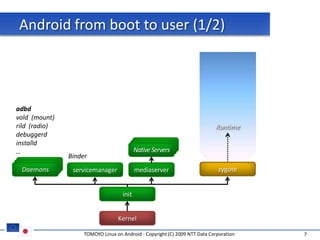
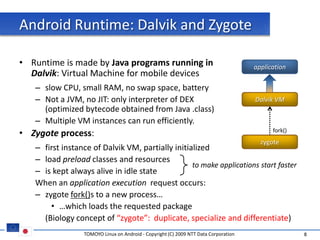
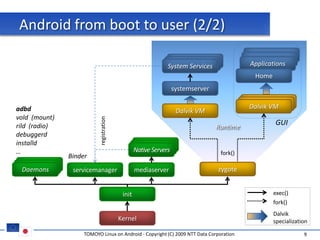
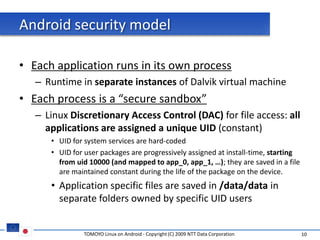
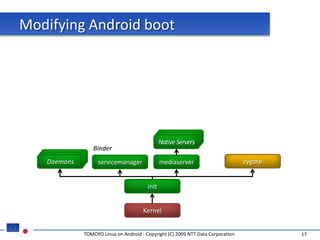
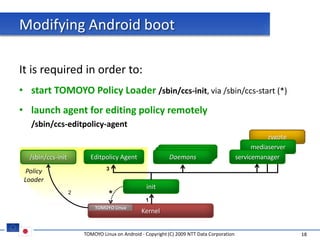
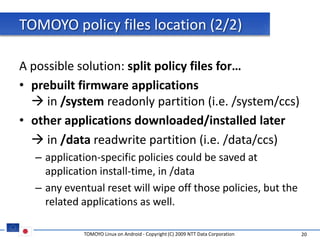
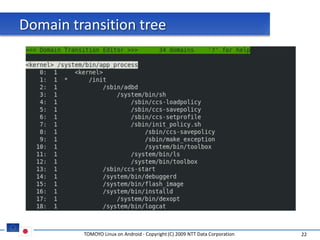
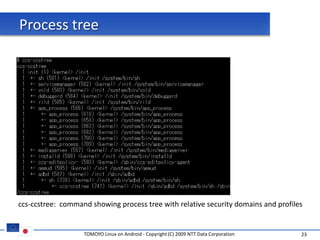
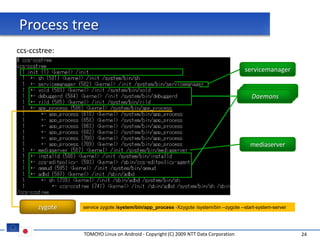
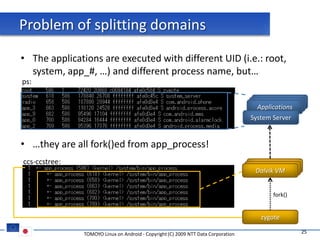
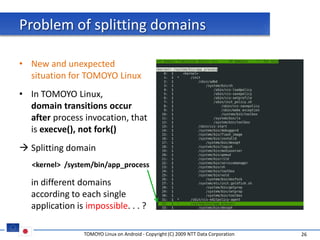
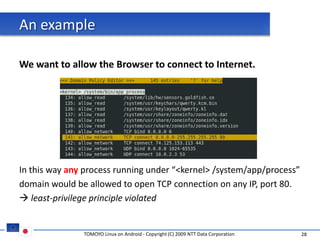
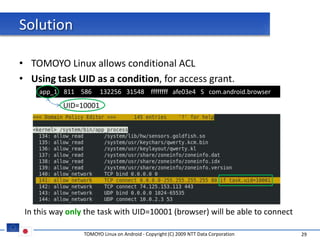
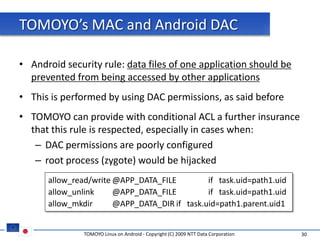
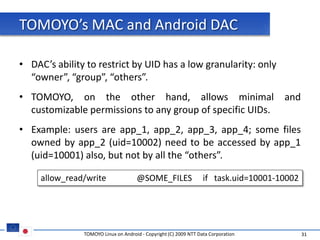
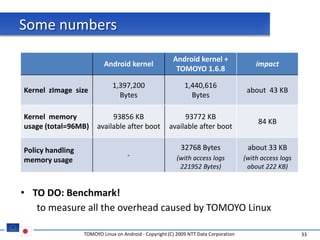
The document discusses porting TOMOYO Linux, a MAC implementation for Linux, to the Android platform. It describes patching the Android kernel with the TOMOYO patch, adapting the TOMOYO policy tools for embedded use, and integrating a TOMOYO policy loader into the Android boot process. Key challenges addressed include splitting security domains given Android's "fork vs exec" app launching approach and using TOMOYO's conditional ACLs to work with Android's existing DAC permissions. A demo is provided of remote management of Android policies using the TOMOYO tools.