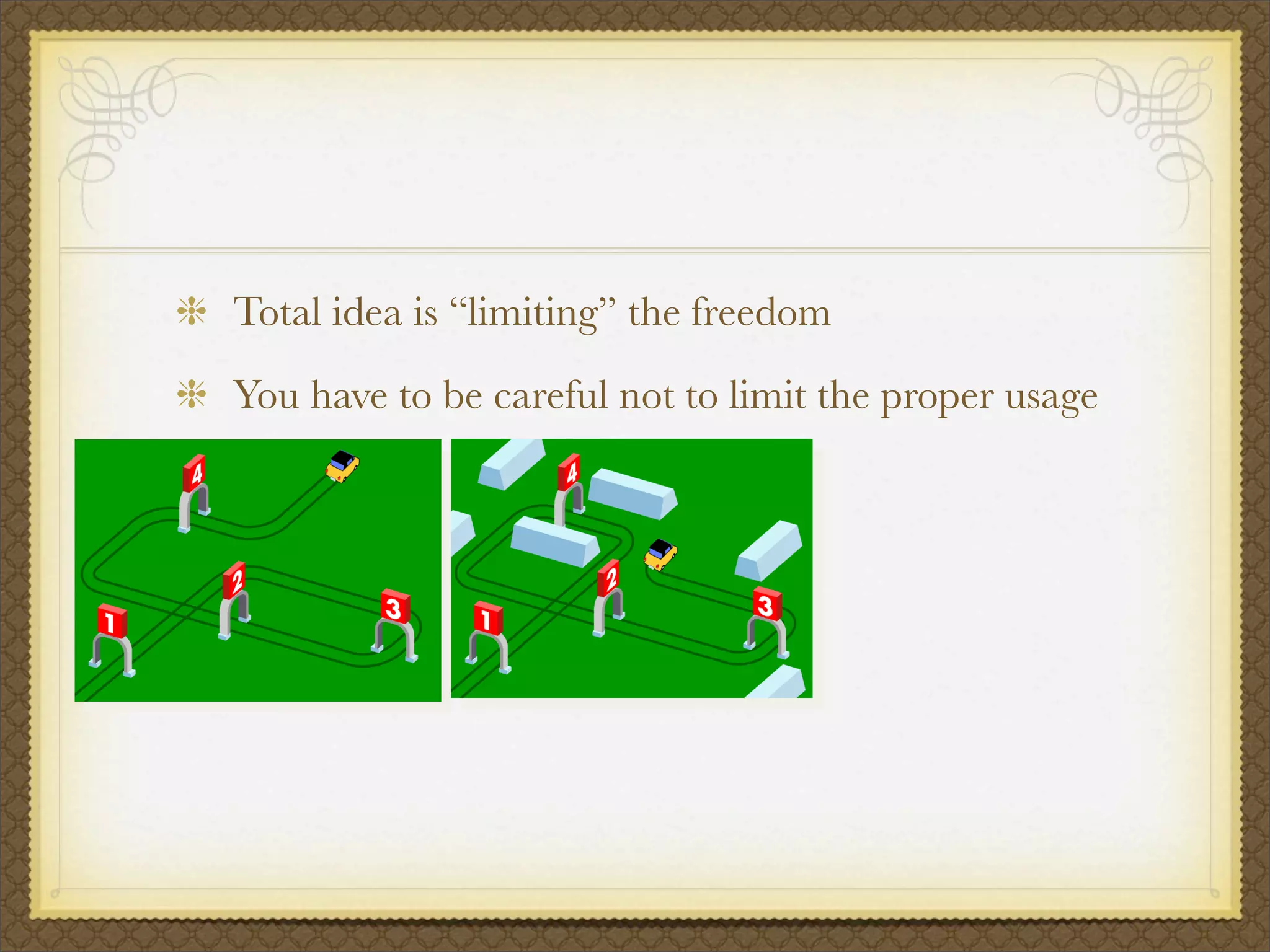
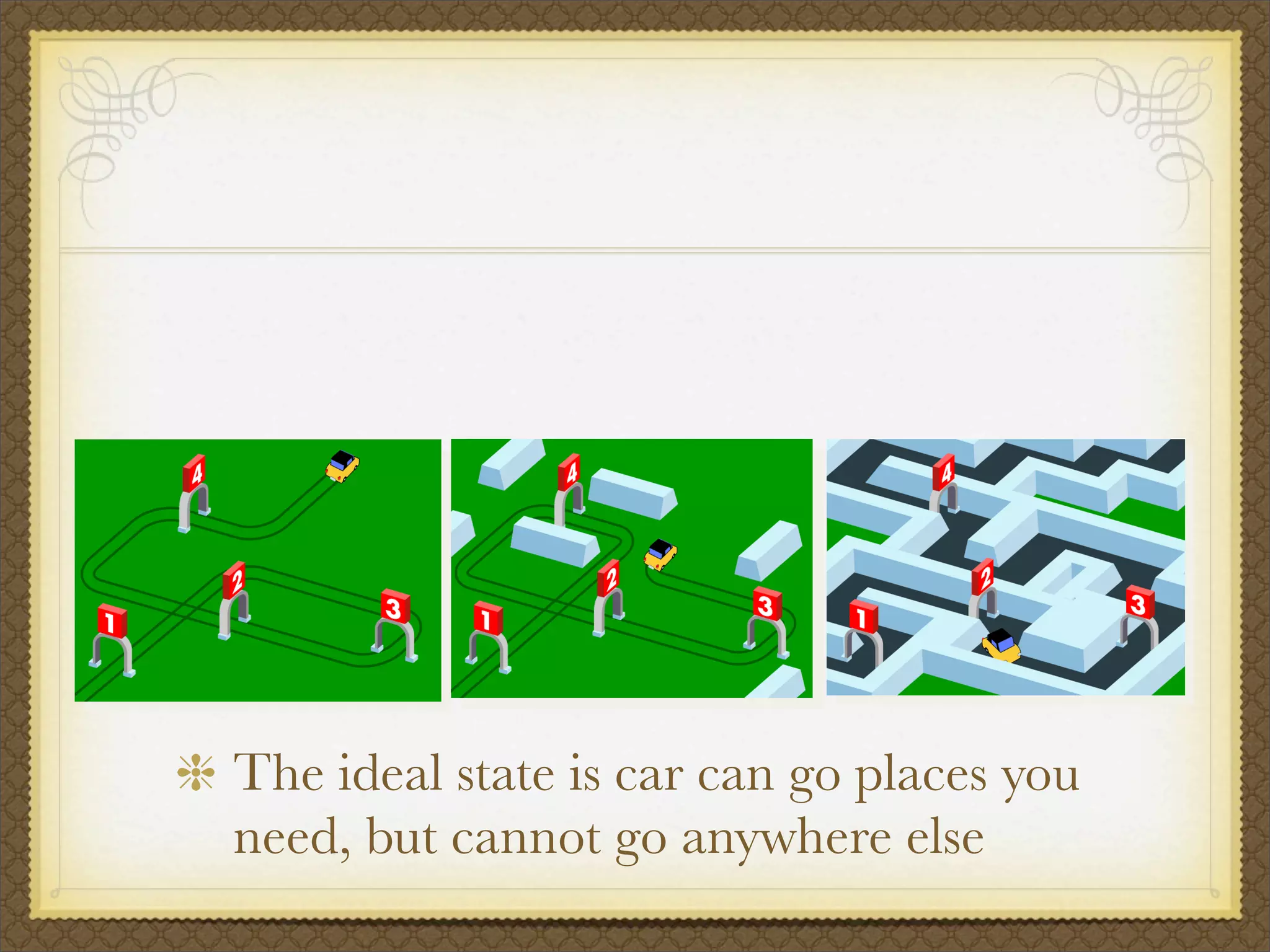
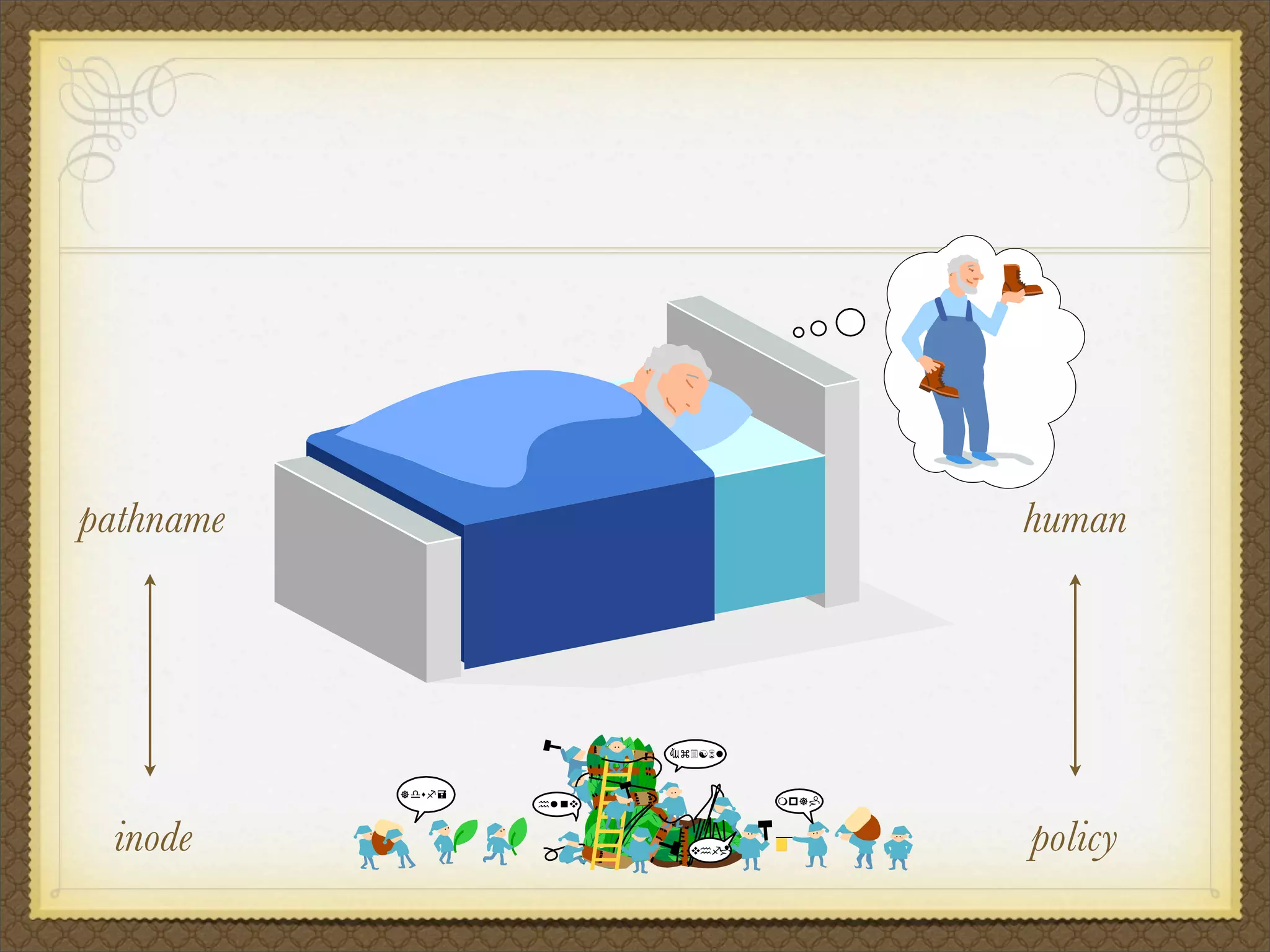
The document discusses operating system security and introduces TOMOYO Linux as an access control mechanism for Linux that can restrict administrator privileges and limit the damage caused by stolen devices or exploited vulnerabilities. It explains that TOMOYO Linux tracks process executions to generate security policies and allows administrators to view process histories to define access control rules. The presentation also provides an overview of SELinux and concludes with an announcement of a demonstration of TOMOYO Linux's policy learning mode capabilities.