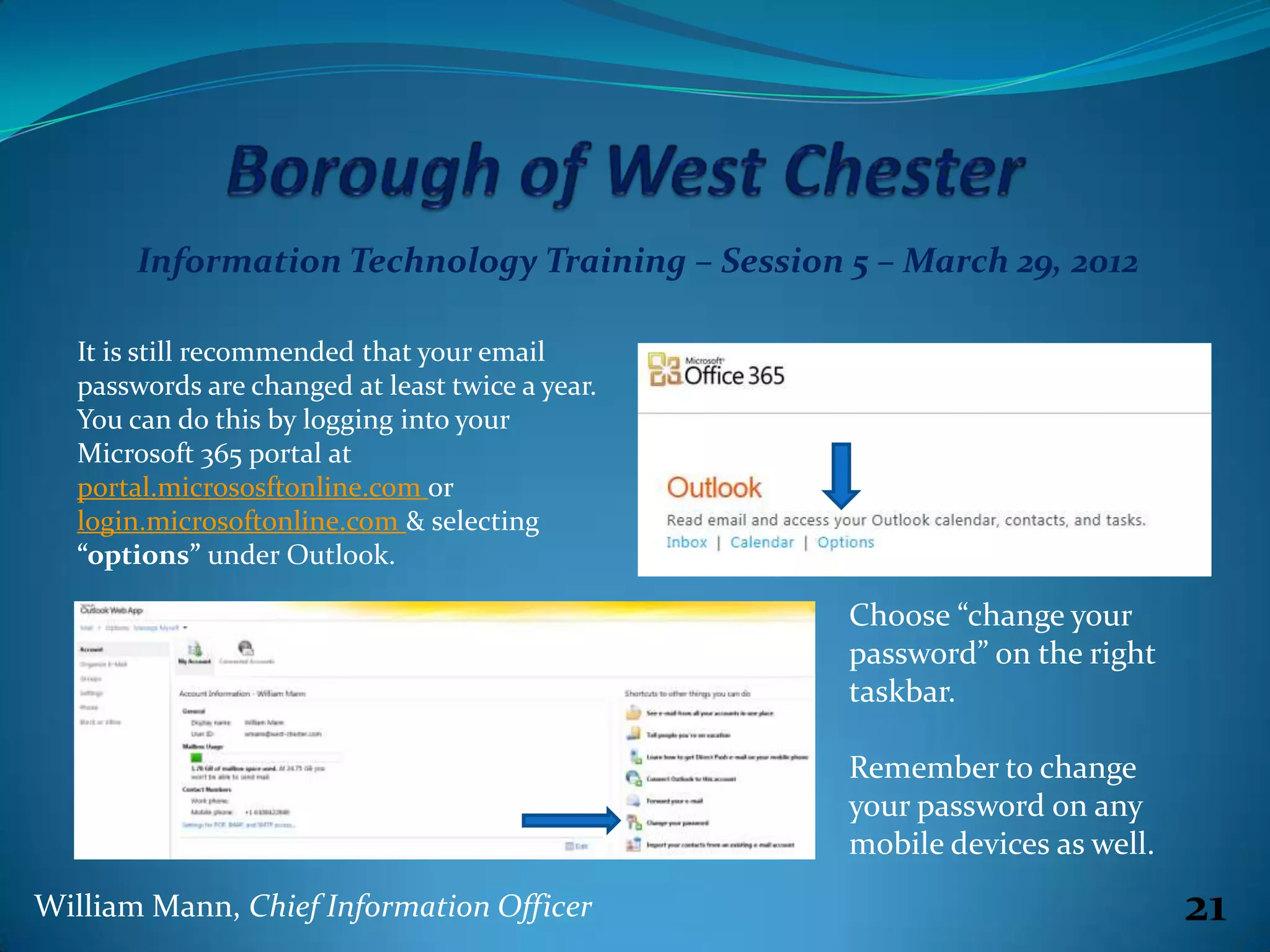
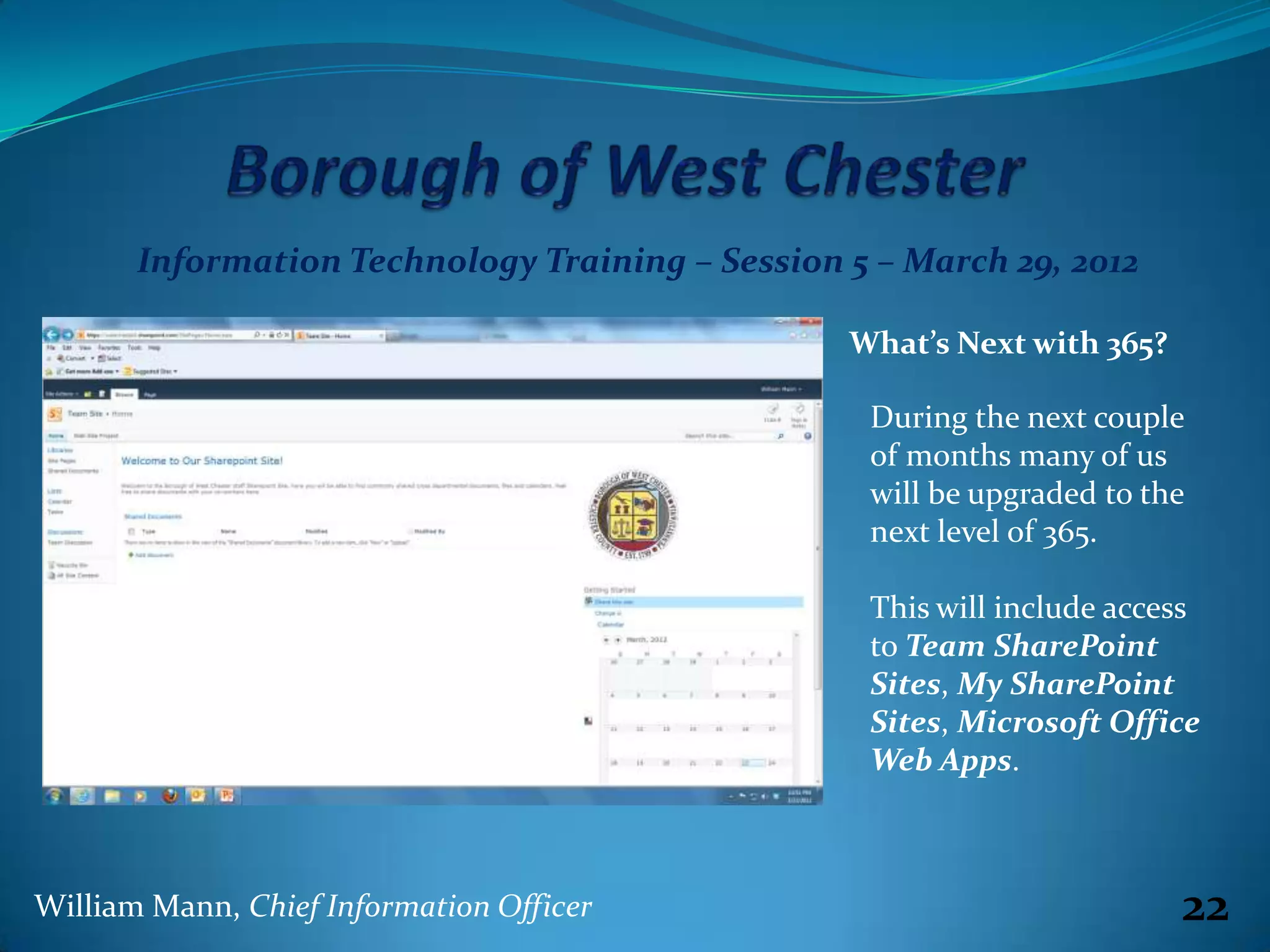
The document summarizes an information technology training session on March 29, 2012. It covers three parts: Microsoft Outlook email and calendar skills, an update on the recent migration to Microsoft 365, and managing passwords. The session demonstrated Outlook features like spelling checks, signatures, folders and rules. It explained that the old login client was uninstalled as part of migrating to 365. The session reminded users that passwords are still recommended to change twice a year and can be changed in the 365 portal.