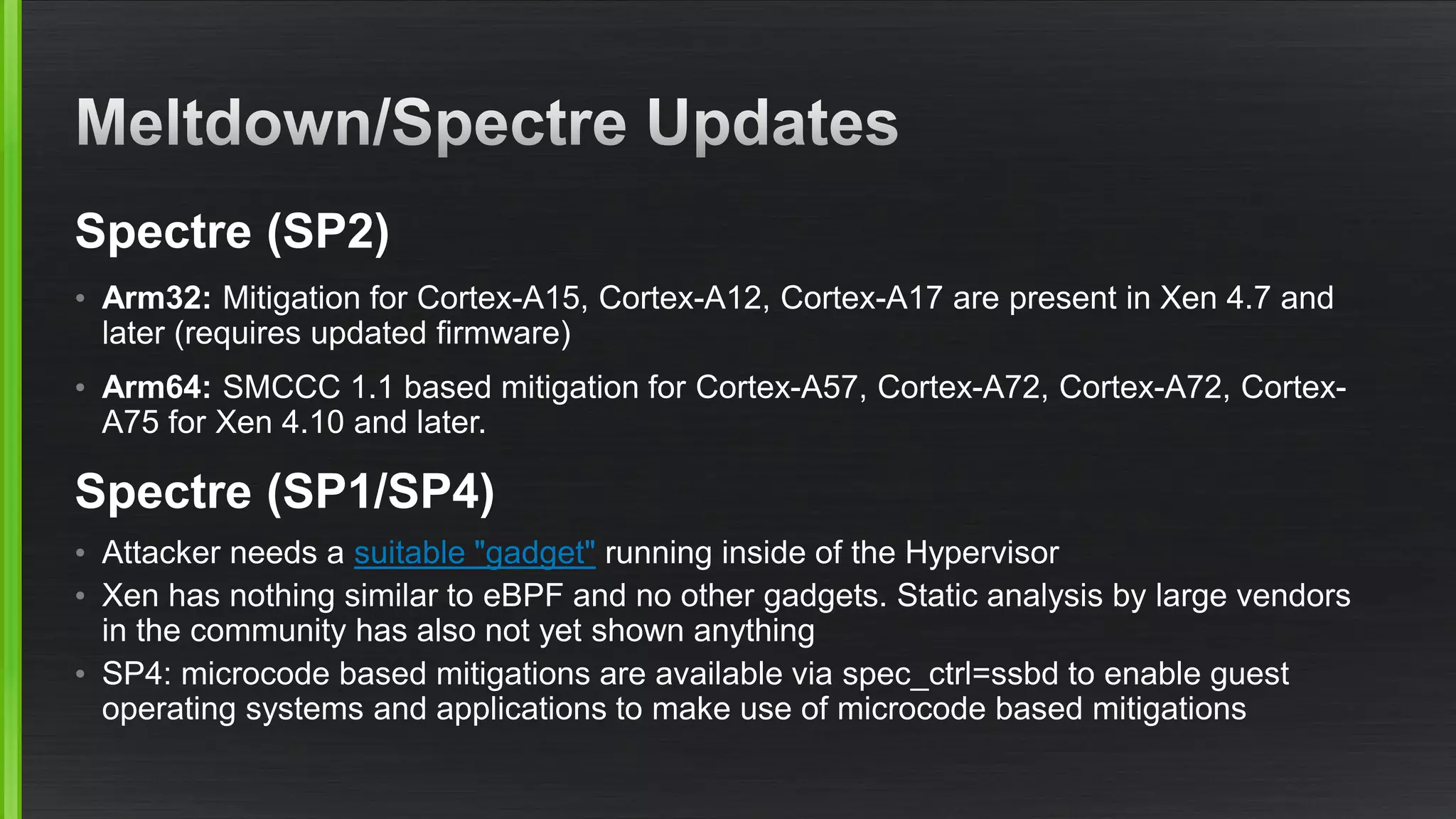
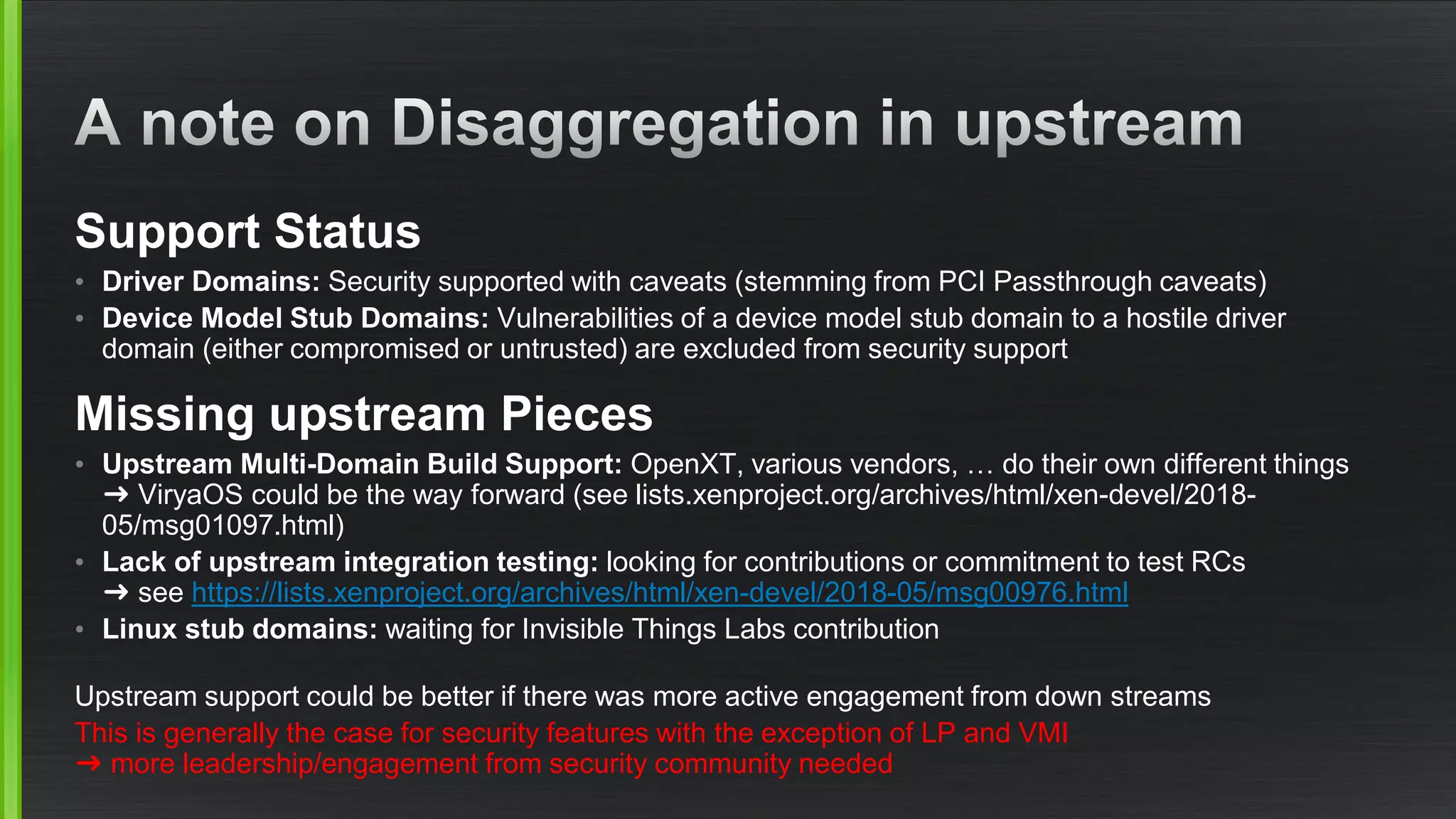
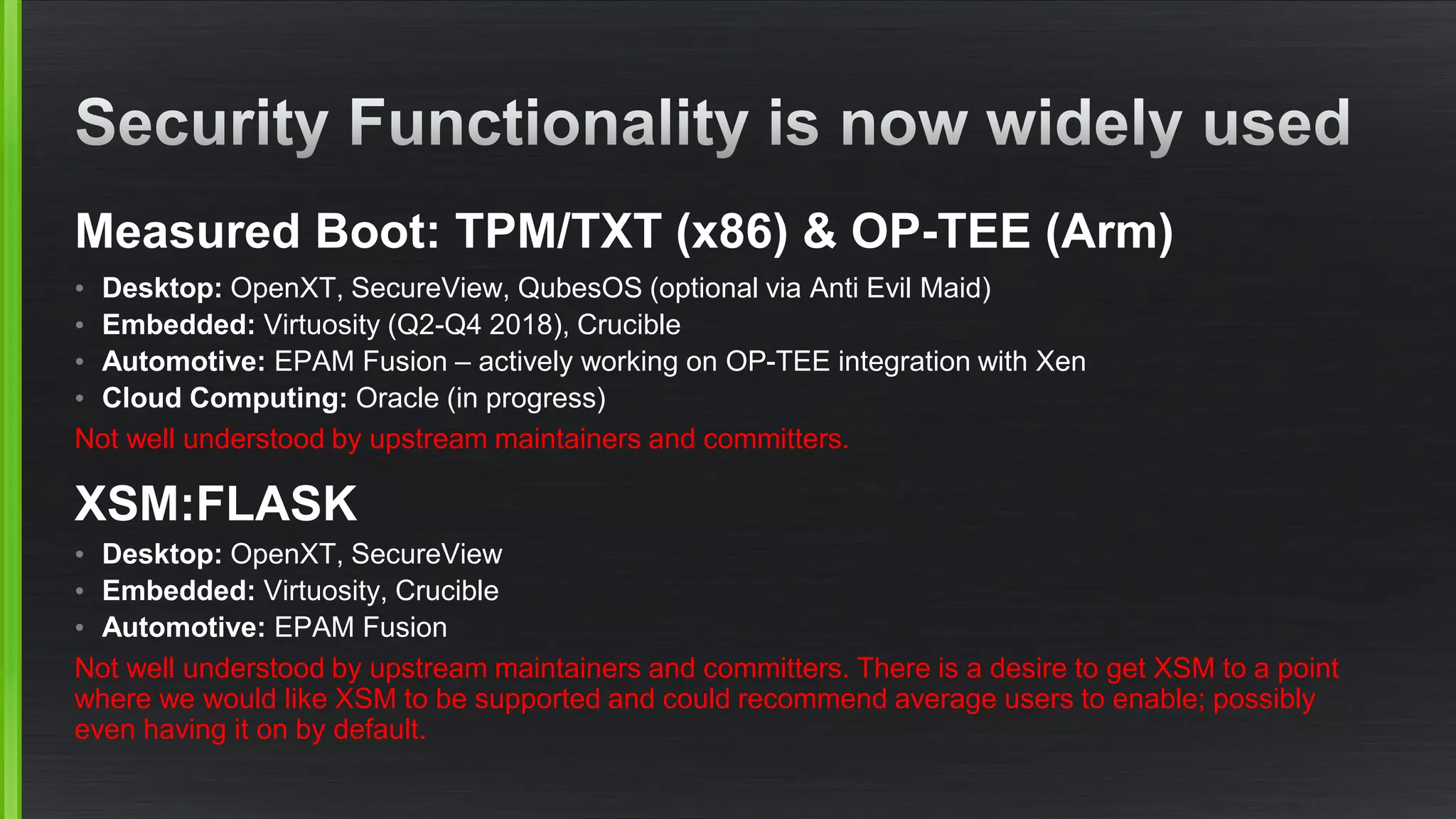
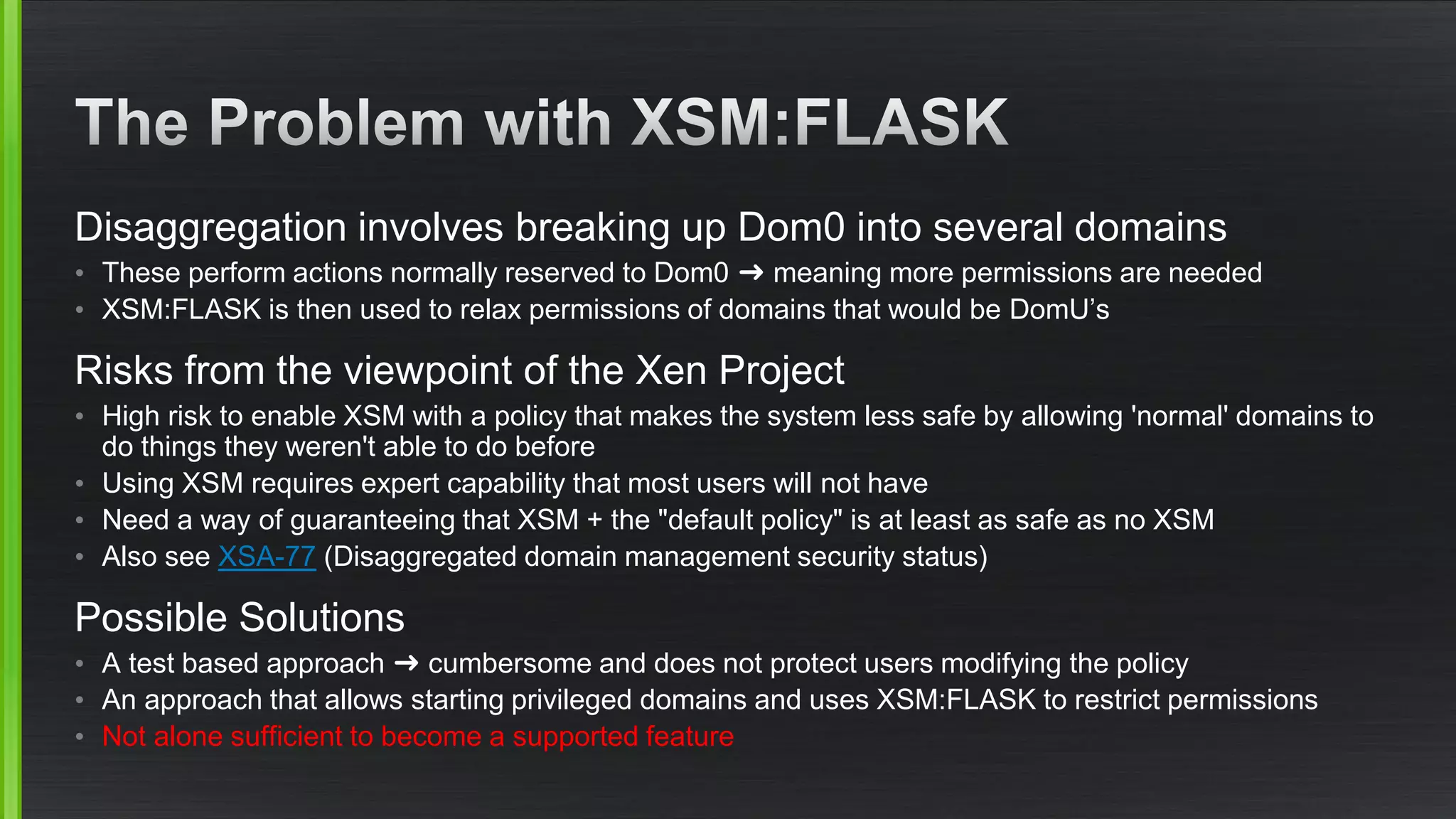
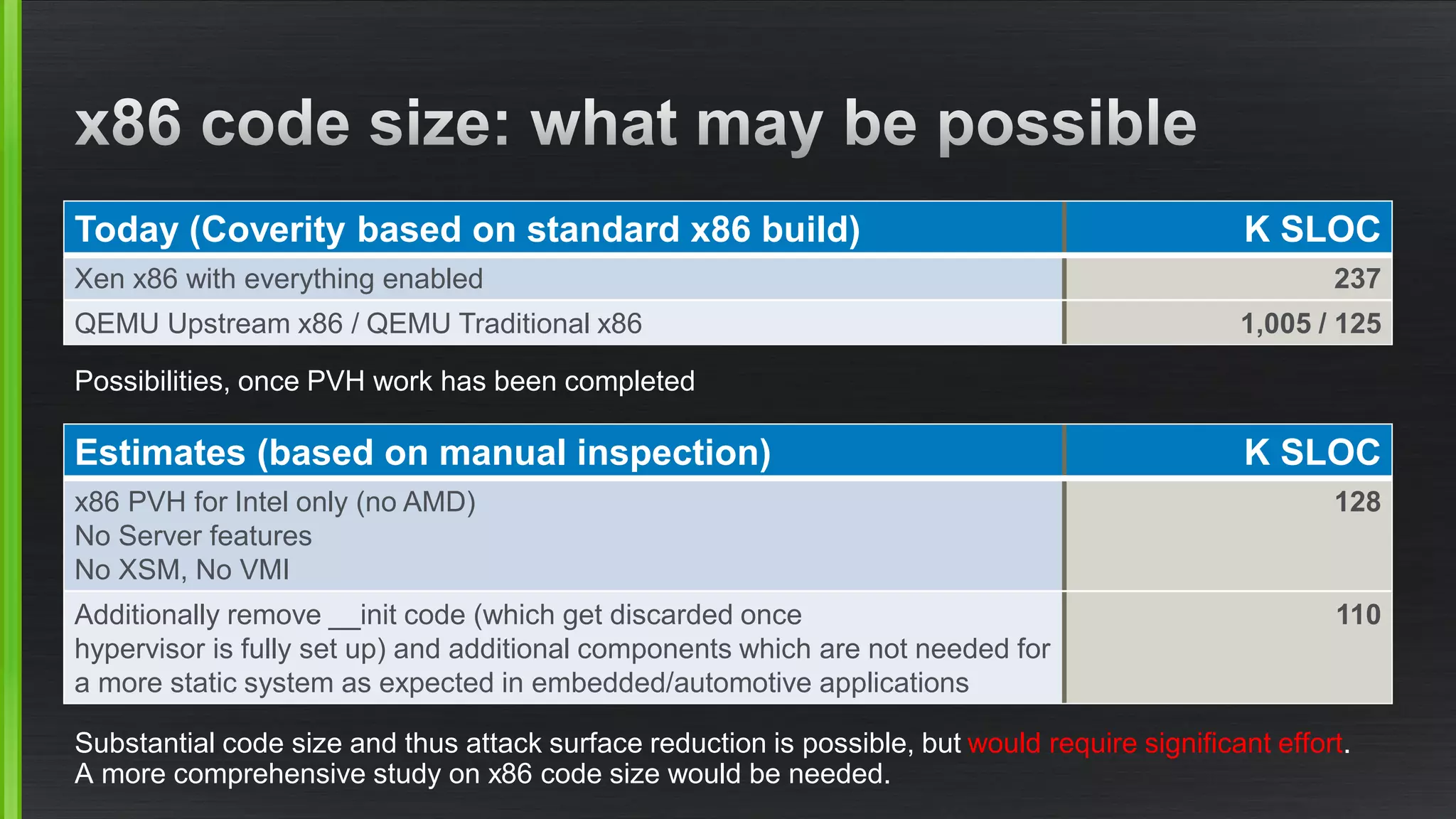
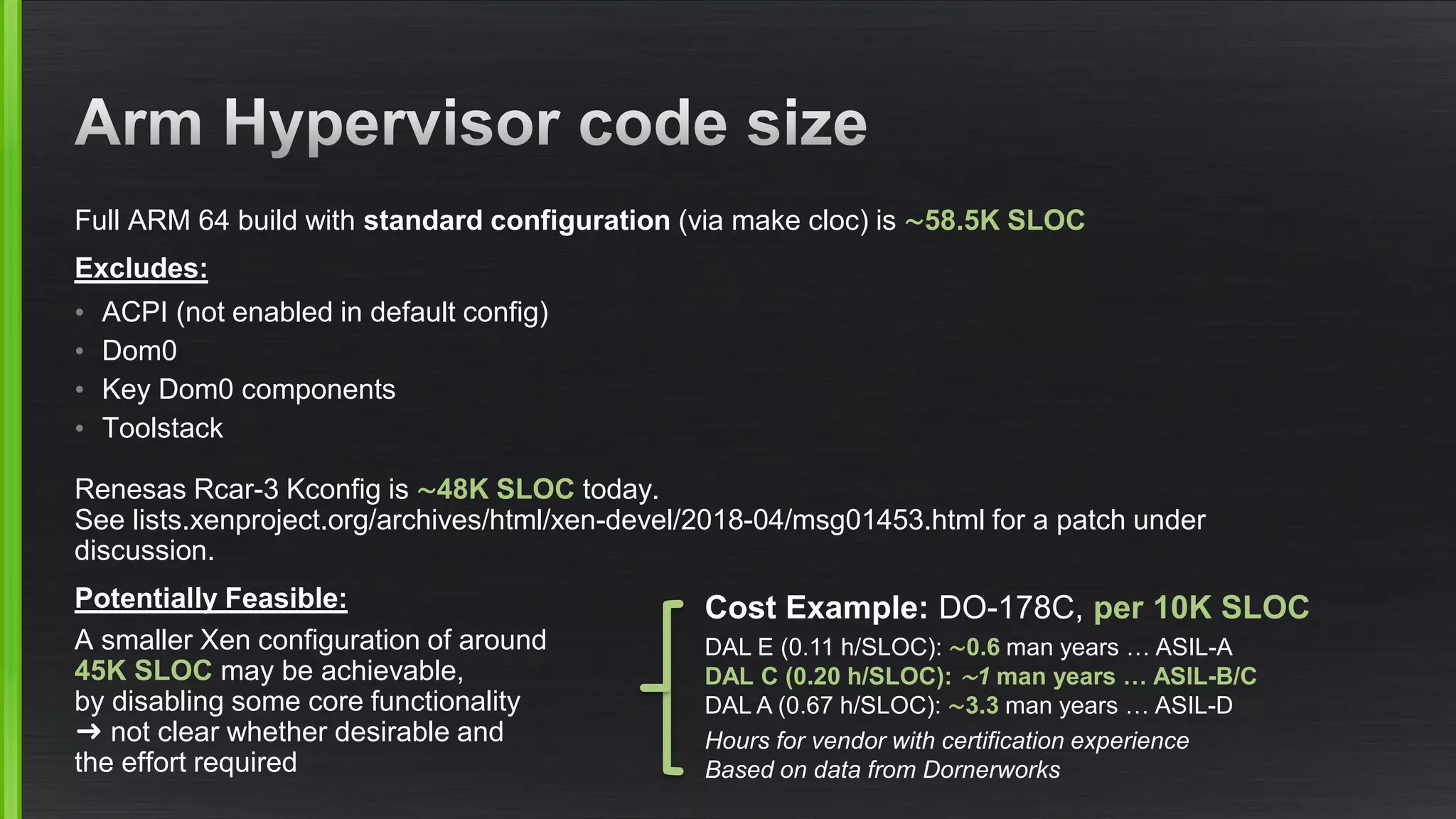
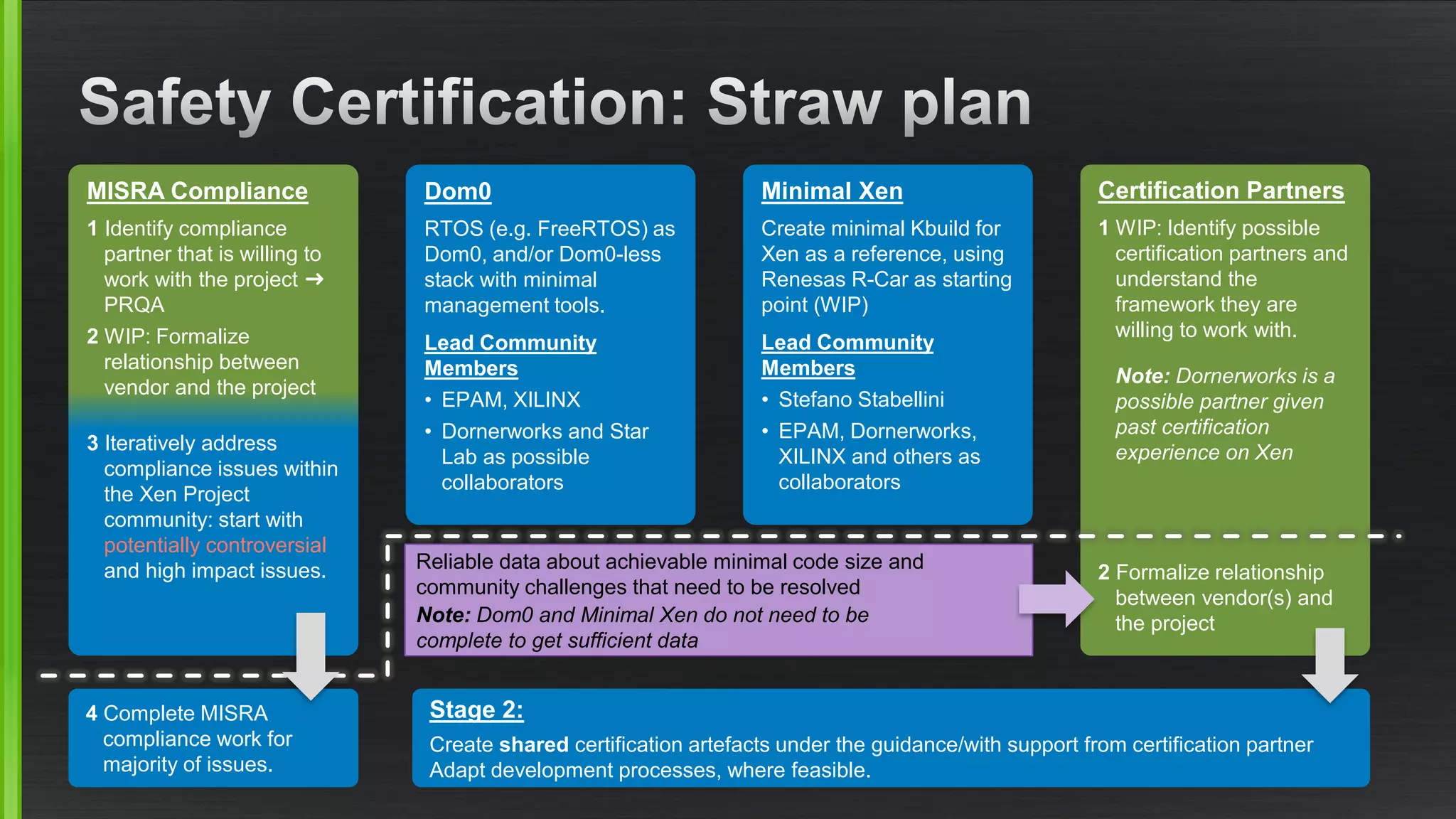
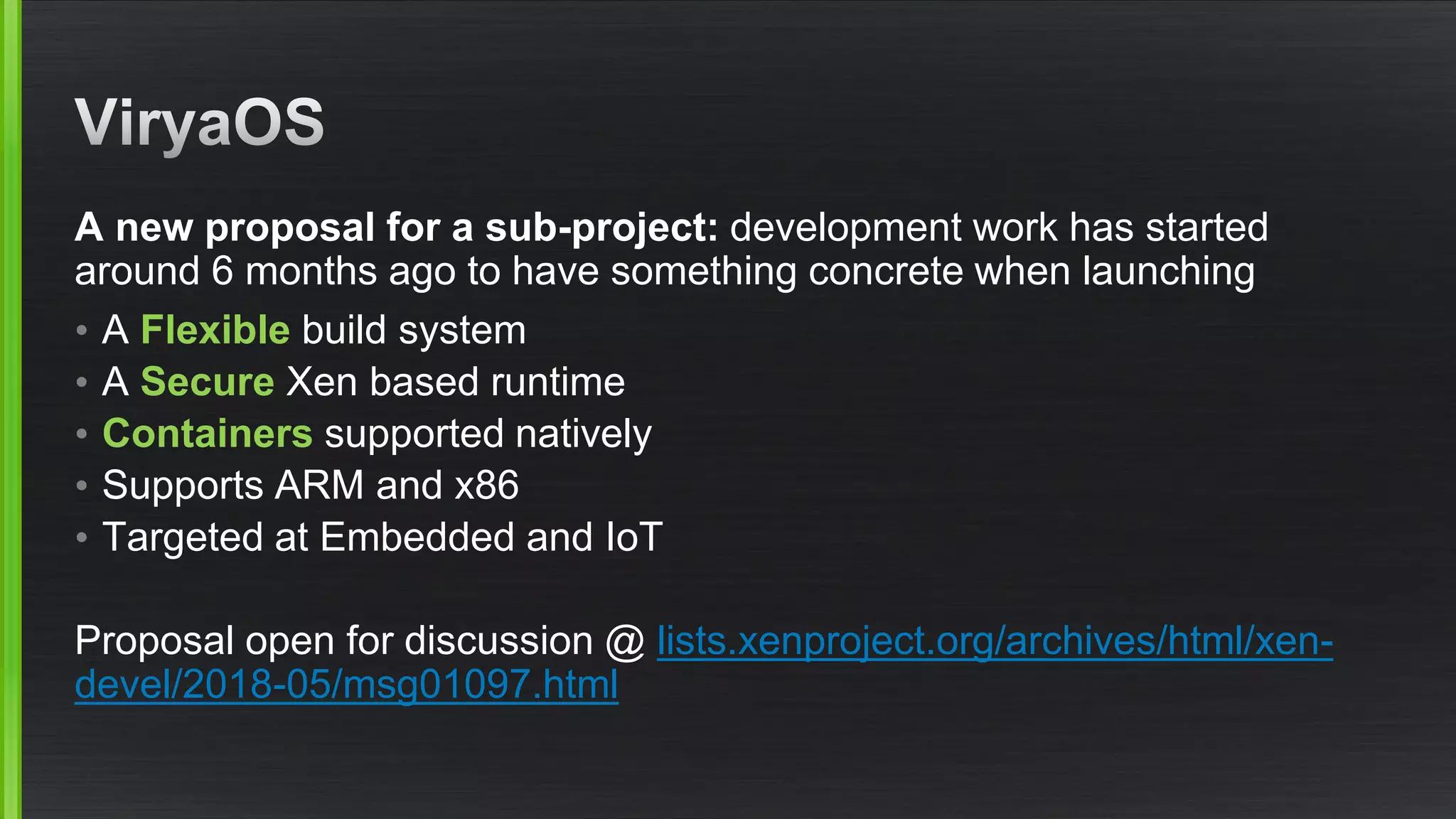
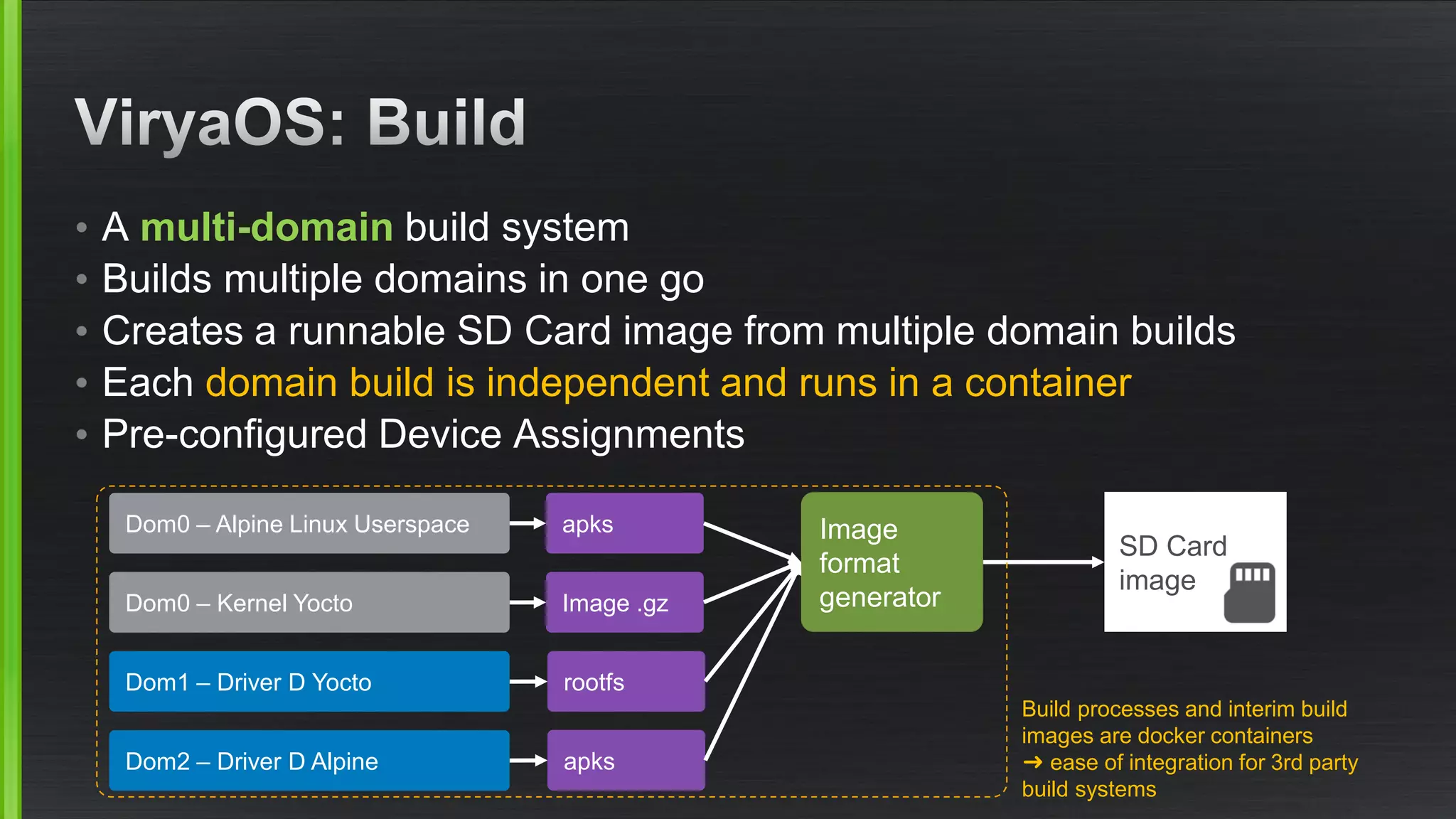
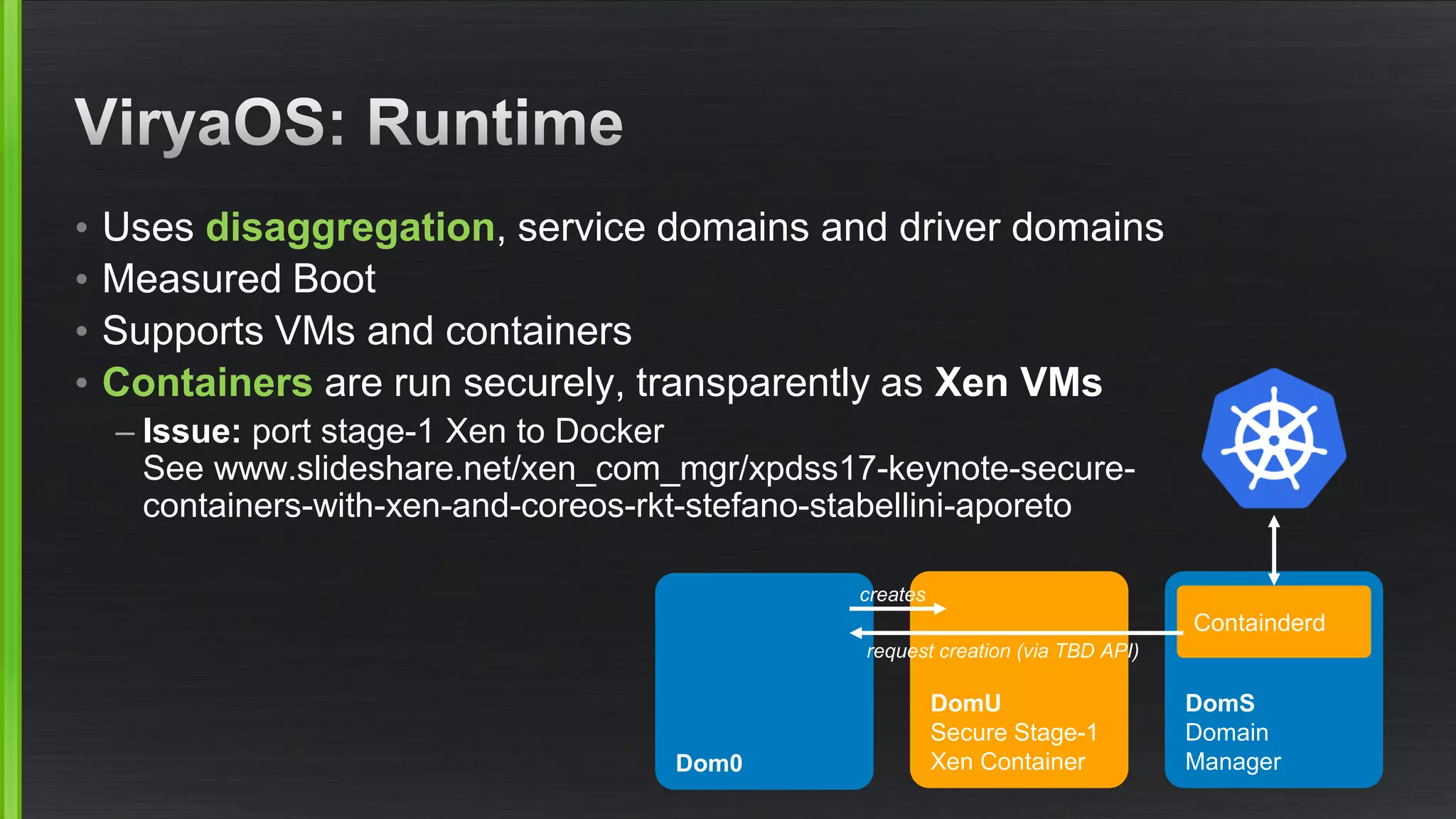
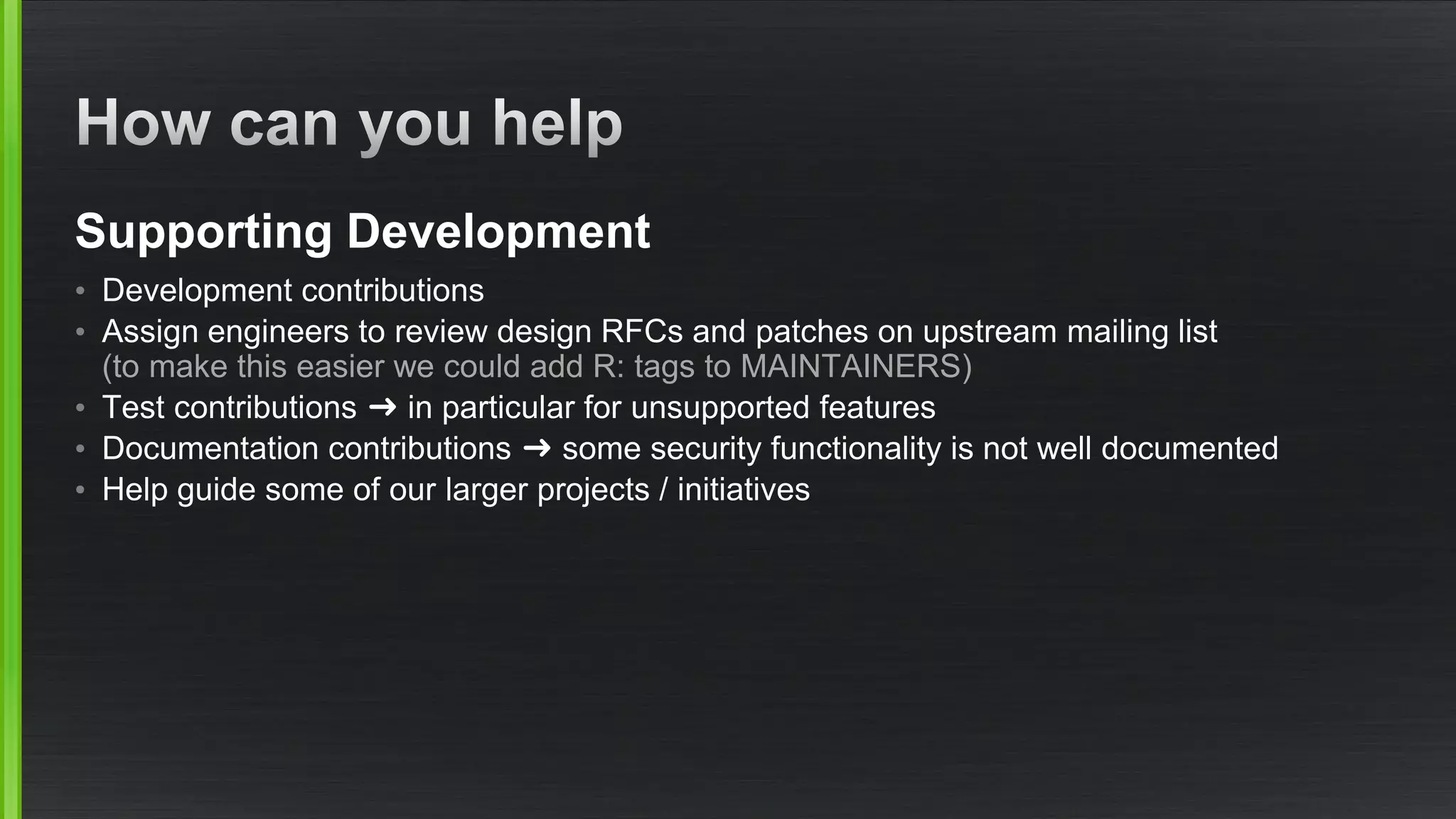
The document outlines various security mitigations and features for the Xen project, addressing vulnerabilities like Meltdown and Spectre across different architectures such as x86 and ARM. It discusses performance improvements, support statuses, and potential future developments, including disaggregation and certification efforts for safety-critical environments. It highlights the need for better upstream integration and community engagement to improve security features and support status.