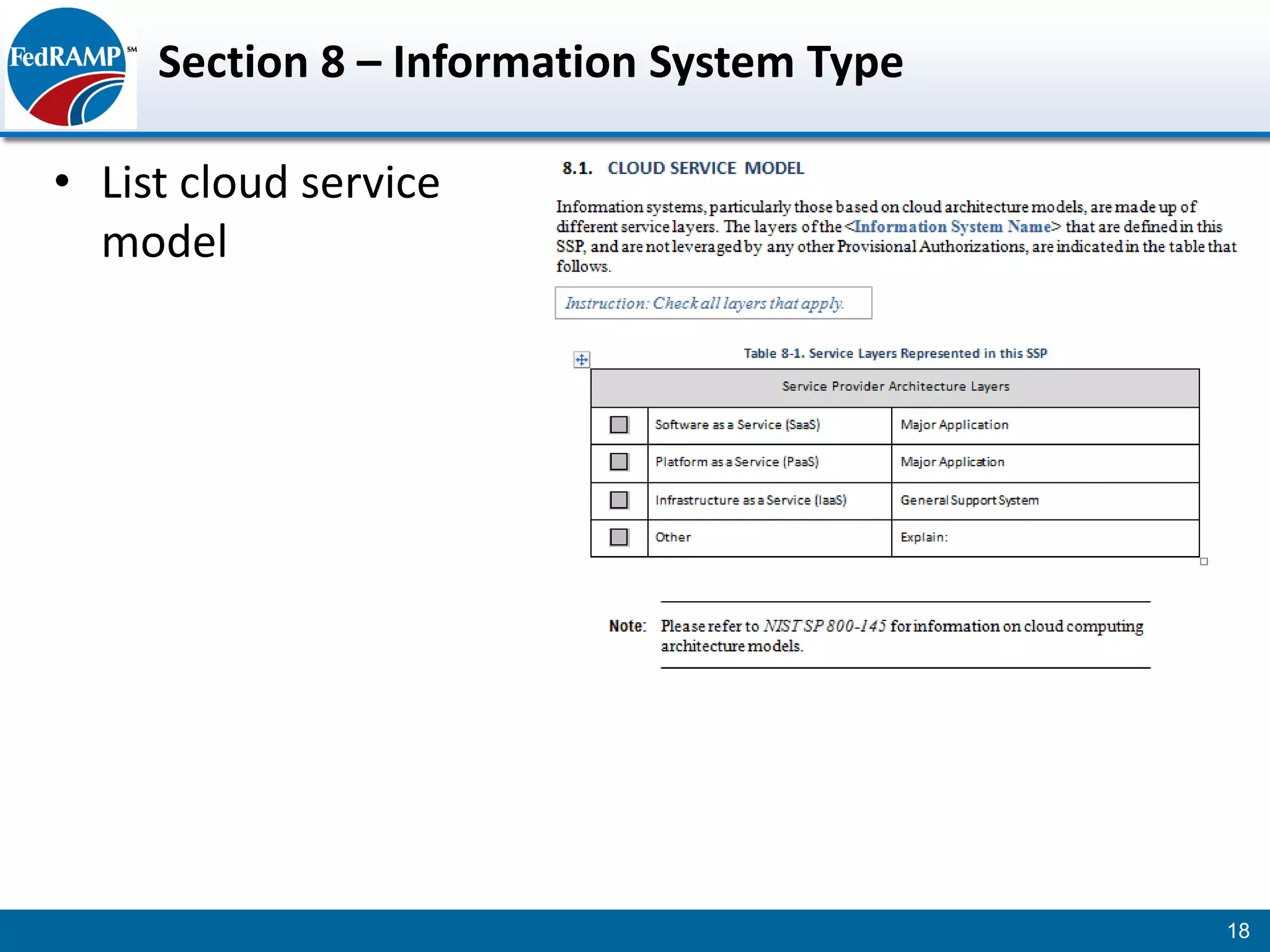
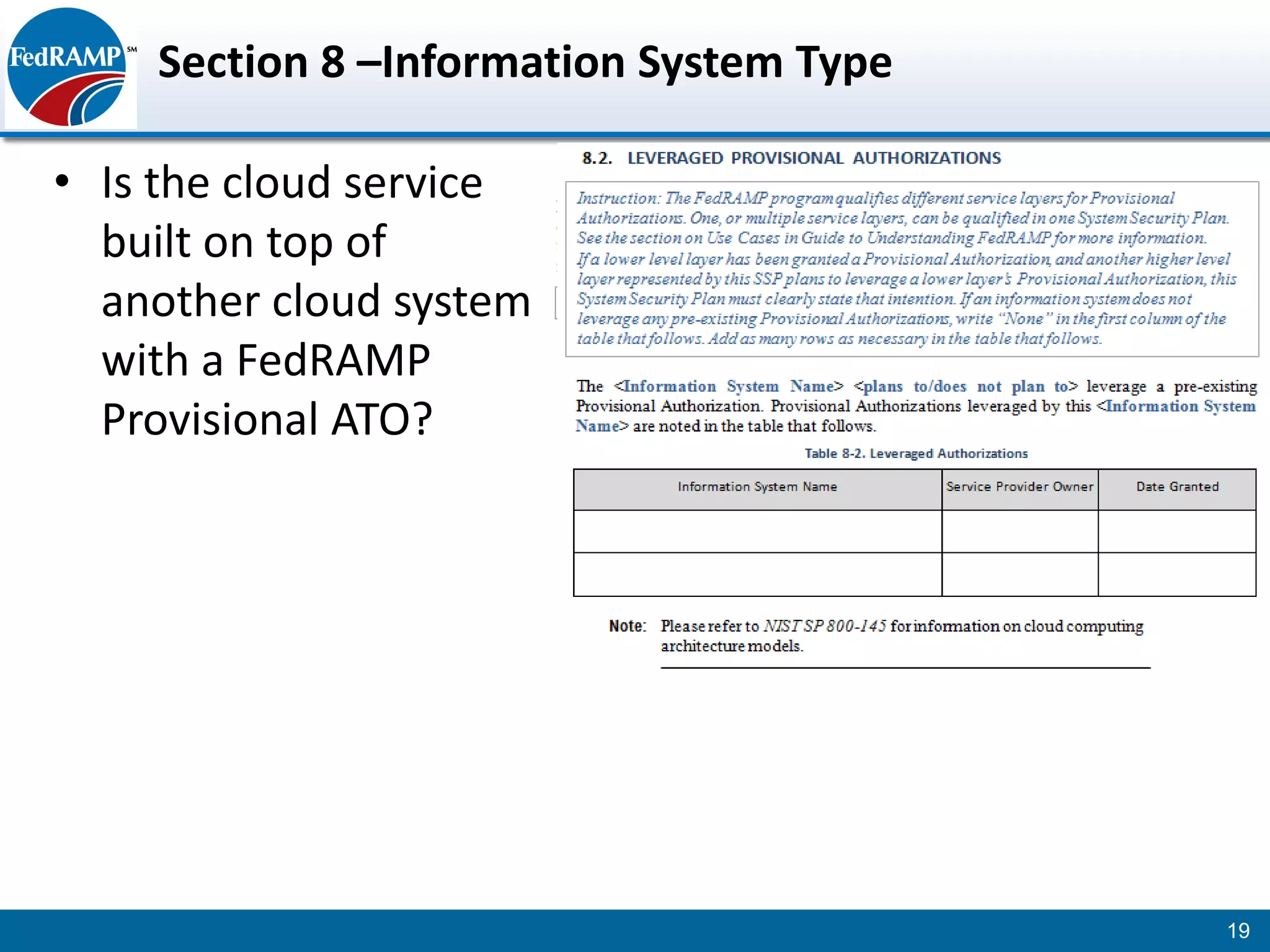
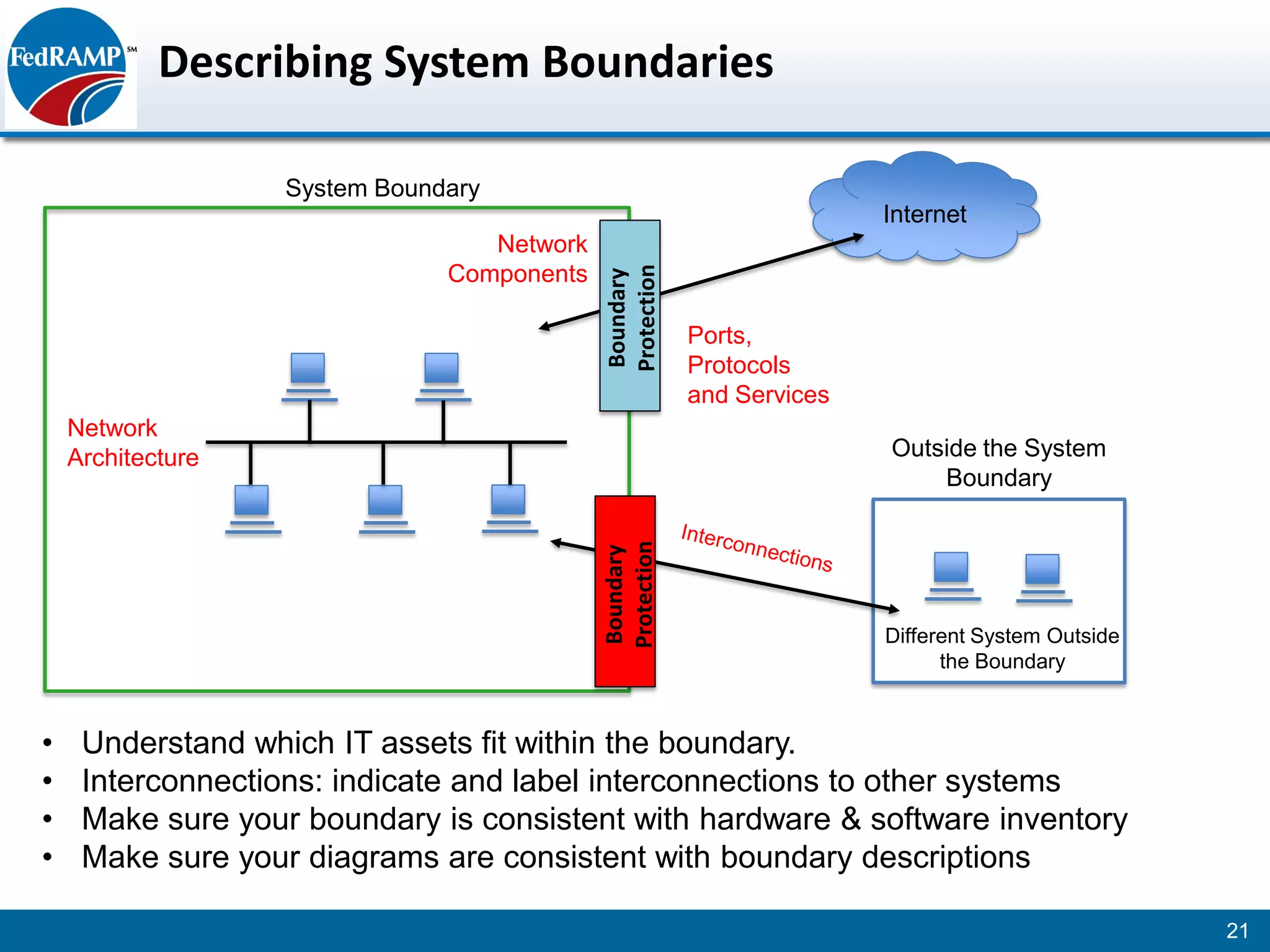
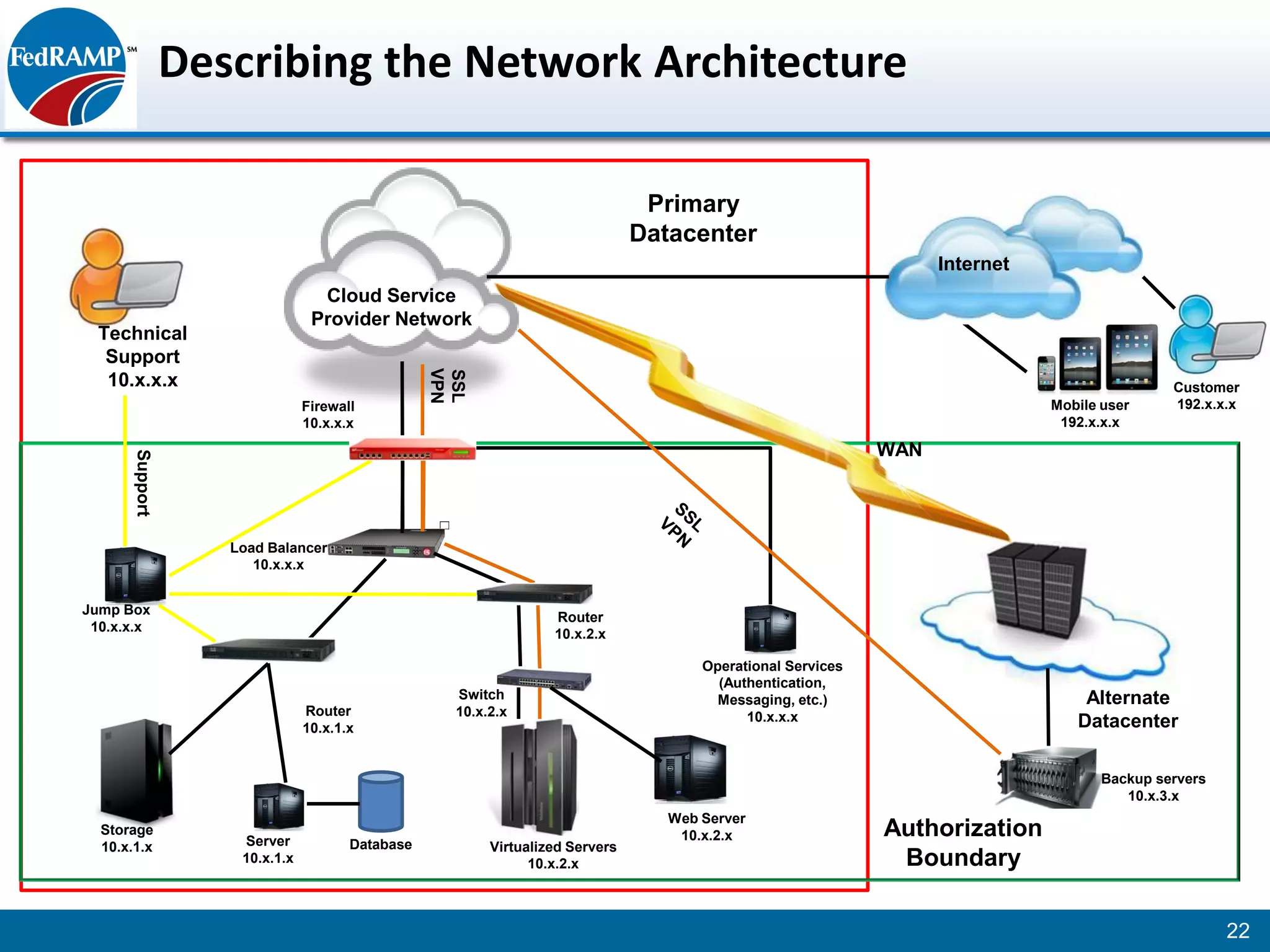
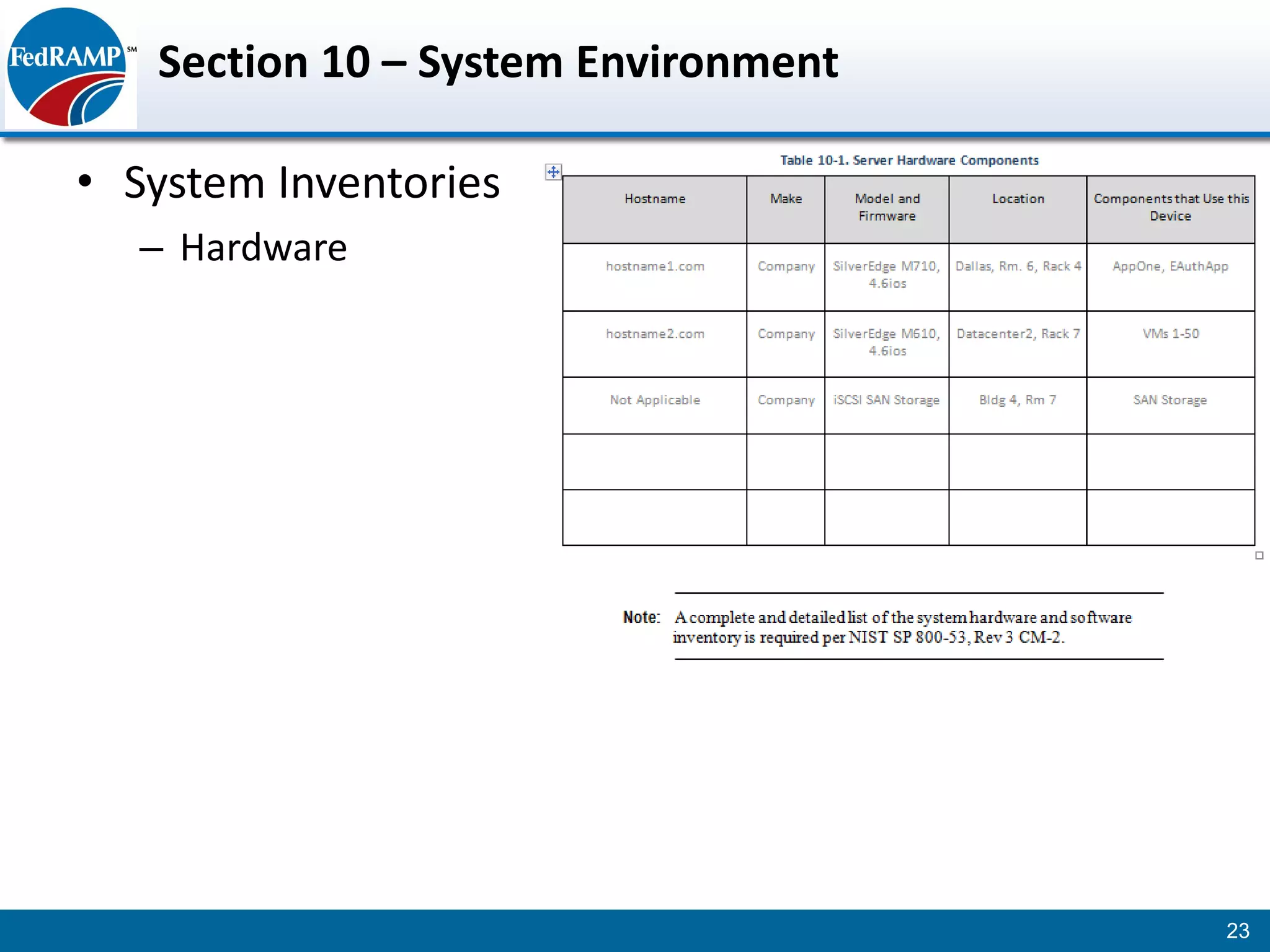
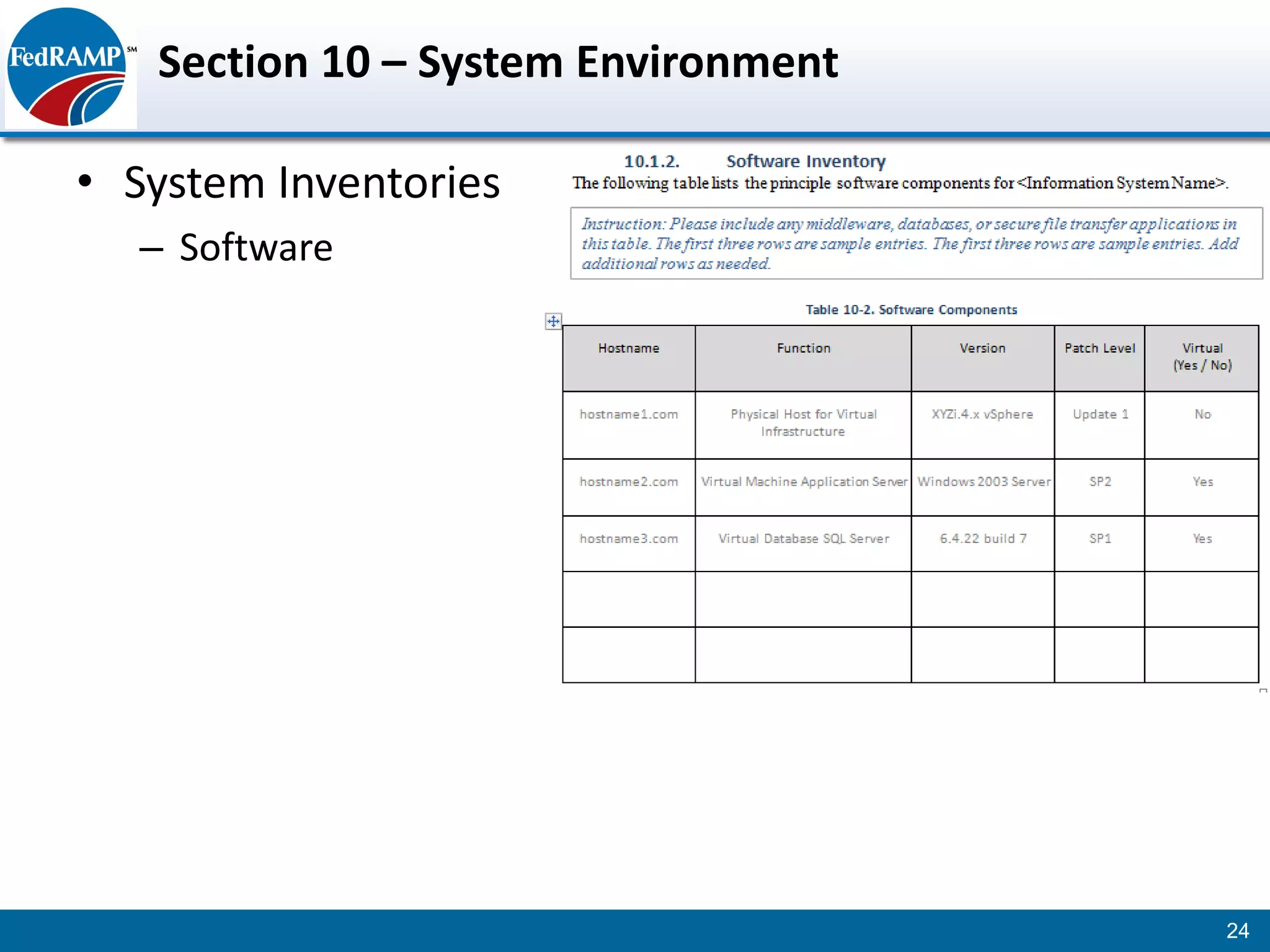
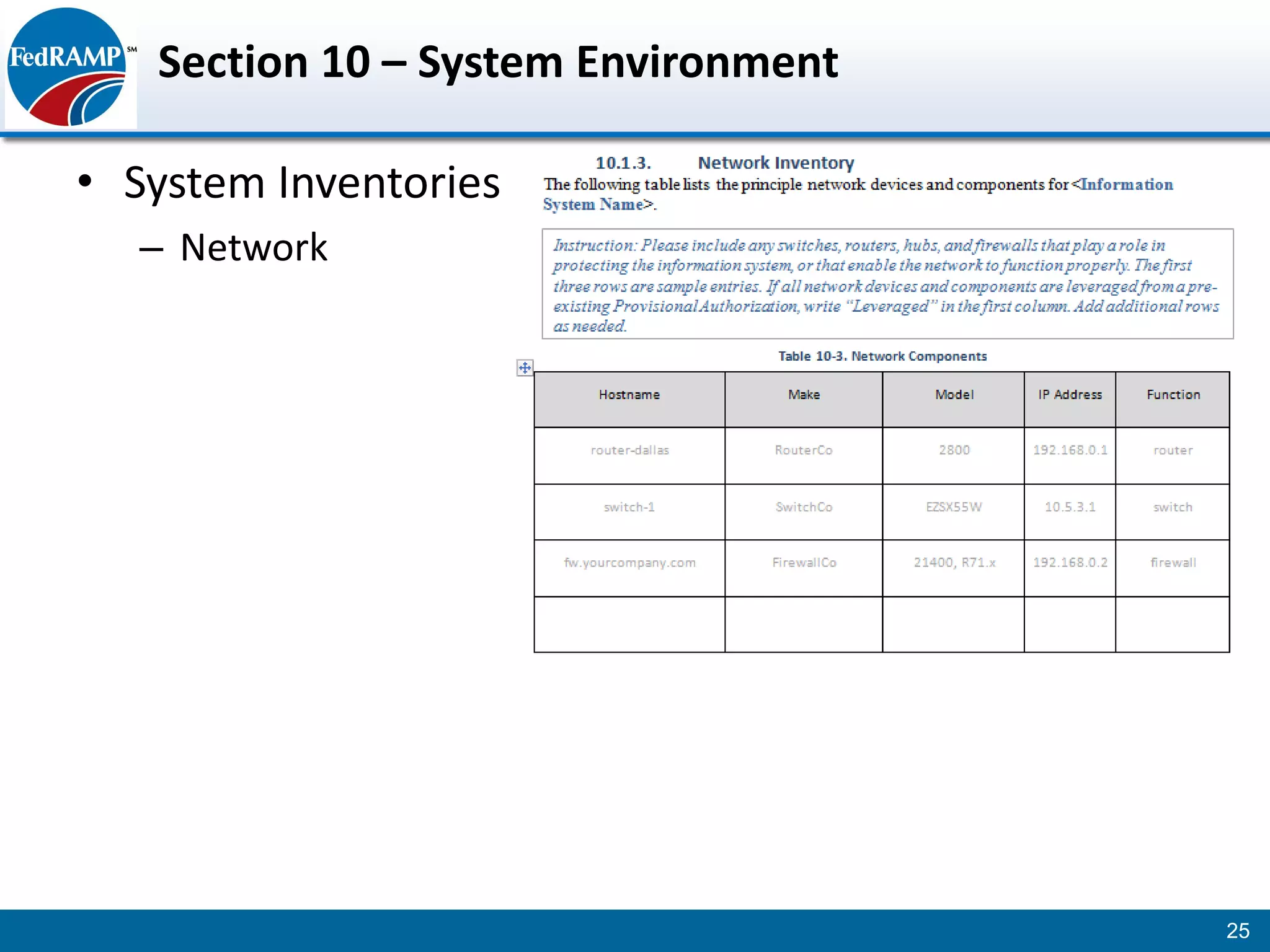
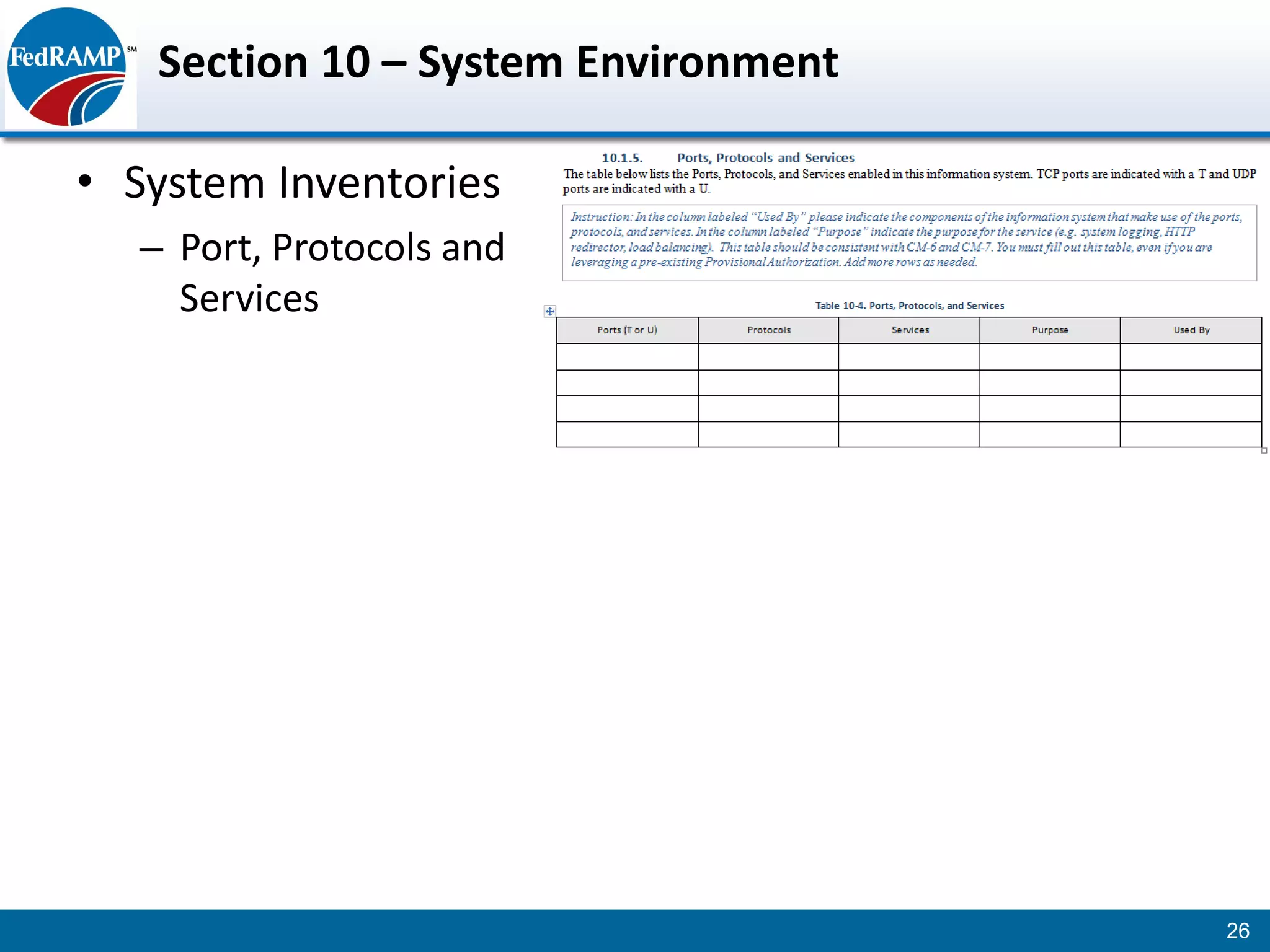
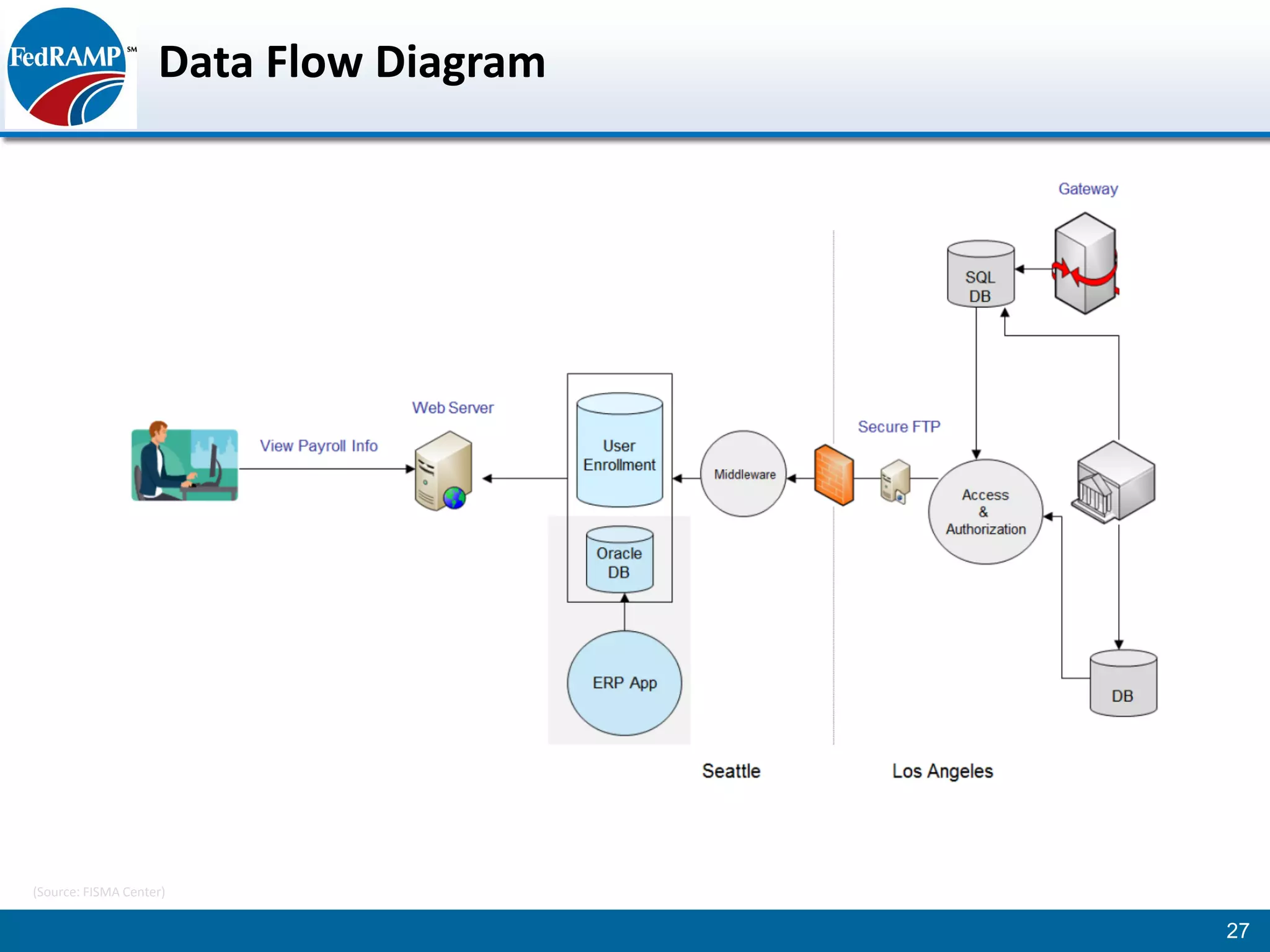
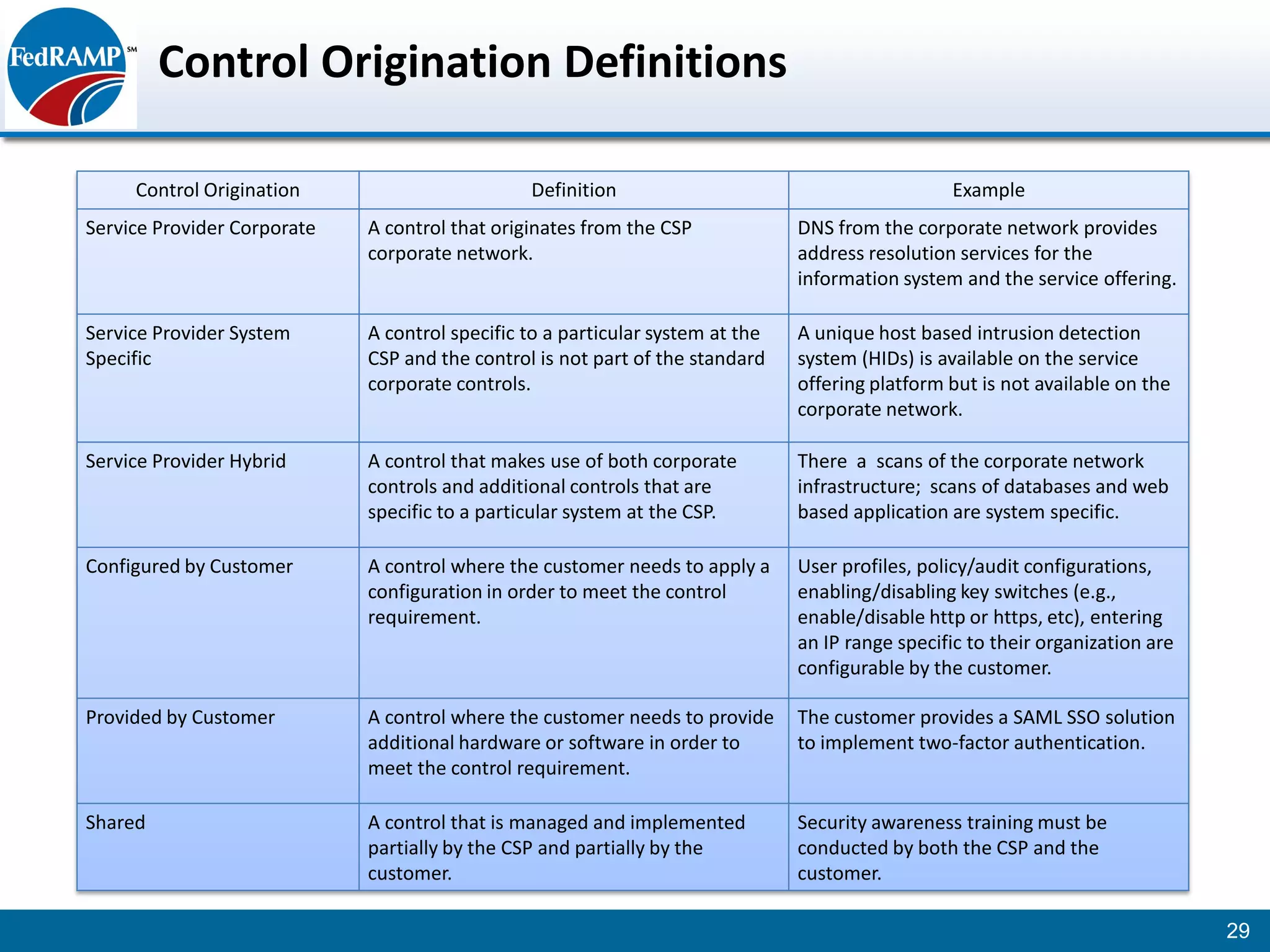
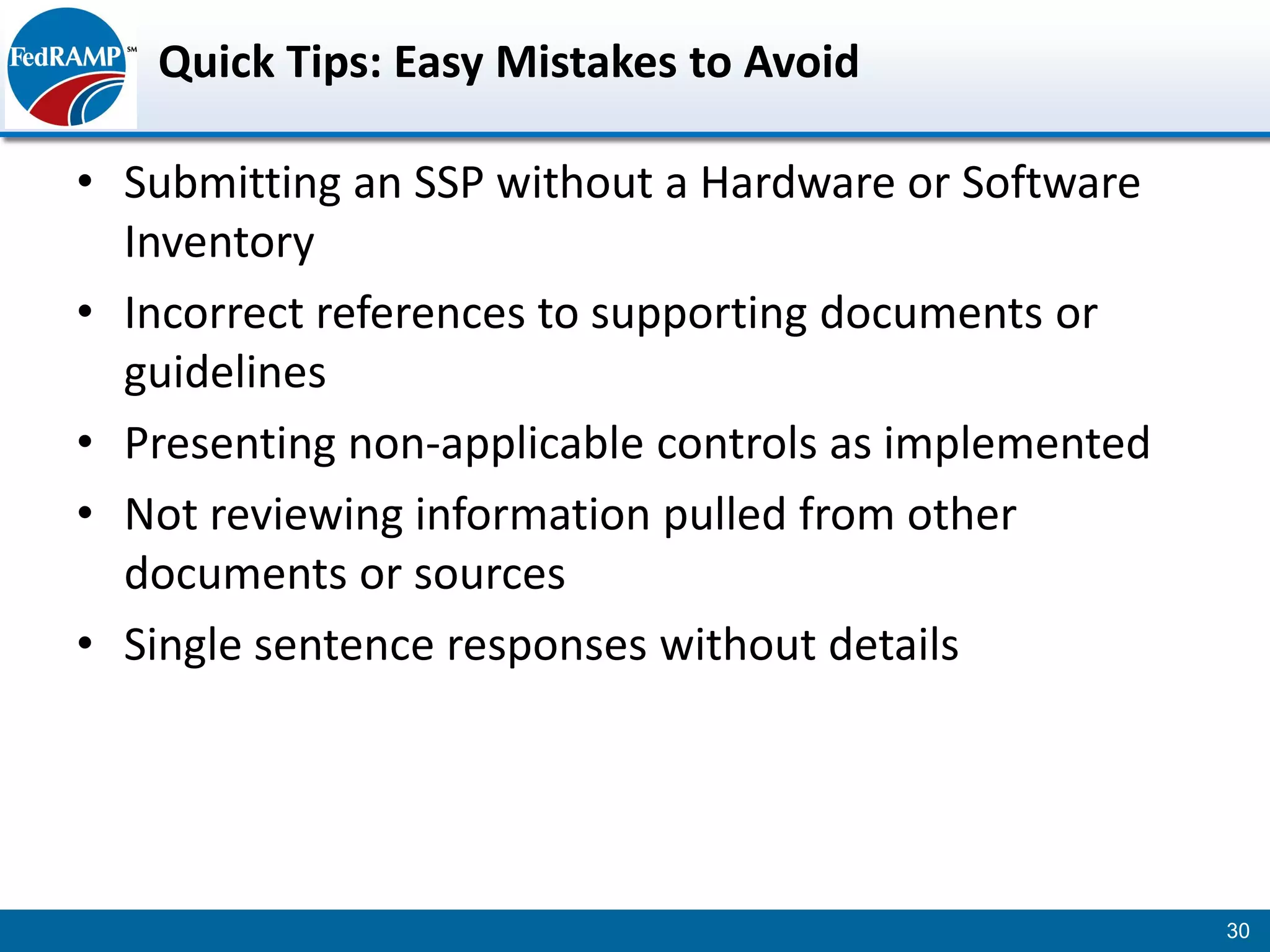
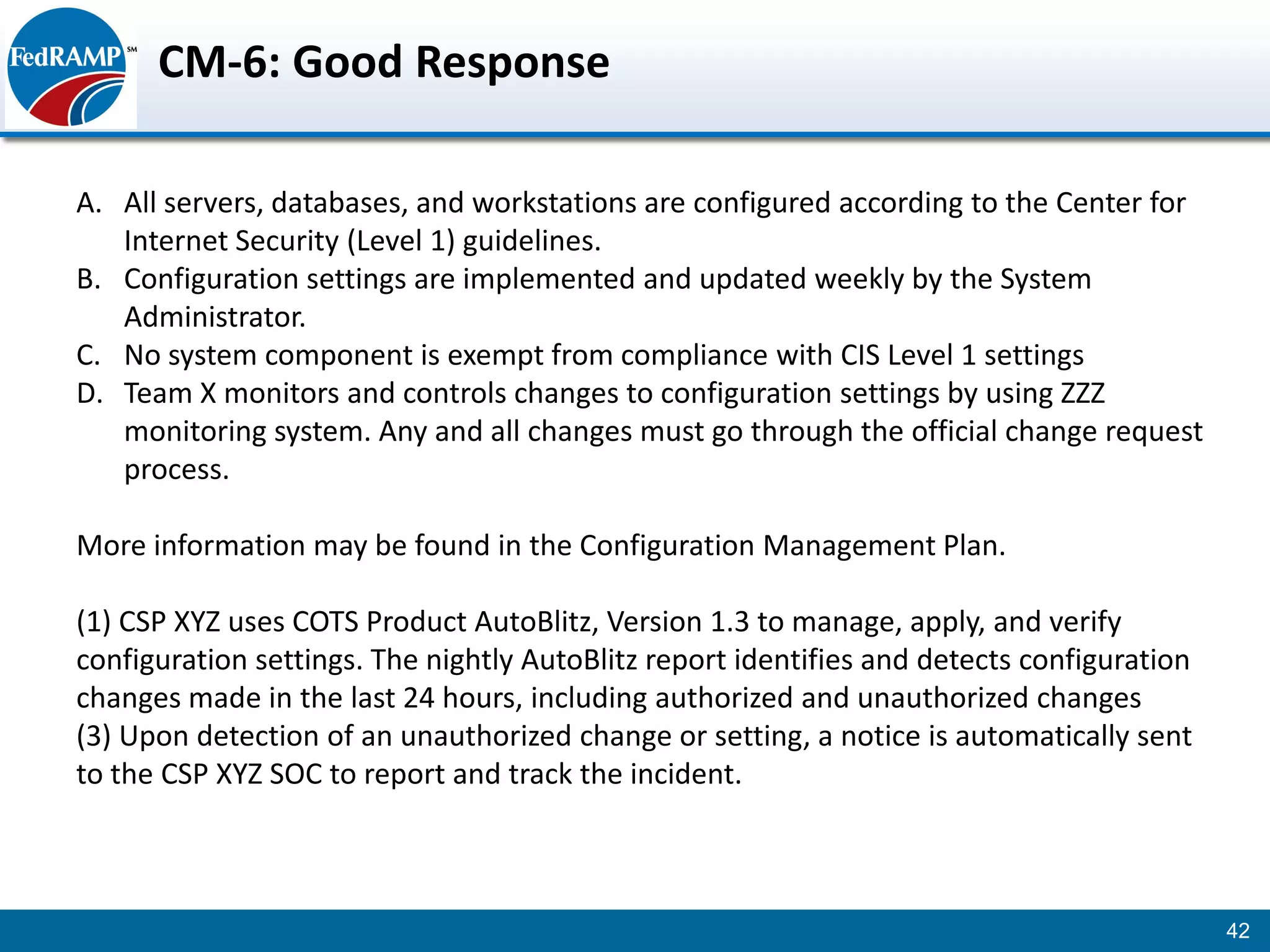
The document discusses developing a System Security Plan (SSP) for the Federal Risk and Authorization Management Program (FedRAMP). The SSP is a detailed document that describes how security controls have been implemented based on NIST SP 800-53. It provides an overview of the system, identifies responsible personnel, and delineates control responsibilities. Developing a thorough SSP can streamline the FedRAMP assessment process. The SSP template is lengthy at 352 pages to fully document the system and control implementation.