C n practical file
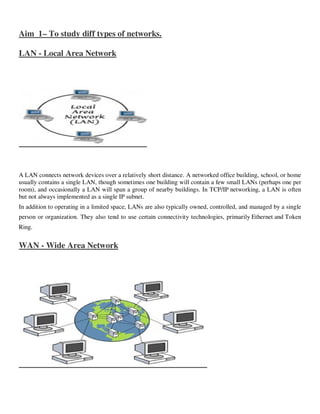
- 1. Aim 1– To study diff types of networks. LAN - Local Area Network A LAN connects network devices over a relatively short distance. A networked office building, school, or home usually contains a single LAN, though sometimes one building will contain a few small LANs (perhaps one per room), and occasionally a LAN will span a group of nearby buildings. In TCP/IP networking, a LAN is often but not always implemented as a single IP subnet. In addition to operating in a limited space, LANs are also typically owned, controlled, and managed by a single person or organization. They also tend to use certain connectivity technologies, primarily Ethernet and Token Ring. WAN - Wide Area Network
- 2. As the term implies, a WAN spans a large physical distance. The Internet is the largest WAN, spanning the Earth. A WAN is a geographically-dispersed collection of LANs. A network device called a router connects LANs to a WAN. In IP networking, the router maintains both a LAN address and a WAN address. A WAN differs from a LAN in several important ways. Most WANs (like the Internet) are not owned by any one organization but rather exist under collective or distributed ownership and management. WANs tend to use technology like ATM, Frame Relay and X.25 for connectivity over the longer distances. Metropolitan Area Network It is a network spanning a physical area larger than a LAN but smaller than a WAN, such as a city. A MAN is typically owned an operated by a single entity such as a government body or large corporation.
- 3. Aim 2- To study diff types topologies used in networking. Topology Topology means how the computers/ nodes are physically connected to each other. Bus topology • Uses a trunk or backbone to which all of the computers on the network connect. • Systems connect to this backbone using T connectors or taps. • Coaxial cablings ( 10Base-2, 10Base5) were popular options years ago. Bus Topology characteristics -Does not use any specialized network to troubleshoot equipment. -A break in the cable will prevent all systems from accessing the network. -Require less cable -Network disruption when computers are added or removed -Cheap and easy to implement Ring Topology • Logical ring – Meaning that data travels in circular fashion from one computer to another on the network. – Typically FDDI, SONET or Token Ring technology are used to implement a ring – Ring networks are most commonly wired in a star configuration • Token Ring has multi-station access unit (MSAU),equivalent to hub or switch. MSAU performs the token circulation internally.
- 4. Ring Topology characteristics -A single break in the cable can disrupt the entire network. -Ring networks are moderately easy to install -Expansion to the network can cause network disruption -Cable faults are easily located, making troubleshooting easier Star Topology • All computers/devices connect to a central device called hub or switch. • Each device requires a single cable • point-to-point connection between the device and hub. • Most widely implemented • Hub is the single point of failure Star Topology characteristics -More difficult -Easy to troubleshoot and isolate to implement problems -A central connecting device allows for a single point of failure -Cable failure affects only a single user -Easily expanded without disruption Requires more cable to the network Mesh Topology
- 5. • Each computer connects to every other. • High level of redundancy. • Rarely used. – Wiring is very complicated – Cabling cost is high – Troubleshooting a failed cable is tricky – A variation hybrid mesh – create point to point connection between specific network devices, often seen in WAN implementation. Mesh Topology characteristics -Complicated -The network can be expanded implementation without disruption to current uses -Requires more cable than the other -LAN topologies Provides redundant paths between devices
- 6. Aim 3: To study various types of guided transmission media in detail. Transmission Media Communication of data propagation and processing of signals is called transmission. Signals travel from transmitter to receiver via a path. This path is called medium. Medium can be guided or unguided. Twisted-Pair Copper Wire The least-expensive and most commonly-used transmission medium is twisted-pair copper wire. For over one-hundred years it has been used by telephone networks. In fact, more than 99% of the wired connections from the telephone handset to the local telephone switch use twisted-pair copper wire. Most of us have seen twisted pair in our homes and work environments. Twisted pair consists of two insulated copper wires, each about 1 mm thick, arranged in a regular spiral pattern:. The wires are twisted together to reduce the electrical interference from similar pairs close by. Typically, a number of pairs are bundled together in a cable by wrapping the pairs in a protective shield. A wire pair constitutes a single communication link. Unshielded twisted pair (UTP) It is commonly used for computer networks within a building, that is, for local area networks (LANs). Data rates for LANs using twisted pair today range from 10 Mbps to 100 Mbps. The data rates that can be achieved depend on the thickness of the wire and the distance between transmitter and receiver. Two types of UTP are common in LANs: category 3 and category 5. Category 3 corresponds to voice-grade twisted pair, commonly found in office buildings.Office buildings are often prewired with two or more parallel pairs of category 3 twisted pair; one pair is used for telephone communication, and the additional pairs can be used for additional
- 7. telephone lines or for LAN networking. 10 Mbps Ethernet, one of the most prevalent LAN types, can use category 3 UTP. Category 5, with its more twists per centimeter and Teflon insulation, can handle higher bit rates. 100 Mbps Ethernet running on category 5 UTP has become very popular in recent years. In recent years, category 5 UTP has become common for preinstallation in new office buildings. When fiber-optic technology emerged in the 1980s, many people disparaged twisted-pair because of its relatively low bit rates. Some people even felt that fiber optic technology would completely replace twisted pair. But twisted pair did not give up so easily. Modern twisted-pair technology, such as category 5 UTP, can achieve data rates of 100 Mbps for distances up to a few hundred meters. Even higher rates are possible over shorter distances. In the end, twisted-pair has emerged as the dominant solution for high-speed LAN networking. Twisted-pair is also commonly used for residential Internet access. We saw that dial-up modem technology enables access at rates of up to 56 Kbps over twisted pair. We also saw that ISDN is available in many communities, providing access rates of about 128 Kbps over twisted pair. We also saw that ADSL (Asymmetric Digital Subscriber Loop) technology has enabled residential users to access the Web at rates in excess of 6 Mbps over twisted pair. Coaxial-Cable Like twisted pair, coaxial cable consists of two copper conductors, but the two conductors are concentric rather than parallel. With this construction and a special insulation and shielding, coaxial cable can have higher bit rates than twisted pair. Coaxial cable comes in two varieties: baseband coaxial cable and broadband coaxial cable. Baseband coaxial cable, also called 50- ohm cable, is about a centimeter thick, lightweight, and easy to bend. It is commonly used in LANs; in fact, the computer you use at work or at school is probably connected to a LAN with either baseband coaxial cable or with UTP. Take a look at the the connection to your computer's interface card. If you see a telephone-like jack and some wire that resembles telephone wire, you are using UTP; if you see a T-connector and a cable running out of both sides of the T- connector, you are using baseband coaxial cable. The terminology "baseband" comes from the fact that the stream of bits is dumped directly into the cable, without shifting the signal to a different frequency band. 10 Mbps Ethernets can use either UTP or baseband coaxial cable. It is
- 8. a little more expensive to use UTP for 10 Mbps Ethernet, as UTP requires an additional networking device, called a hub. Broadband coaxial cable, also called 75-ohm cable, is quite a bit thicker, heavier, and stiffer than the baseband variety. It was once commonly used in LANs and can still be found in some older installations. For LANs, baseband cable is now preferable, since it is less expensive, easier to physically handle, and does not require attachment cables. Broadband cable, however, is quite common in cable television systems. With broadband coaxial cable, the transmitter shifts the digital signal to a specific frequency band, and the resulting analog signal is sent from the transmitter to one or more receivers. Both baseband and broadband coaxial cable can be used as a guided shared medium. Specifically, a number of end systems can be connected directly to the cable, and all the end systems receive whatever any one of the computers transmits. Fiber Optics
- 9. An optical fiber is a thin, flexible medium that conducts pulses of light, with each pulse representing a bit. A single optical fiber can support tremendous bit rates, up to tens or even hundreds of gigabits per second. They are immune to electromagnetic interference, have very low signal attenuation up to 100 kilometers, and are very hard to tap. These characteristics have made fiber optics the preferred long-haul guided transmission media, particularly for overseas links. Many of the long-distance telephone networks in the United States and elsewhere now use fiber optics exclusively. Fiber optics is also prevalent in the backbone of the Internet. However, the high cost of optical devices -- such as transmitters, receivers, and switches – has hindered their deployment for short-haul transport, such as in a LAN or into the home in a residential access network. AT&T Labs provides an excellent site on fiber optics, including several nice animations.
- 10. Aim 4: To study various types of connectors used in computer networks. Connectors used in Computer Networks – A connector is best known for providing the physical link between two components. The use of a connector might be a connector linking a cable and a network interface card or NIC card, a connector linking a transceiver and a cable or even a connector linking two cable segments. There are various types of connectors used for different transmission media such as – 1. RJ – 45 A registered jack (RJ) is a standardized physical network interface — both jack construction and wiring pattern — for connecting telecommunications or data equipment to a service provided by a local exchange carrier or long distance carrier. The physical connectors that registered jacks use are mainly of the modular connector and 50-pin miniature ribbon connector types. RJ45 is a registered jack standard for a modular connector using 8 conductors, which specifies the physical male and female connectors as well as the pin assignments of the wires in a telephone cable. The "RJ45" physical connector is standardized as the IEC 60603-7 8P8C modular connector with different "categories" of performance, with all eight conductors present but 8P8C is commonly known as RJ45. The physical dimensions of the connectors are specified in ANSI/TIA-1096-A and ISO-8877 standards. 2. BNC The BNC connector (Bayonet Neill–Concelman) is a common type of RF connector used for coaxial cable. It is used with radio, television, and other radio-frequency electronic equipment, test instruments, video signals, and was once a popular computer network connector. BNC connectors are made to match the characteristic impedance of cable at either 50 ohms or 75 ohms. It is usually applied for frequencies below 3 GHz and voltages below 500 Volts. The BNC connector is used for signal connections such as: 1. analog and serial digital interface video signals 2. amateur radio antennas 3. aviation electronics (avionics) 4. test equipment.
- 11. 3. SC Connector SC stands for Subscriber Connector- a general purpose push/pull style Connector developed by NTT. SC has an advantage in keyed duplexibility to support send/receive channels. SC Connectors are frequently used for newer Network applications. The SC is a snap-in connector that is widely used in singlemode systems for its performance. The SC connector is also available in a Duplex configuration. They offer low cost, simplicity, and durability. SC connectors provide for accurate alignment via their ceramic ferrules. The square, snap-in connector latches with a simple push- pull motion and is keyed. They feature a 2.5mm Ferrule and molded housing for protection. Typical matched SC connectors are rated for 1000 mating cycles and have an Insertion Loss of 0.25 dB. 4. ST Connector ST stands for Straight Tip - a quick release bayonet style Connector developed by AT&T. STs were predominant in the late 80s and early 90s. ST Connectors are among the most commonly used Fiber optic connectors in networking applications. They are cylindrical with twist lock coupling, 2.5mm keyed ferrule. ST Connectors are used both short distance applications and long line systems. The ST connector has a bayonet mount and a long
- 12. cylindrical Ferrule to hold the fiber. Because they are spring-loaded, you have to make sure they are seated properly. They are easily inserted and removed due to their design. If you experience high Light loss, try reconnecting. ST connectors come in two versions: ST and ST-II. These are keyed and spring- loaded. They are push-in and twist types. They are rated for 500 mating cycles. The typical Insertion Loss for matched ST connectors is 0.25 dB. 5. MT-RJ Connector MT-RJ stands for Mechanical Transfer Registered Jack. MT-RJ is a fiber-optic Cable Connector that is very popular for small form factor devices due to its small size. Housing two fibers and mating together with locating pins on the plug, the MT-RJ comes from the MT connector, which can contain up to 12 fibers. The MT-RJ is one of the newly emerging small form factor connectors that are becoming more common in the networking industry. The MT-RJ utilizes two fibers and integrates them into a single design that looks similar to a RJ45 connector. Alignment is completed through the use of two pins that mate with the connector. Transceiver jacks found on NICs and equipment typically have the pins built into them. The MT-RJ is commonly used for networking applications. Its size is slightly smaller than a standard phone jack and just as easy to connect and disconnect. It's half the size of the SC Connector it was designed to replace. The MT-RJ connector is a small form-factor Fiber optic connector which resembles the RJ-45 connector used in Ethernet networks. Compared to single-fiber terminations such as SC, the MT-RJ Connector offers lower Termination cost and greater density for both electronics and cable management hardware. The MT-RJ Connector is significantly lower in cost and smaller in size than the SC Duplex interface. The small MT-RJ Interface can be spaced the same as copper, effectively doubling the number of fiber ports. The net effect is a Drop in the overall price per fiber Port making fiber-to-the- desktop solutions more competitive with copper
- 13. Aim 5: To study diff. types of protocols in tcp/ip suit TCP/IP Protocol Suite The TCP/IP model is a descriptive framework for computer network protocols created in the 1970s by DARPA, an agency of the United States Department of Defense. The name derives from the two most important protocols of the networking protocol suite, the Transmission Control Protocol (TCP) and the Internet Protocol (IP). The model evolved from the operational principles of the ARPANET, which was an early wide area network and a predecessor of the Internet. The TCP/IP model is formalized in the Internet protocol suite and is sometimes called the Internet model or the DoD model. The TCP/IP model describes a set of general design guidelines and implementations of specific networking protocols to enable computers to communicate over a network. TCP/IP provides end-to-end connectivity specifying how data should be formatted, addressed, transmitted, routed and received at the destination. Protocols exist for a variety of different types of communication services between computers. TCP/IP has four abstraction layers as defined in RFC 1122, The TCP/IP model and related protocols are maintained by the Internet Engineering Task Force (IETF). User Datagram Protocol The User Datagram Protocol is very simple. The PDU used by UDP is called a datagram. Datagrams are considered unreliable,in that there is no guarantee datagrams will be received in the correct order, if at all. If reliability of the information transmitted is needed, UDP should not be used.While UDP is unreliable, the lack of error checking and correction make UDP fast and effic -ient for many less data intensive or timesensitive applications, such as the Domain Name Service (DNS), the Simple Network Management Protocol (SNMP),
- 14. the Dynamic Host Configuration Protocol (DHCP) and the Routing InformationProtocol (RIP). UDP is also well suited for streaming video. Transmission Control Protocol In the TCP/IP protocol suite, TCP is the intermediate layer between IP below it, and an application above it. Using TCP, applications on networked hosts can establish reliable connections to one another. The protocol guarantees in-order delivery of data from the sender to the receiver. Both tcp and udp works on port no.from range.0-32768. TCP connections have three phases: 1. Connection establishment 2. Data transfer 3. Connection termination • File Transfer Protocol (FTP)— It works on port no.21. Provides a mechanism for moving data files between systems. The FTP client and server programs, as well as most Web browsers, contain an implementation of the FTP protocol. • HyperText Transfer Protocol (HTTP)— It works on port no. 80.Protocol used to move Web pages across an internet connection. The HTTP protocol is built into Web browsers and Web servers. • Interactive Mail Access Protocol (IMAP)— It works on port no. 143.Provides clients access to e-mail messages and mailboxes over a network. It is incorporated into e-mail applications. • Post Office Protocol (POP)— It works on port no. 110.Allows clients to read and remove e-mail residing on a remote server. It is incorporated into e-mail applications. • Remote Login (Rlogin)— Provides network remote login capability. • Simple Mail Transfer Protocol (SMTP)— It works on port no. 25.Used to deliver email from one system to another. It is incorporated into email applications. • Secure Shell (SSH)—Provides remote access to computers while providing encryption of the data. • Telnet— It works on port no. 23.Provides network terminal, or remote login capability. The Internet Protocol (IP) It is a data-oriented protocol used for communicating data across a network. It is a best effort protocol; it does not guarantee delivery. It also makes no guarantee as to the correctness of the data it transports. Transmission using IP may result in duplicated packets and/or packets out-of-order. All of these contingencies are addressed by an upper layer protocol (For example, TCP) for applications that require reliable delivery. Address Resolution Protocol The Address Resolution Protocol is a method for translating between Internet layer and network layer address. The ARP module in a computer or router maintains a translation table of logical to physical mappings it is aware of, called the ARP cache. If there is not a translation for the address in the table, it will make an ARP broadcast. RARP (Reverse Address Resolution Protocol)
- 15. It is a protocol by which a physical machine in a local area network can request to learn its IP address from a gateway server's Address Resolution Protocol (ARP) table or cache. A network administrator creates a table in a local area network's gateway router that maps the physical machine (or Media Access Control - MAC address) addresses to corresponding Internet Protocol addresses. When a new machine is set up, its RARP client program requests from the RARP server on the router to be sent its IP address. Assuming that an entry has been set up in the router table, the RARP server will return the IP address to the machine which can store it for future use. A reverse address resolution protocol (RARP) is used for diskless computers to determine their IP address using the network. Internet Control Message Protocol (ICMP) It works on port no. 113. The Internet Control Message Protocol (ICMP) is a helper protocol that supports IP with facility for: – Error reporting – Simple queries • ICMP messages are encapsulated as IP datagrams Internet Group Management Protocol (IGMP) It works on port no.119. It work on It is a communications protocol used by hosts and adjacent routers on IP networks to establish multicast group memberships .IGMP is an integral part of the IP multicast specification. It is analogous to ICMP for unicast connections. IGMP can be used for online streaming video and gaming, and allows more efficient use of resources when supporting these types of applications. IGMP is used on IPv4 networks. Multicast management on IPv6 networks is handled by Multicast Listener Discovery (MLD) which uses ICMPv6 messaging contrary to IGMP's bare IP encapsulation. The Point-to-Point Protocol (PPP)- It is commonly used to establish a direct physical connection between two nodes. It can connect hosts using serial cable, phone lines, cellular phones, radio links, or fiber optic cables. Most dial-up internet service providers use PPP for customer access to the Internet Various Protocols with respective Port Numbers. Sno. Protocol Port number 1. TCPMUX 1 2. FTP Data Transfer 20 3. FTP Control 21 4. Telnet 23 5. SMTP 25 6. IMP 51 7. DHCP Server 67 8. DHCP Client 68 9. HTTP 80 10. POP2 109 11. POP3 110 12. IRC 113 13. NNTP 119 14. NTP 123 15. IMAP 143 16. SGMP (Simple Gateway Monitoring Protocol) 153 17. SNMP 161 18. IRC 194 19. IMAP v3 220
- 16. 20. HTTPS 443 21. RIP 520 22. DNS 953
- 18. Aim 6 :Discuss the working of E-Mail . E-Mail Electronic mail, commonly known as email or e-mail, is a method of exchanging digital messages from an author to one or more recipients. Modern email operates across the Internet or other computer networks. Some early email systems required that the author and the recipient both be online at the same time, in common with instant messaging. Today's email systems are based on a store-and-forward model. Email servers accept, forward, deliver and store messages. Neither the users nor their computers are required to be online simultaneously; they need connect only briefly, typically to an email server, for as long as it takes to send or receive messages. An email message consists of three components, the message envelope, the message header, and the message body. The message header contains control information, including, minimally, an originator's email address and one or more recipient addresses. Usually descriptive information is also added, such as a subject header field and a message submission date/time stamp. Originally a text-only (7-bit ASCII and others) communications medium, email was extended to carry multi- media content attachments, a process standardized in RFC 2045 through 2049. Collectively, these RFCs have come to be called Multipurpose Internet Mail Extensions (MIME). Electronic mail predates the inception of the Internet, and was in fact a crucial tool in creating it, but the history of modern, global Internet email services reaches back to the early ARPANET. E-Mail Working Consider Alice composes a message using her mail user agent (MUA). She enters the email address of her correspondent, and hits the "send" button. Her MUA formats the message in email format and uses the Submission Protocol (a profile of the Simple Mail Transfer Protocol (SMTP), see RFC 6409) to send the message to the local mail submission agent (MSA), in
- 19. this case smtp.a.org, run by Alice's internet service provider (ISP). The MSA looks at the destination address provided in the SMTP protocol (not from the message header), in this case bob@b.org. An Internet email address is a string of the form localpart@exampledomain. The part before the @ sign is the local part of the address, often the username of the recipient, and the part after the @ sign is a domain name or a fully qualified domain name. The MSA resolves a domain name to determine the fully qualified domain name of the mail exchange server in the Domain Name System (DNS). The DNS server for the b.org domain, ns.b.org, responds with any MX records listing the mail exchange servers for that domain, in this case mx.b.org, a message transfer agent (MTA) server run by Bob's ISP. smtp.a.org sends the message to mx.b.org using SMTP. This server may need to forward the message to other MTAs before the message reaches the final message delivery agent (MDA). The MDA delivers it to the mailbox of the user bob. Bob presses the "get mail" button in his MUA, which picks up the message using either the Post Office Protocol (POP3) or the Internet Message Access Protocol (IMAP4). That sequence of events applies to the majority of email users. However, there are many alternative possibilities and complications to the email system: Alice or Bob may use a client connected to a corporate email system, such as IBM Lotus Notes or Microsoft Exchange. These systems often have their own internal email format and their clients typically communicate with the email server using a vendor-specific, proprietary protocol. The server sends or receives email via the Internet through the product's Internet mail gateway which also does any necessary reformatting. If Alice and Bob work for the same company, the entire transaction may happen completely within a single corporate email system. Alice may not have a MUA on her computer but instead may connect to a webmail service. Alice's computer may run its own MTA, so avoiding the transfer at step 1. Bob may pick up his email in many ways, for example logging into mx.b.org and reading it directly, or by using a webmail service. Domains usually have several mail exchange servers so that they can continue to accept mail when the main mail exchange server is not available. Email messages are not secure if email encryption is not used correctly. Many MTAs used to accept messages for any recipient on the Internet and do their best to deliver them. Such MTAs are called open mail relays. This was very important in the early days of the Internet when network connections were unreliable. If an MTA couldn't reach the destination, it could at least deliver it to a relay closer to the destination. The relay stood a better chance of delivering the message at a later time. However, this mechanism proved to be exploitable by people sending unsolicited bulk email and as a consequence very few modern MTAs are open mail relays, and many MTAs don't accept messages from open mail relays because such messages are very likely to be spam. Your e-mail client allows you to add attachments to e-mail messages you send, and also lets you save attachments from messages that you receive. Attachments might include word processing documents, spreadsheets, sound files, snapshots and pieces of software. Usually, an attachment is not text (if it were, you
- 20. would simply include it in the body of the message). Since e-mail messages can contain only text information, and attachments are not text, there is a problem that needs to be solved. The recipient would then save the uuencoded portion of the message to a file and run uudecode on it to translate it back to binary. The word "reports" in the first line tells uudecode what to name the output file. Modern e-mail clients are doing exactly the same thing, but they run uuencode and uudecode for you automatically. If you look at a raw e-mail file that contains attachments, you'll find that the attachment is represented in the same uuencoded text format shown above! Considering its tremendous impact on society, having forever changed the way we communicate, today's e-mail system is one of the simplest things ever devised! There are parts of the system, like the routing rules in sendmail, that get complicated, but the basic system is incredibly straightforward. The next time you send an e- mail, you'll know exactly how it's getting to its destination! The Real E-mail System For the vast majority of people right now, the real e-mail system consists of two different servers running on a server machine. One is called the SMTP Server, where SMTP stands for Simple Mail Transfer Protocol. The SMTP server handles outgoing mail. The other is a POP3 Server, where POP stands for Post Office Protocol. The POP3 server handles incoming mail. A typical e-mail server looks like this: The SMTP server listens on well-known port number 25, while POP3 listens on port 110mail Clients. You have probably already received several e-mail messages today. To look at them, you use some sort of e-mail client. Many people use well-known stand-alone clients like Microsoft Outlook, Outlook Express, Eudora or Pegasus. People who subscribe to free e-mail services like Hotmail or Yahoo use an e-mail client that appears in a Web page. If you are an AOL customer, you use AOL's e-mail reader. No matter which type of client you are using, it generally does four things: ·· It shows you a list of all of the messages in your mailbox by displaying the message headers. The header shows you who sent the mail, the subject of the mail and may also show the time and date of the message and the message size. It lets you select a message header and read the body of the e-mail message. It lets you create new messages and send them. You type in the e-mail address of the recipient and the subject for the message, and then type the body of the message. Most e-mail clients also let you add attachments to messages you send and save the attachments from messages you receive. Sophisticated e-mail clients may have all sorts of bells and whistles, but at the core, this is all that an e-mail client does.
- 21. Aim 7 : To study brief introduction of packet tracer. Packet Tracer Packet Tracer is a Cisco router simulator that can be utilized in training and education, but also in research for simple computer network simulations. The tool is created by Cisco Systems and provided for free distribution to faculty, students, and alumni who are or have participated in the Cisco Networking Academy. The purpose of Packet Tracer is to offer students and teachers a tool to learn the principles of networking as well as develop Cisco technology specific skills Packet Tracer features The current version of Packet Tracer supports an array of simulated Application Layer protocols, as well as basic routing with RIP, OSPF, and EIGRP, to the extent required by the current CCNA curriculum. While Packet Tracer aims to provide a realistic simulation of functional networks, the application itself utilizes only a small number of features found within the actual hardware running a current Cisco IOS version. Thus, Packet Tracer is unsuitable for modeling production networks. With the introduction of version 5.3, several new features were added, including BGP. BGP is not part of the CCNA curriculum, but part of the CCNP curriculum. Use in education Packet Tracer is commonly used by Cisco Networking Academy students working towards Cisco Certified Network Associate (CCNA) certification. Due to functional limitations, it is intended by Cisco to be used only as a learning aid, not a replacement for Cisco routers and switches
- 22. Aim 8 : To create a point to point topology using cisco packet tracer. Steps to follow: 1.Select two computets and drag them on the editor. 2.Use a copper cable and connect them 3.Assign diff ip to both of them 4.Select a msg and send it to pc1 from pc0.
- 23. Aim 9 : To create a star topology using cisco packet tracer. Steps to follow: 1.Select four computets and a hub, drag them on the editor. 2.Use a copper cable and connect them 3.Assign diff ip to all of them except hub. 4.Select a msg and send it to pc1 from pc0.
- 24. Aim 10 : To create a mesh topology using cisco packet tracer. Steps to follow: 1.Select four computets and four swithes, drag them on the editor. 2.Use a copper cable and connect them 3.Assign diff ip to all of them except swithes. 4.Select a msg and send it to pc1 from pc0.
- 25. Aim 11 : To create a bus topology using cisco packet tracer. Steps to follow: 1.Select a server, five computers and five swithes, drag them on the editor. 2.Use a copper cable and connect them 3.Assign diff ip to all of them except swithes. 4.Select a msg and send it to sever from pc4. 5.Result successful as shown in fig .
- 26. Aim 12: To create a ring topology using cisco packet tracer. Steps to follow: 1.Select six computers and six swithes, drag them on the editor. 2.Use a copper cable and connect them 3.Assign diff ip to all of them except swithes. 4.Select a msg and send it to pc2 from pc5. 5.Result successful as shown in fig .
- 27. Aim 13 : To create a tree topology using cisco packet tracer. Steps to follow: 1.Select seven computers and five hubs, drag them on the editor. 2.Use a copper cable and connect them 3.Assign diff ip to all of them except hubs. 4.Select a msg and send it to pc2 from pc0. 5.Result successful as shown in fig .
- 28. Aim 14: Difference between yahoo mail and Gmail (Google mail): YAHOO MAIL GOOGLE MAIL 1Yahoo started its web mail services under the 1 Google entered the Webmail segment on name Yahoo mail on October 8, 1997, with April 1, 2004 under the name Gmail. Linux at the server end. 2 Yahoo moves onto another page for 2Gmail lets you add attachments more attachments. conveniently from the same screen where you are composing an email, 3 it is not so in gmail 3 In Yahoo, you may require to add boxes for more than five attachments 4 Yahoo sticks onto its independent Instant 4 Gmail offers the chat module integrated to Messenger for chatting. the email module. 5 inYahoo Mail; you can opt to save a contact to your list or not. 5 Gmail automatically stores all email addresses to which you sent and receive emails to your contact list. 6 , Yahoo Mail treats every conversation unique. 6 The webmail is arranged in a conversation model in Gmail as in an Instant Messenger. Every time you reply to someone, it will be added as a conversation to the primary email. 7 it is less vulnerable to spams 7 Yahoo Mail is more vulnerable to Spam emails 8 With Gmail, the user gets email forwarding 8 in Yahoo mail, a user has to upgrade to a paid and POP access for free version in order to gain these services. 9 Gmail is less cluttered 9 YAHOO is more cluttered 10 While Gmail remains as the first webmail to 10 Yahoo later created the Ajax version in employ Ajax Programming technique for its 2004. search oriented interface 11 it allows you to send instant messages to your contacts that are online quickly and 11 Yahoo has IM as well, it is not nearly as easily. accessible as the one found within Gmail. 12 Gmail’s IM is not separate from its e-mail service. 12 Yahoo’s IM is separate from its e-mail service. 13 it allows you to label folders, keeps all your
- 29. folders in approximately the same area, making 13 it allows better folder creation and organization with a large amount of folders organization. Yahoo mail allows you to label difficult. and organize your folders how you like making the mail system . 14 Gmail allows for a bigger attachment 14 Yahoo mail only allows attachments up to size.Upto 20 mb in its free version. 10mb on its free version, 15 one of the more important aspects of Gmail 15 it is considered less professional. is the fact that it is considered the more “professional” of the e-mail services. 16 Gmail, an issue for mobile users. 16 Yahoo is better for mobile users. 17 Gmail gets weird on IMAP and is a devourer of bandwidth. 17 For IMAP lovers, Yahoo’s implementation is much better. 18 when you make a gmailaccount, you can’t just make Gmail. You have other services like youtube, blogger, picasa, and other services 18 An Yahoo id is just for Yahoo. No other linked to it. services are linked to it. 19 Gmail is more user friendly. 20 Gmail “remembers” previously used email 19 Yahoo is less user friendly. addresses so that the address must only be keyed in for the initial email. 20 Yahoo mail users need to type email addresses each time a user needed to send an 21 Google utilized a coding language called email. Ajax which allows Gmail users to delete mail, archive mail, and otherwise move it to any other folder without wasting a few seconds each 21 when emails are either deleted or moved to a time waiting for the screen to refresh. new folder in Yahoo mail the screen must be given time to refresh.
