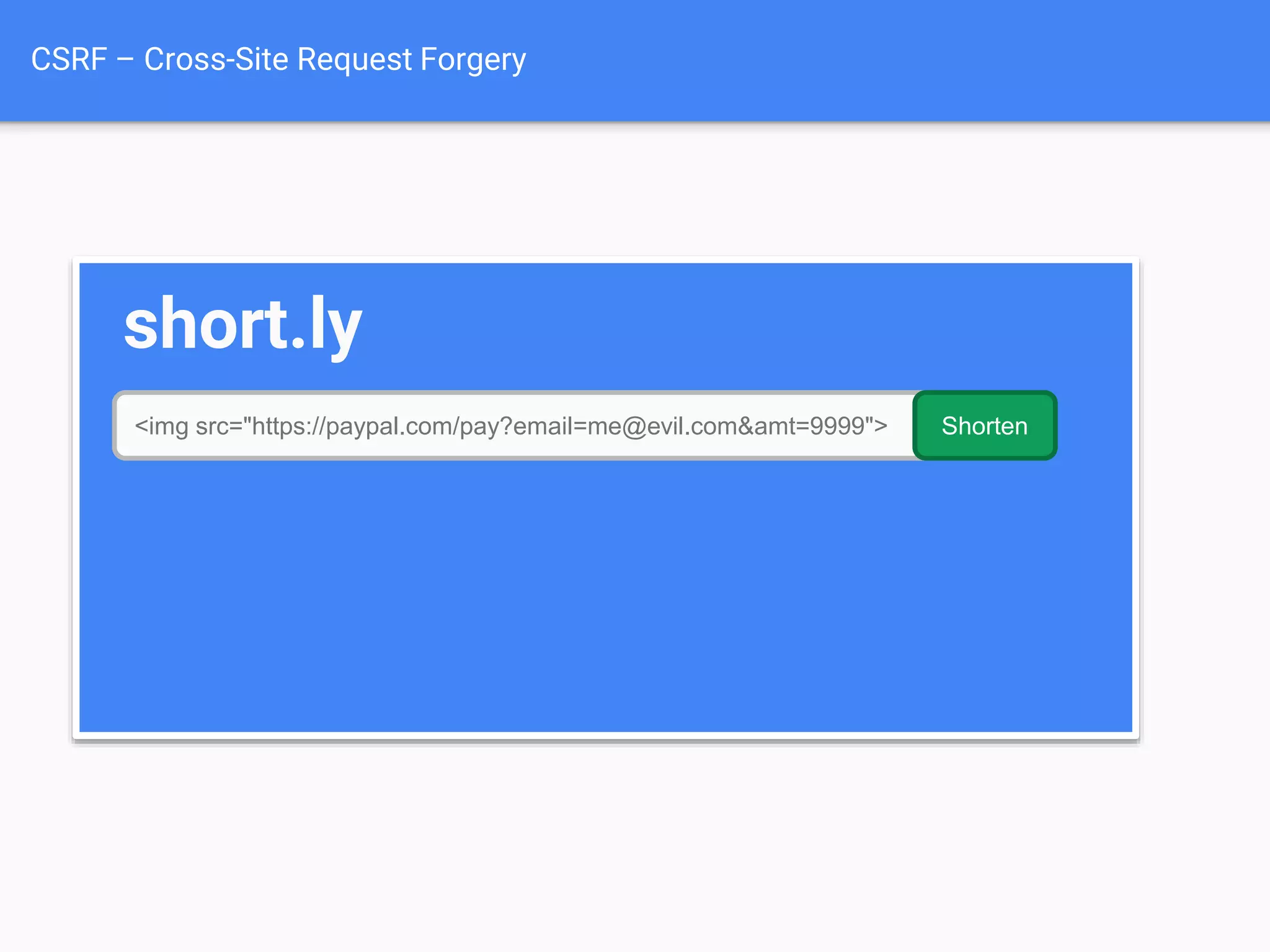
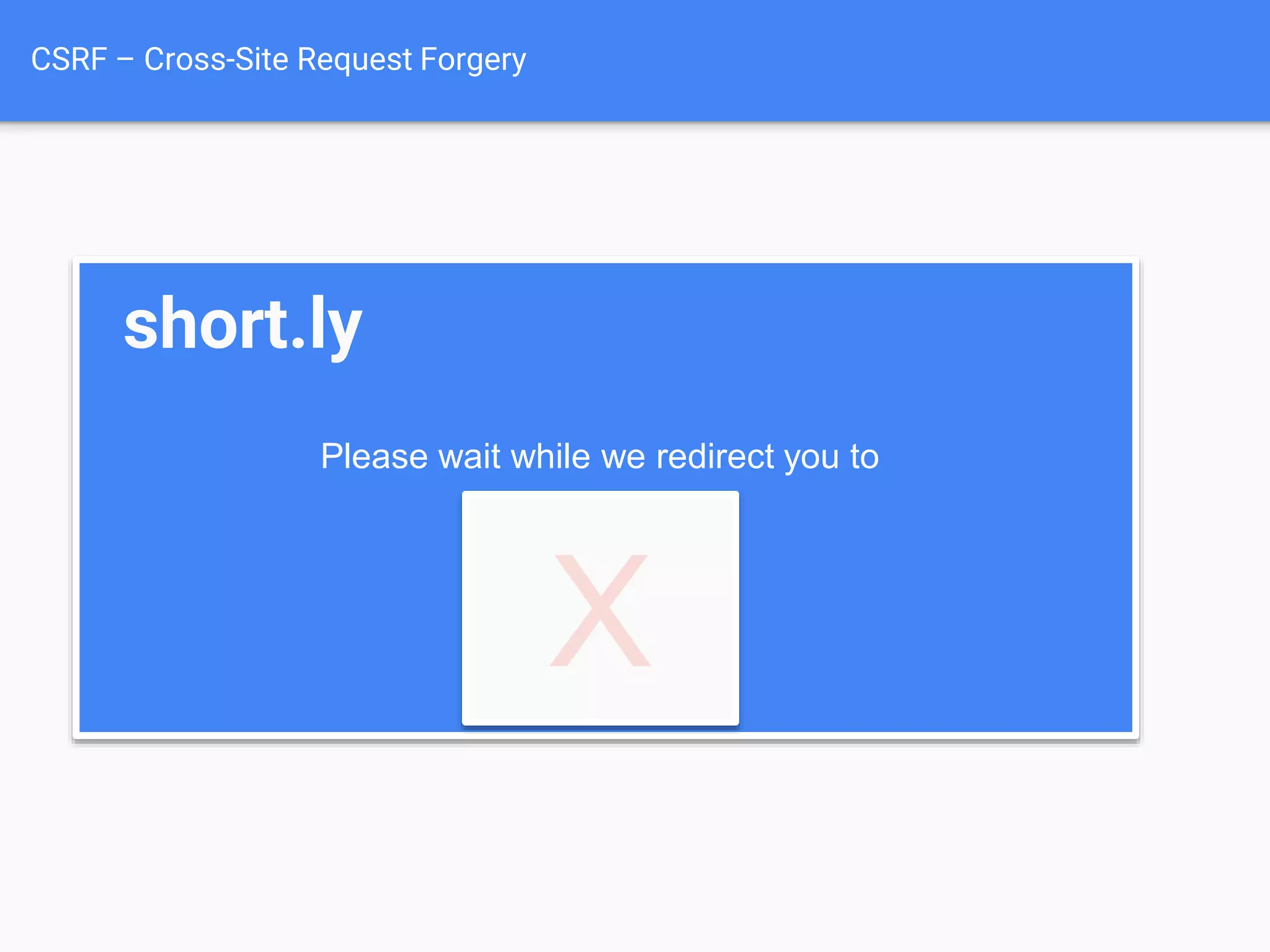
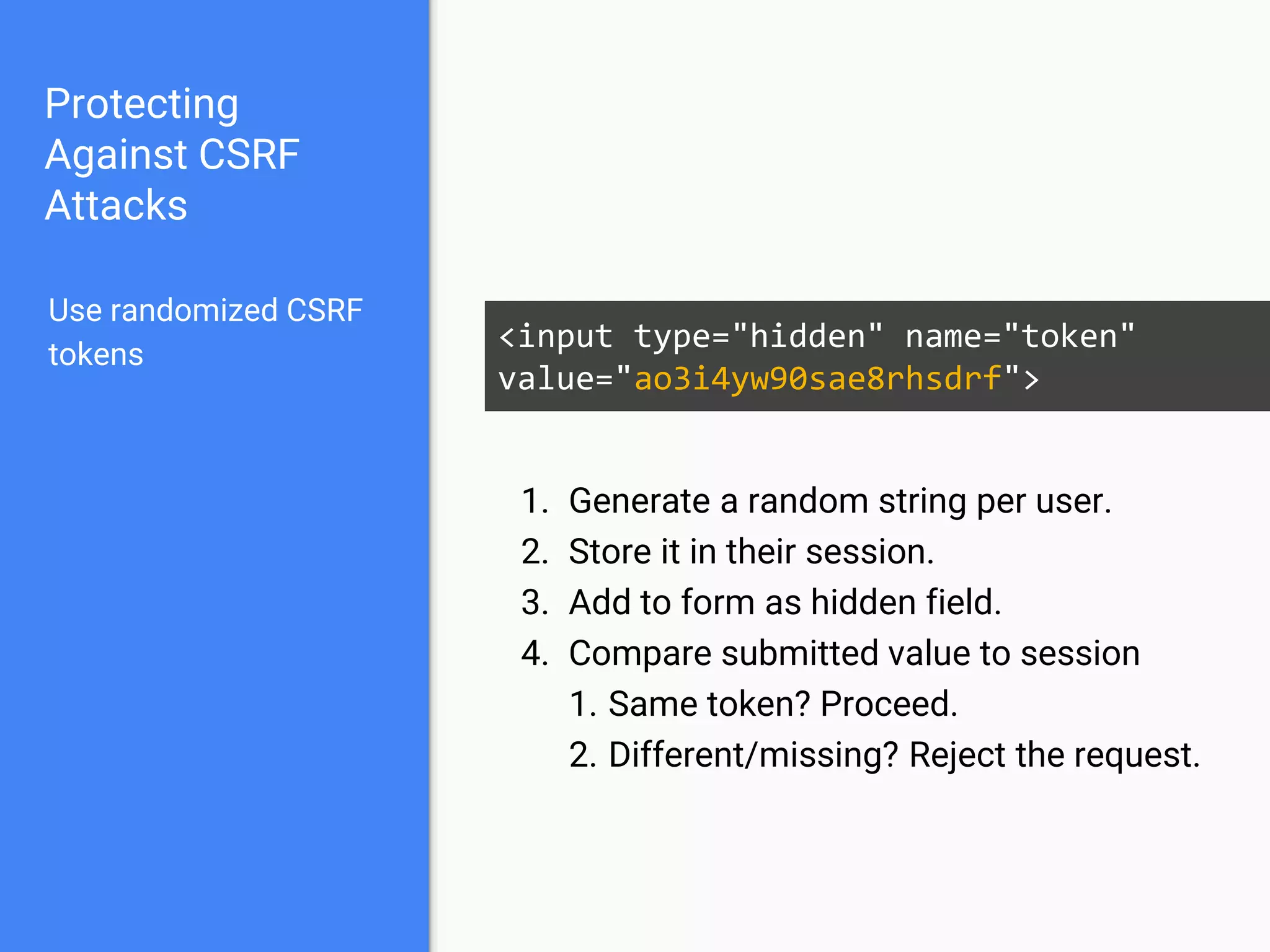
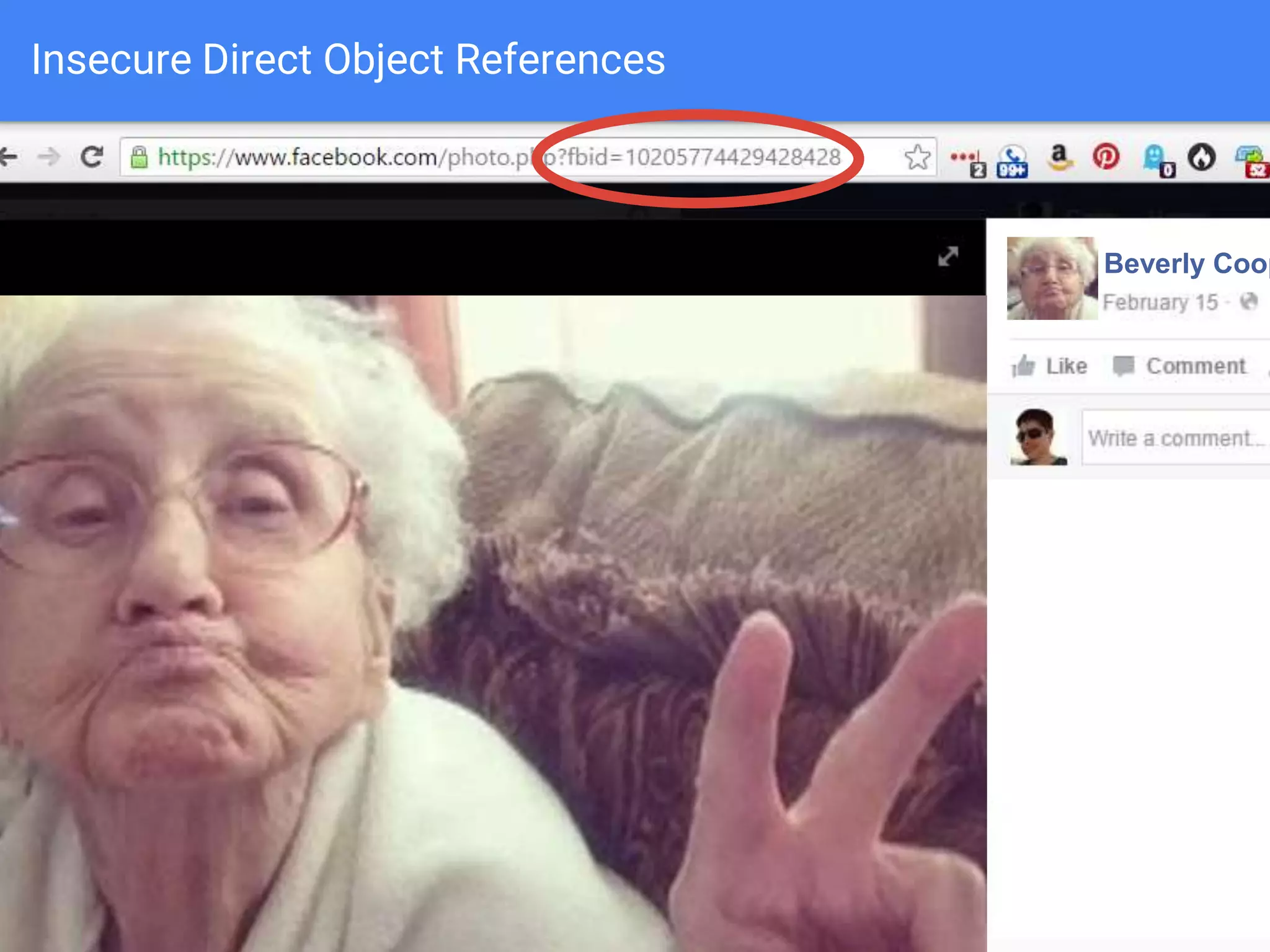
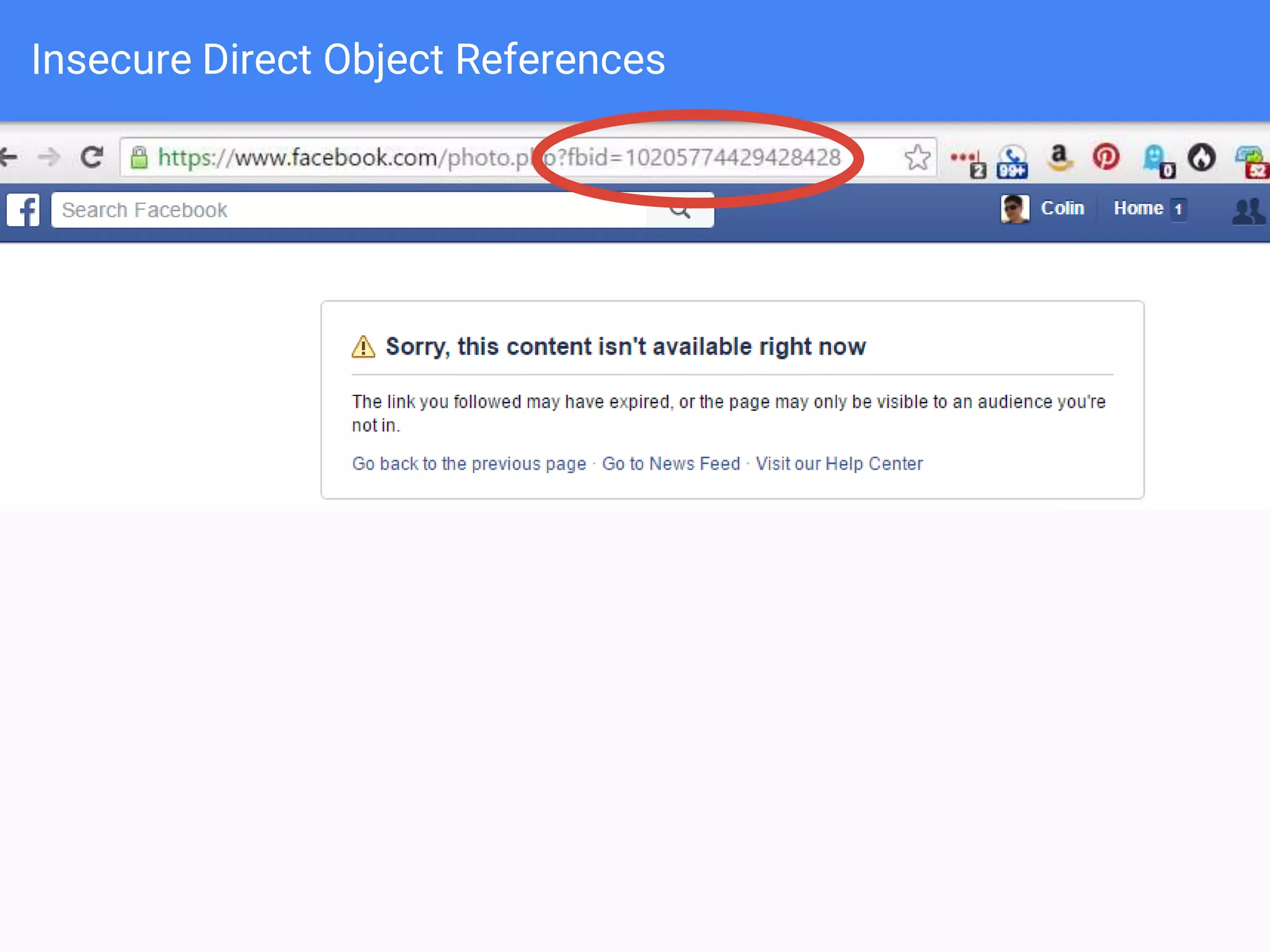
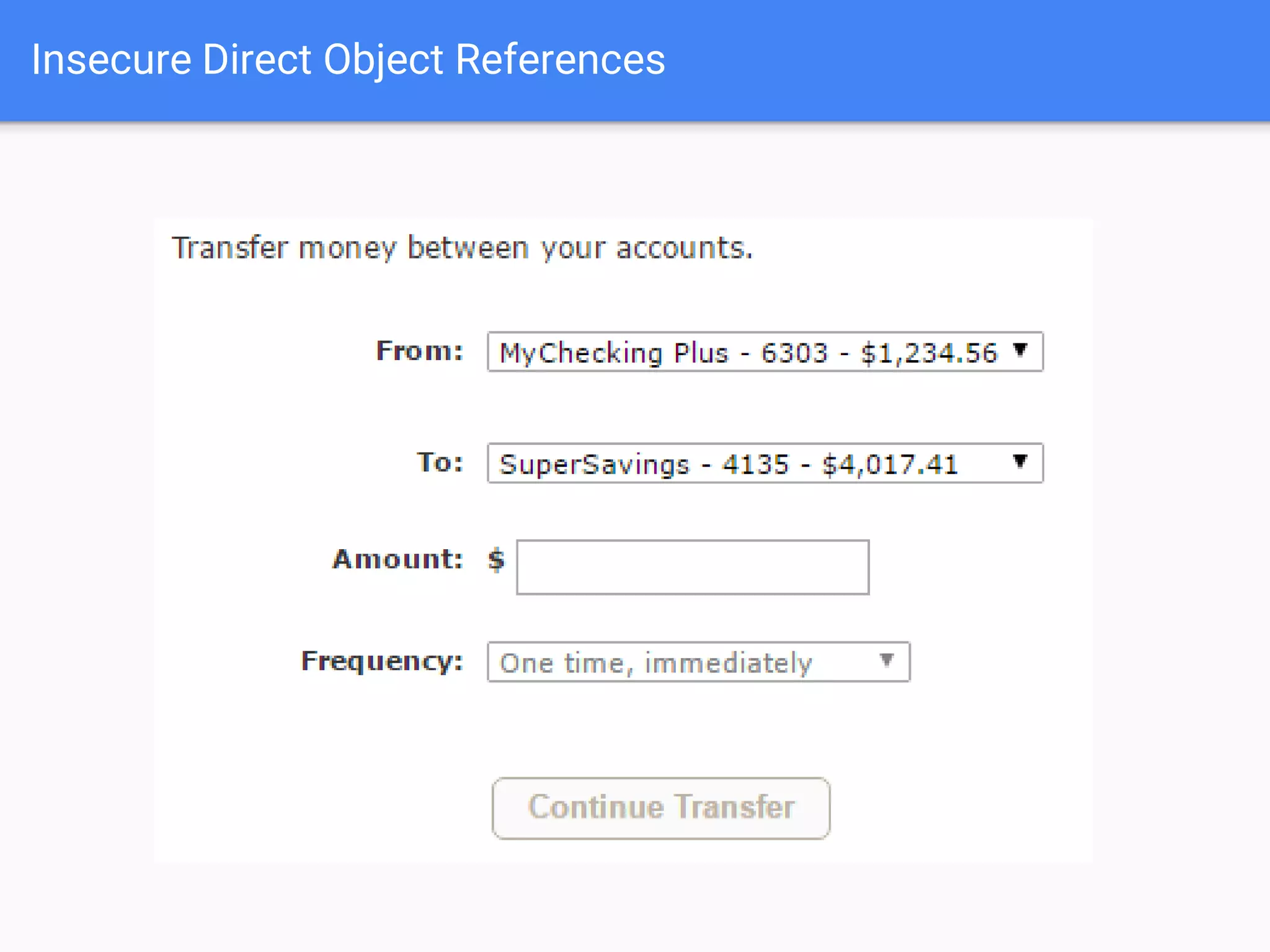
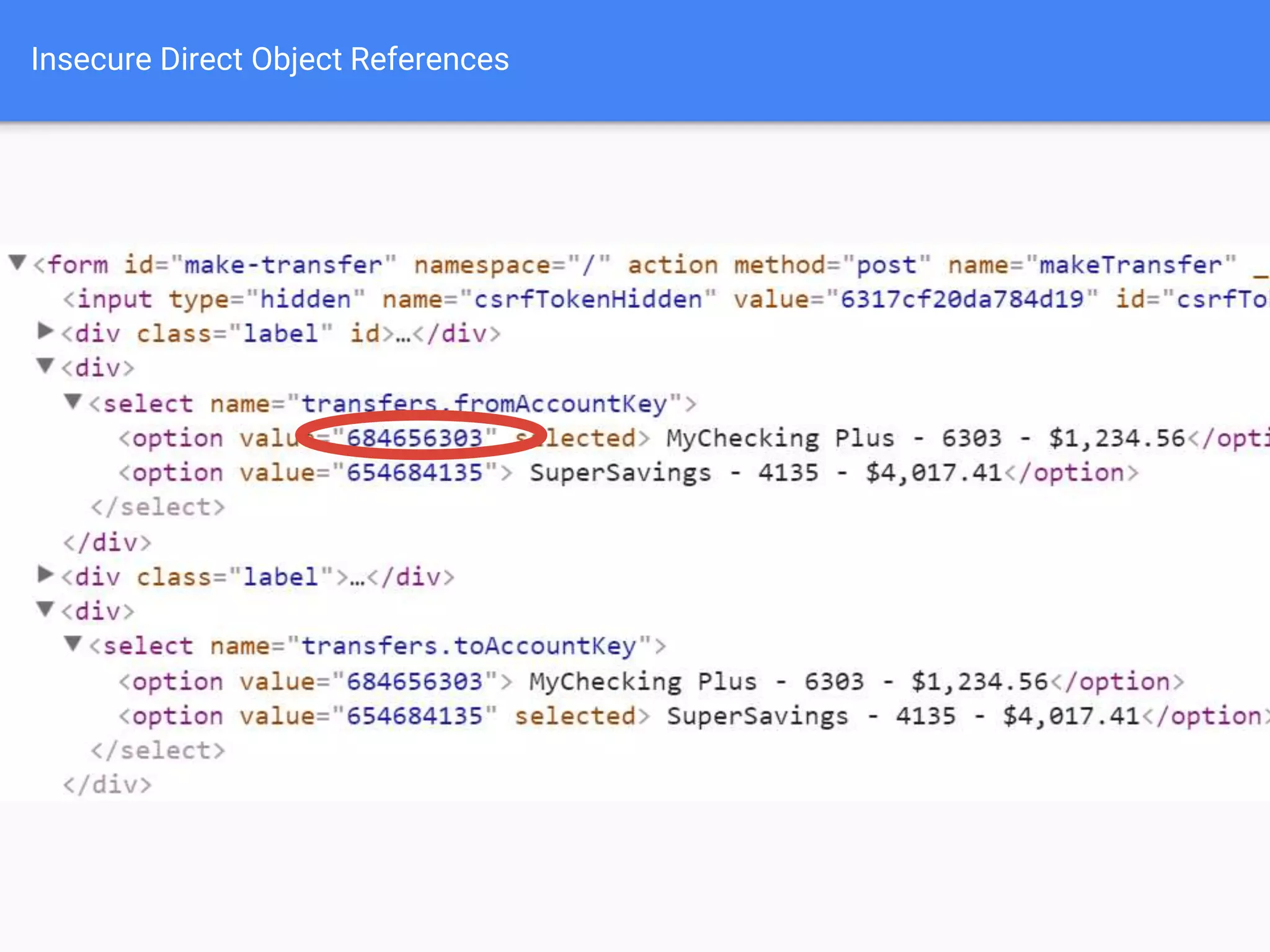
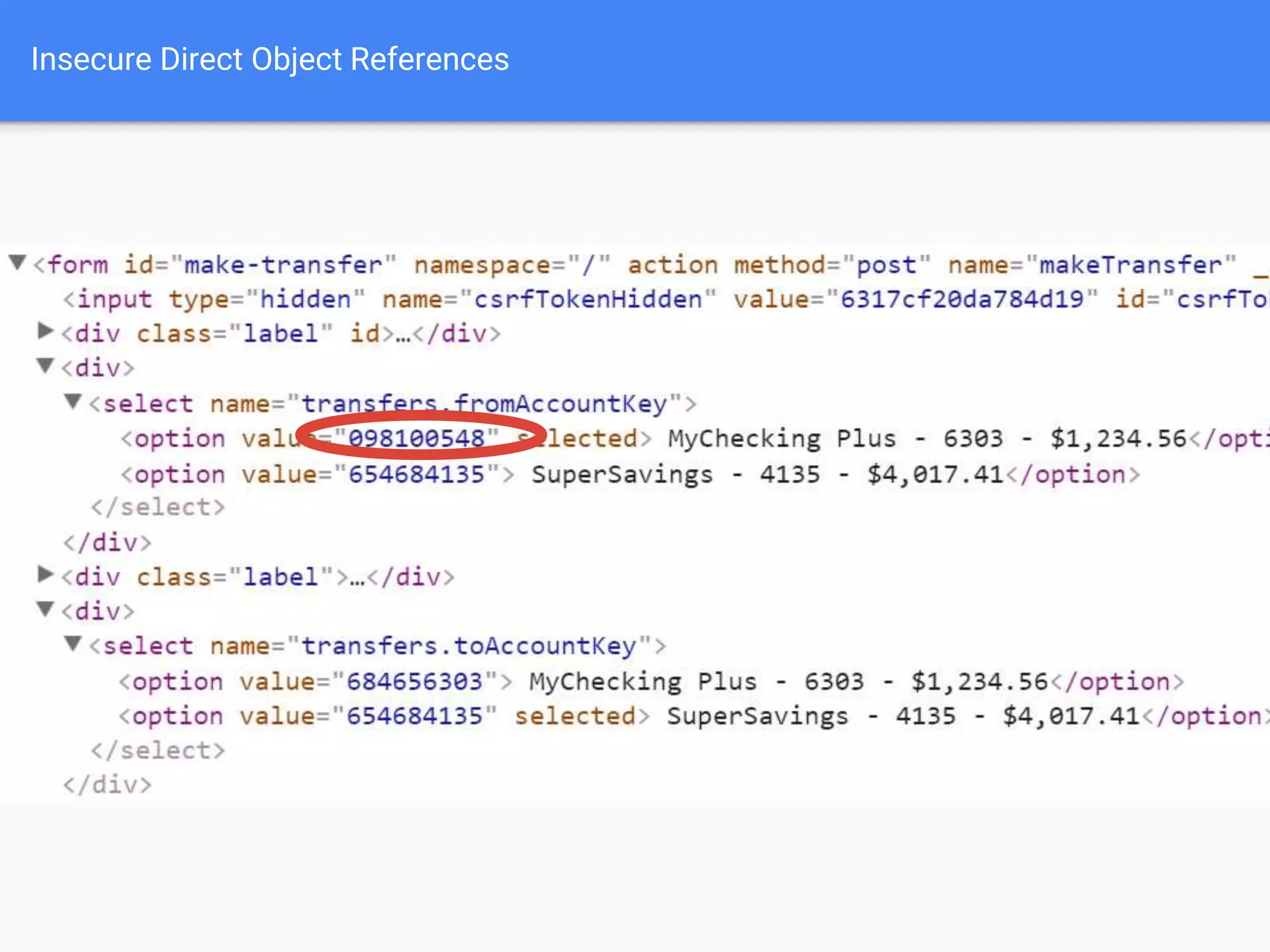
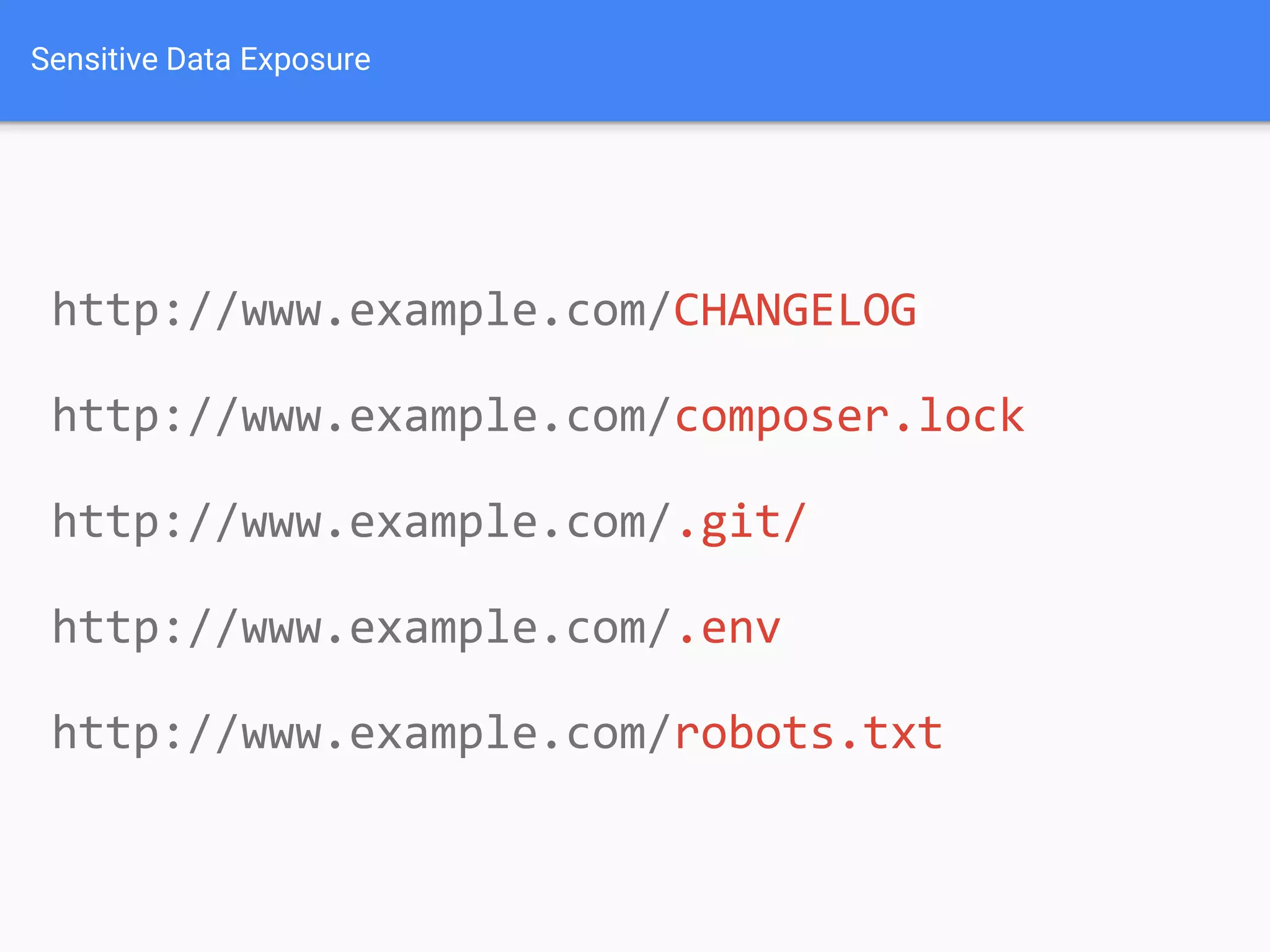
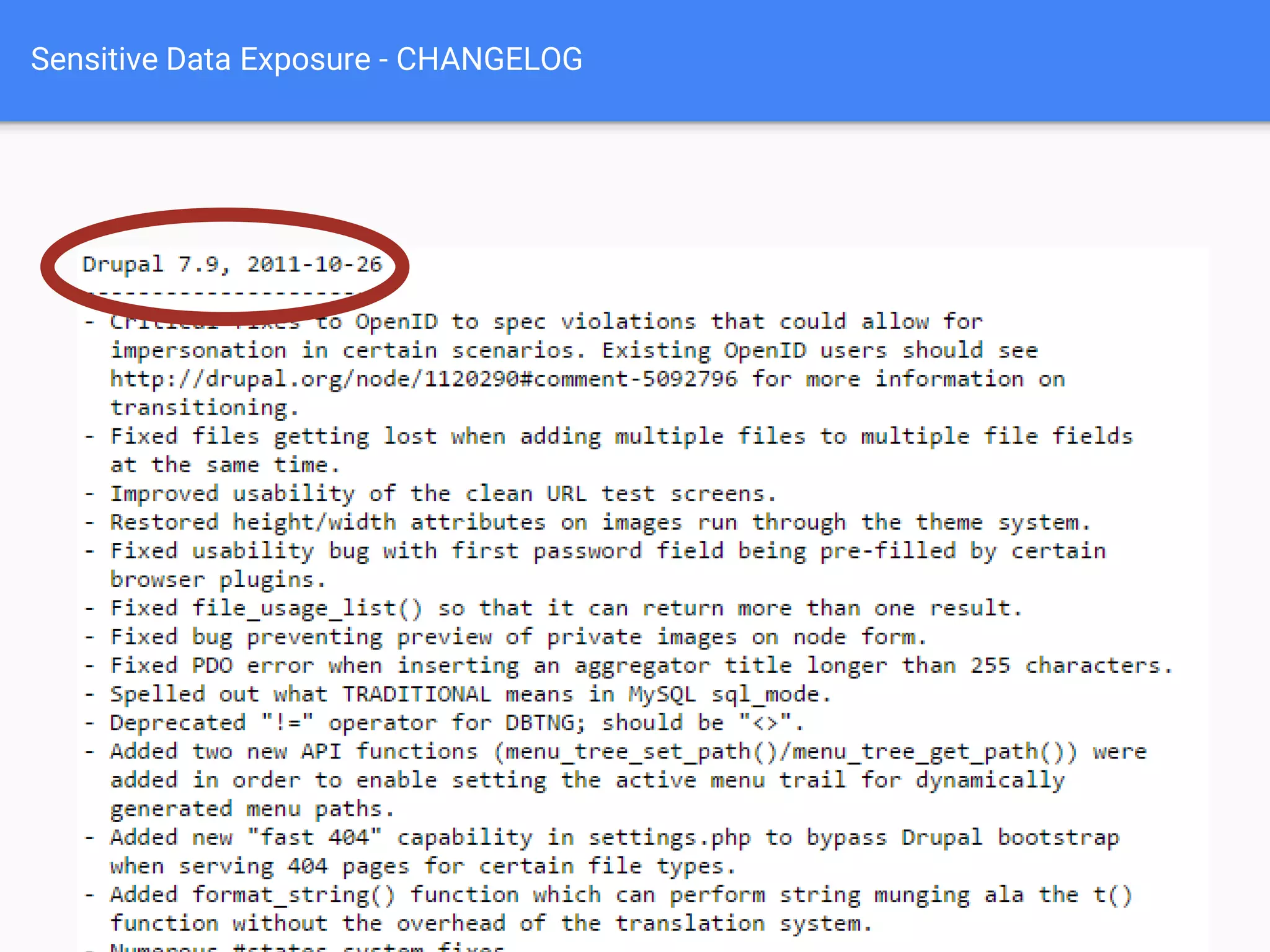
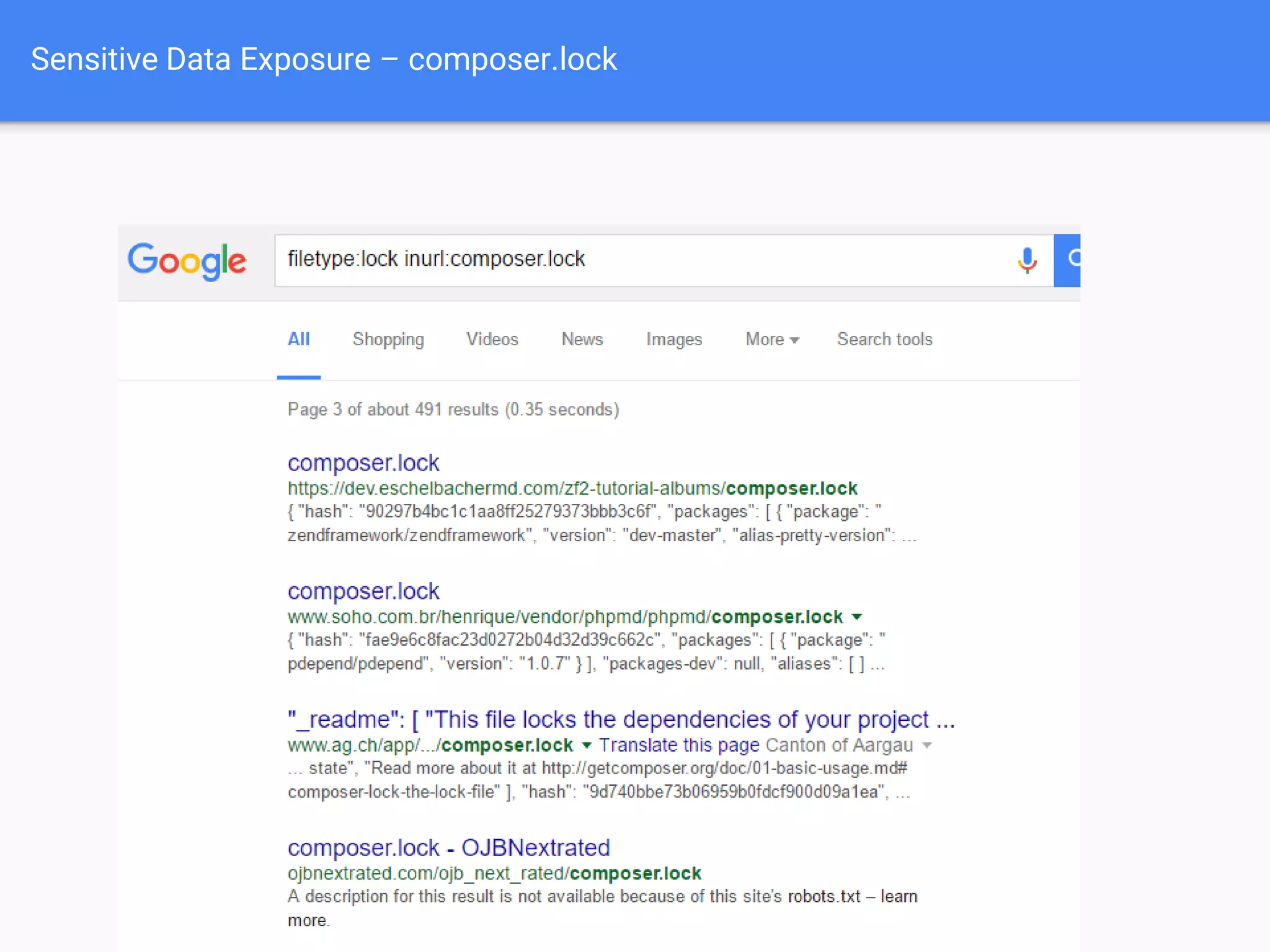
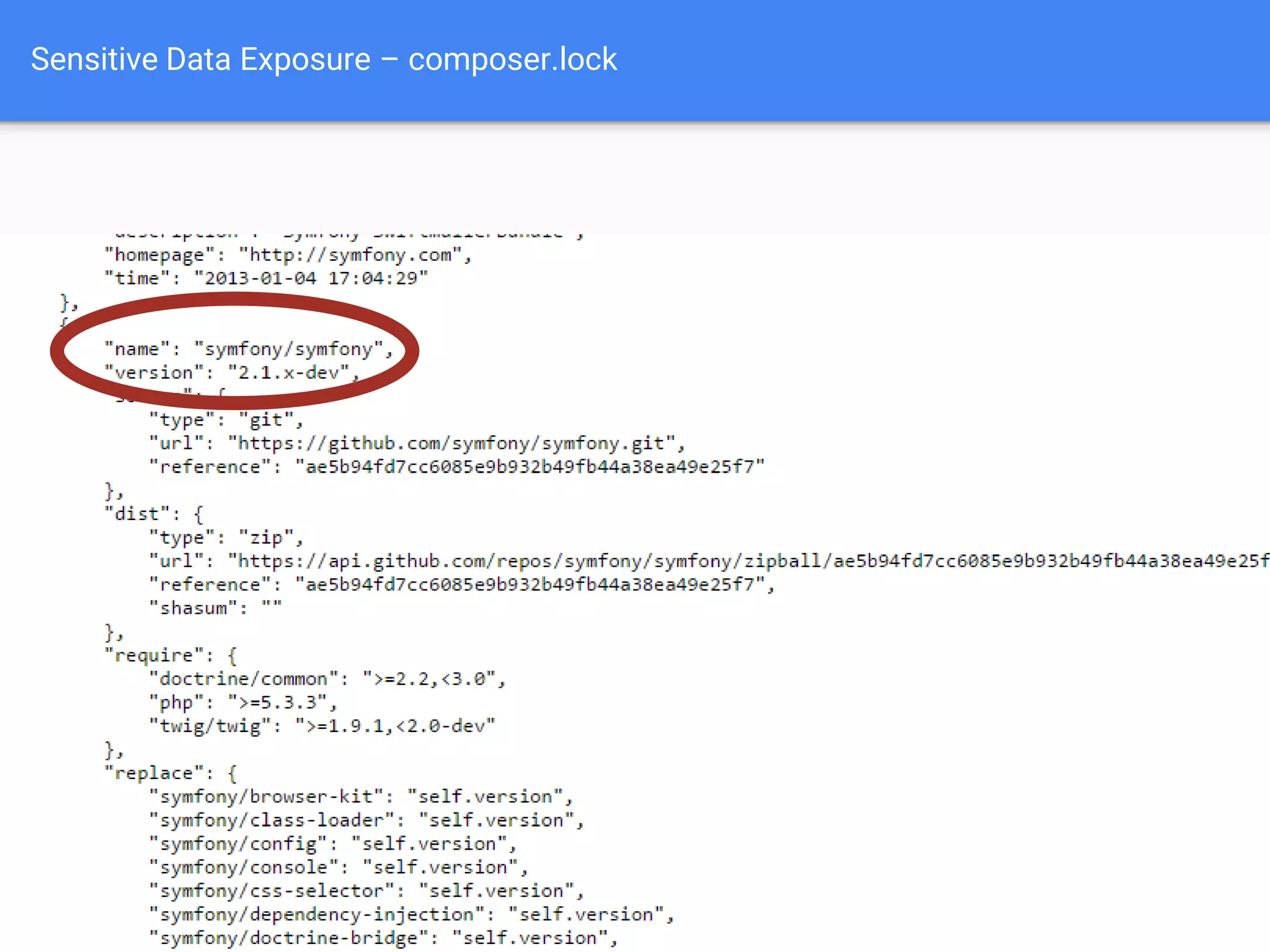
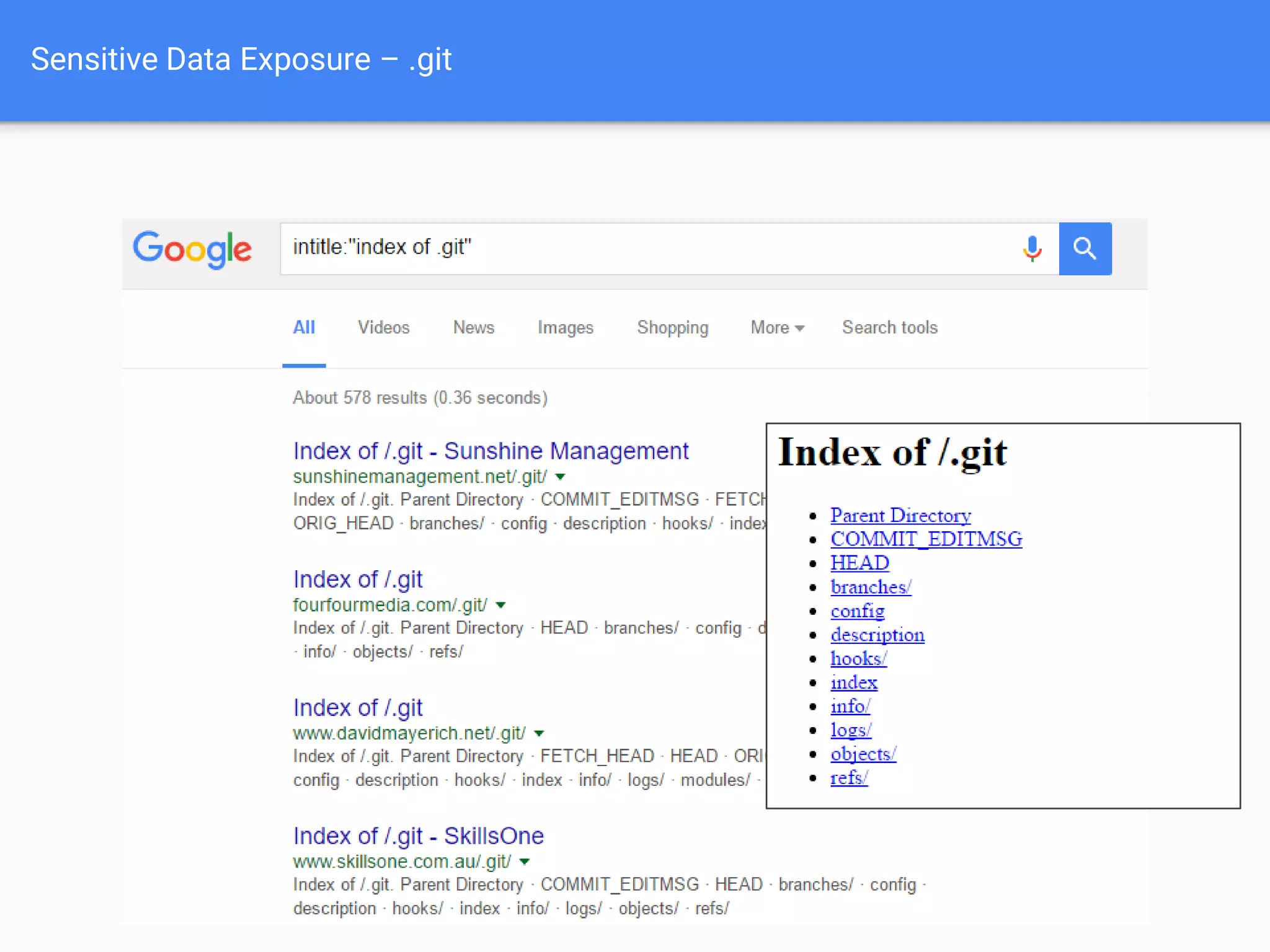
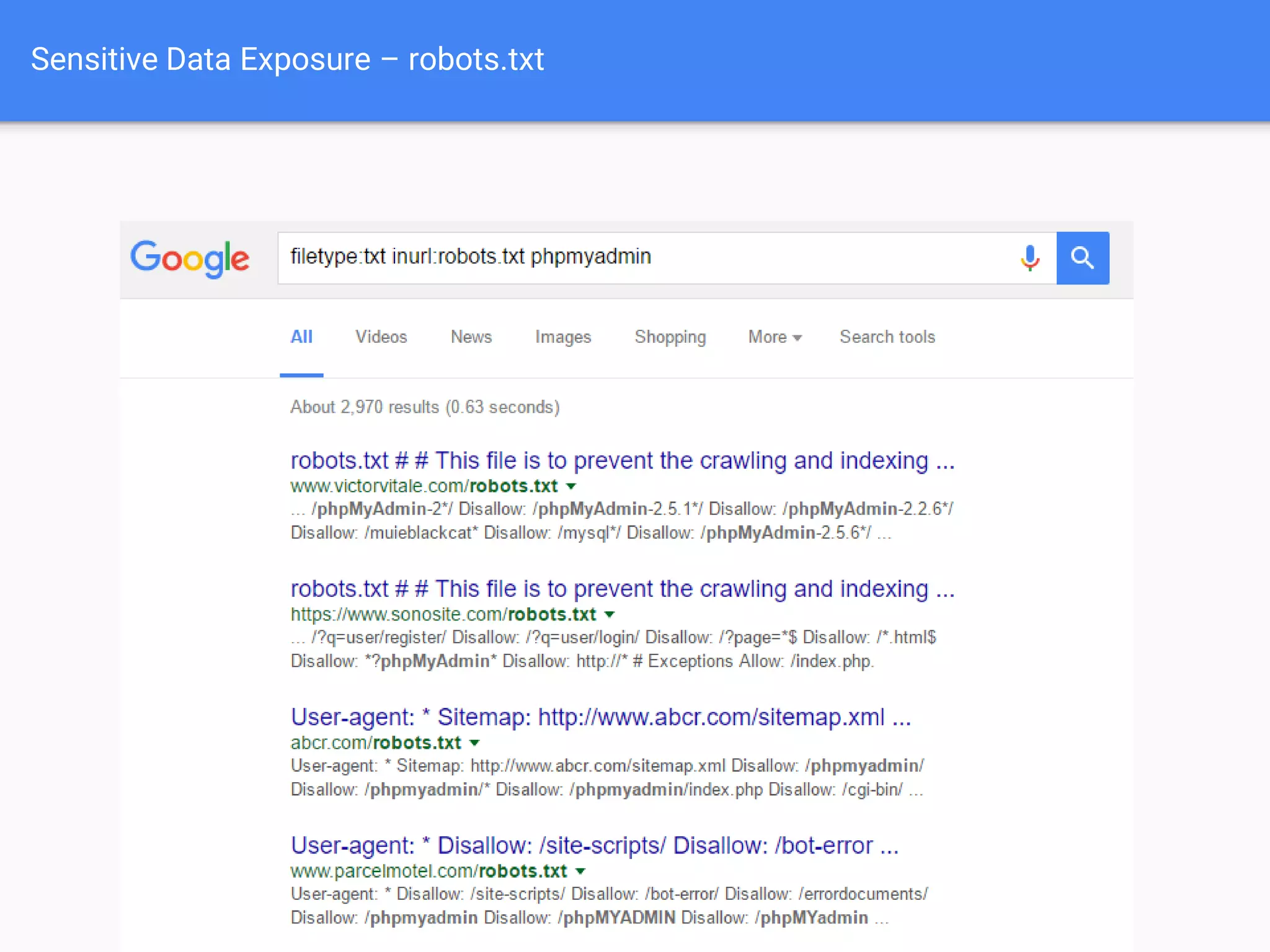
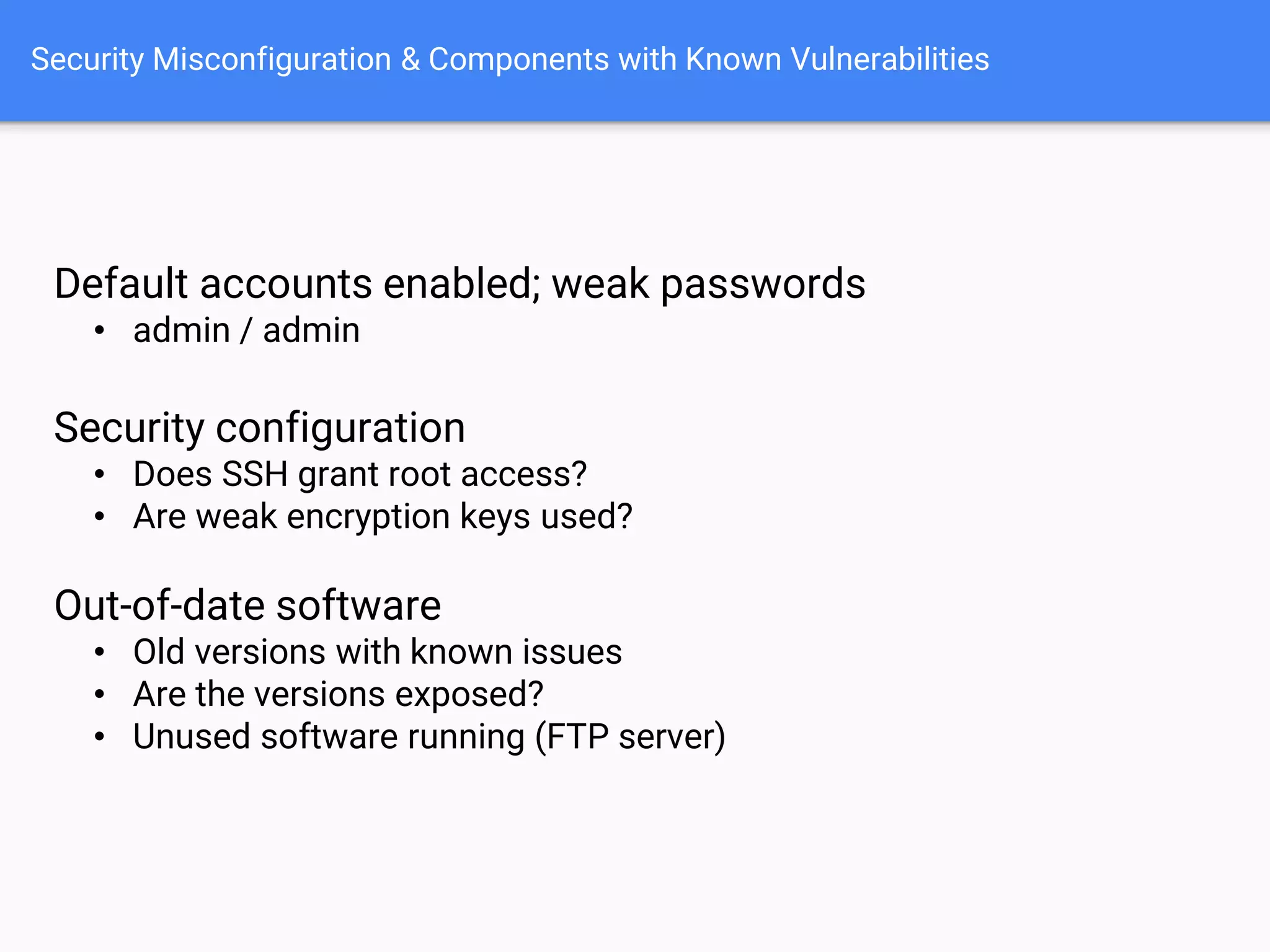
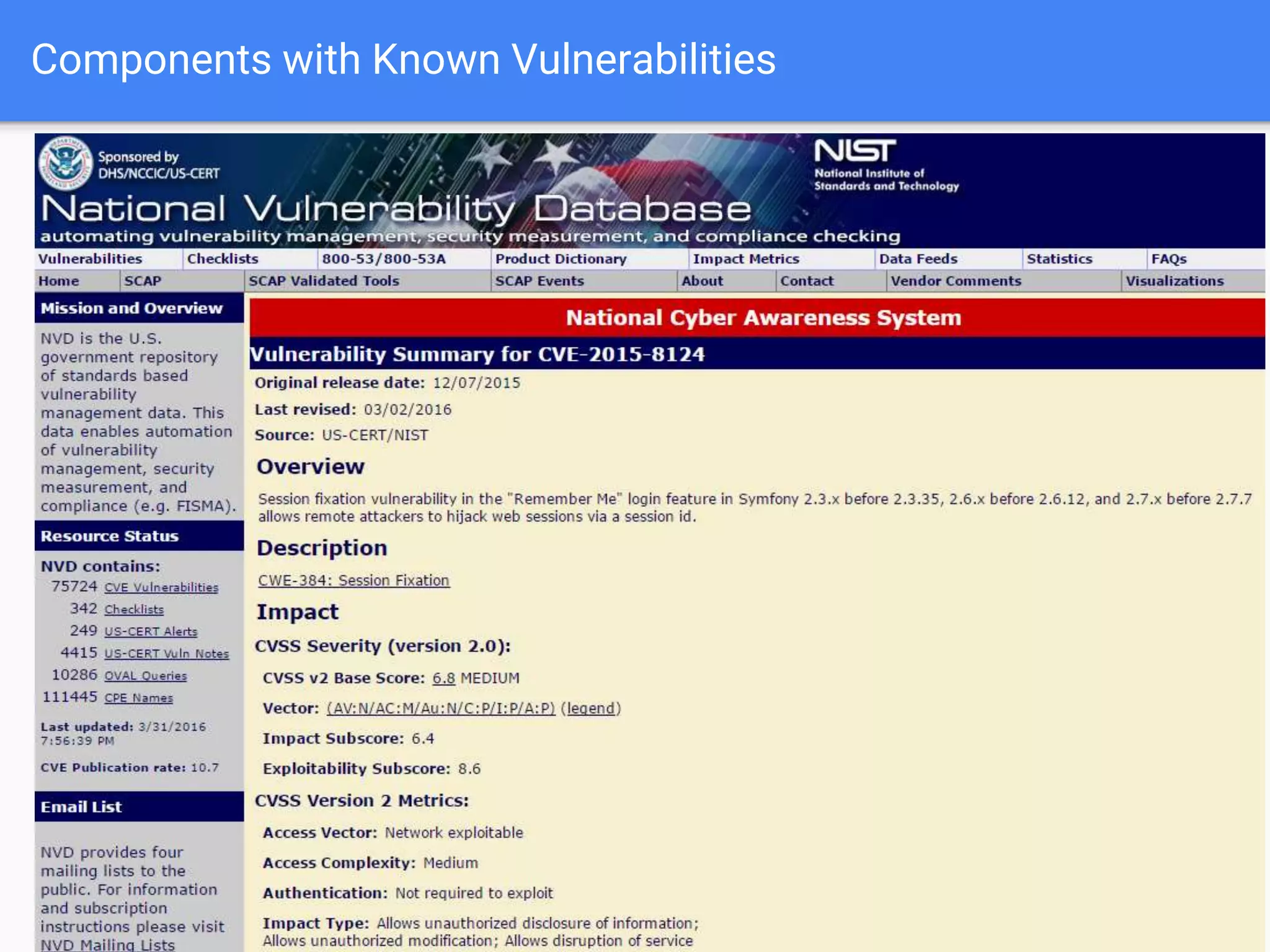
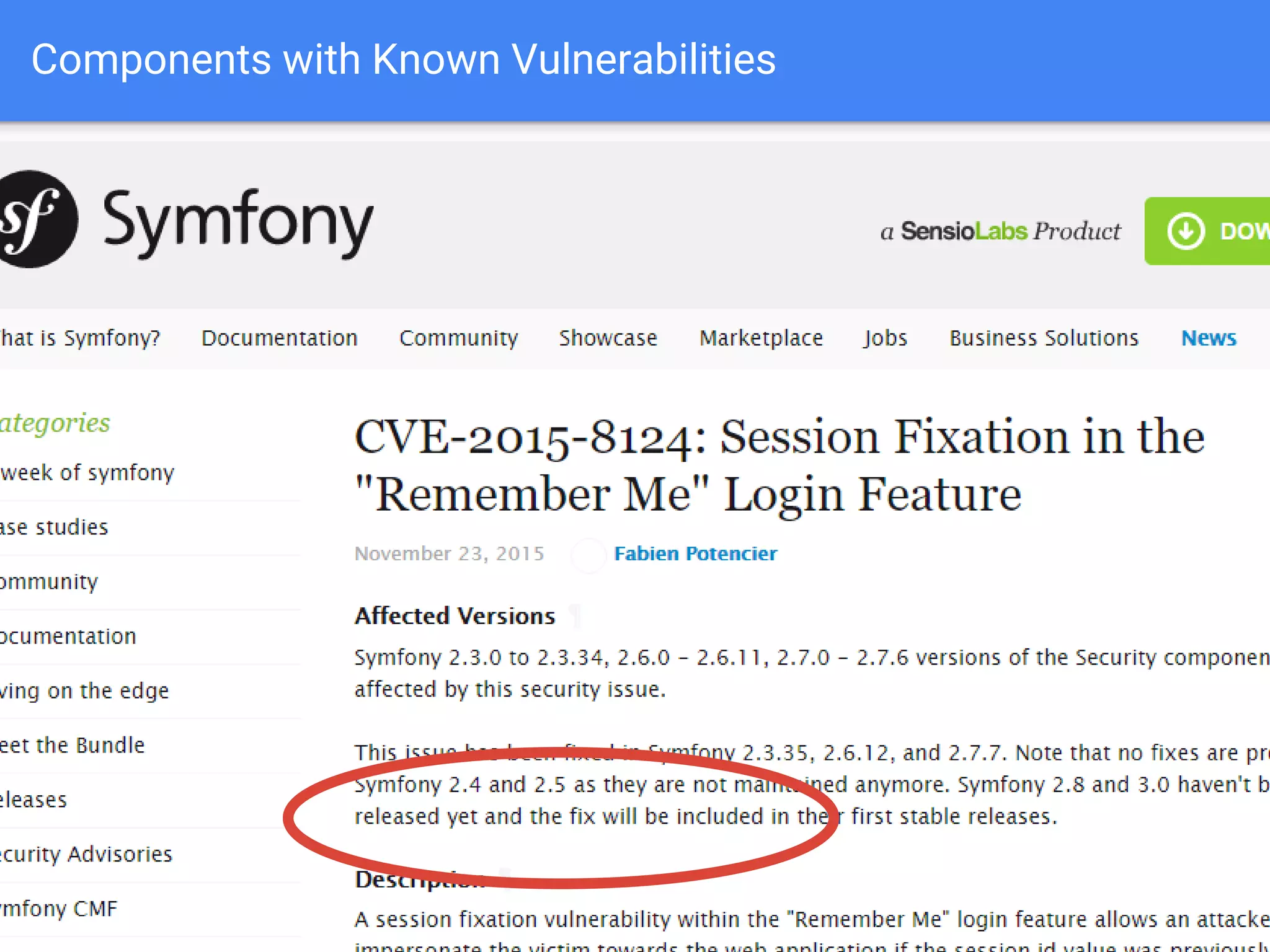
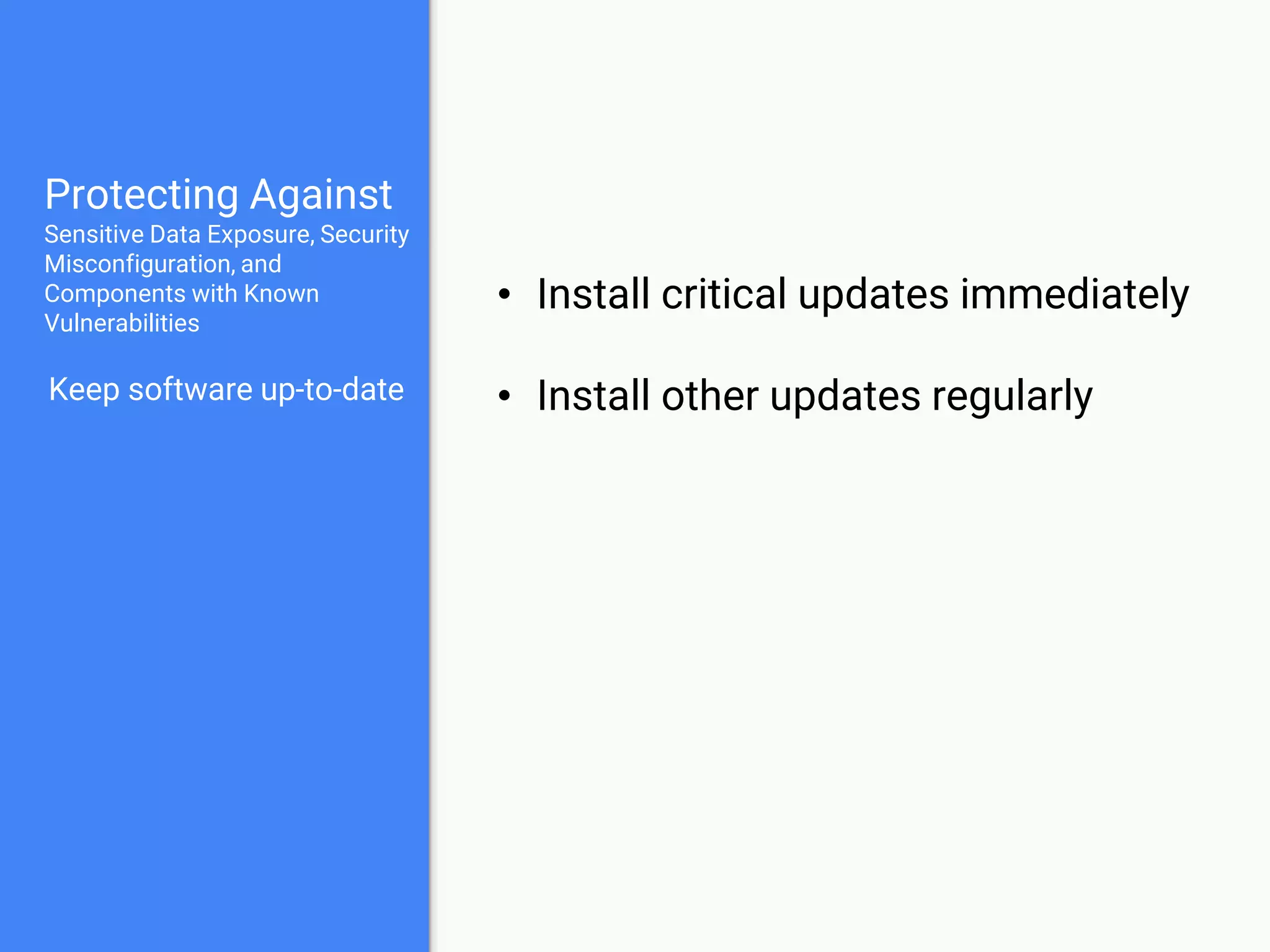
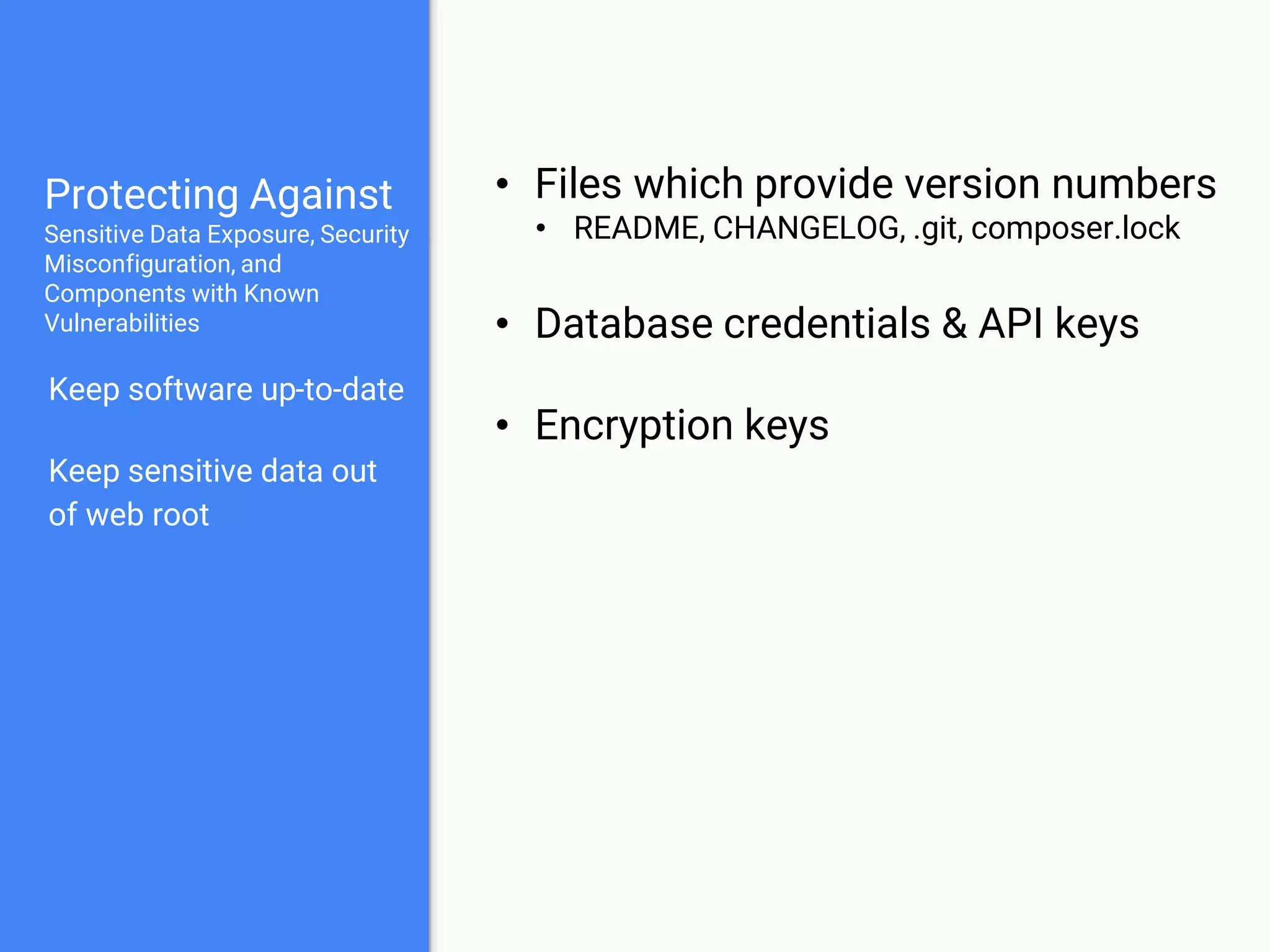
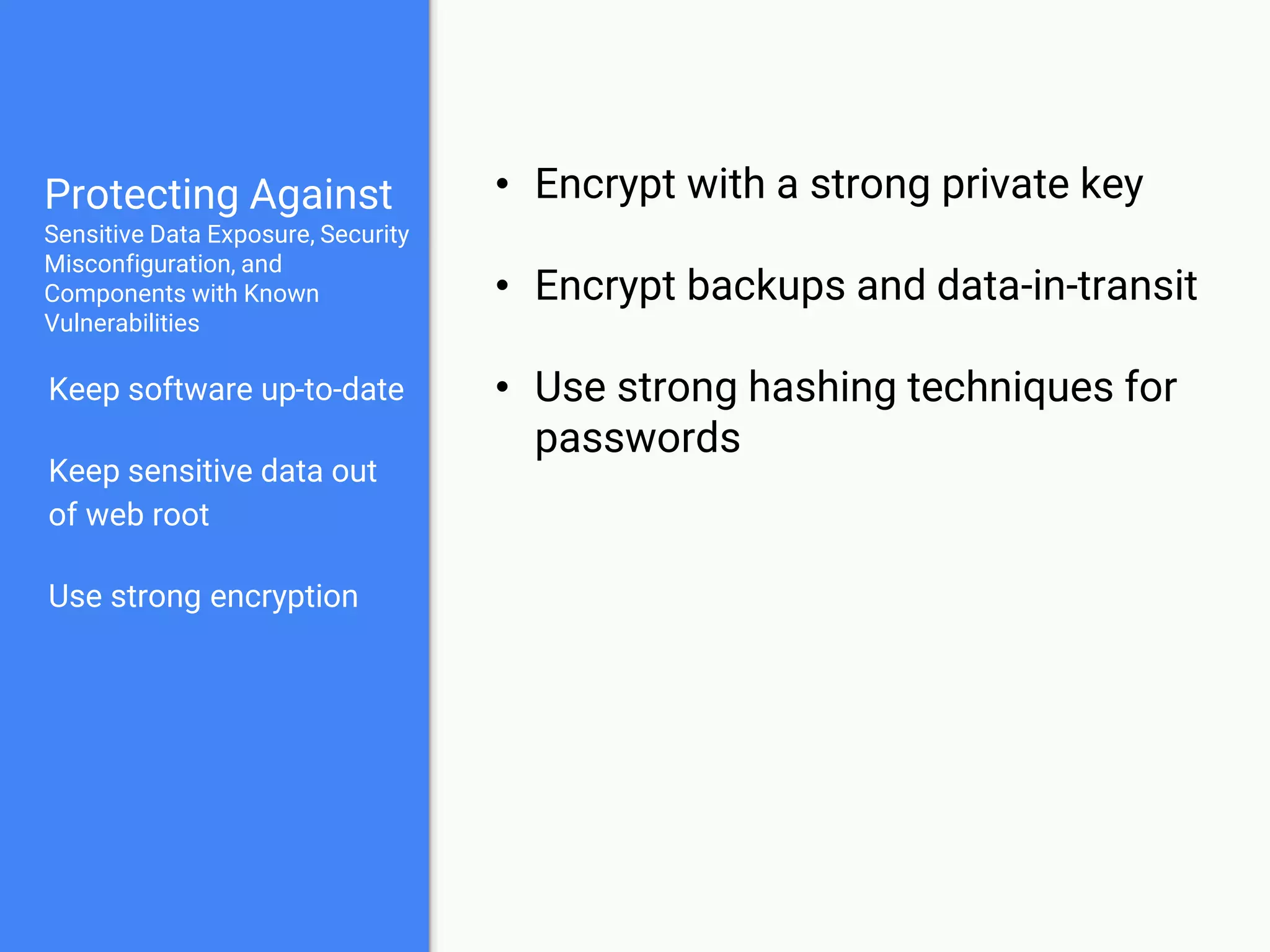
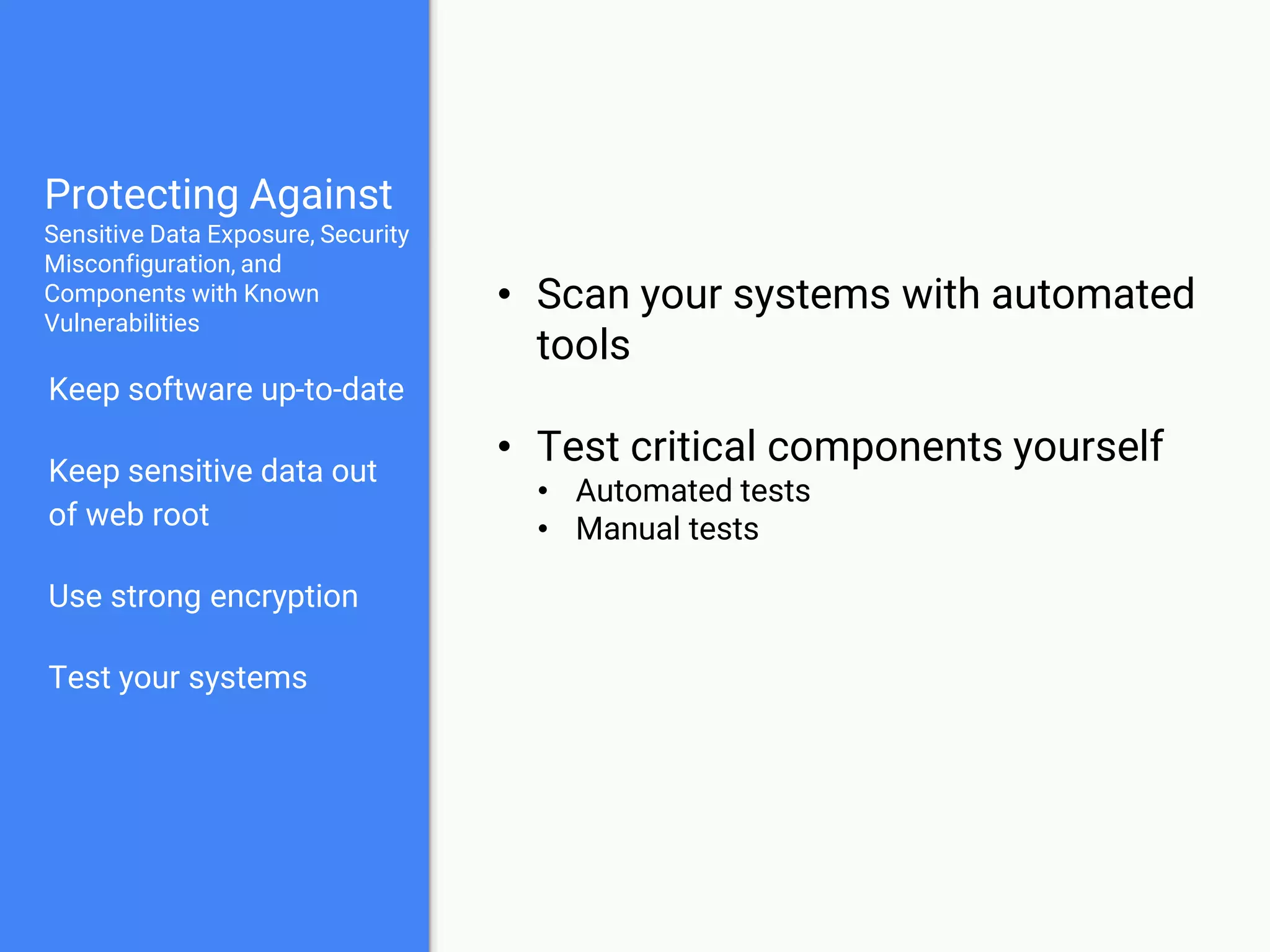
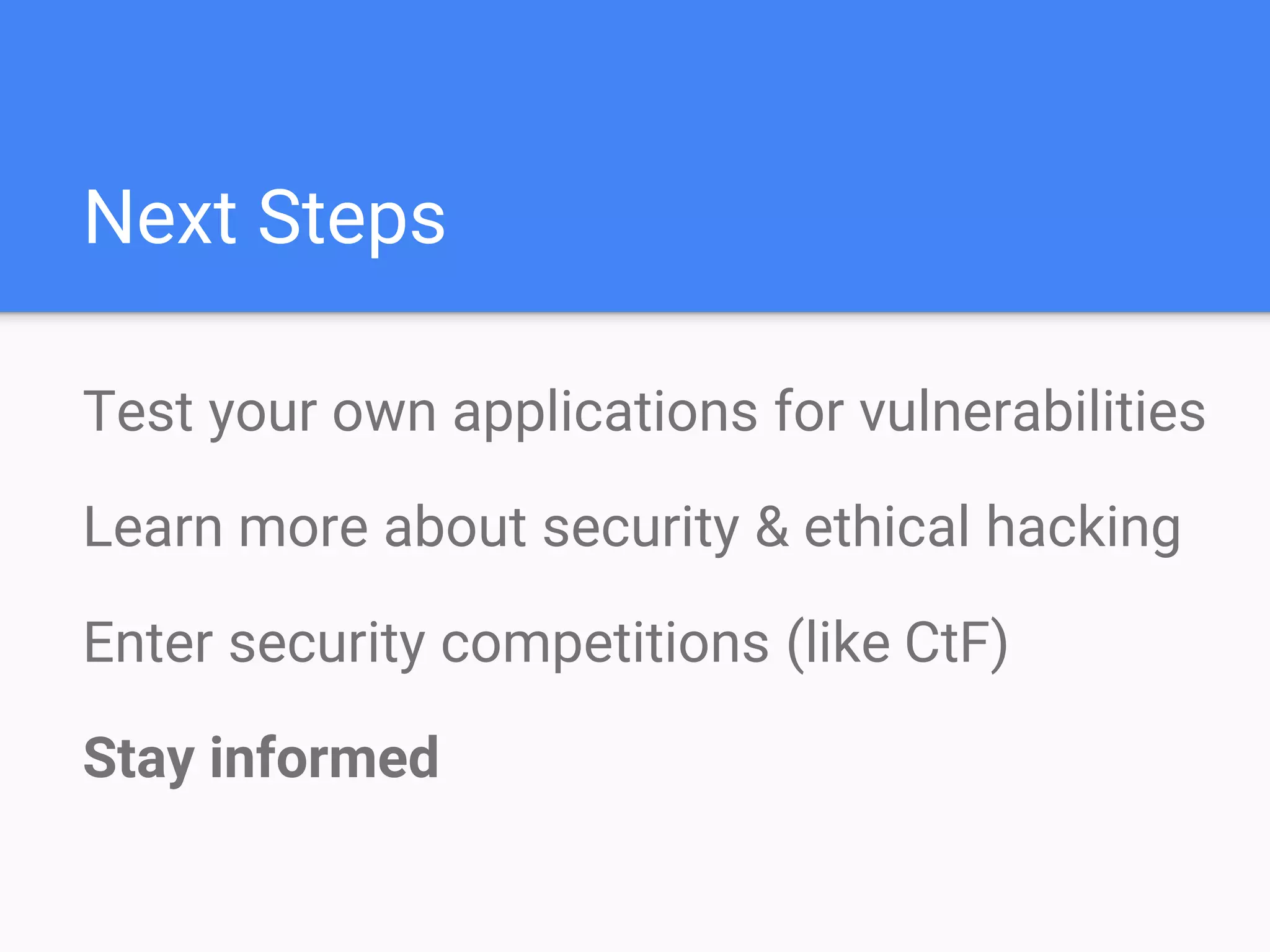
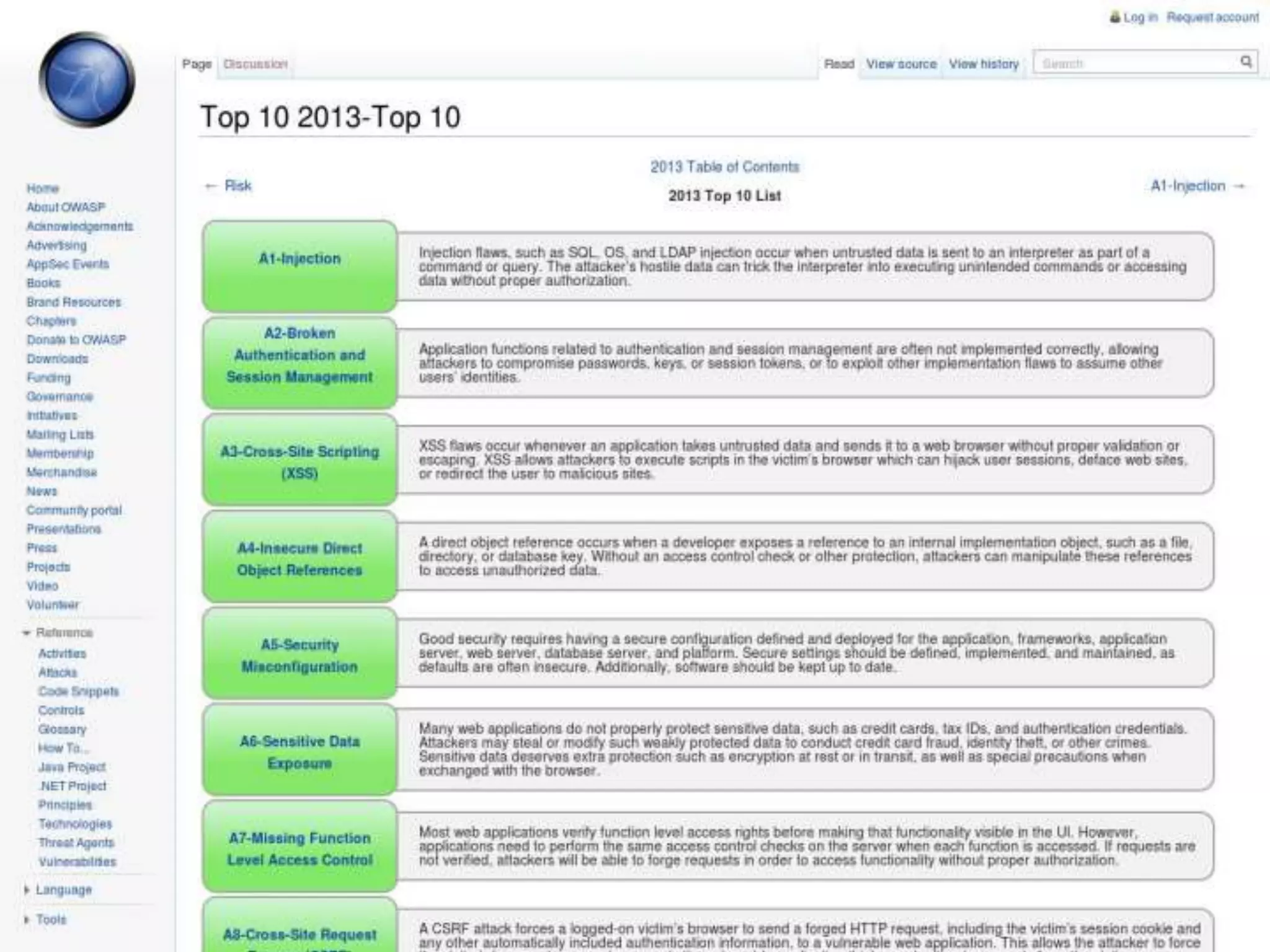
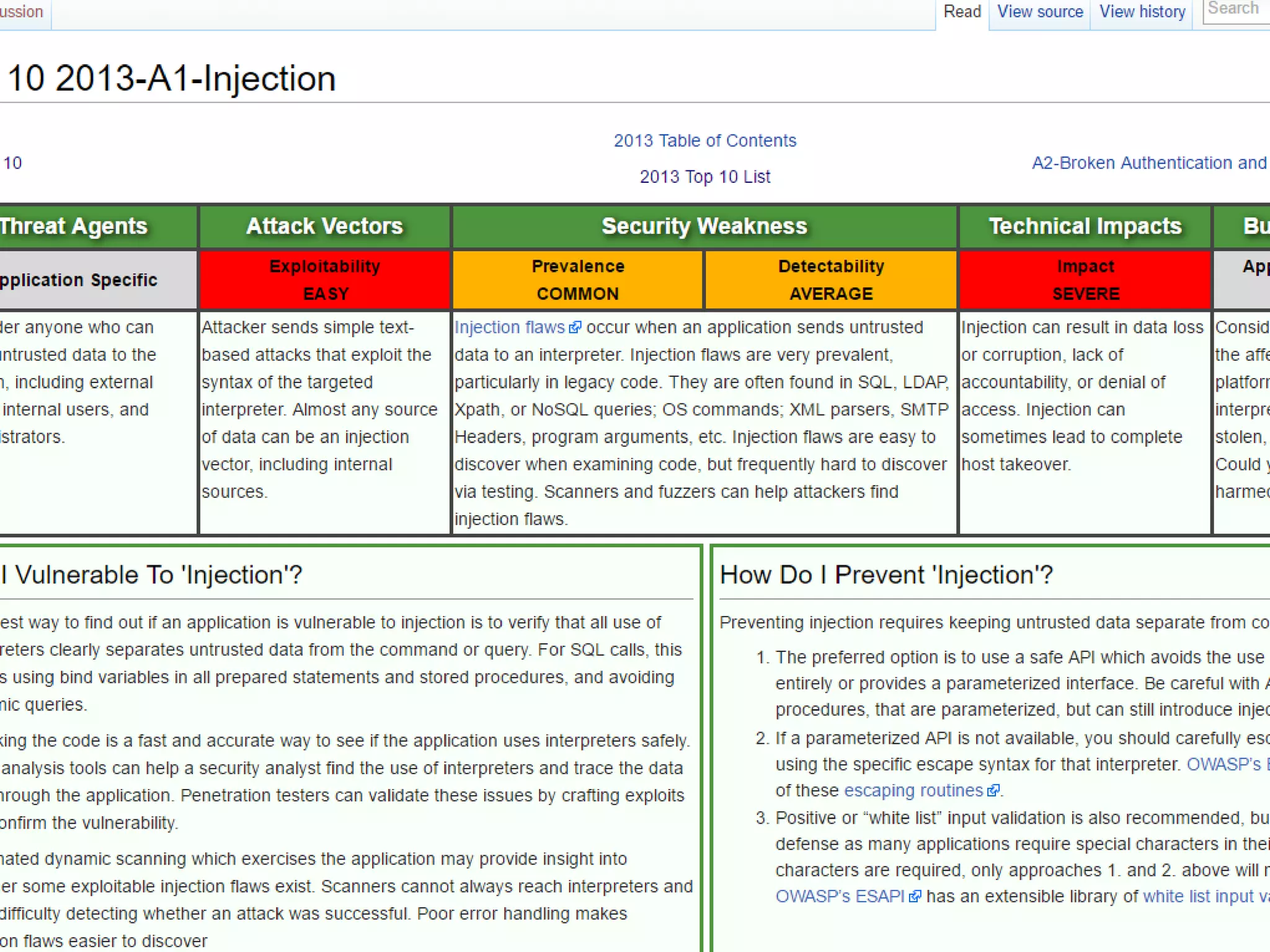
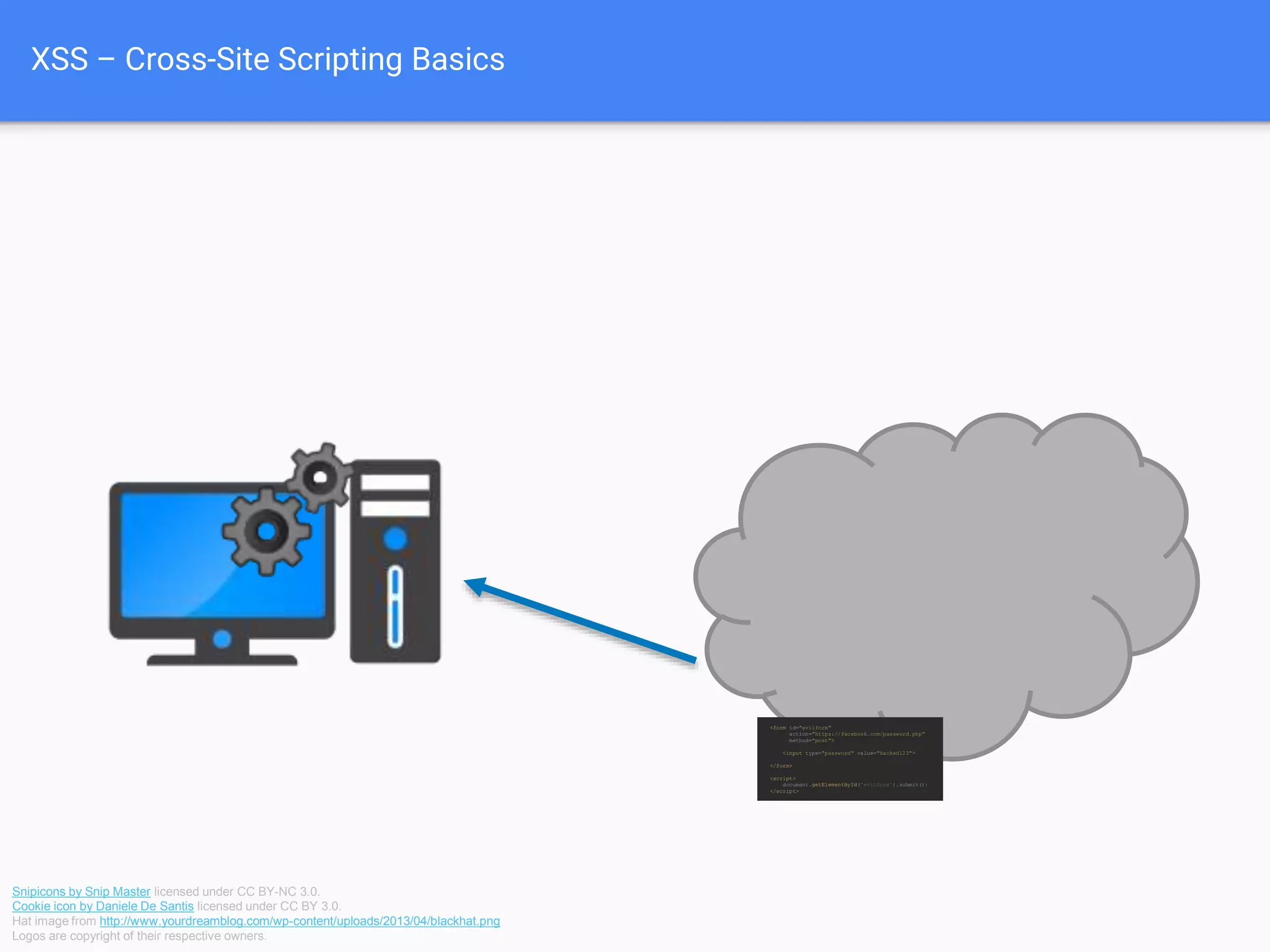
The document discusses web application security, focusing on common vulnerabilities such as SQL injection and cross-site scripting (XSS). It outlines methods for detecting and exploiting these vulnerabilities from an attacker's perspective, while also providing strategies for protection, including escaping user input and using prepared statements. Additionally, it emphasizes the importance of ethical considerations in security testing, urging individuals to seek permission before testing systems they do not own.

![Colin O’Dell
@colinodell
Lead Web Developer at Unleashed Technologies
PHP developer since 2002
league/commonmark maintainer
PHP 7 Upgrade Guide e-book author
php[world] 2015 CtF winner](https://image.slidesharecdn.com/gebhbkmwtryrodvbids0-signature-1b1295ff8d4f63c926cc99fe490d9488deb80d97cdf6a4560e5eb93d780d82cd-poli-160624212034/75/Hacking-Your-Way-To-Better-Security-Dutch-PHP-Conference-2016-2-2048.jpg)





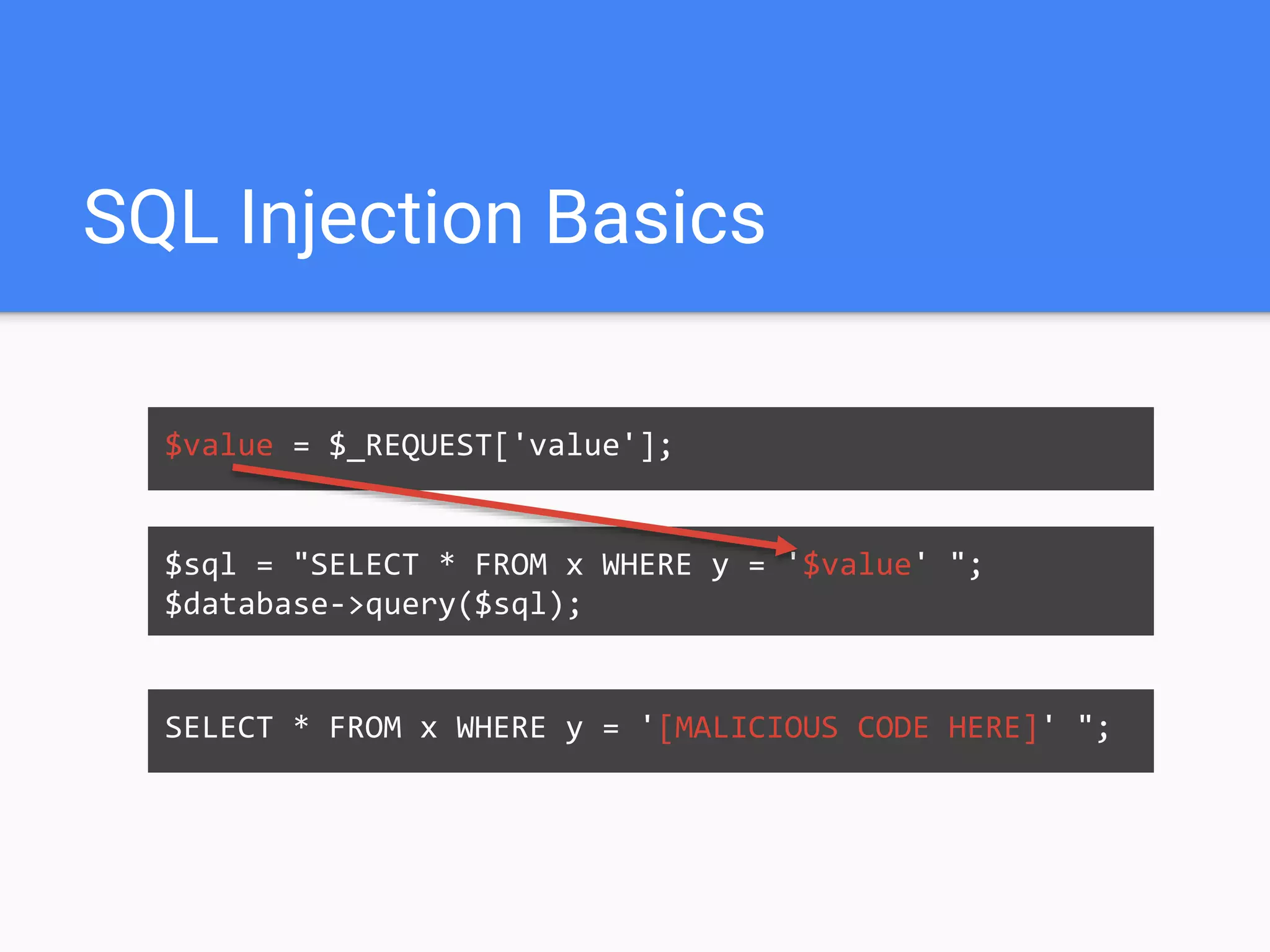
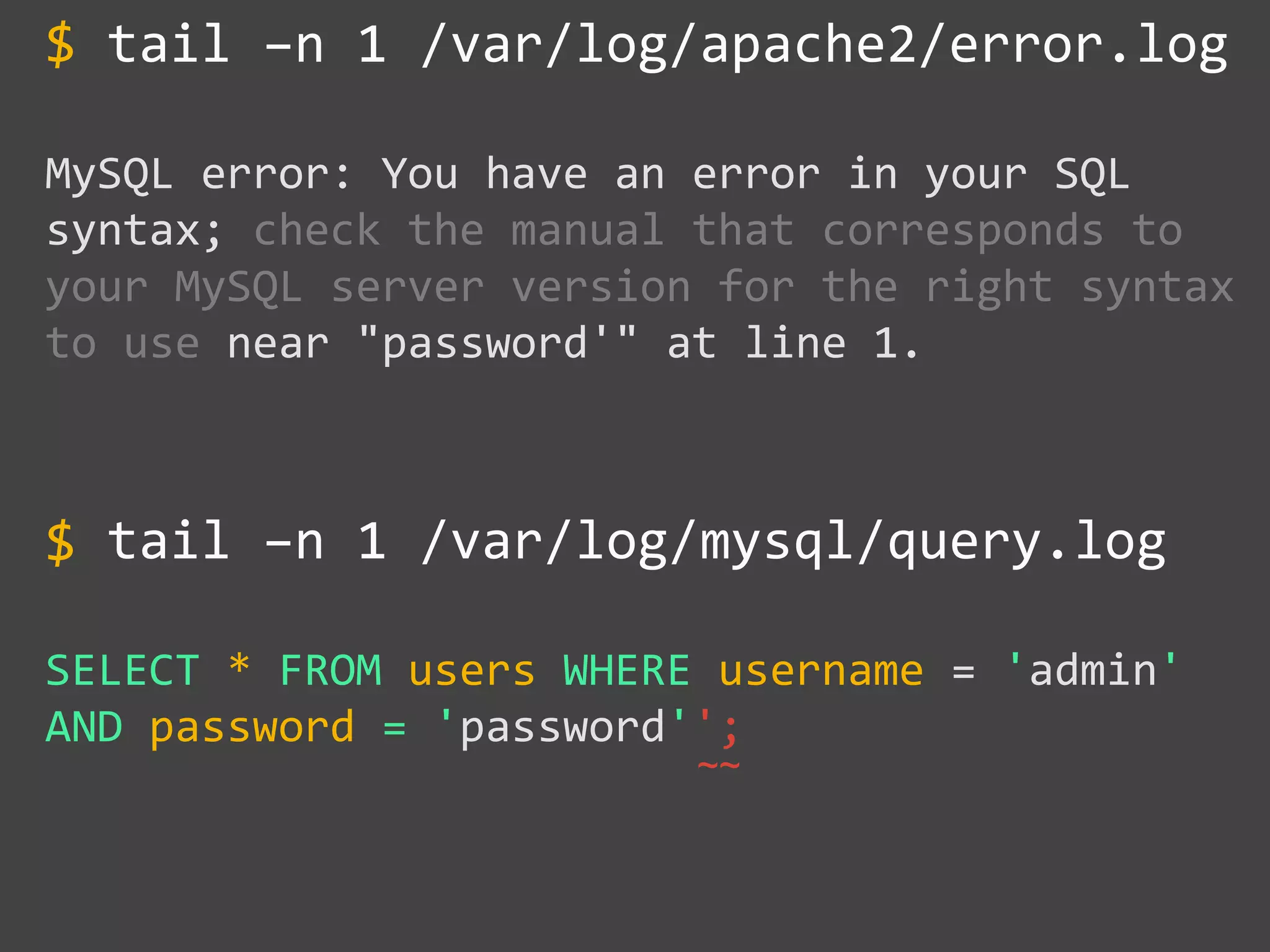
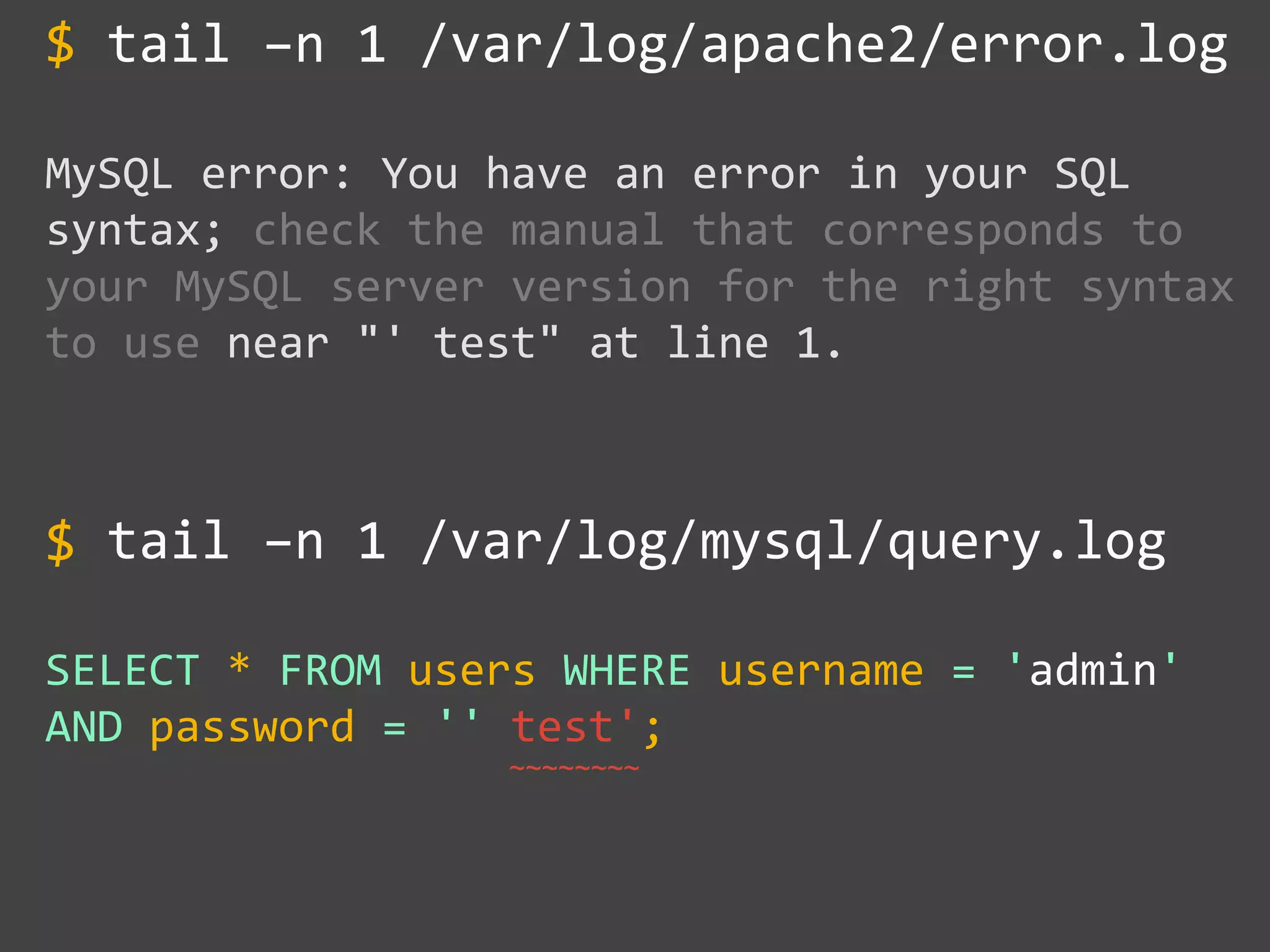
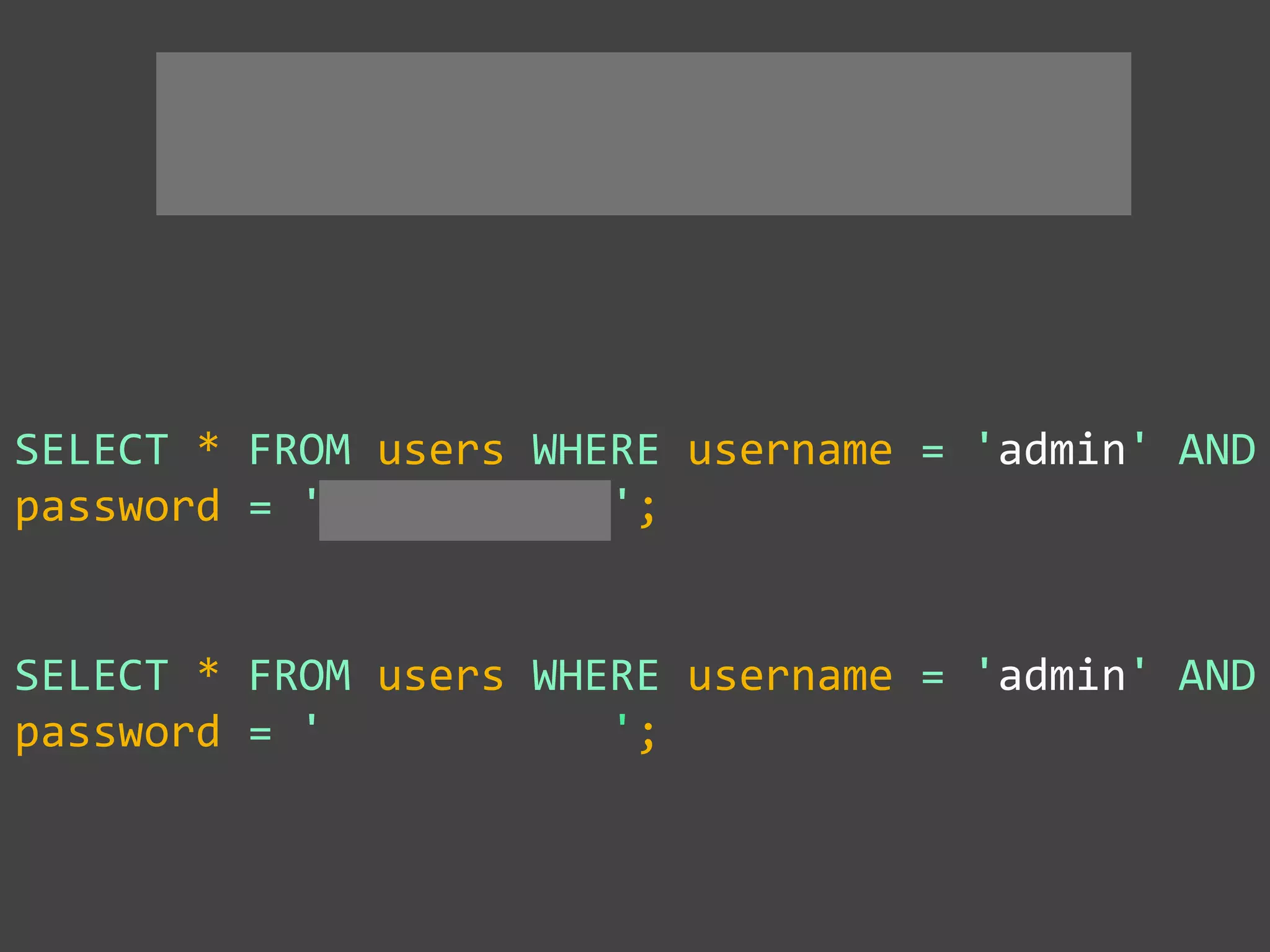
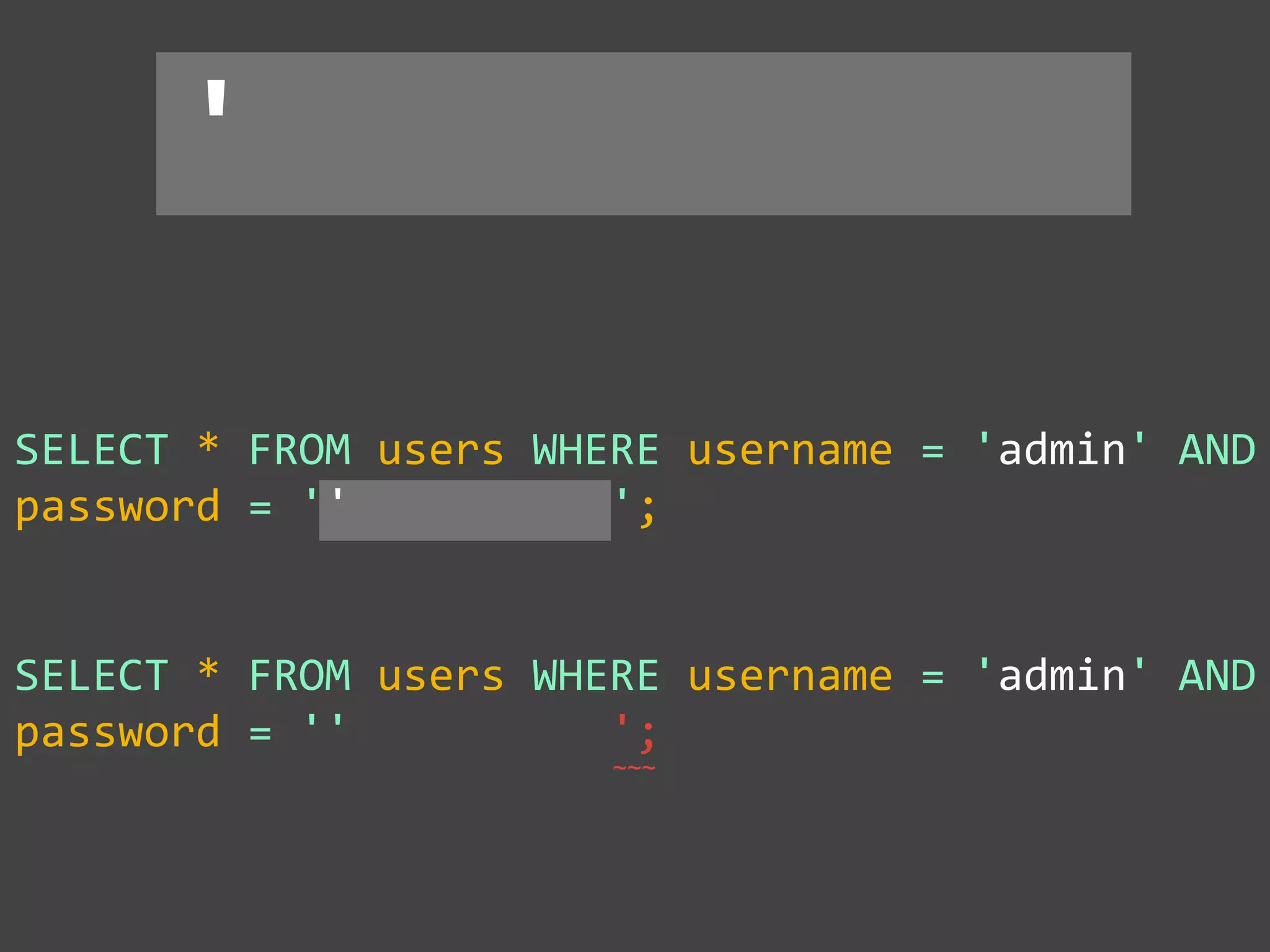
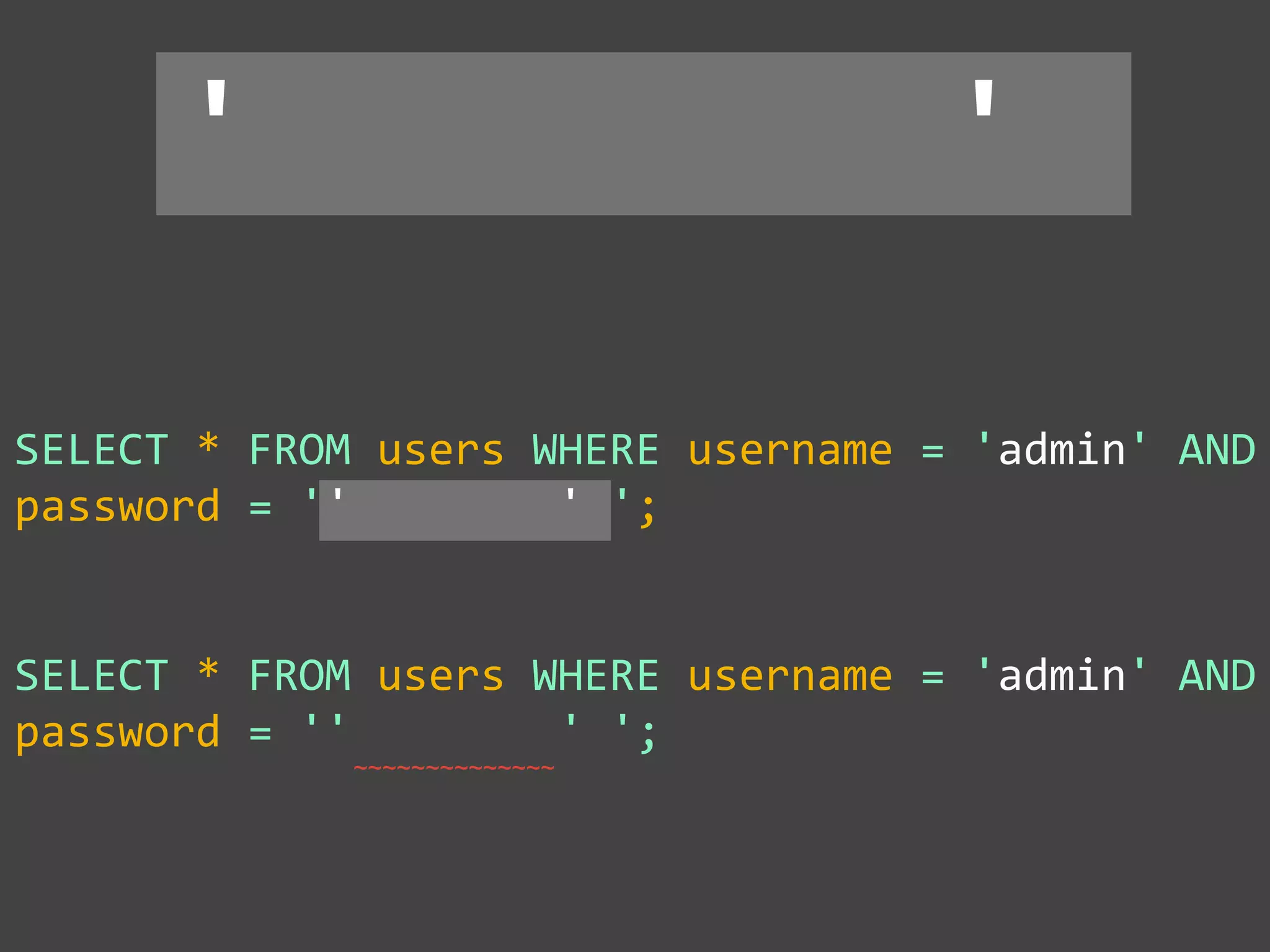
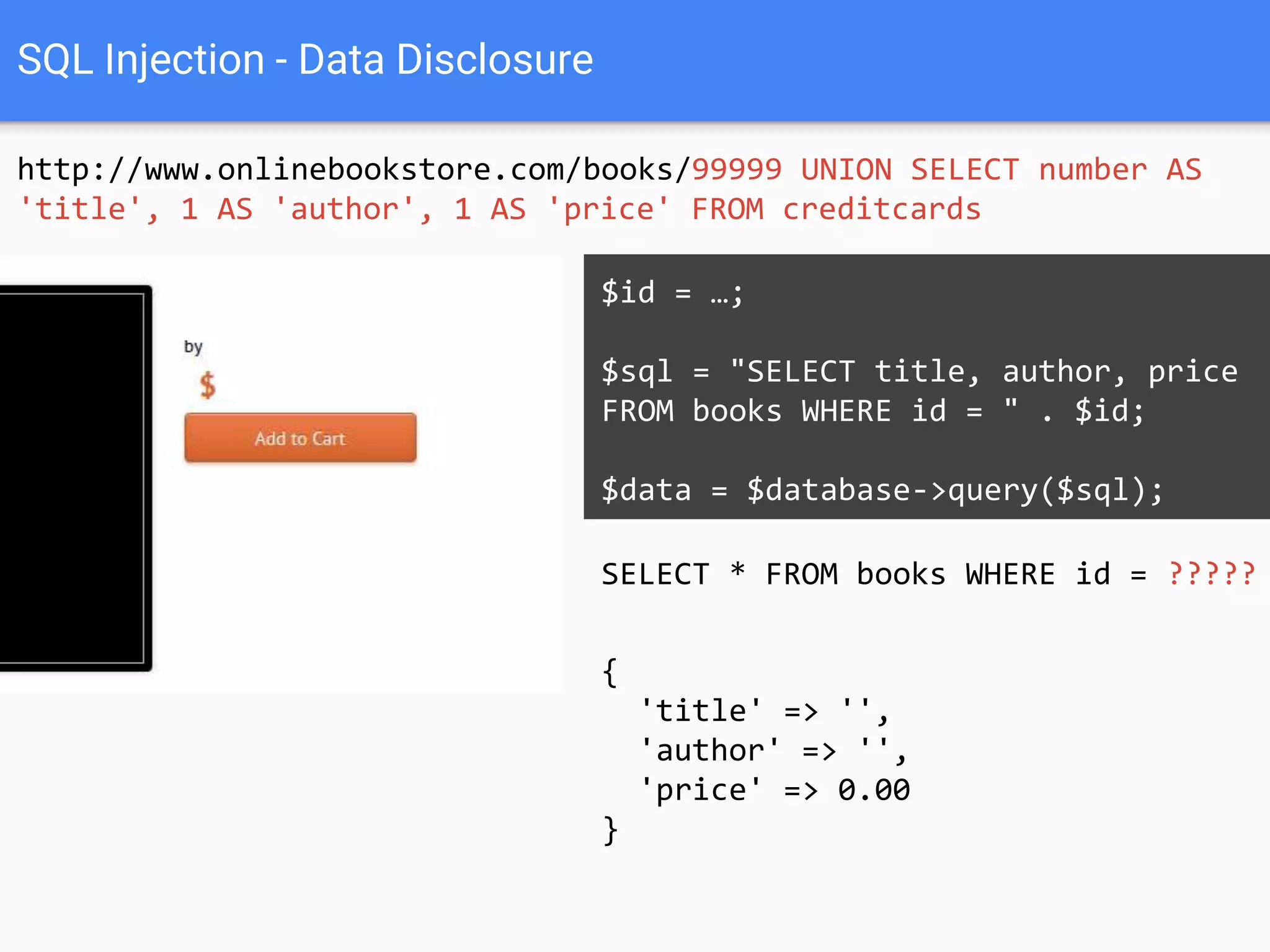
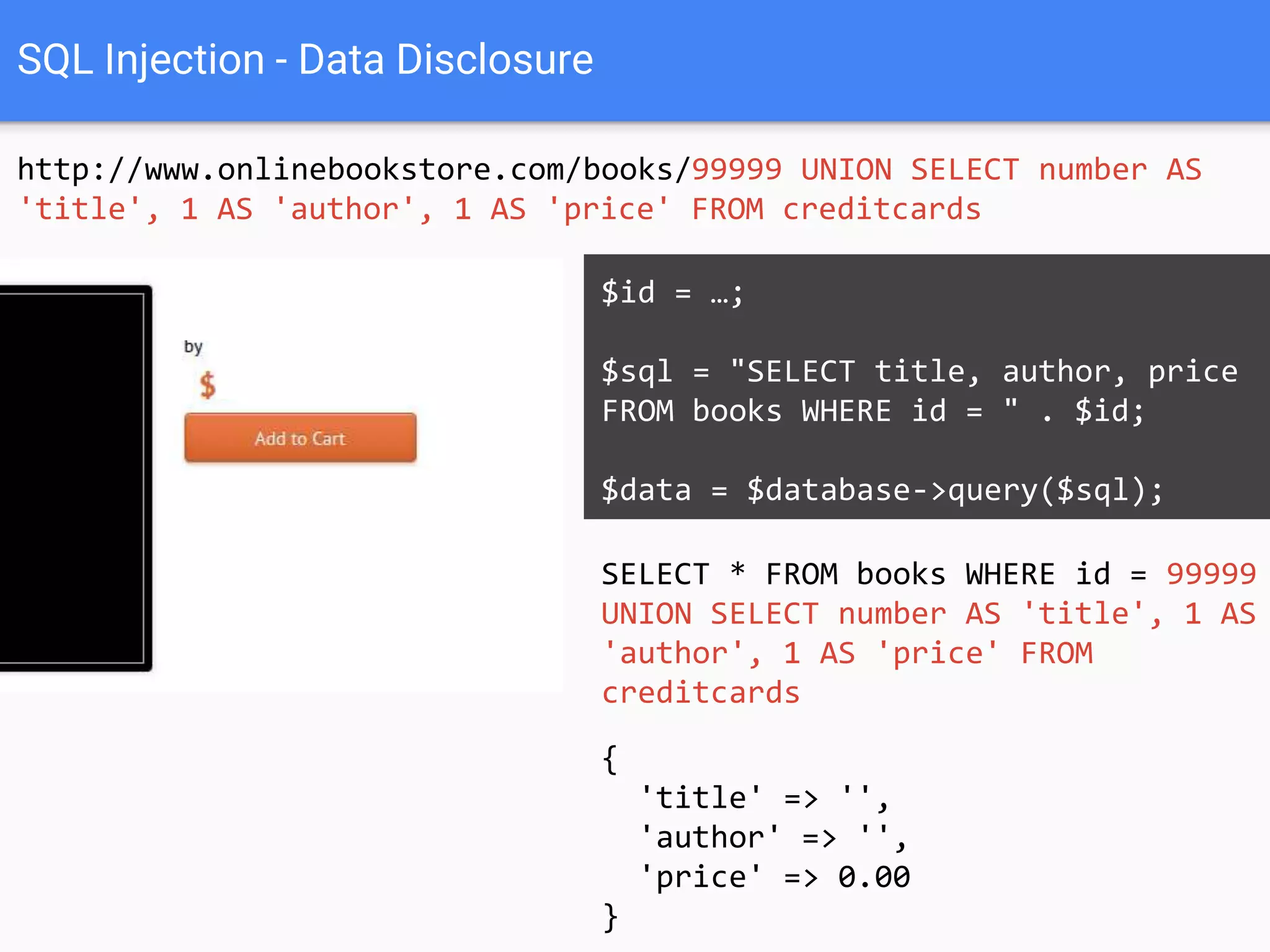
![SQL Injection Basics
$value = $_REQUEST['value'];
SELECT * FROM x WHERE y = '[MALICIOUS CODE HERE]' ";
$sql = "SELECT * FROM x WHERE y = '$value' ";
$database->query($sql);](https://image.slidesharecdn.com/gebhbkmwtryrodvbids0-signature-1b1295ff8d4f63c926cc99fe490d9488deb80d97cdf6a4560e5eb93d780d82cd-poli-160624212034/75/Hacking-Your-Way-To-Better-Security-Dutch-PHP-Conference-2016-10-2048.jpg)
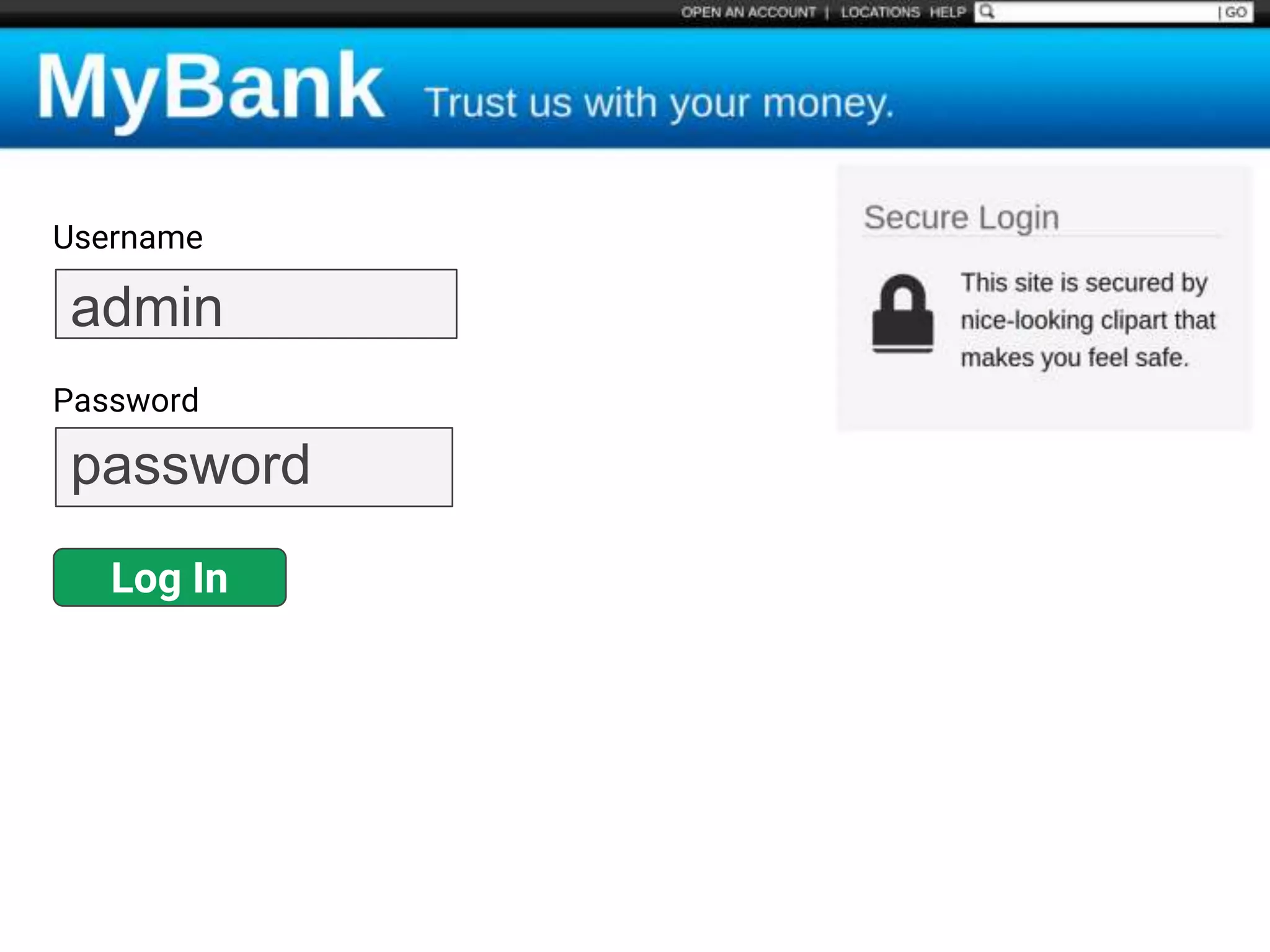
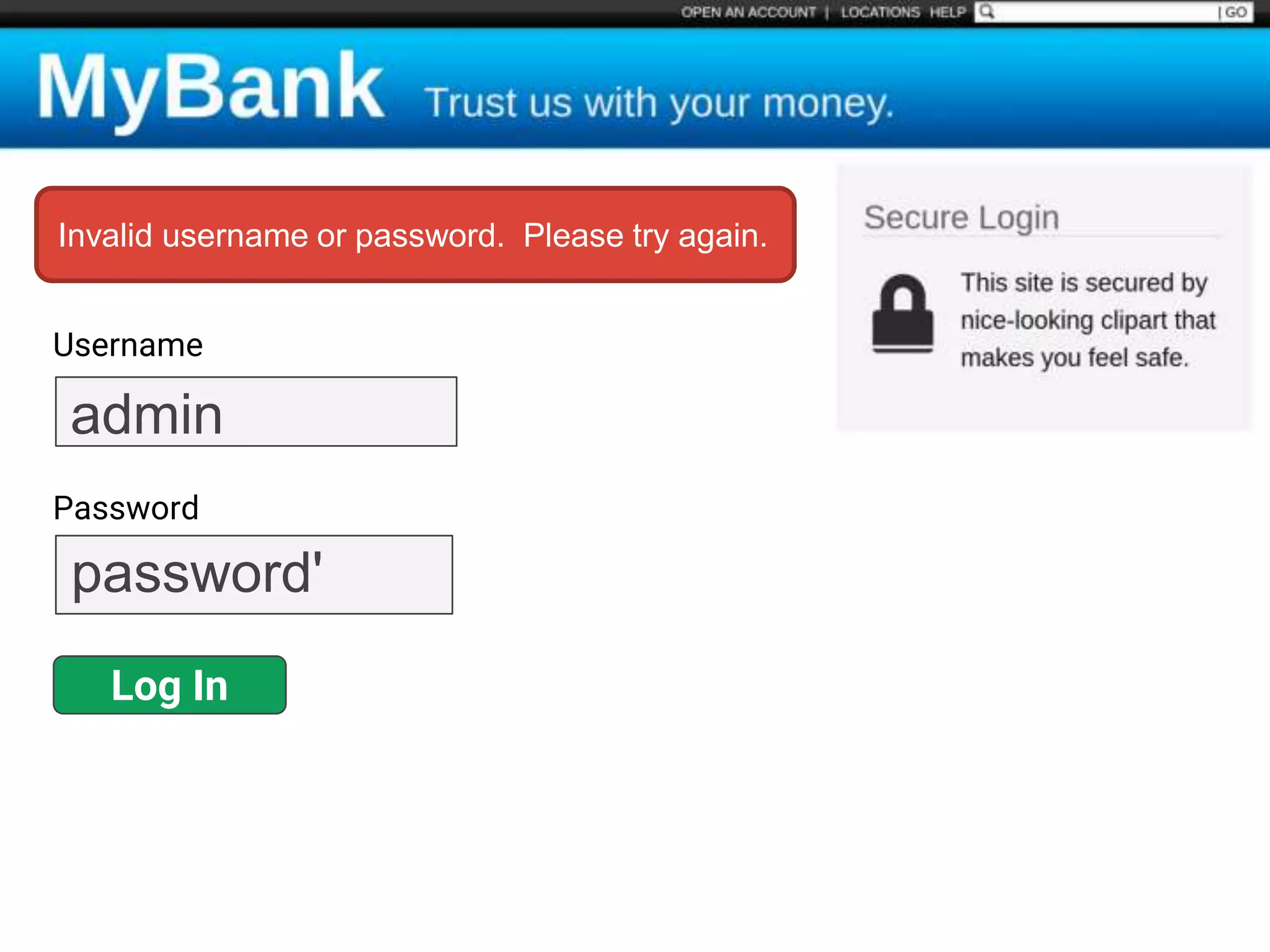
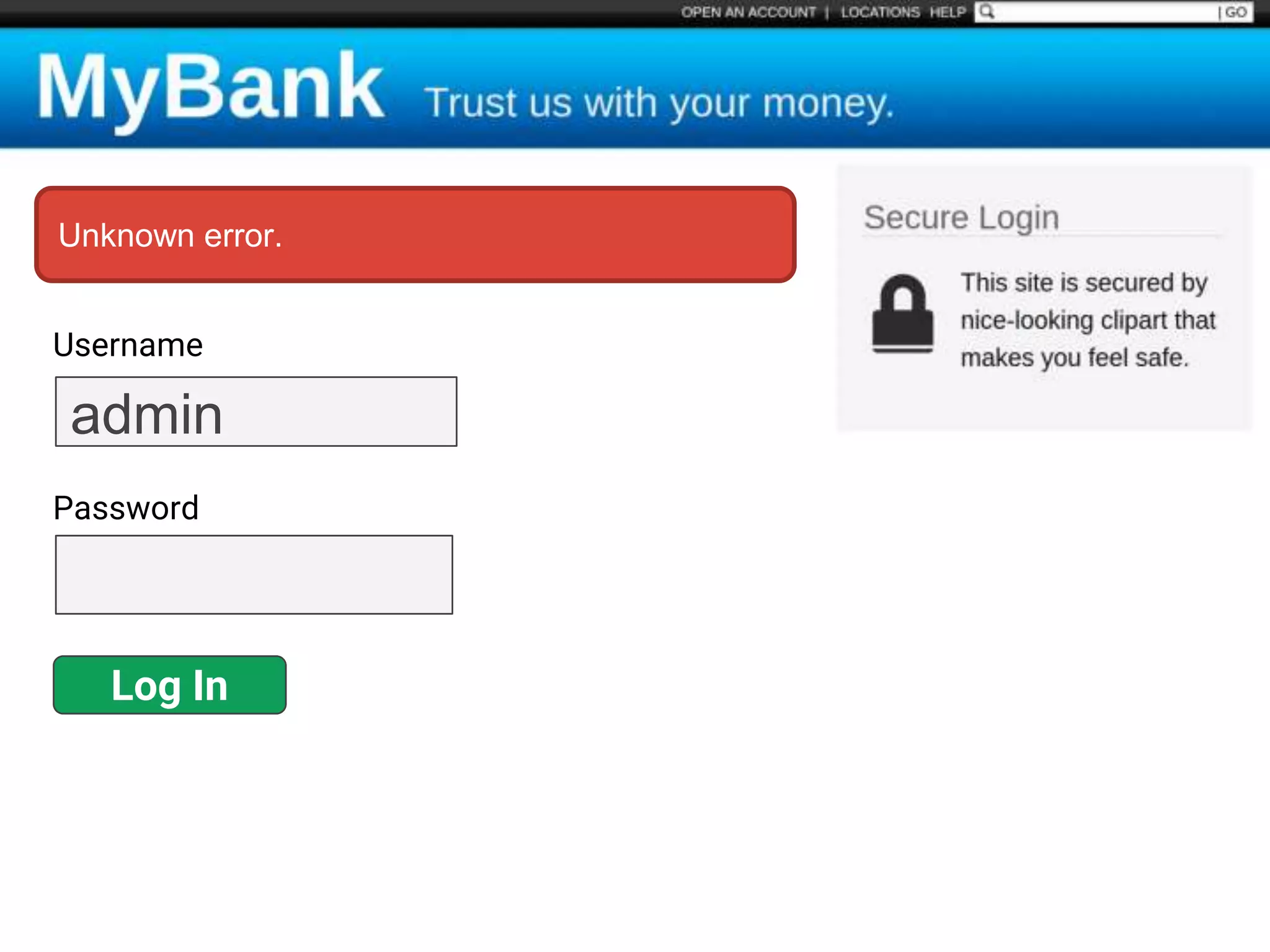
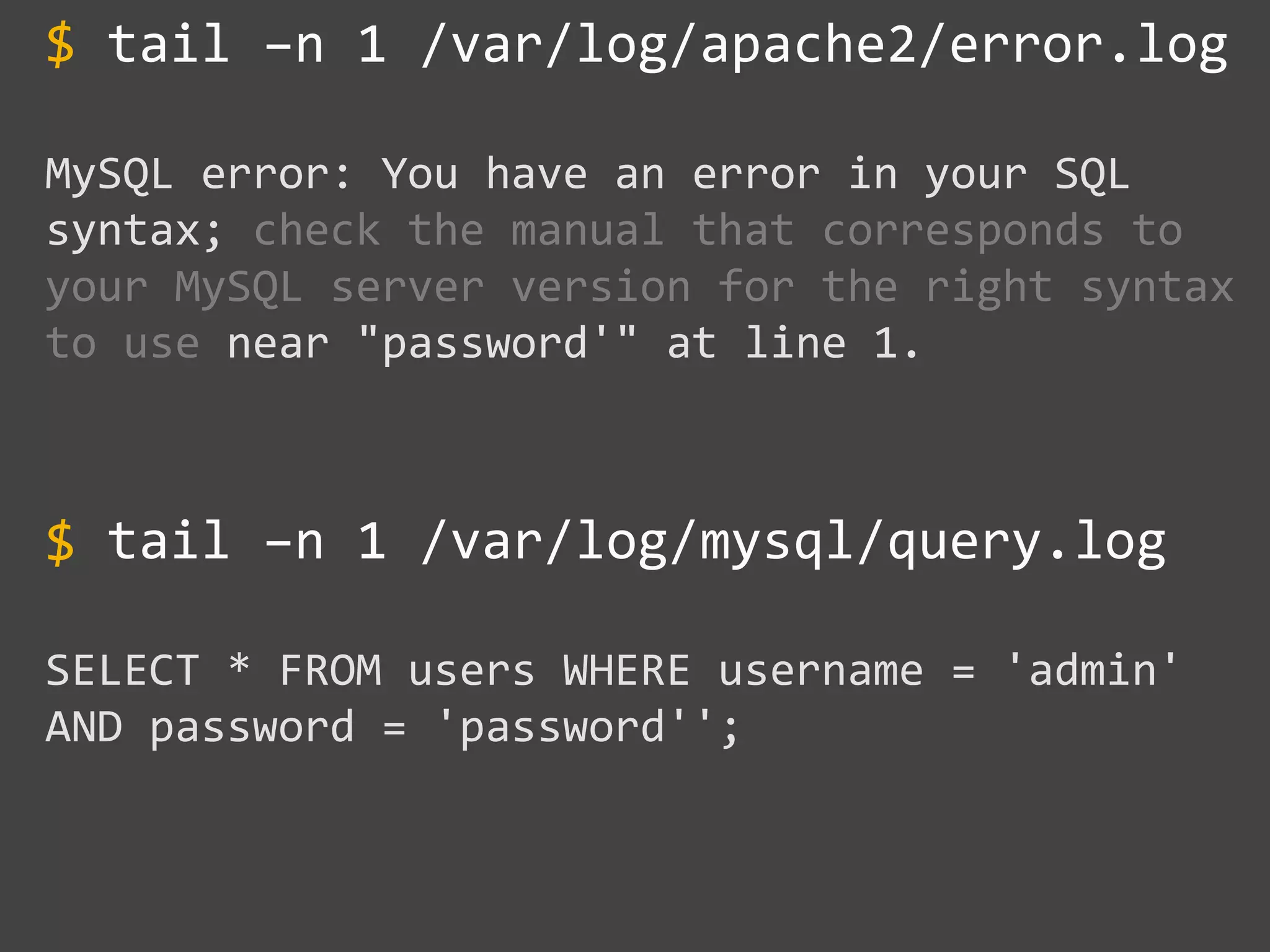
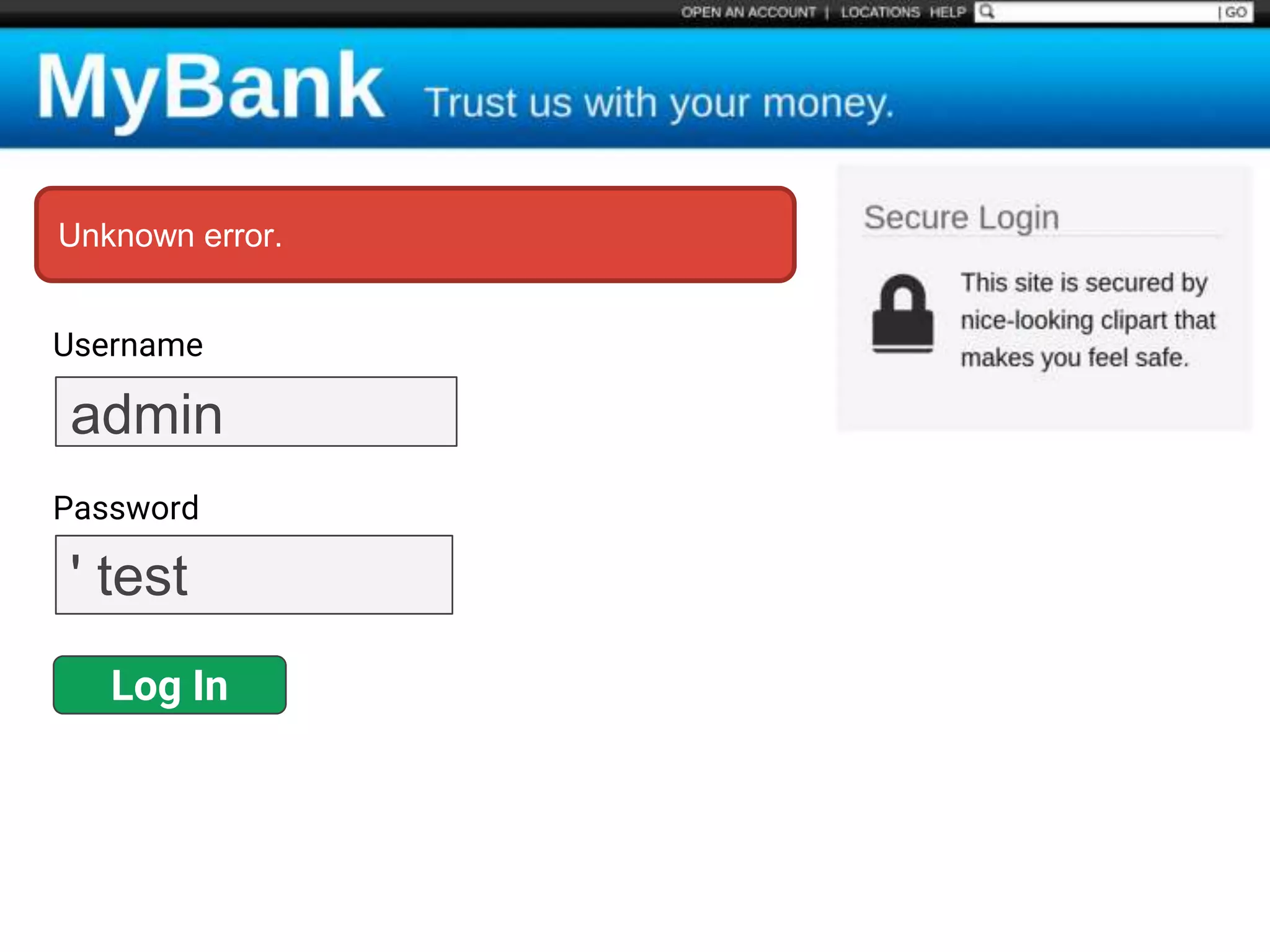
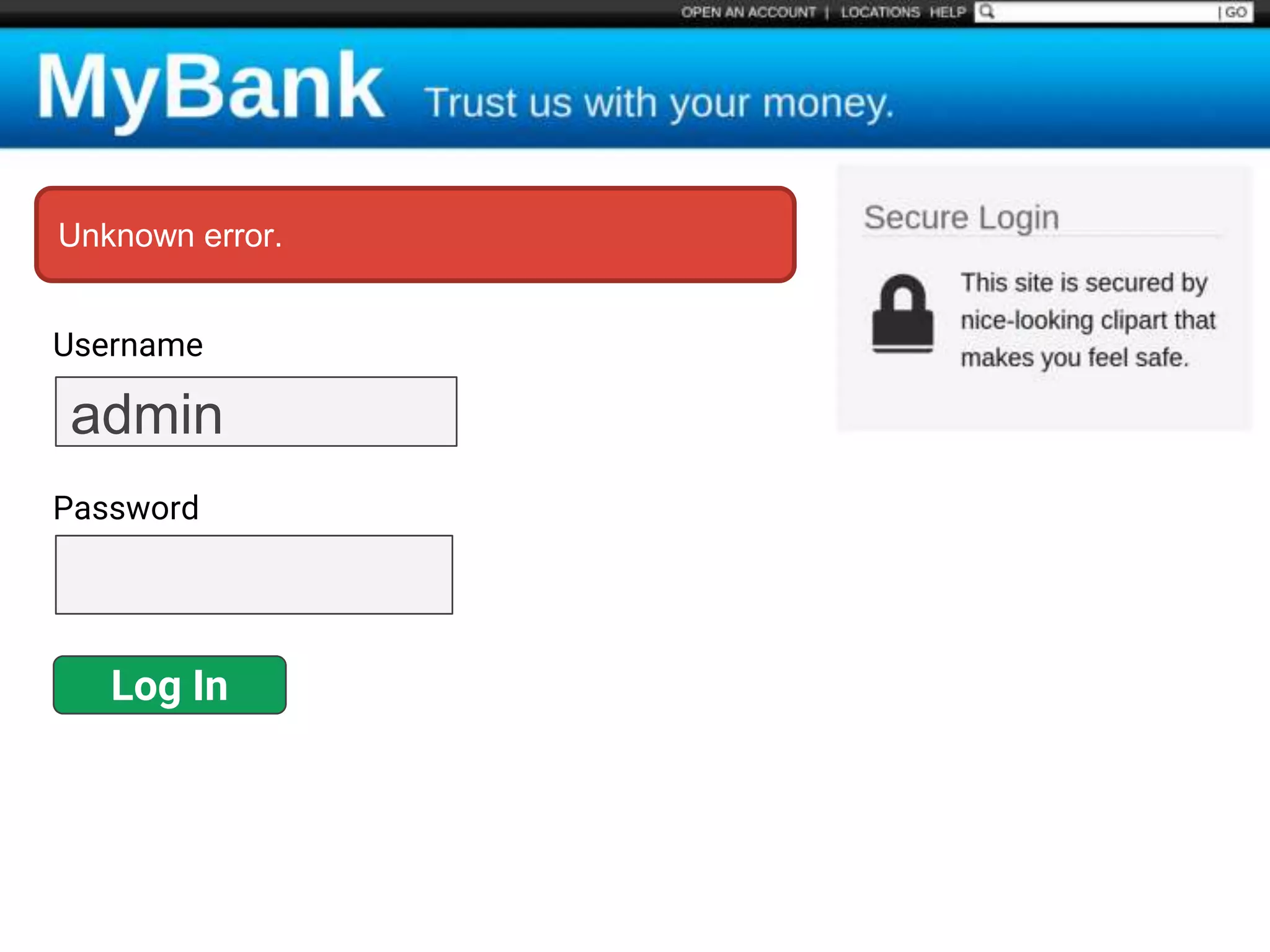
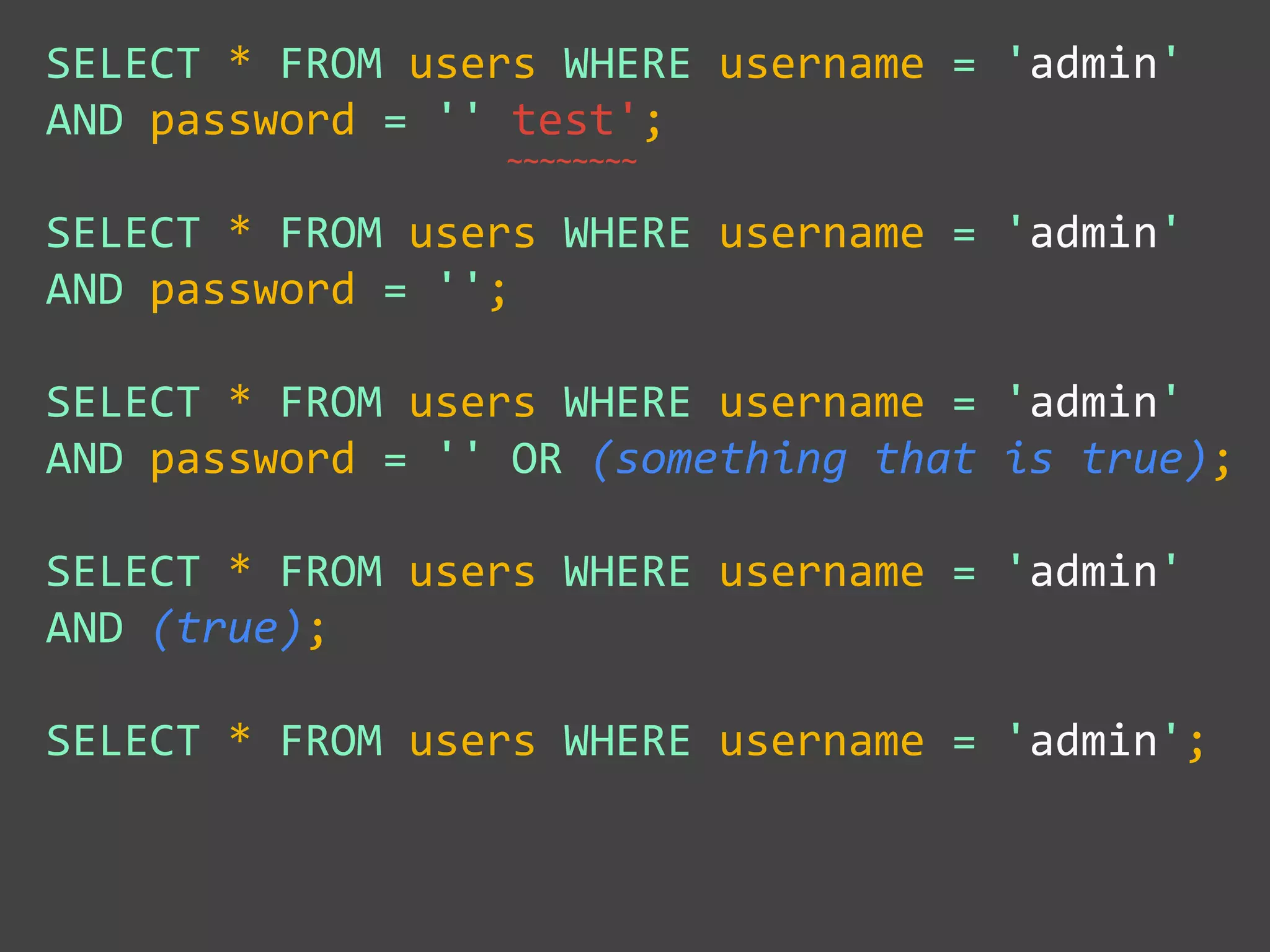
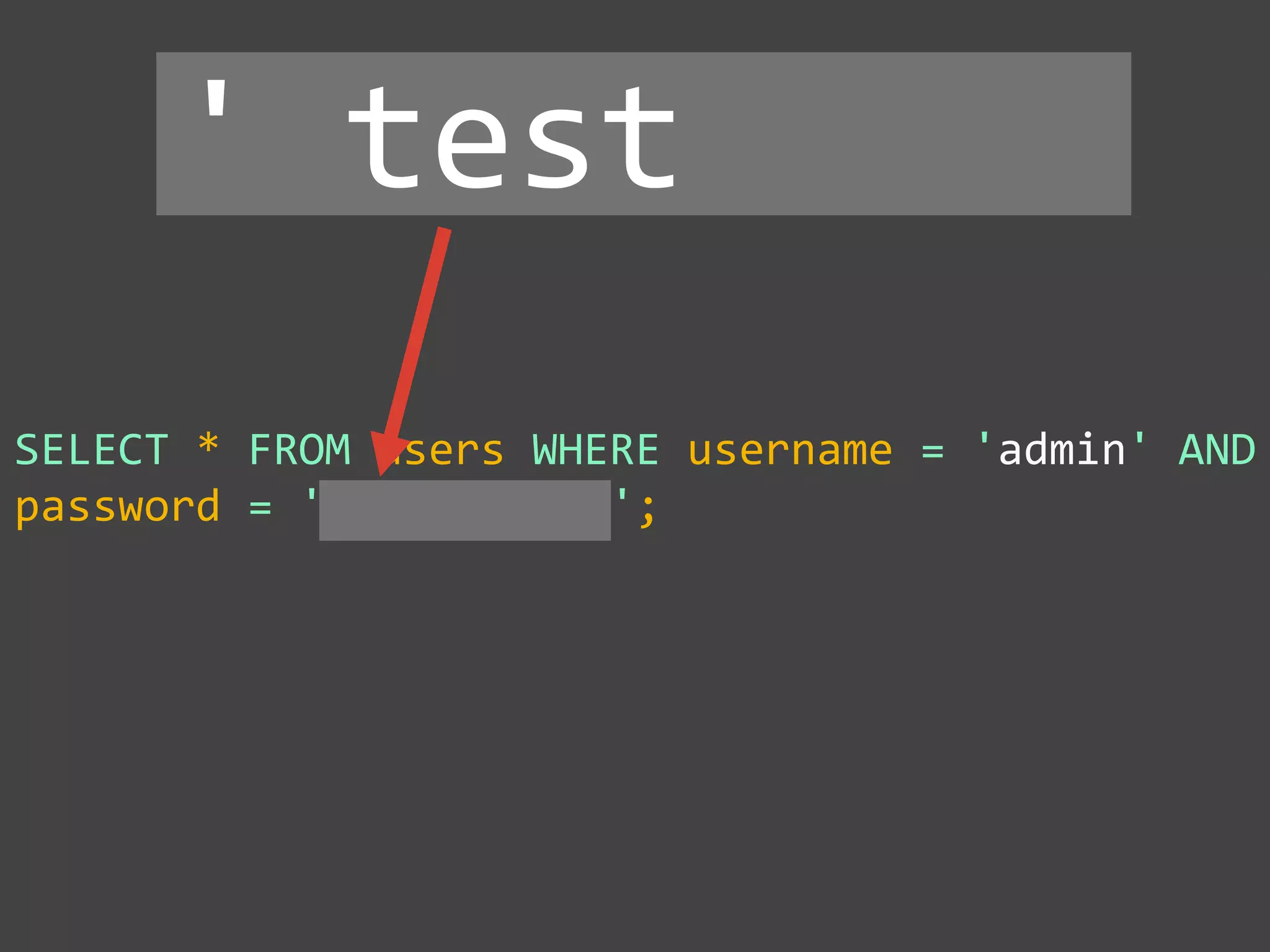
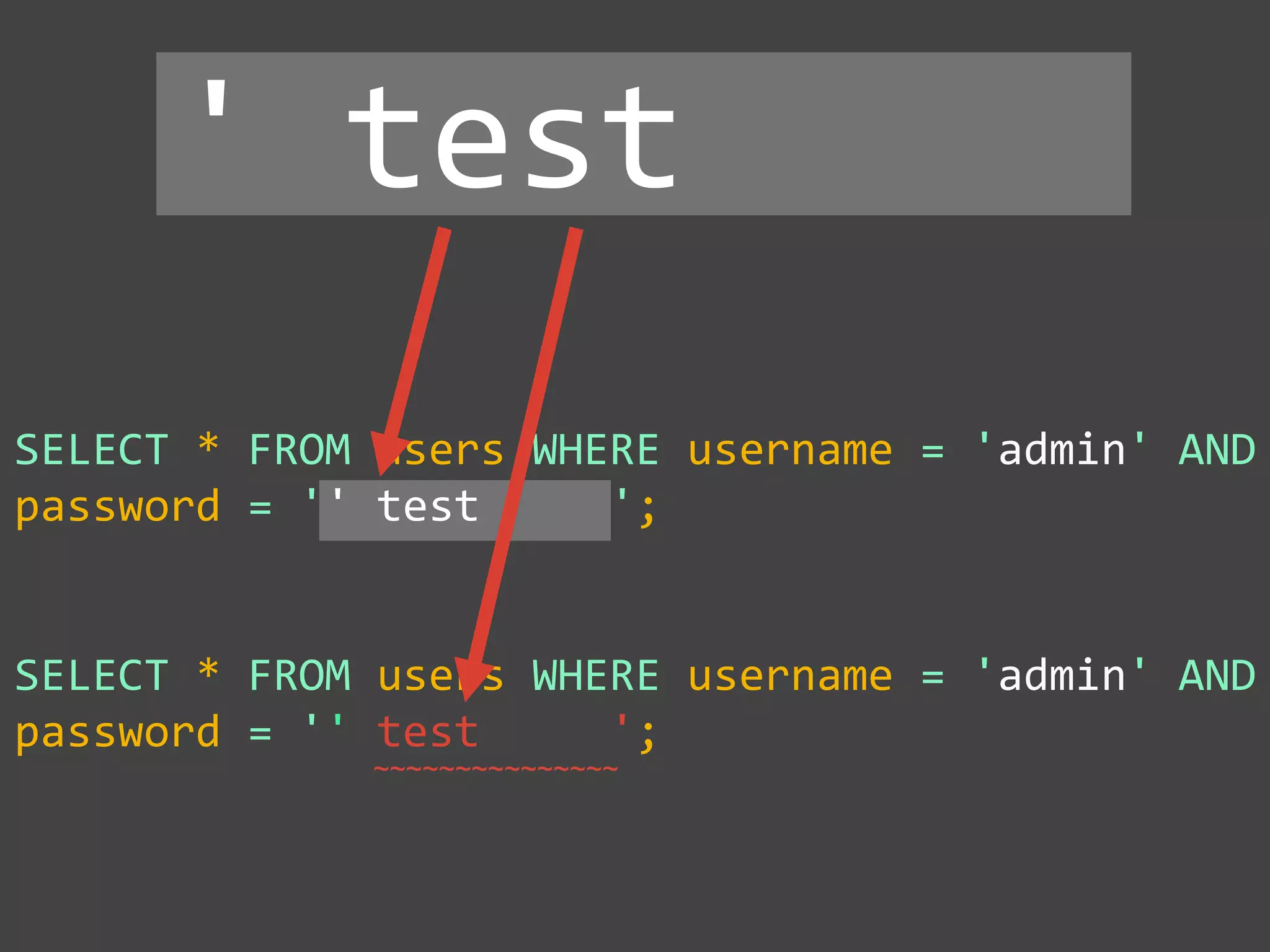
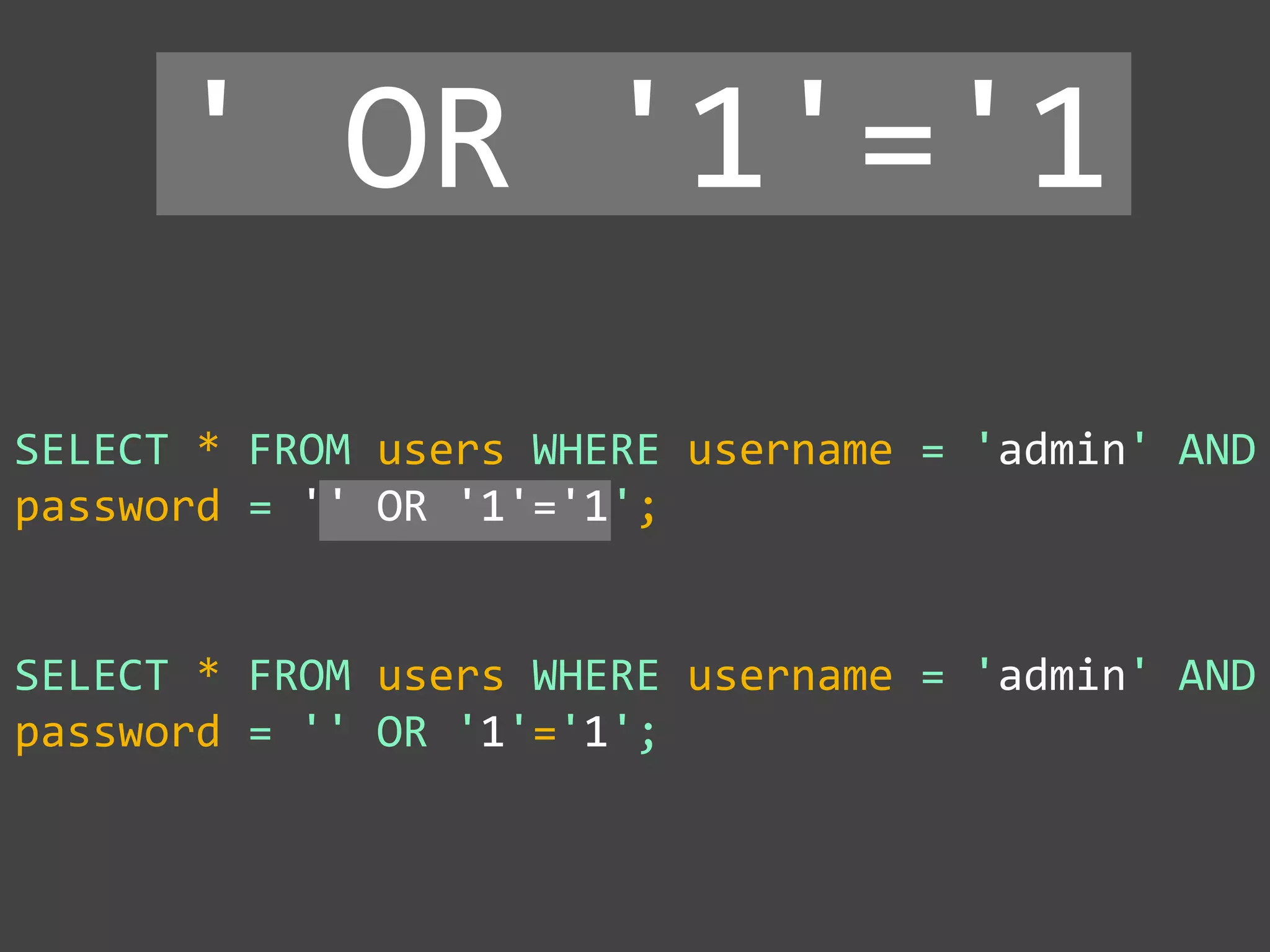
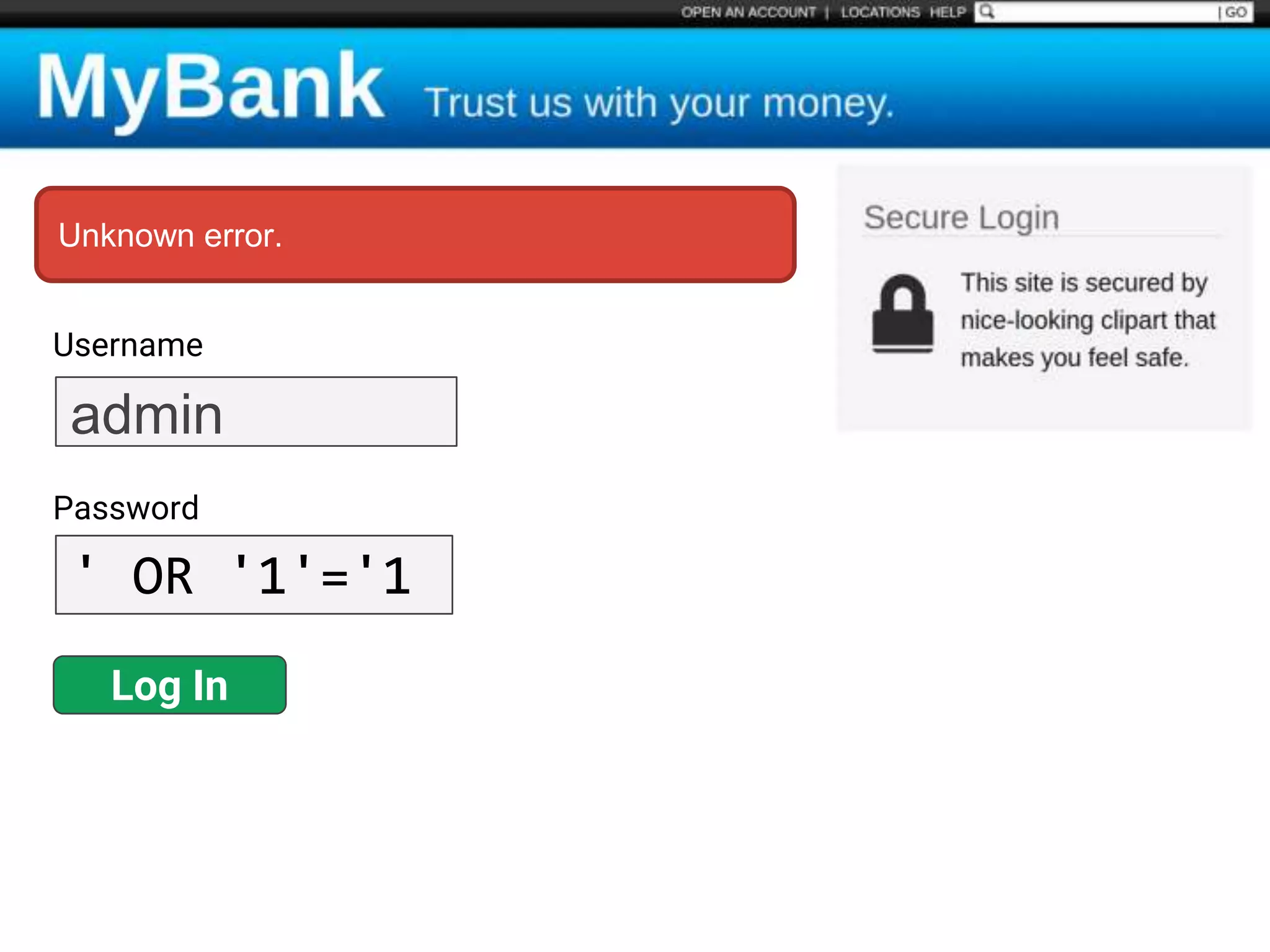
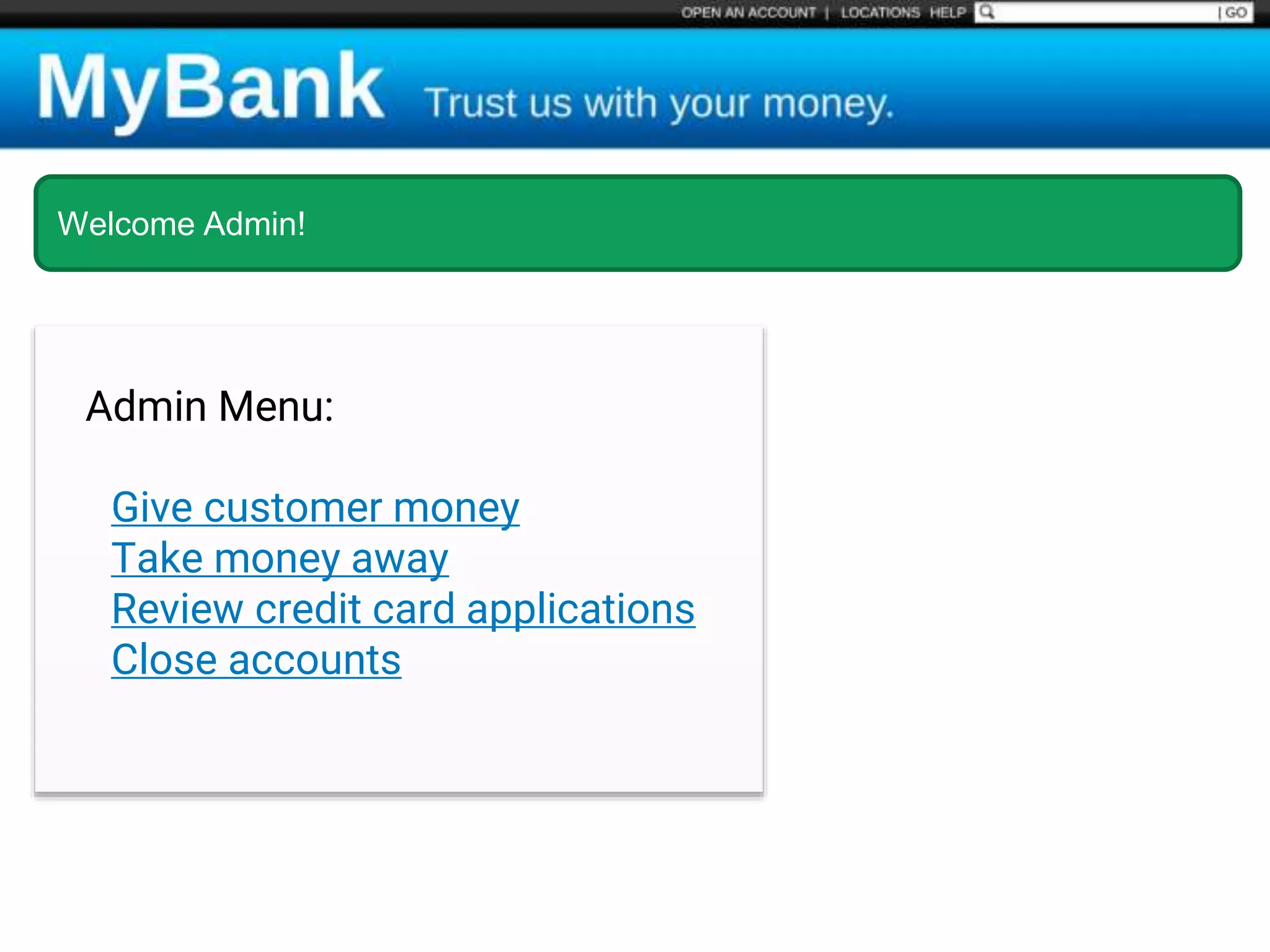

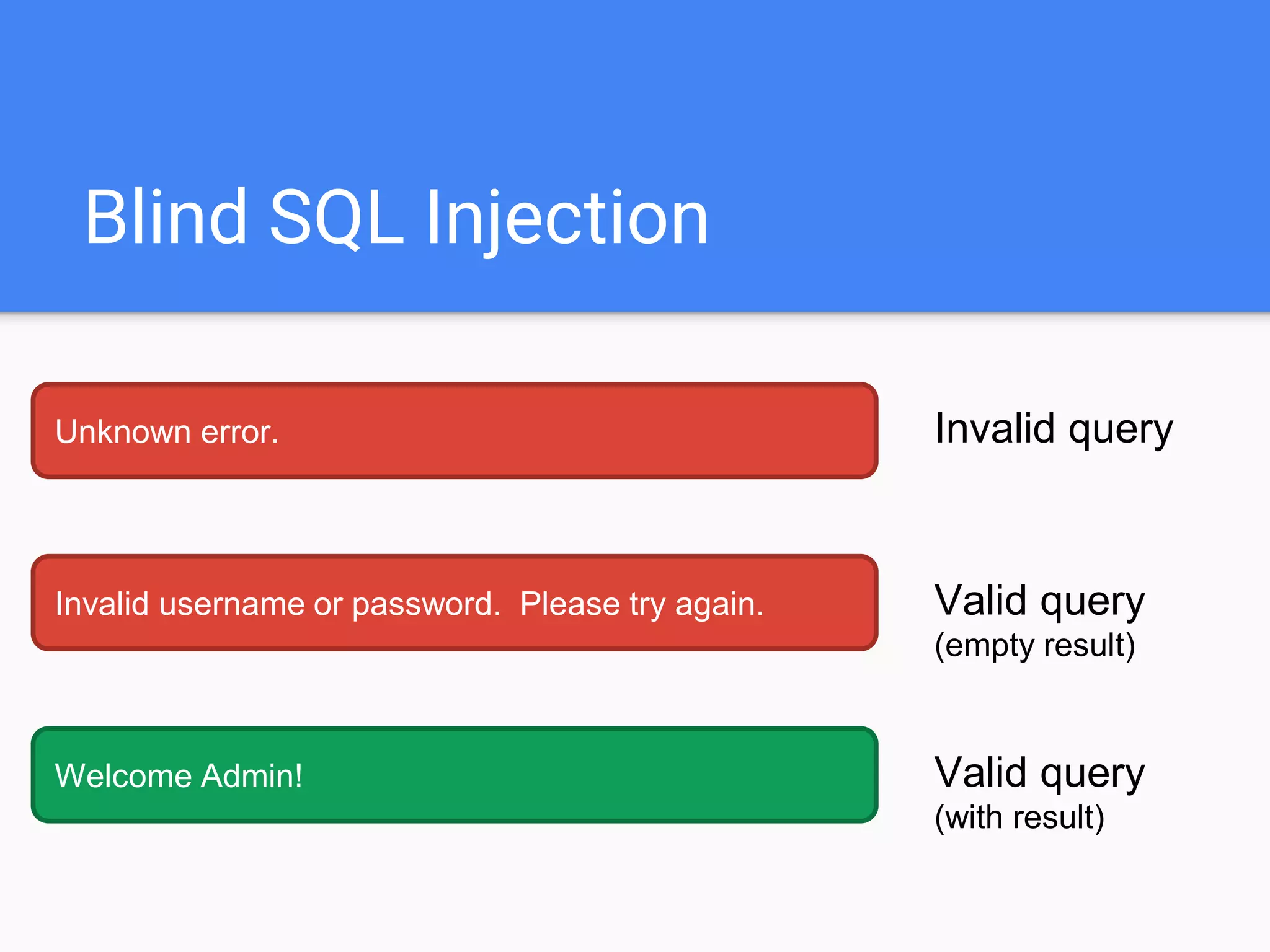
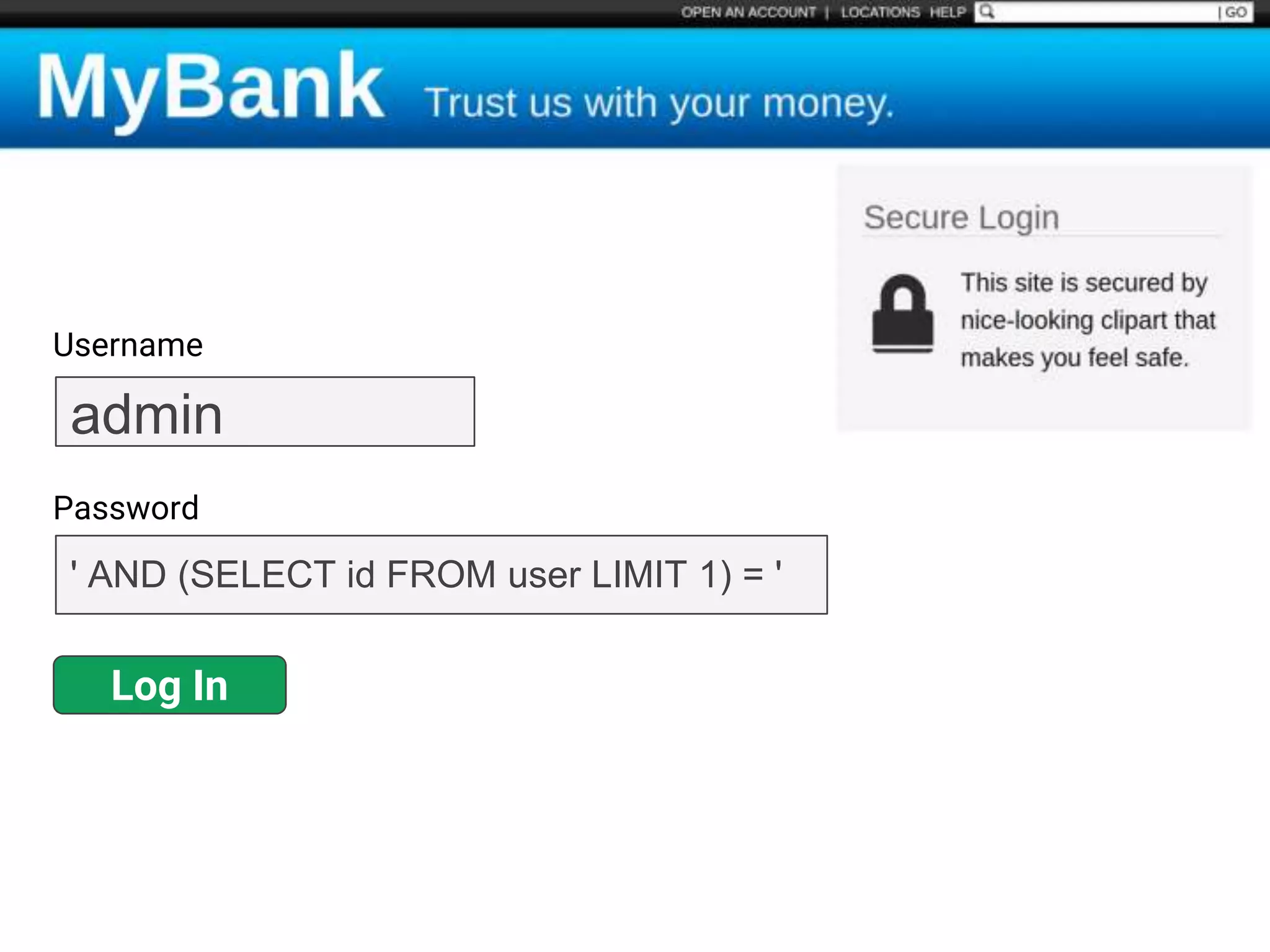
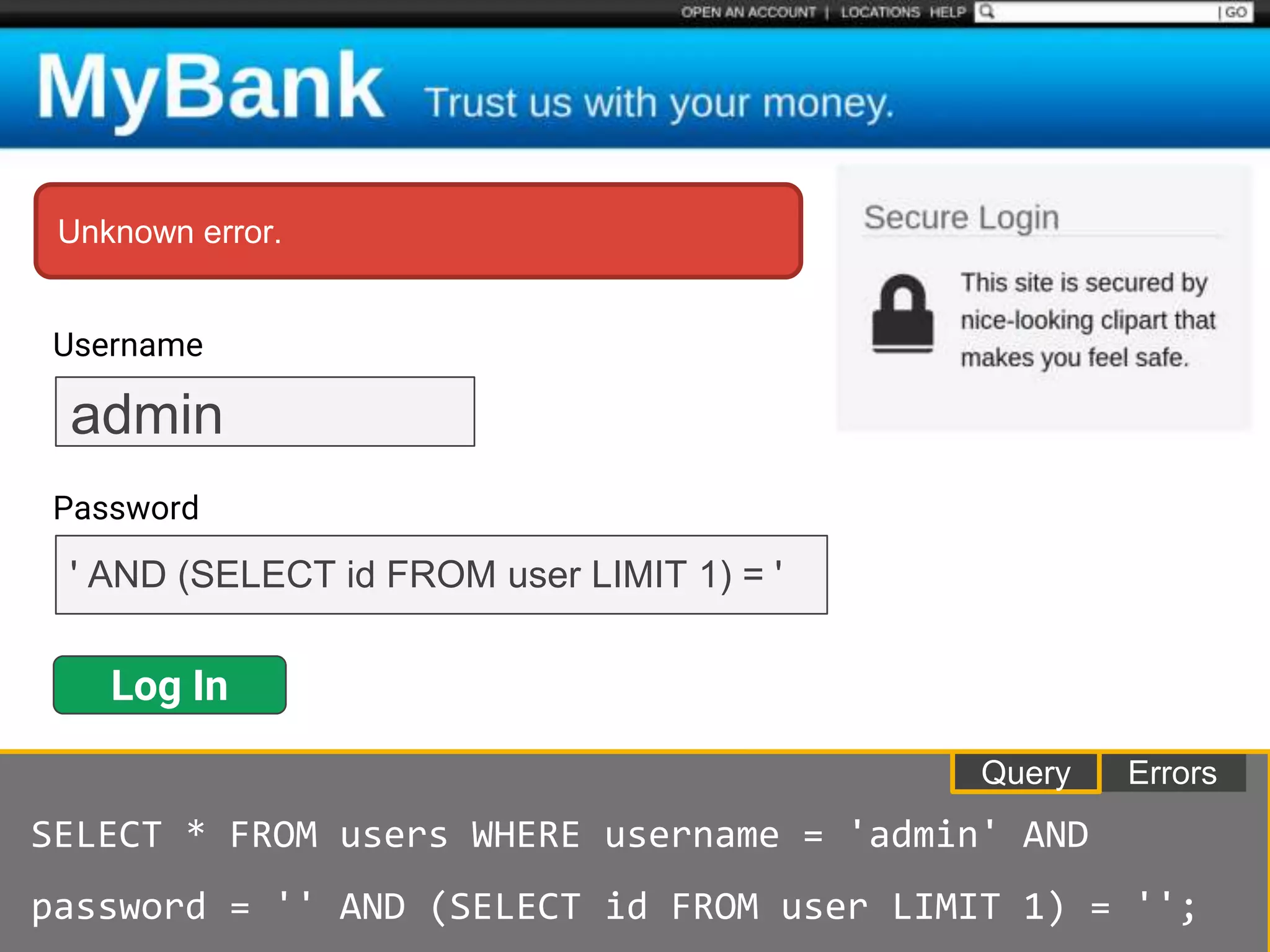
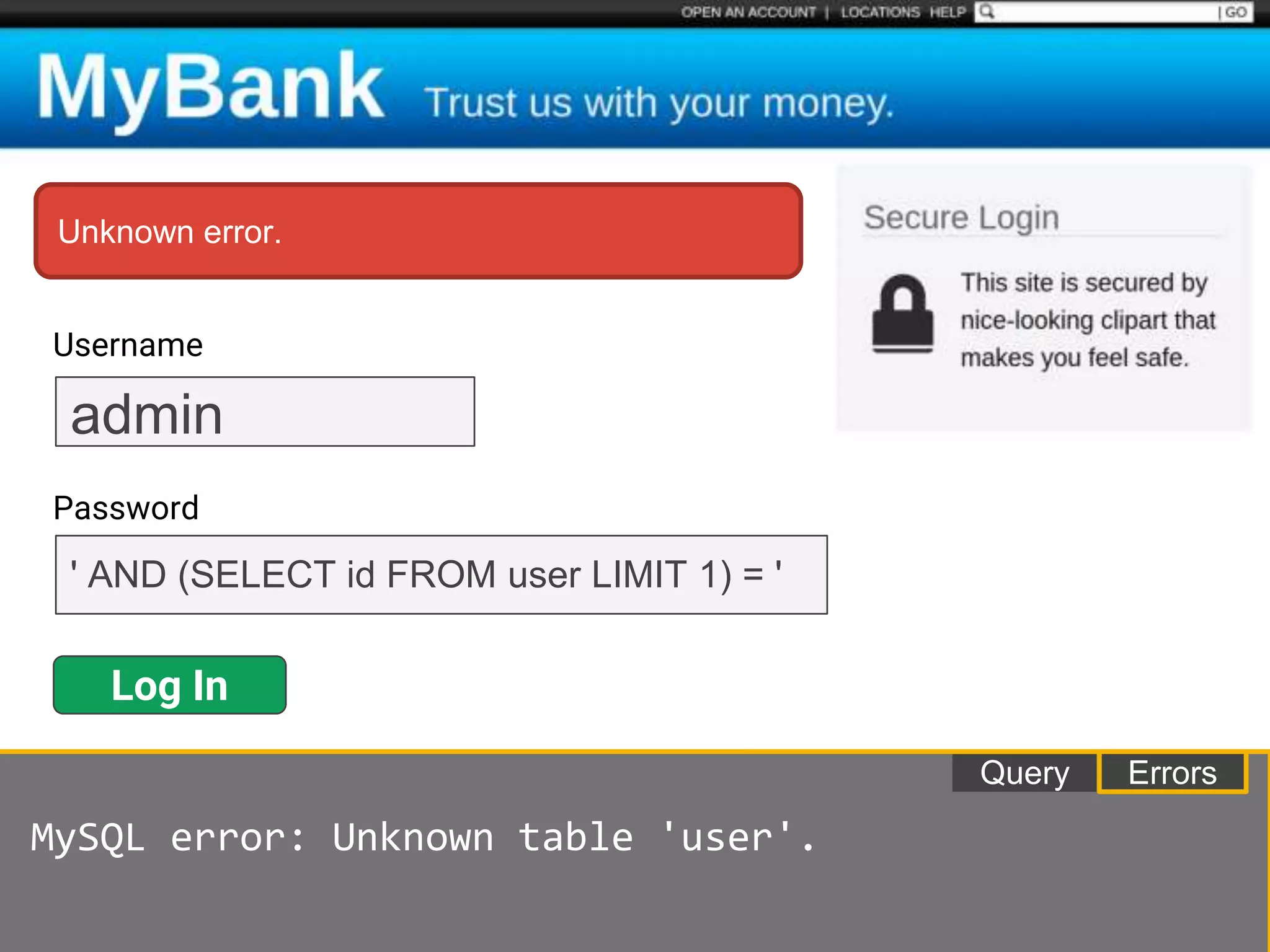
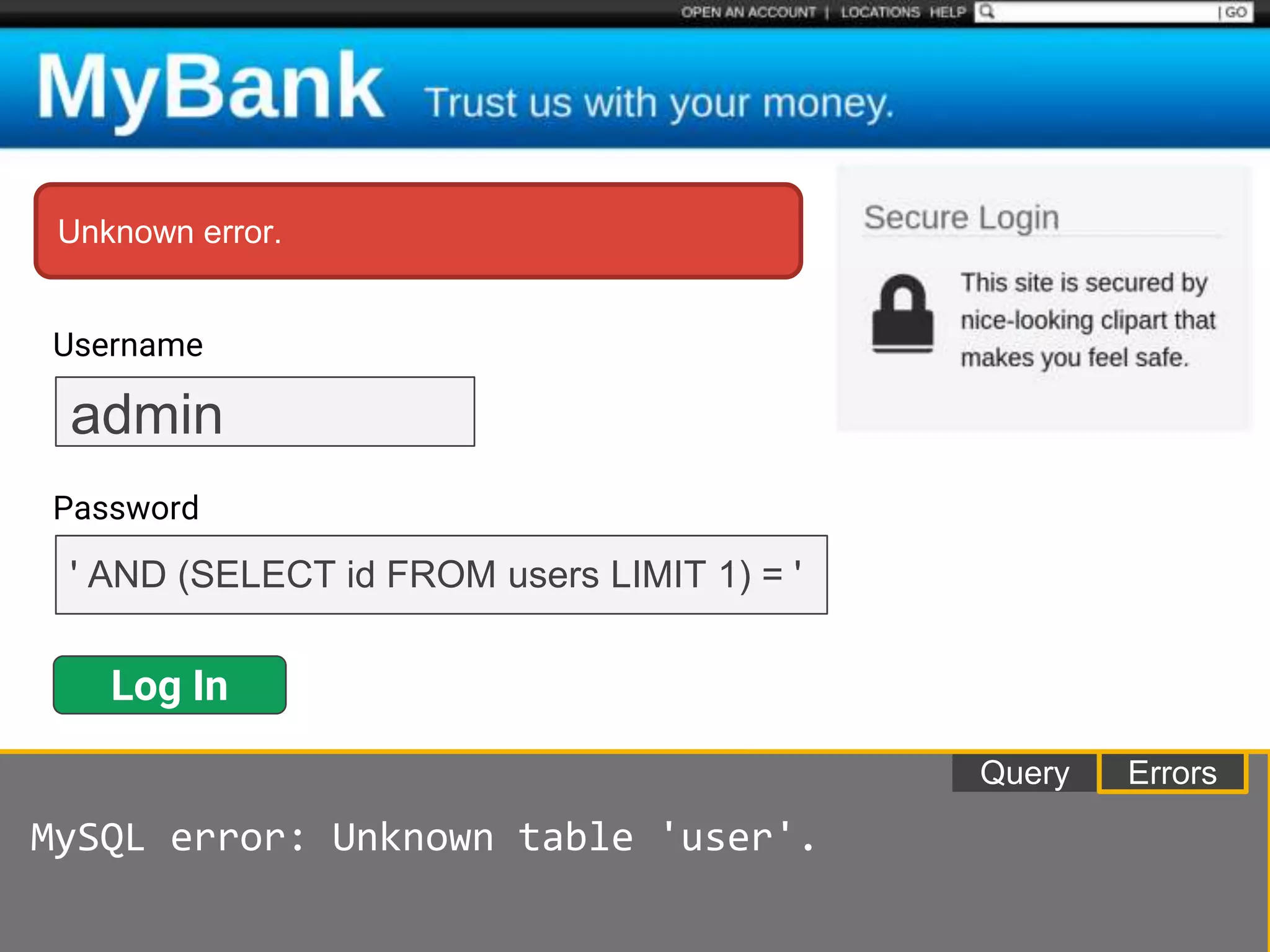
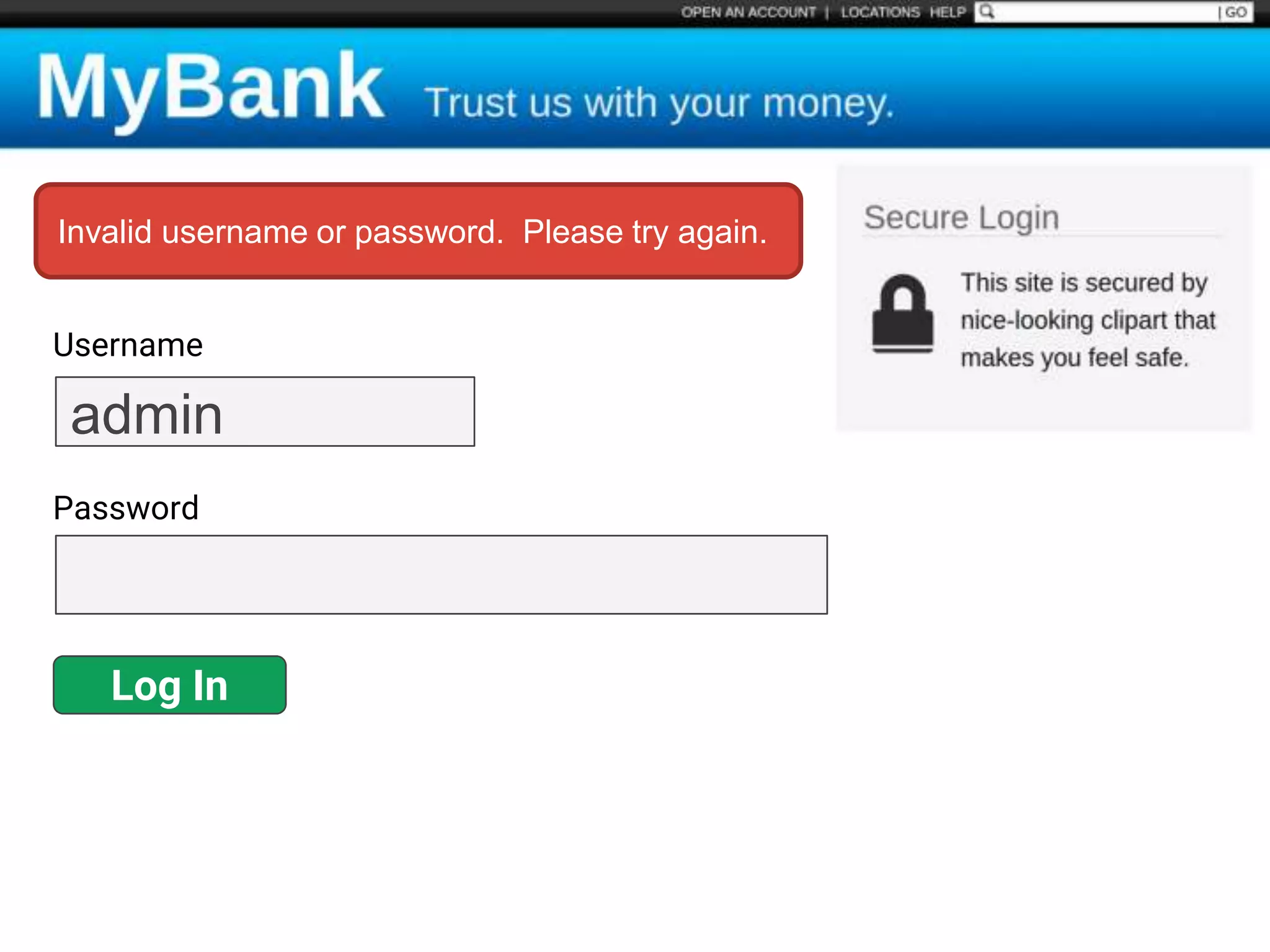

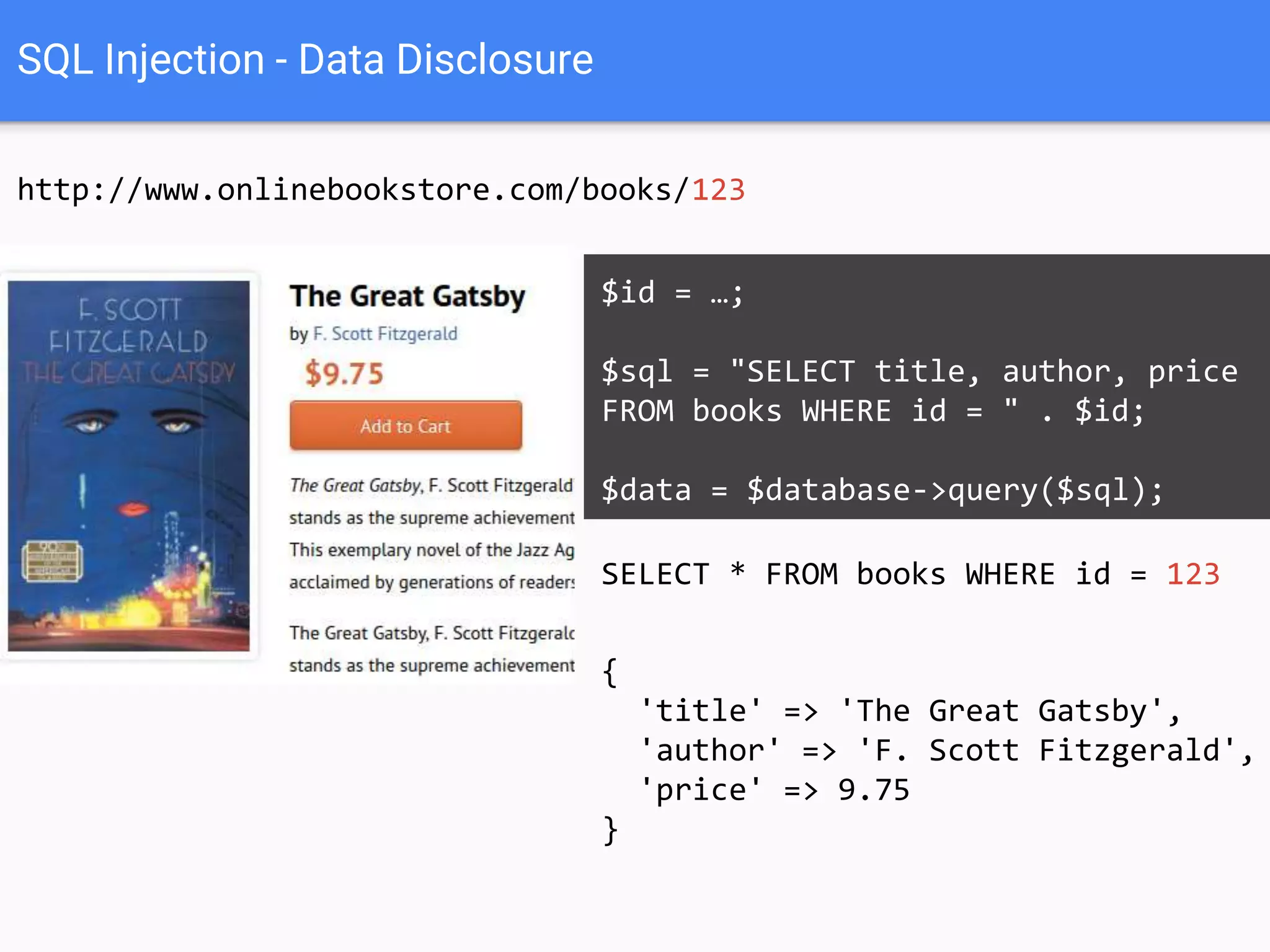
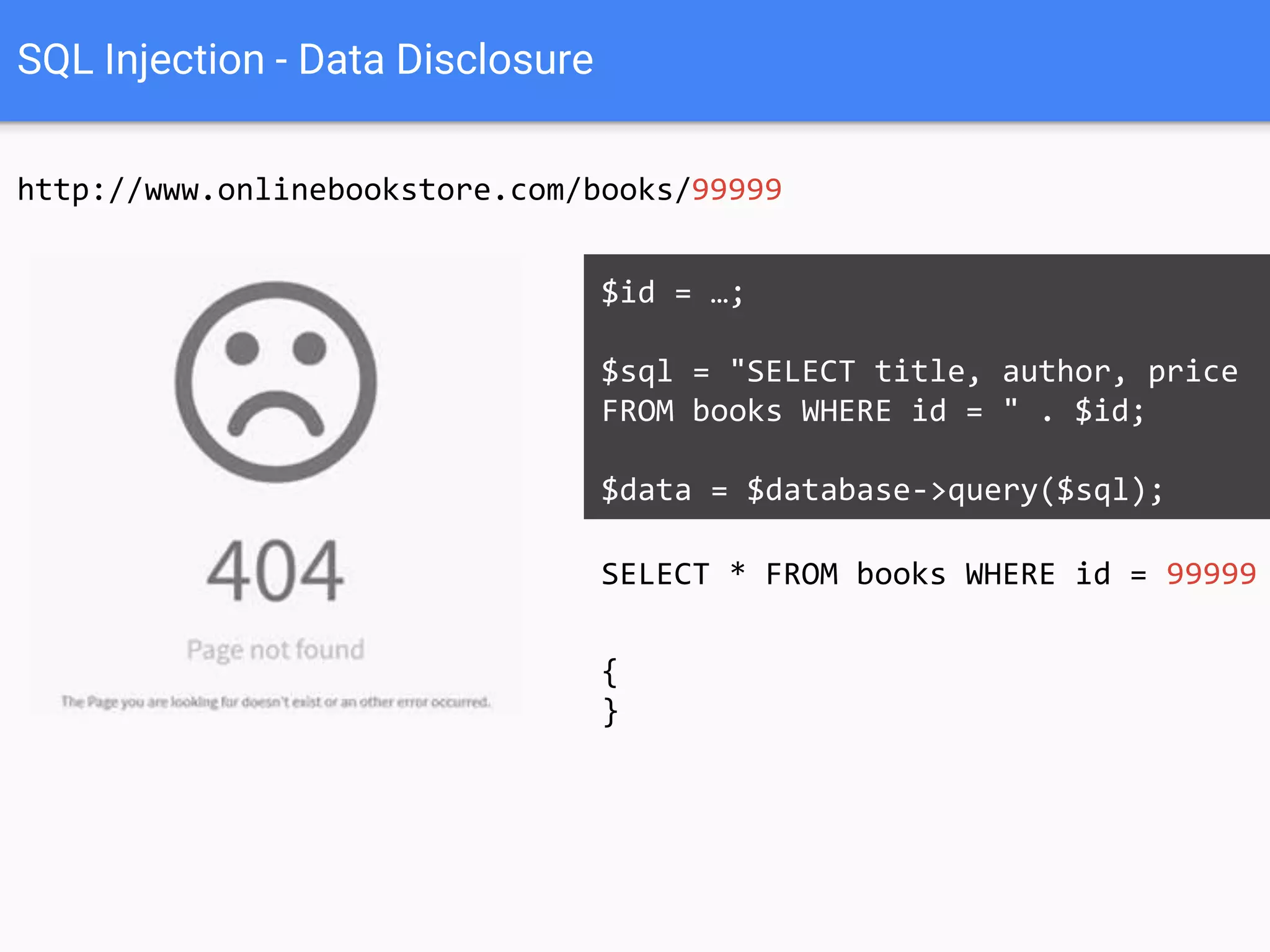
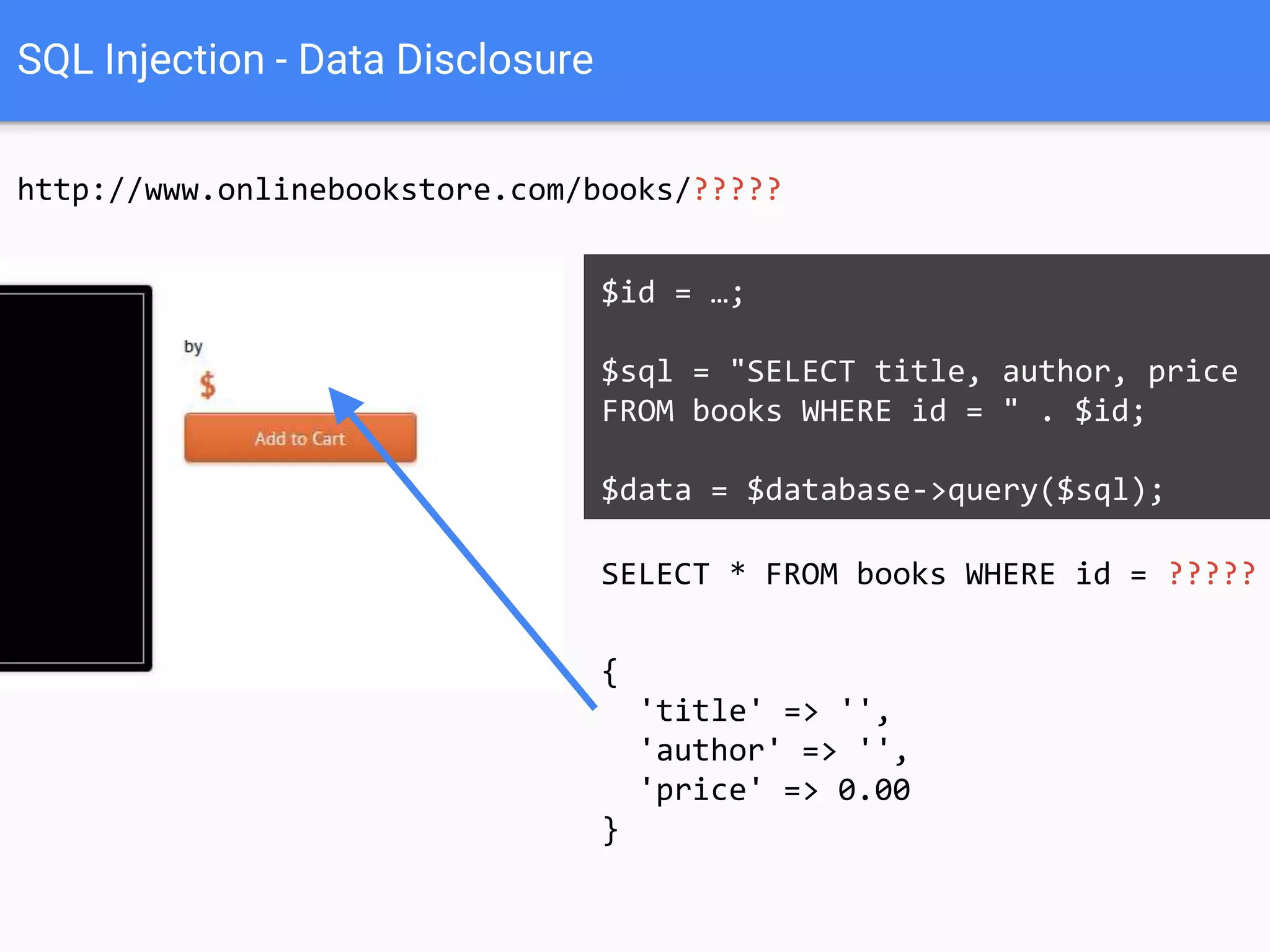
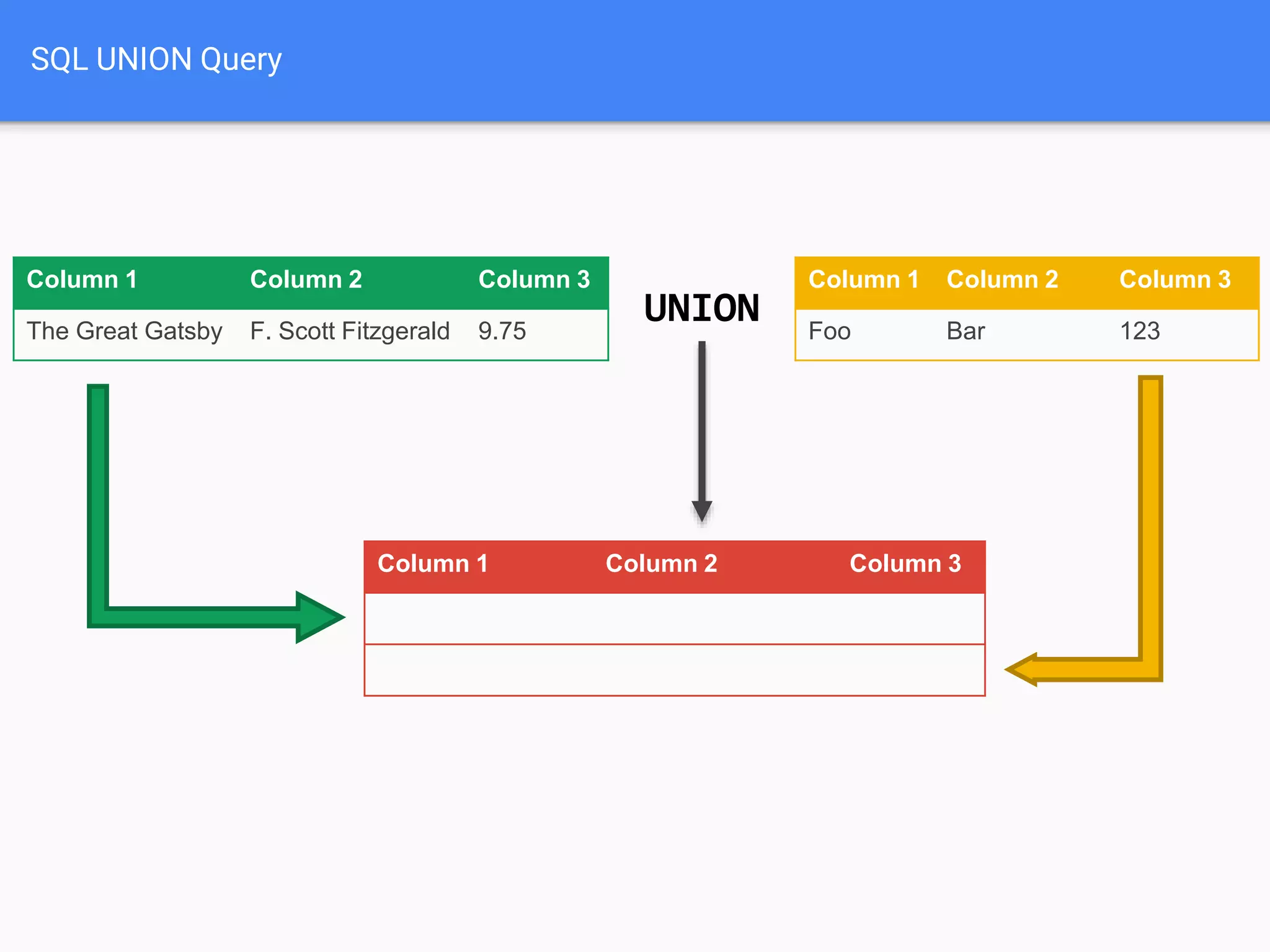
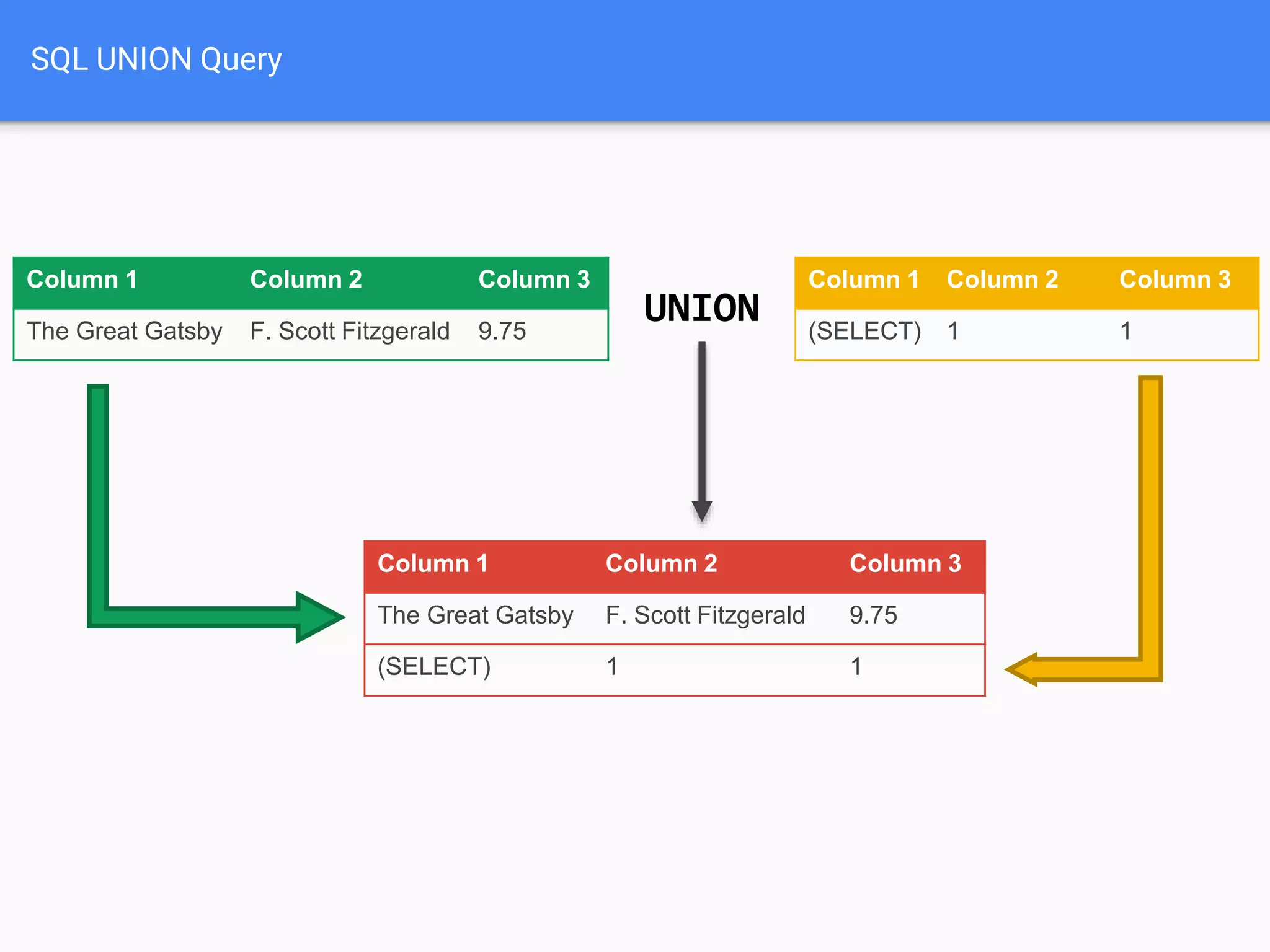
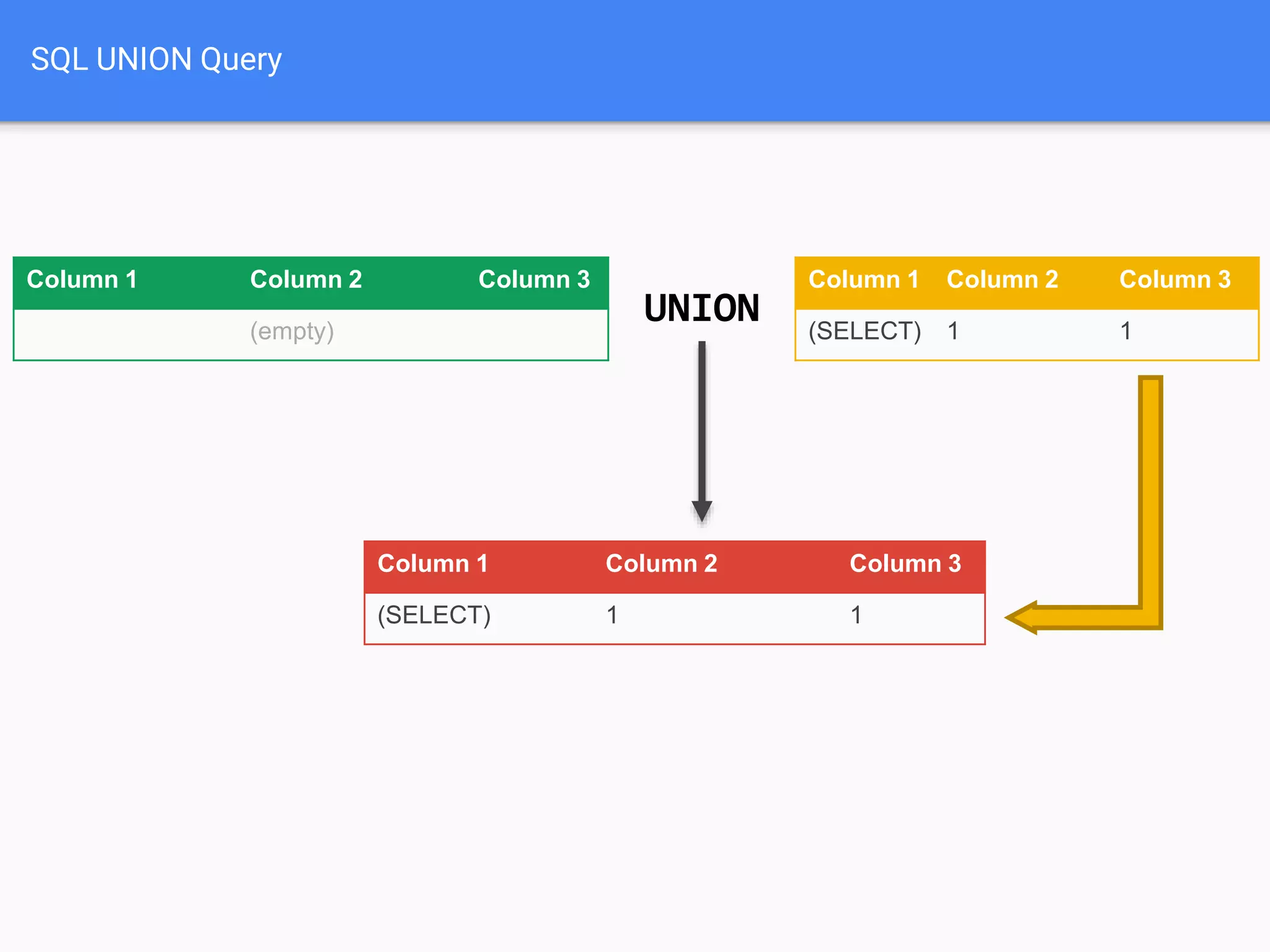
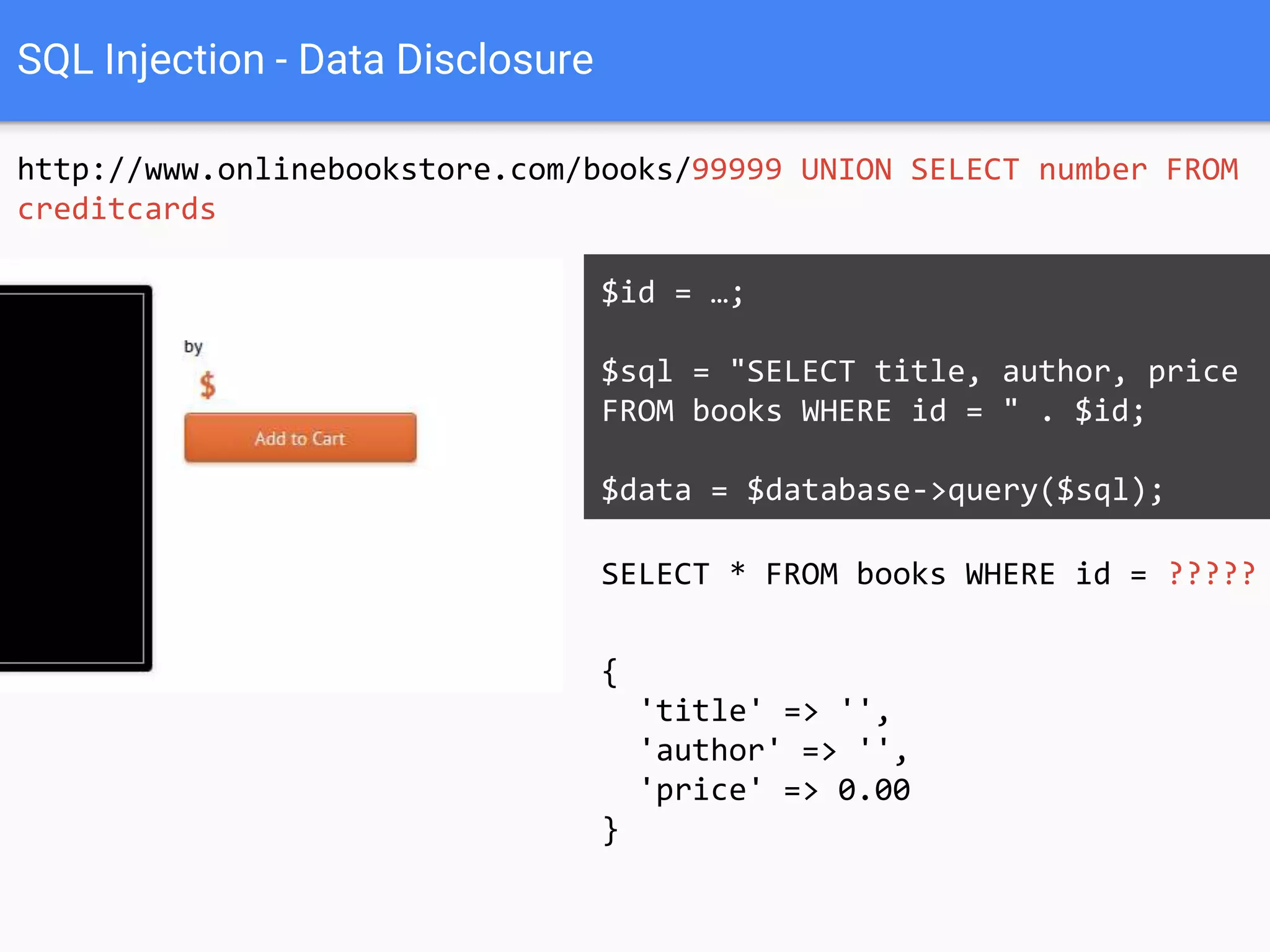
![$val = $_REQUEST['value'];
$sql = "SELECT * FROM x WHERE y = '$val' ";
$database->query($sql);
Protecting Against
SQL Injection
Block input with special
characters](https://image.slidesharecdn.com/gebhbkmwtryrodvbids0-signature-1b1295ff8d4f63c926cc99fe490d9488deb80d97cdf6a4560e5eb93d780d82cd-poli-160624212034/75/Hacking-Your-Way-To-Better-Security-Dutch-PHP-Conference-2016-48-2048.jpg)
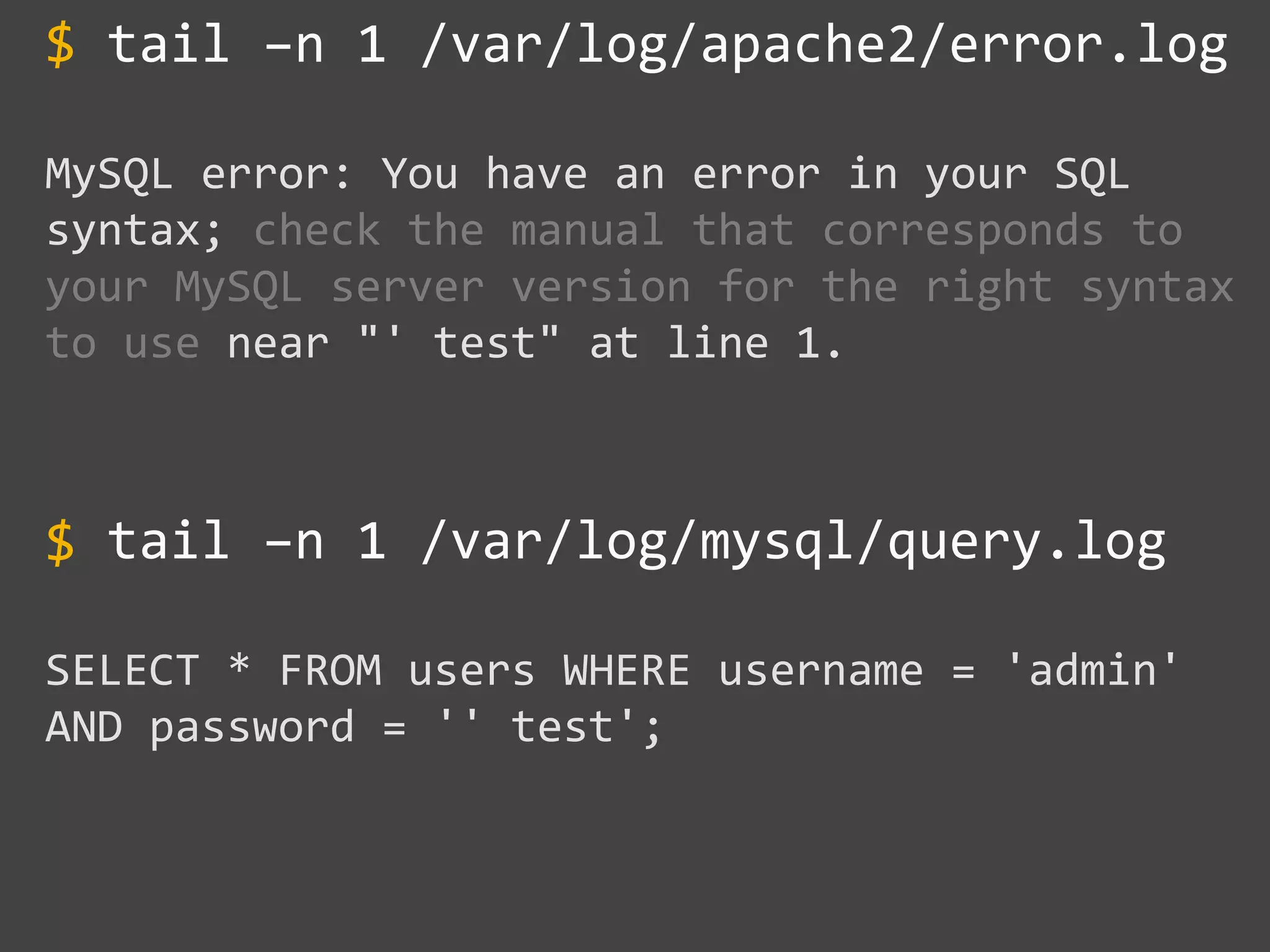
![Protecting Against
SQL Injection
Block input with special
characters
Escape user input
$value = $_REQUEST['value'];
$escaped = mysqli_real_escape_string($value);
$sql = "SELECT * FROM x WHERE y = '$escaped' ";
$database->query($sql);
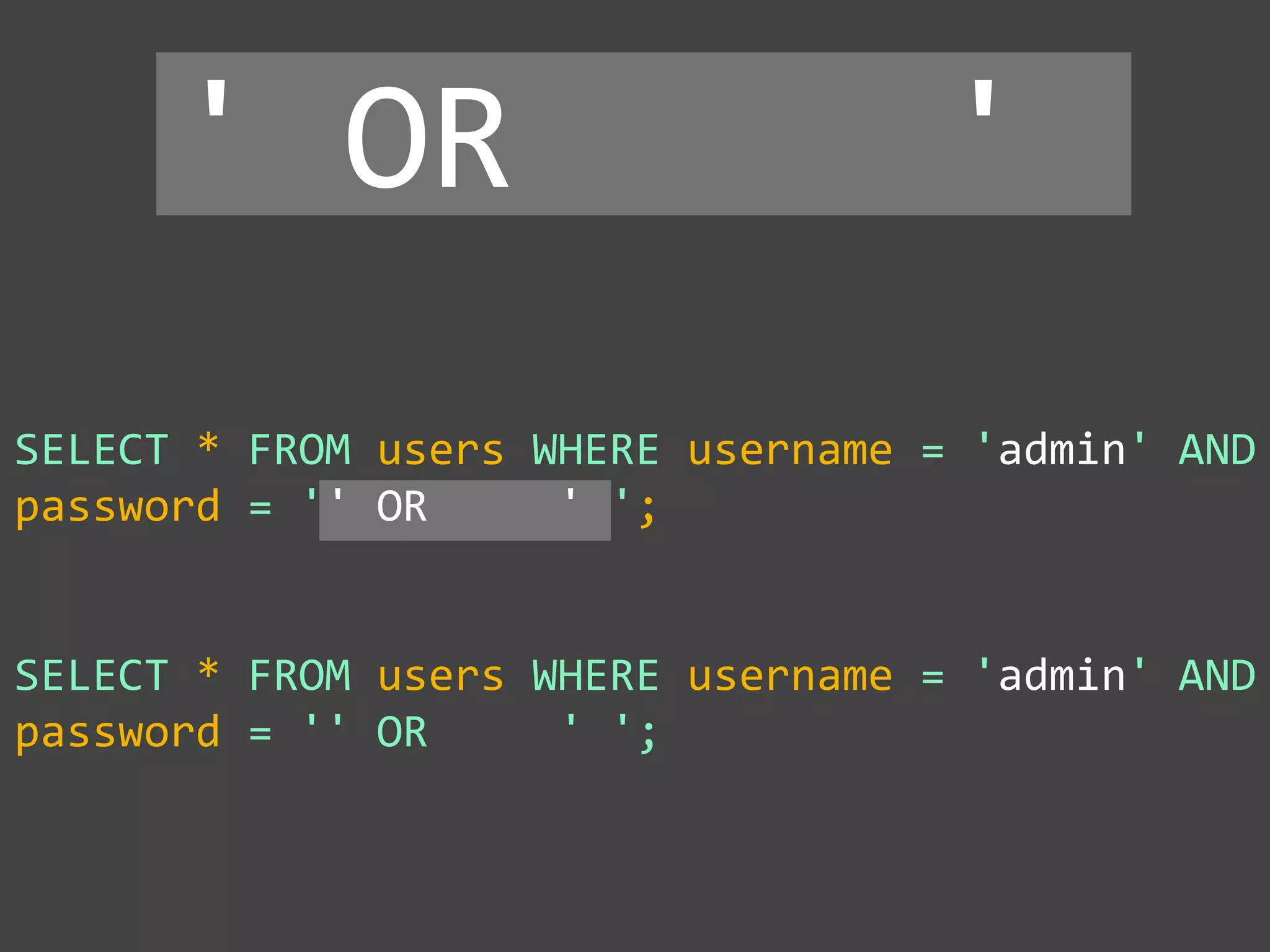
' OR '1' = '1 ' OR '1' = '1
mysqli_real_escape_string()
SELECT * FROM x
WHERE y = '' OR '1' = '1'](https://image.slidesharecdn.com/gebhbkmwtryrodvbids0-signature-1b1295ff8d4f63c926cc99fe490d9488deb80d97cdf6a4560e5eb93d780d82cd-poli-160624212034/75/Hacking-Your-Way-To-Better-Security-Dutch-PHP-Conference-2016-49-2048.jpg)
![Protecting Against
SQL Injection
Block input with special
characters
Escape user input
$value = $_REQUEST['value'];
$escaped = mysqli_real_escape_string($value);
$sql = "SELECT * FROM x WHERE y = '$escaped' ";
$database->query($sql);
' OR '1' = '1 ' OR '1' = '1
mysqli_real_escape_string()
SELECT * FROM x
WHERE y = '' OR '1' = '1'](https://image.slidesharecdn.com/gebhbkmwtryrodvbids0-signature-1b1295ff8d4f63c926cc99fe490d9488deb80d97cdf6a4560e5eb93d780d82cd-poli-160624212034/75/Hacking-Your-Way-To-Better-Security-Dutch-PHP-Conference-2016-50-2048.jpg)
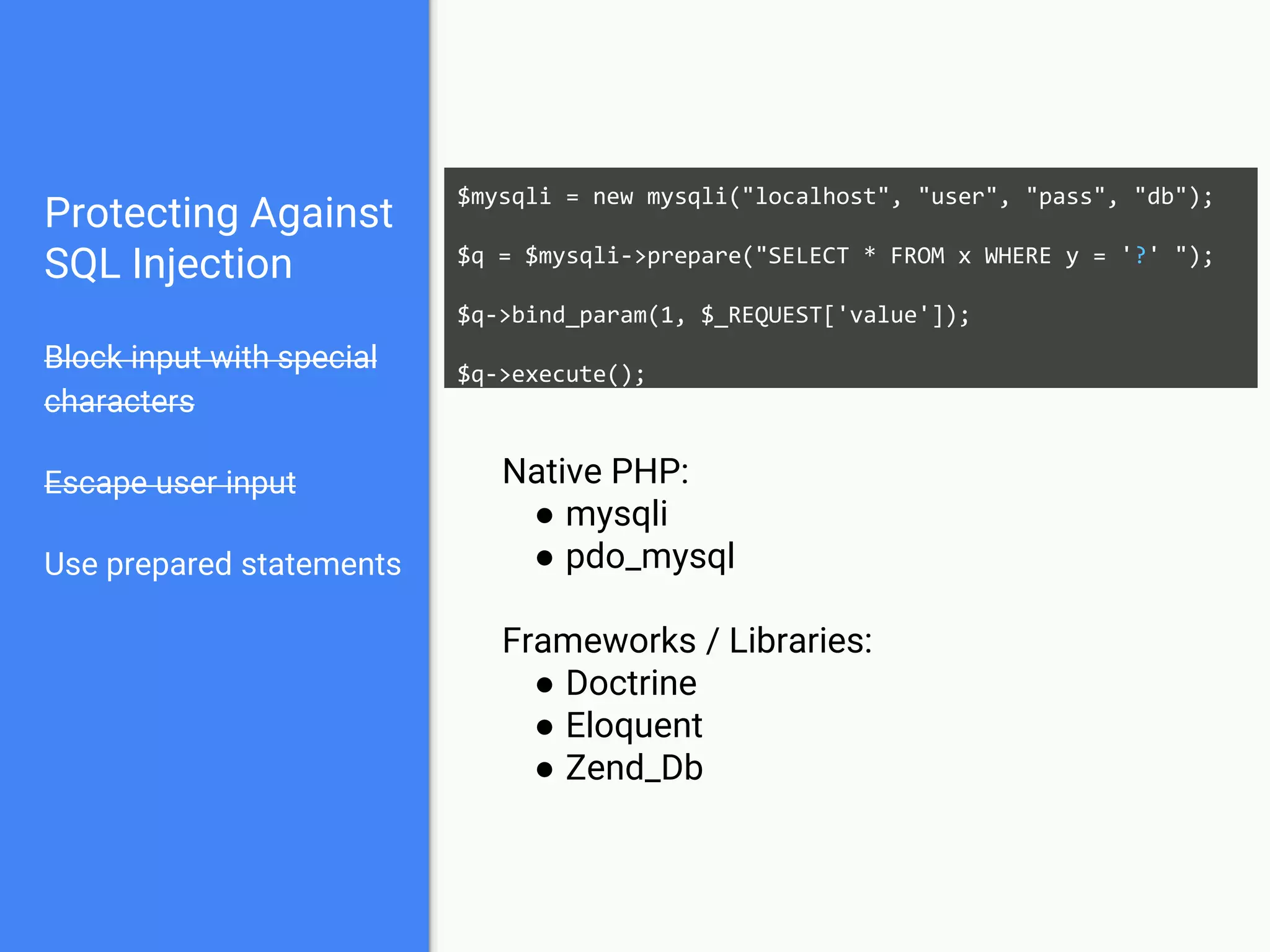
![Protecting Against
SQL Injection
Block input with special
characters
Escape user input
Use prepared statements
$mysqli = new mysqli("localhost", "user", "pass", "db");
$q = $mysqli->prepare("SELECT * FROM x WHERE y = '?' ");
$q->bind_param(1, $_REQUEST['value']);
$q->execute();
Native PHP:
● mysqli
● pdo_mysql
Frameworks / Libraries:
● Doctrine
● Eloquent
● Zend_Db](https://image.slidesharecdn.com/gebhbkmwtryrodvbids0-signature-1b1295ff8d4f63c926cc99fe490d9488deb80d97cdf6a4560e5eb93d780d82cd-poli-160624212034/75/Hacking-Your-Way-To-Better-Security-Dutch-PHP-Conference-2016-51-2048.jpg)
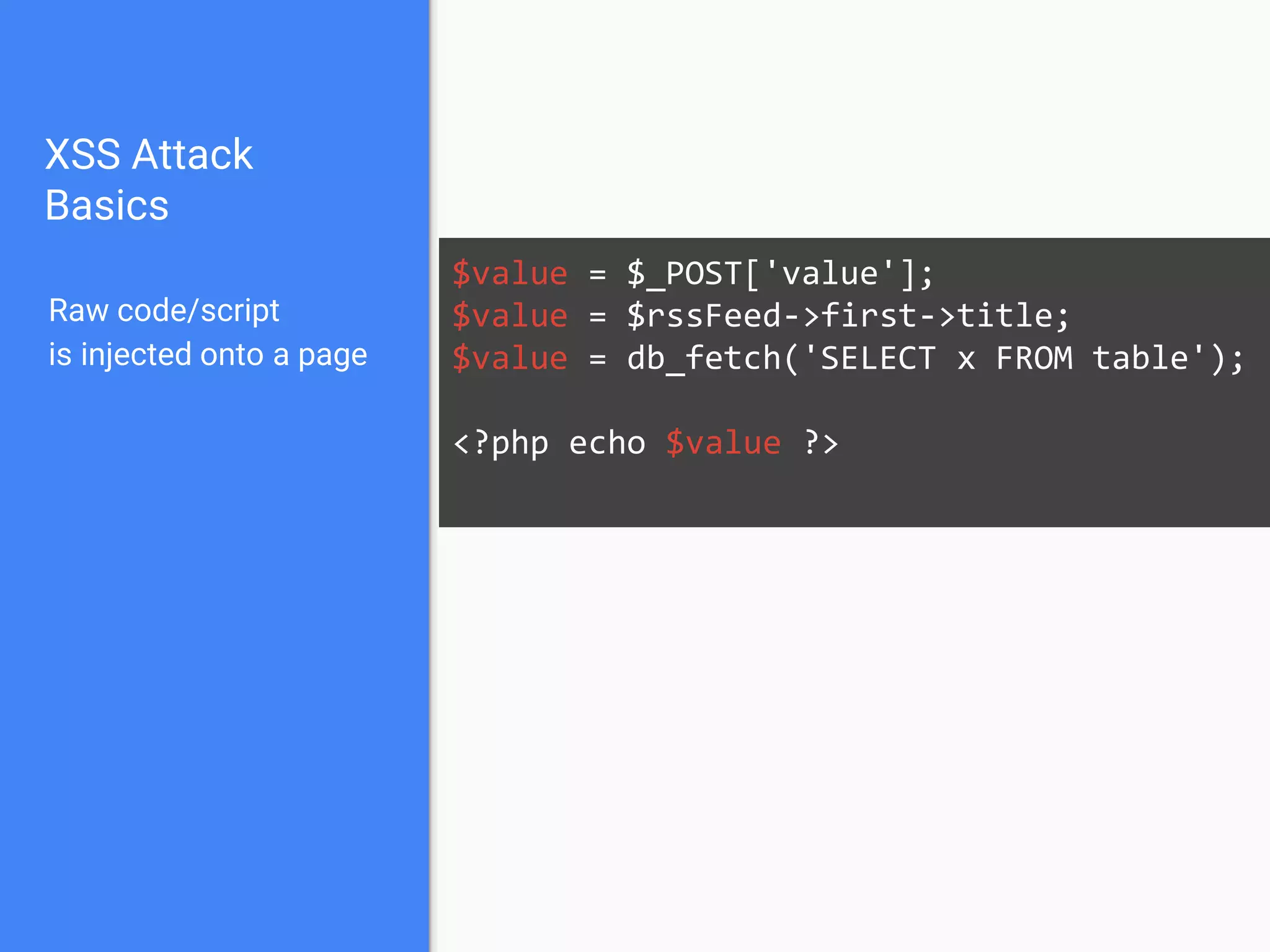
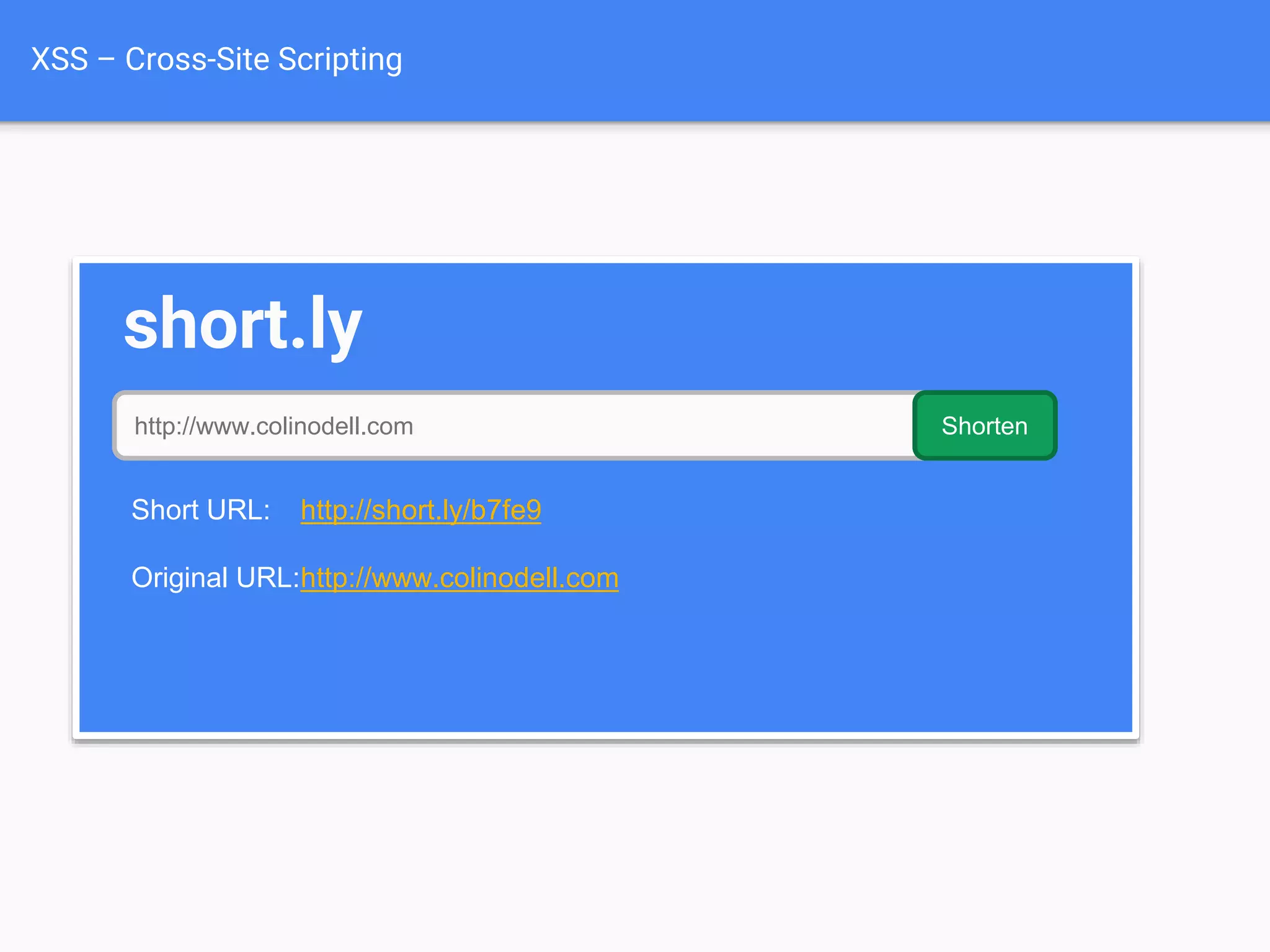
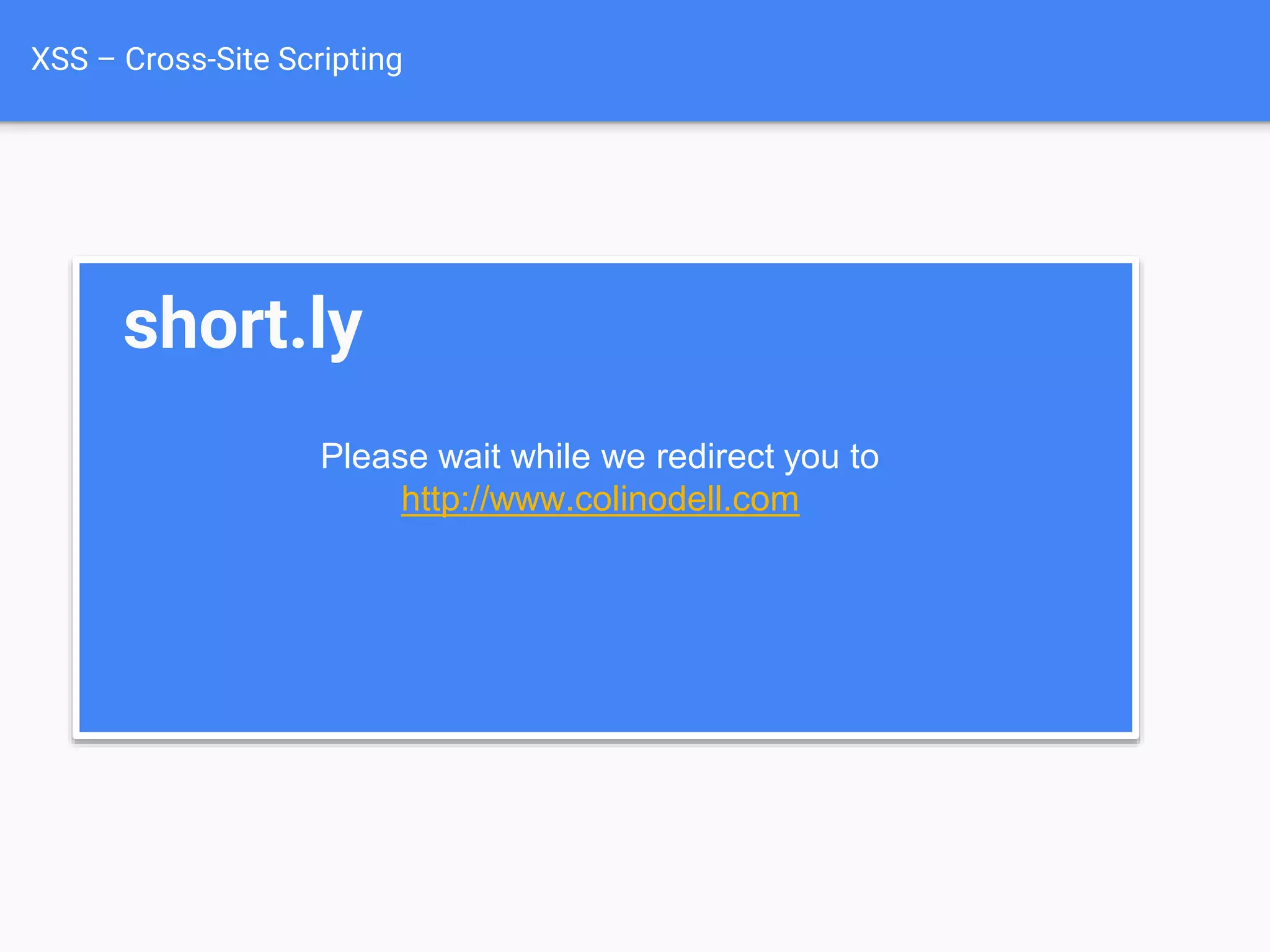
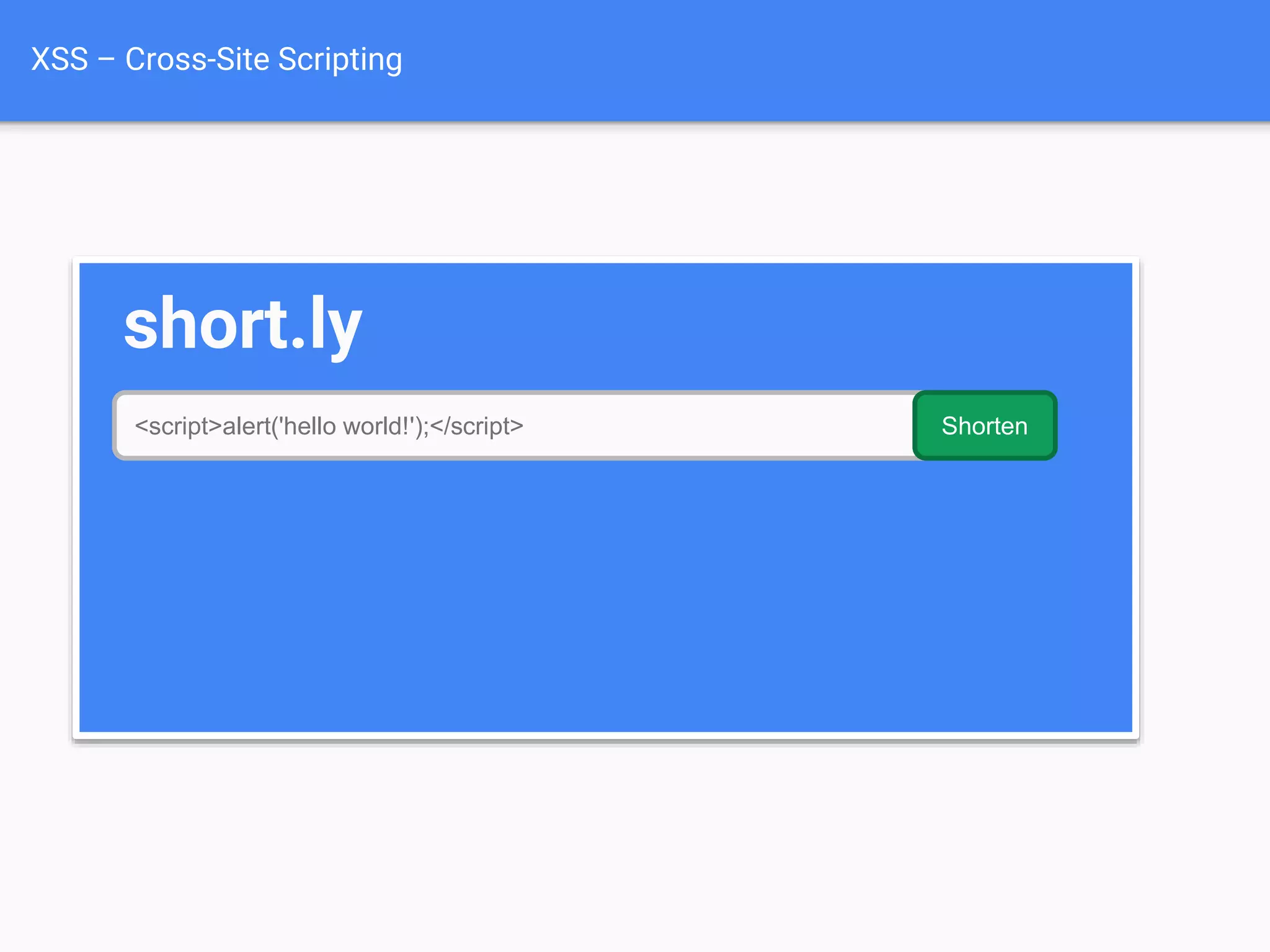
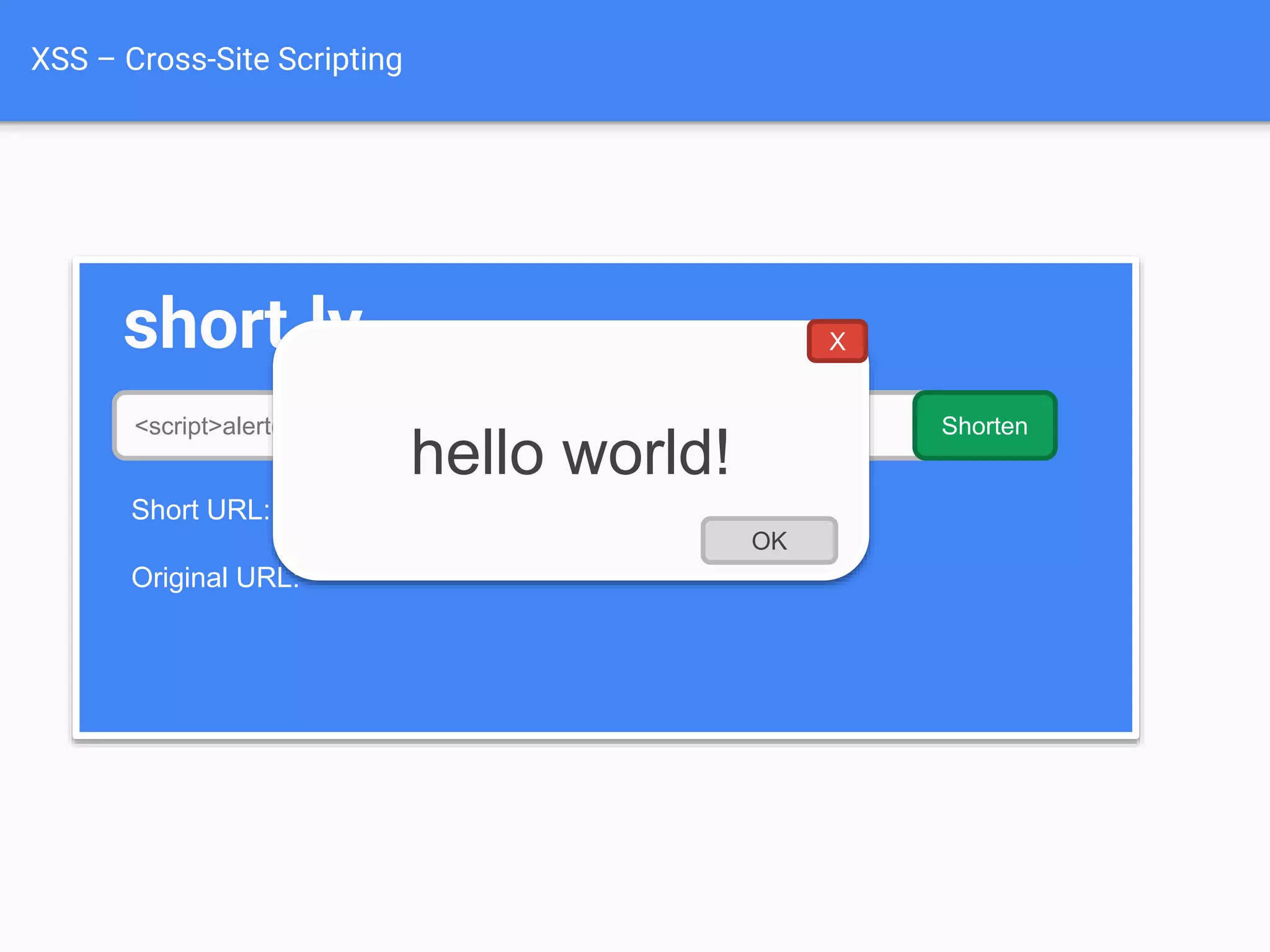
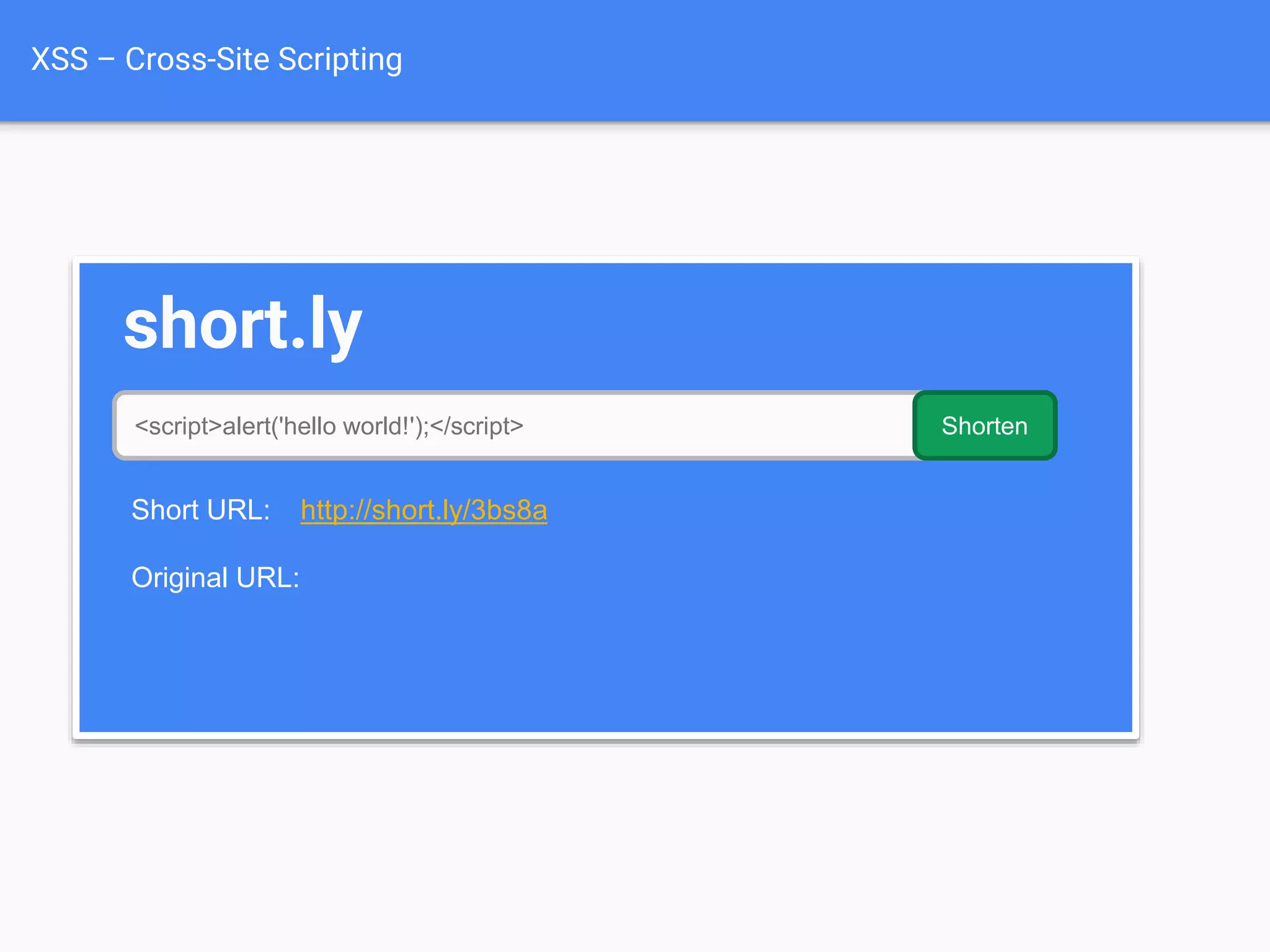
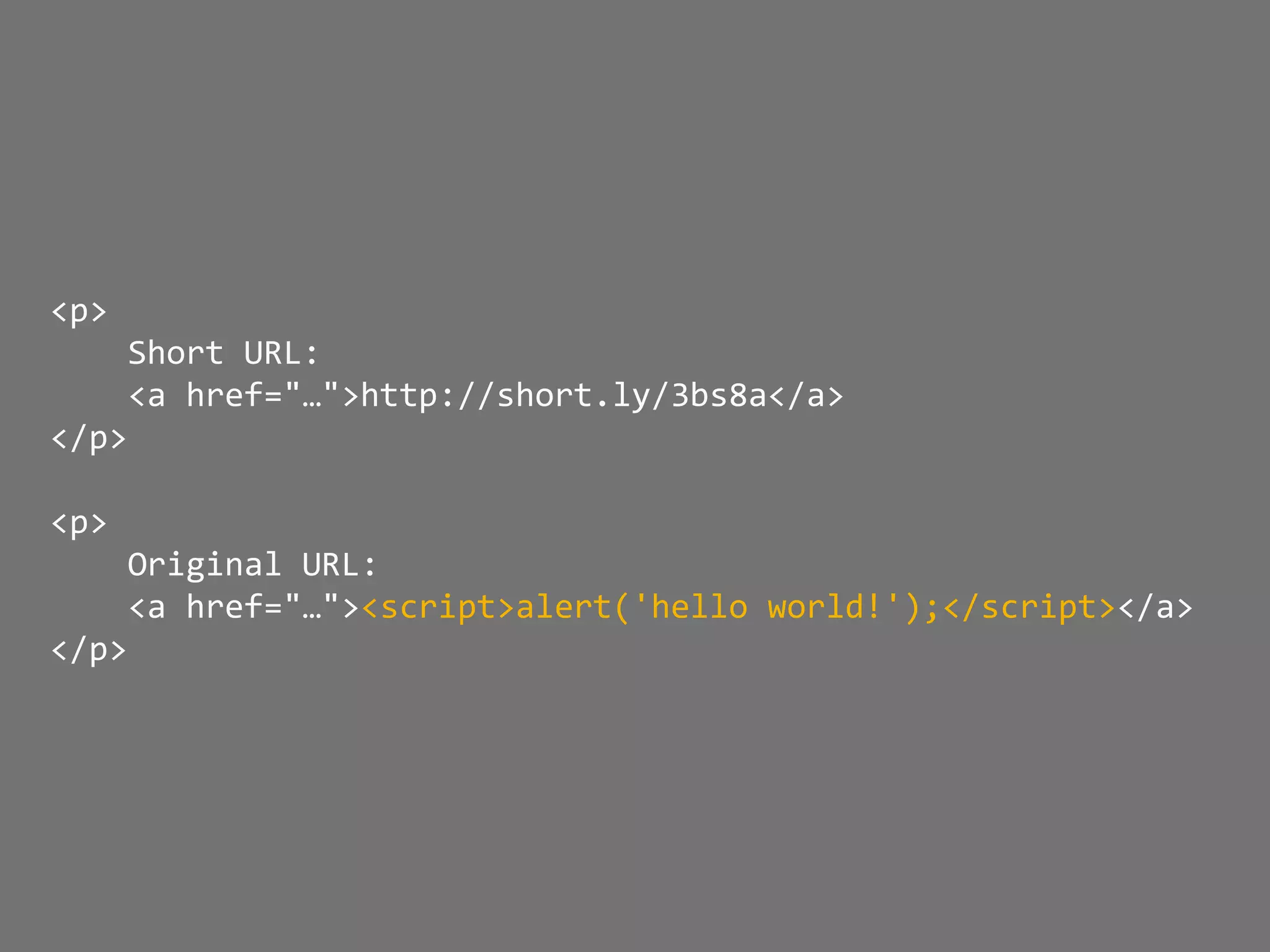
![XSS Attack
Basics
$value = $_POST['value'];
$value = $rssFeed->first->title;
$value = db_fetch('SELECT x FROM table');
<?php echo $value ?>
Raw code/script
is injected onto a page](https://image.slidesharecdn.com/gebhbkmwtryrodvbids0-signature-1b1295ff8d4f63c926cc99fe490d9488deb80d97cdf6a4560e5eb93d780d82cd-poli-160624212034/75/Hacking-Your-Way-To-Better-Security-Dutch-PHP-Conference-2016-54-2048.jpg)
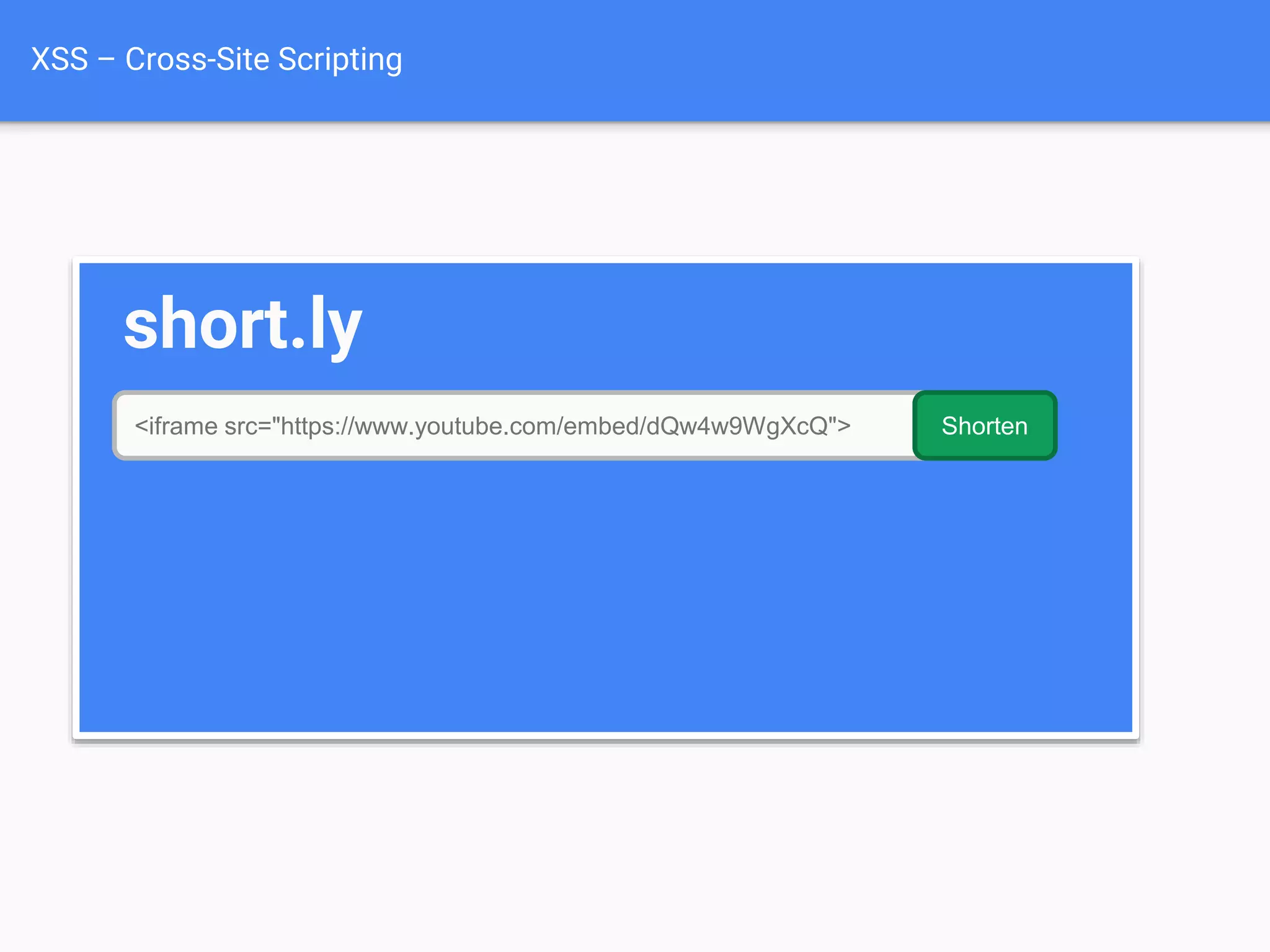
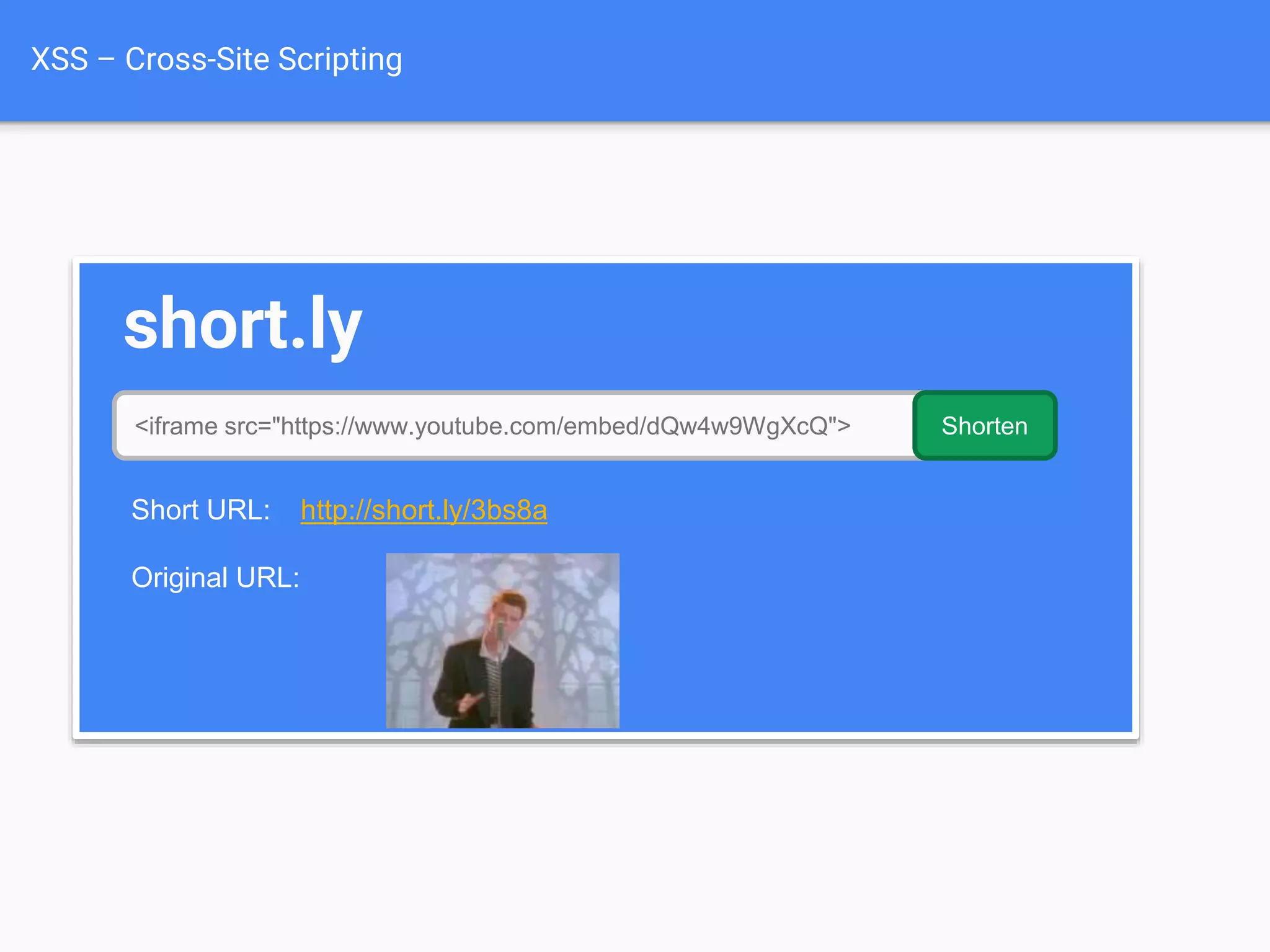
![Protecting
Against XSS
Attacks $value = $_POST['value'];
$value = db_fetch('SELECT value FROM table');
$value = $rssFeed->first->title;
<?php echo $value ?>](https://image.slidesharecdn.com/gebhbkmwtryrodvbids0-signature-1b1295ff8d4f63c926cc99fe490d9488deb80d97cdf6a4560e5eb93d780d82cd-poli-160624212034/75/Hacking-Your-Way-To-Better-Security-Dutch-PHP-Conference-2016-68-2048.jpg)
![Protecting
Against XSS
Attacks
• Filter user input
$value = strip_tags($_POST['value']);
$value = strip_tags(
db_fetch('SELECT value FROM table')
);
$value = strip_tags($rssFeed->first->title);
<?php echo $value ?>](https://image.slidesharecdn.com/gebhbkmwtryrodvbids0-signature-1b1295ff8d4f63c926cc99fe490d9488deb80d97cdf6a4560e5eb93d780d82cd-poli-160624212034/75/Hacking-Your-Way-To-Better-Security-Dutch-PHP-Conference-2016-69-2048.jpg)
![Protecting
Against XSS
Attacks
• Filter user input
• Escape user
input
$value = htmlspecialchars($_POST['value']);
$value = htmlspecialchars(
db_fetch('SELECT value FROM table')
);
$value = htmlspecialchars($rssFeed->first->title);
<?php echo $value ?>
<script> <script>
htmlspecialchars()](https://image.slidesharecdn.com/gebhbkmwtryrodvbids0-signature-1b1295ff8d4f63c926cc99fe490d9488deb80d97cdf6a4560e5eb93d780d82cd-poli-160624212034/75/Hacking-Your-Way-To-Better-Security-Dutch-PHP-Conference-2016-70-2048.jpg)
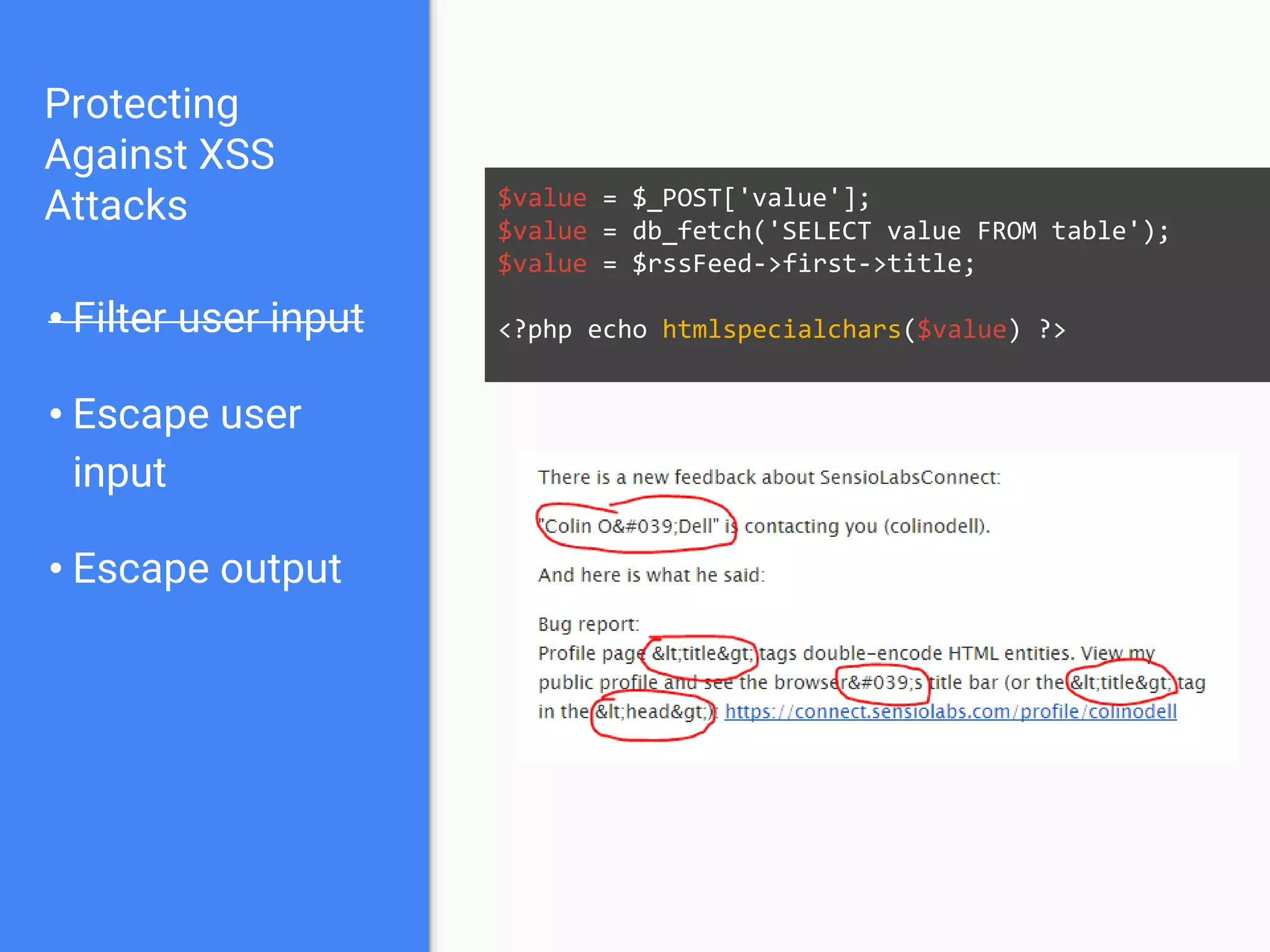
![Protecting
Against XSS
Attacks
• Filter user input
• Escape user
input
• Escape output
$value = $_POST['value'];
$value = db_fetch('SELECT value FROM table');
$value = $rssFeed->first->title;
<?php echo htmlspecialchars($value) ?>](https://image.slidesharecdn.com/gebhbkmwtryrodvbids0-signature-1b1295ff8d4f63c926cc99fe490d9488deb80d97cdf6a4560e5eb93d780d82cd-poli-160624212034/75/Hacking-Your-Way-To-Better-Security-Dutch-PHP-Conference-2016-71-2048.jpg)