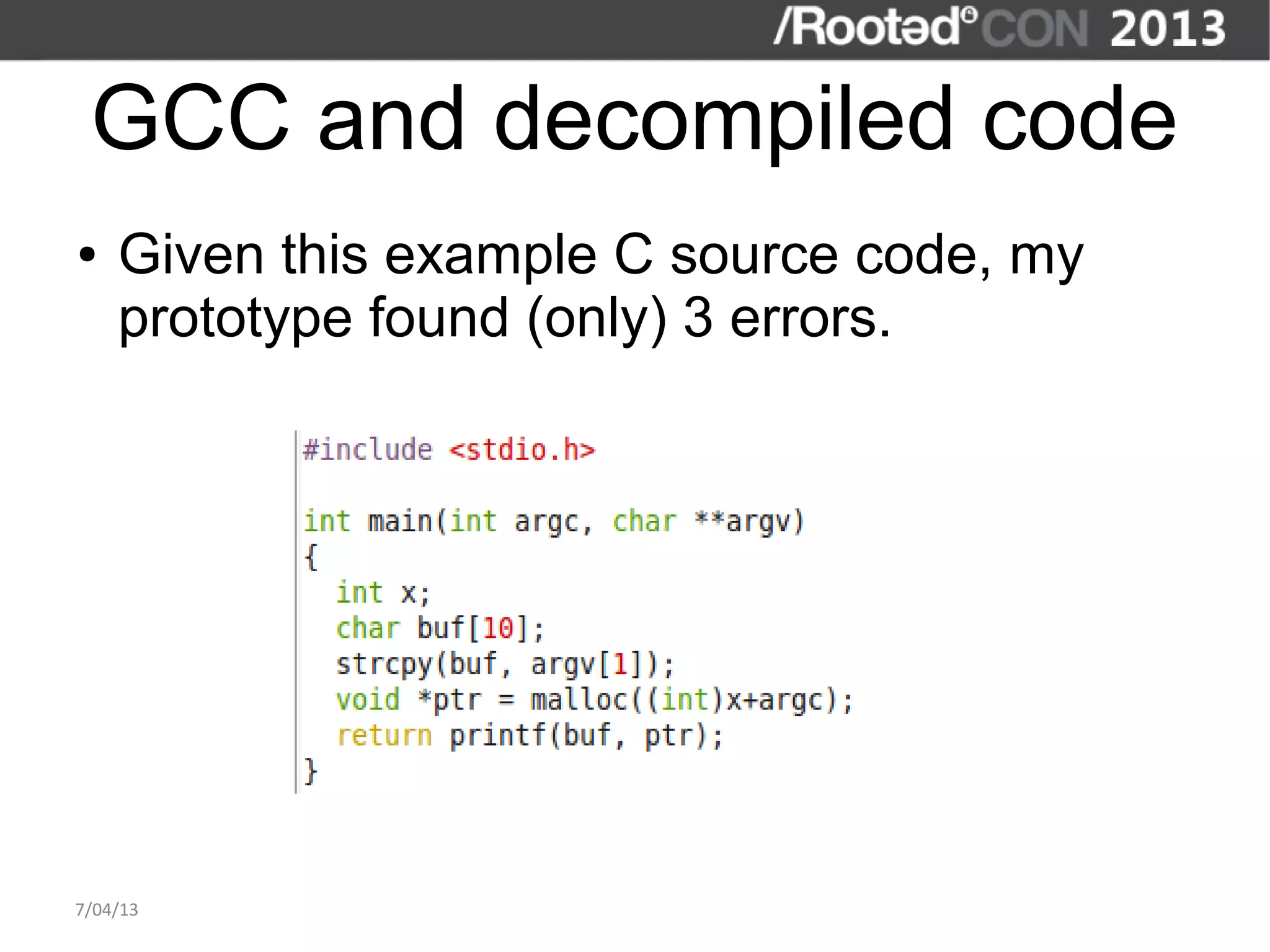
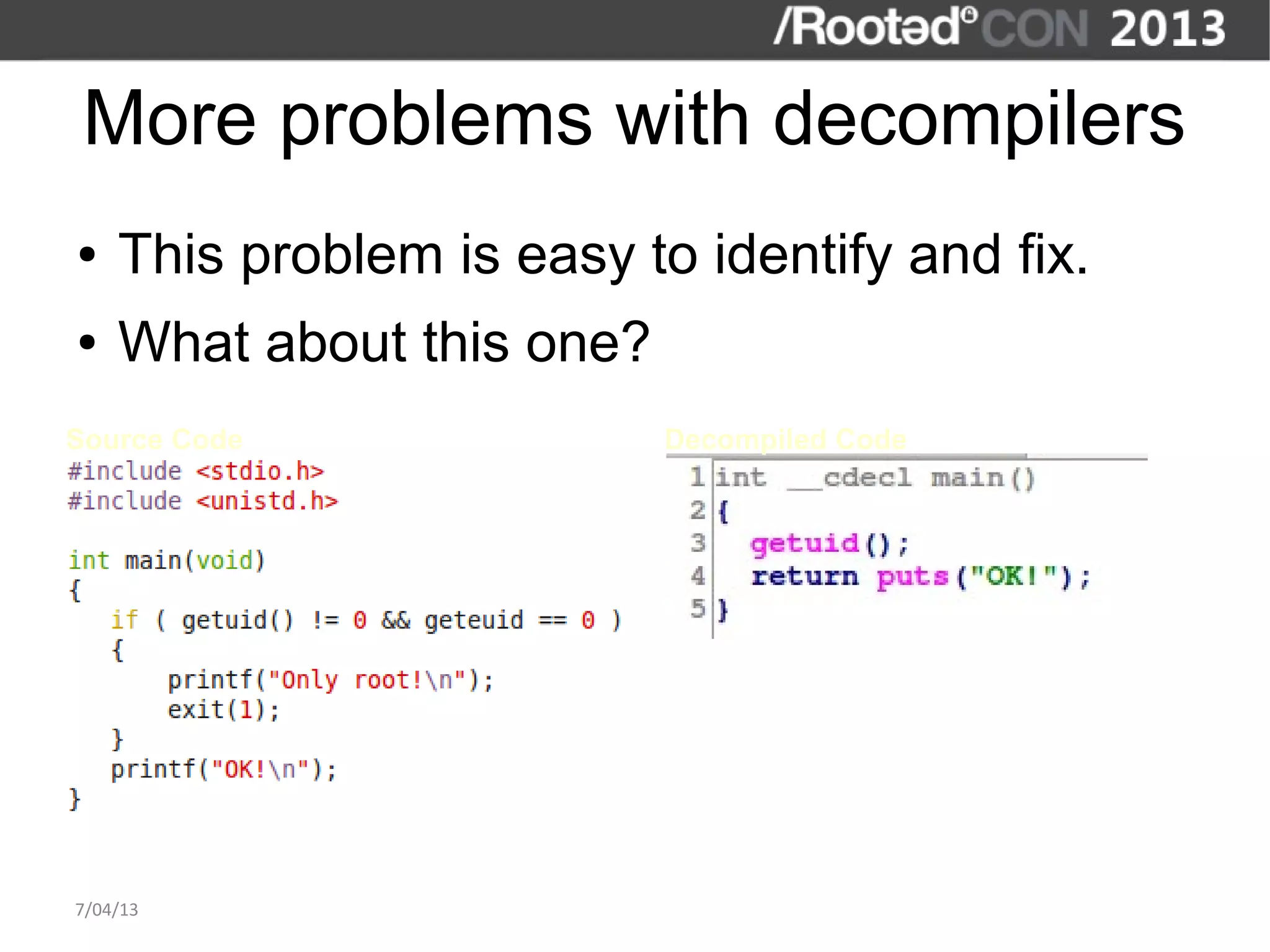
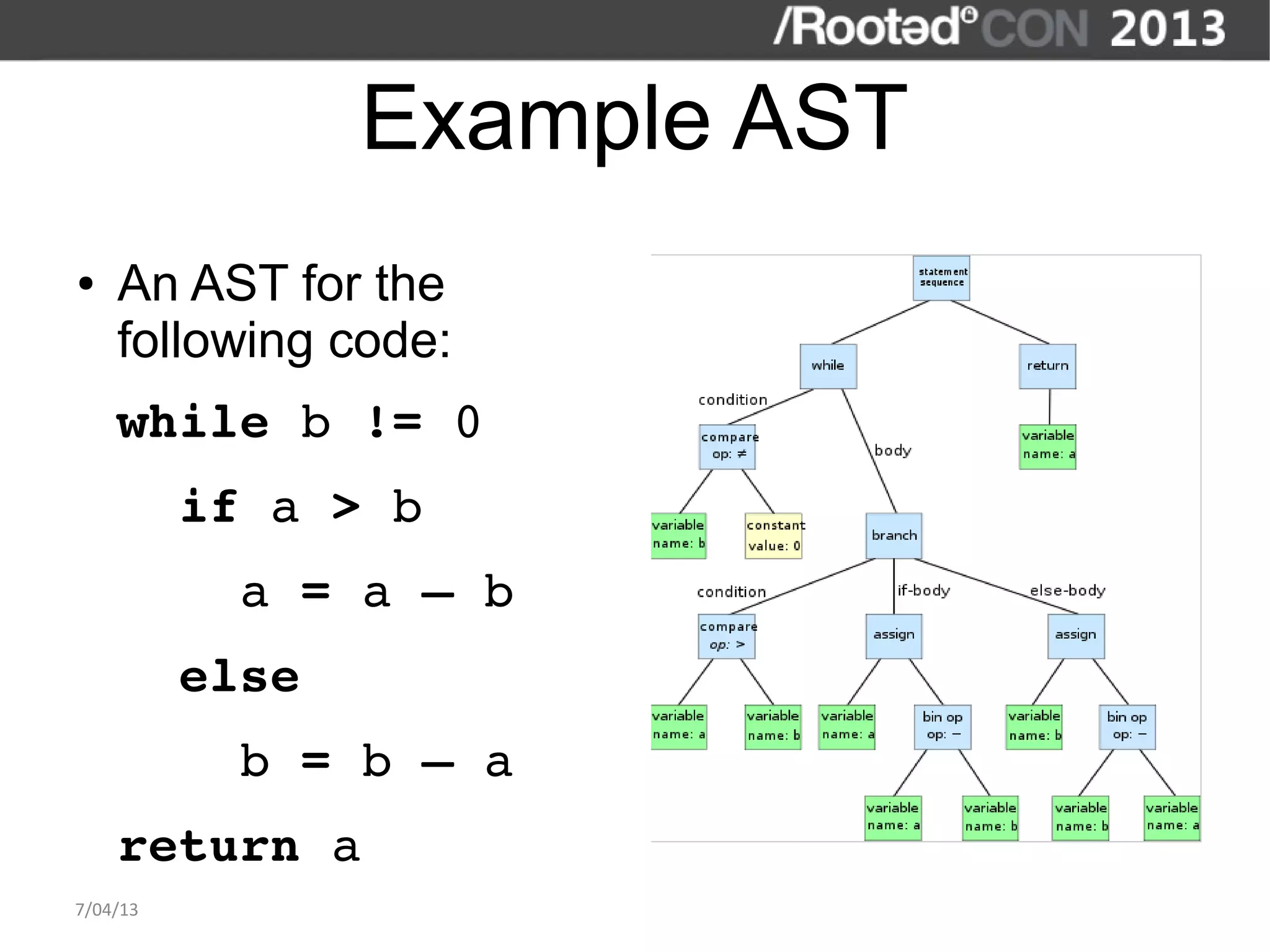
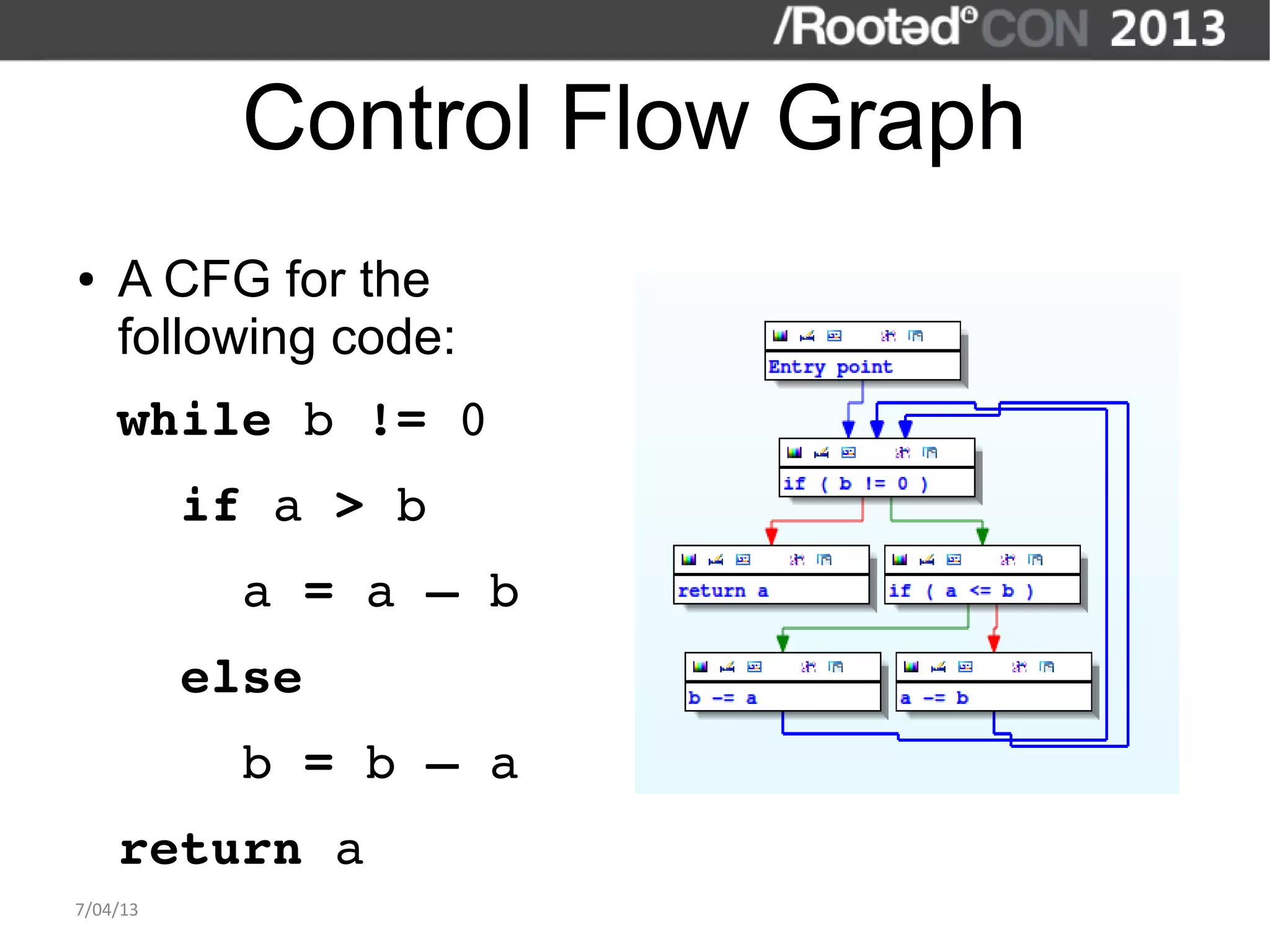
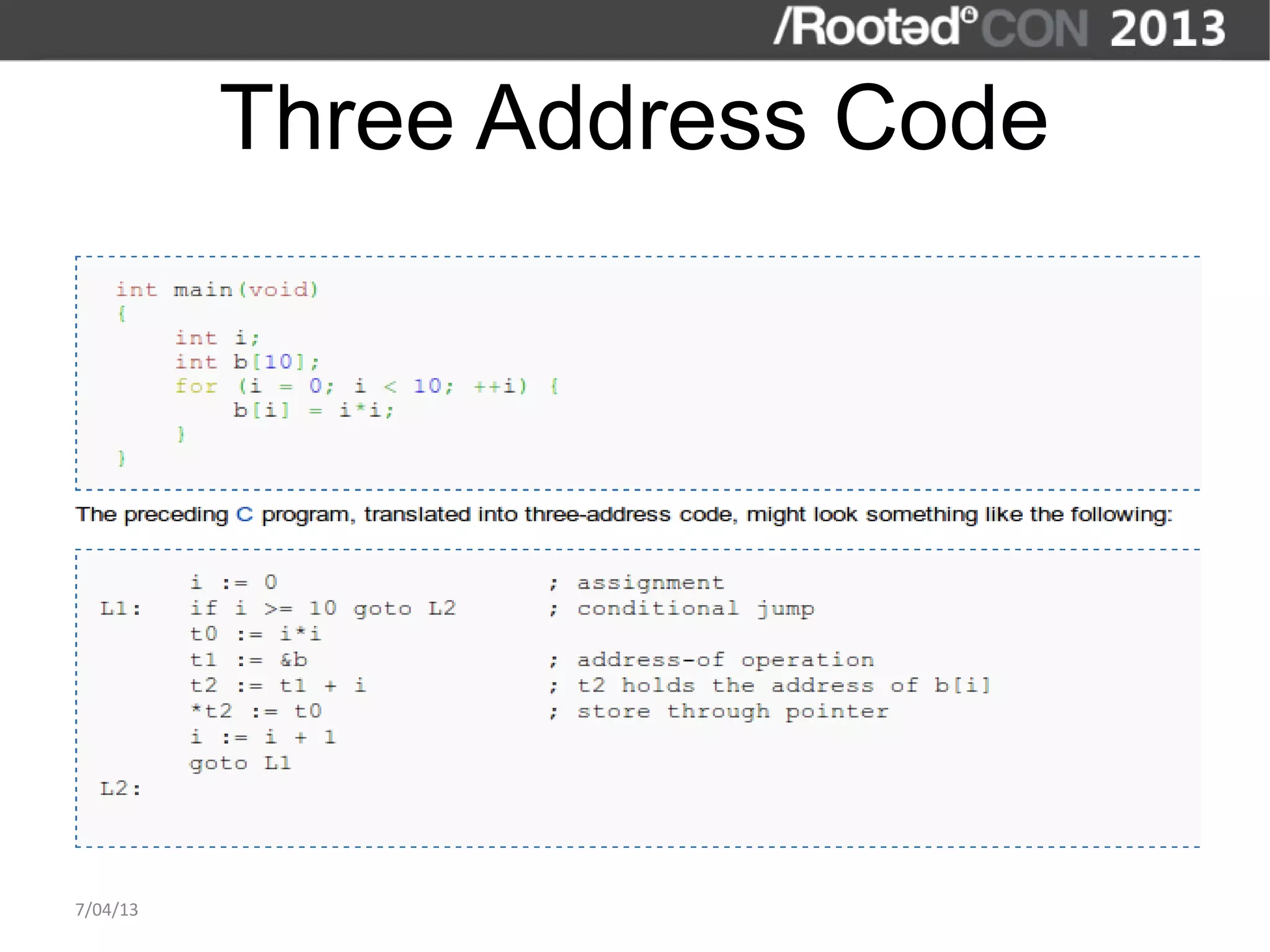
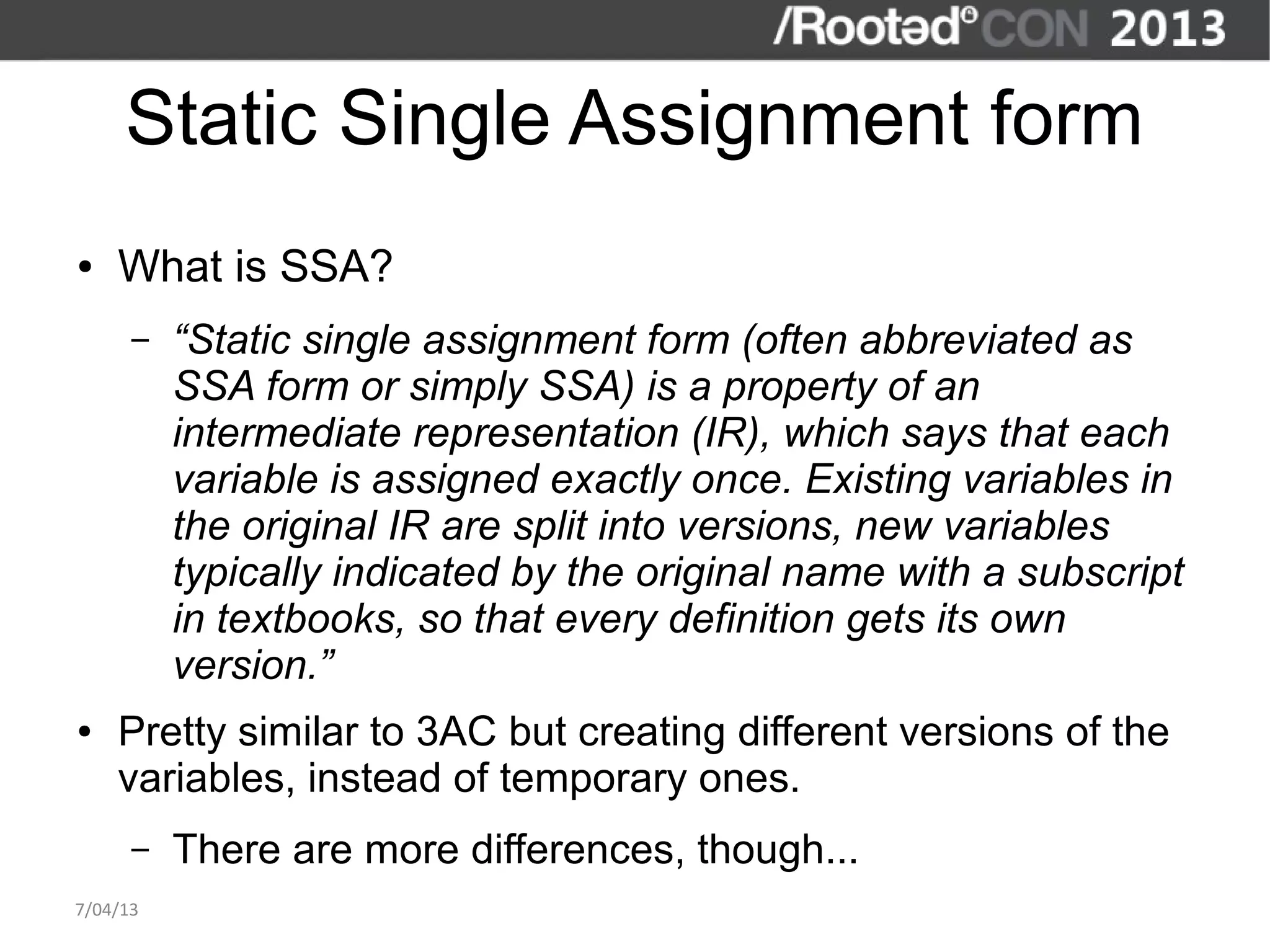
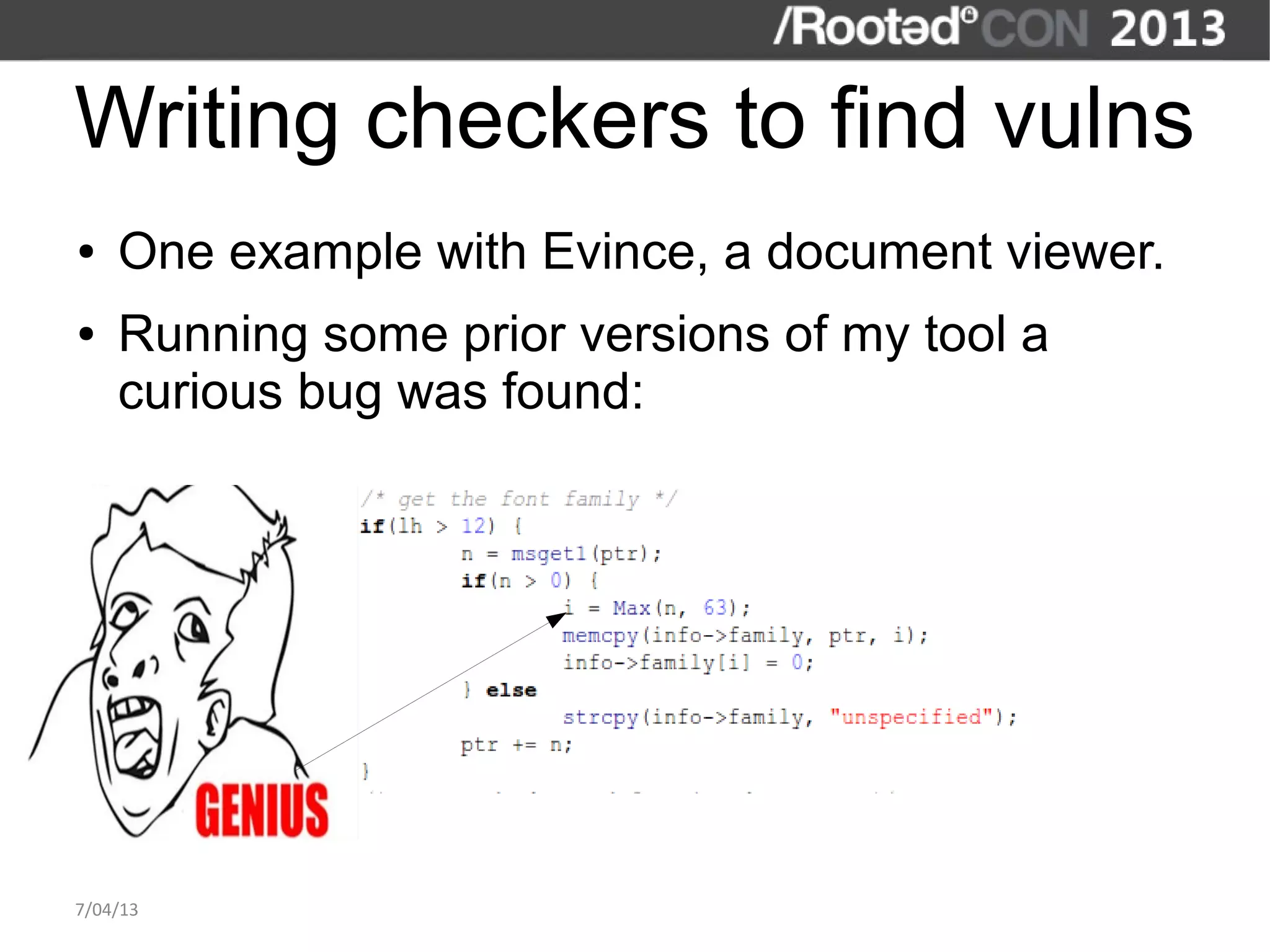
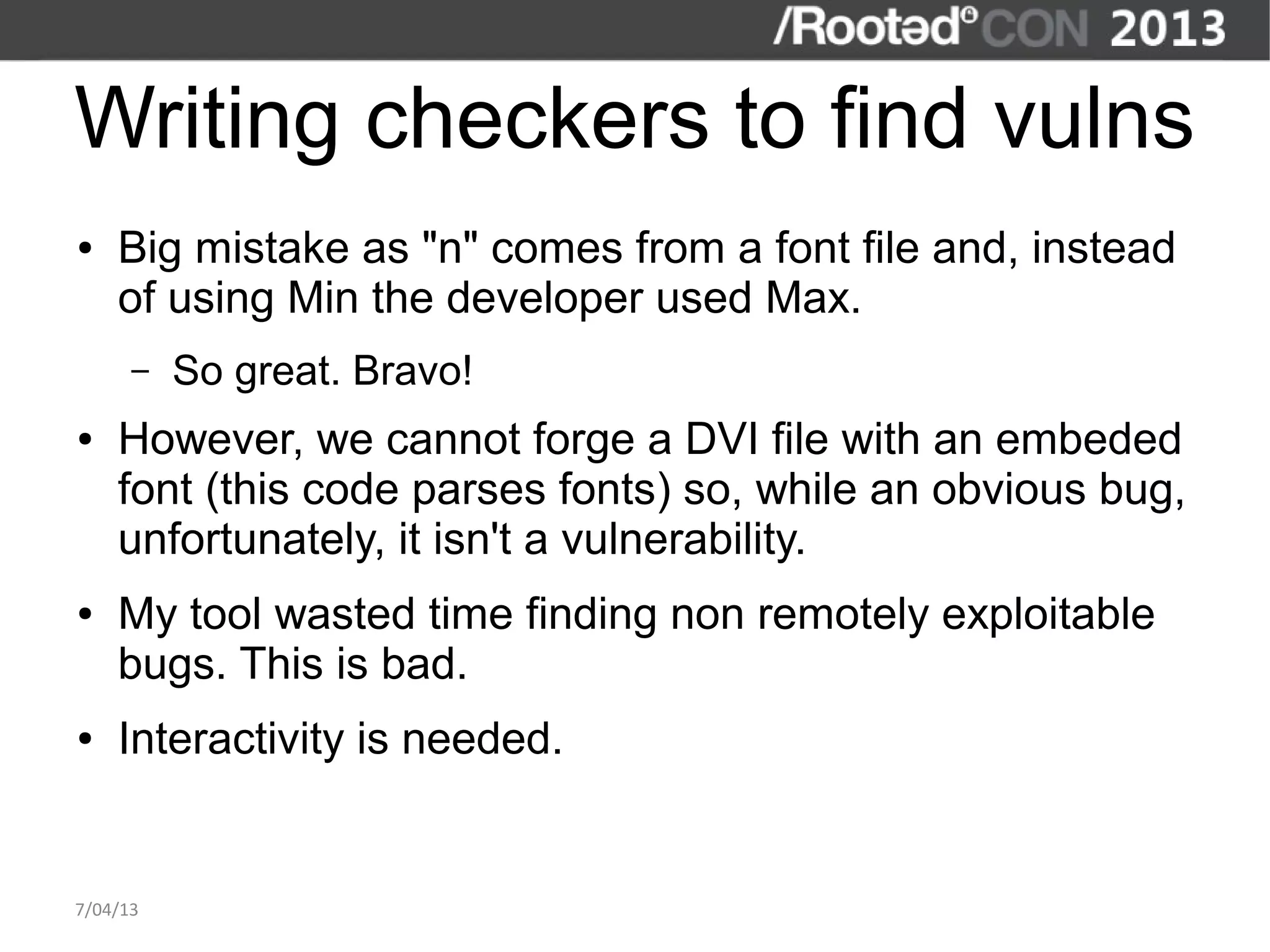
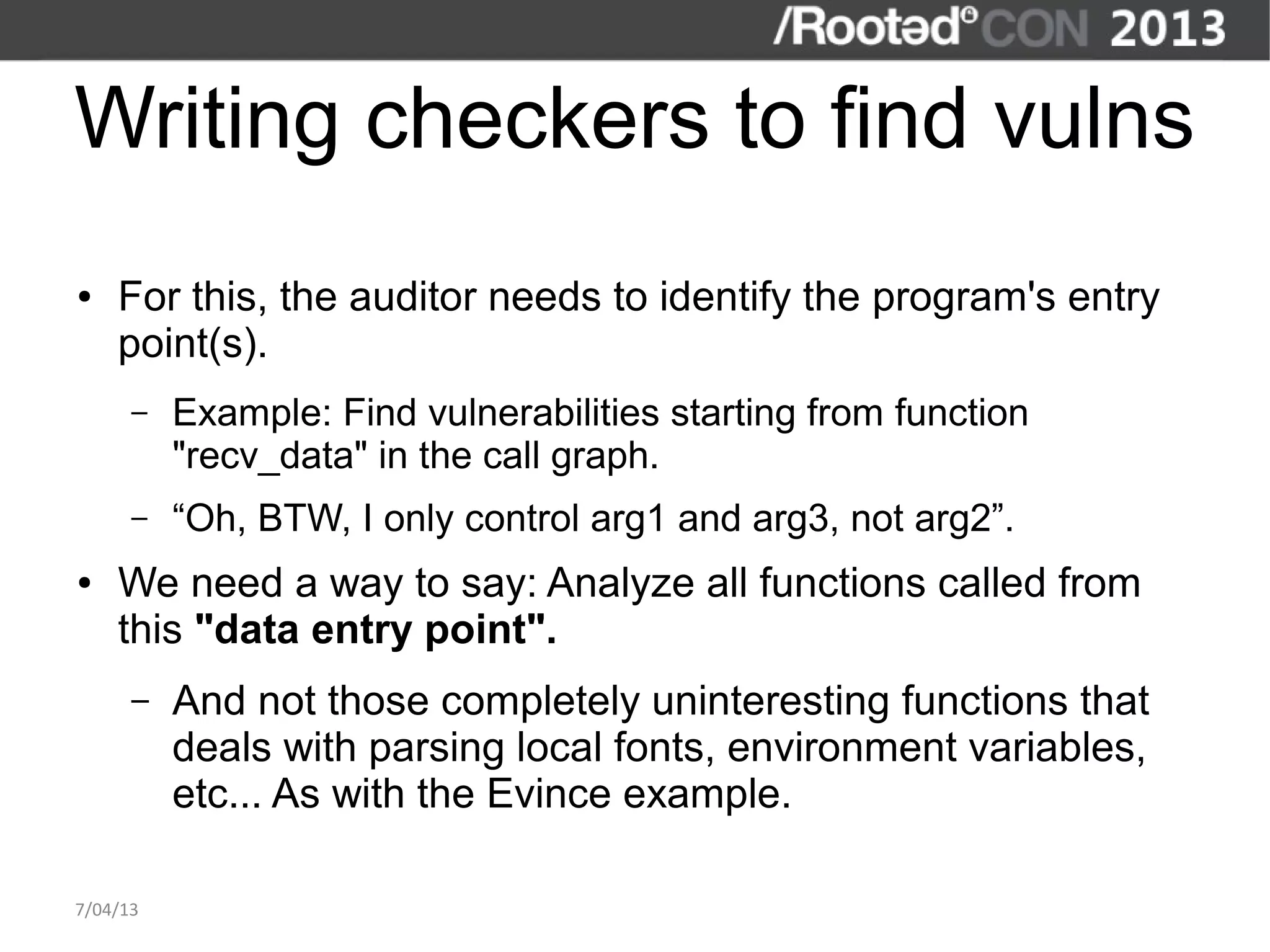
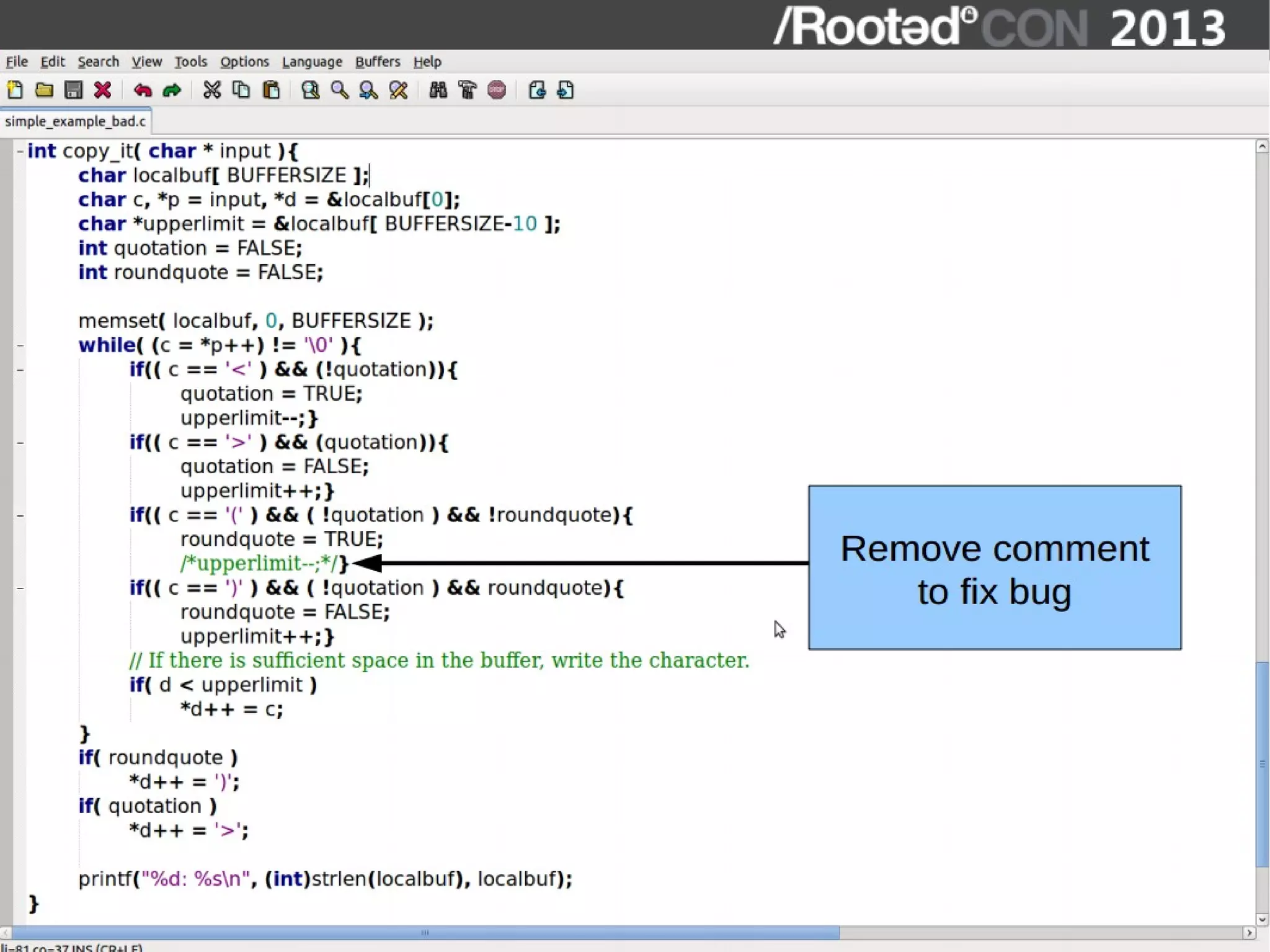
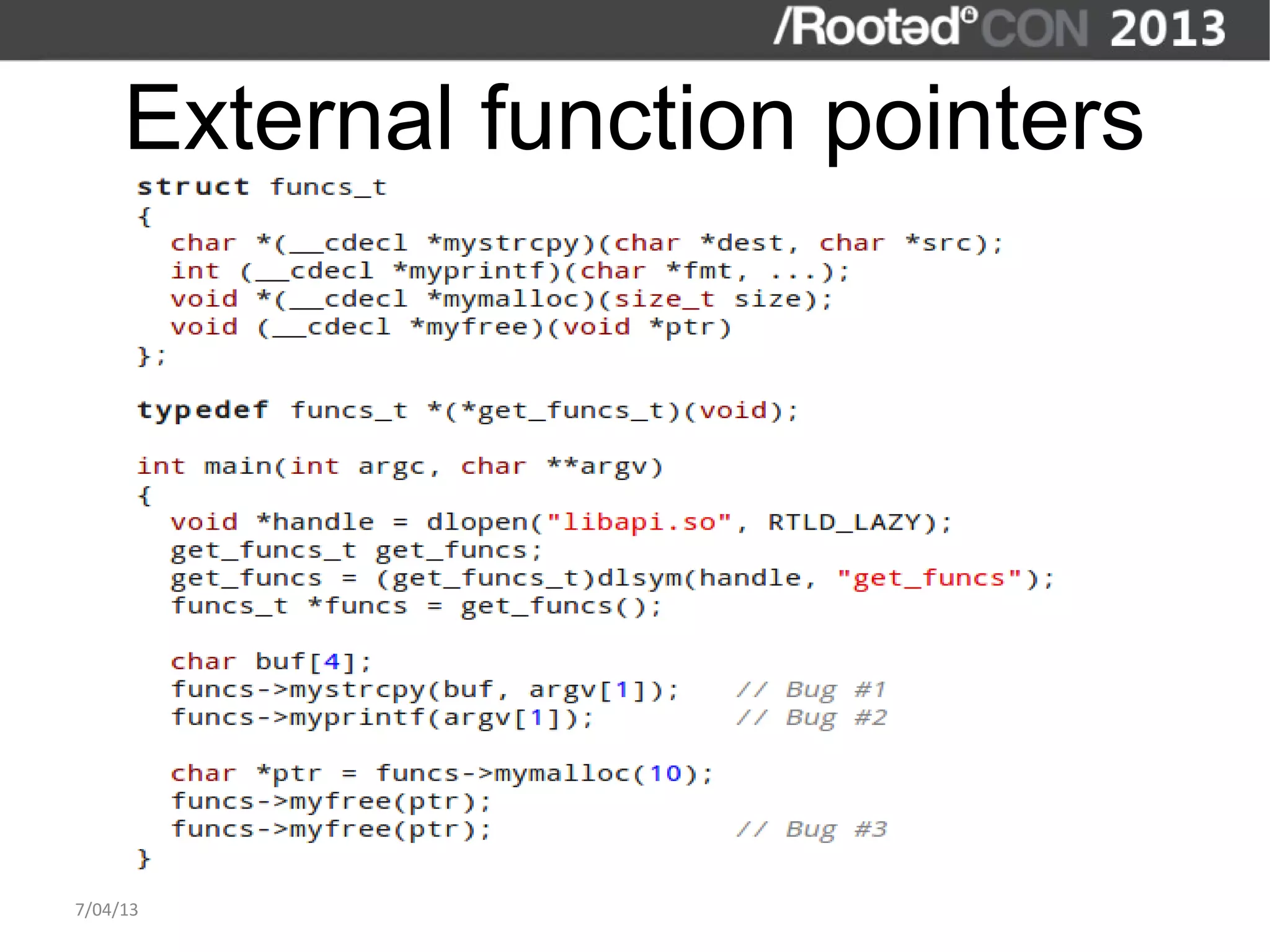
The document discusses the importance of interactive static analysis tools for discovering software vulnerabilities, emphasizing the need for more advanced tools as software complexity increases. It contrasts bug finding tools aimed at developers with vulnerability finding tools targeted at auditors, detailing the requirements for such tools, including the ability to parse various code formats and interact with human auditors. The author proposes a structured approach for developing these tools, including the creation of abstract syntax trees and control flow graphs to effectively analyze code for vulnerabilities.


















![A “parser” for binaries
● My idea: instead of writing a translator for the processors you want, use
existing tools.
– Decompilers. [Public] decompilers for x86 and ARM exists (Hex-Rays).
● Using them "could be" a good idea.
– Hex-Rays decompilers export an API to get the AST for a function.
– Just what I want.
● Problems:
– The decompilers are writen for humans to understand the code.
– Not writen for programs to find vulnerabilities.
– A bad decompiler assumption may generate a lot of false positives.
● Example: GCC.
7/04/13](https://image.slidesharecdn.com/joxeankoret-savulns-130407063141-phpapp01/75/Joxean-Koret-Interactive-Static-Analysis-Tools-for-Vulnerability-Discovery-Rooted-CON-2013-22-2048.jpg)