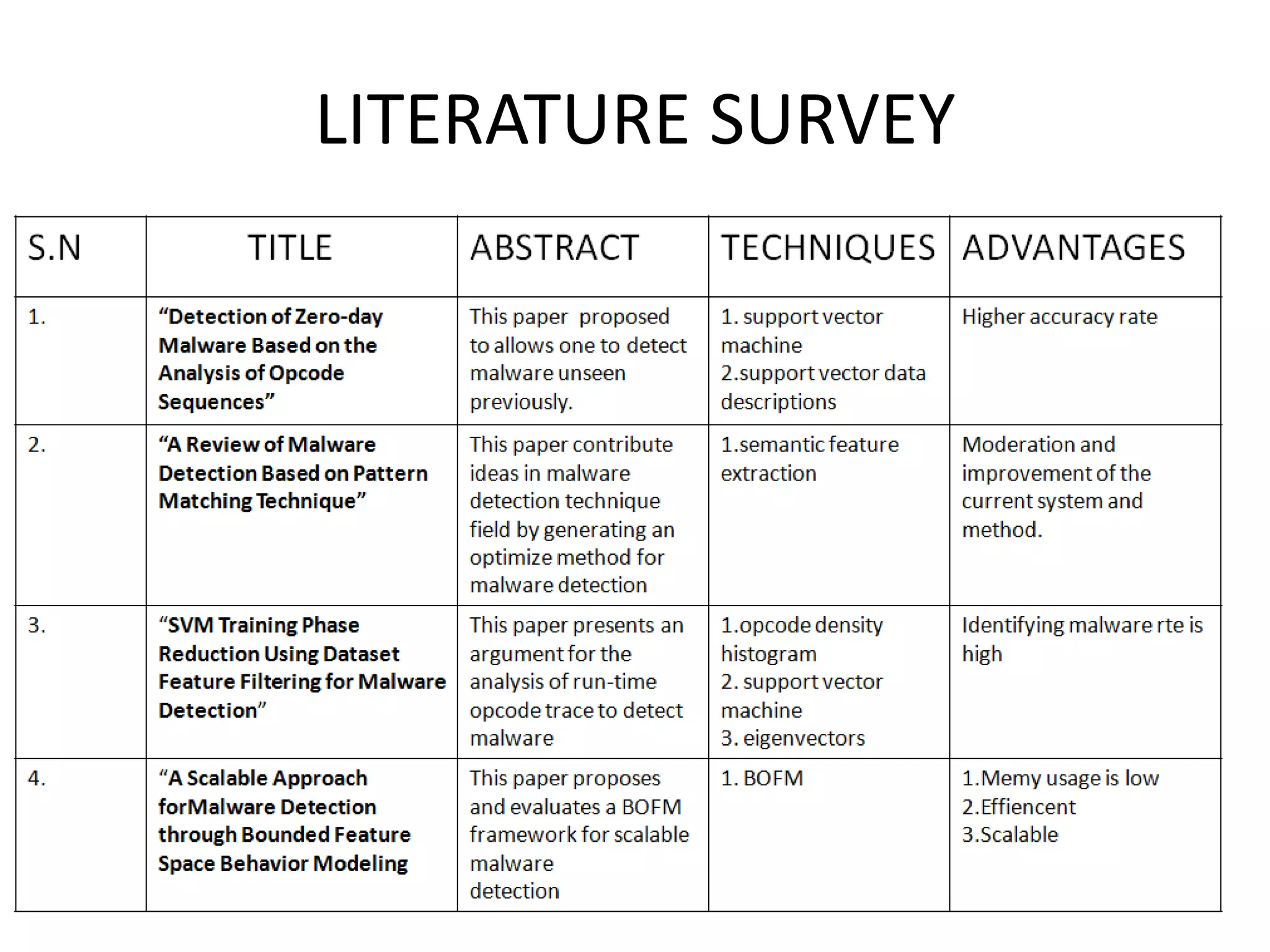
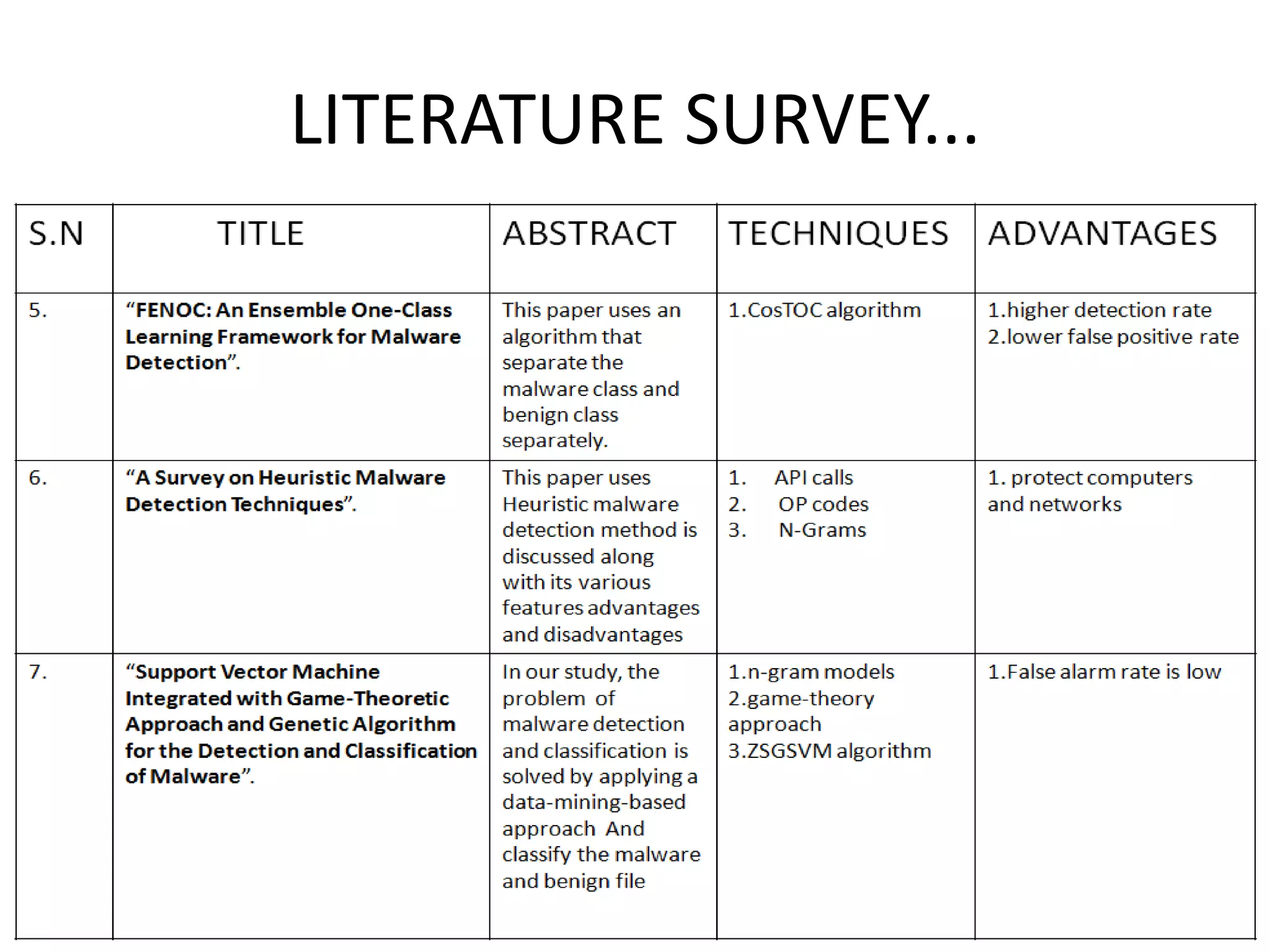
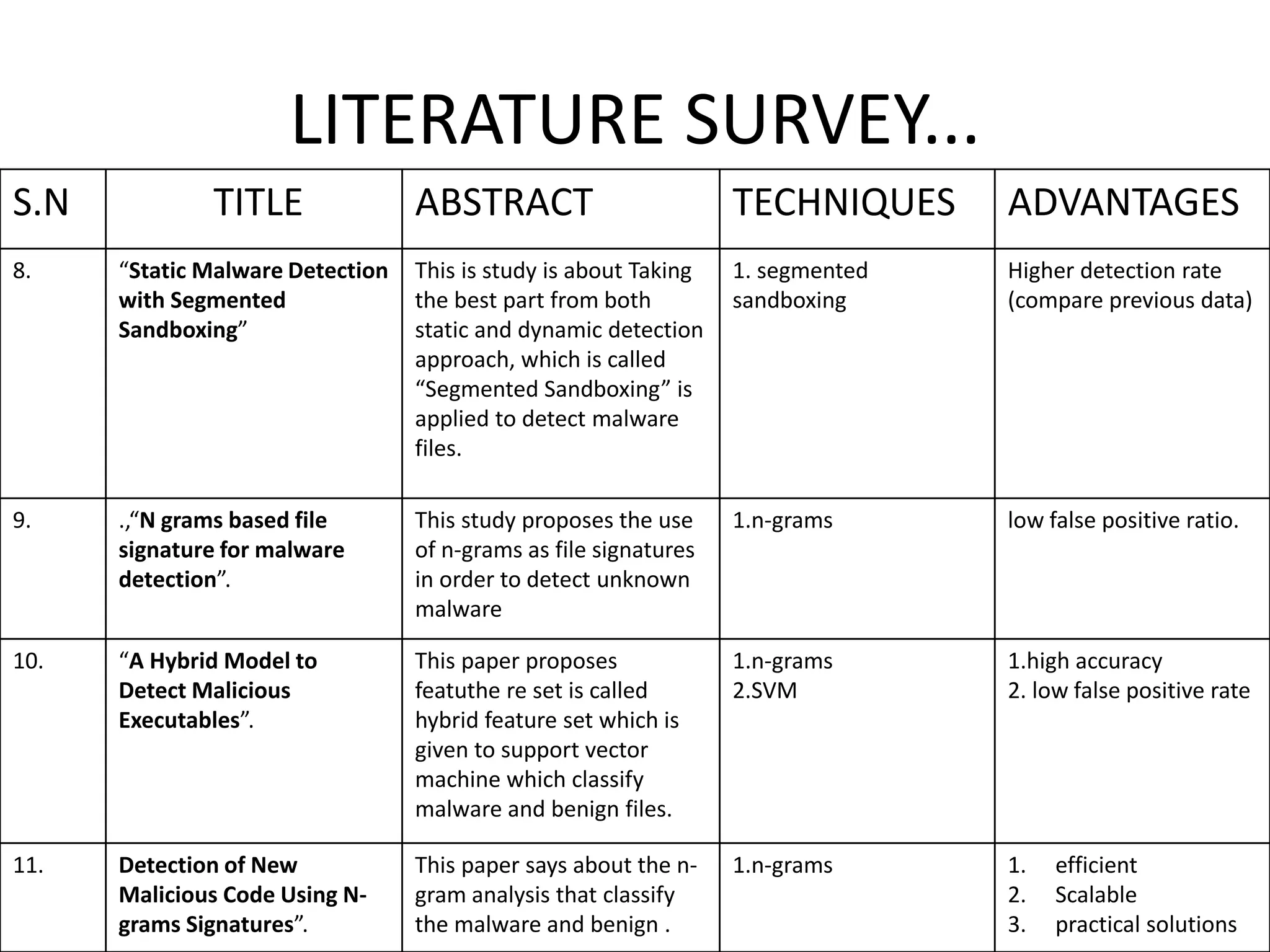
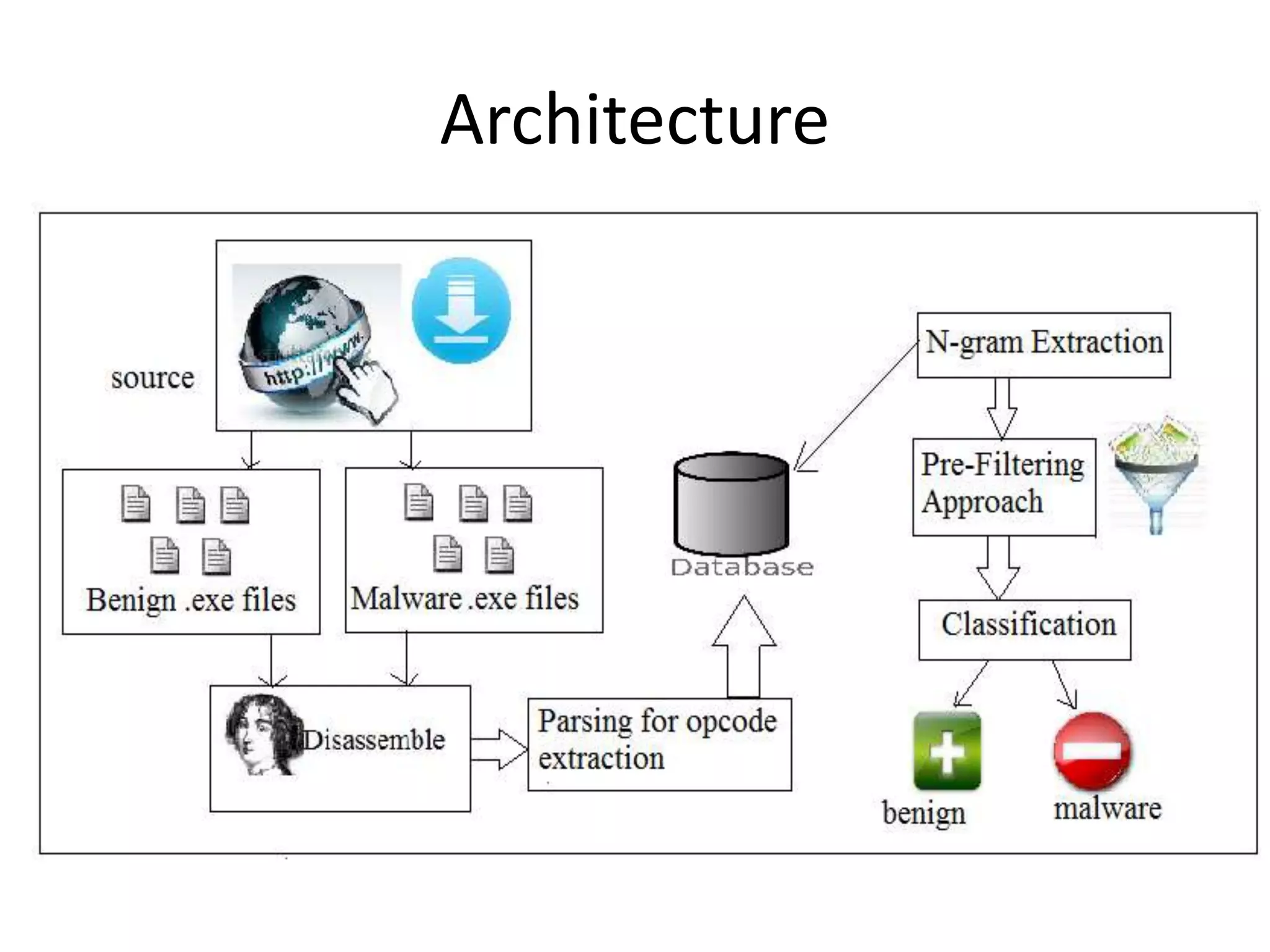
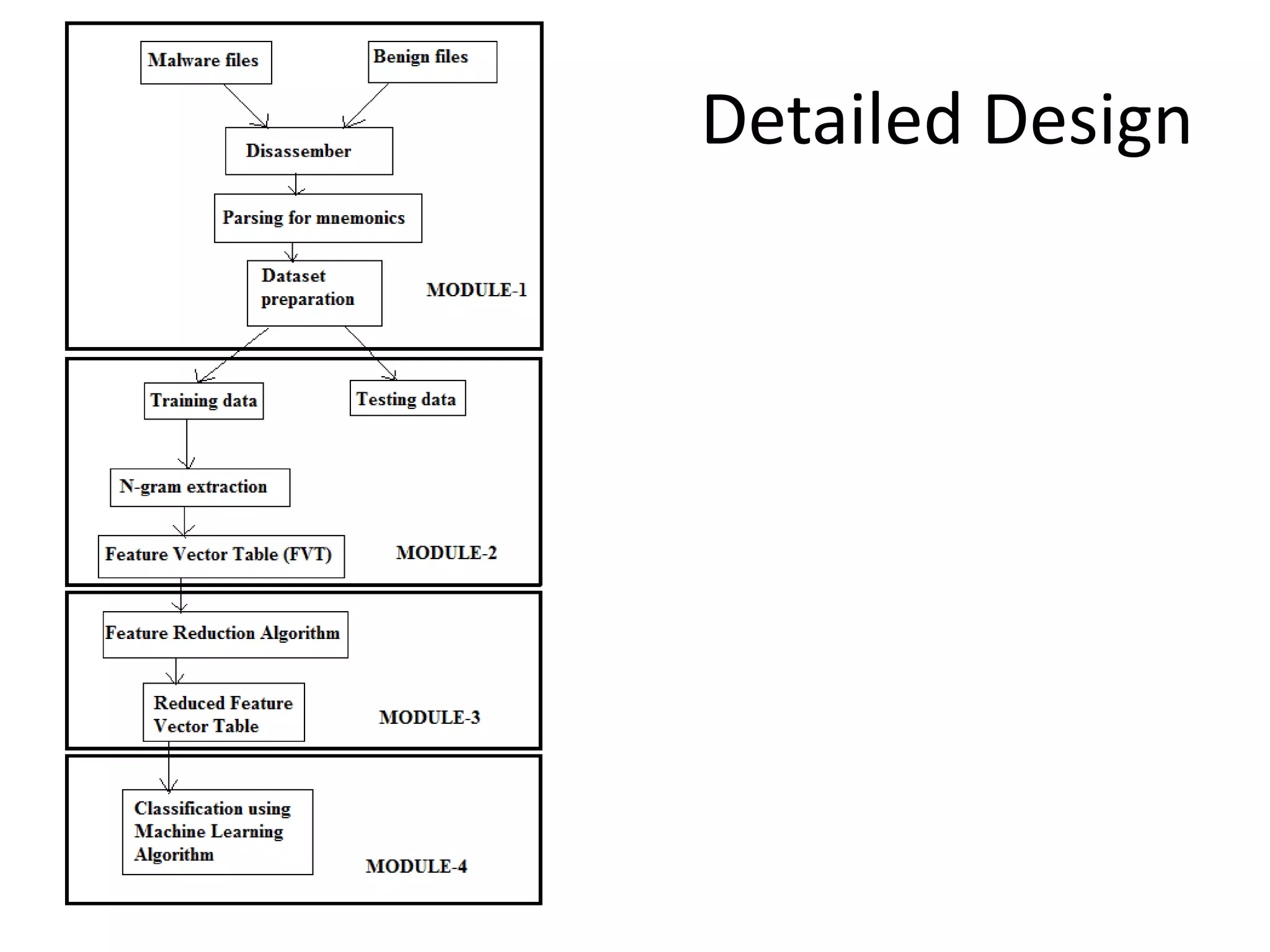
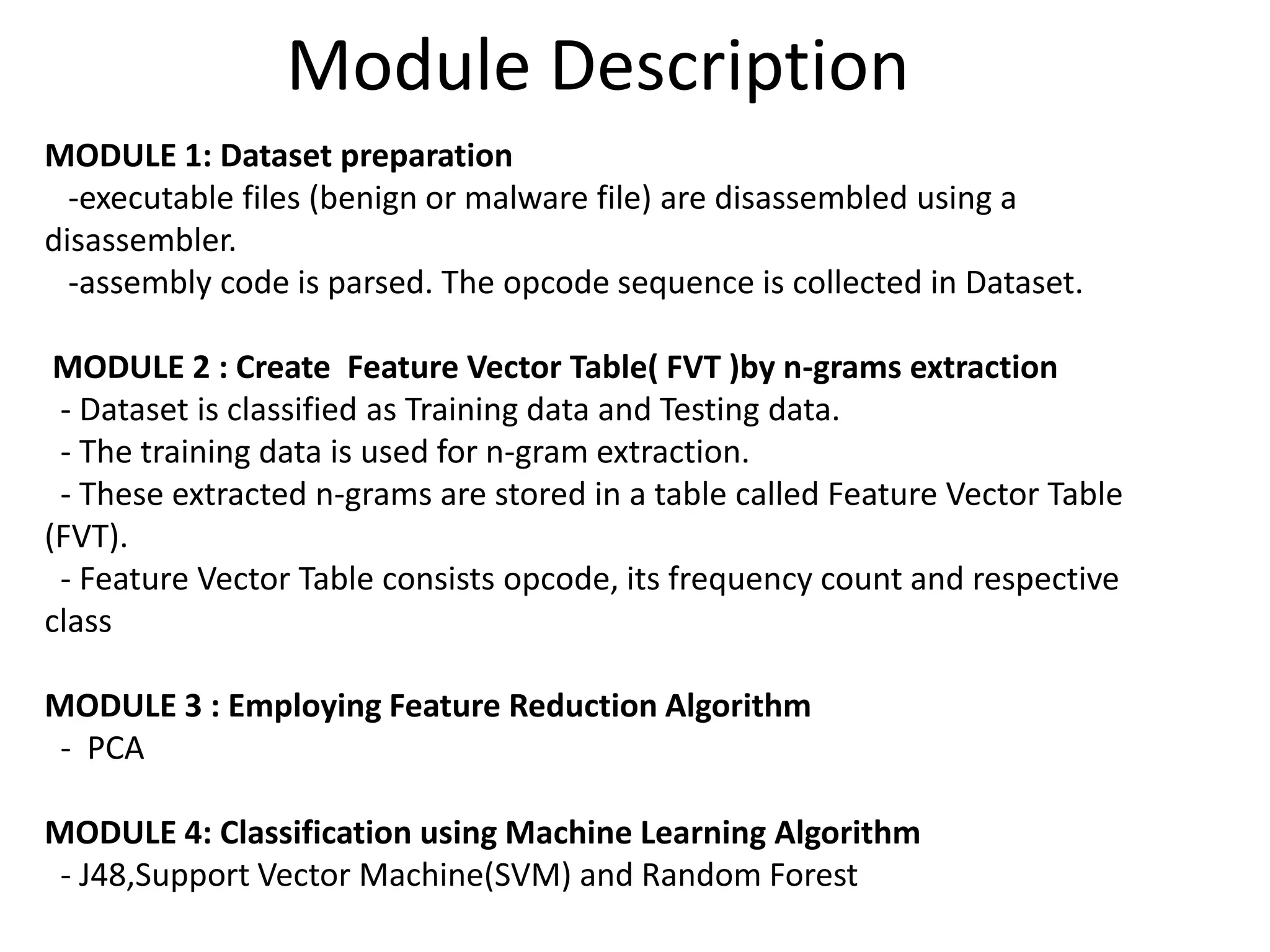
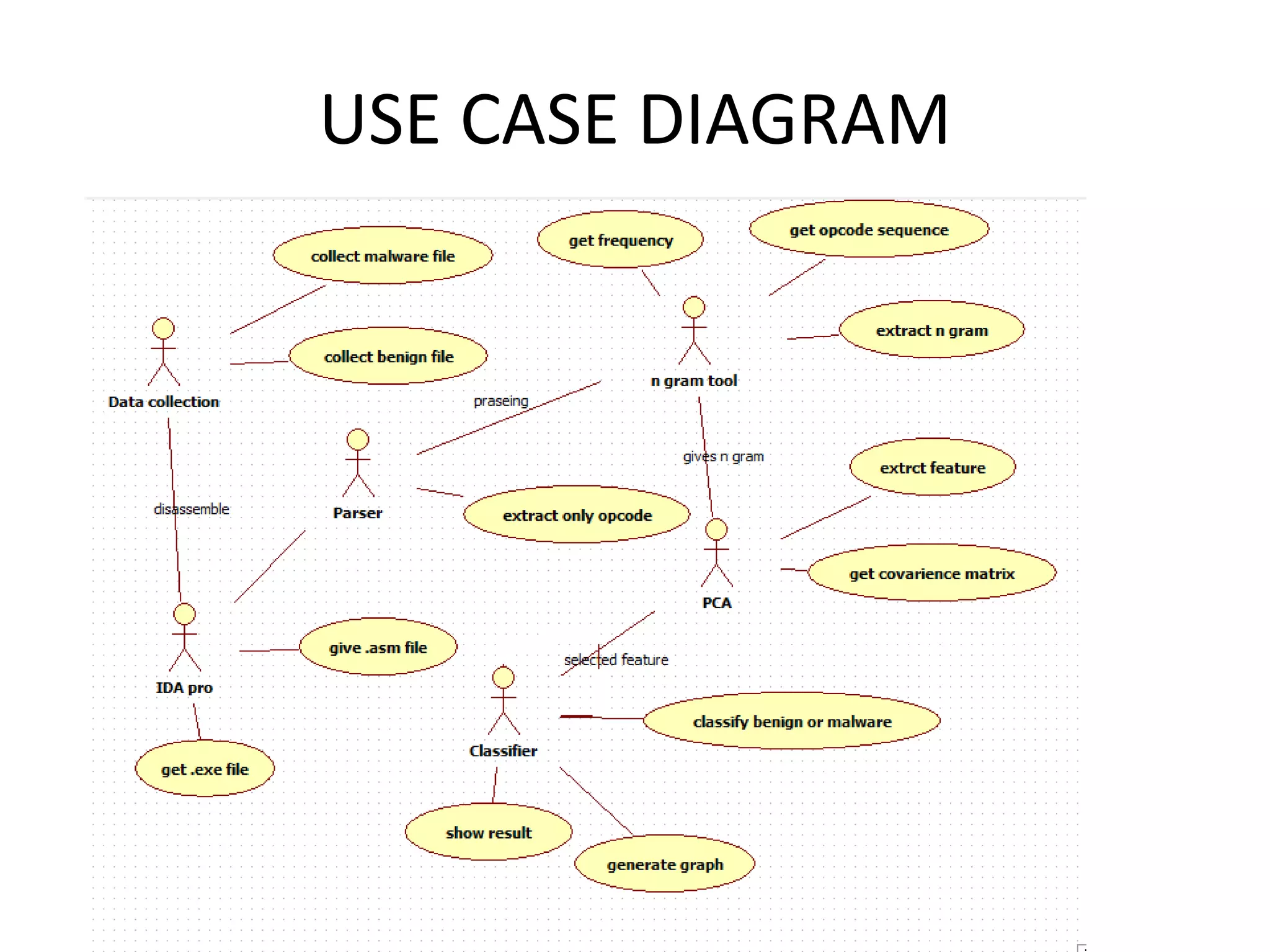
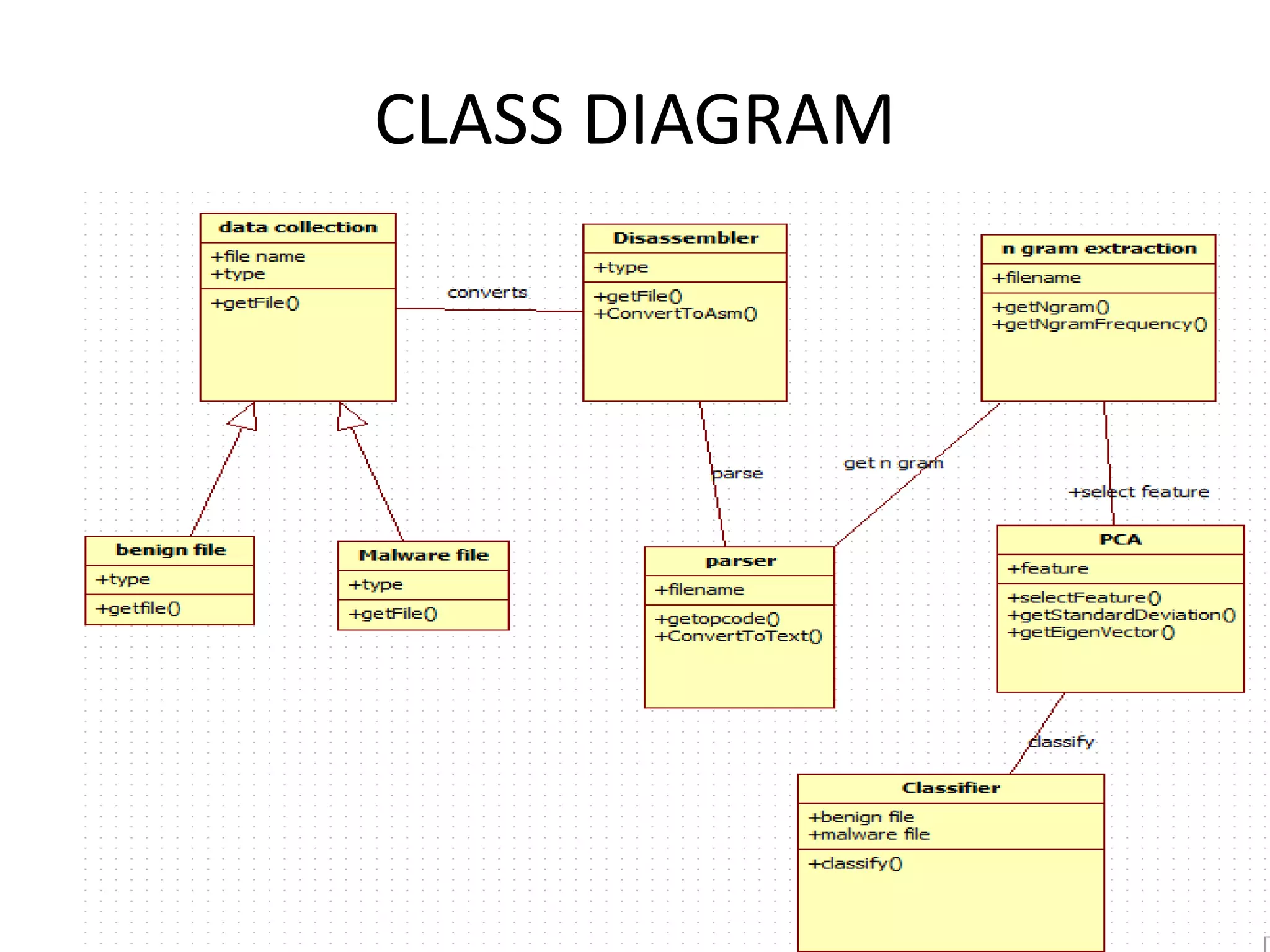
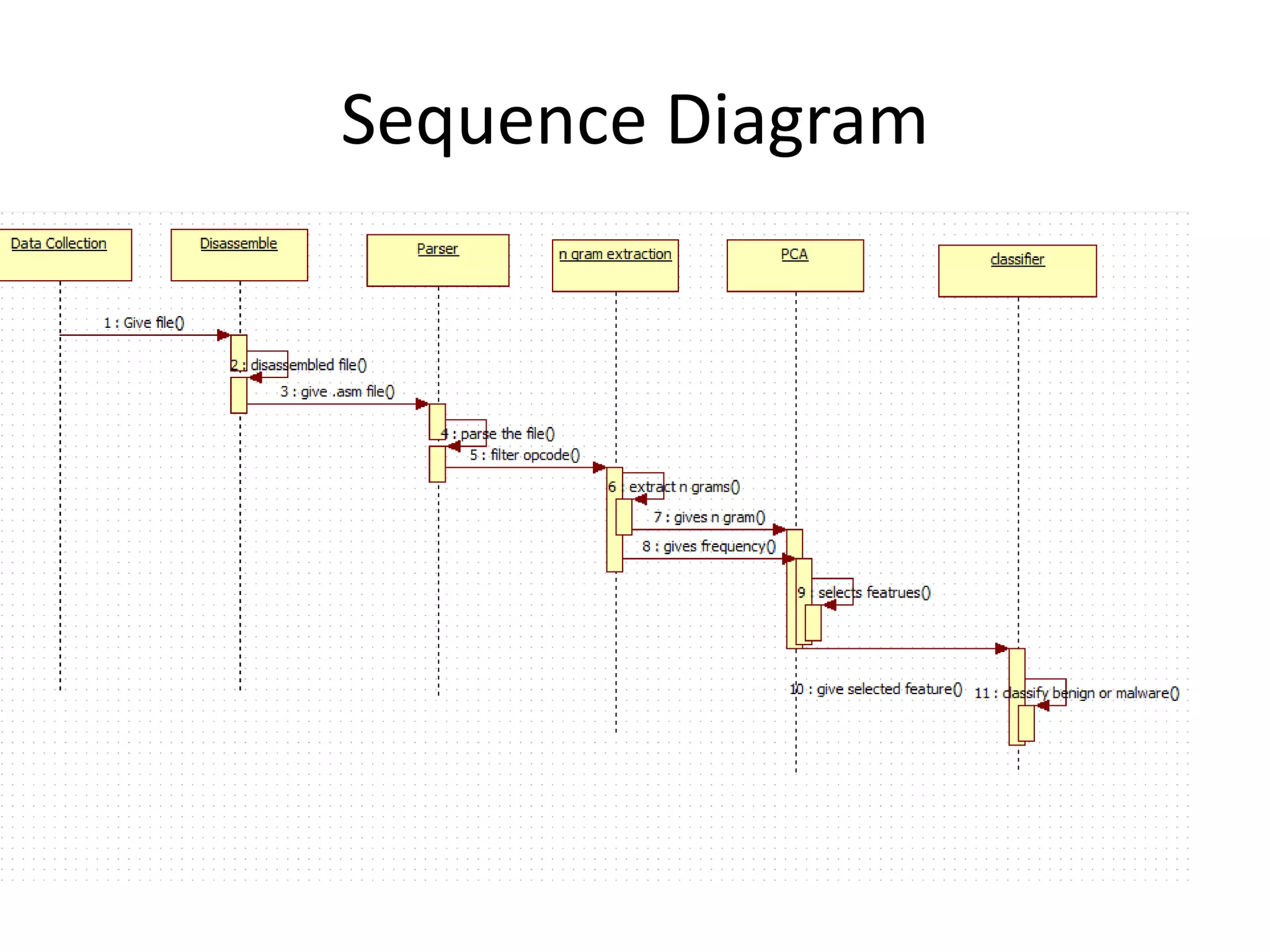
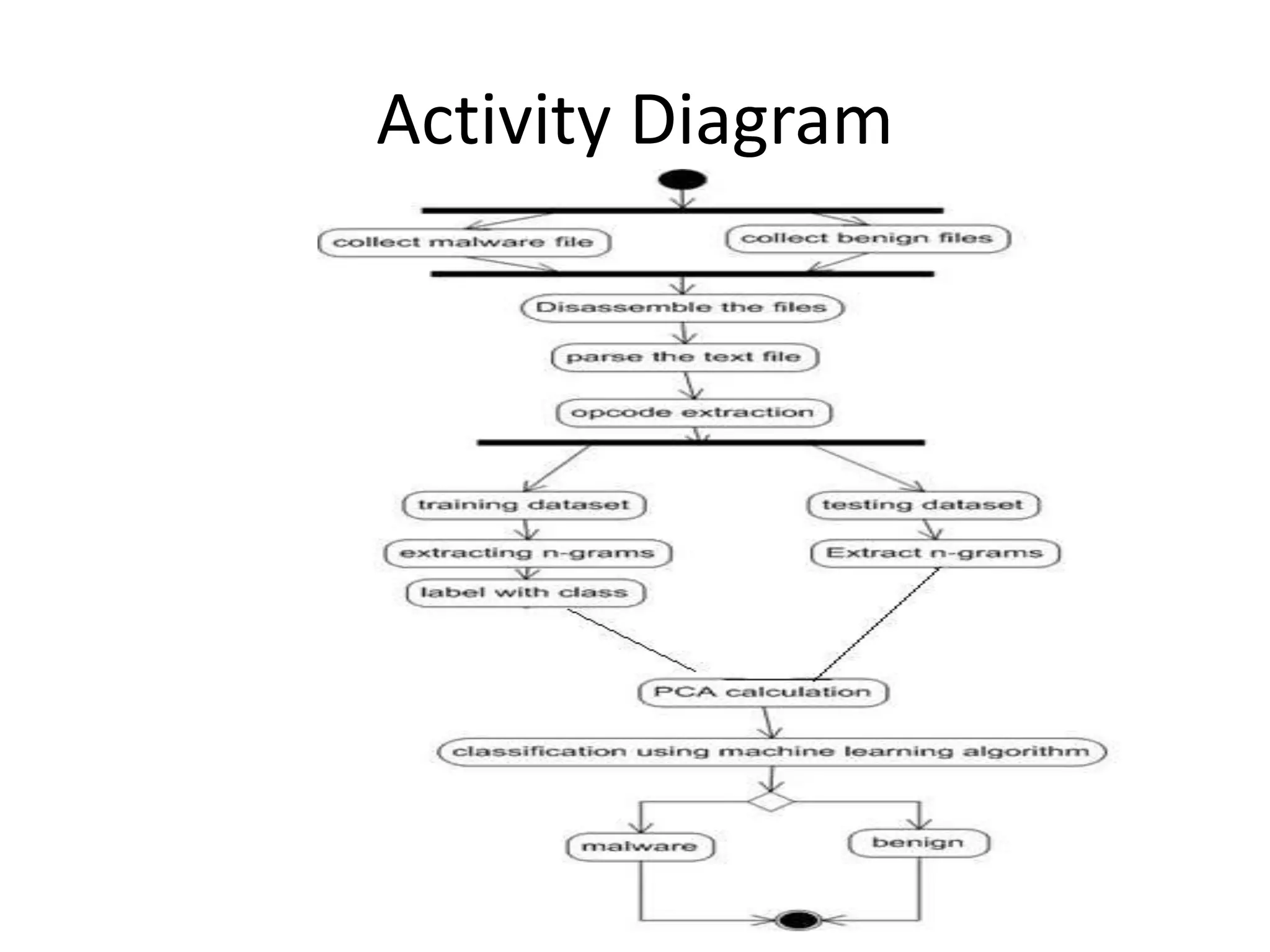
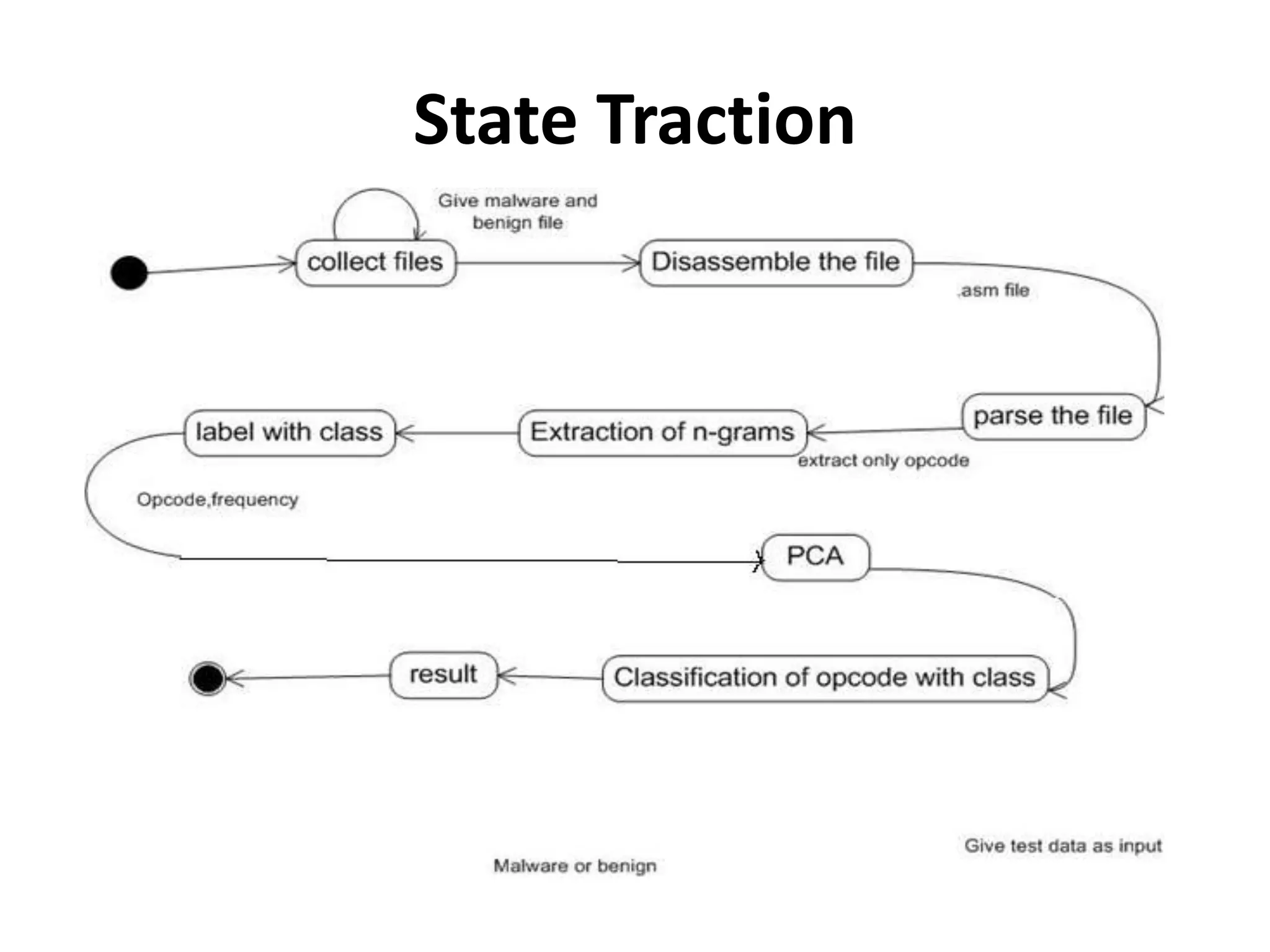
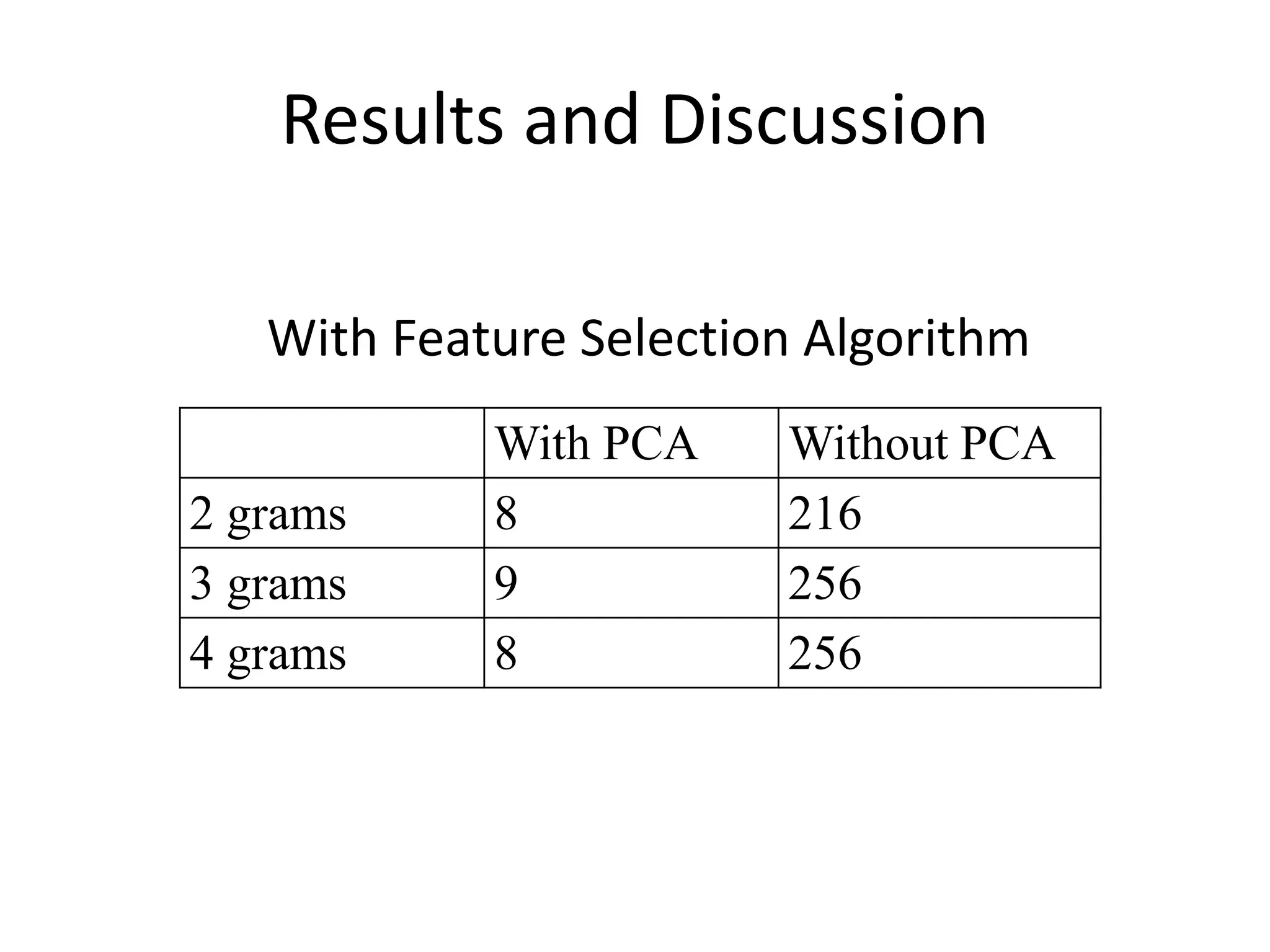
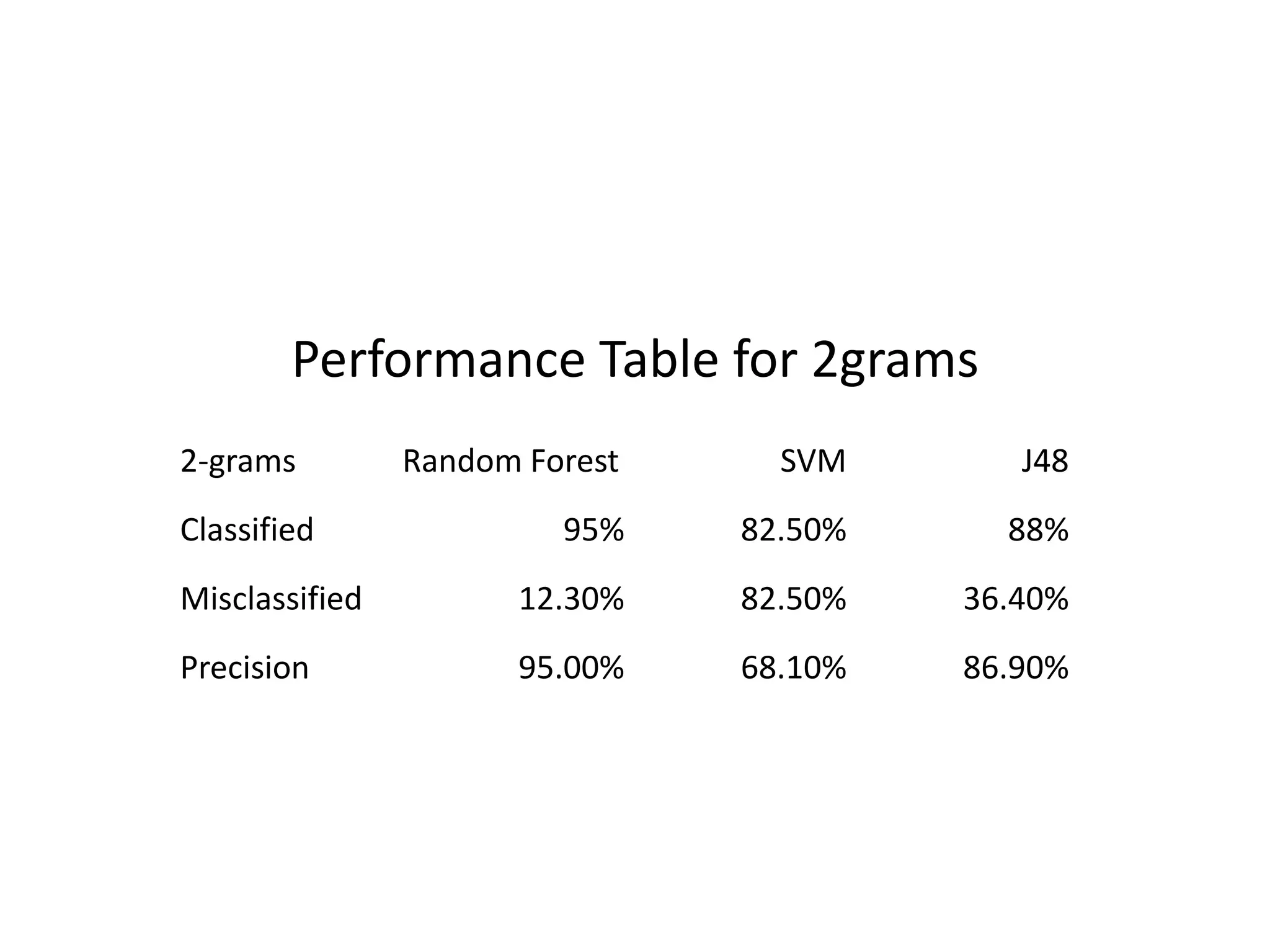
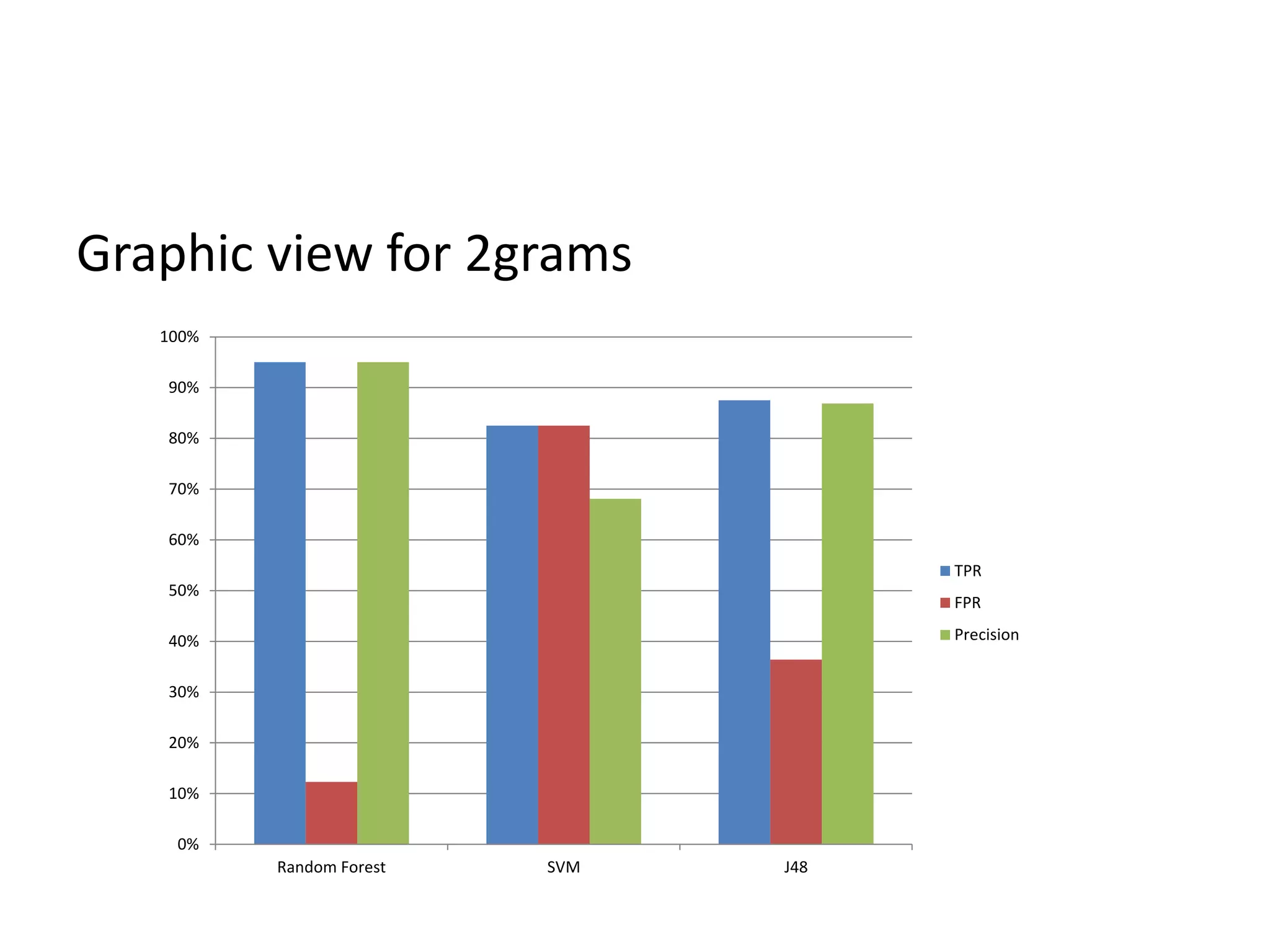
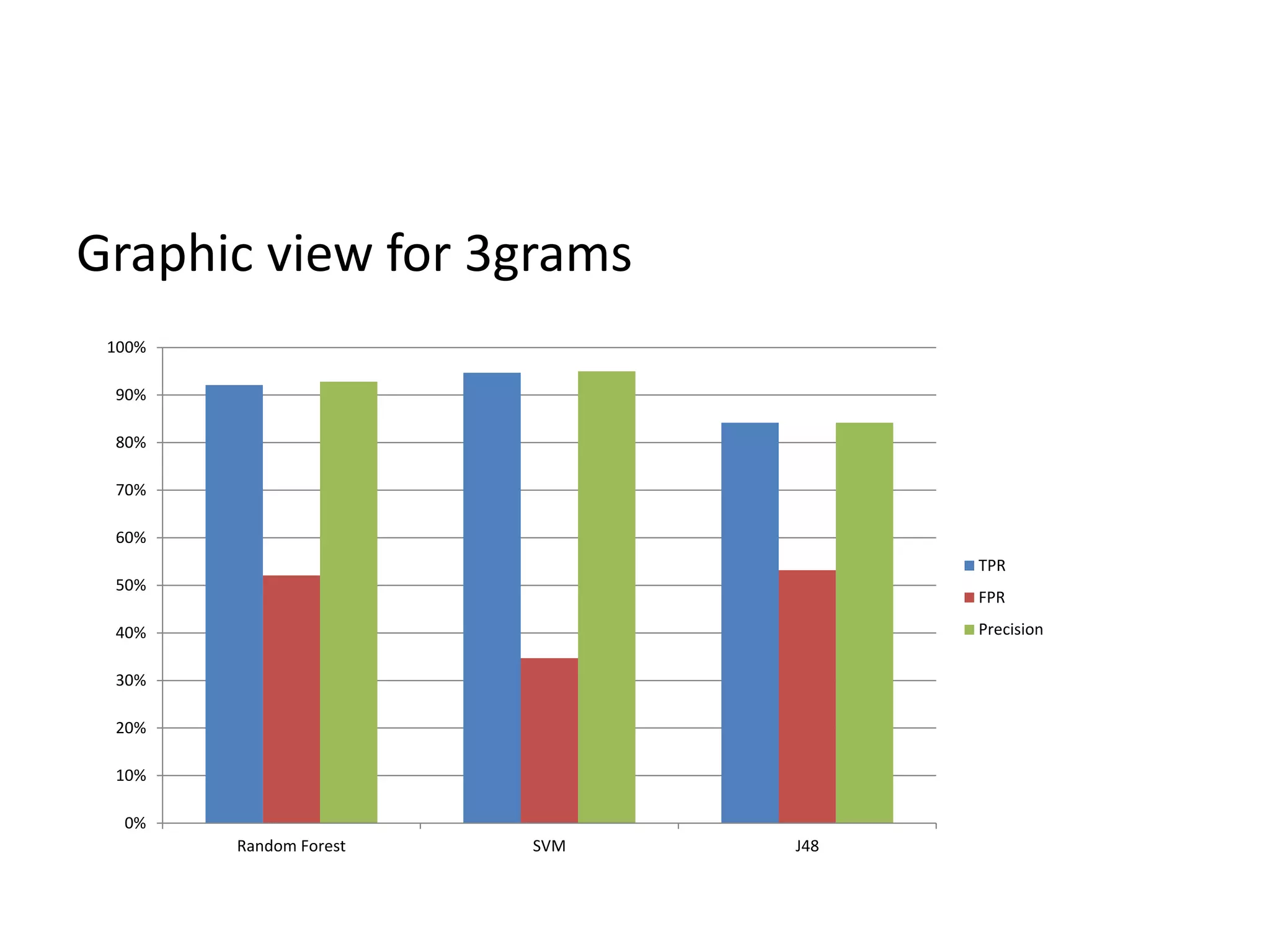
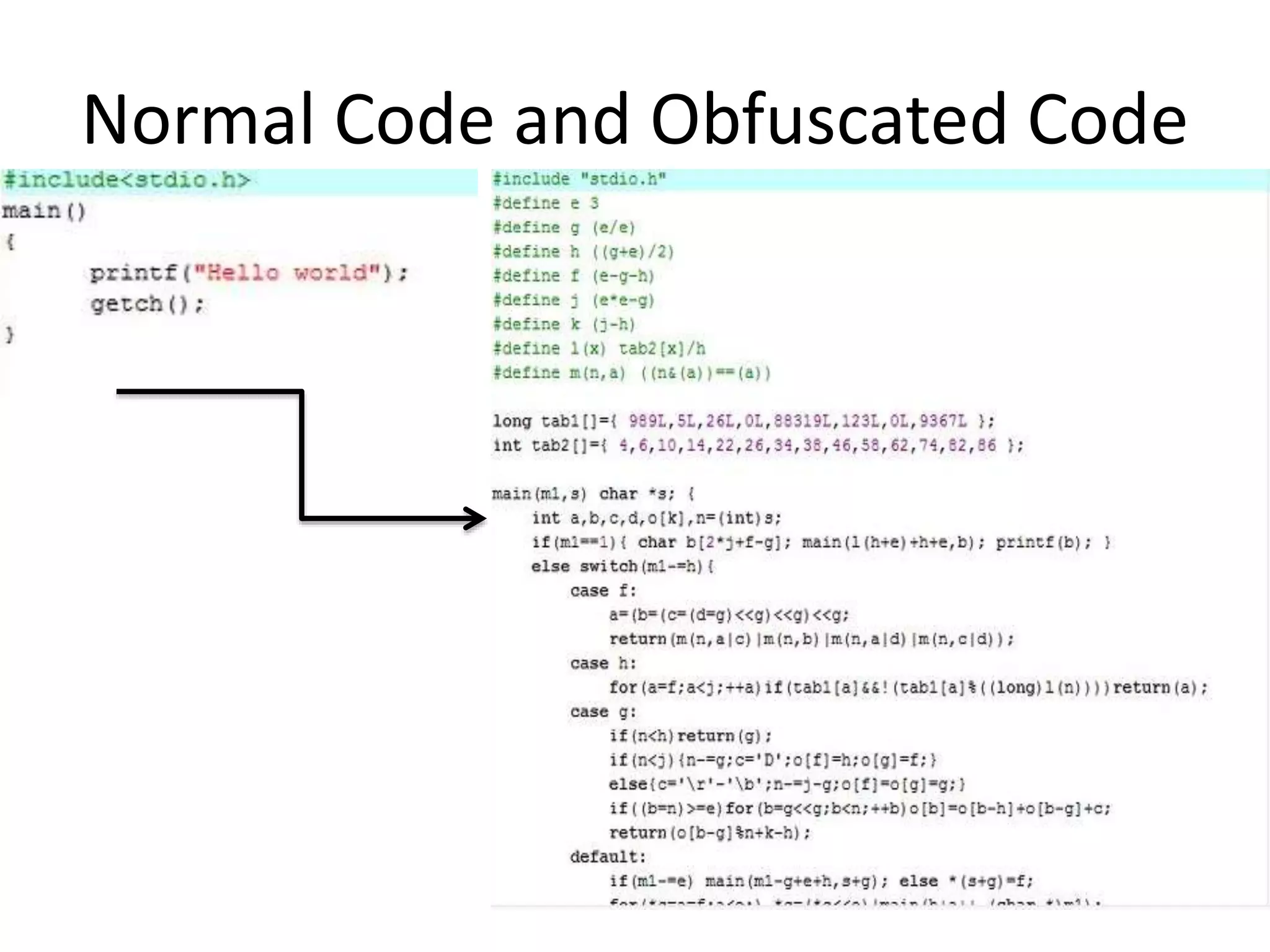
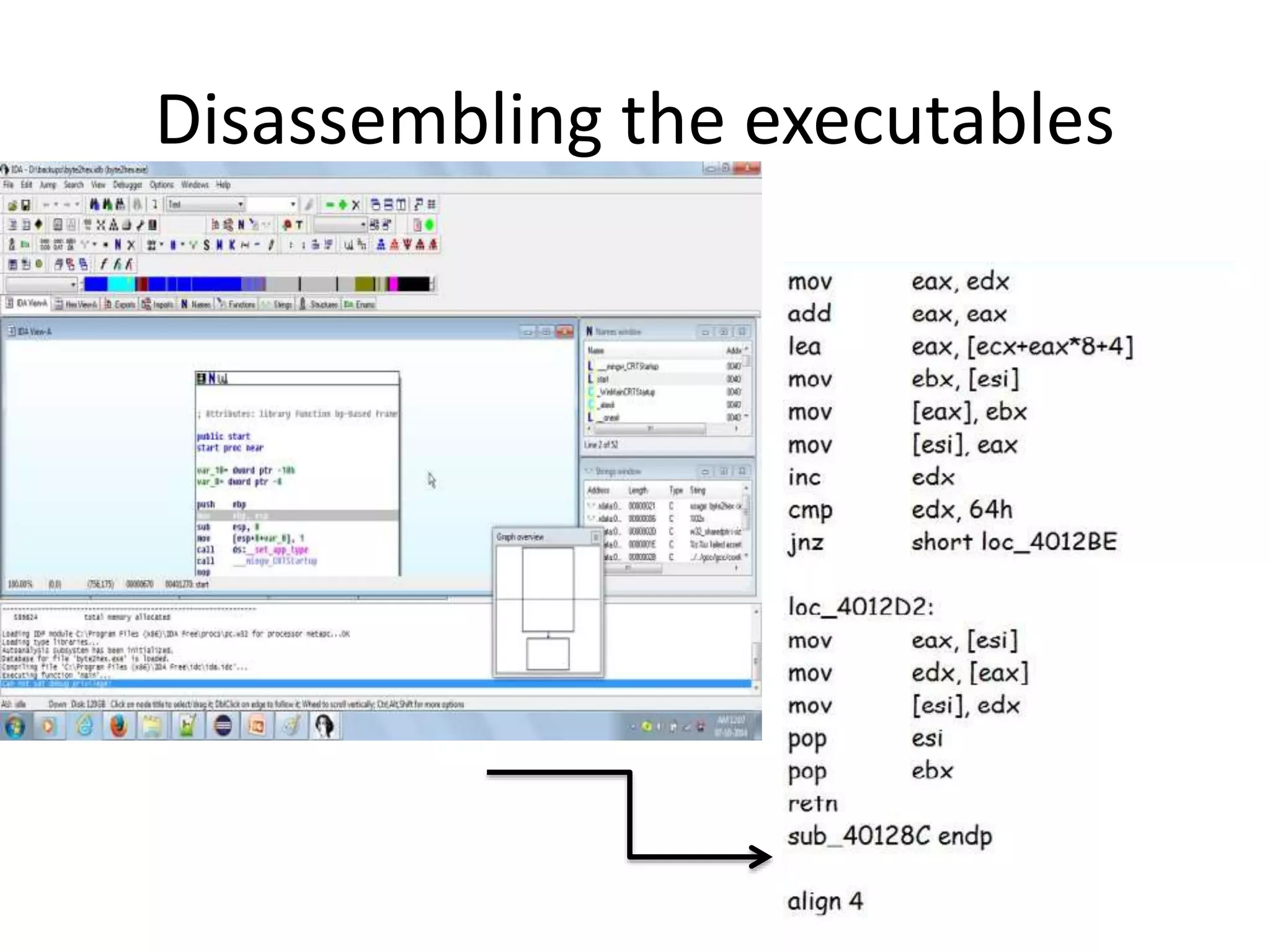
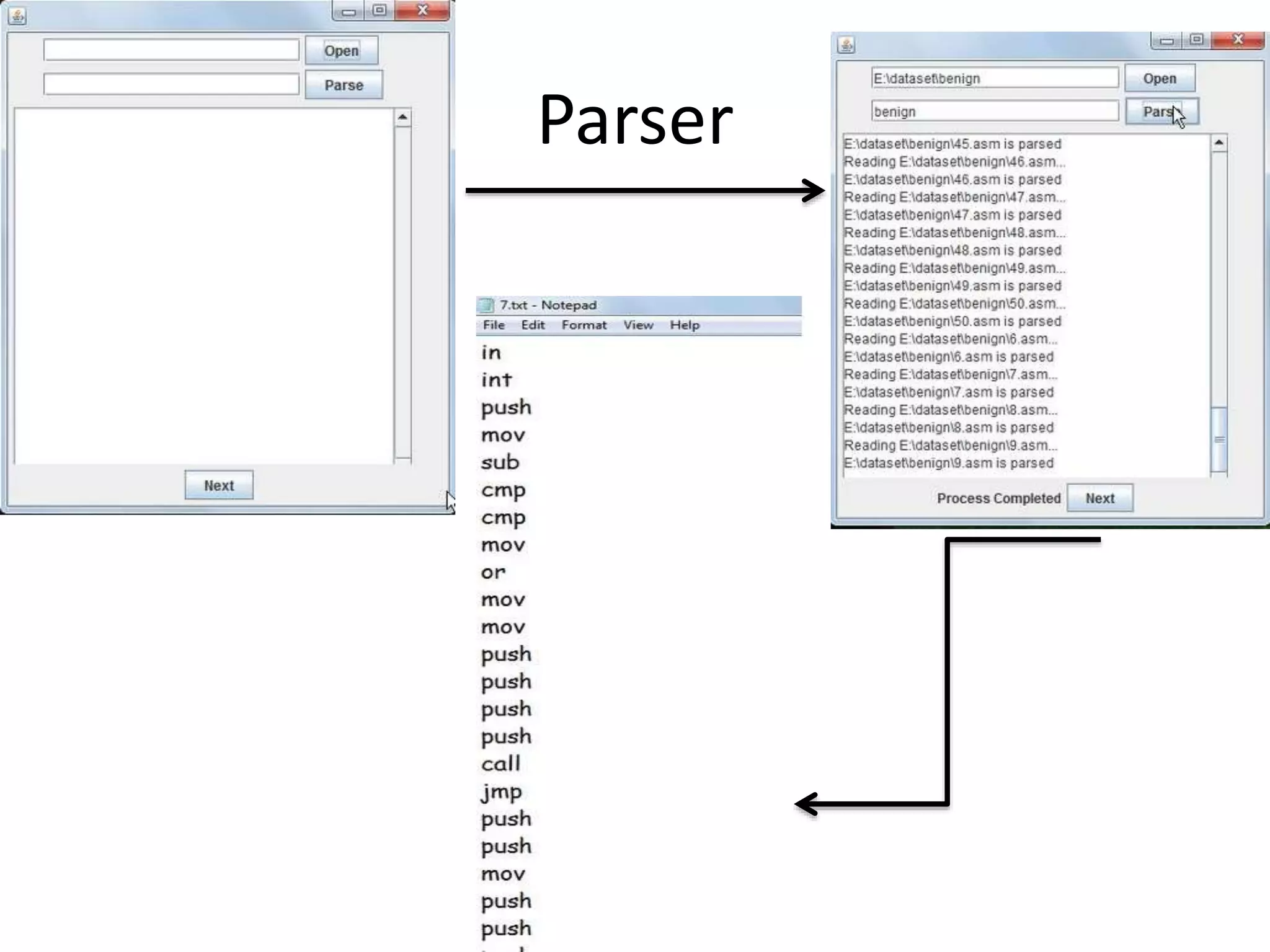
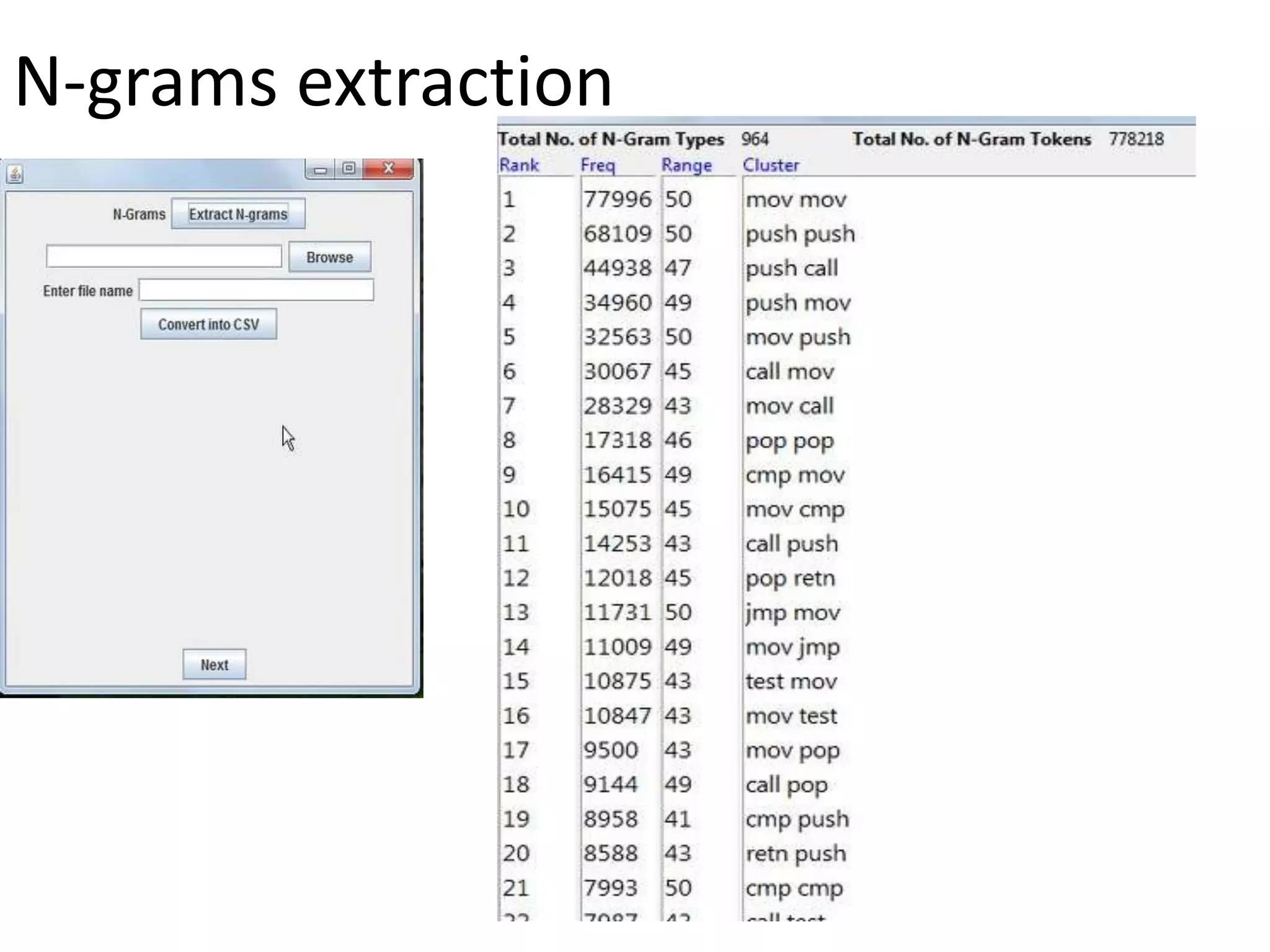
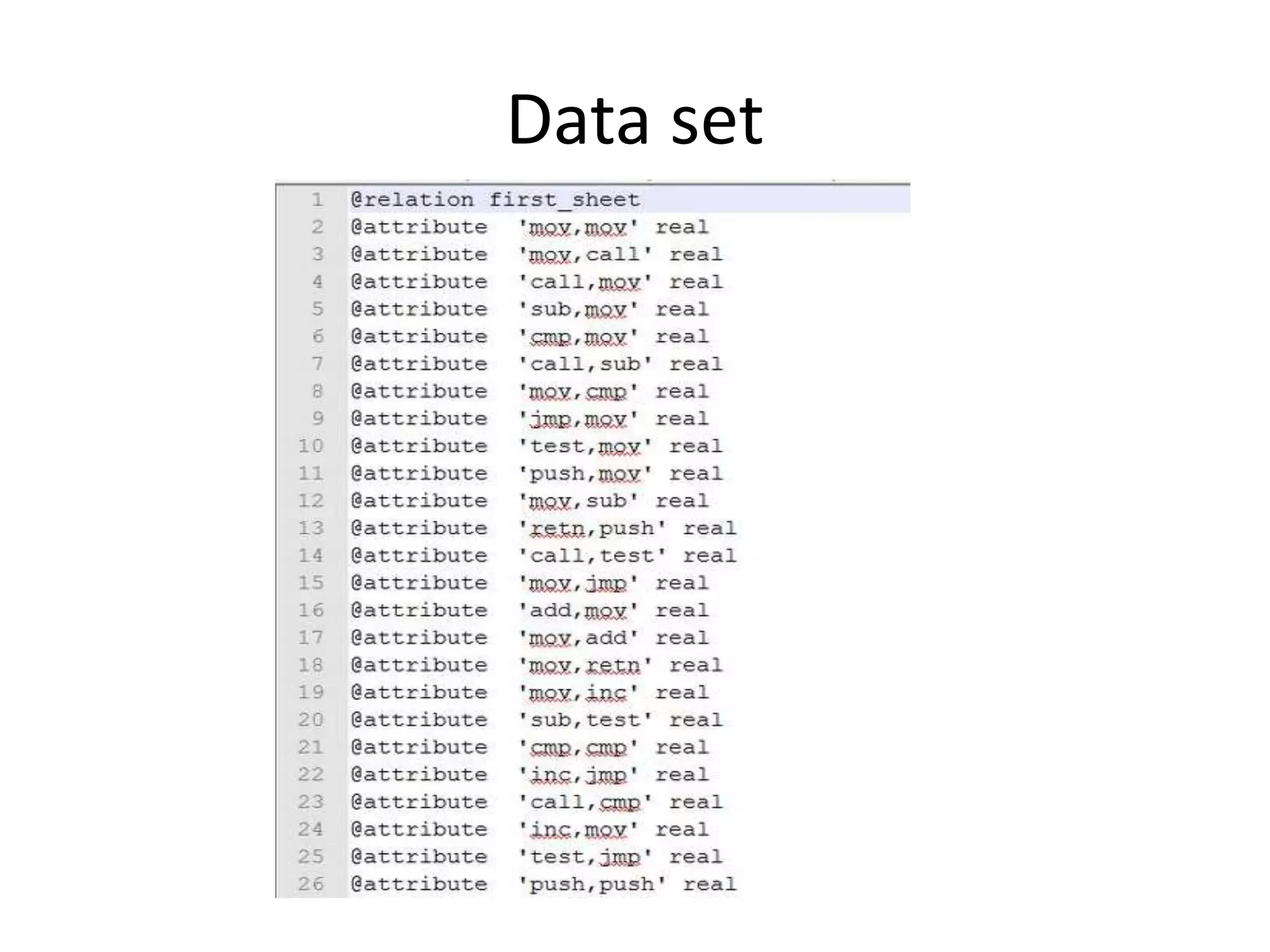
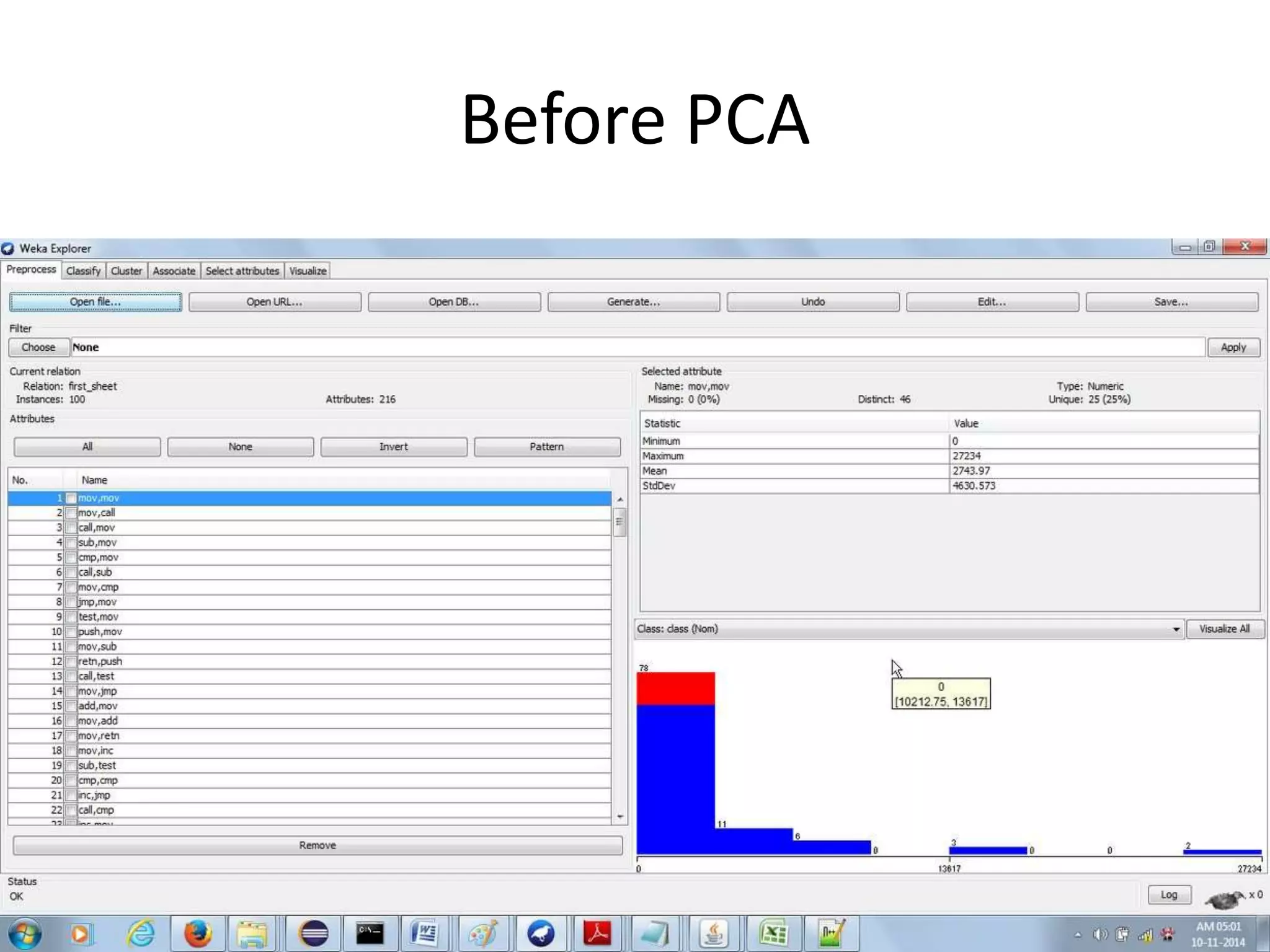
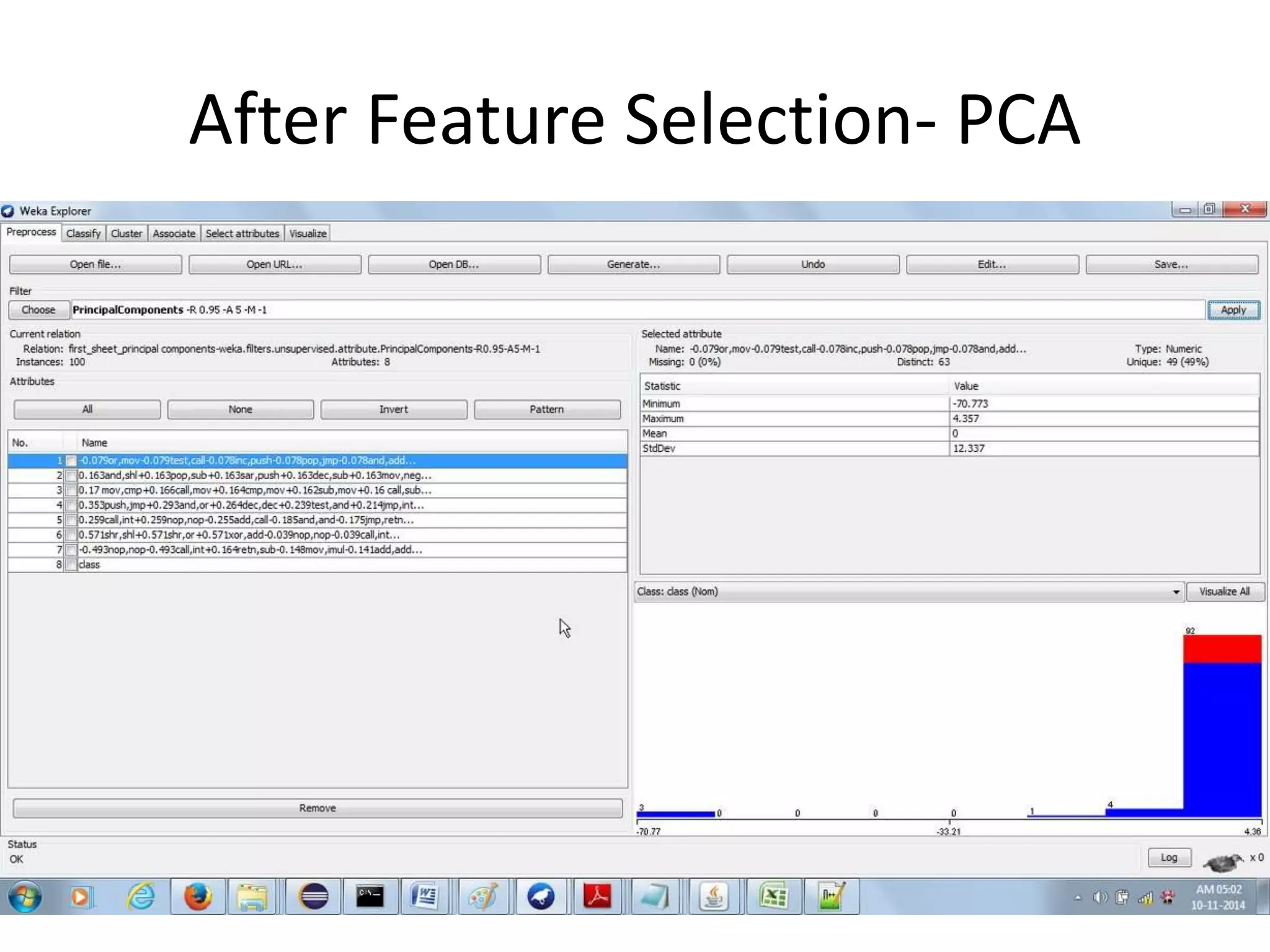
This document discusses detecting malware using n-grams and machine learning algorithms. It analyzes executable files to extract n-gram sequences from the opcode, creates a feature vector table (FVT) of n-grams and their frequencies. This FVT is used to train and test machine learning classifiers like J48, SVM, and Random Forest. Dimensionality reduction using PCA is also applied before classification. The models are evaluated based on metrics like accuracy, misclassification rate, and precision on n-gram datasets of different sizes. Random Forest performs best with over 95% accuracy on 2-grams.