Embed presentation
Download as PDF, PPTX




























The document provides an overview of dynamic and static linking, explaining the differences in symbol resolution at linking time versus execution time. It details the linking process involving object files and the role of linkers in merging, relocating, and resolving symbols, as well as the ELF (Executable and Linkable Format) structure. Additionally, it covers the functions of static libraries and dynamic shared libraries, along with specifics related to Solaris linking processes.











































Overview of dynamic and static linking, advantages and disadvantages of each type.
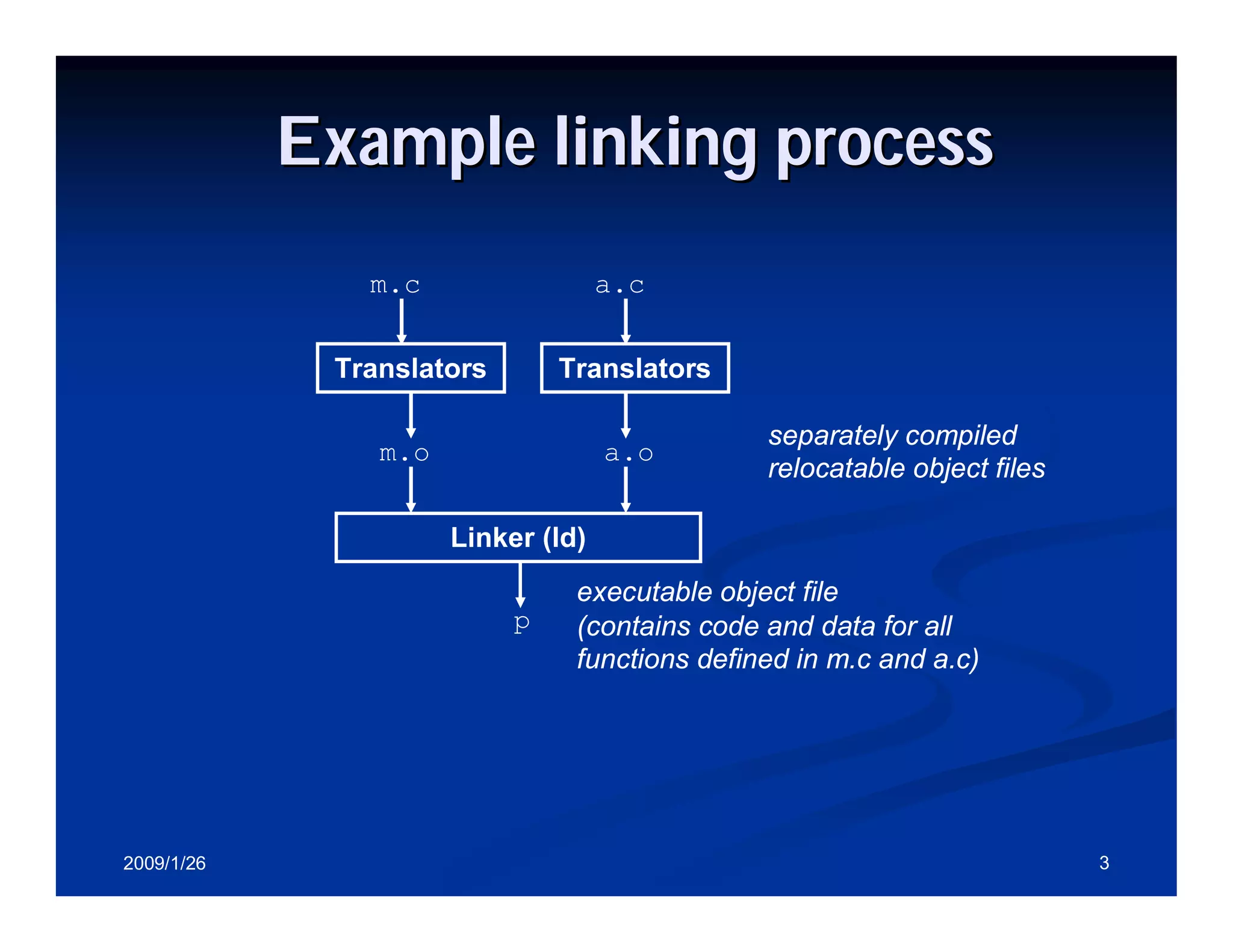
Functions of the linker: merging files, resolving references, relocating symbols, and ELF format details.
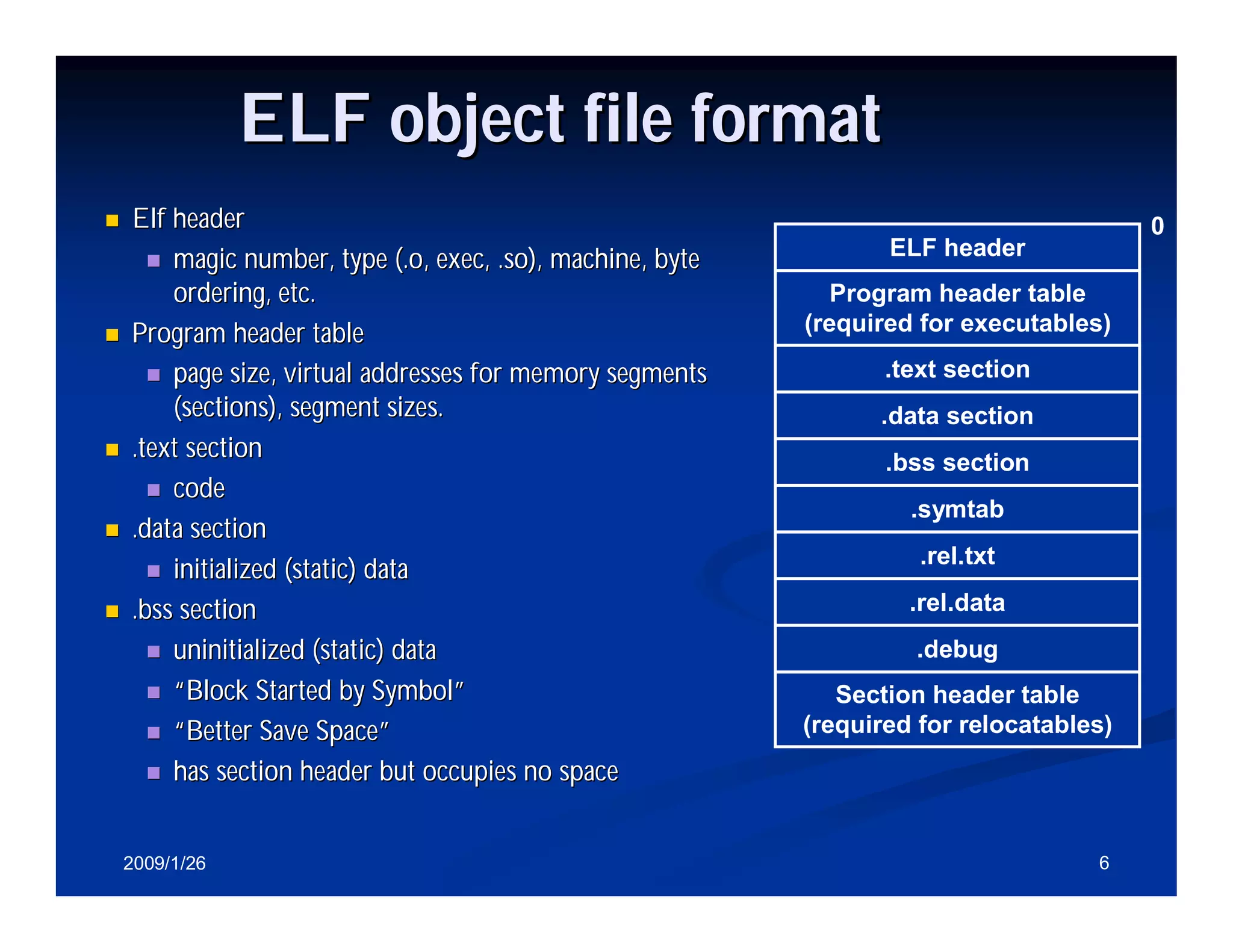
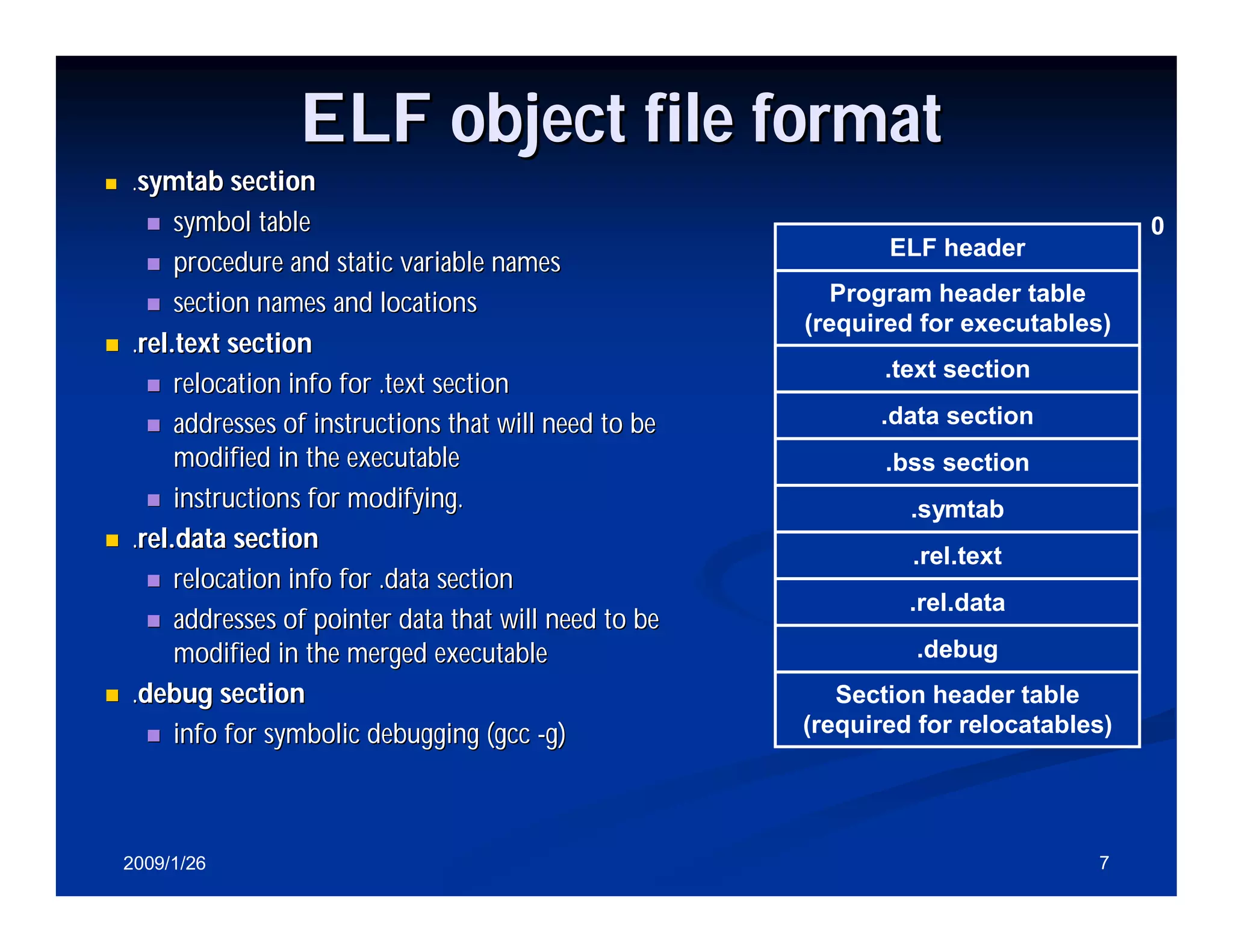
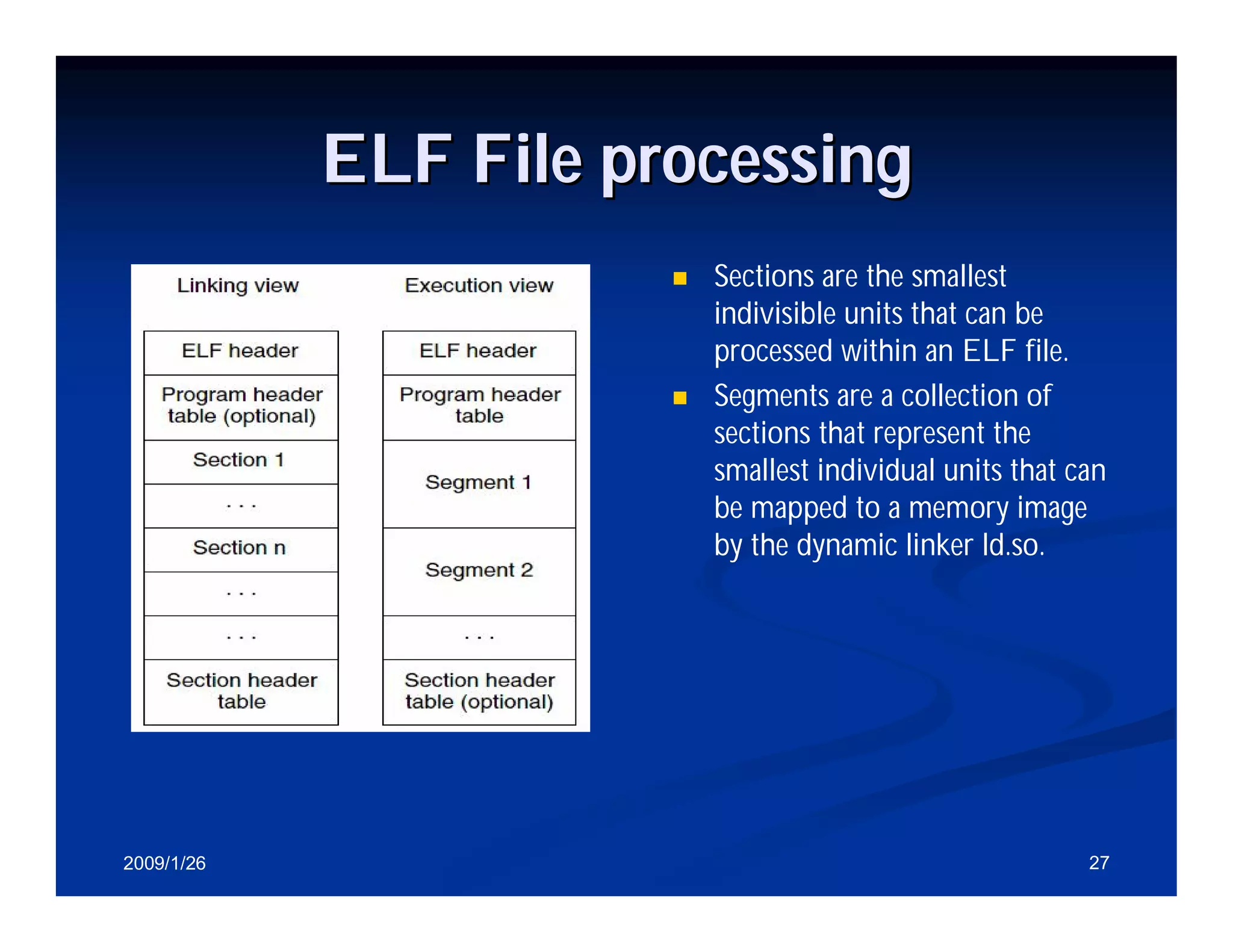
Details about ELF object file format, including sections like .text, .data, and their purposes.
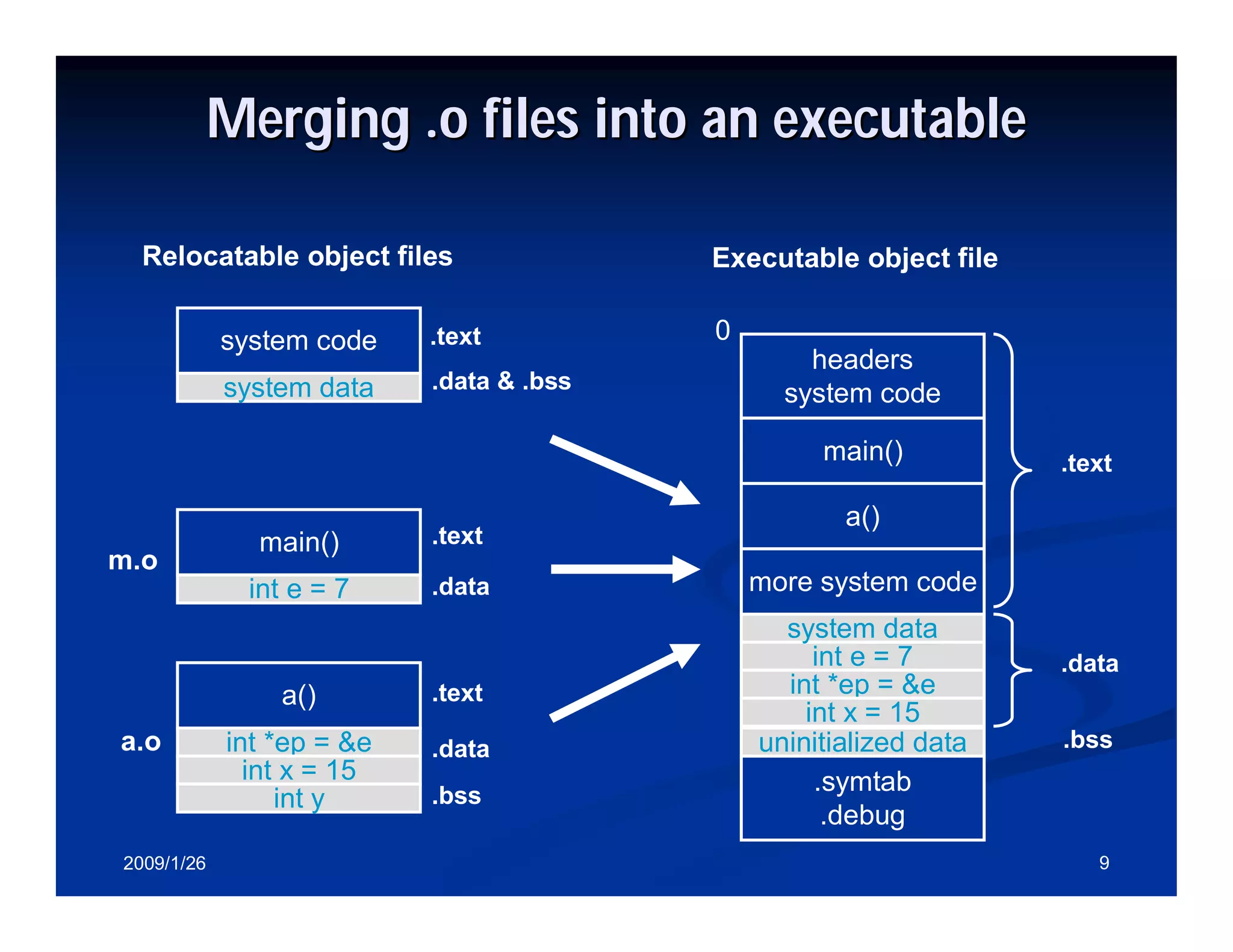
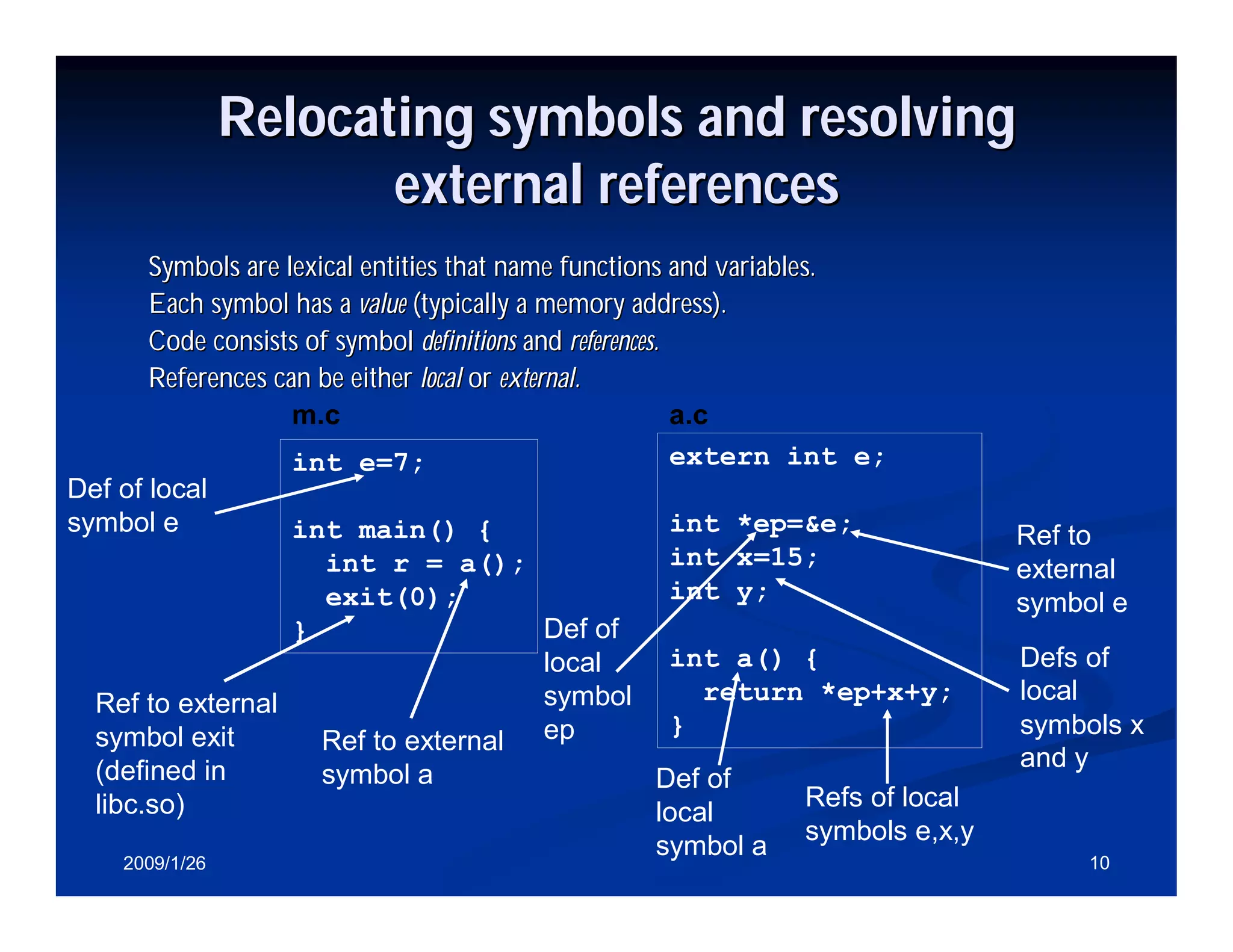
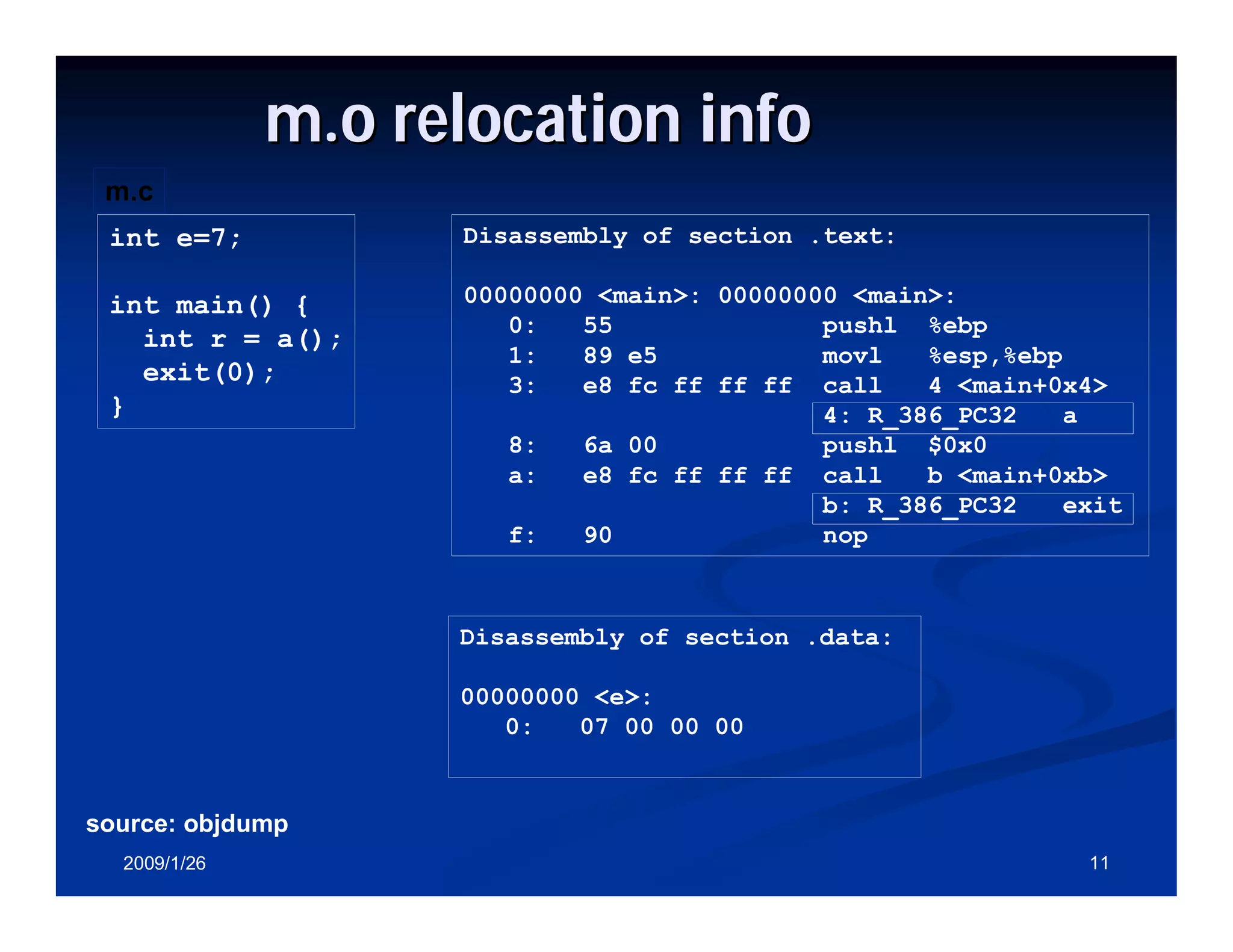
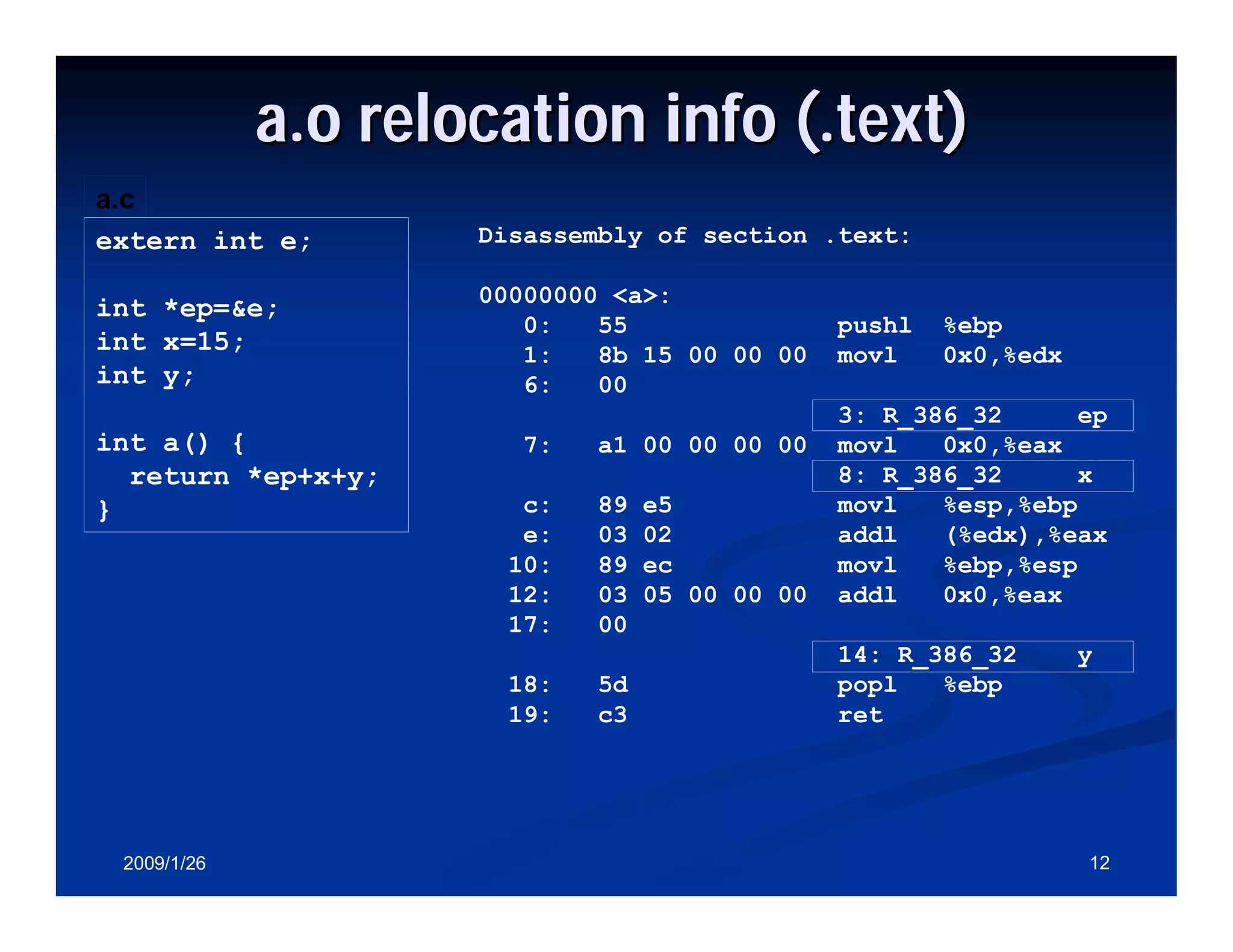
Process of merging object files into an executable and symbols relocation and external references resolution.
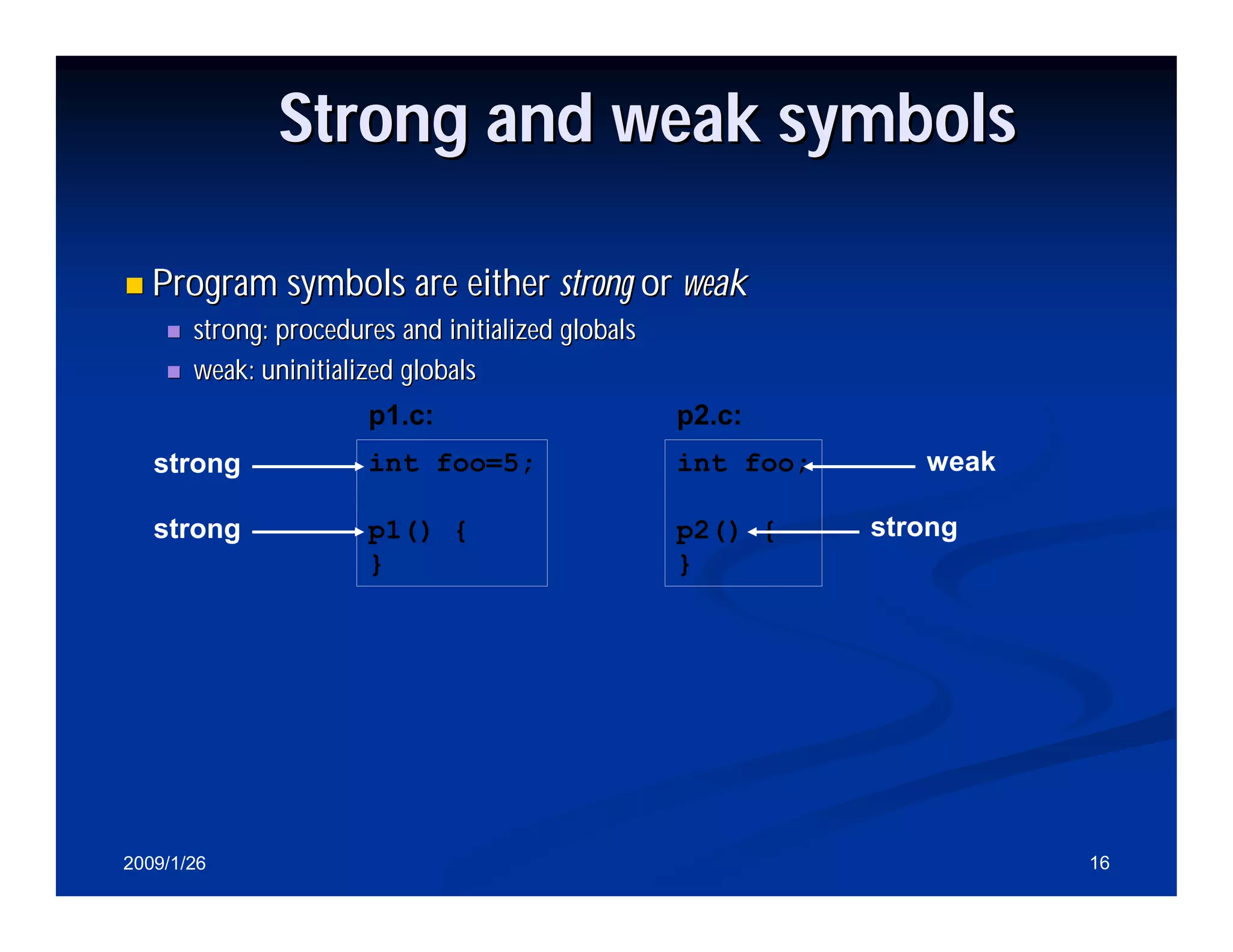
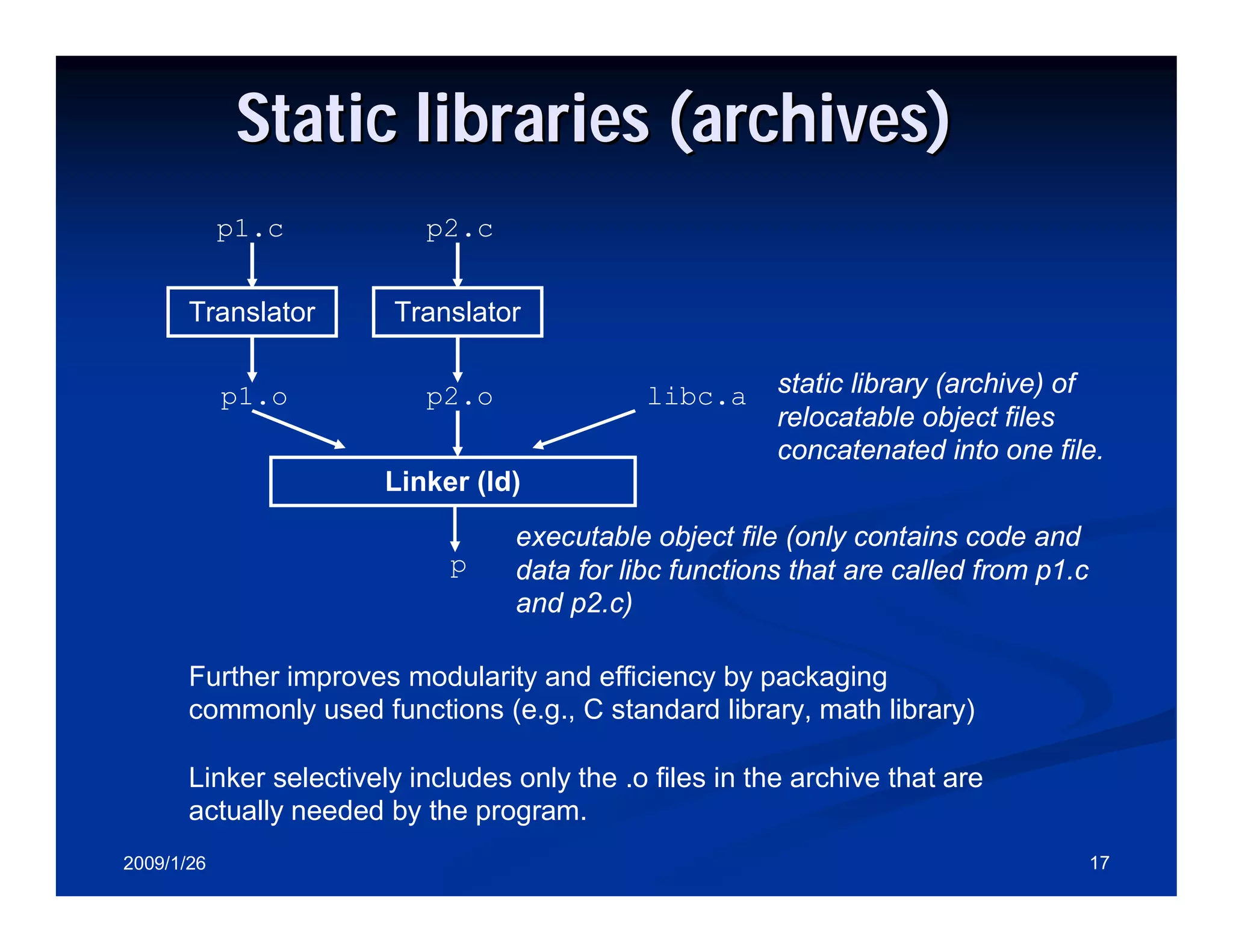
Different types of symbols in programs: strong vs weak symbols, and static libraries.
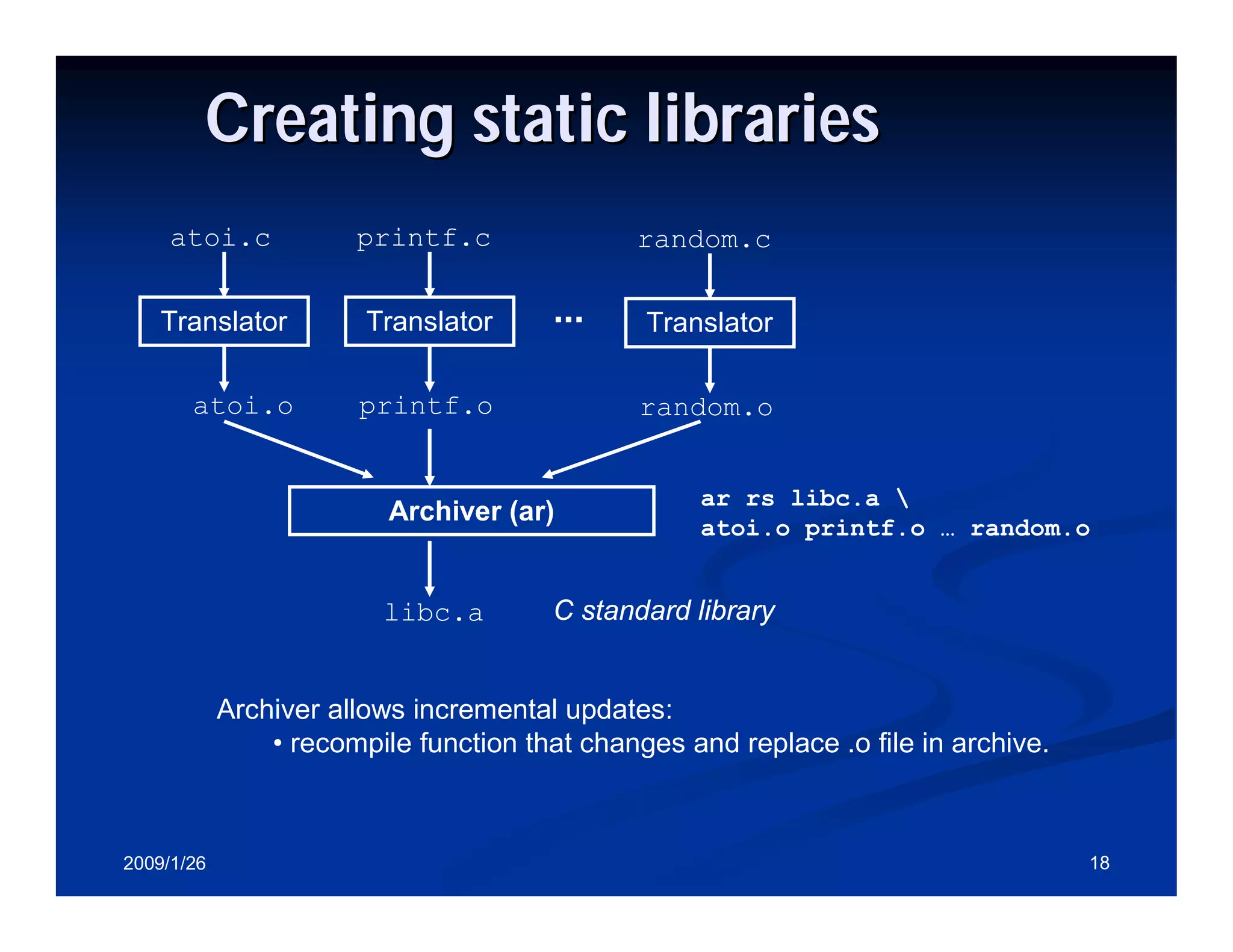
Process of creating static libraries including archiving object files into libraries.
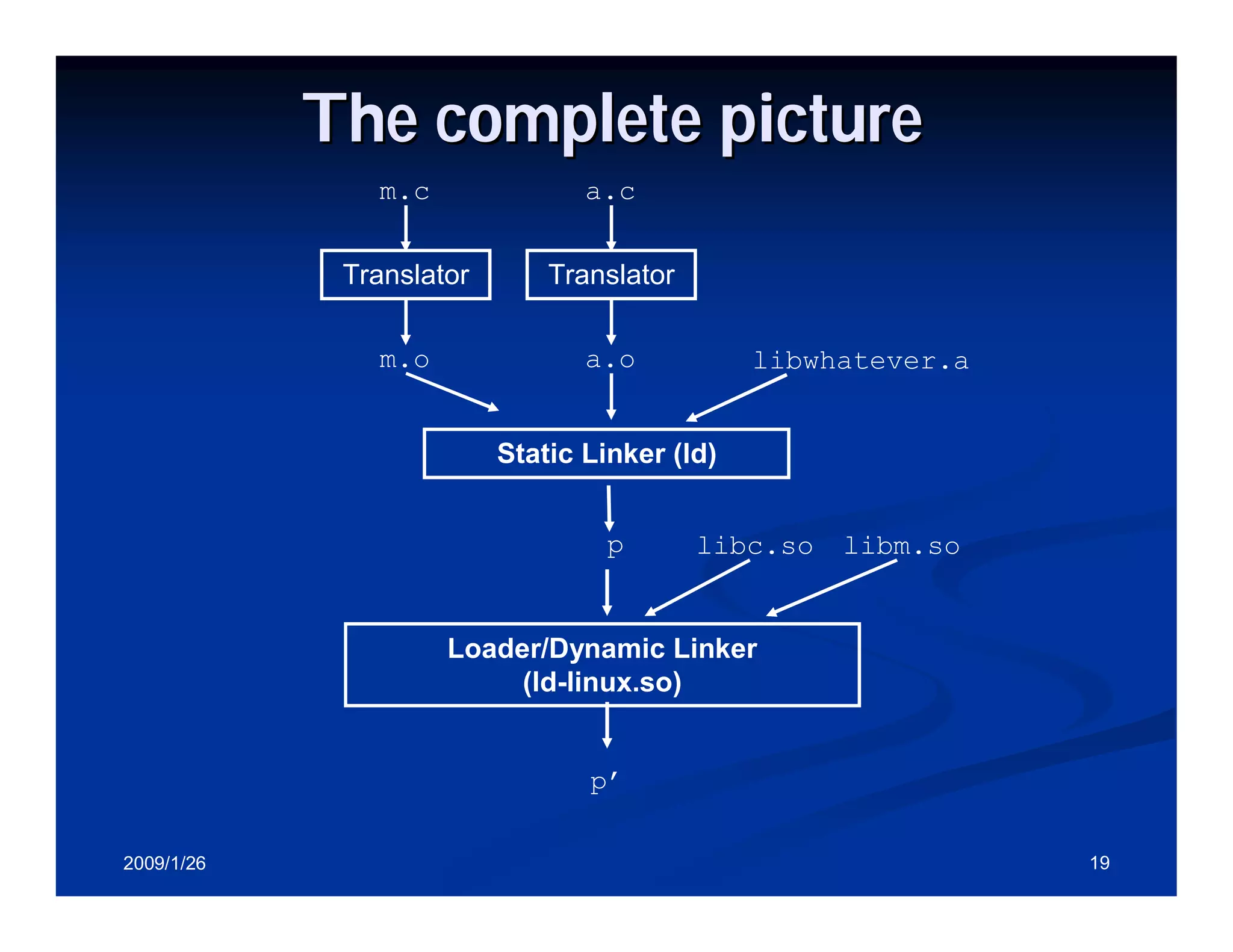
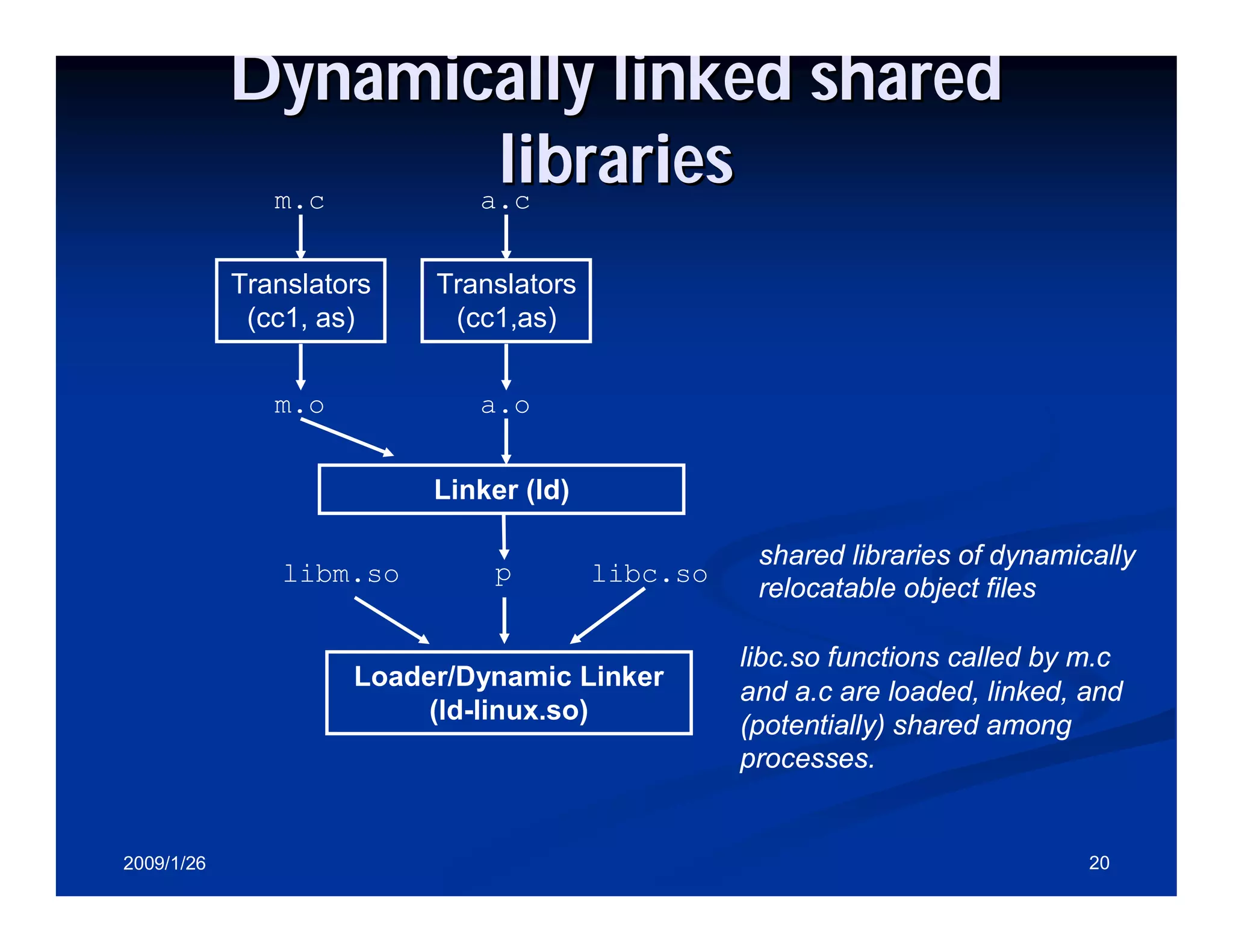
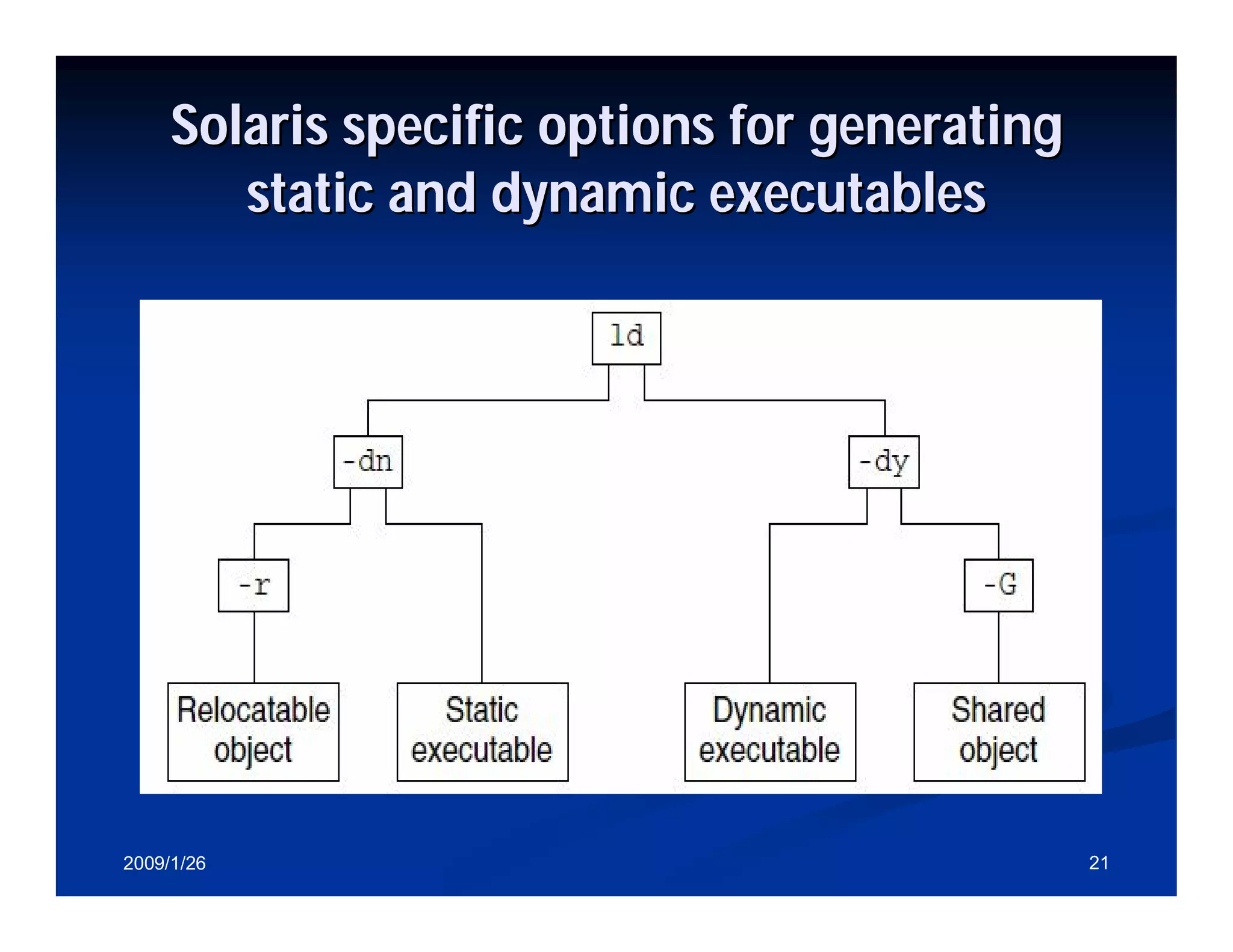
Explanation of dynamic linking including shared libraries, linking in Solaris, and link editor functions.
How the Link Editor processes symbols, handles relocations, and loads segments.
Process for resolving dependencies in a dynamic executable and inspecting required libraries.
Details about the symbol table structure, relocation processing, and delayed function binding.
General workings of Solaris runtime linker and details on ARM specific ELF header settings.
Special sections in ARM ELF files including symbol tables and debugging info.