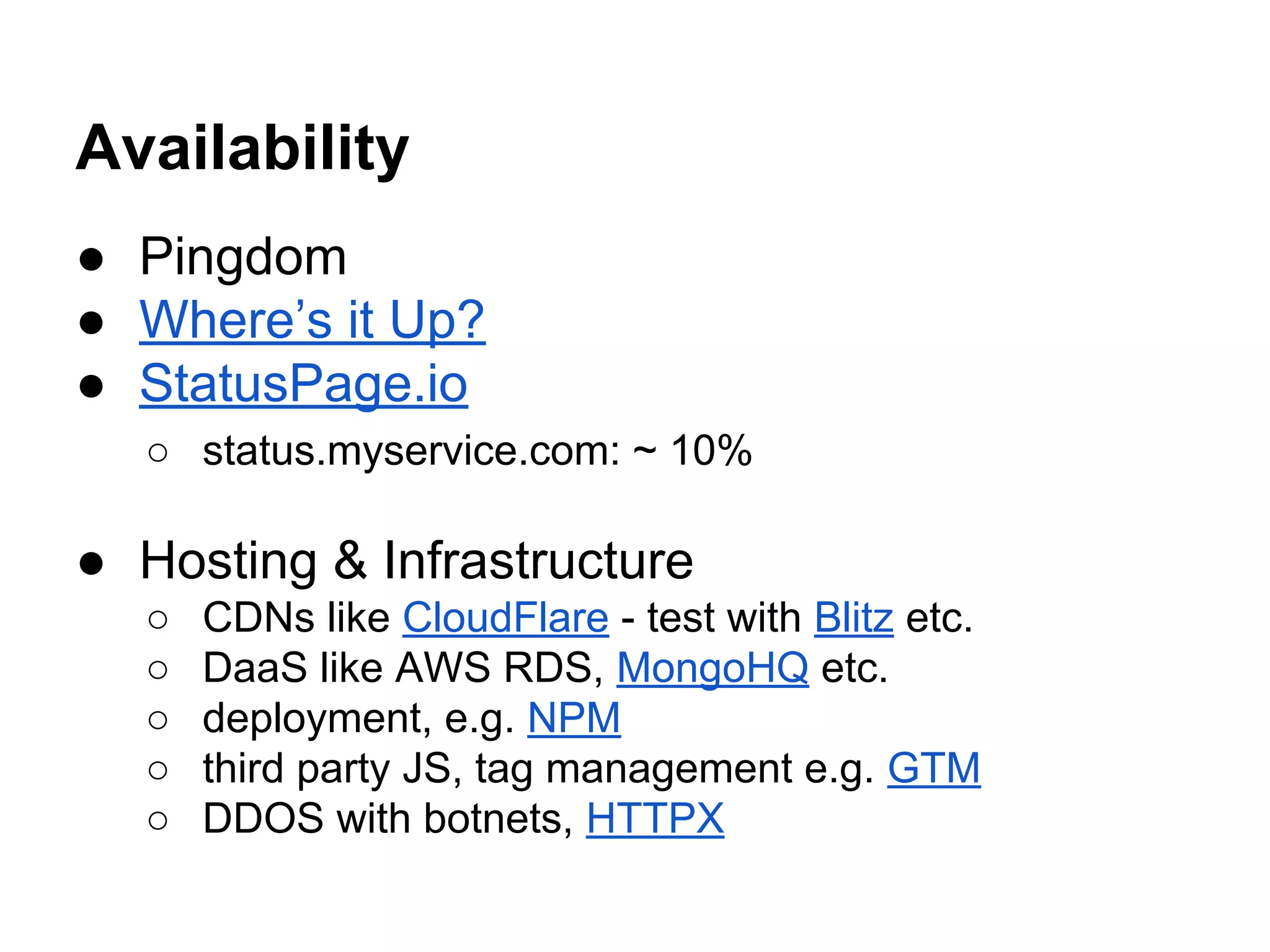
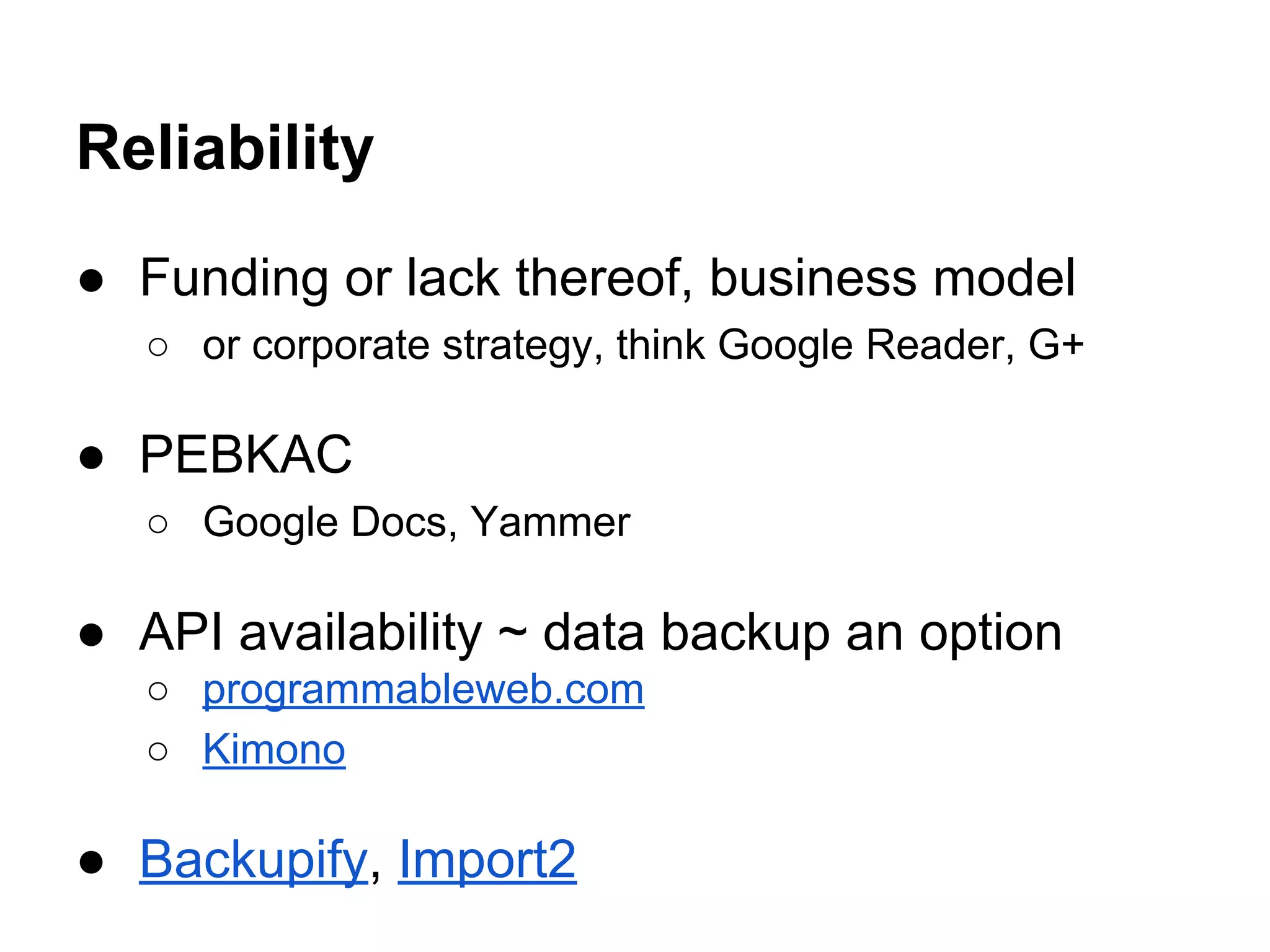
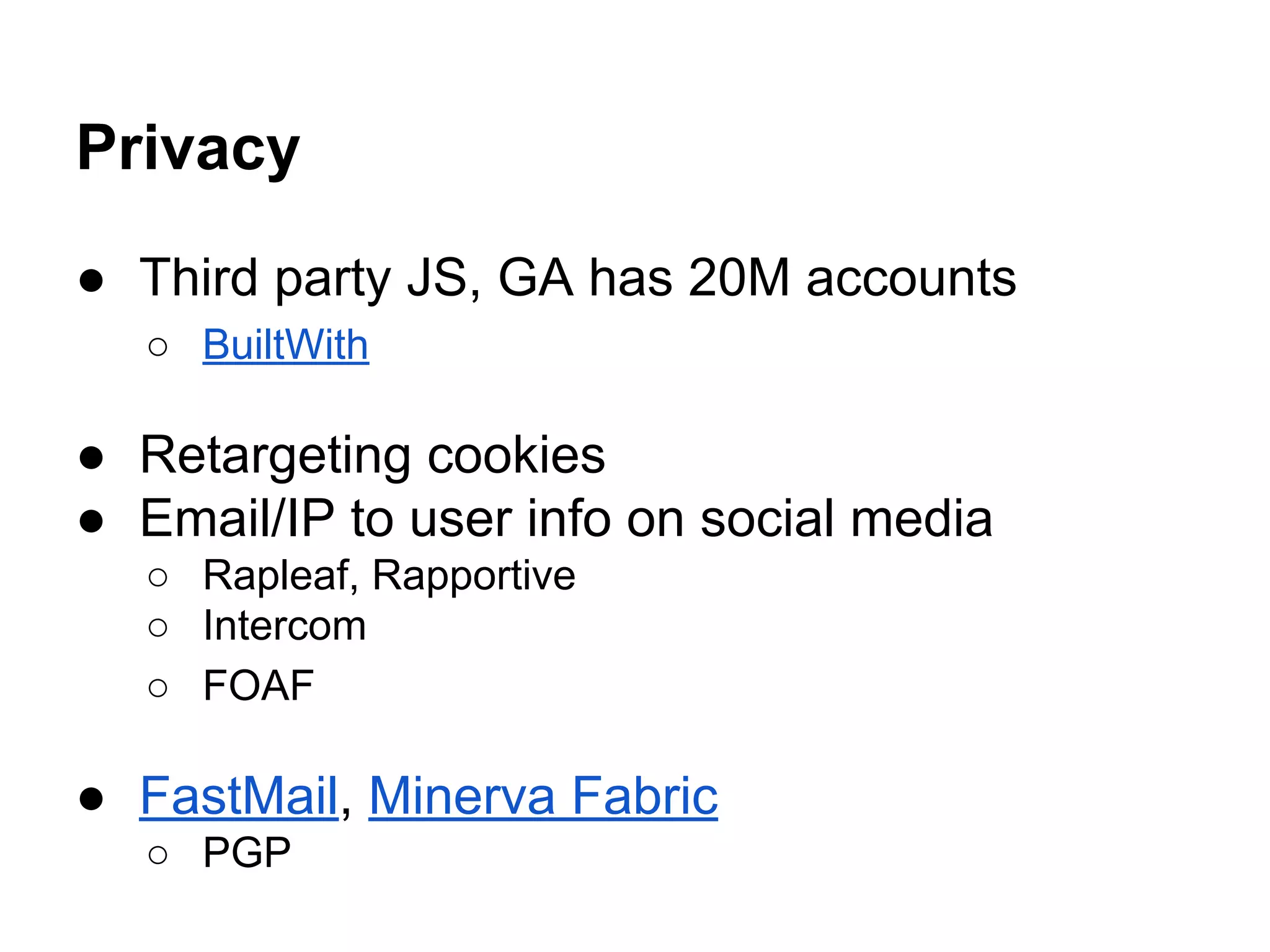
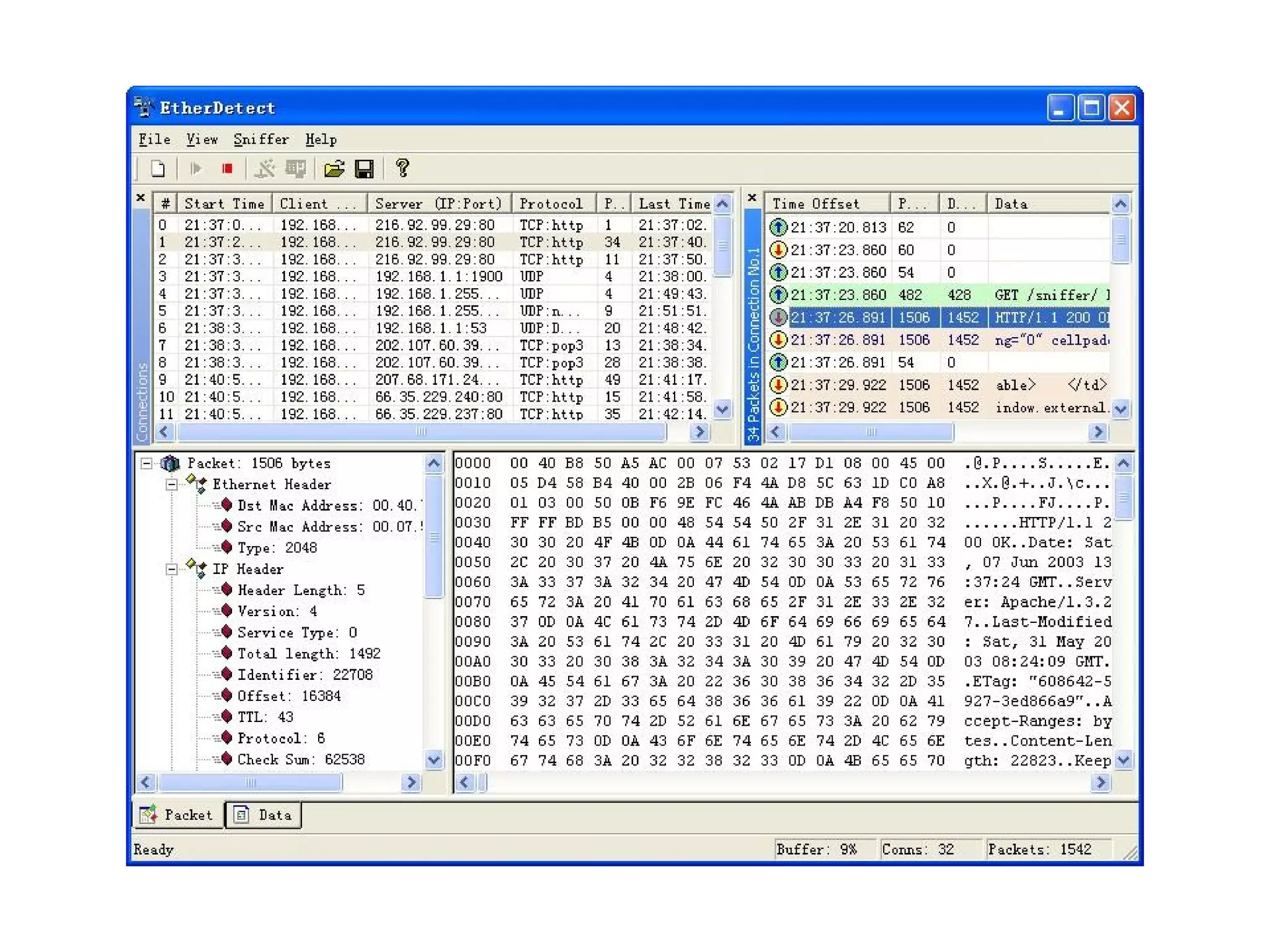
This document discusses various ways to stay safe in the cloud, including ensuring availability, reliability, and privacy. It outlines potential attack vectors like social engineering, packet sniffing, and zero-day exploits. Some recommended countermeasures include encrypted drives, strong passwords, two-factor authentication, and security audits. The document also discusses trade-offs between self-reliance and reliability as well as security and convenience. It notes that while security is important, users often don't care if a service gets hacked and every service will likely experience a breach at some point.