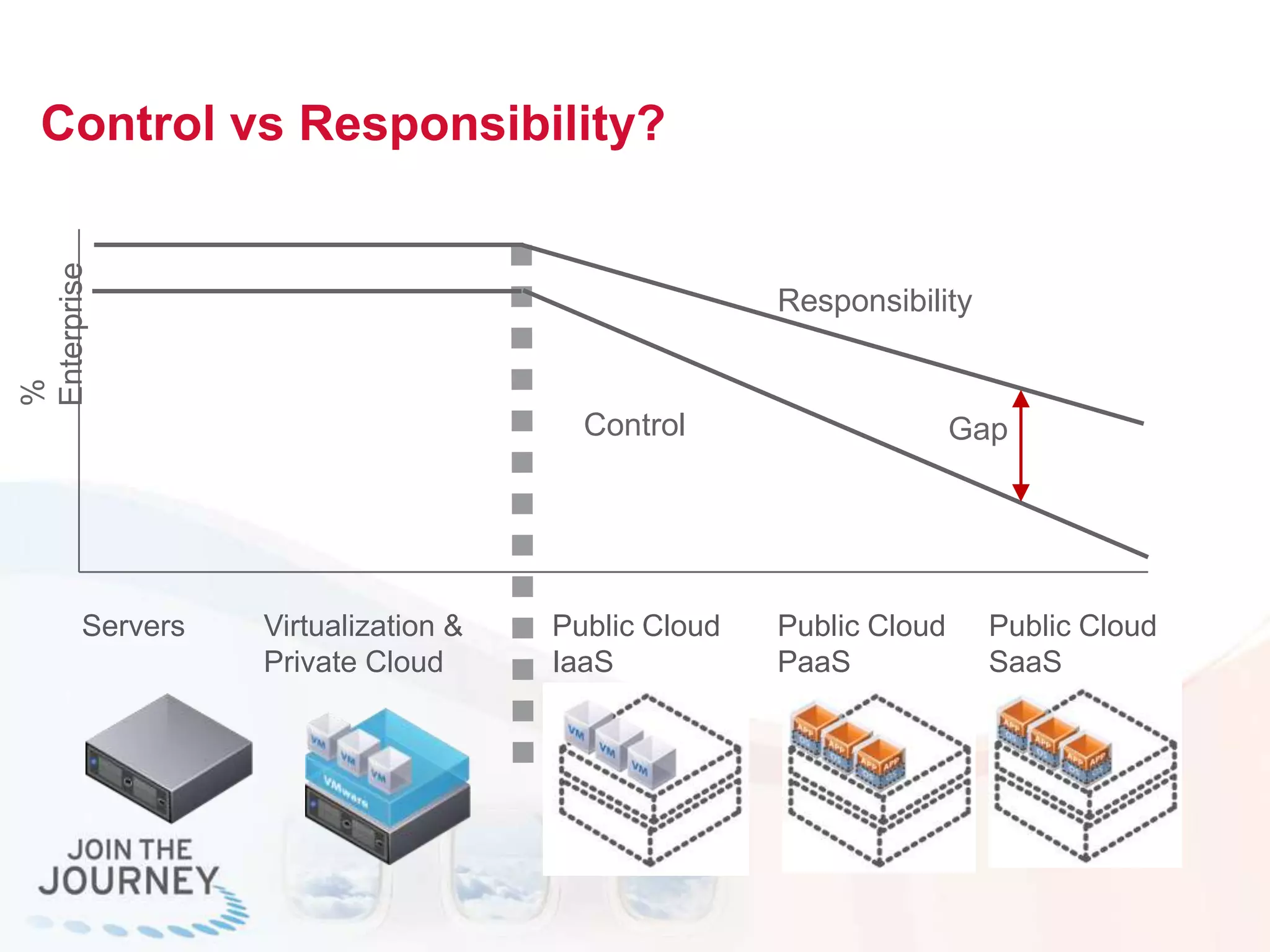
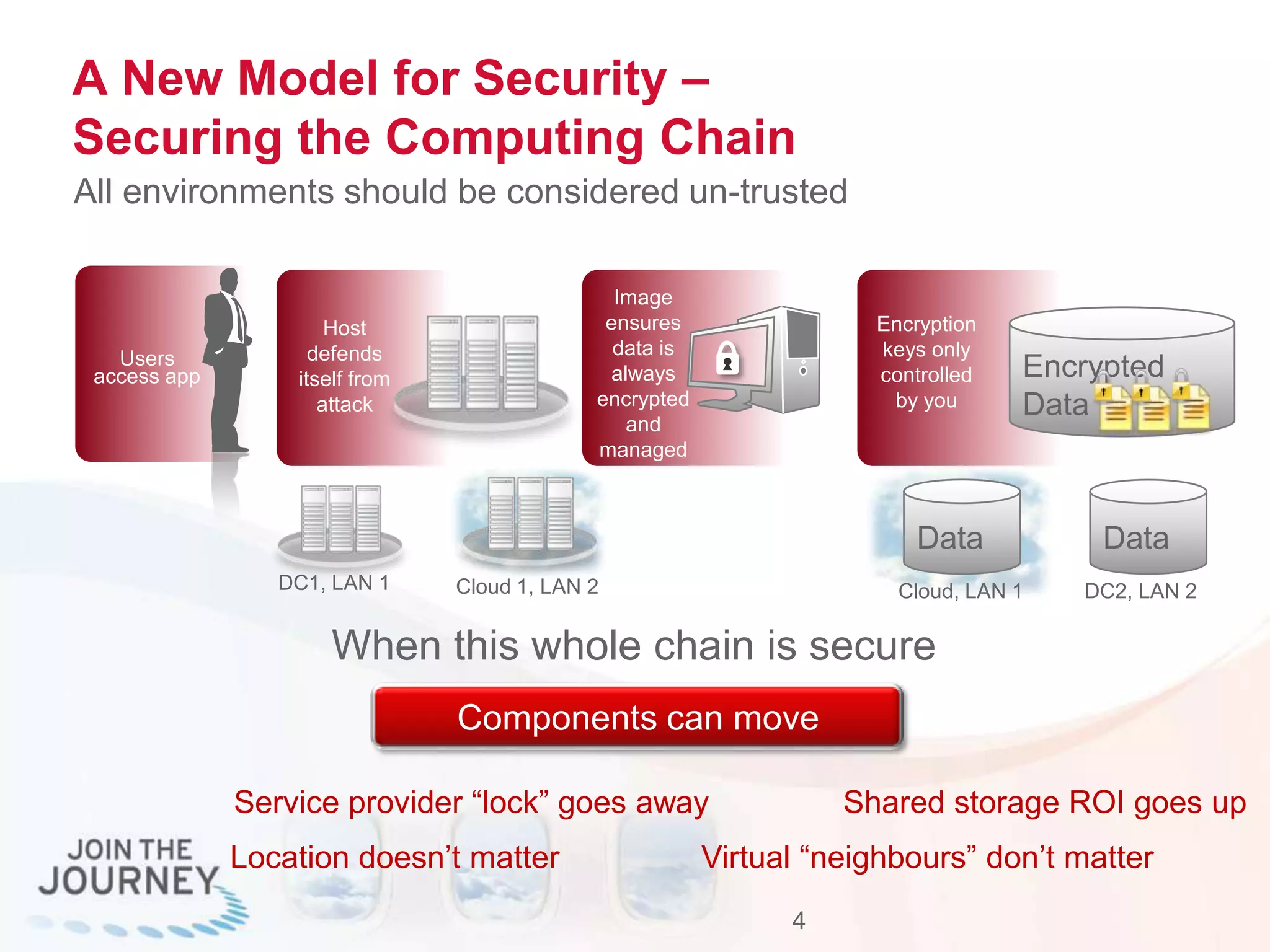
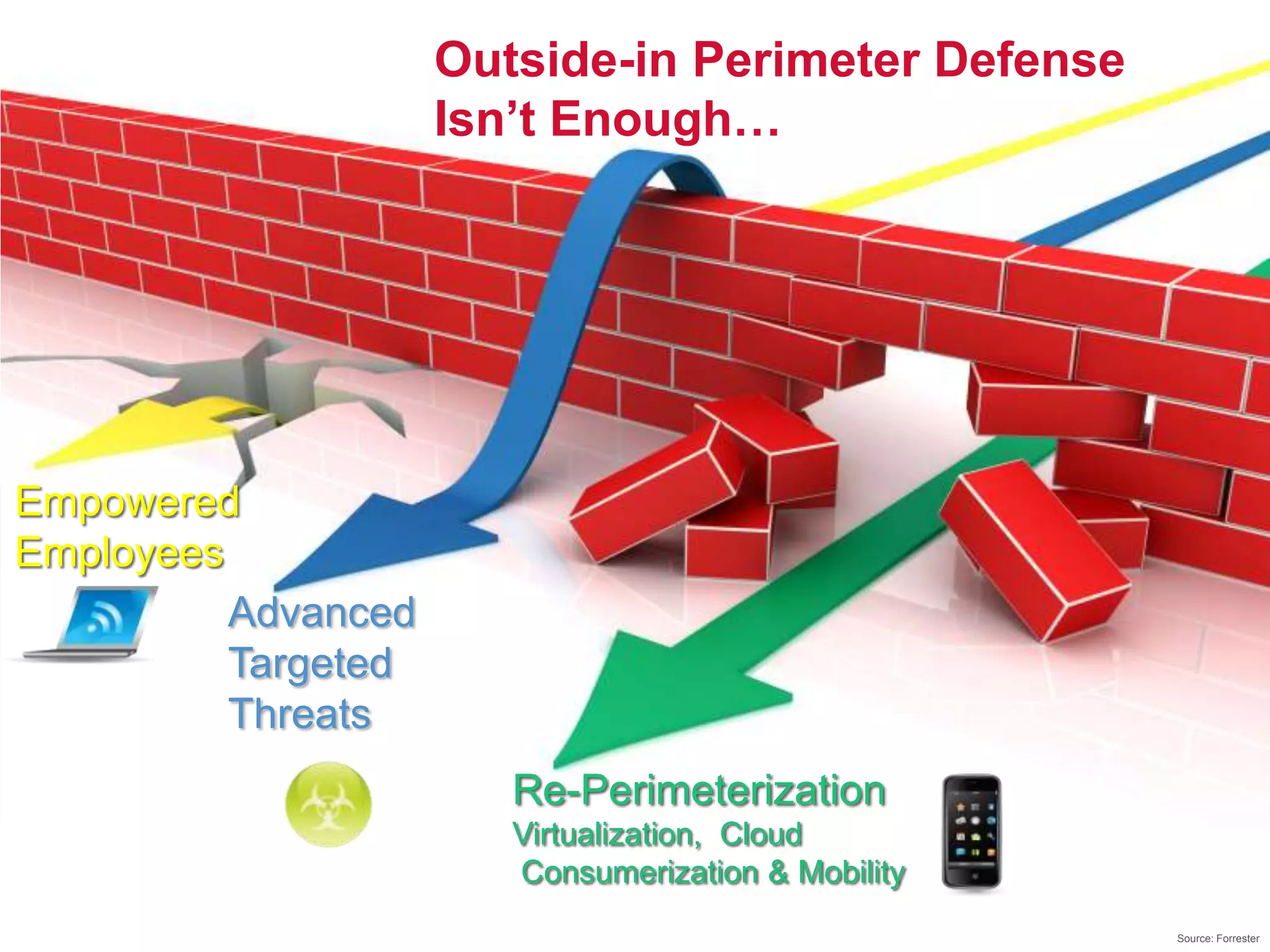
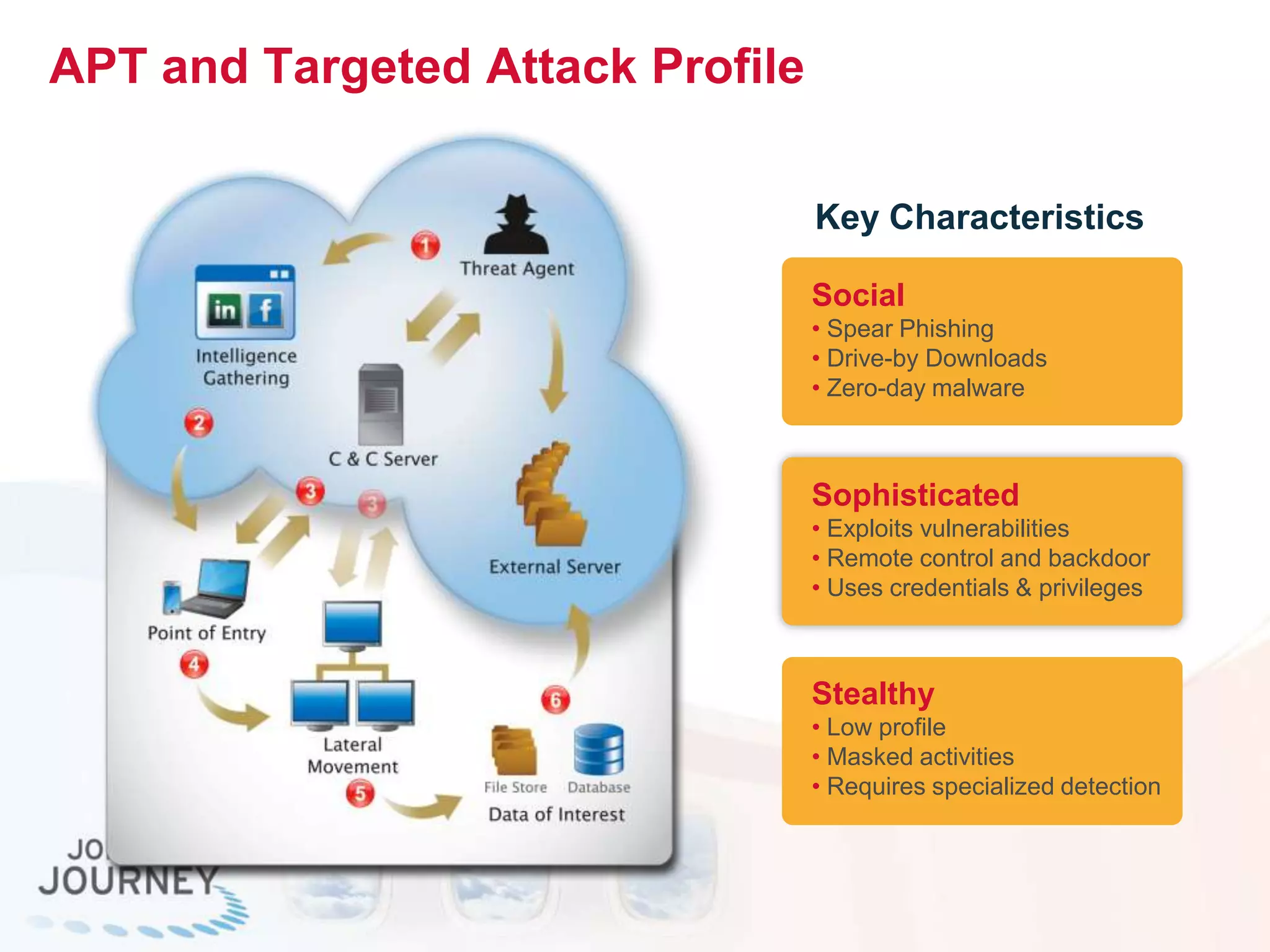
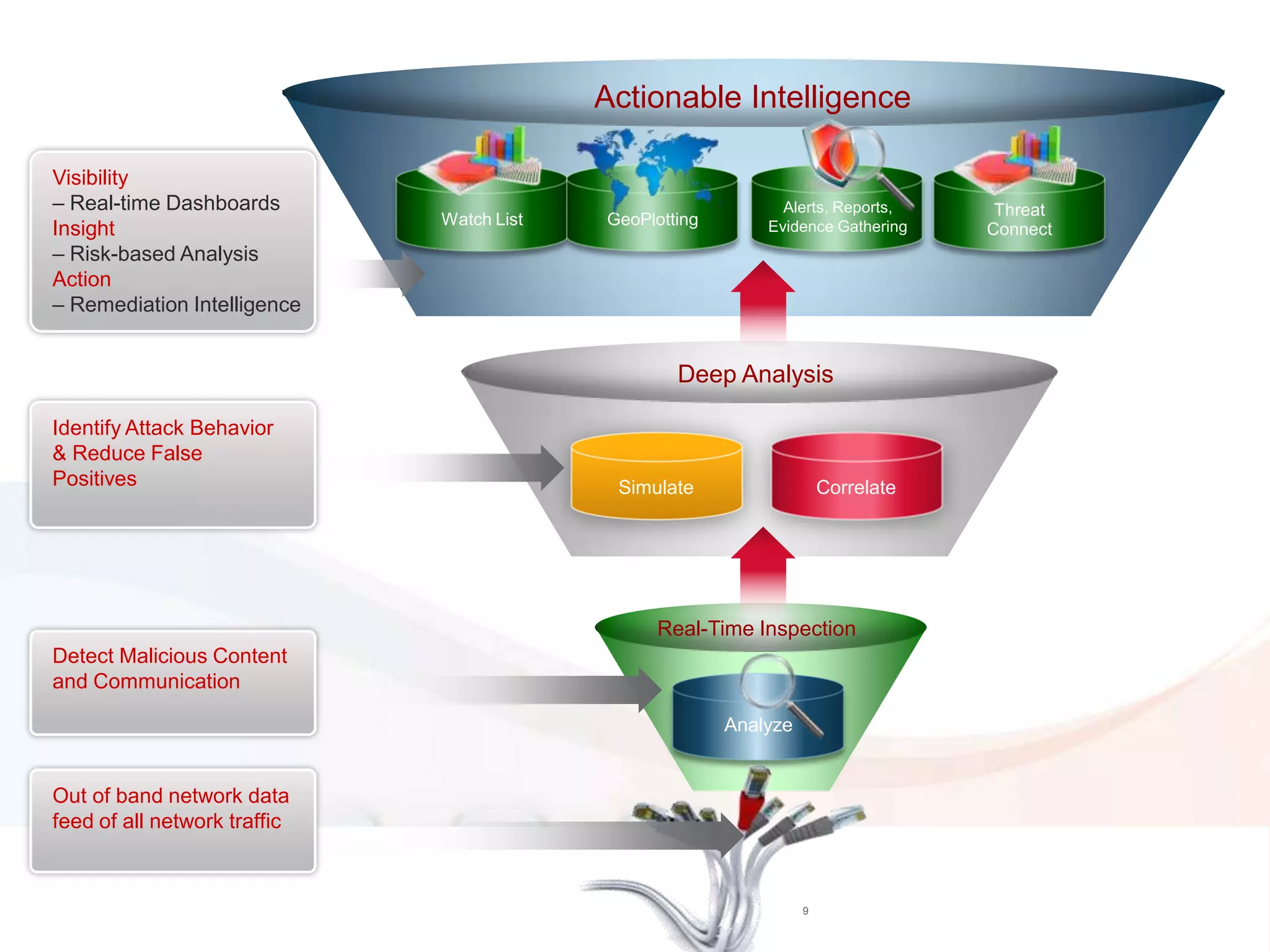
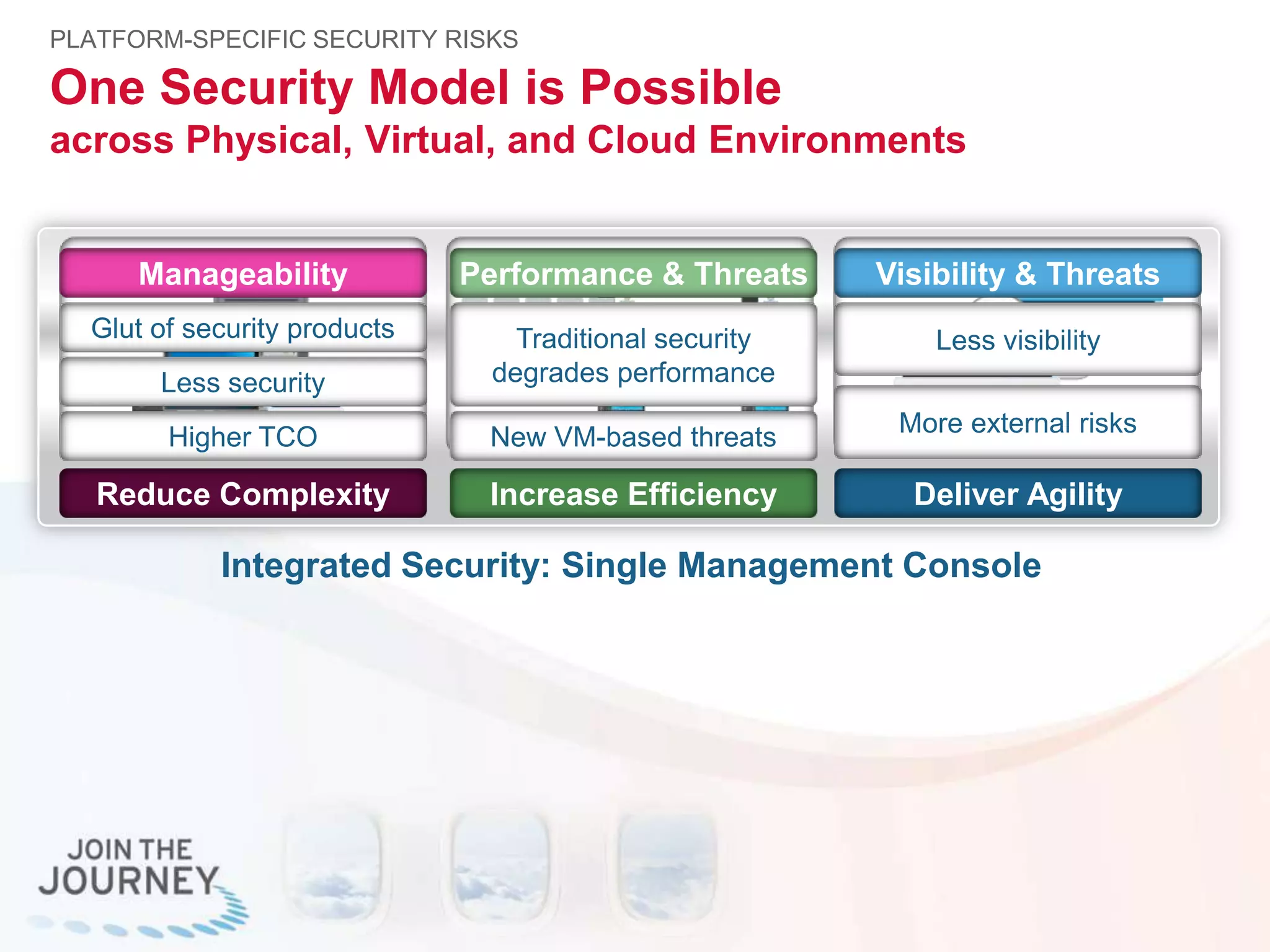
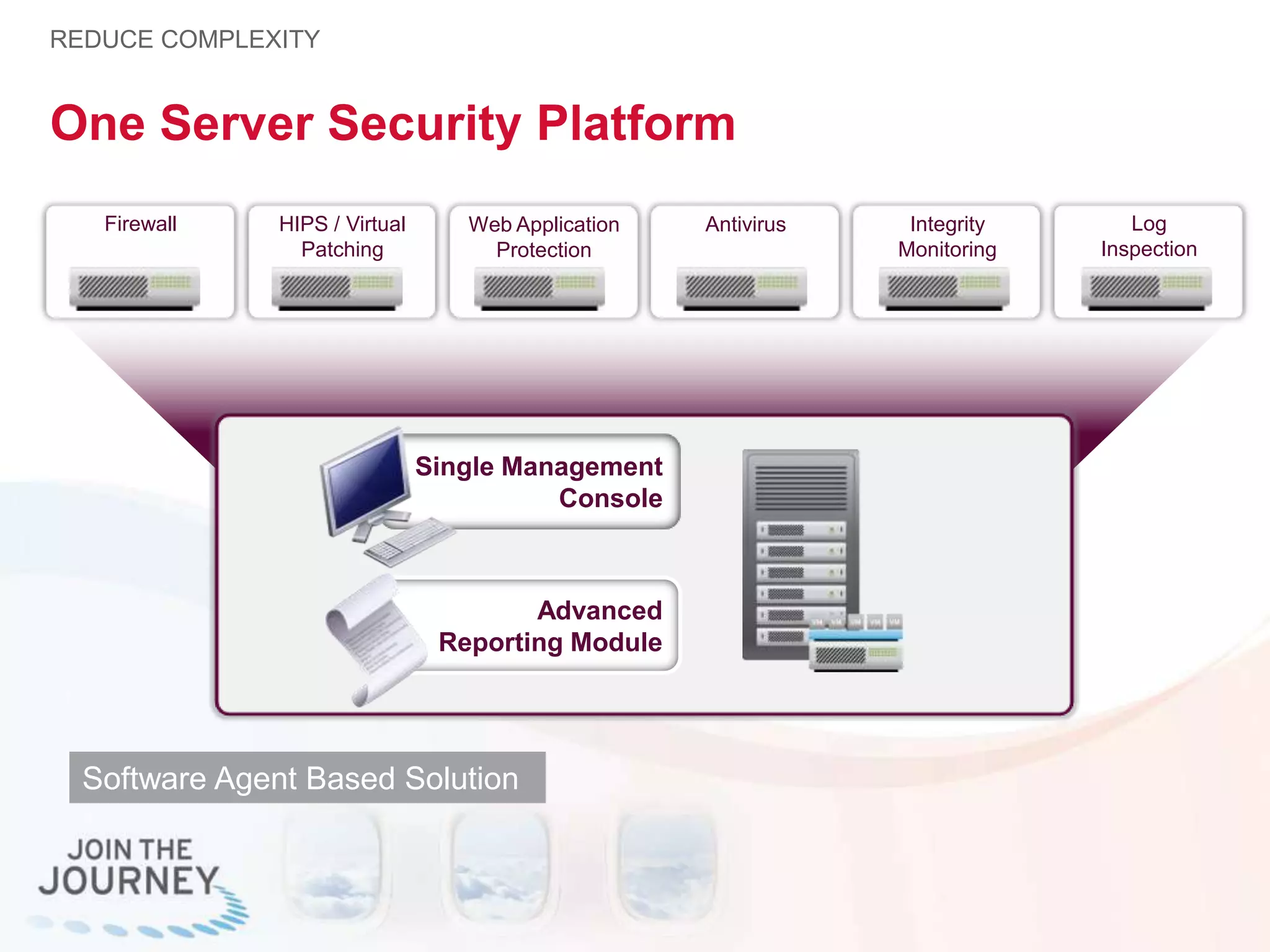
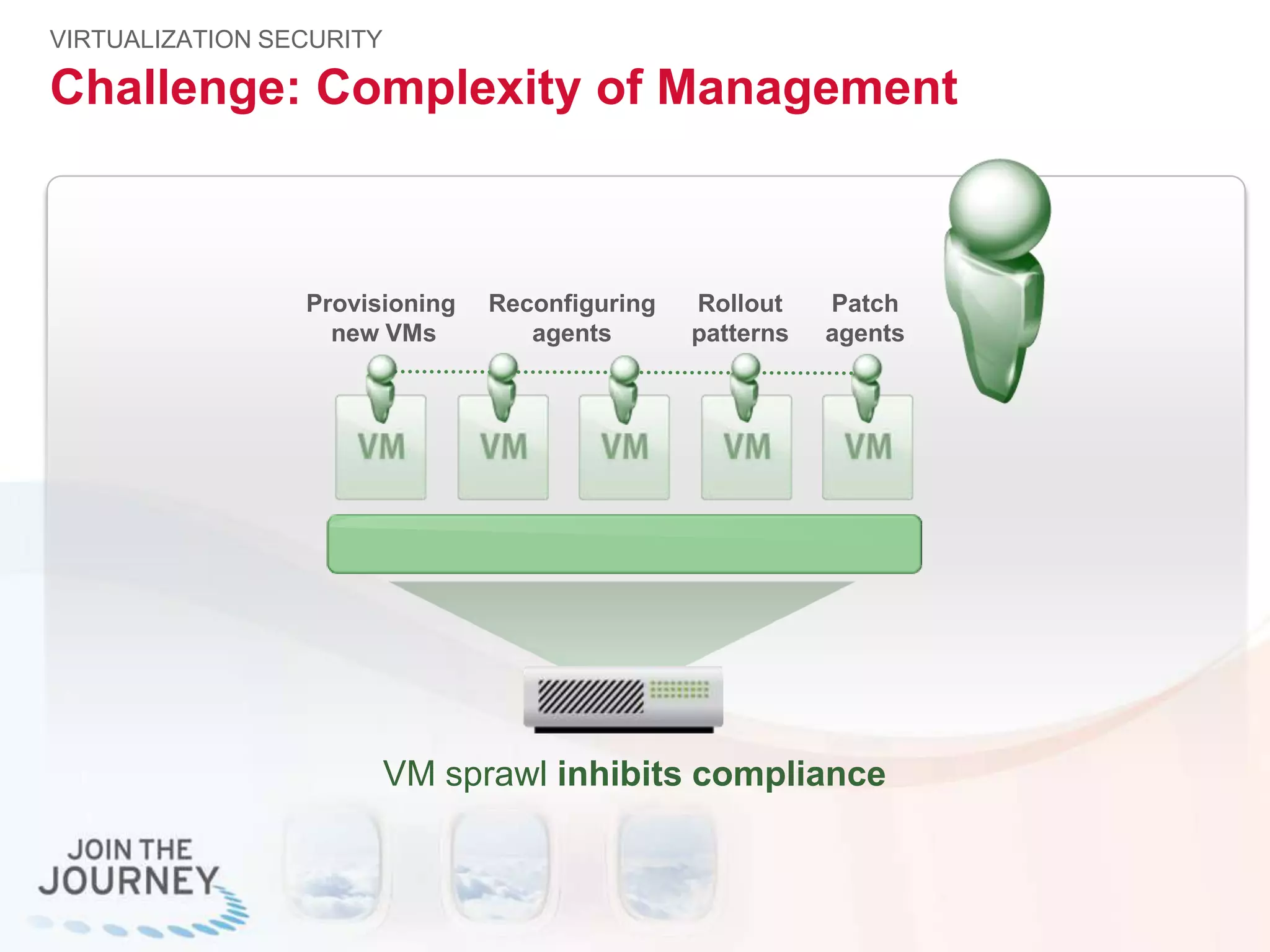
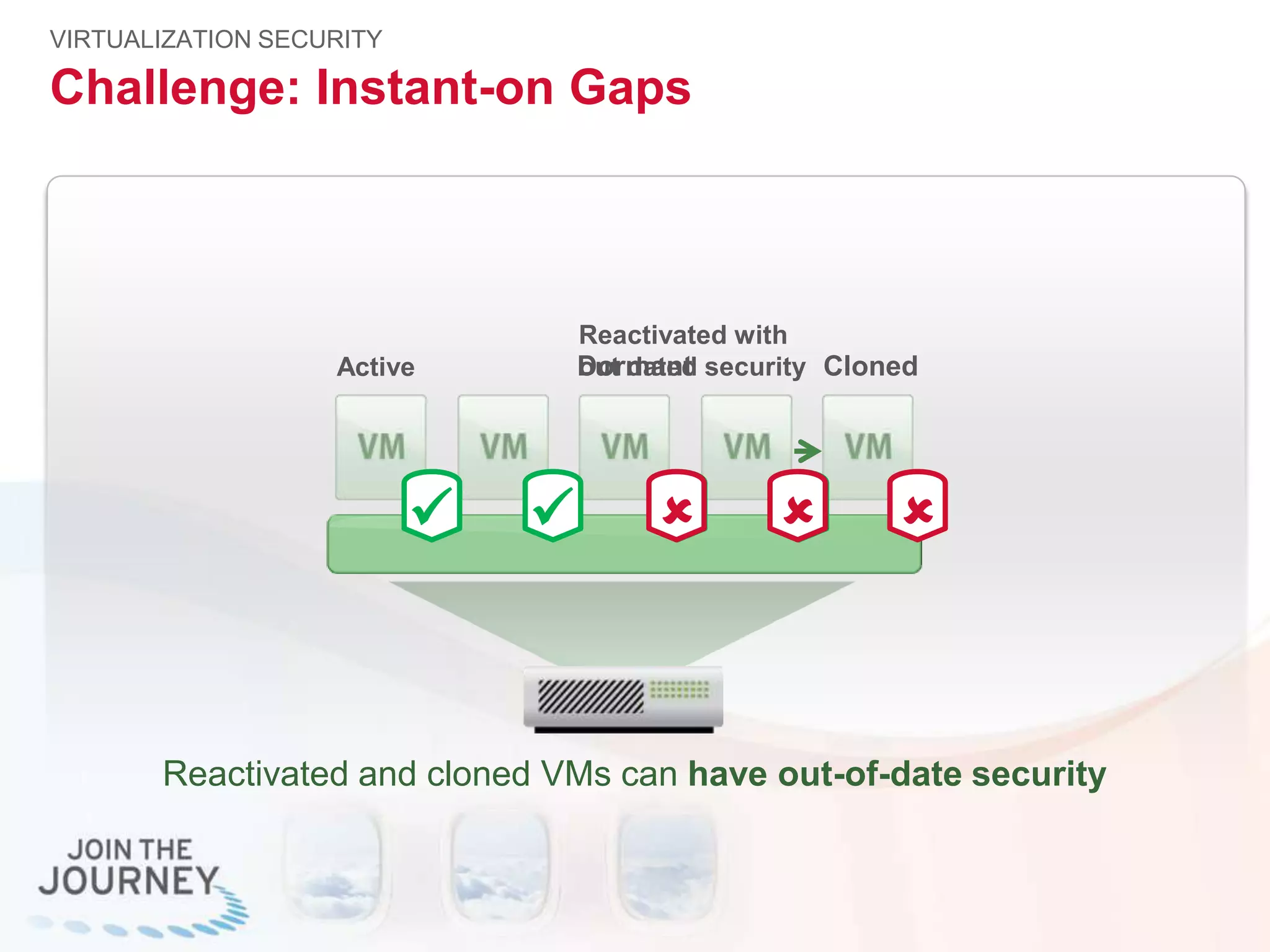
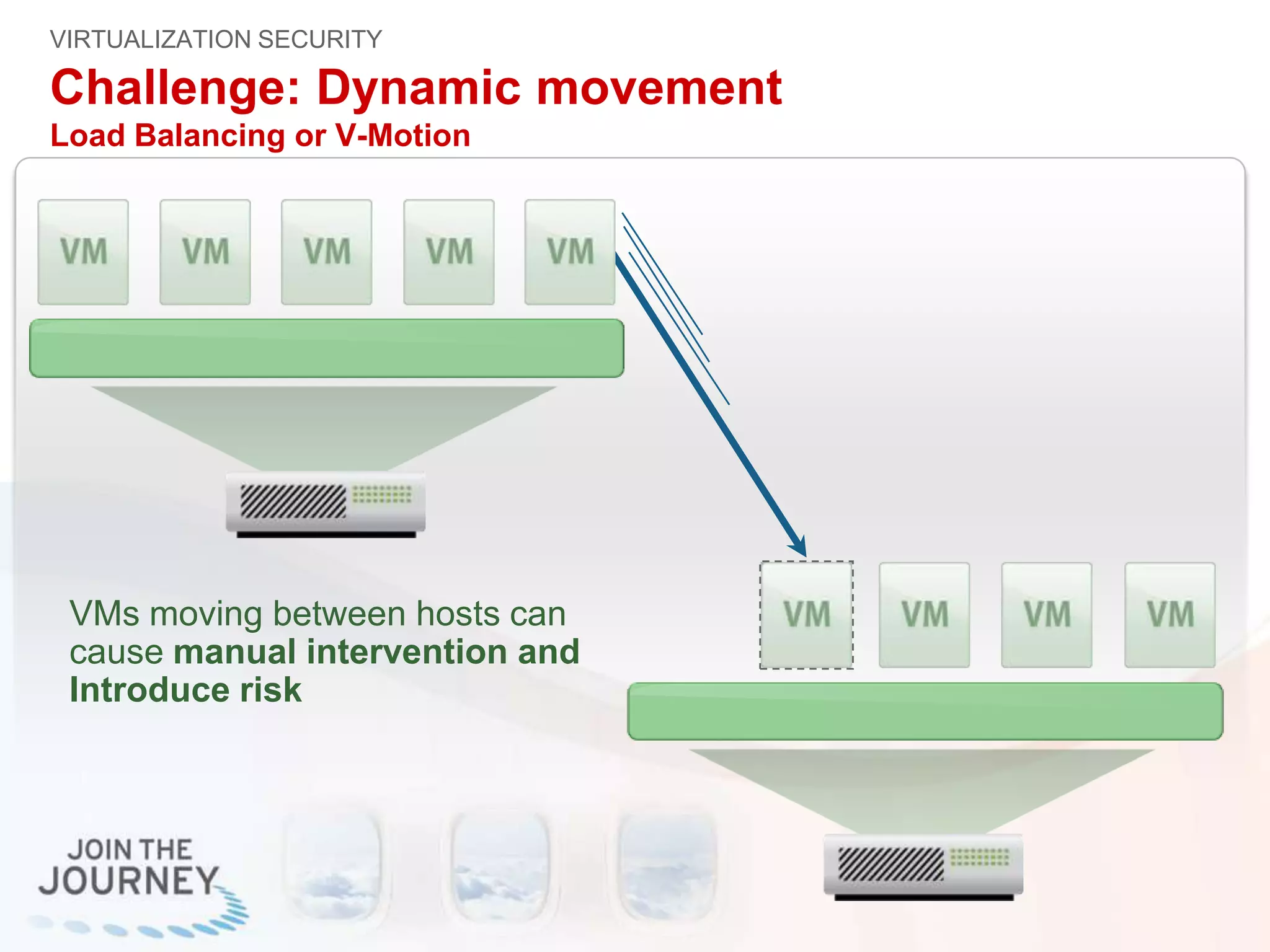
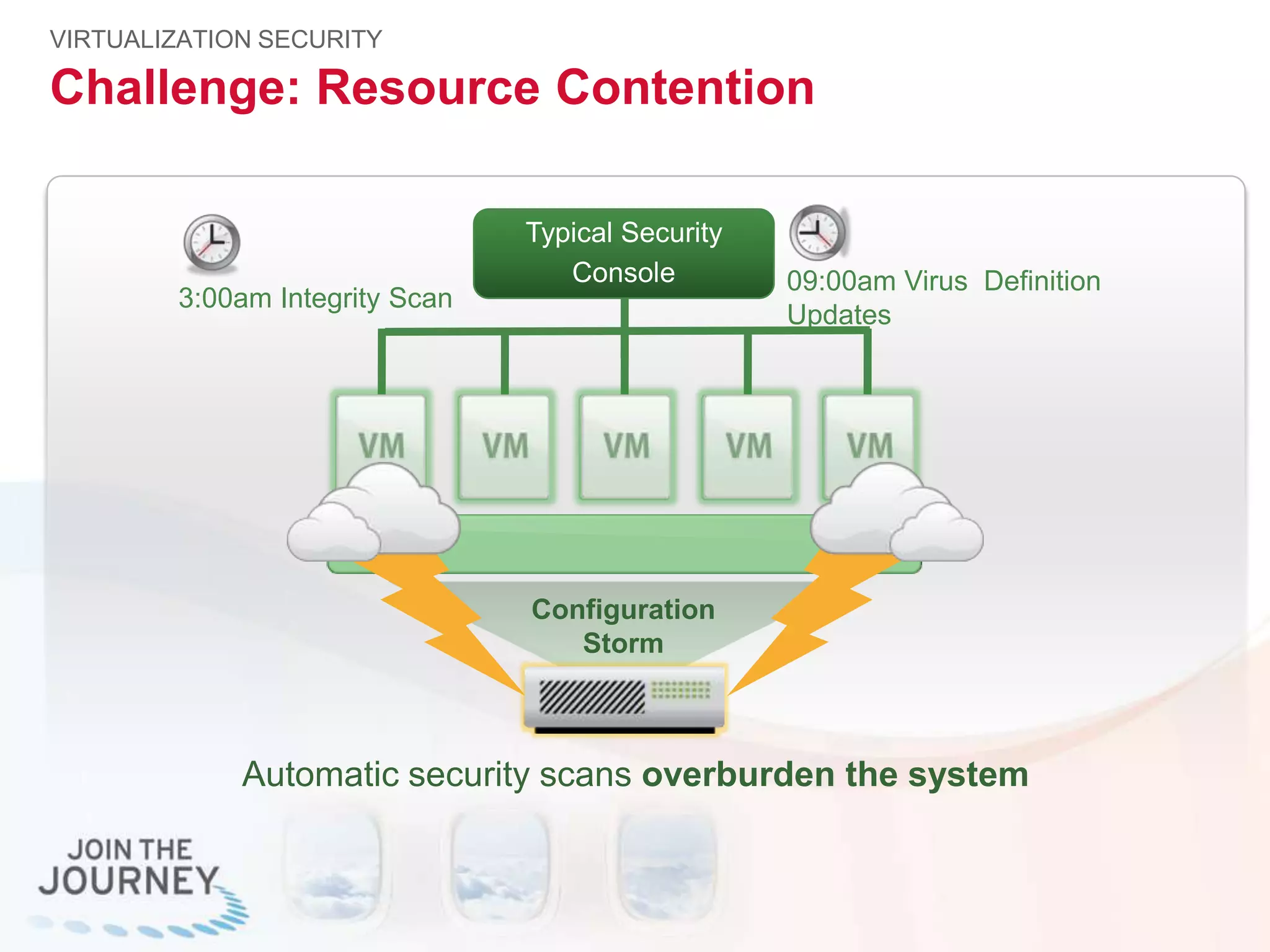
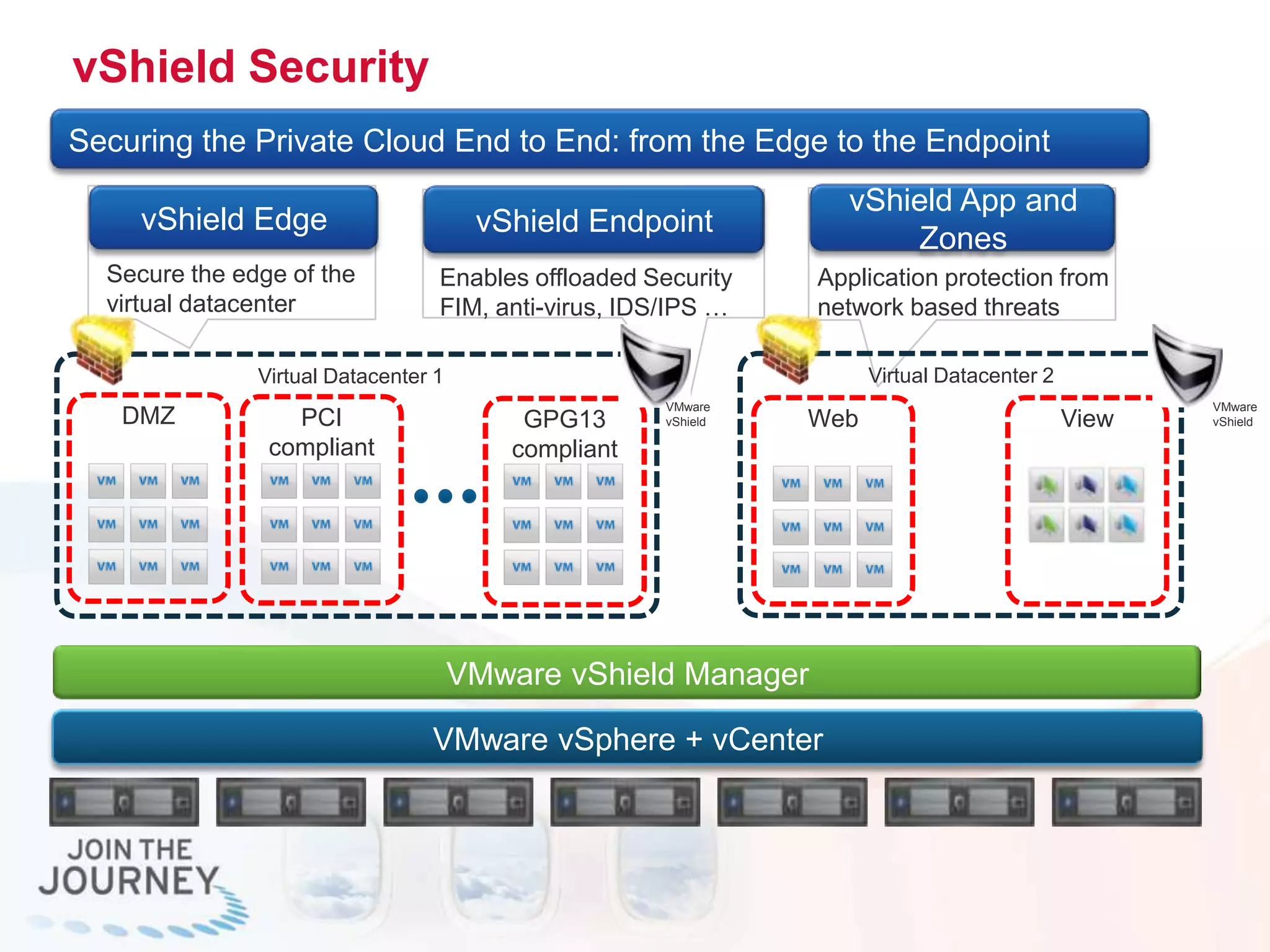
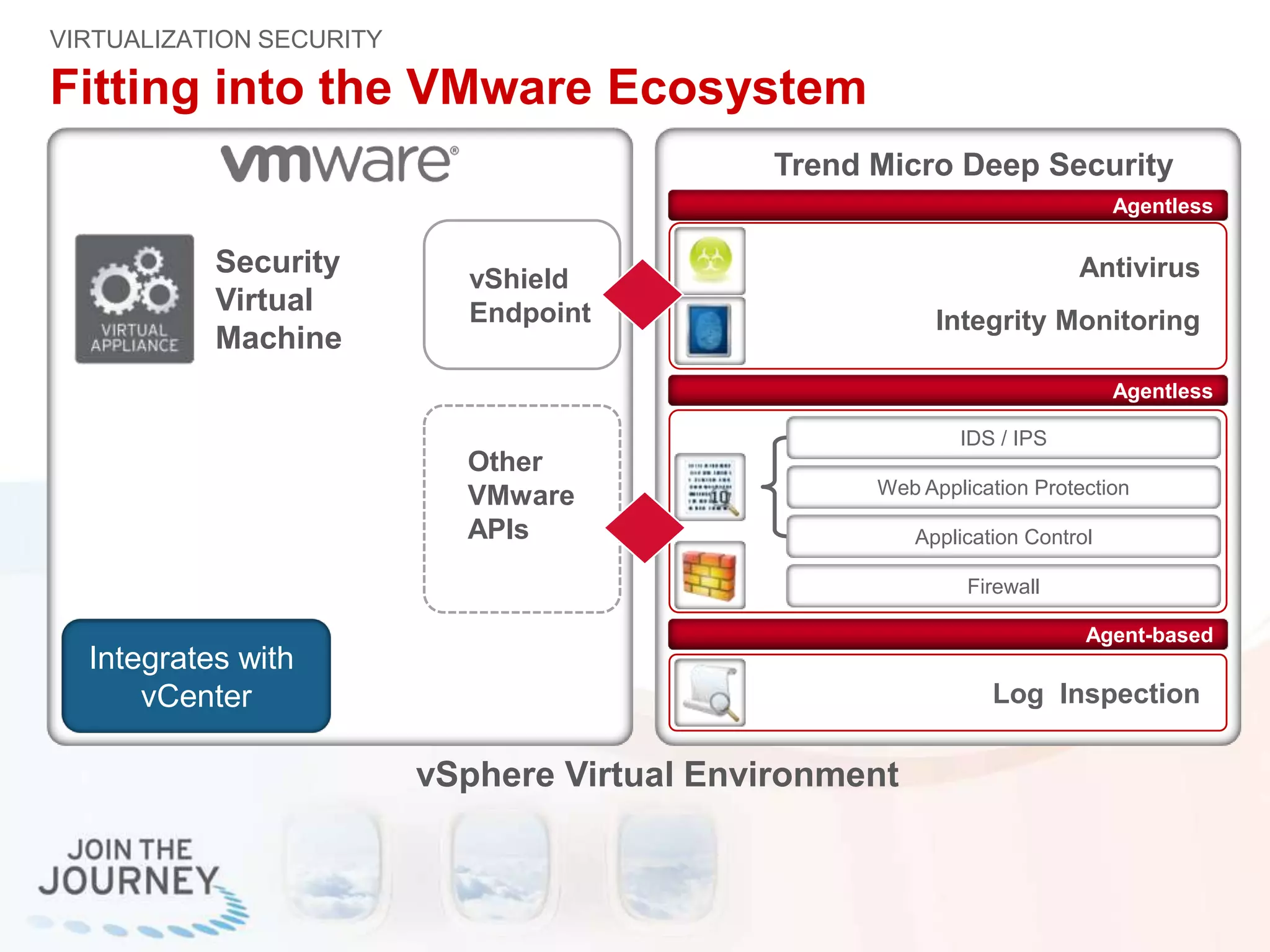
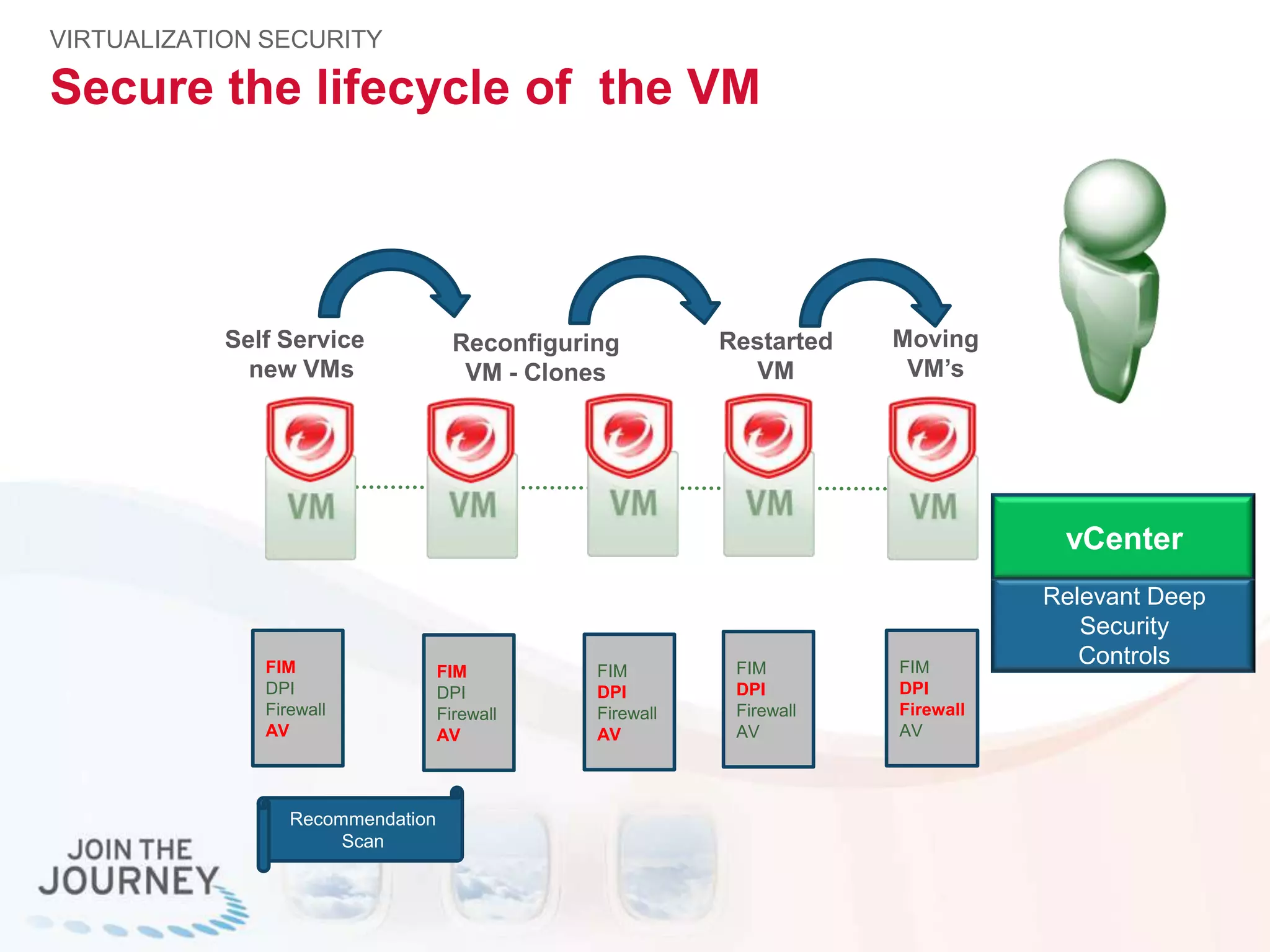
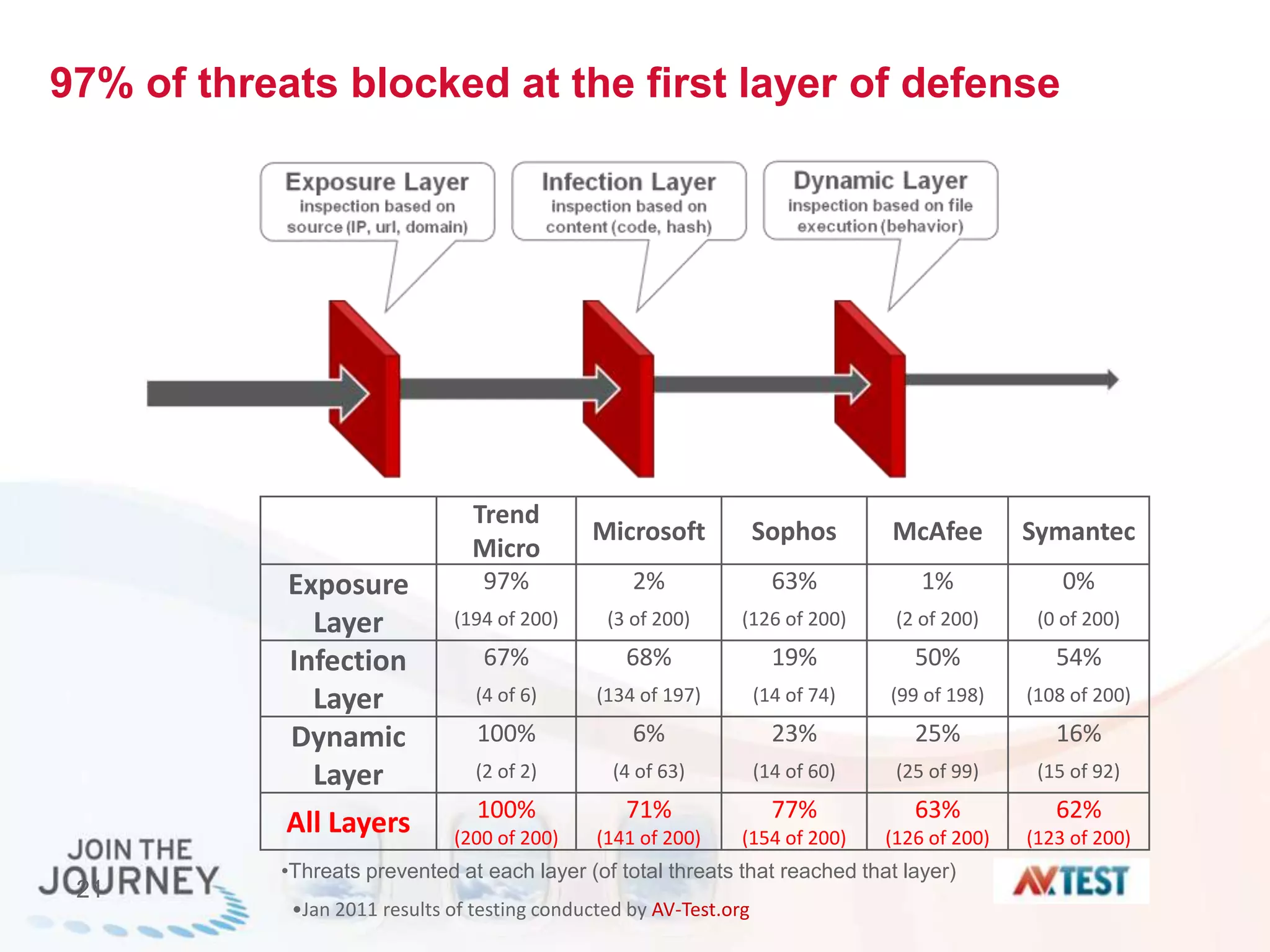
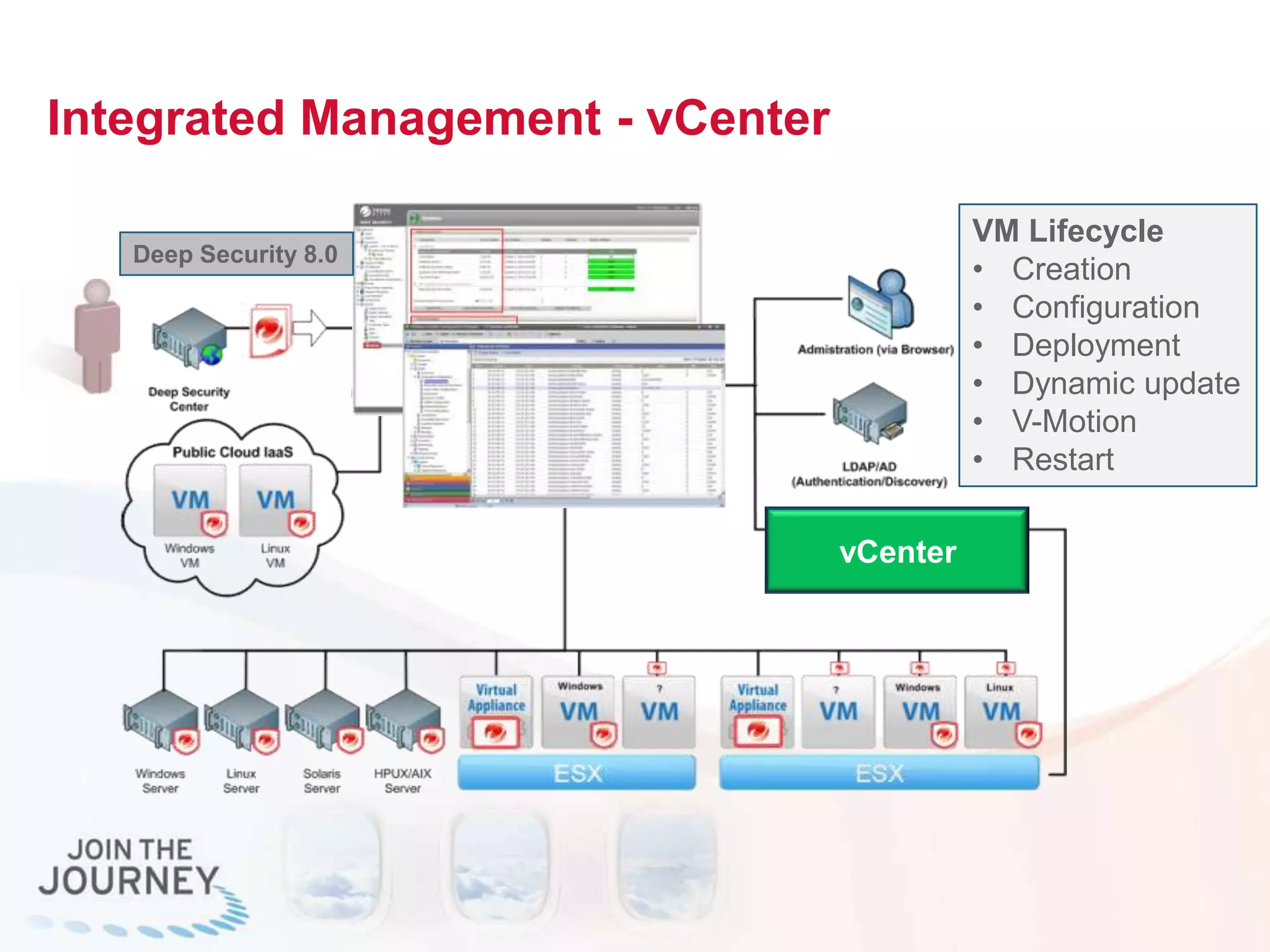
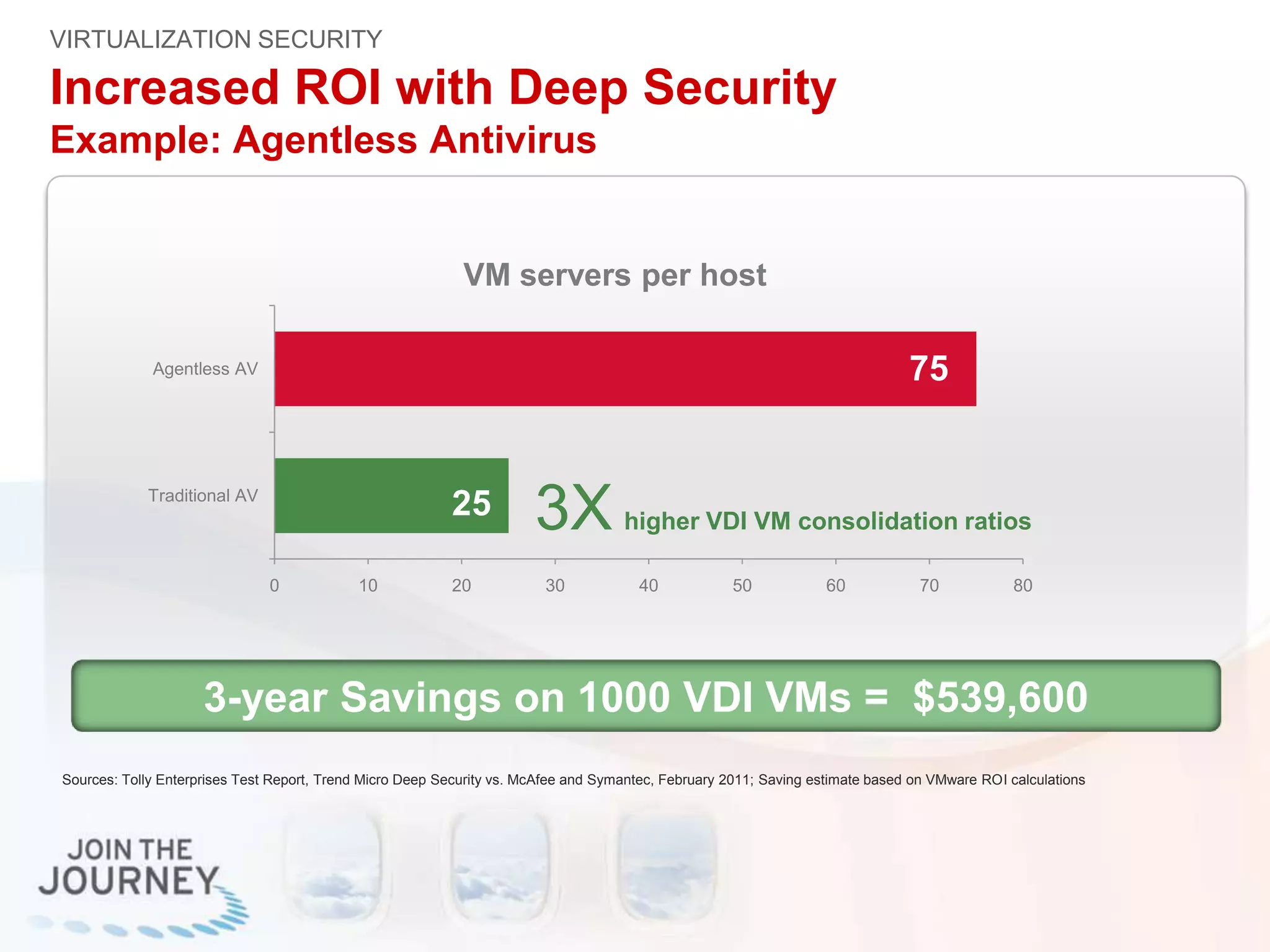
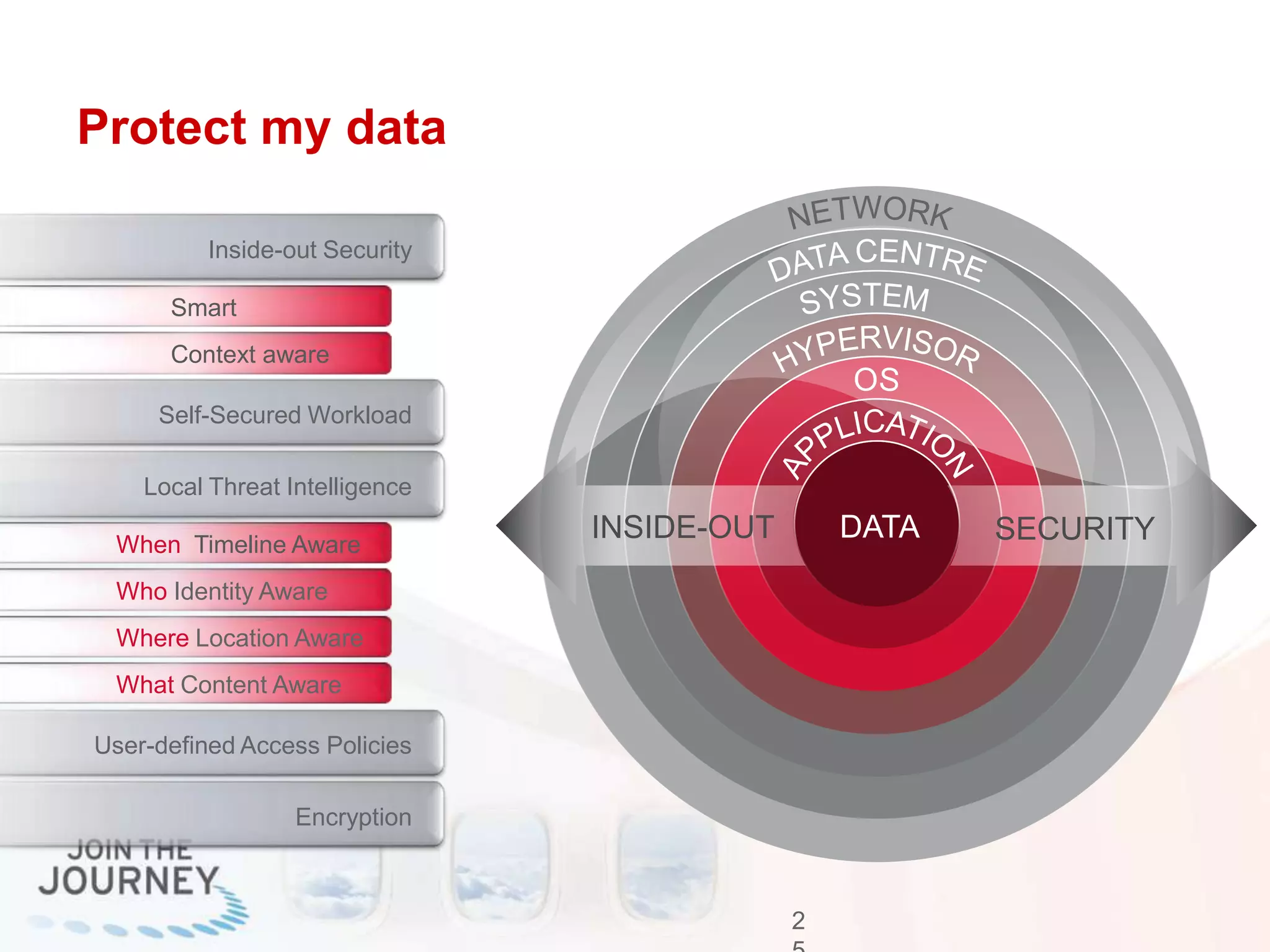
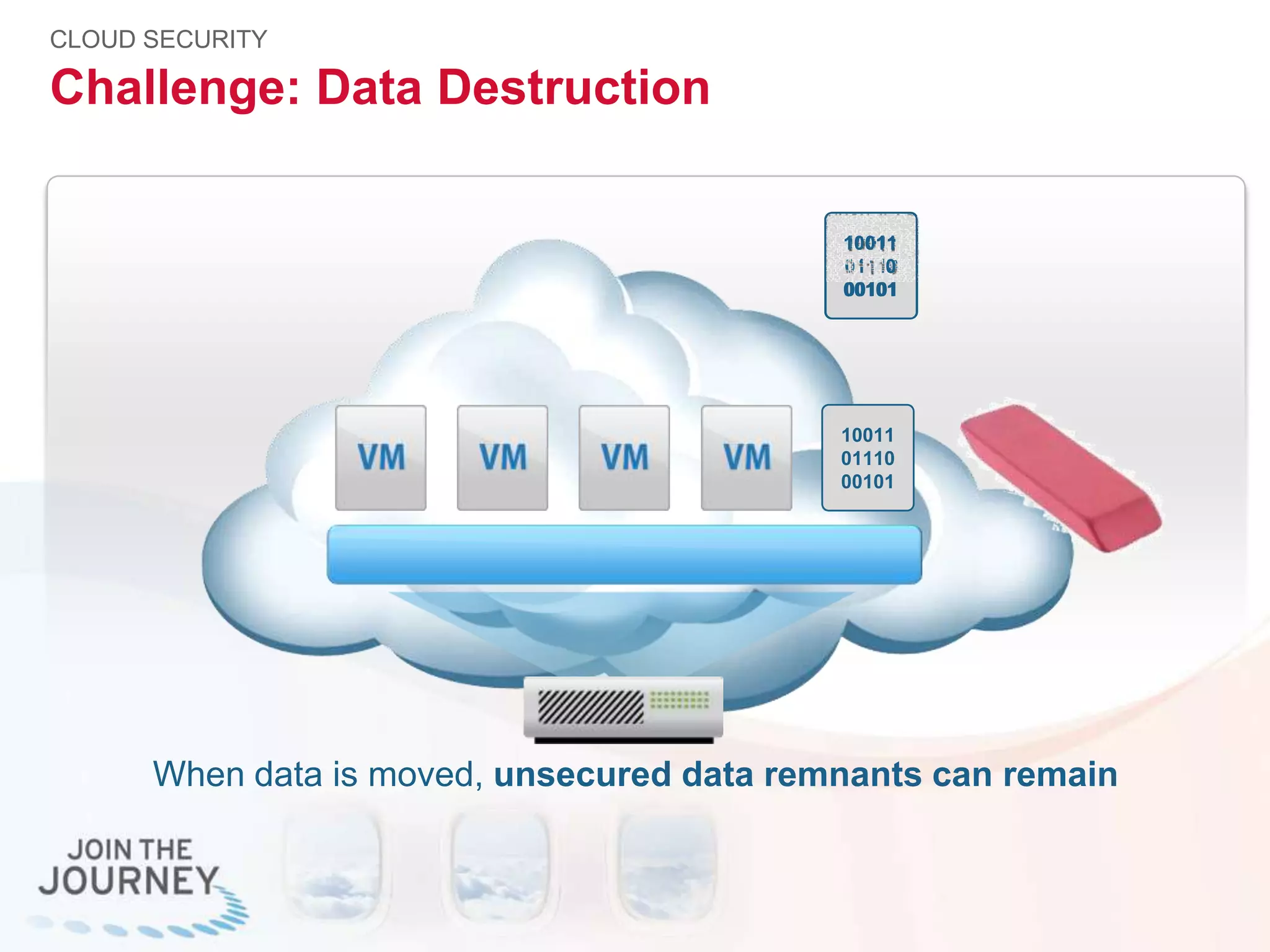
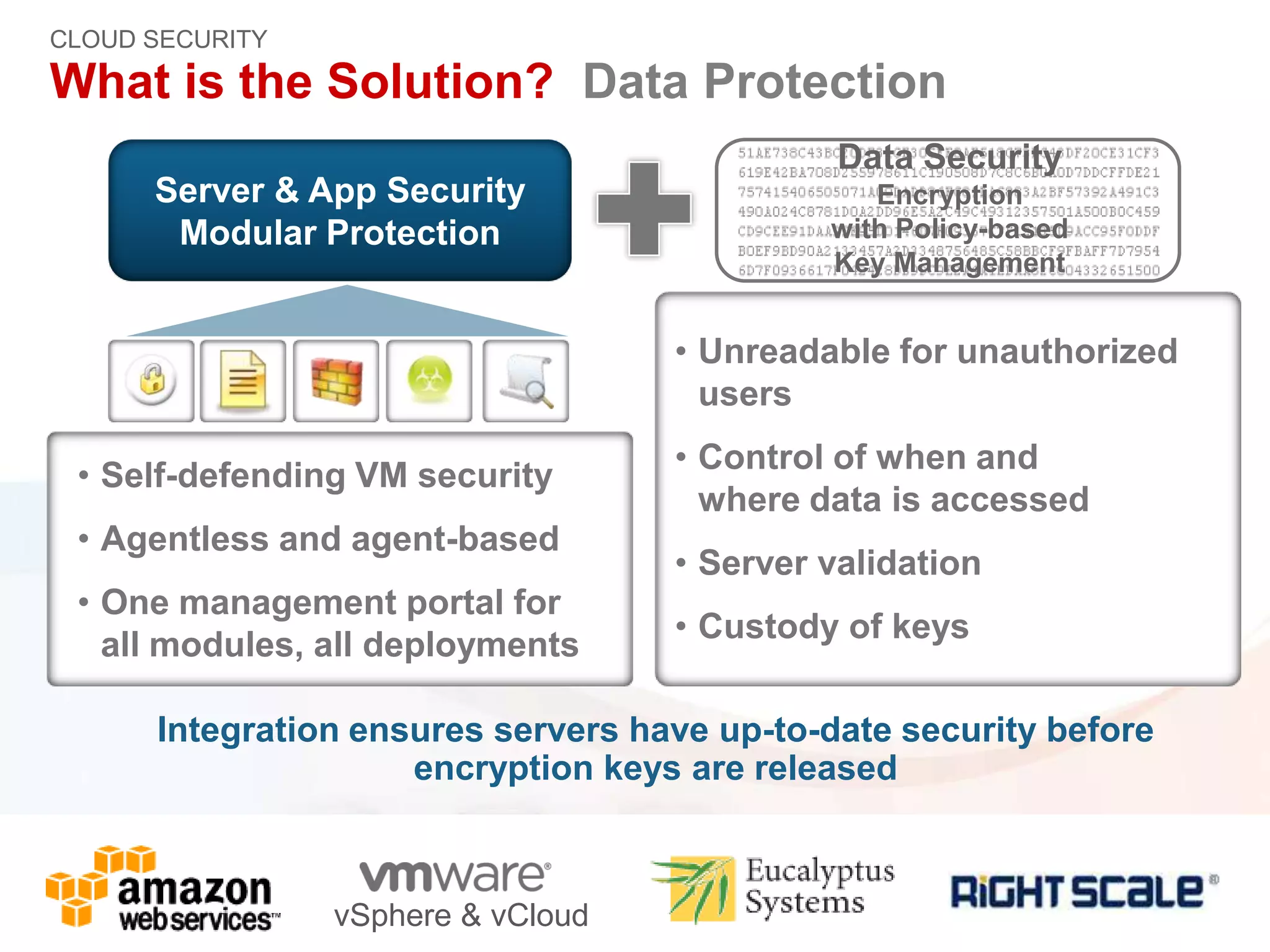
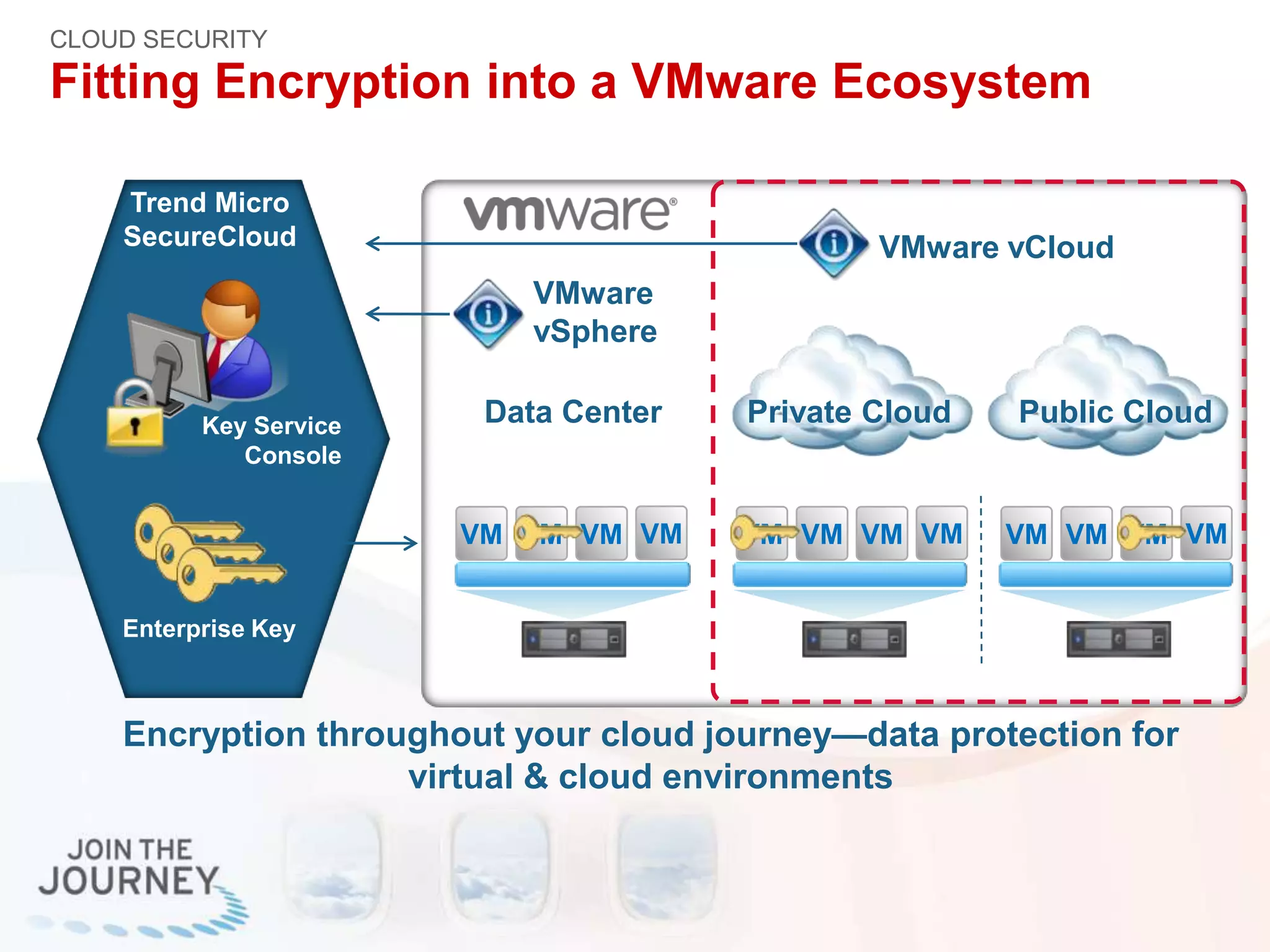
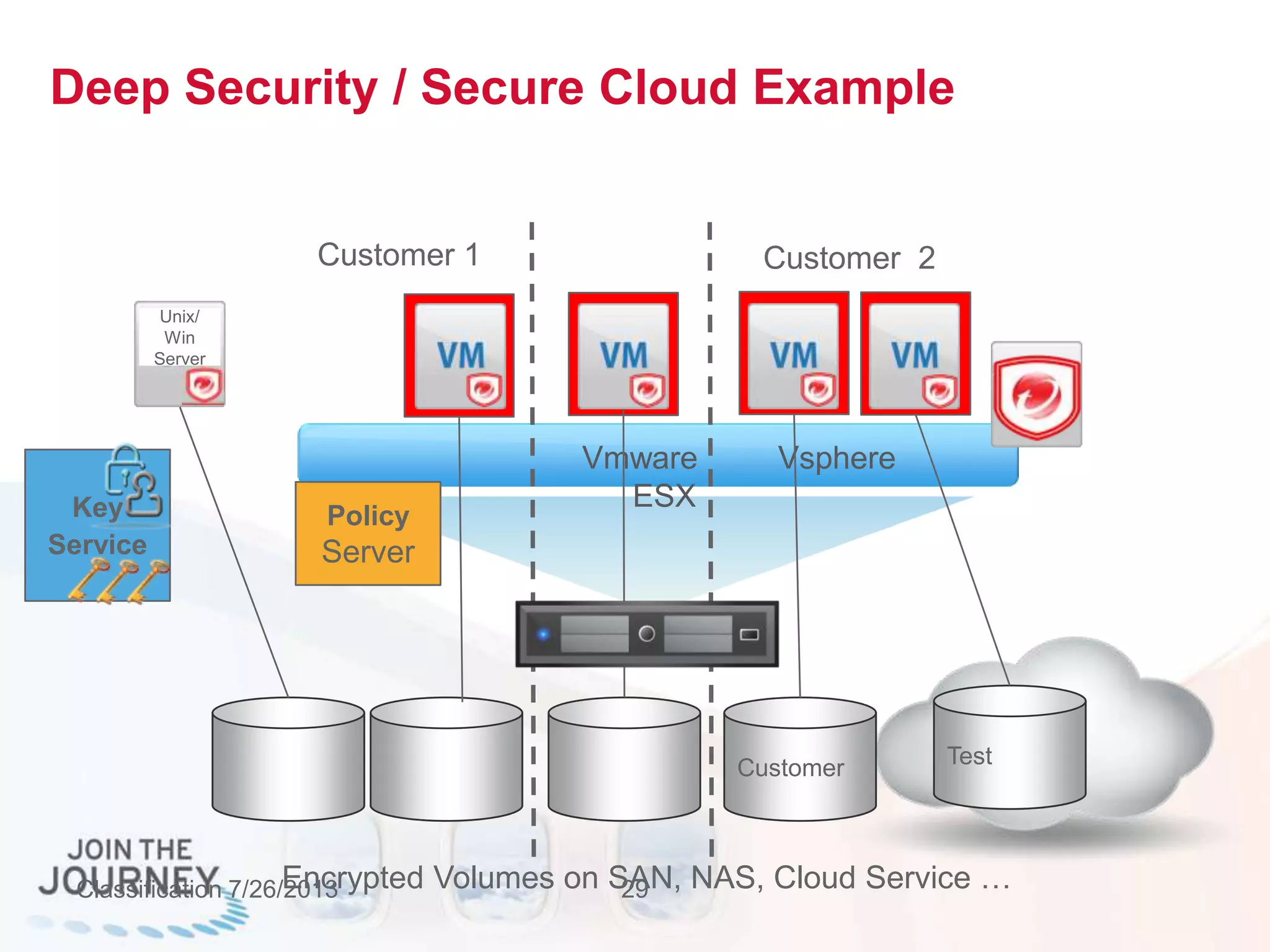
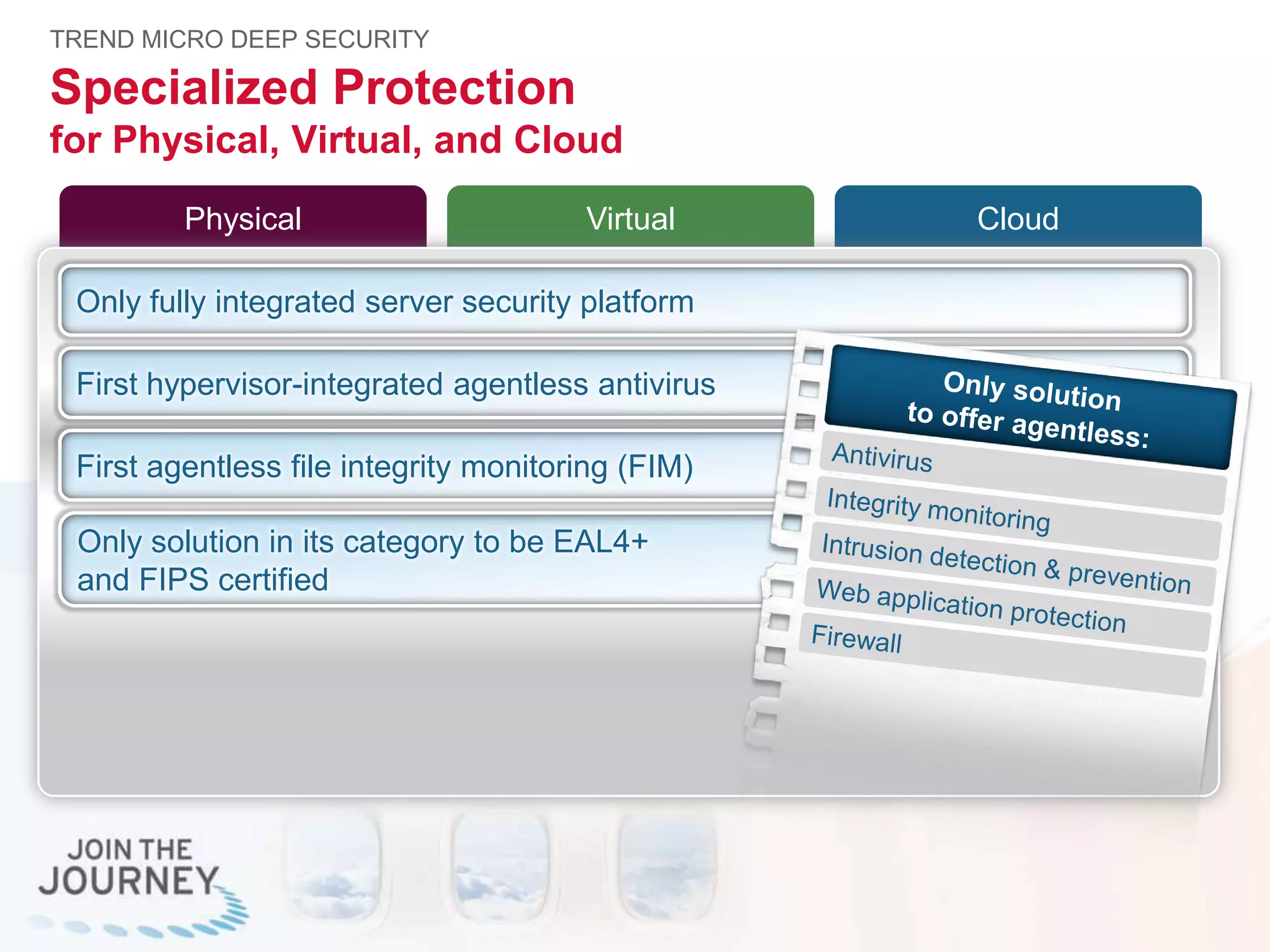
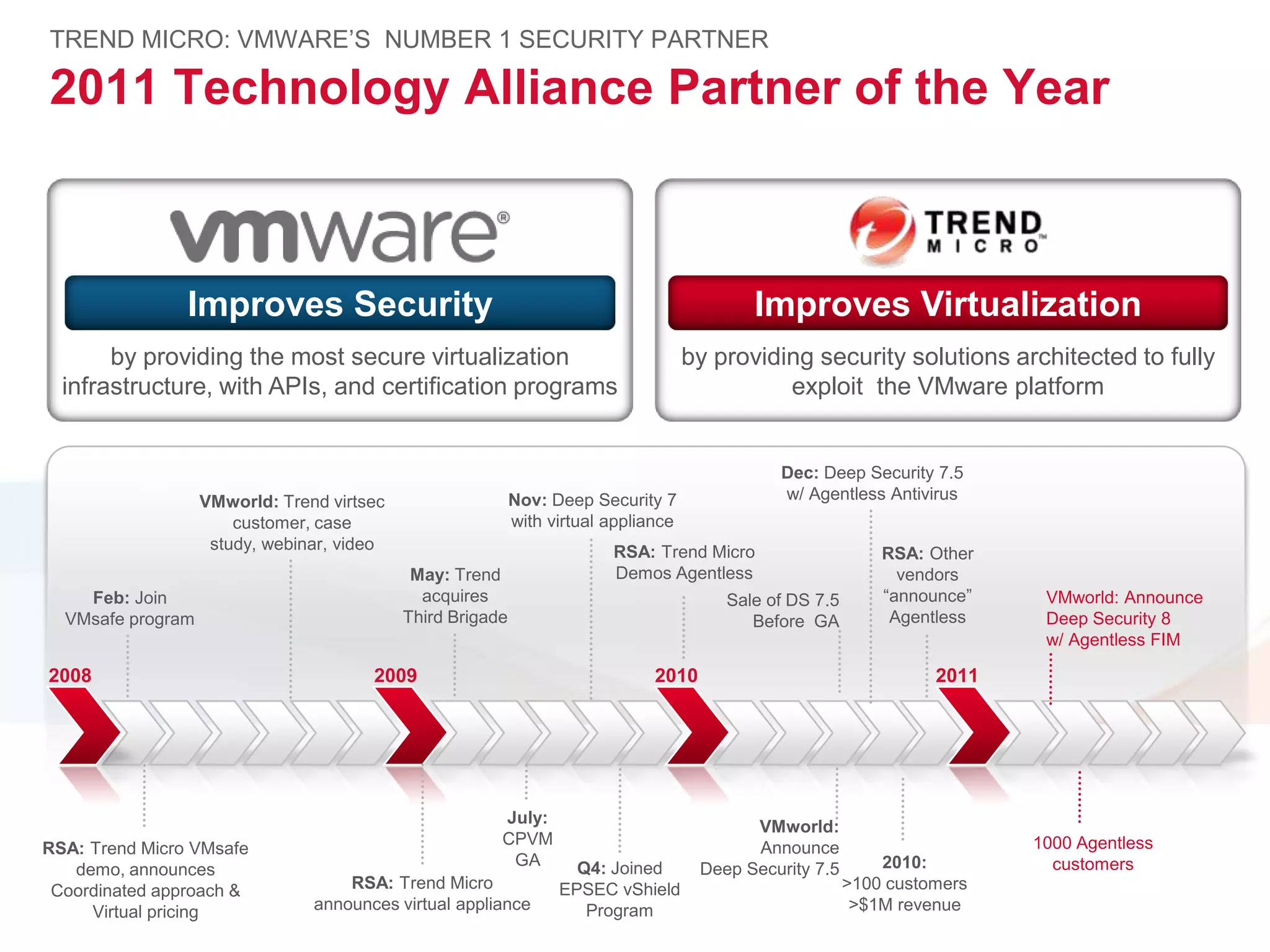
The document discusses the transition to cloud infrastructure, emphasizing the shared responsibility model for security in cloud environments, where customers must secure their content and applications. It highlights challenges related to virtualization security, including the risks of outdated security due to the dynamic nature of virtual machines and the need for integrated security solutions across physical, virtual, and cloud infrastructures. The document also outlines various technologies and strategies for threat detection, data protection, and ensuring compliance within a cloud context.