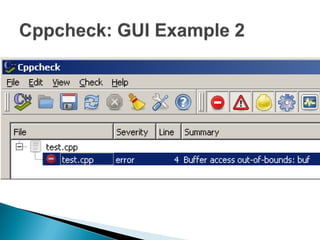
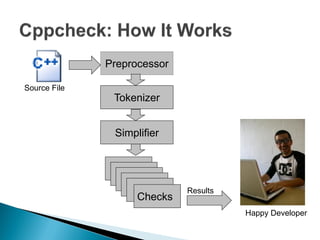
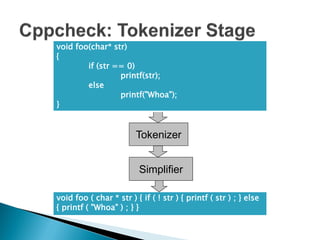
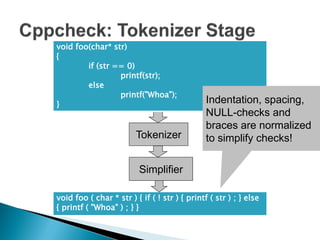
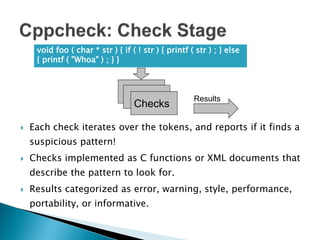
Cppcheck is a free static code analysis tool that finds bugs in C and C++ code without executing the program. It works by tokenizing, simplifying, and checking code for patterns that may indicate bugs. Some checks look for buffer overruns, unused functions, memory leaks, and invalid arguments. Cppcheck is cross-platform, has a GUI and command line interface, and has found hundreds of bugs in open source projects.















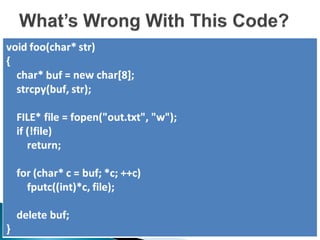
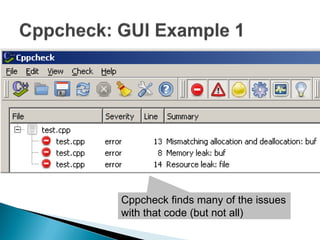
![Possible buffer overrun
Memory leak: buf
Should be “delete[] buf”
Resource leak: file](https://image.slidesharecdn.com/cppcheck-111124221846-phpapp01/85/Static-Code-Analysis-and-Cppcheck-22-320.jpg)