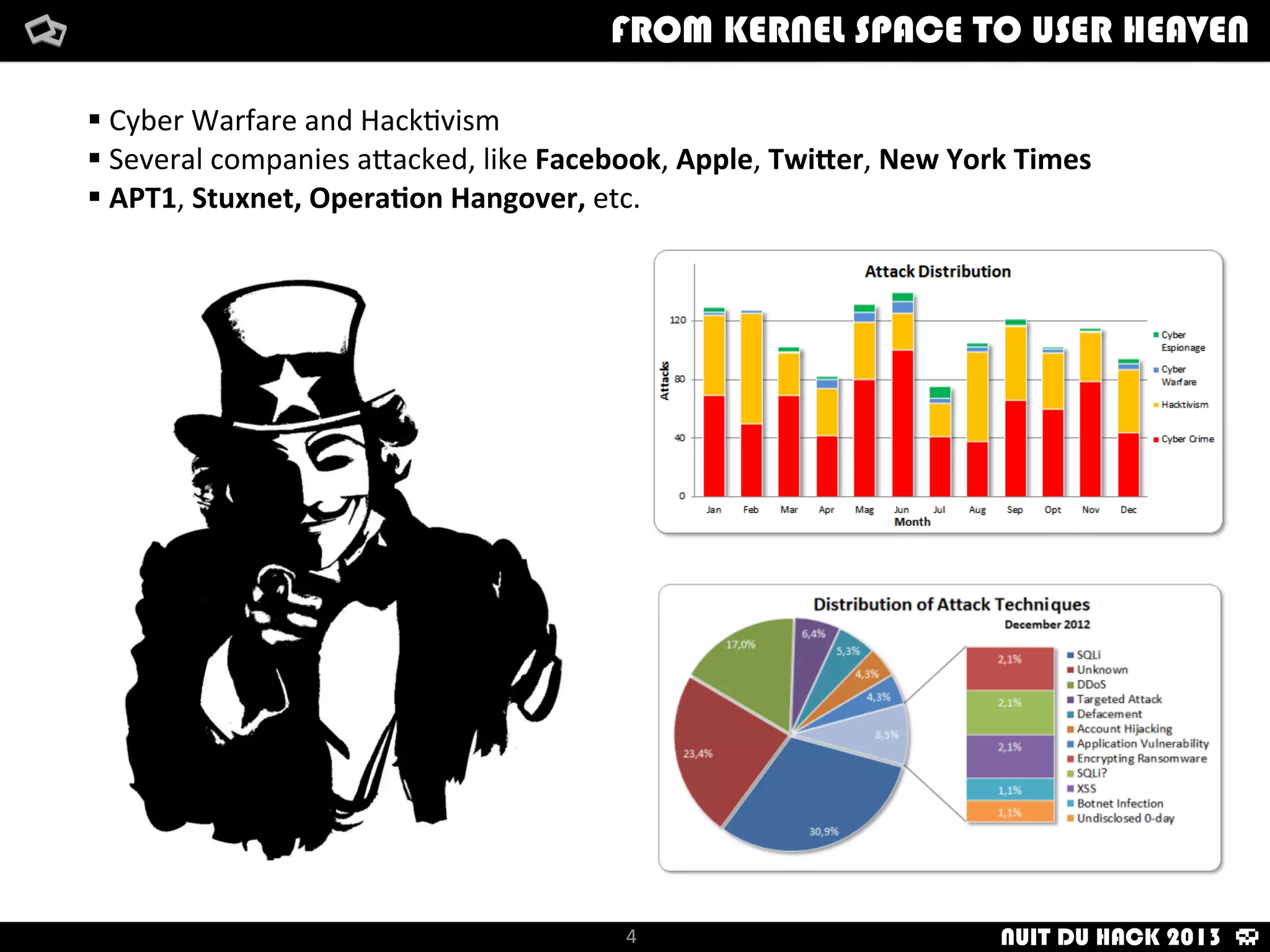
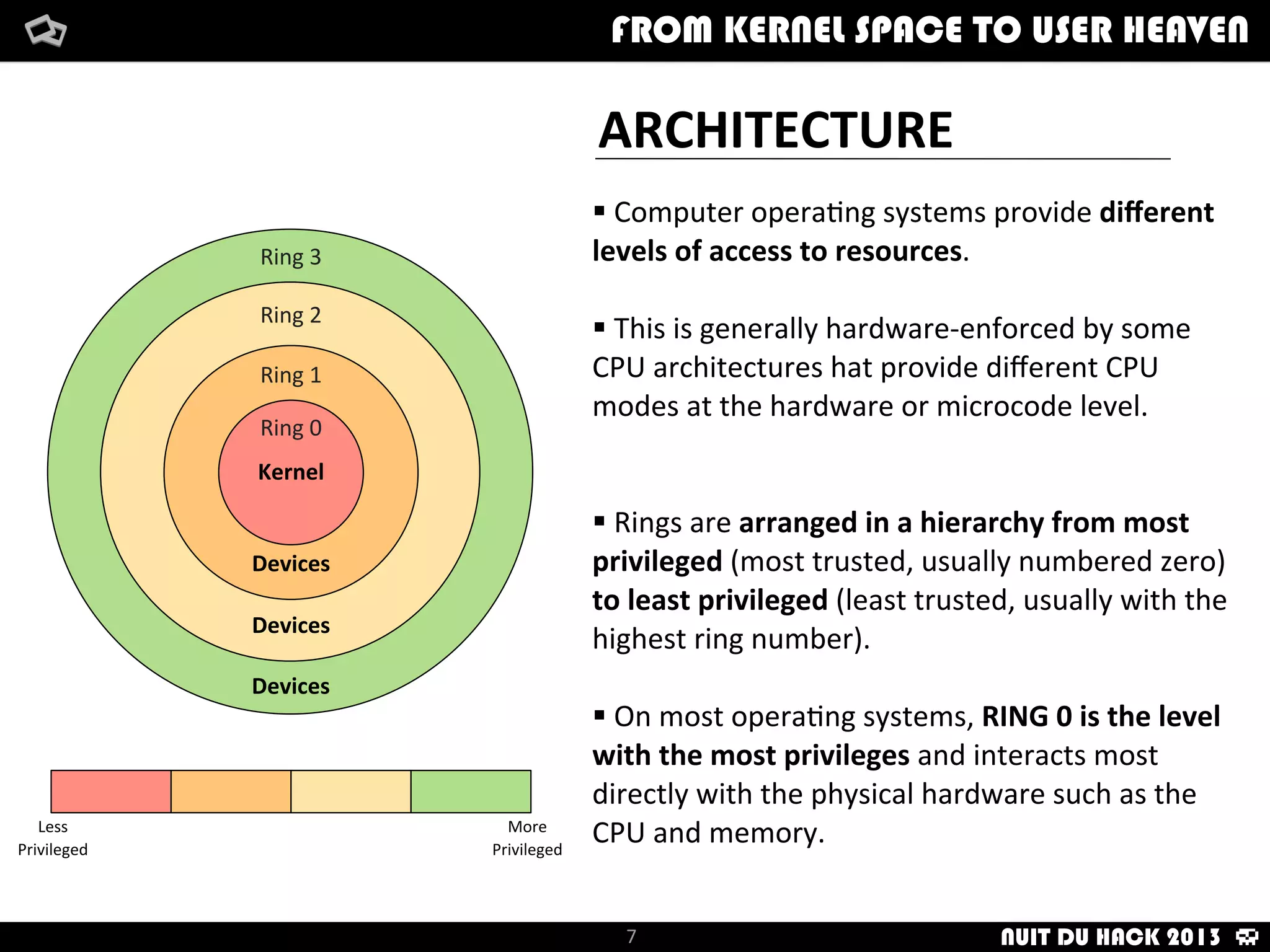
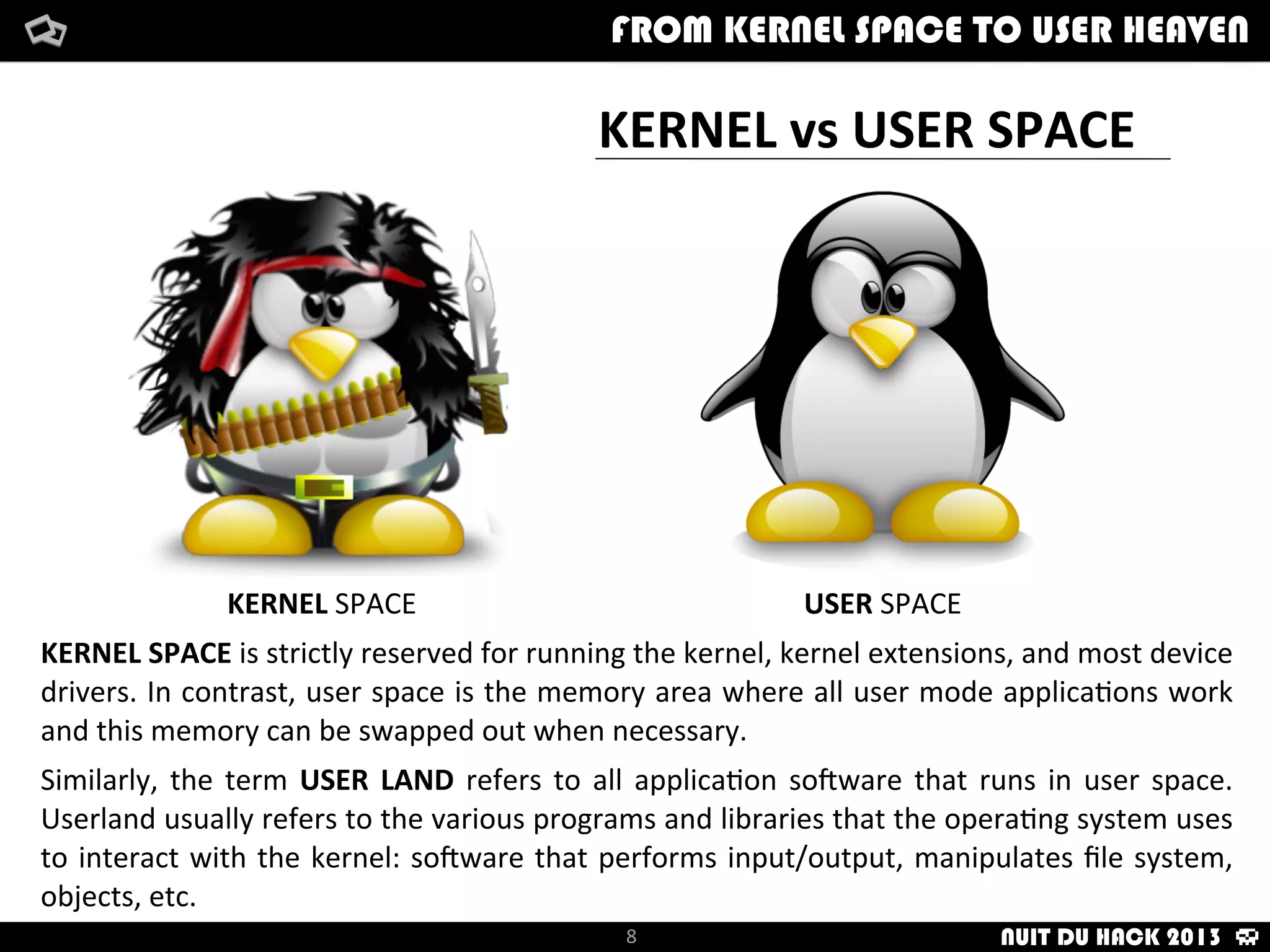
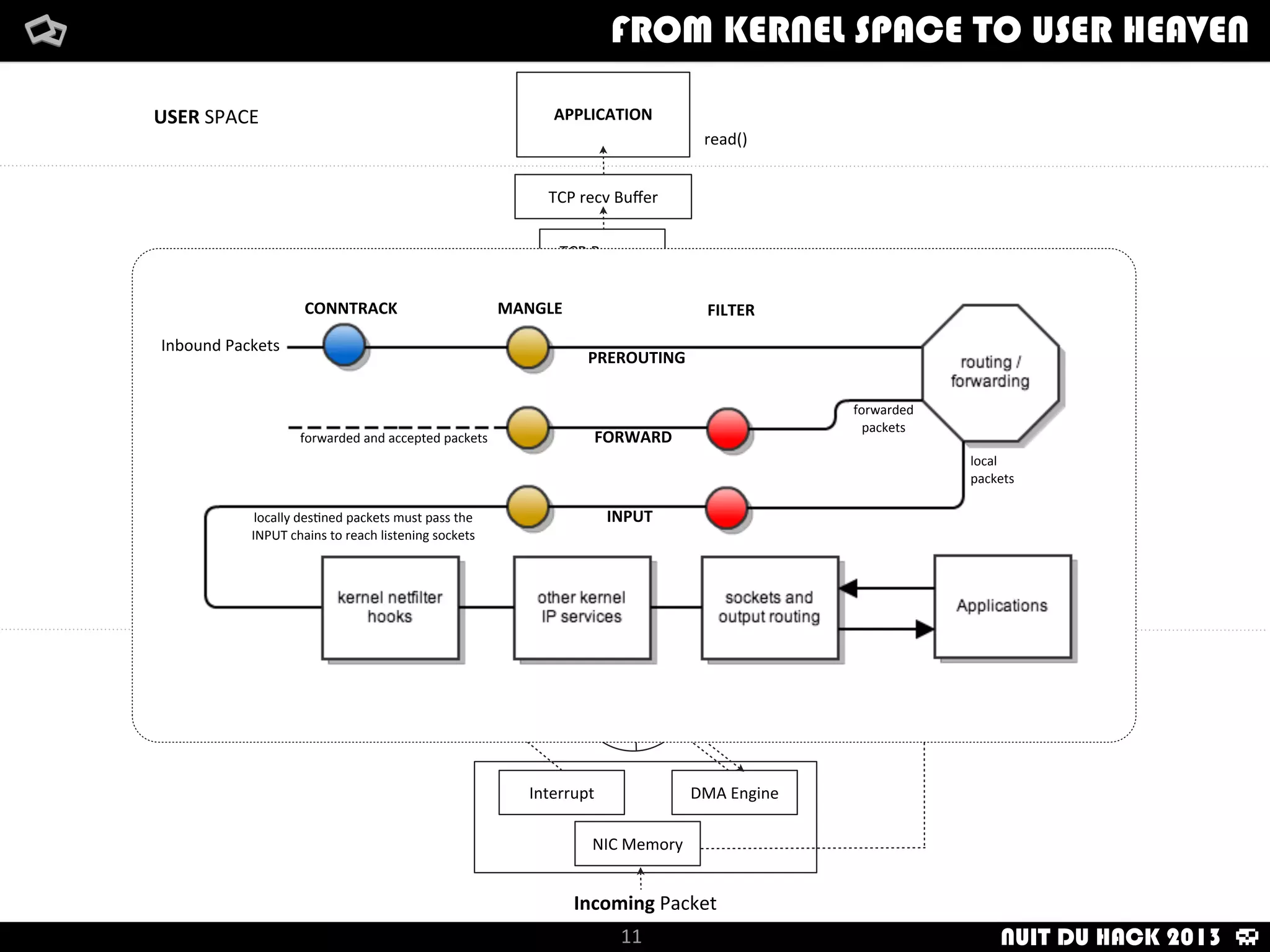
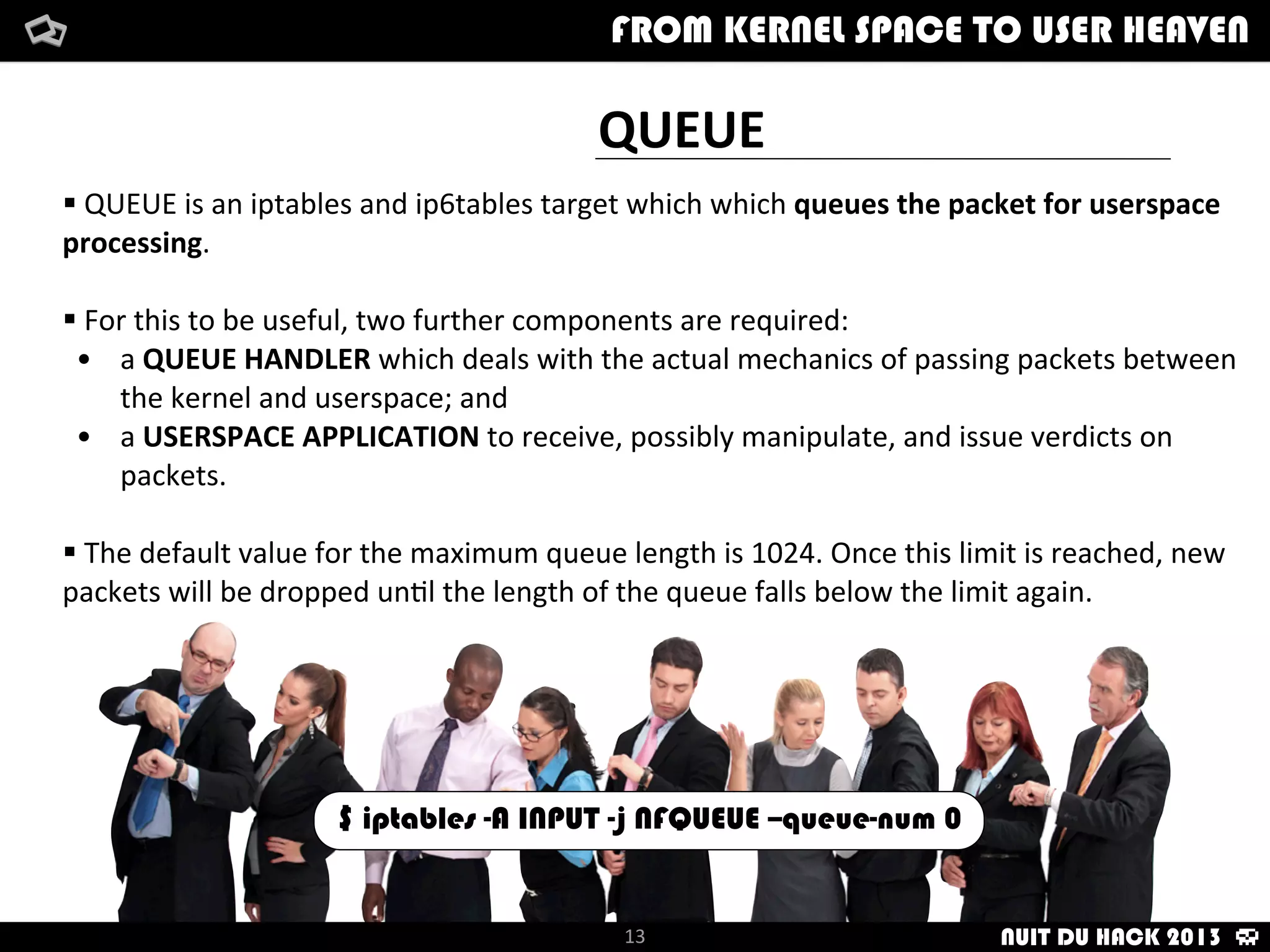
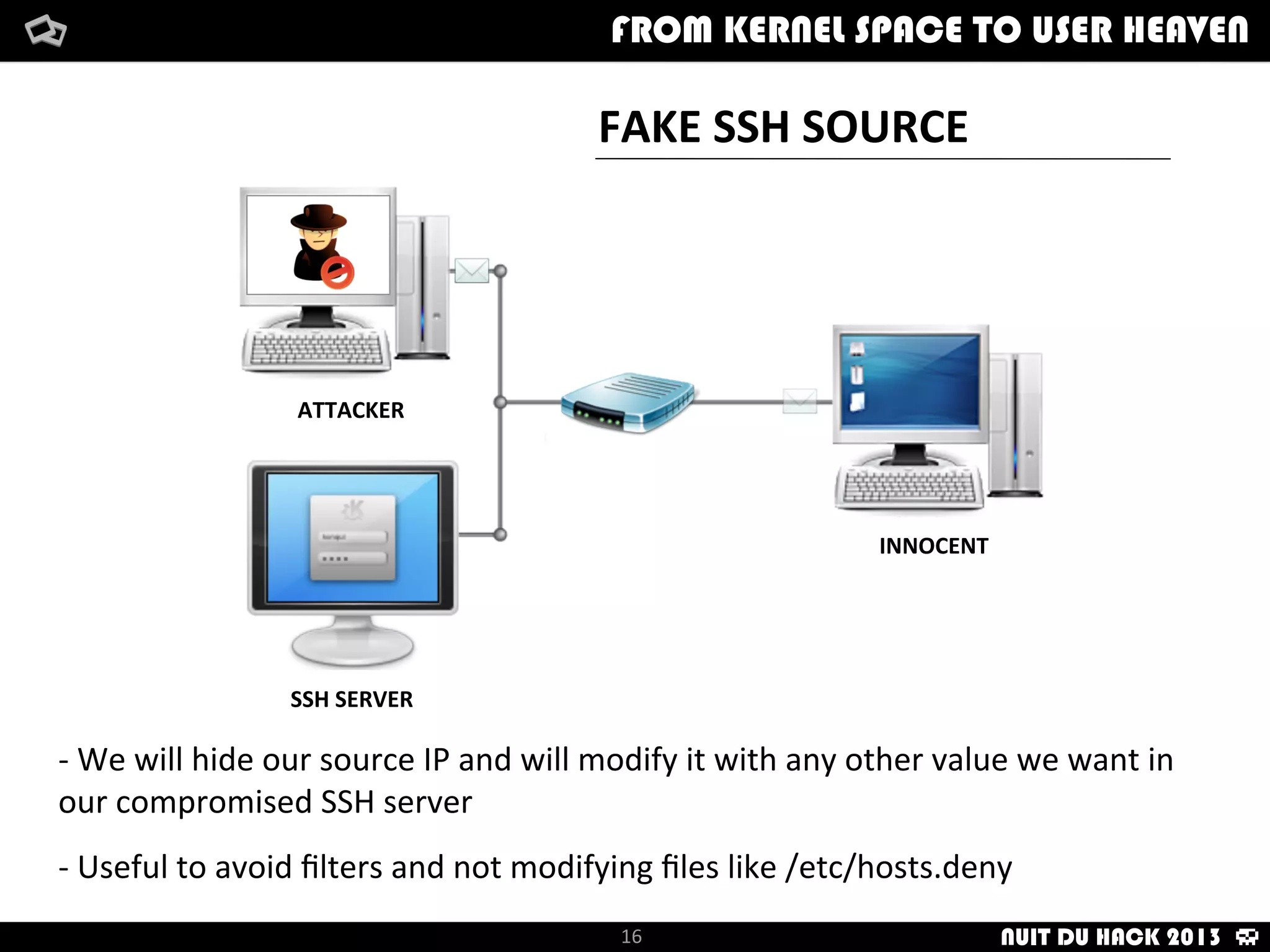
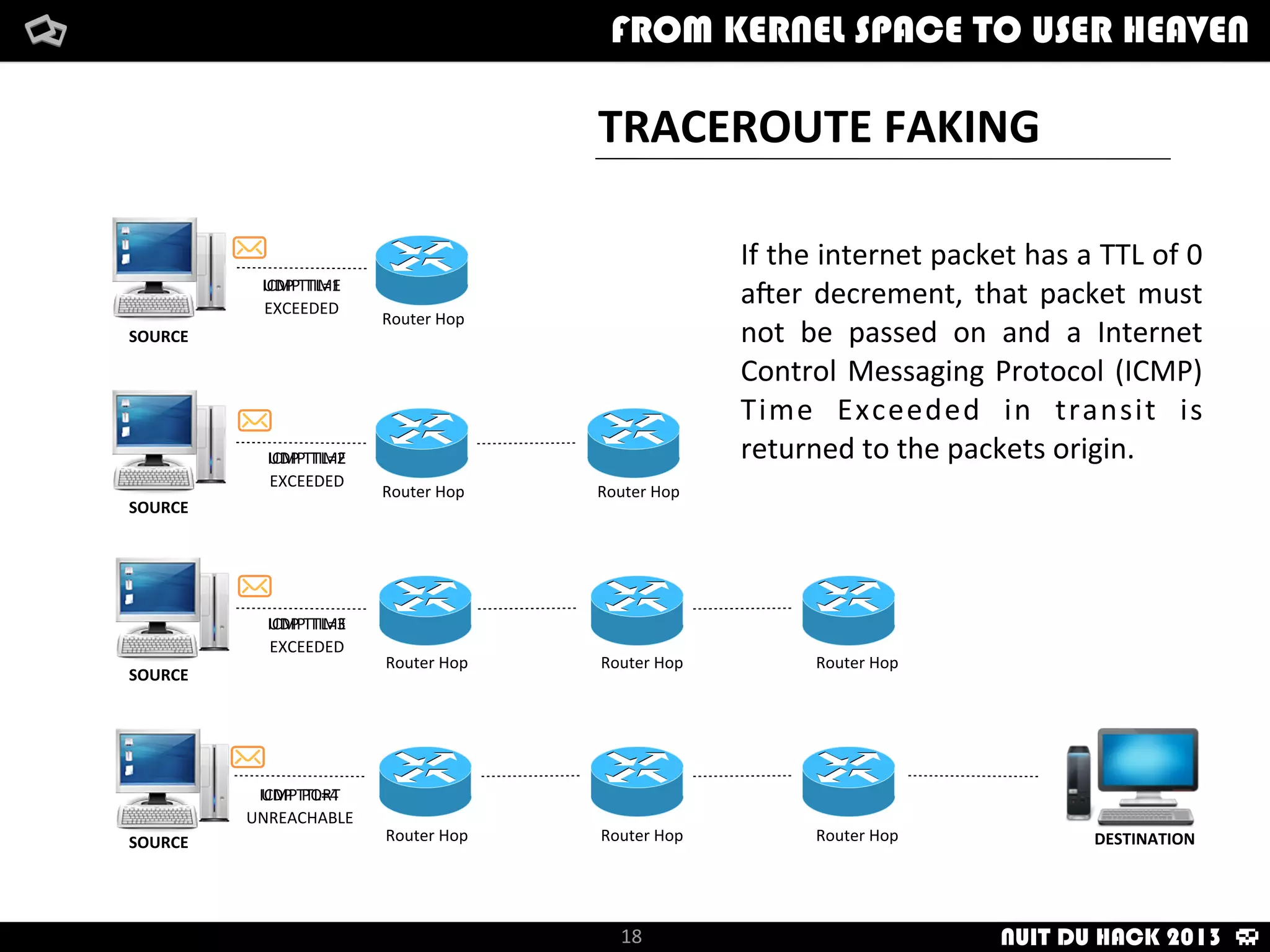
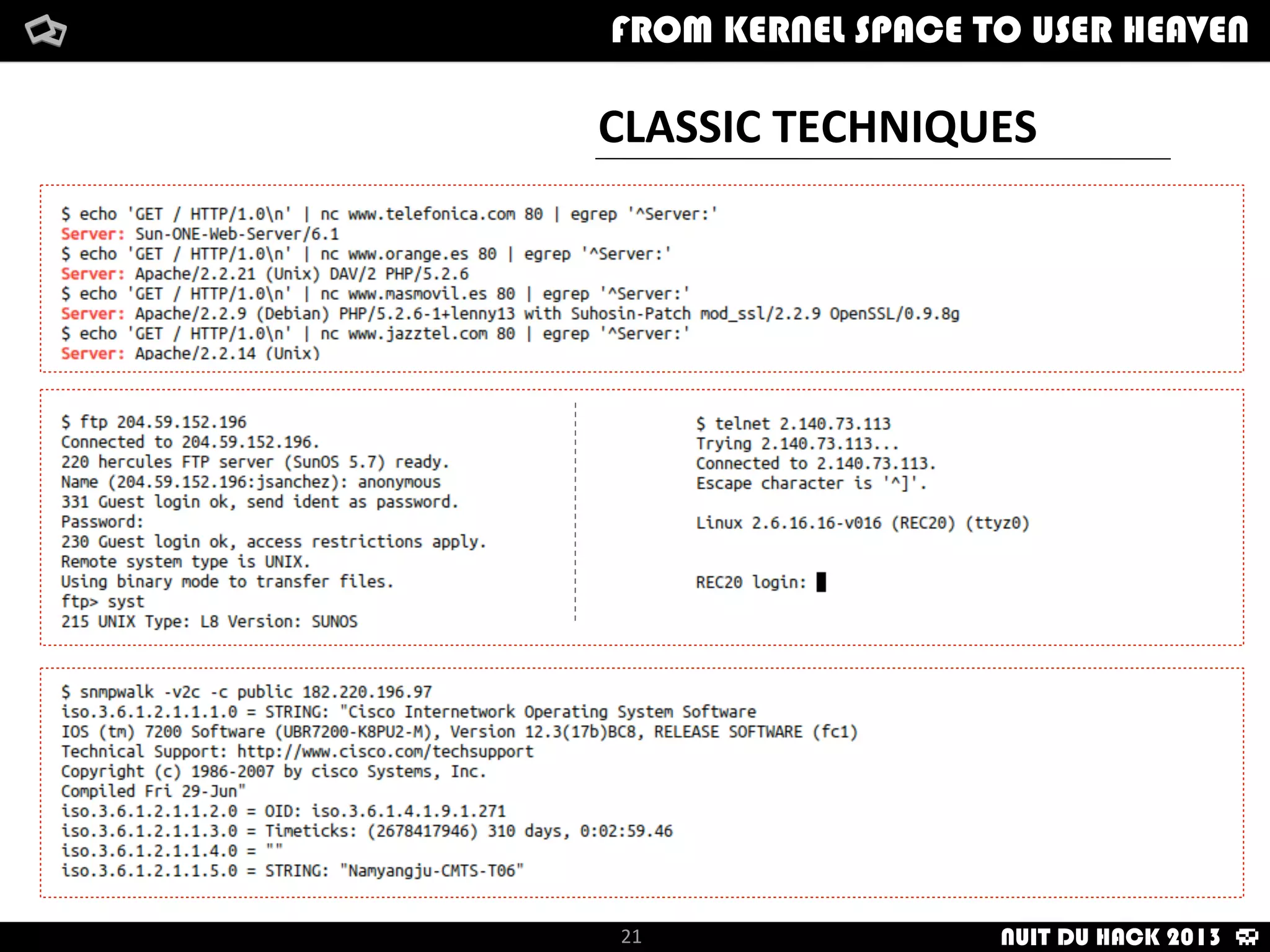
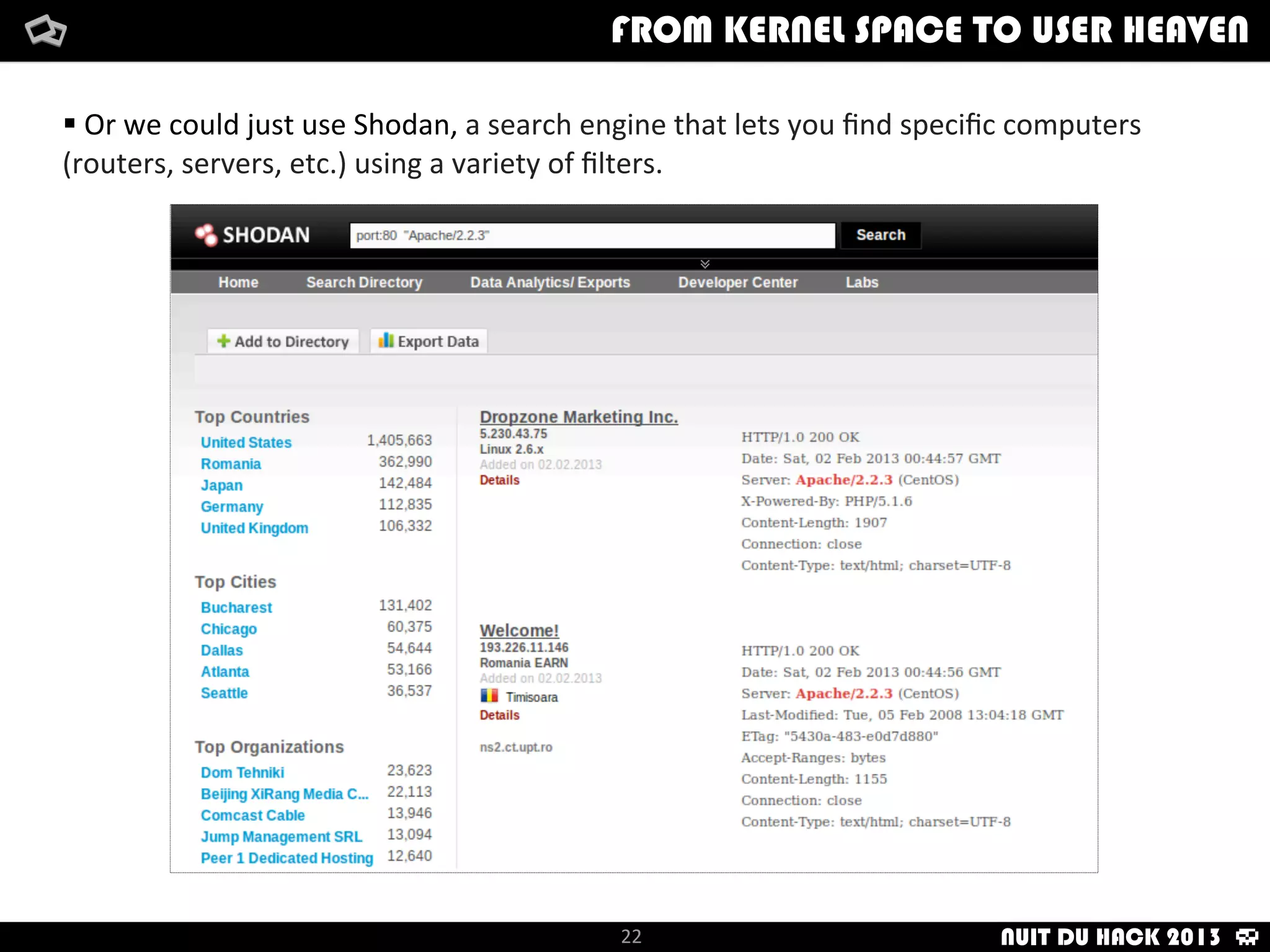
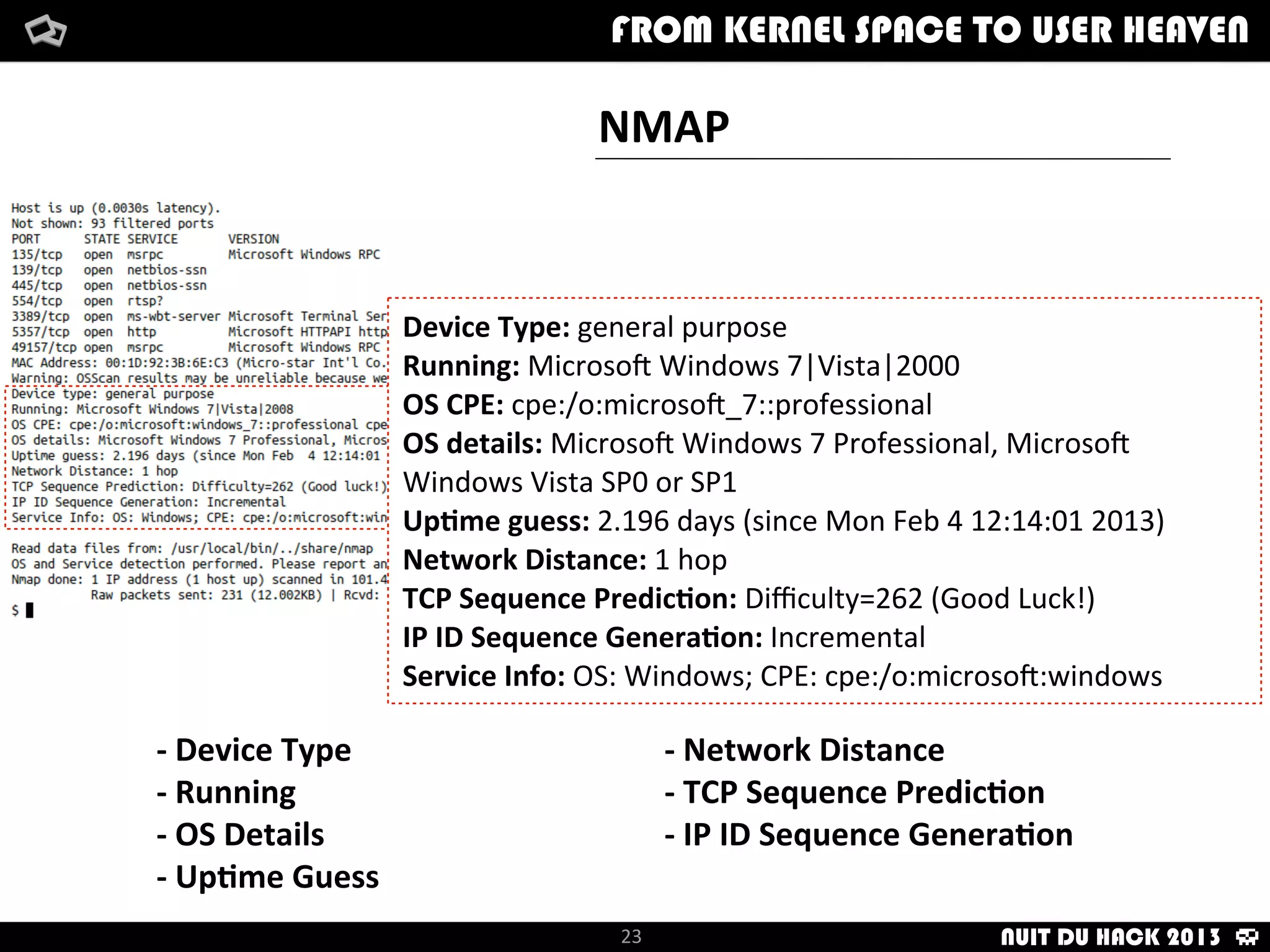
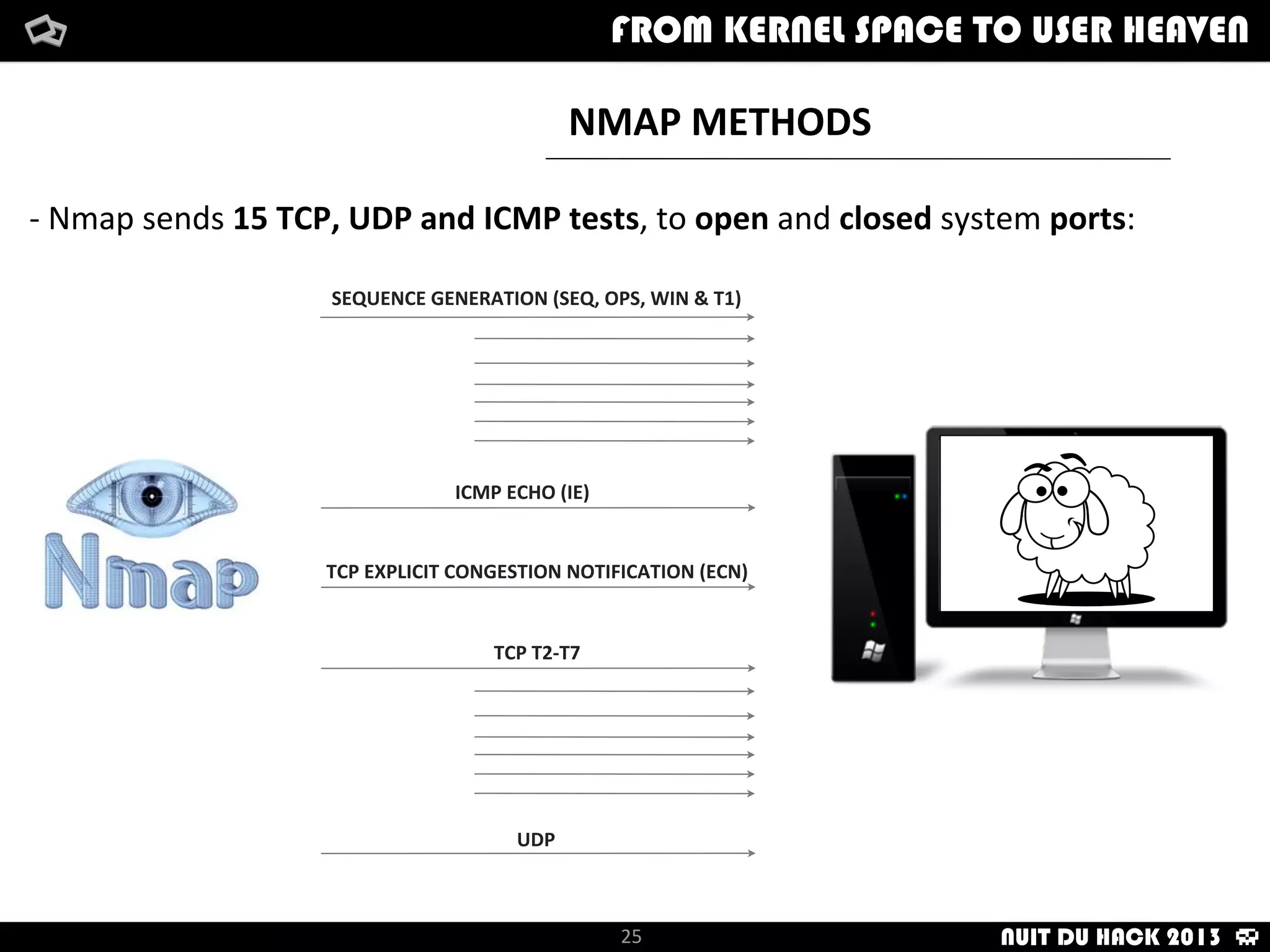
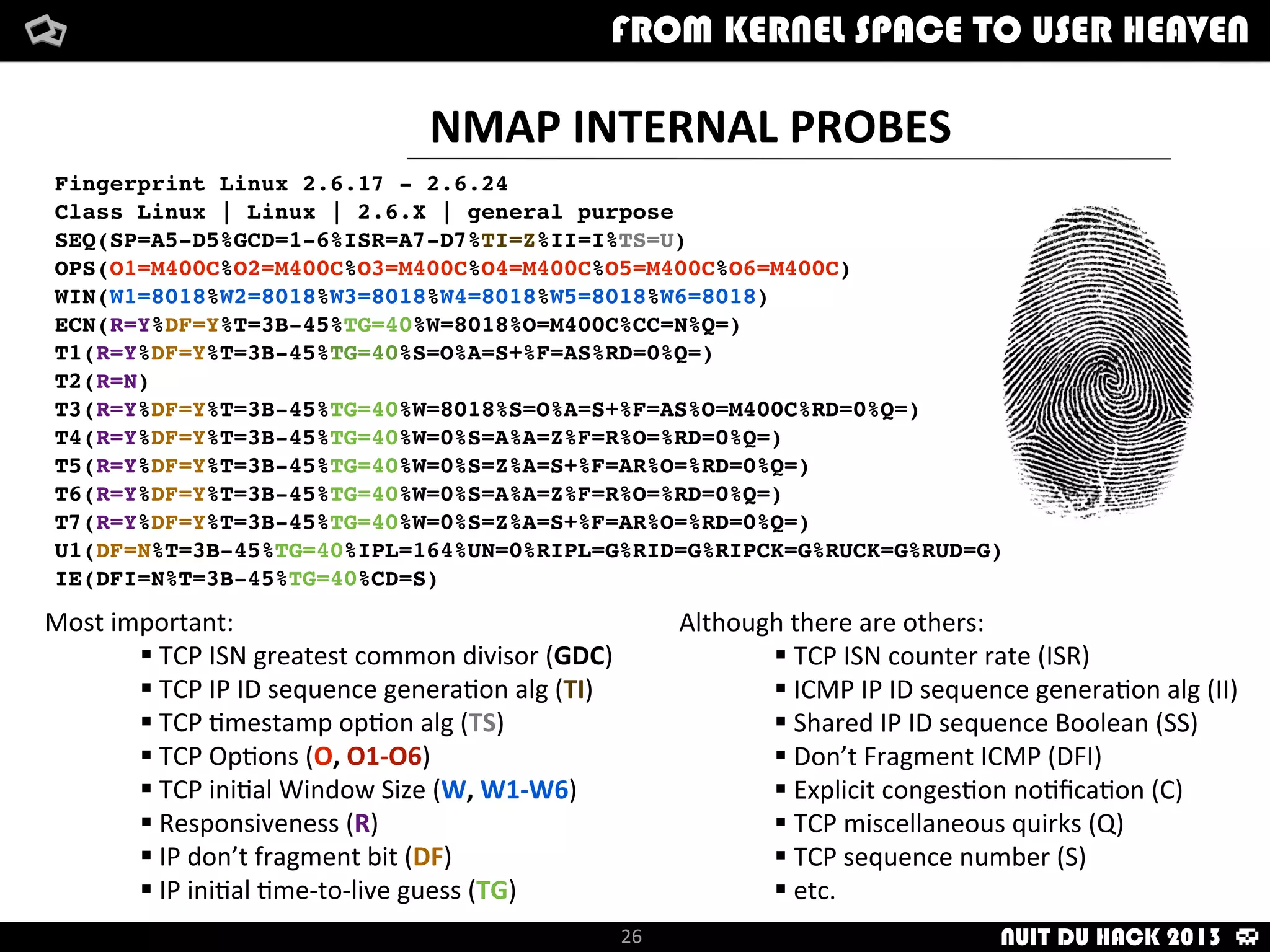
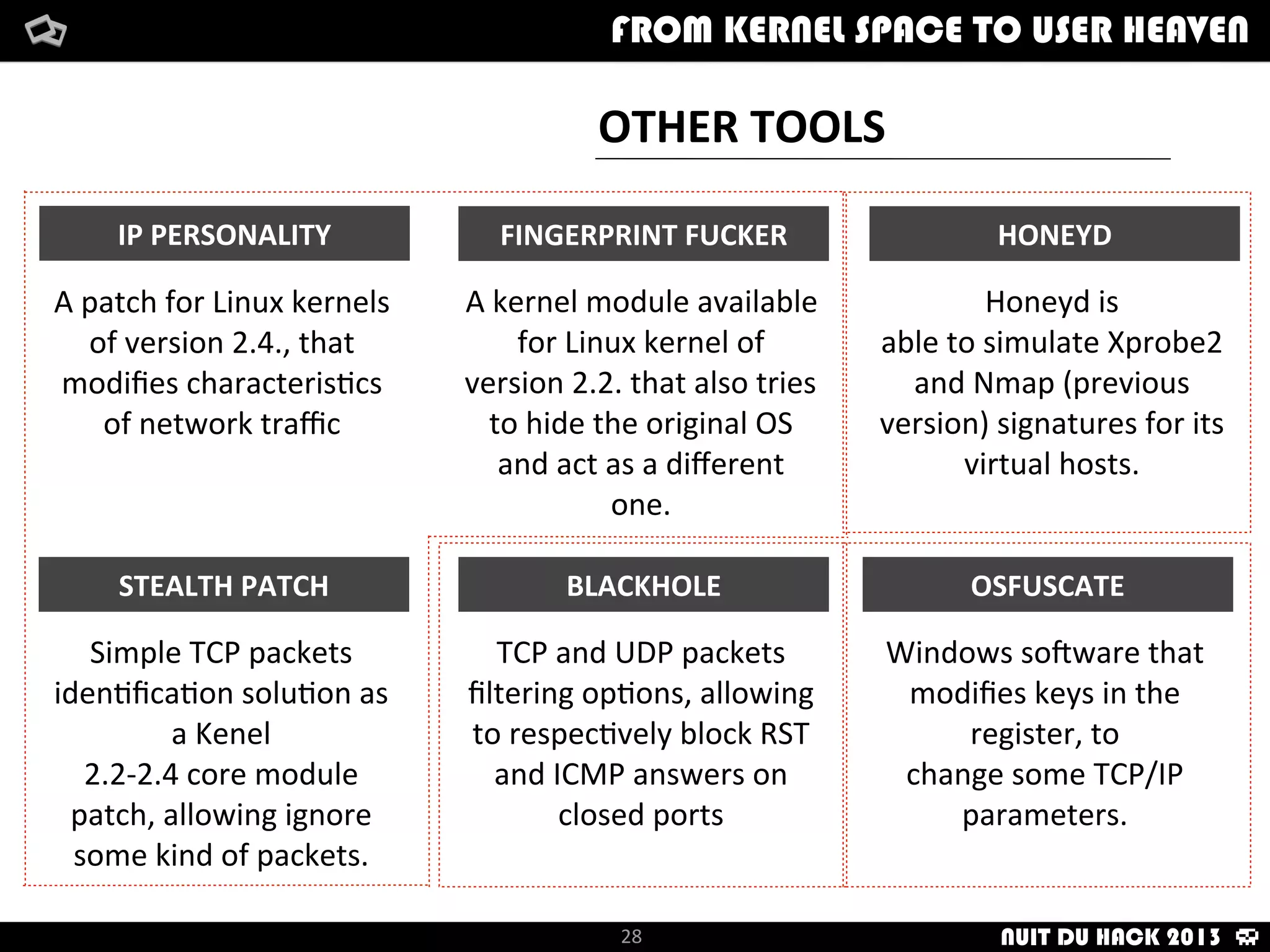
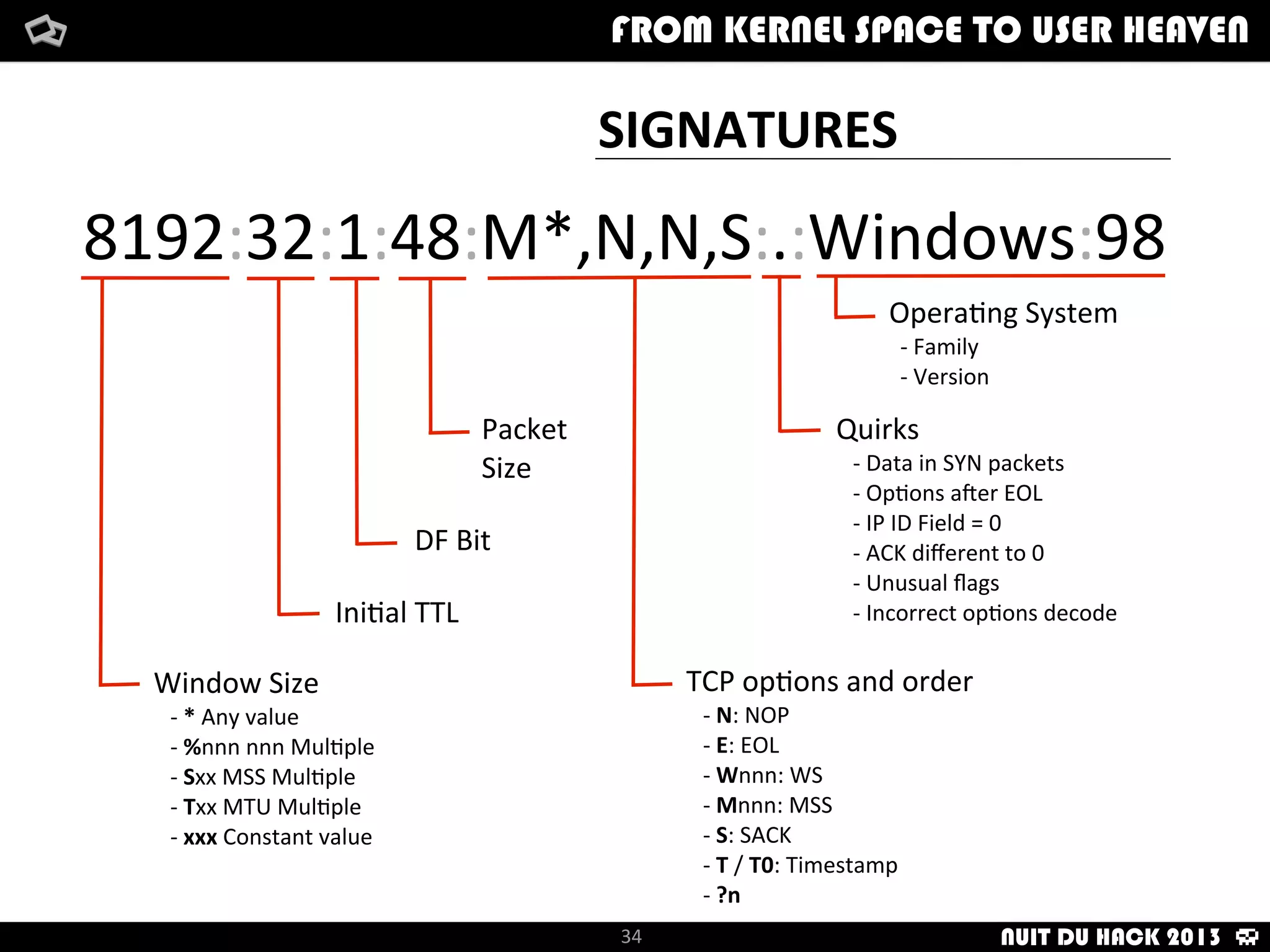
Jaime Sánchez presents techniques to improve cybersecurity against advanced persistent threats (APTs) during his talk at Nuit du Hack 2013, emphasizing the importance of reconnaissance and scanning phases in thwarting attacks. He discusses kernel and user space interactions, as well as various tools and methods for remote OS fingerprinting and stealth techniques to obscure the true nature of systems. The presentation highlights the use of both active and passive fingerprinting tools to enhance security and evade detection.